
A STUDY OF THE EFFECTIVENESS OF “WAKE UP ON LAN”
AS A MEANS OF POWER MANAGEMENT
Colin Pattinson and Linton Robinson
Innovation North Faculty of Information and Technology, Leeds Metropolitan University, Leeds U.K.
Keywords: Power management, wake on LAN, Energy savings in corporate IT.
Abstract: The growing awareness of the fragile nature of our environment, and of the damage that humankind is
causing to that environment, makes it necessary to review the environmental impact of all aspects of human
activity. One such area is the operation of corporate information technology (IT) systems. The growth in the
number and complexity of such systems over recent decades has led to a consequent increase in their power
requirements, to the point where for organisations of any size, “corporate IT” will be a major contributor to
the organisation’s overall energy consumption. A drive for overall reductions in consumption will, in the
words of the chair of the newly formed UK Environmental IT Leadership Team, mean “the IT department
becomes the focus of carbon reduction policies”. It is therefore timely to consider the present situation in
respect of power consumption within corporate IT systems, and to explore the potential avenues for
reducing that consumption. In this paper, we will briefly overview the area of power usage in IT, before
reporting on the outcomes of a specific project in which we explored the operation of the “wake on LAN”
method in a real situation.
1 INTRODUCTION
The rapid growth in computer use is placing a strain
on the UK’s ageing electrical infrastructure. The
growth of networked systems within organisations is
a major factor, with an increase in the number of
servers in a typical organisation from around 4 in the
late 1990s to 10 to 15 times that number (Watson,
2006). In October 2006, there were 2,507,278
registered companies in the UK (Companies House,
2006). While we do not know exactly how many of
these companies operated with the 60 servers in
Watson’s analysis or even as many computers, it is
not unreasonable to suggest that a good proportion
will have PCs, Servers and other network devices.
Data for energy consumption of IT systems vary
according to the exact definition of what is included,
and there is variation in reporting methods.
Kawamoto et. al. (2000) found “devices connected
to the Internet” for “commercial use” were
responsible for 2% of the total U.S. power
consumption. In Germany over 7% of domestic
energy consumption is “computer-related”
(Loerincik 2006).
One attempt to save energy has been to limit the
power taken by devices when not in use by placing
them in a “dormant” state, like the “stand by” mode
of many consumer electronics devices. Note: in a
further parallel with consumer electronics,
“dormant” is not “off”, and some power is still
required. The generic term for this activity is power
management (PM). PM can bring about energy
savings “…of the 74 TWh/yr of electricity
(approximately $6 billion per year) … consumed by
the Internet in the USA alone … 32% could be
saved with effective PM on desktops” (Christensen
et. al. 2007), and the equivalent of 250M litres of
gasoline per day could be saved if 1M PC users
employed PM (Long 2006).
Many current energy reduction activities
(including the one reported here) aim at the desktop
(user PC) element of IT systems, reasonably enough
in view of the numbers of such devices. However,
server and network device (switches, hubs and
routers) must not be overlooked. Allowing such
devices to enter a dormant state is problematic, as
typical network performance and security
monitoring techniques expect networked devices to
respond to a regular sequence of polling packets;
indeed some network management tools generate an
alarm if a device does not react to a probe request;
therefore there is a contradiction. Furthermore,
73
Pattinson C. and Robinson L. (2008).
A STUDY OF THE EFFECTIVENESS OF “WAKE UP ON LAN” AS A MEANS OF POWER MANAGEMENT.
In Proceedings of the International Conference on e-Business, pages 73-76
DOI: 10.5220/0001904300730076
Copyright
c
SciTePress
“[t]he immense increase in networking … is an
important factor [limiting the use of power saving]
because network activity can keep computers from
entering low-power modes” Webber et. al. (2001).
2 APPROACHES TO PM
In the opening parts of this paper, we argued that
there is a contradiction between the conventional
way networks operate, PM and cost savings. Let us
therefore take an overview of the different potential
strategies in this regard. We start by giving a brief
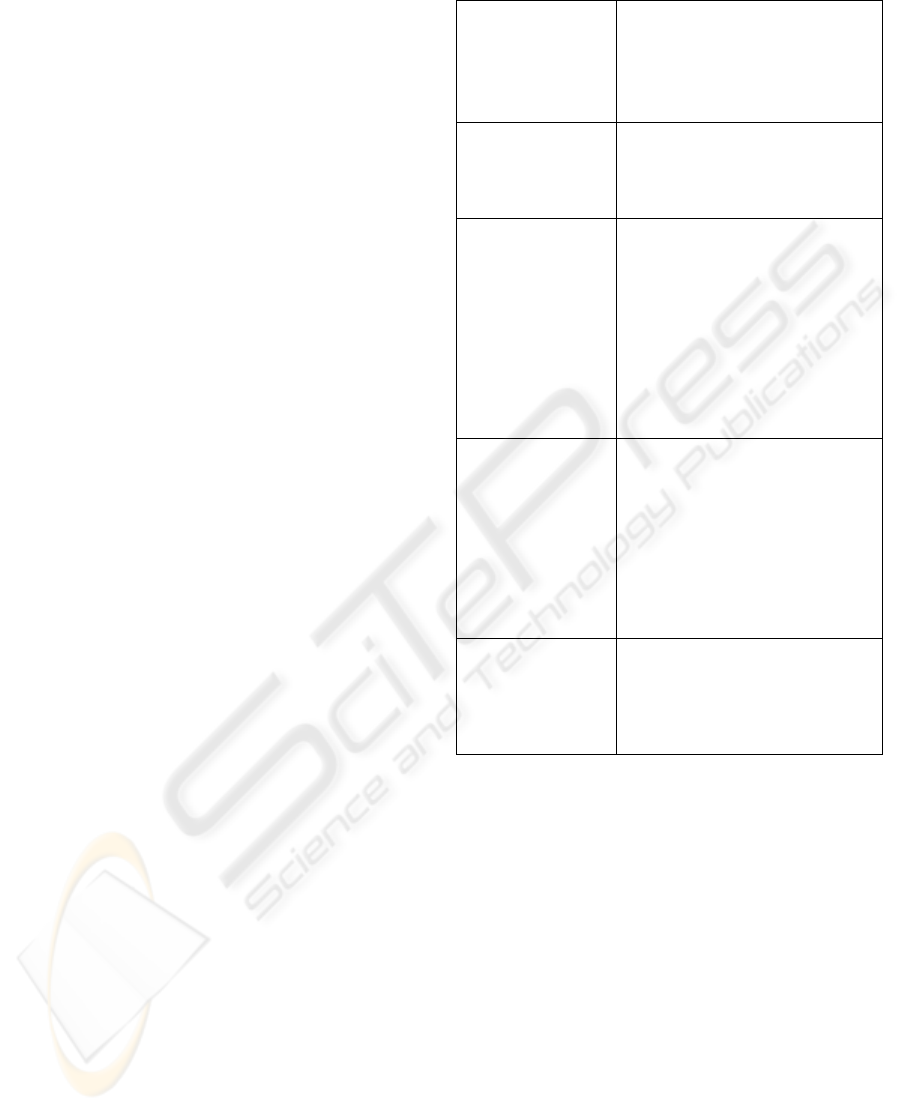
explanation of each of these techniques (Table 1).
To some extent, this table is rather simplistic;
e.g. overlaps between some techniques could
combine to effectively provide a PM solution. In
this study, WOL has been chosen primarily because
of its ease of use and simplicity in implementation.
Also, a previous research project successfully used
WOL in both wired and wireless scenarios, so we
have confidence in the underlying method.
3 QUESTIONS TO ADDRESS
The objective of this research was to determine how
WOL operates; hence we begin by exploring how
WOL will be delivered in a typical networked
scenario. Crucial to the deployment of WOL across
a network are questions of the nature and operation
of the communication process; for instance, are
WOL packets broadcast, unicast or multicast? What
are the issues with regard to a ‘connectionless or
connection-oriented approach?’ and finally, what are
the issues in terms of efficiency and security.
4 THE MAGIC PACKET (MP)
‘Magic Packet’ (MP) and ‘Wake up On LAN’
(WOL), are the same thing. The Magic Packet is
broadcast via port 7 or 9 which can be sent using a
variety of connectionless protocols, with UDP the
most common. (CapaInstaller, 2006). The Magic
Packet structure is similar to an Ethernet packet, but
the destination Medium Access Control (MAC)
address is repeated 16 times within the packet.
Table 1: Alternative PM approaches.
Dynamic Power
Management
(DPM)
Lu et. al. (2000)
Algorithms designed to shut
down a device only when an idle
period is of sufficient length to
justify performance degradation
and state-transition energy.
EZ Group Policy
Objects (GPO)
A free tool which allows network
administrators to centrally
control Power Management
settings using GPOs.
SMS Wakeup
(Hobbs 2006),
SMS 2003 currently lacks the
means for waking up machines, a
plug-in from 1E, Inc., called
SMS Wakeup, provides this
functionality. SMS Wakeup
integrates with SMS and uses
data from the SMS asset
collection to obtain MAC
addresses for each client
computer.
Using a low-power
channel
Shih et. al. (2002),
By adding a second low-power
channel, it is possible to shut the
system off and reduce idle
power. Out-of-band control
information can be sent
simultaneously, to maintain
connectivity and wakeup the
universal communicator (UCoM)
device when necessary.
Wake on LAN
(WOL)
(Korn et. al.,
2006).
Wake on LAN is a Layer 2-based
means for waking up machines
from sleep states such as system
standby, hibernate and shutdown
– and for remote access to them.
WOL encapsulates such Magic Packets inside a
broadcast UDP packet. This gives benefits over raw
Ethernet frames including Operating System (OS)
interoperability.
The complete UDP packet, sent over an Ethernet
interface, looks like this: (Spurgeon 2006)
[Ethernet header][IP header]
[UDP header][Magic sequence][CRCS]
5 TO BROADCAST, UNICAST OR
MULTICAST?
Unicast packets are sent from host to host, a one to
one relationship. Broadcast packets are one to many,
one host communicating with all other hosts.
Multicast is a restricted one to many relationship; a
ICE-B 2008 - International Conference on e-Business
74
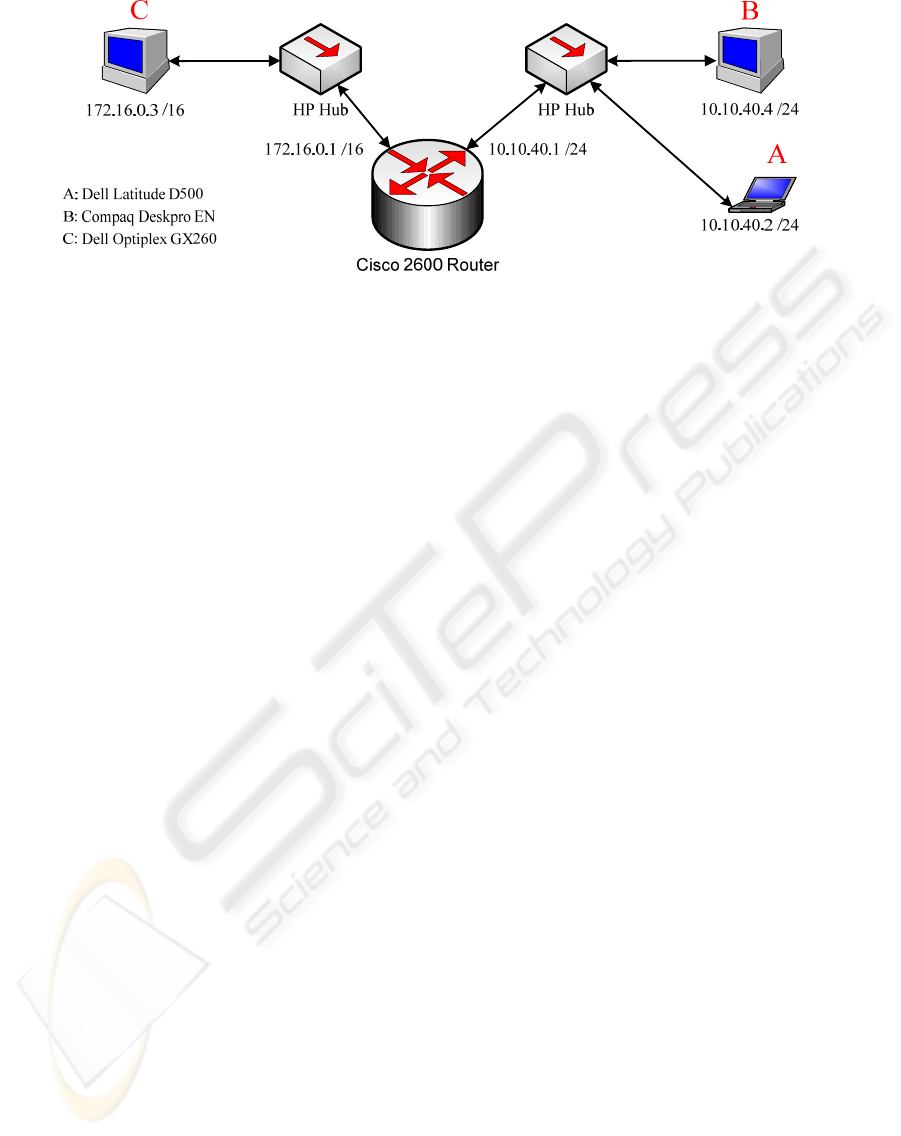
Figure 1: Routed Network – MP Implementation.
single device can communicate with a specific set of
hosts. Our previous work with the MP showed that
it can be transferred by broadcast, unicast and
multicast, however for the purposes of this paper, we
consider a ‘broadcast’ approach, minimising effort
(just one message needs to be created), while
maximising coverage. By design, most modern
routers will block IP broadcast traffic and restrict it
to the local subnet, but this can be changed by the
network administrator.
6 WOL QUESTIONS
6.1 Efficiency
We conducted a series of tests to send the MP over a
wired network with unicast and multicast
instructions to wake machines. In these tests, the
packet successfully woke up and shut down
workstation(s). When this was carried out using a
wireless link, we found that in 2 cases, the
instruction to sleep succeeded, but the instruction to
wake failed if the target machine was in another
subnet. We believe that a correctly configured
wireless AP in that foreign subnet will rectify this
and conclude from these results that the MP is able
to produce satisfactory results and to do so reliably.
6.2 Reliability
It is well known that UDP is not reliable (Bhatti
2007); therefore the immediate question might be
why use it? Why not invoke a connection oriented
protocol with reliable delivery? Once a command is
issued to sleep, there is currently no feedback
mechanism to indicate that command was received
and obeyed. Instead, the network administrator may
need to utilise other tools creating extra work and
traffic, reducing the potential benefits of PM.
Therefore one challenge for developers is to bridge
the gap between the command and the response.
6.3 Security
There are a number of security issues within WOL
and its implementation (Robinson, 2007). For
instance, applying the ‘layered approach’ of most
network designs as in the following model:
((PM + current security) + (LAN security) +
(WAN security) + internet security))
= Total Vulnerabilities
means that vulnerabilities are compounded. We also
found that “more advanced systems” do not
necessarily mean “more advanced PM” a further
indication of the need for research and development
into PM. Min and Chandrasakan (2003) argue that
computational algorithms and low power digital
hardware trade energy for quality, because digital
processing occurs more slowly and uses less energy
when circuit voltage is reduced.
7 BROADCASTING THE MP
OVER ROUTED NETWORK
In section 5, we identified different ways of sending
the MP. Most networks will be routed in some way.
So we first consider if we can broadcast the MP.
Figure 1 shows a routed network with two broadcast
domains (10.10.40.0 /24 and 172.16.0.0 /16),
randomly selected and intentionally kept distant
from each other, (Class A and Class B respectively)
for ease in configuring the router.
It was possible to send the MP from A to B and
C, to shutdown and wake-up. We already knew that
A STUDY OF THE EFFECTIVENESS OF “WAKE UP ON LAN” AS A MEANS OF POWER MANAGEMENT
75

A to B was possible, from results obtained in the
previous test; however, here we successfully showed
that the MP does route to another domain. Though a
single router is used, in a network comprising of
many routers, the MP should also be able to achieve
the ends of Power Management, provided that
routers and firewalls are configured to allow
broadcast packets to travel between subnets (Korn
et. al., 2006). (The tool used in these experiments is
Prof Shutdown 3.2 evaluation version
(profshutdown, 2006)).
8 CONCLUSIONS
This paper shows that PM can be supported by MP
without detriment to network performance. Our own
research indicates that the adoption of PM take-up is
at best ad-hoc, sparse and often a small project after
business critical objectives have been realised. We
believe this to be counterproductive, as buy-in by all
stakeholders will itself contribute to the bottom line
of businesses and our world. Because the MP piggy-
backs Ethernet, we further believe that the case for
its deployment and the potential return on
investment (ROI) is significant.
REFERENCES
CapaInstaller (2006) www.capainstaller.com/index.asp
?page=157&page2=212&page3=269
Christensen, K., George, A.D. Nordman, B. (2007) The
Energy Efficient Internet Project. University of South
Florida. www.csee.usf.edu/~christen/energy/main.html
Companies House (2006) Verbal conversation
Hobbs C. (2006) Does SMS 2003 Support Wake-on-LAN?
http://www.faqshop.com/sms2003/sms2k3swd.htm
Profshutdown (2006) www.profshutdown.com/
(Accessed: December 2006)
Kawamoto, K., Koomey, J. G., Nordman, B., Brown, R.
E., Piette, M.A. Meier, A.K. (2000) Electricity Used
by Office Equipment and Network Equipment in the
U.S. Lawrence Berkeley National Lab document
LBNL-44917 August 2000
Korn D., Huang R., Bolioli T., Walker M. (2006)
Computer Power Management for Enterprises - A
Practical Guide. Proceedings of the 2006 IEEE
International Symposium on Electronics and the
Environment, May 2006 .pp. 161- 166
Loerincik, Y (2006) Environmental impacts and benefits
of information and communication technology
infrastructure and services, using process and input-
output life cycle assessment. PhD Thesis Ecole
Polytechnique Federale de Lausanne. September 2006.
Long C. (2006) Energy cost of PCs on standby. British
Broadcasting Corporation (BBC). news.bbc.co.uk/
go/pr/fr/-/2/hi/programmes/click_online/4929594.stm
Lu Yung-Hsiang, Chung Eui-Young, Simuni’c Tajana,
Benini Luca (2000) Quantitative Comparison of
Power Management Algorithms. Proceedings of the
conference on Design, Automation and Test in
Europe, March 2000 pp. 20-26.
Min R. Chandrakasan A (2003), Top Five Myths about the
Energy Consumption of Wireless Communication
Mobile Computing and Communications Review Vol.
7 No. 1 pp. 65 - 67 January 2003
Shih E., Bahl, P., Sinclair, M.J.(2002) Wake on wireless:
An event driven energy saving strategy for battery
operated devices. Proceedings of the Eighth Annual
International Conference on Mobile Computing and
Networking (MOBICOM'02), September 2002.
Robinson L. (2007) An Investigation into Power
Management and Power Savings: Is this achievable?
MSc Mobile and Distributed Computer Networks
Dissertation, Leeds Metropolitan University July
2007.
Rtsecurity (2006) www.rtsecurity.com/kb/tech/
wakeonlan.php (Accessed: 23/11/07)
Spurgeon C. (2006) Wake on LAN. http://gsd.di.
uminho.pt/jpo/software/wakeonlan/mini-howto/wol-
mini-howto-2.html
Watson J. (2006) Power shortage hits IT
www.computing.co.uk/computing/news/2150433/pow
er-shortage-hits
Webber C. A., Roberson J. A., Brown R. E., Payne C. T.,
Nordman B., Koomey J. G., (2001) Field Surveys of
Office Equipment Operating Patterns. Energy Analysis
Program. Lawrence Berkeley National Laboratory.
http://enduse.lbl.gov/info/LBNL-46930.pdf.
ICE-B 2008 - International Conference on e-Business
76
