
FOUNTAIN CODES FOR RELIABLE DATA TRANSMISSION IN
LOW VOLTAGE POWER-LINE NETWORKS
Juan Pedro Mu˜noz-Gea, Pedro Jose Pi˜nero-Escuer, Josemaria Malgosa-Sanahuja
Pilar Manzanares-Lopez and Juan Carlos Sanchez-Aarnoutse
Department of Information Technologies and Communications, Polytechnic University of Cartagena
Campus Muralla del Mar, 30202, Cartagena, Spain
Keywords:
Fountain codes, Online codes, Power-line communication, HomePlug AV, Home networking.
Abstract:
Home appliances are becoming information devices which can be networked to exchange information. No-
new-wires networks are the most promising candidate networking technologies to provide both residential
and Small and Medium Enterprise (SME) networking services. Among them, broadband communication over
power line networks has attracted much interest in academy and industry recently. The HomePlug Powerline
Alliance has developed a new specification for in-home networking called HomePlug AV. The HomePlug AV
MAC layer provides a connectionless, prioritized contention service based on CSMA/CA to support best-effort
applications. When there are connections competing for the channel utilization, UDP connections lose a big
amount of packets. In addition, the bidirectional nature of TCP protocol may not be the adequate transmission
mechanism in a half-duplex channel. In this scenario, the use of Fountain codes could be a good alternative
to UDP and TCP to transmit reliable data. Online Codes are a free-software Fountain codes version. In this
work, it is evaluated the feasibility to use Online Codes for binary data transmission in a low-voltage PLC
network.
1 INTRODUCTION
Nowadays, home appliances are becoming informa-
tion appliances and they can be networked to ex-
change their information. Therefore, it is necessary
a home network able to provide support for video
and data transmission from a variety of sources in the
home. Candidate networking technologies to provide
convenient and widespread residential networking
services may be categorized as wireless, wired and
no-new-wires networks. For the no-new-wires net-
works category, broadband communication over low
voltage (220v) power lines or PLC (Power Line Com-
munications) has attracted much interest in the aca-
demic and industrial context recently. The HomePlug
Powerline Alliance (Afkhamie et al., 2005) has de-
veloped a new specification for in-home networking
called HomePlug AV (HomePlug Audio and Video,
or simply HPAV). HomePlug AV employs advanced
physical and medium access control (MAC) technolo-
gies that provide a 200 Mbps power line network.
The physical layer utilizes this 200 Mbps rate to pro-
vide a 150 Mbps information rate. Nowadays, there
are about 70 certified HomePlug products (HomePlug
Certified Products, 2009). They range from a simple
HomePlug Ethernet adapter (which connects the Eth-
ernet devices to the HomePlug network) to 1 Gbps
high performance low-voltage PLC modem (Gigle,
2009). On the other hand, nowadays some companies
are adding HomePlug circuits directly into multime-
dia home entertainment equipment. By this way, it
will not be necessary any additional equipment (like
Ethernet adapters) to connect the electrical appliances
to the PLC network
However, it is necessary to take into account that
there are several aspects of the PLC medium that
make it difficult to share resources fairly. For exam-
ple, all the electronic or electrical equipments con-
nected to the power lines are considered as noise re-
sources on the power grid (Jensen and Kjarsgaard,
2007). Therefore, our first goal in this work is to char-
acterize the network behavior in presence of electrical
equipment of a typical home when using a commer-
cial HPAV modem.
135
Pedro Muñoz-Gea J., Jose Piñero-Escuer P., Malgosa-Sanahuja J., Manzanares-Lopez P. and Carlos Sánchez-Aarnoutse J. (2009).
FOUNTAIN CODES FOR RELIABLE DATA TRANSMISSION IN LOW VOLTAGE POWER-LINE NETWORKS.
In Proceedings of the 4th International Conference on Software and Data Technologies, pages 135-140
DOI: 10.5220/0002252001350140
Copyright
c
SciTePress

Another important aspect in PLC networks is
that, although the HPAV MAC layer provides a
connection-oriented service based on TDMA to sup-
port QoS requirements, almost all commercial HPAV
modems only support traditional connectionless, pri-
oritized contention service based on CSMA/CA to
transmit best-effort applications and applications that
rely on prioritized QoS. In other words, the PLC chan-
nel is broadcast (i.e. shared) and half-duplex by na-
ture. This fact made us think that the use of unidi-
rectional rateless codes to transmit the information
may be advantageous as opposed to traditional solu-
tions based on bidirectional (full-duplex) TCP pro-
tocol. Rateless codes are also known as Fountain
codes because the sender is theoretically always send-
ing coded packets. Some of them are lost in the noisy
channel but when the destination node has received
enough of them, the information can be completely
restored. They are mainly used in multimedia applica-
tions, such as IPTV or radio broadcasting, because in
these cases there is usually no feedback channel, and
it is impossible to take advantage of any type of er-
ror or flow control. Online Codes are a free-software
Fountain codes alternative, which achieve linear cost
for encoding and decoding operations. In this work,
the feasibility to use Online Codes for reliable data
transmission in an in-home PLC network is evaluated.
The remainder of the paper is organized as fol-
lows. Section 2 presents the HomePlug AV specifica-
tion. Section 3 introduces the encoding and decoding
procedure used by Online Codes. Section 4 evaluates
the use of Online Codes for data transmission in a real
scenario. Finally, Section 5 concludes the paper.
2 HOMEPLUG AV
As it was previously introduced, there are several as-
pects of the PLC medium that make it difficult to
share resources fairly. In order to solve these prob-
lems, advanced coding and modulation mechanisms
are used. The Physical Layer (PHY) operates in the
frequency range of 2 - 28 MHz and provides a 200
Mbps channel rate and a 150 Mbps information rate.
It uses OFDM and a powerful Turbo Convolutional
Code (TCC). OFDM is a spectrum efficient modu-
lation technique, which uses simultaneous transmis-
sion of a large number of narrow band carriers. These
carriers divide a large frequency channel into a num-
ber of subchannels. Subchannels can differ greatly
in their quality, defined by their signal to noise ratio-
SNR-. Adaptive coding modulation for each subchan-
nel solves this problem by giving each subchannels an
appropriate capacity, and by switching off those with
a poor channel condition.
HomePlug AV provides two kinds of commu-
nication services: a connection-oriented contention
free service, based on periodic Time Division Mul-
tiple Access (TDMA) allocations of adequate dura-
tion, to support the QoS requirements of demand-
ing applications; and a connectionless, prioritized
contention service, based on Collision Sense Multi-
ple Access/Collision Avoidance (CSMA/CA), to sup-
port both best-effortapplications and applications that
rely on prioritized QoS. To efficiently provide both
kinds of communication service, HomePlug AV im-
plements a flexible, centrally-managed architecture.
The central manager is called a Central Coordinator
(CCo). The CCo establishes a beacon period and a
schedule which accommodates both the cotention free
allocations and the time allotted for contention-based
traffic. The Beacon Period is divided into 3 regions:
beacon region, CSMA region and TDMA region.
3 FOUNTAIN CODES
3.1 Description
The main idea behind Fountain codes is that the trans-
mitter is represented like a fountain of water that is
able to produce an infinite number of water drops.
The receiver represents a bucket that needs to col-
lect a number of these water drops to obtain the in-
formation. The main advantage of these codes is that
the receiver can obtain the information irregardless
of which drops it has collected. Therefore, Fountain
codes should have the following properties:
• A transmitter can generate a potentially infinite
amount of encoded packets from the original data.
• A receiver can decode a message that would re-
quire K packets from any set of K
′
encoded pack-
ets, for K
′
slightly larger than K.
The most important implementations of Foun-
tain codes are LT codes (Luby, 2002), Raptor codes
(Shokrollahi, 2006) and Online Codes (Maymounkov
and Mazi`eres, 2003). LT codes were the first prac-
tical realization of a fountain code. The only draw-
back of these codes is that their encoding and decod-
ing costs scale as Klog
e
K, where K is the file size.
Raptor codes are an evolution of LT that achieve lin-
ear cost for encoding and decoding. Finally, Online
Codes are a free-software alternative to Raptor codes
that also achieve linear cost for both operations.
There are lots of application of Fountain codes
in digital communications. They are mainly used
in multimedia applications, such as IPTV or radio
ICSOFT 2009 - 4th International Conference on Software and Data Technologies
136

Figure 1: Structure of Online Codes.
broadcasting because in these cases there is no feed-
back channel. Therefore, it is impossible to take ad-
vantage of any type of error or flow control. Another
kind of service that could also use these codes is mul-
ticast transmission. When a transmitter sends a file to
different receivers, each of these receivers could ex-
perience independent losses, delays, jitter, etc. With-
out the Fountain codes facility, the number of control
packets needed to maintain the multicast connection
could be very high.
3.2 Online Codes
Online Codes are characterized by two parameters ε
and q. The first parameter is related to the number
of coded blocks (also called check blocks) that the
receiver needs in order to decode the original mes-
sage, and the second one has an effect on the proba-
bility of succesful decoding. In particular,the receiver
can recover the original message from any (1+ 3ε)K
check blocks with a success probability determined
by 1− (ε/2)
q+1
The structure of Online Codes is depicted in Fig.
1. The encoding process is divided into two layers,
the inner code and the outer code. The inner code is
in charge of generating the check blocks. Every check
block is computed as the XOR operation of d blocks
uniformly chosen from the message (d represents the
degree of the check block). The probability that d = i
is given by the probability distribution ρ
i
:
ρ
1
= 1−
(1+ 1/F)
(1+ ε)
(1)
ρ
i
=
(1+ ρ
1
)F
(F − 1)i(i− 1)
i = 2,3,...,F (2)
where F is given by
F =
ln(ε
2
/4)
ln(1 − ε/2)
(3)
However, due to the random selection of the mes-
sage blocks, some of them may not be selected in the
inner coding process. One solution to this problem is
to add a preliminar coding process (called outer cod-
ing) which generates 0.55qεK auxiliary blocks from
the original message. The message blocks that do not
participate in the inner process will be able to be de-
coded thanks to this redundancy. In fact, the input
blocks of the inner coding are the message blocks plus
auxiliary blocks. All this set is called composite mes-
sage.
From all the available procedures to gener-
ate redundancy (Reed-Solomon, Cyclic Redundancy
Check, Parity Bits, etc.), Online Codes uses one of
the simplest: for each block of the original message,
q auxiliary blocks are chosen. Each auxiliary block is
computed as the XOR operation of the original mes-
sage blocks assigned to it.
The original message can be decoded from the
check blocks, with the success probability showed be-
fore. The decoding process is also divided into two
steps. In the first step a 1 − ε/2 fraction of compos-
ite message blocks should be recovered. The knowl-
edge of this fraction of blocks is enough to decode the
original message: the composite message has such a
property thanks to the redundancy added by the outer
code. The second step consists of recovering the orig-
inal message from the composite message blocks re-
covered in the first step.
In order to successfully recover the needed frac-
tion of composite message blocks, it is necessary to
get to know the degree of each check block and the
composite message blocks from which it is made up
(also called adjacent blocks). A way to send this in-
formation to the receiver must be implemented on
the transmitter side. However, if the receiver uses
the same random number generation algorithm as the
transmitter, it will only be necessary to send the seed
to reach this objective. Next, the decoding process
can start. It has the following steps:
1. Find a check block with only one adjacent block
(d = 1) and recoverthis composite message block.
2. Remove this recovered block from other check
blocks that also have this recovered block as adja-
cent (by simple substracting it; that is, computing
the XOR again). After this, some check blocks
can become degree-one blocks.
3. Continue with this process until a 1−ε/2 fraction
of composite message blocks is recovered.
The process can fail if in some of these steps there
are no degree-one blocks.
When all the needed composite message blocks
are recovered, the same process can be used to obtain
the original message blocks. In this case the success
probability is close to one because only the auxiliary
blocks have a degree higher than one.
FOUNTAIN CODES FOR RELIABLE DATA TRANSMISSION IN LOWVOLTAGE POWER-LINE NETWORKS
137

4 EVALUATION
In this section we want to evaluate two characteris-
tics of HomePlug AV specification: First, the variable
capacity model of the physical layer; and second, the
contention-based service of the MAC layer. All the
evaluations presented in this section have been made
using a laboratory test-bed. The lab has three phases
of 220 volts, and all the PLC adapters and PC comput-
ers used in the evaluation are connected to the main
phase. We have used the PLE200 HomePlug AV Eth-
ernet adapters of Linksys (Cisco-Linksys, 2009). This
adapter connects the Ethernet device of a computer to
the 220 V power line.
4.1 Evaluation of the Variable Capacity
of the Physical Layer
Our first objective is to evaluate the adaptation of the
data transmission rate according to the noise level.
For this aim, we use two computers connected to the
HomePlug AV network using the corresponding Eth-
ernet adapters. Their power suppliers are connected
to another electrical phase of the lab, different from
the one used to implement the HomePlug AV net-
work. Knowing that in Europe the common point of
two distinct phases is located in the low voltage trans-
former, the distance between two elements connected
to different phases is around 300 meters. This dis-
tance is large enough to ensure the absence of inter-
ference among devices connected to different phases.
In order to measure the capacity of the network,
we used a UDP traffic generator which transmits traf-
fic to the maximum capacity allowed by the physical
network. We achieved the results presented in Fig.
2. In particular, it can be observed that the network
is able to achieve a maximum capacity around of 80
Mbps (which is nearly to the maximum capacity as-
signed to the CSMA region). Next, after 8 seconds,
we connected the power suppliers of all the avail-
able computers in the lab to the electrical phase of
the HomePlug AV network. In Fig. 2 it can be ob-
served that the connection of all the computers to the
power line causes the reduction of the network capac-
ity to 60 Mbps. After 17 seconds, we disconnected
all the computers from the electrical line and we de-
tected that the transmission rate increased up to 80
Mbps again. The reason for this phenomenom is that
the powerful coding and modulation technique used
in HomePlug AV is able to adapt the transmission
speed according to the noise level generated by the
electrical devices in order to avoid the losses of pack-
ets.
5e+07
5.5e+07
6e+07
6.5e+07
7e+07
7.5e+07
8e+07
8.5e+07
0 5 10 15 20 25
Throughput [Bits/sec]
Time [secs]
Figure 2: Evaluation of the network capacity.
4.2 Evaluation of the Contention-based
Service of the MAC Layer
As it was previously introduced, the HomePlug AV
MAC layer offers a contention service based on
CSMA/CA. In packet communication networks, con-
tention is a media access method that is used to share
a broadcast medium. In this method all the hosts con-
nected to the medium compete in order to transmit
to the broadcast medium and they can only do that
when the channel is “idle”. In order to evaluate this
characteristic of HomePlug networks, in our next ex-
periment we establish three simultaneous (compete
against one another) file transmissions using UDP
connections, and we evaluate the performance of one
of them. The size of the transmitted file varies from 1
up to 20 Mbytes and the distance between the PLC de-
vices of the measured connection is about 45 meters.
This is aproximately the longest distance between two
PLC devices in a real in-home scenario (worse case).
The most remarkable result is the big proportion of
lost packets, represented in Table 1. It means that
the UDP receiver is not able to receive the full files.
These losses are mainly due to the buffer overflow at
the PLC interface because the incoming packet rate
is greater than the outgoing rate at which CSMA/CA
can transmit packets. Therefore, in this environment
the use of UDP applications which do not implement
any flow control is not recommended for reliable data
transmission.
In order to avoid the losses of packets in a con-
tention environment,like a HomePlug networks, there
are two options: first, using a protocol that imple-
ments a flow control mechanism, for example TCP
(Transmission Control Protocol); second, using an ap-
plication that implements some kind of forward error
correction, for example, the use of Fountain codes. In
the following experiments, we want to compare the
ICSOFT 2009 - 4th International Conference on Software and Data Technologies
138
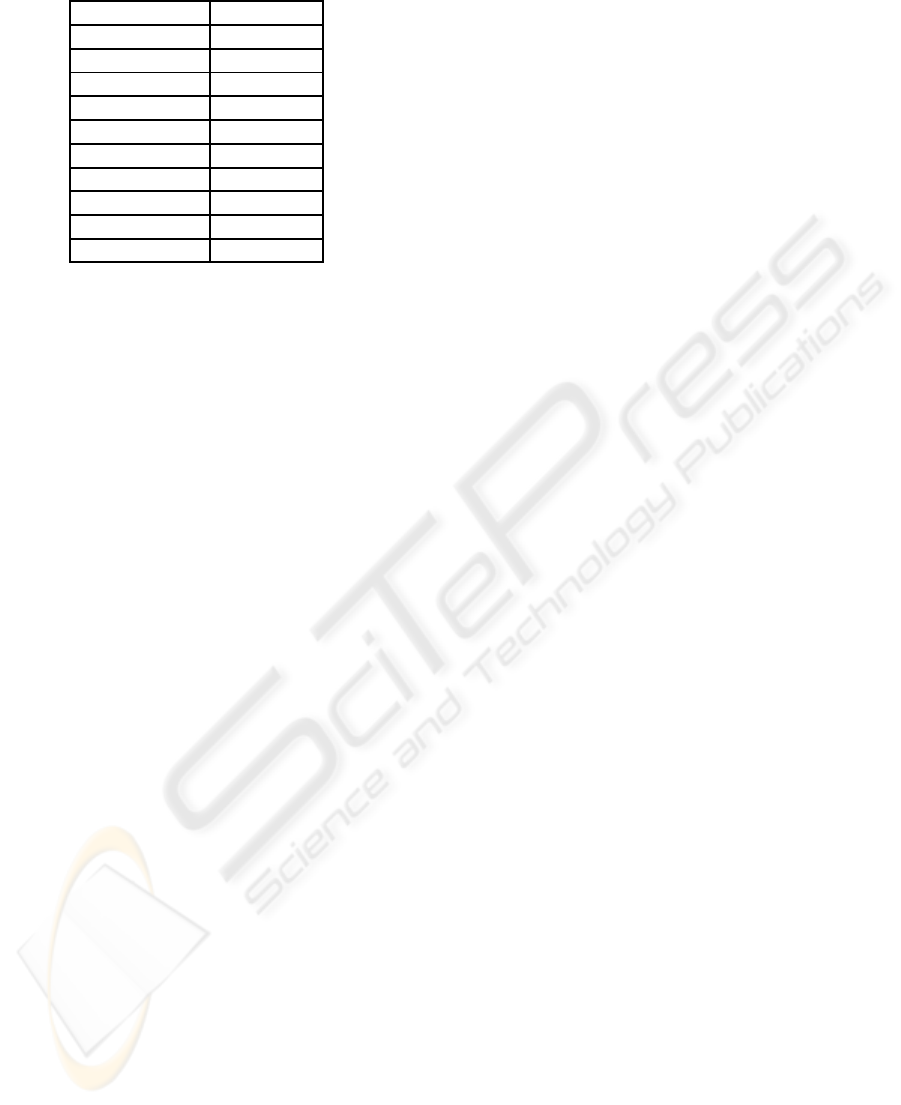
Table 1: Proportion of lost packets in UDP connections.
File size [MB] Losses [%]
1 0
2 16.66
3 36.5
4 38.17
5 30.84
6 40.77
8 34.73
10 41.45
15 37.25
20 37.73
performance achieved by two file tranmission appli-
cations, one of them uses TCP as transport protocol,
and the other one uses a kind of Fountain codes (con-
cretely Online codes).
We used the scp program (scp, 2009) as a TCP-
based file transmission application. On the other
hand, in order to implement the application based on
Online codes, we used the Online Codes implemen-
tation available in (Implementation of Online Codes,
2009). UDP transmission capability has been added
to this implementation. In contrast with some real-
time multimedia applications, in a file transmission
application the packet loss probability must be zero
(i.e., the file must be fully received). In order to
achieve this with Online Codes, the decoding fail-
ure possibility must be eliminated. This is obtained
by trying to decode the original information for ev-
ery received block. When the process fails, the re-
ceiver waits for the next check block and it tries to de-
code it again. With this method the number of check
blocks that need to be decoded is a little bigger than
(1+3ε)K, but the decoding failure probability is zero.
However, our application does not really decode
the received blocks, it only deduces whether the re-
ceived packets are enough to decode the original file,
and it finishes when it has already received enough
packets in order to decode it. This program imple-
ments a “light decoding” process and it gives as a
result the previous amount of packets. The decod-
ing mechanism can be implemented by another con-
current program, or it may be performed when the
previous program has finished, that is, when it has
received the necessary blocks to decode the original
file. On the other hand, the packets can also be stored
in a coded way. This second option could be a good
choice if the coded packets are going to be retrans-
mited (e.g. in a P2P network) or if a OS implements
a facility that is able to recognize this kind of coded
files.
Both file transmission applications are evaluated
in a contention scenario, with other two simultaneous
file transmission connections. The size of the trans-
mitted file varies from 1 up to 20 Mbytes. In this
case, both applications are able to receive the full file
without errors. Therefore, in the evaluation we are
going to compare them taking into account the neces-
sary time to receive the full file. The distance between
the PLC devices of the measured connection is about
45 meters, like in the UDP scenario. Fig. 3 shows
the average duration of the scp and Online Codes ses-
sions, extracted from 5 different sessions. In addition,
the figure also represents the 95% confidence inter-
val. The first result that can be concluded from the
previous figure is that the Online Codes sessions are
always faster than the scp sessions. In addition, the
increase of the scp sessions with respect to the Online
Codes sessions is approximatelyconstant and equal to
1 second, though for big files this increment increases
up to 2 seconds. Therefore, we can draw that in a con-
tention scenario the performance achieved by an On-
line Codes-based file transmission application is bet-
ter than the performanceachieved by a TCP-based file
transmission application. Although not represented,
we have also tested the FTP protocol, which also uses
TCP as transport protocol. In this case, the sessions
duration are always higher than with scp, and there-
fore the difference between the Online Codes appli-
cation and FTP is also higher.
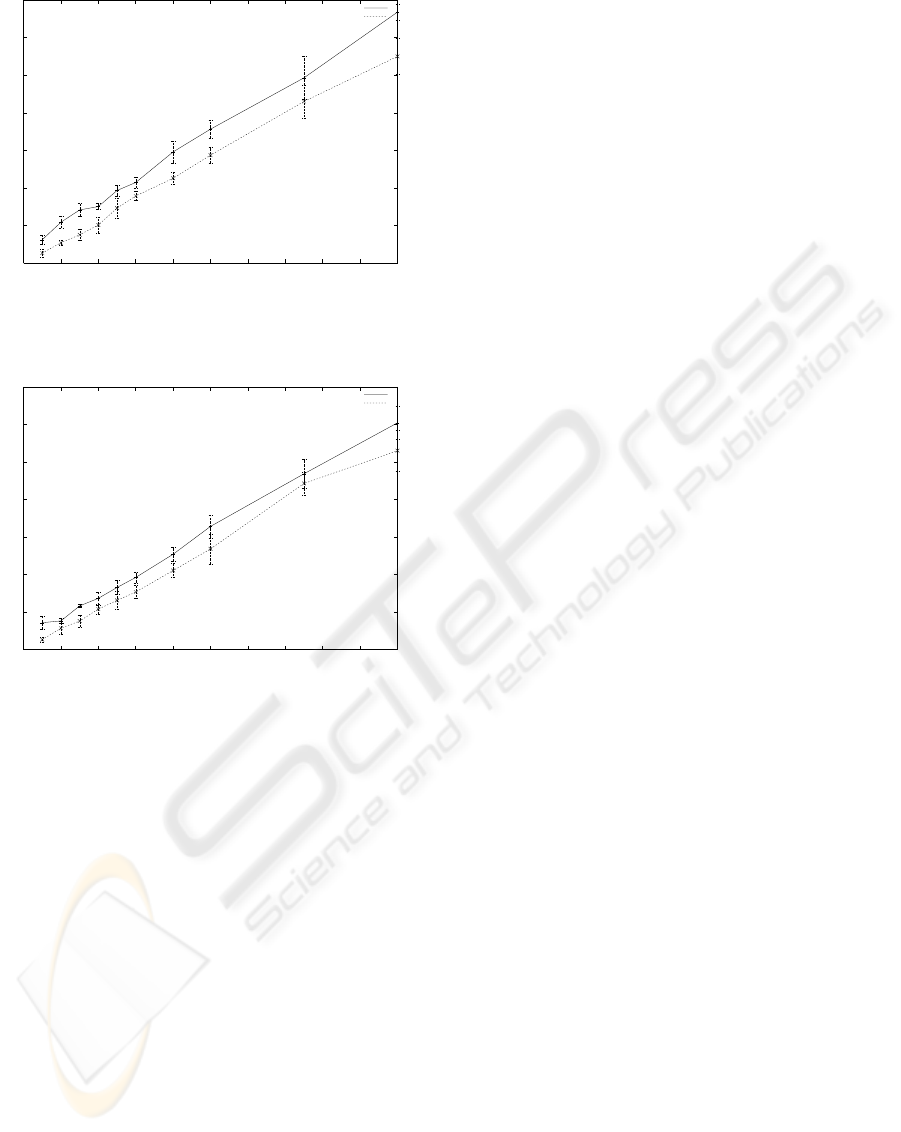
Next, both file transmission applications are eval-
uated again in a contention scenario, but in this case,
with four simultaneous file transmission connections.
Fig. 4 shows the average duration of the scp and On-
line Codes sessions, extracted again from 5 different
sessions, and the associated 95% confidence interval.
In this scenario, the Online Codes sessions are also
faster than the scp sessions. However, in this case the
increase of the scp sessions with respect to the On-
line Codes sessions is higher than in the previous sce-
nario, approximately equal to 2 second, and for big
files this increment increases up to 4 seconds. On
the other hand, if we compare these results with those
presented in Fig. 3, we can observe that the increase
of simultaneous file transmission connections causes
an increase in the length of the sessions. This result is
absolutely obvious because in this case the broadcast
medium has to be shared by a bigger number of users.
As a conclusion, in multiple access networks (like
in-home PLC based networks), the access control
mechanism produces losses in unidirectional (like
UDP) transmissions. In these cases, it is necessary
to add some type of flow control (e.g. using TCP
as transport protocol), or implementing some kind of
forward error correction, for example, the use of On-
line Codes. We have compared the session lengths
FOUNTAIN CODES FOR RELIABLE DATA TRANSMISSION IN LOWVOLTAGE POWER-LINE NETWORKS
139
0
2
4
6
8
10
12
14
0 2 4 6 8 10 12 14 16 18 20
Time [secs]
File Size [MB]
TCP
Online Codes
Figure 3: Duration of TCP (scp) and Online Codes sessions
in a noisy channel with two (background) data flows sharing
the channel. The confidence interval has been set to 95%.
0
5
10
15
20
25
30
35
0 2 4 6 8 10 12 14 16 18 20
Time [secs]
File Size [MB]
TCP
Online Codes
Figure 4: Duration of TCP (scp) and Online Codes sessions
in a noisy channel with four (background) data flows shar-
ing the channel. The confidence interval has been set to
95%.
of a TCP file transmission application and an Online
Codes based application, and we have extracted that
the Online Codes sessions are always faster than the
TCP sessions. Therefore, we have proved that in con-
tention scenarios the performance achieved by Online
Codes is better than the performance achieved by a
TCP-based file transmission application.
5 CONCLUSIONS
Online Codes must be mainly used when the net-
work or the application is unidirectional (broadcast-
TV, satellite, IP live-TV, etc.) or in applications that
cannot directly use TCP (like Application Layer Mul-
ticast). However, in a multiple access in-home net-
work (HPAV, wireless 802.11, PhonePNA, etc.) the
Online Codes are a good alternative to TCP for reli-
able data transmission.
ACKNOWLEDGEMENTS
This research has been supported by project grant
TEC2007-67966-C03-01/TCM(CON-PARTE-1) and
it is also developed in the framework of “Programa de
Ayudas a Grupos de Excelencia de la Regi´on de Mur-
cia, de la Fundaci´on S´eneca, Agencia de Ciencia y
Tecnolog´ıa de la RM (Plan Regional de Ciencia y Tec-
nolog´ıa 2007/2010)”. Pedro Jos´e Pi˜nero-Escuer also
thanks “Fundaci´on S´eneca” for a S´eneca Program FPI
pre-doctoral fellowship.
REFERENCES
Afkhamie, K. H., Katar, S., Yonge, L., and Newman, R.
(2005). An overview of the upcoming homeplug av
standard. In Proceedings of 2005 Internacional Sym-
posium on Power Line Communications and its Appli-
cations.
Cisco-Linksys (2009). Cisco-linksys. http://www.linksys
bycisco.com/.
Gigle (2009). Gigle semiconductor. http://www.gigle.biz/.
HomePlug Certified Products (2009). Homeplug certified
products. http://www.homeplug.org/kshowcase/view.
Implementation of Online Codes (2009). Implementation
of online codes. http://sourceforge.net/projects/online
codes/.
Jensen, B. and Kjarsgaard, S. (2007). Benchmarking and
qos of in-house powerline equipment under noisy con-
ditions. In Proceedings of 2007 Internacional Sympo-
sium on Power Line Communications and its Applica-
tions.
Luby, M. (2002). Lt codes. In Foundations of Computer
Science, 2002. Proceedings. The 43rd Annual IEEE
Symposium on, pages 271–280.
Maymounkov, P. and Mazi`eres, D. (2003). Rateless codes
and big downloads. In Peer-to-Peer Systems II, Sec-
ond International Workshop, IPTPS 2003, Berke-
ley, CA, USA, February 21-22,2003, Revised Papers,
pages 247–255.
scp (2009). scp-secure copy. http://www.mkssoftware.com/
docs/man1/scp.1.asp.
Shokrollahi, A. (2006). Raptor codes. IEEE/ACM Trans.
Netw., 14(SI):2551–2567.
ICSOFT 2009 - 4th International Conference on Software and Data Technologies
140
