
SECURE COMMUNICATION IN MOBILE AD HOC NETWORK
USING EFFICIENT CERTIFICATELESS ENCRYPTION
Peter Hyun-Jeen Lee, Shivaramakrishnan Narayan and Parampalli Udaya
Department of Computer Science and Software Engineering, University of Melbourne, Victoria, 3010, Australia
Keywords:
CLE, MANET, Bilinear Pairing, IBE.
Abstract:
Establishing secure communication in a wireless network such as Mobile Ad Hoc Network (MANET) is par-
ticularly challenging because: (i) the network is self-organizing; (ii) messages are broadcasted; (iii) messages
travel in a hop-by-hop manner; (iv) nodes are constrained in terms of computation and battery power. We pro-
pose a flexible and efficient Certificateless Encryption scheme which is optimized for MANET environment.
Further, we couple the idea of Resurrecting Duckling with the scheme to achieve efficient key establishment
and demonstrate the use of the transparent policy encoder which facilitates the authentication. We also show
the security of the scheme in random oracle model assuming k-Bilinear Diffie-Hellman Inversion problem is
hard.
1 INTRODUCTION
Wireless network is gaining increasing attention due
to its freedom in connectivity. Mobile Ad Hoc Net-
work (MANET) is one such a network where it is
particularly challenging to enforce security. This is
because MANET is a self-organizing wireless net-
work where messages are broadcasted to travel hop-
by-hop and nodes are limited in terms of computa-
tional power and battery. These characteristics make
MANET vulnerable to various kind of attacks rang-
ing from passive attacks (eg. eavesdroppingon broad-
casted messages) to active attacks (eg. compromising
nodes).
Identity Based Encryption (BF-IBE) by Boneh
and Franklin (Boneh and Franklin, 2001) has been
a popular choice as a cryptographic primitive in
MANET due to its low infrastructural cost and con-
venience in deriving the authentic public key. One
disadvantage of IBE however, is the forced uncondi-
tional trust towards the Private Key Generator (PKG).
This limits the use of IBE to a closed environment
where key escrow is acceptable.
Thus majority of previous attempts involved the
use of threshold cryptography (Bohio and Miri, 2004;
Luo et al., 2002; Pan et al., 2007; Zhang et al., 2005)
in order to provide secure communication in MANET.
While threshold public key cryptography helps estab-
lishing escrow free secure communication without the
presence of a central authority, it is not a favorable
choice due to the following reasons: (i) n number of
nodes need to be online and reachable at a given time
for key establishment; (ii) incurs a high overhead dur-
ing the decryption.
On the other hand, Al-Riyami and Paterson pro-
posed Certificateless Encryption (CLE) (Al-Riyami
and Paterson, 2003) in an effort to overcome the key
escrow problem of IBE. CLE does this successfully
while remaining non-directory based by incorporat-
ing positive aspects from both IBE (implicit authenti-
cation of a public key via its associated identity) and
conventional PKC (user contributed secret in private
key generation). Yet, their CLE carries over simi-
lar computationalburden including map-to-pointhash
function and pairings involved in both encryption and
decryption due to its close resemblance to BF-IBE.
Another IBE scheme proposedby Sakai and Kasa-
hara (SK-IBE) (Sakai and Kasahara, 2003) in 2003
has not received much attention due to the lack of se-
curity proof which was not available until Chen and
Cheng (Chen and Cheng, 2005) proved its security
under k-Bilinear Diffie-Hellman Inversion (BDHI)
assumption. SK-IBE presents better efficiency by
avoiding map-to-point hash function and reducing the
number of pairing operations required to one.
In 2006, Libert and Quisquater (Libert and
Quisquater, 2006) gave a construction of CLE which
is computationally more efficient than previously pro-
306
Hyun-Jeen Lee P., Narayan S. and Udaya P. (2008).
SECURE COMMUNICATION IN MOBILE AD HOC NETWORK USING EFFICIENT CERTIFICATELESS ENCRYPTION.
In Proceedings of the International Conference on Security and Cryptography, pages 306-311
DOI: 10.5220/0001921703060311
Copyright
c
SciTePress

posed CLE schemes from the above observation.
However, their public key size is too big as it is an ele-
ment in the extension field (typical size of 1024 bits).
Although they suggest the use of two special types of
curves which can reduce the size of public key by a
considerable amount, it adds extra complexity.
While the consequence of these drawbacks may
be subtle in a desktop environment, its effect can
be significant in a resource constrained environment
such as Mobile Ad Hoc Network (MANET). With this
motivation we propose a CLE scheme optimized for
efficient computation, storage and communication.
1.1 Contribution
We propose a CLE scheme which is optimized
for efficiency, targeting the resource constrained
environment such as MANET. Specifically, our
scheme is more efficient than the scheme by Lib-
ert and Quisquater by two field exponentiations in
computation-wise and up to 40% in public key size-
wise when MNT curves (Miyaji et al., 2001) are used.
Our scheme facilitates secure communication in
MANET with efficient key establishment which can
readily be initiated due to the virtue of key escrow
freeness. Further, the use of the transparent policy
encoder eases authentication process.
Our scheme is secure against adaptive chosen-
ciphertext-attack in the random oracle model assum-
ing k-BDHI assumption holds. We show the reduc-
tion by closely modeling the adversary model in (Al-
Riyami and Paterson, 2003) and applying the result
in (Chen and Cheng, 2005). We also show that our
scheme is resistant to the recent attack by Au et al.
(Au et al., 2007). Due to space limitation, we omit
the security proof (available in the full version of the
paper).
The rest of the paper is organized as follows. Sec-
tion 2 gives the necessary background for the Basic
and Full Scheme presented in Section 3. In Section 4,
we show key establishment followed by performance
analysis in Section 5. Finally we show the conclusion
and future works in Section 6.
2 PRELIMINARIES
In this section, we describe the necessary mathemati-
cal background required.
2.1 Bilinear Groups
G
1
,G
2
and G
T
are cyclic groups of prime order q. P
1
is a generator of G
1
and P
2
is a generator of G
2
. ψ is
an isomorphism from G
2
to G
1
with ψ(P
2
) = P
1
. ˆe is
a bilinear map ˆe : G
1
× G
2
→ G
T
.
Necessary requirements for the bilinear map ˆe are:
Bilinear. For all P ∈ G
1
and all Q ∈ G
2
and all a, b ∈
Z we have ˆe(aP, bQ) = ˆe(P,Q)
ab
.
Non-degenerate: ˆe(P
1
,P
2
) 6= 1.
Computable: There is an efficient algorithm to com-
pute ˆe(P,Q) for all P and Q.
2.2 Assumptions
Assumption 1 (Bilinear Diffie-Hellman (BDH).).
Given (P
2
,aP
2
,bP
2
,cP
2
) where P
2
∈ G
2
and a,b,c ∈
R
Z
∗
q
, computing ˆe(P
1
,P
2
)
abc
is hard.
Assumption 2 (Bilinear Diffie-Hellman Inversion
(k-BDHI).). For an integer k, and x ∈ Z
∗
q
,P
1
= ψ(P
2
),
ˆe : G
1
× G
2
→ G
T
, given (P
1
,P
2
,xP
2
,x
2
P
2
,...,x
k
P
2
),
computing ˆe(P
1
,P
2
)
1/x
is hard.
2.3 Security Model
Let K be a security parameter, and M and C denote
the plaintext and ciphertext spaces respectively. A
CLE system consists of the following polynomially
bounded algorithms.
Setup. Given security parameter K , returns a master
public key M
pk
and a master secret key M
sk
.
Partial-Private-Key-Extract: Given M
pk
,M
sk
and
ID
A
∈ {0,1}
∗
, which is an identifier string for en-
tity A, returns the corresponding partial private
key ∂d
A
.
Extract. Given M
pk
,∂d
A
and the user chosen secret
k, returns the corresponding full private key d
A
.
Set-Public-Key : Given M
pk
and the user chosen se-
cret k, returns the randomly generated public key
K
pub
.
Encrypt. Given M
pk
,ID
A
,K
pub
and a message m ∈
M, returns the ciphertextC ∈ C.
Decrypt. Given M
pk
,ID
A
,d
A
and C, returns the
plaintext m or a failure symbol ⊥.
Next, we define the security of our scheme using
the following game model.
Setup. The challenger C takes a security parameter
K and runs the Setup algorithm. C gives M
pk
to
the adversary A and keeps M
sk
secret to himself.
Phase 1. A issues any of the following queries.
1. Partial private key extraction on ID
i
: C runs the
Partial-Private-Key-Extract algorithm to gener-
ate ∂d
i
.
SECURE COMMUNICATION IN MOBILE AD HOC NETWORK USING EFFICIENT CERTIFICATELESS
ENCRYPTION
307

2. Extraction query on ID
i
: C runs the Extract al-
gorithm to generate d
i
and passes it to A .
3. Decryption query on (ID
i
,C
i
): C decrypts by
searching for the corresponding d
i
in H
list
1
.
4. Request public key on (ID
i
): C returns the pub-
lic key generated by running Set-Public-Key.
5. Replace public key for (ID
i
): A is free to make
any valid change to the given public key and re-
quest to replace its given public key to the mod-
ified public key.
Challenge. Once A decides that Phase 1 is over, A
outputs two equal length plaintexts m
0
,m
1
∈ M,
and an identity ID
ch
on which A wishes to be
challenged. The only constraint is that A must
not have queried the extraction oracle on ID
ch
in
Phase 1. C picks a bit b ∈
R
{0,1} and sets C
ch
=
Encrypt(M
pk
,ID
ch
,m
b
) ∈ C. C sends C
ch
as the
challenge to A .
Phase 2. A issues more queries as in Phase 1 butwith
two restrictions: (1) Extraction queries cannot be
issued on ID
ch
; (2) Decryption queries cannot be
issued on (ID
ch
,C
ch
).
Guess. Finally, A outputs a guess b
′
∈ {0,1} and
wins the game if b
′
= b.
Next we define two different types of adversaries
Type 1 and 2.
Type 1. Type I adversary A
1
does not have access to
the master secret s. However, is given the partial
private key component k and is allowed to request
for the public key replacement. Restrictions are:
1. A
1
cannot extract the private key for ID
ch
at any
time.
2. A
1
request the private key for any identity if the
corresponding public key has been replaced.
3. A
1
cannot both replace the public key for the
challenge identity ID
ch
before the challenge
phase and extract the partial private key for
ID
ch
in some phase.
4. In Phase 2, A
1
cannot make a decryption query
on the challenge ciphertext C
ch
for the combi-
nation of identity ID
ch
and the public key P
ch
that was used to encrypt m
b
.
5. When requesting for a public key replacement,
δ applied to the public key needs to be informed
to the simulator.
Type 2. Type II adversary A
2
does have access to the
master secret s. However, A
2
is not allowed to
replace public keys.
1. A
2
cannot replace public keys.
2. A
2
cannot extract the private key for ID
ch
.
3. In Phase 2, A
2
cannot make a decryption query
on the challenge ciphertext C
ch
for the combi-
nation of identity ID
ch
and public key P
ch
that
was used to encrypt m
b
.
Definition 2.1. A CLE scheme is secure against
adaptive-chosen-plaintext-attack (IND-CPA) if no
polynomially bounded adversary A (Type 1 or Type
2) has a non-negligible advantage against the chal-
lenger in the described game model (excluding the
decryption oracle).
Definition 2.2. A CLE scheme is secure against
adaptive-chosen-ciphertext-attack (IND-CCA) if no
polynomially bounded adversary A (Type 1 or Type
2) has a non-negligible advantage against the chal-
lenger in the described game model.
3 EFFICIENT CLE SCHEMES
3.1 Basic Scheme
Setup. Given a security parameter K ∈ Z
+
, generate
the following:
1. Three groups G
1
,G
2
and G
T
of prime order q
and a bilinear map ˆe : G
1
× G
2
→ G
T
.
2. Random generators P
1
∈ G
1
, P
2
∈ G
2
and a ran-
dom master secret s ∈ Z
∗
q
then set P
pub
= sP
2
.
3. Cryptographic hash functions H
1
: {0,1}
∗
→
Z
∗
q
, H
2
: G
T
→ { 0,1}
n
for some integer n > 0.
Finally publish M
pk
=
hq,G
1
,G
2
, ˆe, ψ, P
1
,P
2
,P
pub
, H
1
,H
2
,ni as the
master public key and M
sk
= s as the master
private key. The plaintext space is M = {0, 1}
n
and the ciphertext space is C = G
1
× {0,1}
n
.
Partial-Private-Key-Extract. Given a string identi-
fier for an entity A ID
A
∈ {0,1}
n
,
¯
k,M
pk
and M
sk
,
do the following:
1. Compute h
A
= H
1
(ID
A
||
¯
k).
2. Compute the partial private key as ∂d
A
= (h
A
+
s)
−1
P
2
.
Extract. Given M
pk
, a partial private key ∂d
A
and
user’s chosen secret k, do the following:
1. Compute k
−1
.
2. Set the private key as d
A
= k
−1
∂d
A
.
Set-Public-Key. Given M
pk
and the user chosen se-
cret k, generate the public key K
pub
as follows.
1. Compute kP
1
and kP
pub
.
2. Set the public key as K
pub
= (kP
1
,kP
pub
,
¯
k).
Encrypt. A plaintext message m ∈ M,ID
A
,K
pub
and
M
pk
results in a ciphertext C as follows:
SECRYPT 2008 - International Conference on Security and Cryptography
308

1. Check that ˆe(kP
1
,P
pub
) = ˆe(P
1
,kP
pub
). If not,
output ⊥ and abort.
2. Pick r ∈
R
Z
∗
q
.
3. Compute h
A
and g
r
. Note that g = ˆe(P
1
,P
2
)
needs only be computed once.
4. Then encrypt as C = (U,V) = (r(h
A
kP
1
+
kψ(P
pub
)),M ⊕ H
2
(g
r
)).
Decrypt. Given C,d
A
and M
pk
:
1. Compute g
′
= ˆe(U,d
A
) and σ
′
= V ⊕ H
2
(g
′
).
2. Compute m
′
= V ⊕ H
2
(g
′
) and return m
′
as the
plaintext.
Above is true since,
g
′
= ˆe(U, d
A
) = ˆe(r(h
A
kP
1
+ kψ(P
pub
)),k
−1
(h
A
+
s)
−1
P
2
) = ˆe(P
1
,P
2
)
r
= g
r
3.2 Full Scheme
This scheme is constructed by applying FO trans-
formation (Fujisaki and Okamoto, 1999) to Basic
Scheme.
Setup. Given a security parameter K ∈ Z
+
, generate
the following:
1. Followsthe Steps 1-3 of Basic Scheme’sSetup.
2. Two additional cryptographic hash functions
H
3
: { 0,1}
n
× {0,1}
n
→ Z
∗
q
and H
4
: { 0,1}
n
→
{0,1}
n
for some integer n > 0.
Finally publish M
pk
=
hq,G
1
,G
2
, ˆe, ψ, P
1
,P
2
,P
pub
, H
1
,H
2
,H
3
,H
4
,ni
as the master public key and M
sk
= s as the
master private key. The plaintext space is the
same as in Basic Scheme. The ciphertext space is
C = G
1
× {0,1}
2n
.
Partial-Private-Key-Extract. Follows Basic
Scheme’s Extract.
Extract. Follows Basic Scheme’s Extract.
Set-Public-Key. Follows Basic Scheme’s Set-
Public-Key.
Encrypt. A plaintext message m ∈ M,ID
A
,K
pub
and
M
pk
results in a ciphertext C as follows:
1. Check that ˆe(kP
1
,P
pub
) = ˆe(P
1
,kP
pub
). If not,
output ⊥ and abort.
2. Pick a σ ∈
R
{0,1}
n
and compute r = H
3
(σ,m).
3. Compute h
A
and g
r
as in Basic Scheme’s En-
crypt.
4. Then encrypt as C = (U,V,W) = (r(h
A
kP
1
+
kψ(P
pub
)),σ⊕ H
2
(g
r
),m⊕ H
4
(σ).
Decrypt. Given C,d
A
and M
pk
:
1. Compute g
′
= ˆe(U,d
A
) and σ
′
= V ⊕ H
2
(g
′
).
2. Compute m
′
= W ⊕H
4
(σ
′
) and r
′
= H
3
(σ
′
,m
′
).
3. If U 6= r
′
(h
A
kP
1
+ kψ(P
pub
)), output ⊥, else re-
turn m
′
as the plaintext.
4 KEY ESTABLISHMENT
The characteristics of MANET demand an efficient,
escrow-free and self-configuring encryption scheme
in order to establish secure communication between
the participating nodes. Many threshold-based cryp-
tographic approaches proposed so far are not adequate
for MANET for at least two reasons: (i) n number of
nodes need to be online and reachable at a given time
for key establishment; (ii) incurs a high overhead dur-
ing the decryption.
Resurrecting Duckling is a novel approach by Sta-
jano and Anderson (Stajano and Anderson, 2000) for
key establishment in MANET. The idea is simple, a
node A will recognize another node B as its master
if B sends A a secret key before any other node does
(known as imprinting). This allows the network to
readily begin secure communication instead of having
to wait until a certain number of nodes become avail-
able in the network. However, such a master-slave
relationship between nodes are not suitable where ev-
ery node is autonomous and compromising a mas-
ter node can significantly endanger the security of its
slave nodes.
We propose the use of our scheme combined with
Resurrecting Duckling idea to leverage the vulnerable
master-slave relationship to facilitator-benefitor rela-
tionship. Due to the escrow free property of CLE, a
node A acting as a PKG does not have the full control
over the other node B which obtains its partial private
key from A. Instead, A merely facilitates the secure
communication (by setting up the public parameters
and generating the partial private key) and B benefits
from A’s service. By using the blinding technique, the
secure channel (such as SSL) between A and B need
not be established when transferring the partial pri-
vate key. We now describe how the key establishment
can readily start in the absence of any online central
authority (N is the number of existing nodes).
N = 2: Node A and B come in contact of each other.
• A and B starts negotiating on the public param-
eter selection for their secure communication.
Note that each node will choose its master se-
cret independently as s
A
and s
B
.
• Once the negotiation is done, A chooses a blind-
ing factor x ∈
R
Z
∗
q
and sends (ID
A
,
¯
k,xP
2
) to B.
• Upon successful authentication of A, B per-
forms Partial-Private-Key-Extract and com-
SECURE COMMUNICATION IN MOBILE AD HOC NETWORK USING EFFICIENT CERTIFICATELESS
ENCRYPTION
309

putes the blinded partial private key ∂d
A
=
(h
A
+ s
B
)
−1
xP
2
where h
A
= H
1
(ID
A
||
¯
k), then
sends the key to A.
• A obtains its unblinded partial private key =
x
−1
(h
A
+s
B
)
−1
xP
2
= (h
A
+s
B
)
−1
P
2
as required.
• B follows the same procedure to obtain its par-
tial private key from A.
Notice that even if an adversary eavesdrops on
the communication and catches (h
A
+ s
B
)
−1
xP
2
,
he cannot use this to impersonate as A since x is
unknown to him nor can he become a valid mem-
ber of the network.
N > 2: Another node C joins the network.
• C broadcasts the request that it wishes to join
the network.
• Nodes willing to provide PKG service will re-
ply to the request.
• C randomly selects one among the replied
nodes.
• The rest follows the same procedure as in N =
2 case.
4.1
¯
k as the Transparent Policy Encoder
In this subsection, we demonstrate how to use
¯
k as
the policy encoder and show how its transparency can
ease the task of authentication. Recall that in our Ba-
sic and Full Scheme, we have used
¯
k as a simple ran-
dom element in Z
∗
q
. Instead, we can use
¯
k as the policy
encoder (eg. validity period, location info, etc) which
can be determined during the negotiation phase. For
example, one may define
¯
k = sP
2
⊕ policy.
Then, nodes C and D each of which have been is-
sued its partial private key from different PKG nodes
A and B respectively, can easily authenticate each
other in the following way.
• C sends its public key (k
C
P
1
,k
C
P
pub
,
¯
k
C
) and s
A
P
2
to D
• D obtains policy =
¯
k
C
⊕ s
A
P
2
and checks if the
policy is valid.
• D follows the same procedure to be authenticated
by C.
• If both C and D are satisfied with each other’s pol-
icy, they can start secure communication.
5 PERFORMANCE
In the Table 1 and 2, we compare the efficiency of dif-
ferent CLE schemes with respect to the number of op-
erations required and their public key sizes. Although
encryption schemes presented in (Al-Riyami and Pa-
terson, 2003; Libert and Quisquater, 2006) imply the
use of supersingular curves, for a fair efficiency com-
parison, we assume MNT curves are used. Also it
is assumed that point compression techniques are ap-
plied. (+160) in the Table 2 denotes the additional
bits needed when
¯
k is used separately as the policy en-
coder. Note that in Table 1, we have not included the
computation required for the public key check since
this only needs to be done once for each new user.
(Libert and Quisquater, 2006) outperforms (Al-
Riyami and Paterson, 2003) by 1 pairing in encryp-
tion. Since pairing is the cost-dominant operation,
this gain outweighs the performance loss due to some
other extra computations. Our scheme makes further
performance improvement by reducing one element
exponentiation in each encryption and decryption.
While we are aware of the recently proposed CLE
without pairing by Sun et al. (Y. Sun and Baek, 2007),
it is not included in our comparison. This is because
although this scheme requires less computation, its
public key size is bigger hence making a straightfor-
ward comparison difficult. To conduct a comparison,
the difference between significance of reducing com-
putational cost and reducing communication cost in
MANET needs to be studied and is beyond the scope
of this paper.
6 CONCLUSIONS AND FUTURE
WORKS
In this paper, we have presented a provably secure
efficient certificateless encryption scheme. We have
shown that our scheme is an ideal choice for key es-
tablishment in MANET when coupled with Resur-
recting Duckling idea. Further, we have shown how
the use of transparent policyencodereases the authen-
tication task. The security of our scheme has been
proven against adaptive-chosen-ciphertext-attack in
the random oracle model assuming k-BDHI holds. To
further enhance our proposal we suggest PGP’s web
of trust concept (Abdul-Rahman, 1997) to manage the
trust level of each node in the network for determining
the potential candidate to take the PKG’s role. This
will aid in avoiding or detecting dishonest node be-
haviours (eg. node impersonation).
ACKNOWLEDGEMENTS
We would like to thank the anonymous reviewers for
their helpful comments.
SECRYPT 2008 - International Conference on Security and Cryptography
310
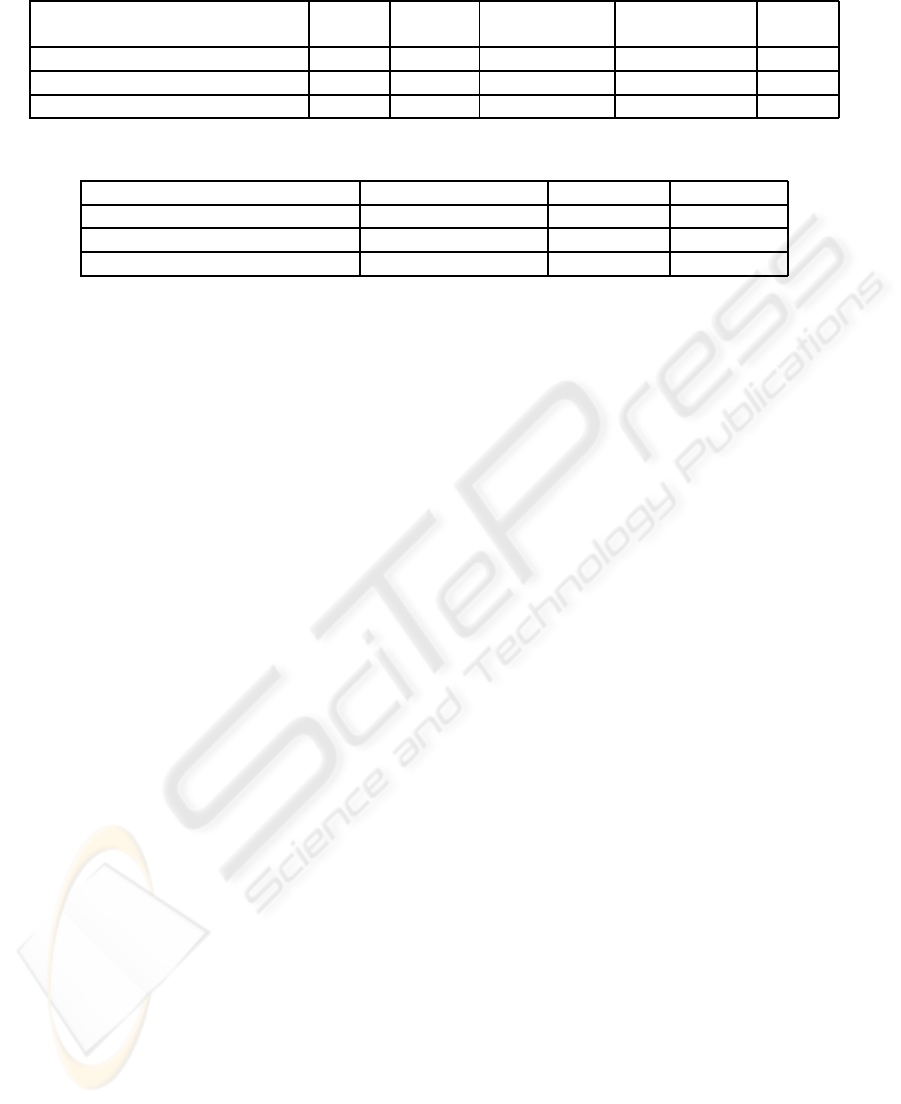
Table 1: Performance Comparison (No. required in encryption/decryption).
Map to Point Scalar Element Pairing
point addition multiplication exponentiation
(Al-Riyami and Paterson, 2003) 1/0 0/0 1/1 1/0 1/1
(Libert and Quisquater, 2006) 0/0 1/1 2/2 2/1 0/1
Our Scheme 0/0 1/1 2/2 1/0 0/1
Table 2: Public Key Size Comparison (in bits).
Supersingular Curve MNT Curve BN Curve
(Al-Riyami and Paterson, 2003) 320 320 320
(Libert and Quisquater, 2006) 1024 512 320
Our Scheme 320 (+ 160) 320 (+ 160) 320 (+ 160)
REFERENCES
Abdul-Rahman, A. (1997). The pgp
trust model. edi- forum, april 1997.
http://www.cs.ucl.ac.uk/staff/F.AbdulRahman/docs/.
Al-Riyami, S. and Paterson, K. (2003). Certificateless pub-
lic key cryptography. In Advances in Cryptology -
ASIACRYPT 2003, pages 452–473. Springer-Verlag.
Au, M. H., Mu, Y., Chen, J., Wong, D. S., Liu, J. K., and
Yang, G. (2007). Malicious kgc attacks in certificate-
less cryptography. In ASIACCS ’07: Proceedings of
the 2nd ACM symposium on Information, computer
and communications security, pages 302–311. ACM.
Bohio, M. and Miri, A. (2004). Efficient identity-based se-
curity schemes for ad hoc network routing protocols.
Journal of Ad Hoc Networks.
Boneh, D. and Franklin, M. K. (2001). Identity-based en-
cryption from the weil pairing. In CRYPTO ’01: Pro-
ceedings of the 21st Annual International Cryptology
Conference on Advances in Cryptology, pages 213–
229. Springer-Verlag.
Chen, L. and Cheng, Z. (2005). Security proof of the
sakai-kasahara’s identity-based encryption scheme. In
Cryptography and Coding, pages 442–459. Springer-
Verlag.
Fujisaki, E. and Okamoto, T. (1999). Secure integration
of asymmetric and symmetric encryption schemes. In
CRYPTO ’99: Proceedings of the 19th Annual Inter-
national Cryptology Conference on Advances in Cryp-
tology, pages 537–554. Springer-Verlag.
Libert, B. and Quisquater, J. J. (2006). On constructing
certificateless cryptosystems from identity based en-
cryption. In Public Key Cryptography - PKC 2006,
volume 3958 of Lecture Notes in Computer Science,
pages 474–490. Springer-Verlag.
Luo, H., Zerfos, P., Kong, J., Lu, S., and Zhang, L. (2002).
Self-securing ad hoc wireless networks. In ISCC ’02:
Proceedings of the Seventh International Symposium
on Computers and Communications (ISCC’02), page
567. IEEE Computer Society.
Miyaji, A., Nakabayashi, M., and Takano, S. (2001).
New explicit conditions of elliptic curve traces for fr-
reduction. In IEICE Transactions on Fundamentals,
volume E84-A, pages 1234–1243.
Pan, J., Cai, L., Shen, X. S., and Mark, J. W. (2007).
Identity-based secure collaboration in wireless ad hoc
networks. Comput. Networks, 51(3):853–865.
Sakai, R. and Kasahara, M. (2003). Id based cryp-
tosystems with pairing on elliptic curve. In 2003
Symposium on Cryptography and Information Se-
curity – SCIS’2003, Hamamatsu, Japan, 2003.
http://eprint.iacr.org/2003/054.
Stajano, F. and Anderson, R. J. (2000). The resurrect-
ing duckling: Security issues for ad-hoc wireless net-
works. In Proceedings of the 7th International Work-
shop on Security Protocols, pages 172–194. Springer-
Verlag.
Y. Sun, F. Z. and Baek, J. (2007). Strongly secure
certificateless public key encryption without pairing.
In Cryptology and Network Security, volume 4856,
pages 194–208. Springer-Verlag.
Zhang, Y., Liu, W., Lou, W., Fang, Y., and Kwon, Y. (2005).
Ac-pki: anonymous and certificateless public-key in-
frastructure for mobile ad hoc networks. In ICC 2005:
2005 IEEE International Conference on Communica-
tions, pages 3515–3519. IEEE.
SECURE COMMUNICATION IN MOBILE AD HOC NETWORK USING EFFICIENT CERTIFICATELESS
ENCRYPTION
311
