
Time-controlled Neighborhood-driven Policy-based Network Selection
Algorithm for Message Dissemination in Hybrid Vehicular Networks
Oleg Oleinichenko, Yagmur Sevilmis, Karsten Roscher and Josef Jiru
Fraunhofer Institute for Embedded Systems and Communication Technologies ESK, Munich, Germany
Keywords:
Hybrid Communication, Network Selection, Adaptive Heterogeneous Networking, VANET, LTE, ITS-G5.
Abstract:
In vehicular ad hoc networks (VANETs), successful delivery of GeoUnicast and GeoBroadcast packets de-
pends on scenario-specific aspects like vehicle density, distribution of vehicles on the road and type of the
environment (e.g., urban, rural). These aspects can significantly influence the reliability of the connection
between communication parties making traditional ITS-G5 based ad hoc networks unreliable. The absence of
communication partners in range, long transmission distances, non-line-of-sight (NLOS) conditions are just
a few examples that could hinder ITS-G5 transmissions. In this paper, we propose a Hybrid Policy-based
Network Selection Algorithm that uses LTE to strengthen and complement ITS-G5 under critical conditions
in which successful transmission over the ad hoc network is highly unlikely. The main objective is to use as
less LTE transmissions as possible whilst maintaining high Packet Delivery Ratio (PDR) within defined delay
constraints. The results, which are derived from extensive simulation campaigns, show a clear advantage of
using the hybrid scheme over solely ITS-G5 or LTE.
1 INTRODUCTION
Information timeliness and reliability are key for V2X
message distribution, however catering for different
Intelligent Transport System (ITS) application classes
and their diverse communication requirements is not
possible using a single wireless access technology.
Strengths and shortcomings of the enabling technolo-
gies namely ETSI ITS-G5 and LTE for hybrid net-
works used in the scope of this work, were ana-
lyzed extensively in literature (5G-PPP, 2015) (Aran-
iti et al., 2013). ITS-G5 (ETSI, 2013) which is the
de facto standard for V2X communication in Europe
allows low-latency communication in quickly chang-
ing network topologies, but it has some drawbacks
due to its shared medium characteristics, transmission
range limitations and network fragmentation issues
that could arise when the penetration rate of ITS-G5
equipped vehicles is under a certain threshold (5G-
PPP, 2015). LTE on the other hand provides wide cov-
erage thanks to its high market penetration rates so it
can be used to bridge communication gaps in low den-
sity scenarios or enable communication in challeng-
ing ones e.g., intersections where NLOS conditions
exist however, it has some shortcomings related to
message transmission latency. Necessity of all trans-
mitted messages to pass through the infrastructure,
random access procedure and mode switching from
idle to connected could create considerable delays
(Araniti et al., 2013). Moreover, it can suffer from
packet loss due to fading for fast moving vehicles. As
a result, provisioning of concepts for intelligent radio
access technology selection in a multi-networking en-
vironment by combining the strengths of ad hoc and
infrastructure-based networks becomes necessary in
order to better fulfill application Quality of Service
(QoS) requirements. Therefore for ITS stations capa-
ble of hybrid communication, it is significant to se-
lect the most appropriate technology/technologies for
message dissemination.
In this work, we propose a policy-based network
selection algorithm that aims to determine the opti-
mal communication technology on a per-packet ba-
sis based on identified context indicators and pre-
defined policies. The main design goal and philos-
ophy behind the algorithm is to enable the cooper-
ation of both ad hoc and cellular radio technologies
with the aim of providing application transparent geo-
localized message dissemination over ITS-G5 and
LTE so that improved QoS will be provided to appli-
cations while keeping the LTE footprint low. Limiting
LTE usage is important since in typical V2X scenar-
ios where a large number of small packets are being
exchanged with high frequencies, the excessive us-
Oleinichenko, O., Sevilmis, Y., Roscher, K. and Jiru, J.
Time-controlled Neighborhood-driven Policy-based Network Selection Algorithm for Message Dissemination in Hybrid Vehicular Networks.
DOI: 10.5220/0006705901410155
In Proceedings of the 4th International Conference on Vehicle Technology and Intelligent Transport Systems (VEHITS 2018), pages 141-155
ISBN: 978-989-758-293-6
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
141

age of this technology might become costly and lead
to cellular network congestion (Araniti et al., 2013).
We focus on geographical (position-based) network-
ing since ETSI ITS GeoNetworking is the network
layer protocol standardized for ITS in Europe. Fur-
thermore, addressing of nodes based on their location
(geo-broadcast) is beneficial for many ITS use cases
(ETSI, 2010) e.g., informing the following vehicles
about a sudden braking maneuver.
The algorithm operates on the network layer (cor-
responding to the ISO/OSI layer 3) of the ETSI
ITS protocol stack. Delegating this task to the net-
work layer enables coordinating multiple applica-
tions. Moreover, direct access to the link layer to
retrieve real-time performance indicators of the un-
derlying access networks becomes possible. The al-
gorithm will gather requirement indicators from the
applications, performance metrics from the link layer
and exploit this information combining it with its
view of the network conditions that are directly avail-
able in the network layer. Using such an approach
abstracts applications from the network selection pro-
cess and provide them an always best informed ap-
proach transparently. The downside is that the appli-
cations lose direct control over technology selection
and message dissemination.
The algorithm was evaluated using a high-fidelity
simulation environment comprising of multiple sim-
ulators coupled together. Orchestration of multiple
simulators for realistic evaluation of vehicular com-
munication protocols is a widely used approach (Ku-
mar et al., 2009) (Sommer et al., 2011b). Two car-
dinally different scenarios (i.e., Manhattan grid and
open highway) were used throughout the simulation
campaigns in order to assess the algorithm’s perfor-
mance under different communication environment
conditions from a delay restricted packet delivery per-
spective with an indication on LTE resources usage.
Taking into consideration the results of our work,
main advantages of the proposed policy-based adap-
tive hybrid networking algorithm are:
• Improved QoS to applications
• An increase in path resilience and fault tolerance
with low LTE footprint
• Efficient use of available resources (i.e., both
intra- and inter-technology optimizations are pos-
sible, limitations imposed by a single technology
are reduced)
• Higher performance without requiring any modi-
fications at the application level (i.e. application-
agnostic)
• Ease of implementation and integration into the
ITS environment
• Performance improvements with respect to the
identified Key Performance Indicators (KPIs)
over individual technologies in all scenarios
• Facilitation in the market introduction for cooper-
ative ITS services (intermittent connectivity due
to network fragmentation in the initial deployment
phase of ITS-G5 can be overcome by LTE)
• Possibility of extension with future technologies
and new services
This article is structured as follows: Section 2
summarizes related work regarding hybrid communi-
cation and network selection in the context of vehicu-
lar networks. Section 3 describes the hybrid network
architecture providing some background information
necessary to understand the context in which the pro-
posed algorithm operates. In section 4 we present the
policy-based network selection algorithm in detail in-
cluding the design considerations made, parameters
used for decision-making and its control flow. Section
5 describes the simulation toolchain, selected scenar-
ios and network configuration parameters used in per-
formance evaluation. Section 6 presents the evalua-
tion results. Section 7 summarizes the findings and
gives an outlook.
2 RELATED WORK
Network selection in hybrid communication environ-
ments is a widely researched problem. (Charilas and
Panagopoulous, 2010) provides a methodological ap-
proach to address this problem by decomposing it into
four steps, namely selection of the parameters that
should be considered in the process, collection of the
values for the selected criteria, estimation of impor-
tance of each parameter by weight assignment and de-
termination of the optimal choice by ranking the alter-
natives. Various methods that can be used in each step
are also provided and analyzed in terms of their pros
and cons. (Wang and Kuo, 2013) gives an overview
of mathematical theories applied in the modeling of
the network selection problem. A broad classification
of the set of attributes that might be considered during
the network selection process is given in (Charilas and
Panagopoulous, 2010) (Kumaran and Shaji, 2014). It
is important to stress that most of the research on net-
work selection is based either on direct feedback or
on continuous measurement of QoS parameters as in
the case of multimedia streaming none of which are
applicable to the vehicular networking case.
On the ITS side, one reference architecture of a
standardized component responsible of coordinating
multiple access technologies is the ETSI communi-
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
142

cation interface (CI) management component which
aims to provide application friendly communication
services to a diverse range of applications over multi-
ple media (Bouali and Senouci, 2015). Although the
specification of the component is at a block diagram
level and no specific methods for network selection
are mentioned, the component architecture stresses
the value of collecting and combining different cri-
teria.
In literature, several policy-based network selec-
tion mechanisms were proposed. Policy-based net-
work selection systems are composed of identified
rules and policies that are used in the technology se-
lection process. Optimum communication medium is
selected by evaluating the current network selection
parameters based on the policies stored. In (Brickley
et al., 2007), estimated quality of the wireless chan-
nel derived from achievable throughput and allow-
able load is used to determine the selection between
UMTS and WLAN. In (Meneguette et al., 2012), a
multi-network packet scheduling technique based on
the mapping of ITS application classes to one or more
channels is proposed. If two application classes com-
pete for the same channel, the order of access is deter-
mined by the priorities associated with each applica-
tion class (e.g., safety applications take priority over
infotainment). In (Olivera et al., 2009), all commu-
nication is done by default over the V2V ad hoc net-
work and complementary technologies are only uti-
lized in cases where it is not possible to communicate
via V2V (e.g., no neighbors in the communication
range). Despite providing improved performance, ap-
proaches based on a few criteria/attributes often result
in suboptimal decisions as they do not follow a holis-
tic approach and therefore cannot adapt to dynamic
environments.
More holistic approaches in which the selection
is done by monitoring the current context of the ve-
hicle and capturing context indicators is suggested in
(Bouali and Senouci, 2015) (Gopinath et al., 2016b)
(Gopinath et al., 2016a). These context indicators can
be provided by in-vehicle sensors, the underlying ac-
cess layer technology or the network layer. The pro-
posed approaches are based on estimating the QoS
that can be offered by the ad hoc and cellular networks
subject to the context indicators and making a selec-
tion based on how well the QoS they offer matches
the requirement indicators (gathered from the appli-
cations) using fuzzy inference systems (Bouali and
Senouci, 2015) (Abbas and Saade, 2015) (Ndashimye
et al., 2016). The drawback of using fuzzy inference
systems is that they do not scale well when the num-
ber of input parameters increase.
The approach we propose strikes a delicate bal-
ance between the tradeoffs mentioned in this section
i.e., it uses a holistic approach taking a multitude of
parameters and most importantly application require-
ments (maximum tolerable latency, required reliabil-
ity in terms of PDR) into account and still remains
viable to be used for ITS applications that have strict
latency requirements.
3 HYBRID NETWORK
ARCHITECTURE
Hybrid communication systems (HCS) are systems
that are able to leverage multiple communication
technologies for improved QoS. Although a wide va-
riety of technologies can be utilized in order to realize
such a system, in the context of vehicular network-
ing use of cellular networks with Dedicated short-
range communications (DSRC) is regarded as a po-
tential solution for meeting ITS application require-
ments (Zheng et al., 2015). Therefore we focused
on enabling hybrid communications in a distributed
manner using ITS-G5 and in a centralized manner via
LTE since these technologies are already available.
Some background information about the hybrid net-
work architecture we utilized is given below so as to
ease understanding of the network selection algorithm
that will follow.
3.1 ITS-G5
The distributed approach with ITS-G5 is based on
short range wireless radio and position based ad hoc
networking. Using this approach, data packets can
be distributed to the specified geographical position
or geographical area potentially in a multi-hop fash-
ion via direct communication among the vehicles and
possibly Roadside Units (RSUs) without requiring
back-end infrastructure support (Le et al., 2011). Dis-
tribution of packets in geographical areas is possi-
ble through a set of network layer functionalities also
known as GeoNetworking (ETSI, 2017). GeoNet-
working supports multiple addressing schemes mak-
ing it possible to address an individual node by its
position or multiple nodes within a geographical re-
gion. Each node maintains a location table which
holds information about neighboring nodes and their
locations along with other features that might become
relevant for the protocol operation. Packets received
by a node are locally forwarded towards their geo-
graphic destination based on the nodes view of the
network topology and the geographical address con-
tained in the packet.
Time-controlled Neighborhood-driven Policy-based Network Selection Algorithm for Message Dissemination in Hybrid Vehicular Networks
143
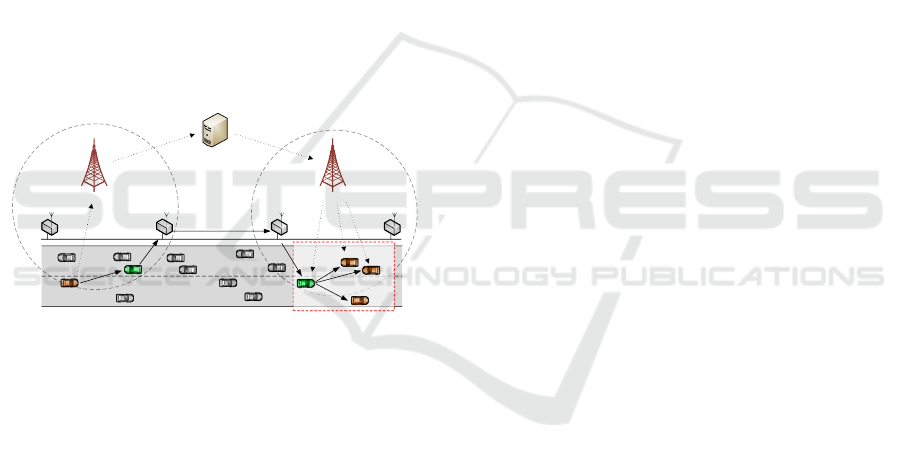
3.2 LTE and GeoMessaging Server
The infrastructure assisted approach is based on LTE.
The aim of this approach is to emulate the function-
ality of the ETSI ITS-G5 network using the cellular
network i.e. to support ad hoc like communication
between ITS stations equipped with LTE. In order to
realize this approach, we introduced a new network
component called the GeoMessaging Server (GMS).
GMS manages the distribution of ETSI ITS GeoNet-
working data packets over cellular networks. It op-
erates on the network layer (ISO/OSI layer 3) of the
protocol stack thus is unaware of the information and
contents of messages pertaining to higher protocol
layers making it application agnostic. It maintains the
context of the vehicular network through periodic lo-
cation updates sent from nodes which are LTE capa-
ble. Since GMS is aware of the mapping between IP
addresses and geographical positions, it can distribute
messages to vehicles in a geographical target area via
cellular links (Le et al., 2011). Figure 1 shows the
possible communication flows in a hybrid V2X net-
work.
eNodeBeNodeB
GeoServer
RSU
Relevance
Area
Figure 1: Possible communication flows in a hybrid V2X
network.
Hybrid ITS stations were enabled to communi-
cate with the GMS with what can be seen as a vir-
tual access layer device. This device makes UDP/IP
tunneling of GeoNetworking packets over LTE pos-
sible. Moreover, it has the added benefit of being
completely coherent with the ETSI common refer-
ence architecture as no modifications to the network
layer and above are necessary in order to use it. Un-
like wireless ad hoc communications which relies on
a shared medium with broadcast characteristics via
direct communication among the ITS stations, com-
munication is based on a client-server design with in-
dividual connections for each user and traverses the
infrastructure of the cellular network. When a vehicle
for instance detects an event and determines the geo-
graphical target area where this event should be dis-
seminated, it sends this message uplink (UL) to the
base station towards the GMS. The GMS then evalu-
ates the headers of the GeoNetworking protocol as-
sociated with this message to determine the packet
transport type and destination geographical area. It
then distributes the message downlink (DL) accord-
ingly over the cellular infrastructure. In order to
receive messages from the GMS, at least one loca-
tion update should have been sent by the ITS station
(through a time-based beaconing scheme) otherwise
the GMS would be unaware of the ITS station and
have no means to deliver the message to it.
4 POLICY-BASED NETWORK
SELECTION ALGORITHM
The design goal of the hybrid algorithm is to exploit
ITS-G5 as the primary (default) technology for trans-
mission and complement it with a limited and se-
lective support via LTE under critical conditions in
which successful transmission over the ad hoc net-
work is highly unlikely and while doing so keeping
the LTE footprint low. The algorithm takes into con-
sideration a multitude of parameters. Selection is per-
formed by each node i.e., both source and forward-
ing nodes along a packet’s path towards its destination
by monitoring application, mobility and QoS related
context indicators. As it relies on simple policies with
basic rules and parameters for network selection can
be collected without additional communication over-
head, it is characterized by its ease of implementation
and integration into the ITS environment.
In the following design considerations and main
building blocks of the algorithm will be described
followed by a detailed explanation of the parame-
ters used in the decision-making process along with
their optimal thresholds derived from conducted anal-
ysis and/or literature review. After explaining its con-
stituent components i.e. two pillars on which it rests
namely the time control mechanism and classifica-
tion of neighbors into reliable and unreliable ones, the
overall control flow of the algorithm will be provided.
4.1 Design Considerations and Features
GeoNetworking requires forwarding of a packet to-
wards the destination. This process is called line for-
warding. GeoUnicast uses line forwarding, GeoAny-
cast and GeoBroadcast use it as well if the sender
is not located within the destination area (Cam-
polo et al., 2015). There are two approaches for
line forwarding namely Contention-Based Forward-
ing (CBF) and greedy forwarding. CBF has shown to
provide much better performance in terms of reliabil-
ity than the greedy approach as it leverages multiple
forwarding candidates (Roscher et al., 2016) and is
therefore the basis of our algorithm.
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
144

Using CBF every node that is closer to the desti-
nation than the previous forwarder is considered a vi-
able forwarding candidate and sends the packet with
a delay inversely proportional to its distance progress.
This means that the candidate that is closest to the
destination will try to forward the packet first. A
forwarding candidate refrains from transmitting the
packet if it received it the second time while its CBF
contention timer is running since it means the packet
was already forwarded by another node (Campolo
et al., 2015). This suppression mechanism is an in-
tegral part of CBF.
In light of this information, it is important to ana-
lyze what would happen if the forwarding nodes were
allowed to perform network selection. In such a case,
multiple forwarding candidates might prefer to trans-
mit the packet via LTE and send the packet imme-
diately towards the GMS. As a result, the destina-
tion would receive the same packet over LTE multiple
times resulting in a very redundant usage of cellular
network resources and high congestion assuming that
under ideal network conditions, it is enough to use
LTE only once along a transmission path. The suc-
cessive forwarding over ITS-G5 only aggravates the
problem. Addressing this problem necessitates hav-
ing to implement a suppression mechanism for LTE
message transmissions by introducing additional mes-
sages or extending standardized messages for piggy-
backing this information.
In order to avoid introducing proprietary mech-
anisms and instead utilize the existing ones, LTE
transmission mechanism is integrated with CBF. This
means that whenever LTE is selected, the packet is
queued in the CBF buffer and is sent to the GMS only
when its CBF contention timer expires. It should be
noted that forwarders are not allowed to select only
LTE and should use ITS-G5 in parallel whenever LTE
is selected so as to make use of the CBF suppression
mechanism. This ensures that when the forwarder
with the most distance progress forwards the packet
first, possible LTE transmissions of other forward-
ing candidates which overhear this transmission over
ITS-G5 will be suppressed. The downside of utilizing
the CBF mechanism for LTE transmissions is that the
packets will incur queuing delays in the CBF buffer.
Also there might be some redundant transmissions in
the UL channel due to some nodes not overhearing
the ITS-G5 transmissions (NLOS conditions) how-
ever, these redundant transmissions are detected by
the duplicate packet detection performed by the GMS
based on packet IDs and sequence numbers and do not
translate into DL congestion. This logic which elim-
inates duplicates in the DL on the GMS side is also
regarded as an integral part of the algorithm’s func-
tionality.
Another important design feature of the algorithm
related to LTE transmissions is what we termed as the
LTE suppression flag which influences the selection
logic at the forwarding nodes. For this flag, we used
the reserved field of the GeoNetworking basic header
(ETSI, 2017). This flag can assume two values: 0 or
1. Whenever a forwarder receives a packet, it first in-
spects this flag. If the flag is set to 0 the forwarder
refrains from selecting LTE, if it is set to 1 the for-
warder is allowed to select LTE. This flag is set at the
decision making nodes whenever LTE is selected ac-
cording to one of the following 3 strategies and which
strategy to use is a configuration option that applies to
all nodes:
• Always set the flag to 0 i.e., indicate to other
nodes that LTE should not be selected again: This
option will henceforth be referred to as the “Flag
0“ policy. Using this configuration results in other
forwarders which will overhear this transmission
via ITS-G5 to refrain from using LTE. The ad-
vantage of this approach is that it decreases traf-
fic in the UL however, if the LTE transmission of
the node that set the flag fails due to some reason
(e.g., no coverage in the destination area), the pos-
sibility of using LTE at a later stage is eliminated
as the flag gets propagated among the forwarders.
This in turn decreases reliability.
• Always set the flag to 1 i.e. indicate to other
nodes that LTE could be reselected: This option
will henceforth be referred to as the “Flag 1“ pol-
icy. Using this approach the forwarders in the
next hop are allowed to reselect LTE. This ap-
proach increases UL channel congestion, how-
ever improves reliability. For instance if the LTE
transmission of the previous node has failed, next
hops along the transmission path are allowed to
try again and might be successful in delivering the
message.
• Set the flag dynamically: This option will hence-
forth be referred to as the “Flag dynamic“ pol-
icy. It uses the current UL Reference Signal Re-
ceived Power (RSRP) value as an indication of the
network propagation conditions and determines
whether to set the flag based on RSRP to delay
and RSRP to PDR mappings. It constitutes a mid-
dle ground in terms of LTE footprint and relia-
bility between “Flag 0“ and “Flag 1“ policies. If
the estimated delay via LTE is over the remain-
ing lifetime of the packet or the RSRP to message
delivery success probability is below the thresh-
old required by the application, the flag is set to 1
as the LTE transmission is deemed unreliable and
likely to fail.
Time-controlled Neighborhood-driven Policy-based Network Selection Algorithm for Message Dissemination in Hybrid Vehicular Networks
145

4.2 Time Control Mechanism
One of the key parameters that steers the technology
selection logic is the remaining packet lifetime. This
can be classified as an application-related network se-
lection attribute. Depending on its ITS application
class, each application can indicate the maximum tol-
erable latency for a packet. This value is set at the
source and decremented at each hop as the packet is
being forwarded.
Time control mechanism employed by the algo-
rithm is similar for source and forwarders, the only
difference being a minor extension for the source
nodes. It should also be noted that the algorithm takes
into account the CBF buffer queuing time when calcu-
lating the remaining packet lifetime at the forwarding
nodes.
4.2.1 Source Node Specific Functionality
Communication sessions originate at source nodes
thus the source nodes represent unique points in the
decision making process. Since the originated packet
has never been forwarded before and only the source
is aware of its existence at the time of the technol-
ogy selection process, source nodes are allowed to
select only LTE unlike the forwarders. Using only
LTE at the source nodes for long range transmissions
can reduce ITS-G5 channel congestion and decrease
the LTE footprint compared to its use in parallel with
ITS-G5 when “Flag 1“ or “Flag dynamic“ policy is in
effect. But sticking with the design philosophy of us-
ing ITS-G5 by default and supporting it via LTE only
when it is necessary, we limited using only LTE at
the source to one situation: only when the estimated
optimistic delay of ITS-G5 transmission based on dis-
tance to the destination (derived using dense highway
scenarios) is larger than the packet lifetime i.e., trans-
mission via ITS-G5 is not feasible and estimated to
fail.
4.2.2 Common Functionality
The main philosophy behind the time mechanisms ex-
plained in this subsection is to support the transmis-
sions via LTE whenever it is determined or estimated
that using LTE would not be possible in the next hop
due to remaining packet lifetime constraints. Mech-
anisms described in this chapter make use of the two
thresholds defined below:
• LTE Lower Delay Threshold: This is the mini-
mum possible LTE transmission latency. If the
packet lifetime drops below this value, it is not
feasible to use LTE anymore. In our simulated
LTE network this threshold was 35ms.
• LTE Upper Delay Threshold: This value is set
such that the average LTE transmission latency is
in the middle of the LTE Lower Delay Thresh-
old and this value. In our simulated LTE network,
the average LTE transmission latency was 50ms
therefore this threshold was set to 65ms.
Using these two thresholds, time mechanism func-
tions as follows:
• If the remaining packet lifetime is below the min-
imum LTE transmission latency, it is not possible
to transmit via LTE anymore therefore select only
ITS-G5. If this condition holds, LTE suppression
flag is set to 0 regardless of the chosen flag policy
so as to inform forwarders that selecting LTE is
not feasible anymore.
• If the remaining packet lifetime is between the
lower and upper thresholds i.e., it is close to the
average LTE time and destination is not among
forwarder’s reliable neighbors, support the trans-
mission via LTE in parallel to ITS-G5 otherwise
it might be too late to use it again.
• If the remaining packet lifetime is above the up-
per LTE threshold, calculate the CBF delay that
would be incurred by the next forwarder (reliable
neighbor with the most distance progress). If the
remaining packet lifetime drops below the lower
threshold by the taking into account the delay that
would be incurred in the next hop and destination
is not among forwarder’s reliable neighbors, sup-
port the transmission via LTE in parallel to ITS-
G5 otherwise it will be too late to use it again.
4.3 Reliable Neighbors
Success of multi-hop message dissemination in
VANETs depends on the presence of neighboring
nodes with stable links. Therefore a major part of the
algorithms selection logic is based on the current set
of neighbors and their classification into reliable and
unreliable ones. The algorithm classifies a communi-
cation partner as a reliable neighbor if it satisfies all
of the conditions listed below:
• It is a direct neighbor (accessible via 1 hop).
• Its distance progress is positive meaning that it is
closer to the destination than the current node.
• It is a fresh neighbor meaning that time since the
last direct message received from it, is less than
or equal 1 second. Last update time is the most
informative value for neighborhood classification
and its optimal value is taken from (Roscher et al.,
2017).
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
146
• Received signal strength of the last message from
it, is above the configured threshold. This thresh-
old is determined to be -80 dBm based on our sim-
ulations to eliminate the nodes that are close to the
maximum transmission range.
At the end of this classification process if the num-
ber of reliable neighbors is below a certain threshold,
communication is supported via LTE in parallel to
ITS-G5. This threshold was determined to be 1 mean-
ing that whenever a node does not have at least one
reliable neighbor, the algorithm secures the transmis-
sion by selecting LTE in addition to ITS-G5. It should
be noted that setting this threshold above 1 resulted in
considerable increases in LTE footprint without sig-
nificant improvements in PDR.
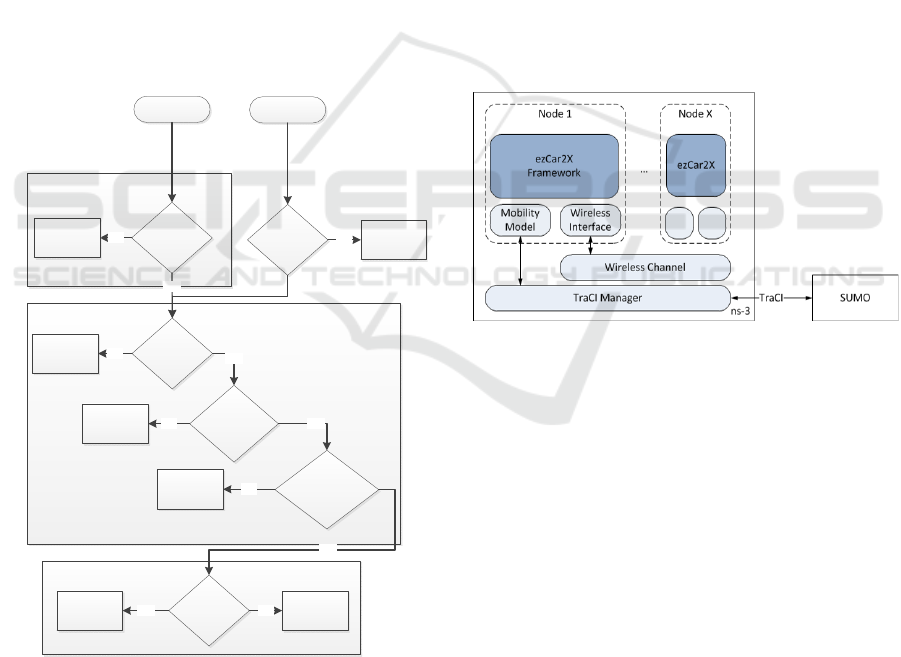
4.4 Algorithm Flowchart
Control flow of the algorithm is provided in a top-
down fashion in figure 2 with “Time-to-live“ (TTL)
denoting the remaining packet lifetime.
Source Node
Time Mechanism
Source Specific Part
Estimated ITS-
G5 delay > TTL
trueLTE
Time Mechanism Common Part
Forwarder
LTE Suppression
flag is 0
ITS-G5true
TTL < Lower LTE
Threshold
ITS-G5 true
ITS-G5 & LTE
true
TTL within
[Lower, Upper]
LTE Threshold
TTL - Delay
incurred by the next
hop < Lower LTE
Threshold
ITS-G5 & LTE true
Reliable Neighbors
# of reliable
neighbors < 1
ITS-G5 & LTEtrueITS-G5 false
false
false
false
false
Figure 2: Algorithm flowchart.
5 SIMULATION ENVIRONMENT
AND SCENARIOS
In this section the constituent components of the sim-
ulation environment are described. Moreover, the sce-
narios used to evaluate the performance of the al-
gorithm are detailed in terms of their road topology
and network design summarizing all the relevant pa-
rameters used and design considerations/assumptions
made.
5.1 Simulation Environment
Simulation environment comprises of the Network
Simulator 3 (ns-3) discrete event simulator (ns-3,
2017), Simulation of Urban Mobility (SUMO) traf-
fic simulator (D. Krajzewicz and Bieker, 2012) and
ezCar2X framework - ETSI ITS-compliant commu-
nication stack with added support for hybrid commu-
nications (Roscher et al., 2014). Figure 3 illustrates
the block diagram of the simulation toolchain.
Figure 3: Block diagram of the simulation environment.
ezCar2X is a modular software framework for rapid
prototyping of cooperative ITS applications and novel
communication protocols. It consists of an ETSI stan-
dard compliant communication stack, which was ex-
tended with an adaptive GeoNetworking layer sup-
porting application transparent geo-localized message
dissemination via ITS-G5 and LTE. ezCar2X pro-
vides basic set of protocols and abstractions, enabling
implementation of new communication algorithms
and concepts. Moreover, it allows using a single im-
plementation for evaluation both within a simulation
environment and on real world prototypes. The net-
work simulator of choice is ns-3.25. It provides out of
the box device models for IEEE 802.11-family as well
as a variety of wireless channel models. On the LTE
side, it includes the LTE/Evolved packet core (EPC)
network simulator (LENA) (LENA, 2017), which was
used for the LTE network design of the scenarios.
Traffic simulator of choice is SUMO. SUMO is cou-
pled with ns-3 using its well documented Traffic Con-
Time-controlled Neighborhood-driven Policy-based Network Selection Algorithm for Message Dissemination in Hybrid Vehicular Networks
147
trol Interface (TraCI) (Wegener et al., 2008) API with
ns-3 nodes mapped to vehicles in SUMO i.e., vehicle
movements in SUMO are communicated to the mo-
bility model of the assigned ns-3 node.
5.2 Simulation Scenarios
Performance evaluation was done utilizing 2 different
scenarios.
The first scenario is the Manhattan grid scenario
with four blocks, one lane roads and one intersec-
tion. A relatively small grid size (720 x 200 m) was
preferred to ensure straightforward results interpre-
tation. This scenario was chosen to simulate urban-
like mobility with very limited line-of-sight (LOS)
conditions. Utilizing a topology with one lane roads
makes it possible to create traffic congestion with
lower number of vehicles particularly at the central in-
tersection as the vehicles cannot drive with their max-
imum target speed as in the case of a highway sce-
nario. Moreover, it helps create a non-uniform distri-
bution of vehicles where inter-vehicle gaps are more
pronounced allowing simulation of challenging con-
ditions for ITS-G5, where ad hoc communication can
be disrupted due to network fragmentation.
The second scenario is the highway - a 10 km long
road with 3 lanes in each direction. This scenario was
chosen to evaluate the algorithm with highly mobile
users in LOS conditions. Contrary to the Manhat-
tan scenario, vehicles do not face any obstacles in the
form of buildings that might disrupt their communi-
cation via ITS-G5 however, due to their high mobility
patterns; they experience higher frequency dispersion
as a result of Doppler shift (fast fading) which reduces
LTE transmission reliability.
5.2.1 Traffic Parameters
Vehicle and packet traffic can be varied using the fol-
lowing parameters:
• Vehicle injection rate: Determines the traffic den-
sity by controlling how many cars depart every
second from each lane.
• Penetration rate: Determines the proportion of ve-
hicles equipped with communication capabilities
i.e, vehicles that are ITS-G5 and LTE capable.
• Packet generation rate: Determines the number of
packets generated within a predefined time frame.
Summary of traffic related parameters for each
scenario is presented in Table 1. It is worth mention-
ing that the values for these parameters were chosen
so as to create low road traffic saturation. This al-
lowed us to test our algorithm under unfavorable ITS-
G5 conditions to gauge the benefits of using a hybrid
Table 1: Summary of traffic related parameters for each sce-
nario.
Scenario Manhattan Highway
Vehicles saturation level
40 180
Penetration rate 0.1, 0.3, 0.6, 1 0.1, 0.3, 0.6, 1
Hybrid capable vehicles (avg.)
4, 12, 24, 40 18, 54, 108, 180
Packet generation rate [Hz]
10 10
Vehicle injection rate [Hz]
0.5 0.1
Average speed [kmph] 30 100
Simulation time [s] 400 500
approach, but also to better understand the influence
of simulation parameters on defined KPIs.
5.2.2 Communication Parameters
In our simulations at every packet generation instant,
the framework picks randomly the source and desti-
nation nodes and creates a corresponding communi-
cation session. These sessions are created uniformly
with respect to distance and correspond to a valid
range of [0,720] m for the Manhattan scenario and
[0,5000] m for the Highway scenario. All created ses-
sions are unicast ones, meaning that each packet is
designated for only one receiving node. Table 2 pro-
vides a summary of ITS-G5 communication parame-
ters.
Table 2: Summary of ETSI ITS-G5 parameters.
Parameter Value
Tx Power 23 dBm
Propagation Model Nakagami with obstacles
Uni-cast Packet size 300 Bytes
Neighbor timeout 20 s
Default Beaconing rate 0.3 Hz
For ITS-G5 communication we used a realis-
tic, computationally inexpensive simulation model
for IEEE 802.11p radio shadowing in urban environ-
ments that allowed us to model a city scenario with
obstacles. It is comprised of the Nakagami fading
channel described in (Taliwal et al., 2004) with the
obstacle shadowing model in (Sommer et al., 2011a).
From the LTE design point of view, the network
is planned to provide good coverage conditions, with-
out severe fading/shadowing effects that would result
in intermittent connectivity. The detailed overview of
LTE design parameters is presented in Table 3. The
Figures 4 and 5 depict the Manhattan and the High-
way scenarios under the coverage of the designed LTE
network respectively.
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
148
Table 3: Summary of relevant LTE design parameters.
Parameter Manhattan Highway
Number of sites (cells)
1 (3) 3 (6)
UL EARFCN 18100
DL EARFCN 100
Frequency Reuse 1
Bandwidth per Cell 25 PRB
Propagation Model Log Distance
Pathloss Exponent 3.9 3.1
Reference Loss 38.57 dB
UE max. Tx Power 23 dBm
eNodeB max. Tx Power
43 dBm
Antenna Model Cosine
UE Antenna Gain 0 dBi
eNodeB Antenna Gain
18 dBi 11 dBi
eNodeB Antenna HPBW
65 degrees 120 degrees
UE NF 7 dB
eNodeB NF 2 dB
Target Edge Throughput
0.5 Mbps
Target min. SINR
0.2 dB
Cell Radius 578 m 1773 m
HO type PBGT
HO Hysteresis 3 dB
HO TTT 256 ms
Average Speed for Channel Fading
30 km/h 100 km/h
Fading Model Time Resolution
1 ms
Figure 4: Schematic coverage area for the Manhattan sce-
nario.
Figure 5: Schematic coverage area for the Highway sce-
nario.
6 PERFORMANCE EVALUATION
The evaluation considers different scenarios and pen-
etration rates as well as the distance to destination
and application time requirements to present impor-
tant KPIs, such as PDR and LTE Packet load, in com-
parison to reference simulations, namely transmission
using only ITS-G5, only LTE and both technologies.
6.1 Methodology
Since for the Manhattan scenario the generated ses-
sions are in the close range of [0,720] m, the re-
sults were not fractioned into different distance bins
and are presented as an average over all transmis-
sions. In the Highway scenario the results are pre-
sented for the following ranges: close [0,500] m,
medium [500,2500] m and far [2500,5000] m. Time
requirement, which is termed as “Application delay
requirement”, is used to assess the performance of the
algorithm under two application-imposed time con-
straints (100ms and 500ms) defined in (Karagiannis
et al., 2011) as plausible thresholds for foreseen ITS
services. Additionally, the algorithm is evaluated un-
der time-unlimited conditions to obtain an insight on
the performance of its Neighborhood-driven part. The
KPIs used, namely PDR and Packet load, are defined
as follows:
PDR
dest
u
=
n
dest
u,r
n
source
u,g
, (1)
where PDR
dest
u
is PDR of unique packets measured
at the destination, n
dest
u,r
is the number of correctly re-
ceived unique packets at the destination and n
source
u,g
is
the total number of unique packets generated at the
source.
L
gms
u
=
n
gms
u,r
n
source
u,g
, (2)
where L
gms
u
is the Packet load due to the unique pack-
ets measured at the GMS, n
gms
u,r
is the number of
uniquely received packets at the GMS and n
source
u,g
is
the total number of unique packets generated at source
nodes.
L
gms
r
=
n
gms
r,r
n
source
u,g
, (3)
where L
gms
r
is the Packet load due to redundant pack-
ets measured at the GMS, n
gms
r,r
is the number of re-
dundantly received packets at the GMS and n
source
u,g
is
the total number of unique packets generated at source
nodes.
L
gms
tot
= L
gms
u
+ L
gms
r
, (4)
where L
gms
tot
is the total Packet load measured at the
GMS. To illustrate the gains of the algorithm over
a single technology, the results were depicted for
the same scenarios and configuration using a single
technology at each node i.e., only ITS-G5 or only
LTE. Moreover, to show the maximum achievable
PDR (ceiling values) using the hybrid ITS-G5/LTE
approach, the same simulations were run using both
technologies simultaneously at each node, without
any DL redundancy suppression techniques at the
GMS/vehicle side. All results are presented with a
confidence level of 95%.
Time-controlled Neighborhood-driven Policy-based Network Selection Algorithm for Message Dissemination in Hybrid Vehicular Networks
149
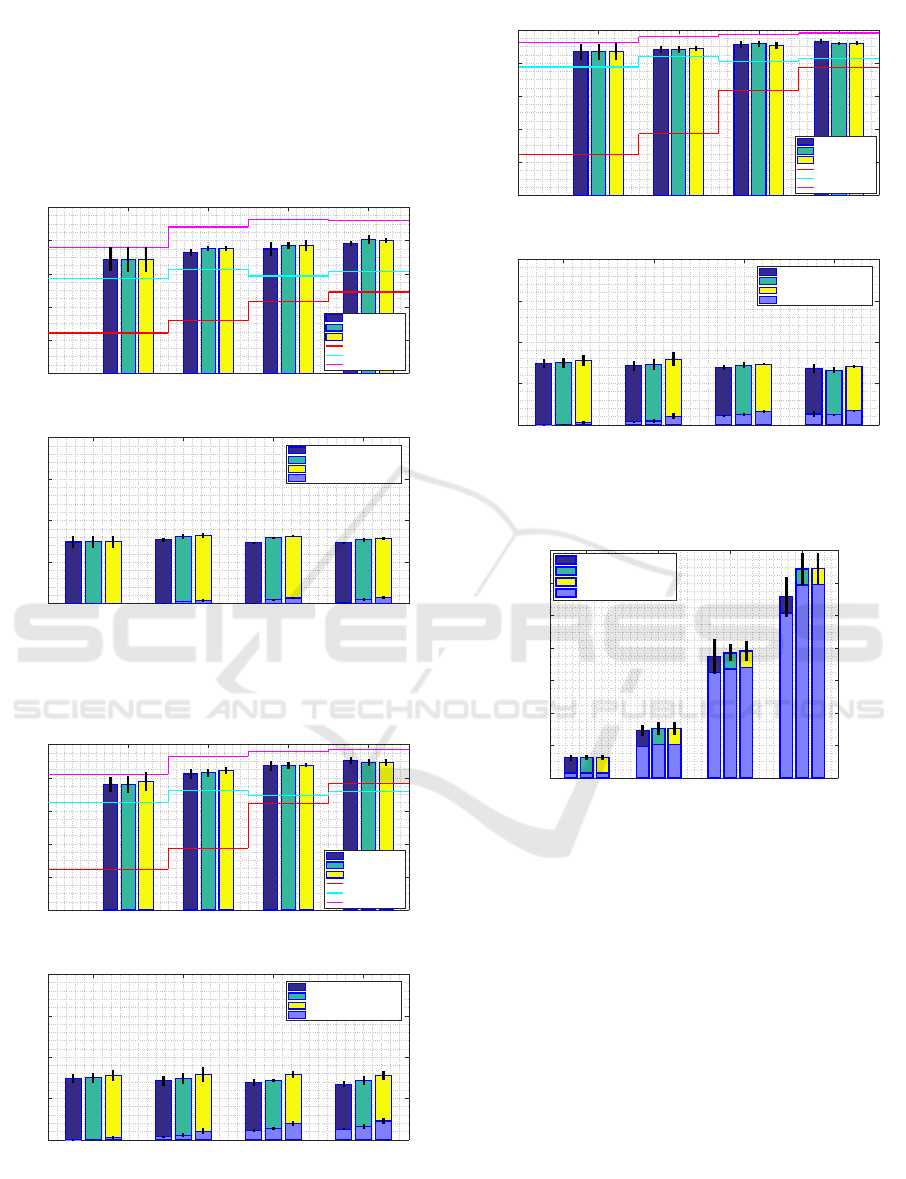
6.2 Simulation Results
In the following the graphs for the Manhattan sce-
nario are shown. Figures 6, 7 and 8 present the results
for 100ms, 500ms and unlimited Application delay
requirements respectively. Figure 9 shows the total
Packet load when both technologies are used.
0.1 (4) 0.3 (12) 0.6 (24) 1.0 (40)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
100ms application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (4) 0.3 (12) 0.6 (24) 1.0 (40)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
100ms application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 6: Upper graph: PDR; Lower graph: Total Packet
load ratio for Application delay requirement 100ms (Man-
hattan scenario).
0.1 (4) 0.3 (12) 0.6 (24) 1.0 (40)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
500ms application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (4) 0.3 (12) 0.6 (24) 1.0 (40)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
500ms application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 7: Upper graph: PDR; Lower graph: Total Packet
load ratio for Application delay requirement 500ms (Man-
hattan scenario).
0.1 (4) 0.3 (12) 0.6 (24) 1.0 (40)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
unlimited application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (4) 0.3 (12) 0.6 (24) 1.0 (40)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
unlimited application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 8: Upper graph: PDR; Lower graph: Total Packet
load ratio for unlimited Application delay requirement
(Manhattan scenario).
0.1 (4) 0.3 (12) 0.6 (24) 1.0 (40)
Penetration rate (avg. number of vehicles)
0
2
4
6
8
10
12
14
total Packet load
100ms (Unique packets)
500ms (Unique packets)
Unlimited (Unique packets)
Redundant packets
Figure 9: Total Packet load using both technologies (Man-
hattan scenario).
From the Manhattan scenario graphs, we observed
a poor ITS-G5 performance - only up to 50% PDR for
time critical transmissions (100ms) and at very low
Penetration rates (0.1) - only up to 25% for any time
requirement. Whereas LTE ensures average to decent
communication support resulting in average at 60%
to 80% PDR depending on the time requirement. In
light of such results, our algorithm demonstrated very
high PDR, above ITS-G5 and LTE for any configura-
tion, resulting in average at 70% to 90% and getting
very close to the value achieved using both technolo-
gies whilst keeping Packet load stable at around 75%.
It is important to note that using both technologies,
the Packet load is drastically higher than for the algo-
rithm and results in up to 17-fold increase (confidence
intervals are provided for the total Packet load only).
Since in this scenario mostly the neighborhood-driven
logic of the algorithm is triggered due to lack of re-
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
150
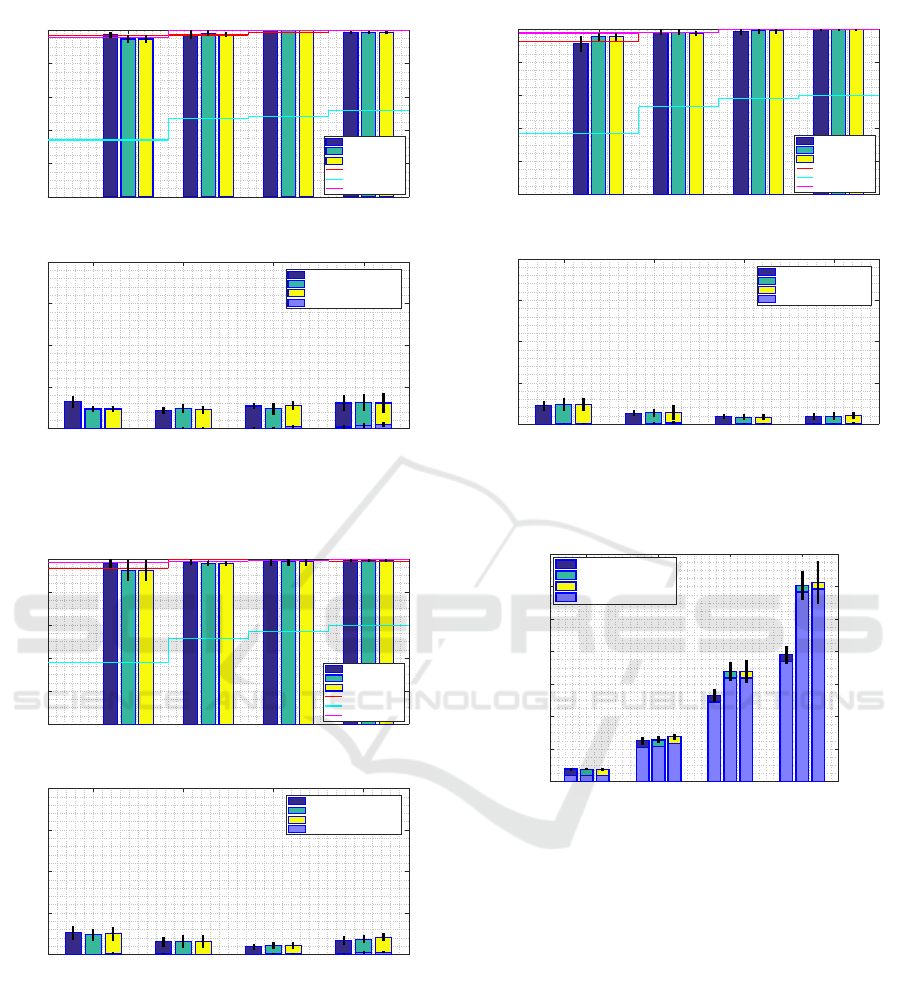
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
100ms application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
100ms application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 10: Upper graph: PDR; Lower graph: Total Packet
load ratio for Application delay requirement 100ms (High-
way scenario, close range).
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
500ms application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
500ms application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 11: Upper graph: PDR; Lower graph: Total Packet
load ratio for Application delay requirement 500ms (High-
way scenario, close range).
liable neighbors, we did not observe any significant
difference in using one of the three LTE suppression
techniques as they get pronounced when the time con-
trol mechanism is used to trigger LTE transmission.
Next, we present the graphs for the Highway sce-
nario. Figures 10, 11 and 12 illustrate the results for
100ms, 500ms and unlimited Application delay re-
quirements respectively for close range transmissions
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
unlimited application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
unlimited application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 12: Upper graph: PDR; Lower graph: Total Packet
load ratio for unlimited Application delay requirement
(Highway scenario, close range).
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
5
10
15
20
25
30
35
total Packet load
100ms (Unique packets)
500ms (Unique packets)
Unlimited (Unique packets)
Redundant packets
Figure 13: Total Packet load using both technologies (High-
way scenario, close range).
up to 500m. Figures 14, 15 and 16 depict the results
for medium range transmissions and Figures 18, 19
and 20 for the far range. Figure 13, 17 and 21 show
the total Packet load for both technologies at close,
medium and far ranges respectively.
From the Highway scenario graphs for closed
range transmissions, we observed that ITS-G5 pro-
vides a very high PDR - on average 95% for all con-
figurations, whereas LTE due to fast fading achieved
at maximum 60%. In this respect, our algorithm had
shown its good adaptability and achieved the same
PDR as ITS-G5 while keeping the total Packet load at
maximum 30% - only in time critical case of 100ms
which proves the proper functioning of its time con-
trol mechanism. Usage of both technologies resulted
in enormous total Packet load, especially in the time
unlimited case where the number reached 3000%.
Time-controlled Neighborhood-driven Policy-based Network Selection Algorithm for Message Dissemination in Hybrid Vehicular Networks
151
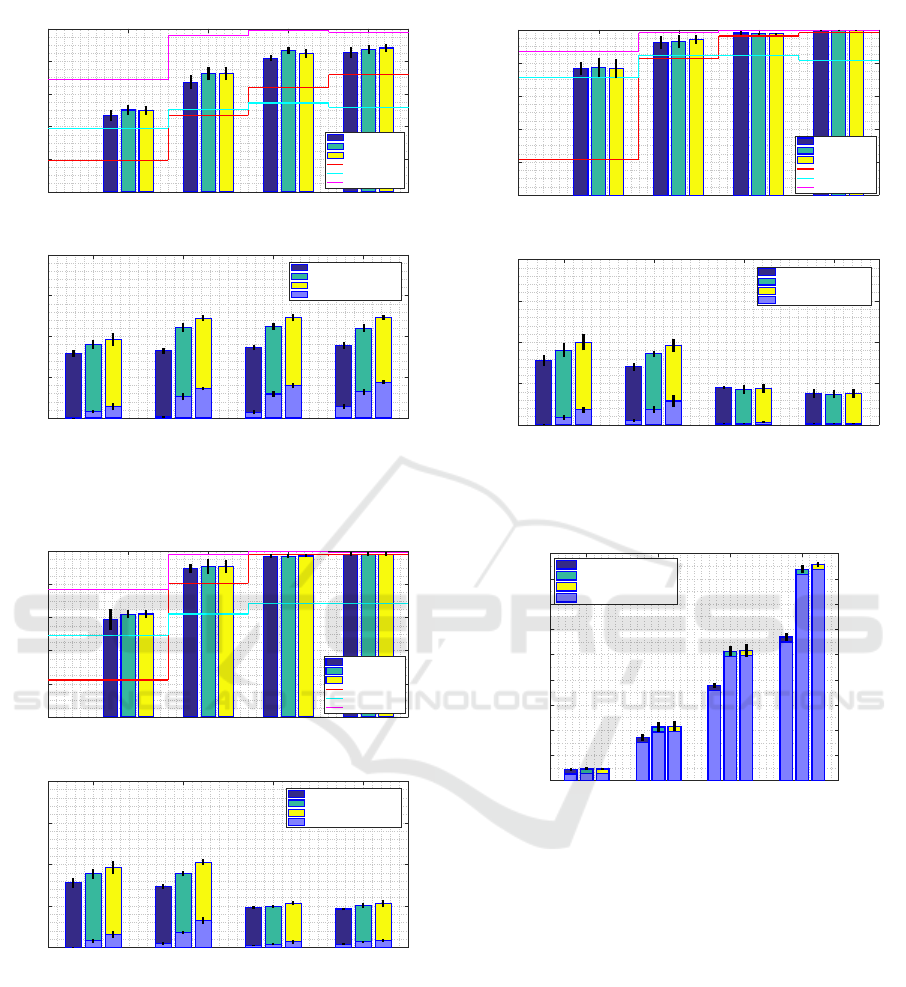
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
100ms application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
100ms application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 14: Upper graph: PDR; Lower graph: Total Packet
load ratio for Application delay requirement 100ms (High-
way scenario, medium range).
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
500ms application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
500ms application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 15: Upper graph: PDR; Lower graph: Total Packet
load ratio for Application delay requirement 500ms (High-
way scenario, medium range).
Again, we did not observe any significant difference
between the three LTE suppression techniques as the
transmission distance is very short.
From the Highway scenario graphs for medium
range transmissions, we observed that ITS-G5 has
very low PDR - 20% for the Penetration rate of 0.1
for all delay requirements and performs mediocre for
all other considered penetration rates in the time crit-
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
unlimited application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
unlimited application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 16: Upper graph: PDR; Lower graph: Total Packet
load ratio for unlimited Application delay requirement
(Highway scenario, medium range).
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
5
10
15
20
25
30
35
40
45
total Packet load
100ms (Unique packets)
500ms (Unique packets)
Unlimited (Unique packets)
Redundant packets
Figure 17: Total Packet load using both technologies (High-
way scenario, medium range).
ical case of 100ms. LTE showed in average 50% to
80% of PDR depending on the time requirement. The
selection algorithm confirmed its efficiency and over-
performed all technologies in all cases for all config-
urations. Importantly, for the time limited scenario
of 100ms, it showed a 10% to 20% increase in PDR
over the best technology. Total Packet load in most of
the cases was below 100%. The usage of two tech-
nologies is highly inexpedient in this scenario and re-
sulted in up to 4500% of total Packet load providing
only minor increases in terms of PDR in the 500ms
and time unlimited cases. For the medium range, us-
ing the dynamic LTE suppression technique i.e., “Flag
dynamic“ policy can save up to 12% of total Packet
load while guaranteeing the same PDR as the unre-
stricted “Flag 1“ policy.
From the Highway scenario graphs for far range
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
152
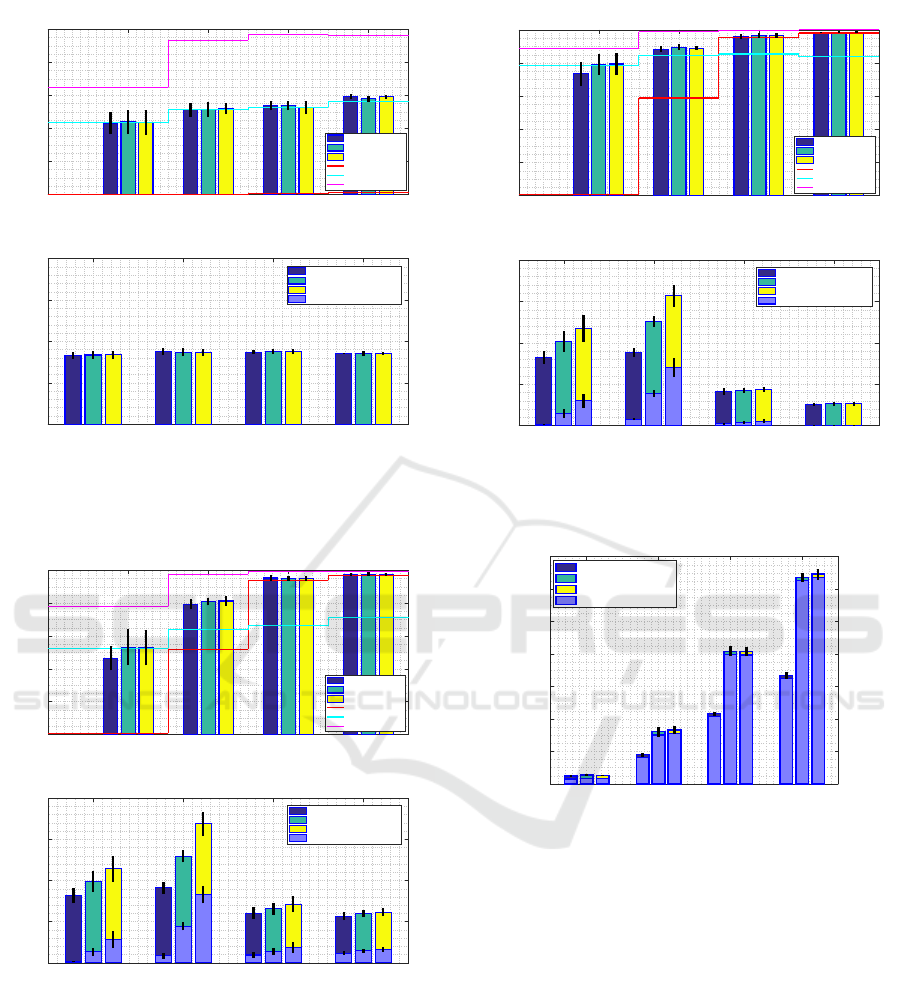
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
100ms application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
100ms application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 18: Upper graph: PDR; Lower graph: Total Packet
load ratio for Application delay requirement 100ms (High-
way scenario, far range).
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
500ms application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
500ms application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 19: Upper graph: PDR; Lower graph: Total Packet
load ratio for Application delay requirement 500ms (High-
way scenario, far range).
transmissions, we observed that cumulative ITS-G5
delay (due to CBF buffer waiting time) excludes the
possibility of successful packet transmission for the
time critical case of 100ms or for the very low pen-
etration rate of 0.1. The only technology that can be
used under these circumstances is LTE, that shows on
average 50% to 80% PDR which our algorithm per-
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.2
0.4
0.6
0.8
1
PDR
unlimited application delay requirement
Flag 0
Flag dynamic
Flag 1
only ITS-G5
only LTE
BOTH technologies
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
0.5
1
1.5
2
total Packet load
unlimited application delay requirement
Flag 0 (Unique packets)
Flag dynamic (Unique packets)
Flag 1 (Unique packets)
Redundant packets
Figure 20: Upper graph: PDR; Lower graph: Total Packet
load ratio for unlimited Application delay requirement
(Highway scenario, far range).
0.1 (18) 0.3 (54) 0.6 (108) 1.0 (180)
Penetration rate (avg. number of vehicles)
0
10
20
30
40
50
60
70
total Packet load
100ms (Unique packets)
500ms (Unique packets)
Unlimited (Unique packets)
Redundant packets
Figure 21: Total Packet load using both technologies (High-
way scenario, far range).
fectly matches in every tested case. Once ITS-G5
PDR rises above zero in the 500ms delay requirement
case, the selection algorithm starts to over-perform
the best technology resulting in a clear improvement
over a single technology approach. In general, if the
time requirement is not too strict (500ms or higher)
and penetration rate is above 0.1, we observed that the
transmission over far distances using our algorithm is
possible with decent PDR values of 80% and above.
Since the communication range is long and average
number of forwarders is larger in comparison to pre-
vious ranges, usage of two technologies redundantly
results in extremely high total Packet load values of
up to 6500%. Using the proposed algorithm and the
“Flag dynamic“ policy in this scenario, one can save
up to 40% of total Packet load while ensuring the
same PDR as the unrestricted “Flag 1“ policy.
Time-controlled Neighborhood-driven Policy-based Network Selection Algorithm for Message Dissemination in Hybrid Vehicular Networks
153

6.3 Evaluation Summary
Abstracting from the absolute numbers, we can con-
clude that the results of our experiments proved the
capability of the proposed algorithm to provide sub-
stantial performance improvements (measured in tens
of percent) over a single technology approach when-
ever using ITS-G5 and LTE is physically possible (i.e.
their respective PDRs are greater than zero). When it
is infeasible or risky to use ITS-G5, the hybrid algo-
rithm will immediately switch to LTE, for instance in
medium/far range transmissions in time limited cases,
which confirms the effectiveness of its time control
mechanism, or under the absence of forwarding vehi-
cles in the vicinity, which confirms the effectiveness
of its neighborhood assessment logic. The ultimate
PDR gain of the policy-based algorithm is not only
achieved by using dozens of times less LTE resources
than the both technologies approach, but it also relies
on the proposed GMS logic that entirely eliminates
LTE DL redundancy.
7 CONCLUSION AND OUTLOOK
In this work we tried to remedy the cases when ITS-
G5 is physically unable to satisfy the QoS require-
ments demanded by applications particularly pertain-
ing to reliable and time critical data transfers. This
occurs usually at low traffic densities with low num-
ber of forwarders, at long communication ranges or in
presence of obstacles. In order to better fulfill appli-
cation QoS requirements we proposed a policy-based
network selection algorithm that enables combining
the strengths of ad hoc and infrastructure-based net-
works. The algorithm was designed to take into ac-
count the most relevant parameters for ITS-G5 to ad-
dress critical cases for vehicular ad hoc connectivity.
It relies on a multi-parameter neighborhood estimate,
being on the other hand secured with a time control
mechanism that facilitates in-time delivery of mes-
sages.
Evaluation showed that the proposed algorithm
significantly improved the overall reliability of ve-
hicular data transmissions in all considered scenarios
and distance ranges, over-performed traditional ITS-
G5, provided a necessary support in neighborhood-
constrained or time critical scenarios and demon-
strated an ability to select the optimal technology to
achieve PDR values always equal or higher than the
best technology. LTE load rarely exceeded the num-
ber of uniquely generated packets leading to a limited
LTE usage which was one of the main design goals of
the algorithm. Performance improvements over ap-
proaches using a single technology is the result of
proper and selective simultaneous usage of ITS-G5
and LTE. It is worth noting that the algorithm not only
achieved higher PDR efficiency than the best technol-
ogy, it also entirely eliminated the DL redundancy,
since the duplicate packets received on the UL are not
forwarded in the DL thanks to the mechanisms imple-
mented on the GMS side.
In the future it is worth evaluating the proposed
algorithm for GeoBroadcast message dissemination
under diverse LTE scenario realizations. Also both
GeoUnicast and GeoBroadcast cases have to be veri-
fied in real field-tests to obtain better insights on the
algorithm’s performance. Additionally, it is foreseen
that the current GMS logic will be improved to take
advantage of UL redundancy by enabling DL success
estimation via incorporation of RSRP values in the
location update beacons sent to the GMS. Moreover,
a scheme utilizing the nodes with negative distance
progress will be considered in order to increase LTE
transmission success in cases exhibiting spotty cover-
age.
ACKNOWLEDGEMENTS
The research leading to these results has received
funding from the Bavarian Ministry of Economic Af-
fairs and Media, Energy and Technology and the Eu-
ropean Union in the Horizon 2020 project TIMON,
Grant Agreement No. 636220.
REFERENCES
5G-PPP (2015). 5G Automotive Vision, White paper.
Abbas, N. and Saade, J. J. (2015). A fuzzy logic based
approach for network selection in wlan/3g heteroge-
neous network. In Consumer Communications and
Networking Conference (CCNC), 2015 12th Annual
IEEE, pages 631–636. IEEE.
Araniti, G., Campolo, C., Condoluci, M., Iera, A., and
Molinaro, A. (2013). Lte for vehicular networking: a
survey. IEEE Communications Magazine, 51(5):148–
157.
Bouali, T. and Senouci, S.-M. (2015). A fuzzy logic-based
communication medium selection for qos preserva-
tion in vehicular networks. In Proceedings of the 5th
ACM Symposium on Development and Analysis of In-
telligent Vehicular Networks and Applications, pages
101–108. ACM.
Brickley, O., Shen, C., Klepal, M., Tabatabaei, A., and
Pesch, D. (2007). A data dissemination strategy for
cooperative vehicular systems. In Vehicular Technol-
ogy Conference, 2007. VTC2007-Spring. IEEE 65th,
pages 2501–2505. IEEE.
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
154

Campolo, C., Molinaro, A., and Scopigno, R. (2015). Ve-
hicular ad hoc networks. Standards, Solutions, and
Research.
Charilas, D. E. and Panagopoulous, A. D. (2010). Mul-
tiaccess radio network enviroments. IEEE Vehicular
Technology Magazine, 5(4):40–49.
D. Krajzewicz, J. Erdmann, M. B. and Bieker, L. (2012).
Recent development and applications of sumo - simu-
lation of urban mobility.
ETSI (2010). ETSI TS 102 637-1 V1.1.1 - Intelligent Trans-
port Systems (ITS); Vehicular Communications; Ba-
sic Set of Applications; Part 1: Functional Require-
ments.
ETSI (2013). ETSI EN 302 663 V1.2.1 - Intelligent Trans-
port Systems (ITS); Access layer specification for In-
telligent Transport Systems operating in the 5 GHz
frequency band.
ETSI (2017). Etsi en 302 636-4-1 v1.3.1 - intelli-
gent transport systems (its); vehicular communica-
tions; geonetworking; part 4: Geographical address-
ing and forwarding for point-to-point and point-
to-multipoint communications; sub-part 1: Media-
independent functionality.
Gopinath, S., Wischhof, L., Jaumann, M., Ponikwar,
C., and Hof, H.-J. (2016a). On context-aware
communication mode selection in hybrid vehicu-
lar networks. In Fachgespr
¨
ach Inter-Vehicle Com-
munication 2016-(inter-veh-comm-2016). Humboldt-
Universit
¨
at zu Berlin.
Gopinath, S., Wischhof, L., Ponikwar, C., and Hof, H.-J.
(2016b). Hybrid solutions for data dissemination in
vehicular networks. In Wireless Days (WD), 2016,
pages 1–4. IEEE.
Karagiannis, G., Altintas, O., Ekici, E., Heijenk, G., Jaru-
pan, B., Lin, K., and Weil, T. (2011). Vehicular net-
working: A survey and tutorial on requirements, ar-
chitectures, challenges, standards and solutions. IEEE
Communications Surveys and Tutorials, 13:584–616.
Kumar, V., Bauza, R., Filali, F., Gozalvez, J., Lin, L., and
Rondinone, M. (2009). itetris-a large scale integrated
simulation platform for v2x communications: Appli-
cation to real-time traffic management. In Proc. of the
9th international conference on Intelligent Transport
Systems Telecommunications (ITST), Lille.
Kumaran, U. and Shaji, R. (2014). Vertical handover
in vehicular ad-hoc network using multiple parame-
ters. In Control, Instrumentation, Communication and
Computational Technologies (ICCICCT), 2014 Inter-
national Conference on, pages 1059–1064. IEEE.
Le, L., Festag, A., Mader, A., Baldessari, R., Sakata, M.,
Tsukahara, T., and Kato, M. (2011). Infrastructure-
assisted communication for car-to-x communication.
In Proceedings of the ITS world congress.
LENA (2017). Lte-epc network simulator.
http://networks.cttc.es/mobile-networks/software-
tools/lena/. Last accessed on 26.10.2017.
Meneguette, R. I., Madeira, E. R., and Bittencourt, L. F.
(2012). Multi-network packet scheduling based on ve-
hicular ad hoc network applications. In Proceedings of
the 8th International Conference on Network and Ser-
vice Management, pages 214–218. International Fed-
eration for Information Processing.
Ndashimye, E., Sarkar, N. I., and Ray, S. K. (2016). A
novel network selection mechanism for vehicle-to-
infrastructure communication. In Dependable, Auto-
nomic and Secure Computing, IEEE 14th Intl Conf
on Pervasive Intelligence and Computing, 2016, pages
483–488. IEEE.
ns-3 (2017). Network simulator 3. http://www.nsnam.org.
Last accessed on 26.10.2017.
Olivera, J. A., Cort
´
azar, I., Pinart, C., Los Santos, A.,
and Lequerica, I. (2009). Vanba: a simple handover
mechanism for transparent, always-on v2v communi-
cations. In Vehicular Technology Conference, 2009.
VTC Spring 2009. IEEE 69th, pages 1–5. IEEE.
Roscher, K., Bittl, S., Gonzalez, A., Myrtus, M., and Jiru,
J. (2014). ezcar2x: rapid-prototyping of communica-
tion technologies and cooperative its applications on
real targets and inside simulation environments. In
11th Conference Wireless Communication and Infor-
mation, pages 51–62.
Roscher, K., Jiru, J., and Knorr, R. (2016). Low-delay
forwarding with multiple candidates for vanets using
multi-criteria decision making. In Vehicular Network-
ing Conference (VNC), 2016 IEEE, pages 1–8. IEEE.
Roscher, K., Nitsche, T., and Knorr, R. (2017). Know thy
neighbor - a data-driven approach to neighborhood es-
timation in vanets. IEEE Vehicular Technology Con-
ference.
Sommer, C., Eckhoff, D., German, R., and Dressler, F.
(2011a). A computationally inexpensive empirical
model of ieee 802.11 p radio shadowing in urban en-
vironments. In Wireless On-Demand Network Sys-
tems and Services (WONS), 2011 Eighth International
Conference on, pages 84–90. IEEE.
Sommer, C., German, R., and Dressler, F. (2011b). Bidirec-
tionally coupled network and road traffic simulation
for improved ivc analysis. IEEE Transactions on Mo-
bile Computing, 10(1):3–15.
Taliwal, V., Jiang, D., Mangold, H., Chen, C., and Sen-
gupta, R. (2004). Empirical determination of channel
characteristics for DSRC vehicle-to-vehicle commu-
nication. In Proceedings of the 1st ACM international
workshop on Vehicular ad hoc networks, page 88.
ACM.
Wang, L. and Kuo, G.-S. G. (2013). Mathematical mod-
eling for network selection in heterogeneous wireless
networksa tutorial. IEEE Communications Surveys &
Tutorials, 15(1):271–292.
Wegener, A., Pi
´
orkowski, M., Raya, M., Hellbr
¨
uck, H., Fis-
cher, S., and Hubaux, J.-P. (2008). Traci: an interface
for coupling road traffic and network simulators. In
Proceedings of the 11th communications and network-
ing simulation symposium, pages 155–163. ACM.
Zheng, K., Zheng, Q., Chatzimisios, P., Xiang, W., and
Zhou, Y. (2015). Heterogeneous vehicular network-
ing: a survey on architecture, challenges, and so-
lutions. IEEE communications surveys & tutorials,
17(4):2377–2396.
Time-controlled Neighborhood-driven Policy-based Network Selection Algorithm for Message Dissemination in Hybrid Vehicular Networks
155
