
Sensornet
A Key Predistribution Scheme for Distributed Sensors using Nets
Deepak Kumar Dalai
1
and Pinaki Sarkar
2
1
School of Mathematical Sciences, National Institute of Science Education and Research, Bhubaneswar 752 050, India
2
Department of Computer Science and Automation, Indian Institute of Science, Bengaluru 560 012, India
Keywords:
Partial Spread, Net, Combinatorial Designs, Key Predistribution Scheme, Distributed Sensor Networks.
Abstract:
Key management is an essential functionality for developing secure cryptosystems; particularly for implemen-
tations to low cost devices of a distributed sensor networks (DSN)–a prototype of Internet of Things (IoT).
Low cost leads to constraints in various resources of constituent devices of a IoT (sensors of a DSN); thereby
restricting implementations of computationally heavy public key cryptosystems. This leads to adaptation of
the novel key predistribution trick in symmetric key platform to efficiently tackle the problem of key man-
agement for these resource starved networks. After a few initial proposals based on random graphs, most
key predistribution schemes (KPS) use deterministic (combinatorial) approaches to assure essential design
properties. Combinatorial designs like a (v,b,r,k)−configuration which forms a µ(v,b,r,k)−CID are effective
schemes to design KPS (Lee and Stinson, 2005). A net in a vector space is a set of cosets of certain kind of
subspaces called partial spread. A µ(v,b,r, k)−CID can be formed from a net. In this paper, we propose a key
predistribution scheme for DSN, named as sensornet, using net. Effectiveness of sensornet in term of crucial
metrics in comparison to other prominent schemes has been theoretically established.
1 INTRODUCTION
Distributed (Wireless) Sensor Networks (DSN) are
regarded as revolutionary information gathering sys-
tems owing to their easy deployment and flexible
topology. They are decentralized with numerous
low-cost identical resource starved wireless devices,
called sensors or nodes, that deal with sensory data.
They are considered to be a nice prototype of Internet
of Things (IoT) which is a sophisticated concept that
aims to connect our world. This has boosted the study
of such distributed networks in modern times.
Prominent scientific applications of IoT are smart
homes, smart cities, smart grids, smart water net-
works, agriculture, health-care, etc. Of particular in-
terest are applications of DSN to networks where se-
curity is a premium; For instance, security may be es-
sential for certain sensitive scientific and military net-
works that are meant for (i) military surveillance, (ii)
force protection arenas, (iii) self healing minefields,
and so on. Primary tasks of devices of an IoT in any
such application are to collect information from their
surrounding, process and forward them to other de-
vices. Depending on specific applications, they may
be further required to (i) track and/or classify an ob-
ject, (ii) determine parametric value(s) of a given lo-
cation, etc. These sensitive task for such critical ap-
plications create the necessity of secure message ex-
change among the low cost IoT devices.
1.1 Type of Cryptosystem for KPS
Constraints in resources of constituent ordinary de-
vices of any IoT (like sensors of DSN) make us opt for
symmetric key cryptosystems (SKC) over their public
key counterparts while designing security protocols
for such networks. SKC require both the sender and
receiver(s) to possess same encryption-decryption key
before message exchange. Standard online key ex-
change techniques that involve public parameters are
generally avoided due to their heavy computations.
One can think of two trivial key distribution tech-
niques. First is to assign a single key for entire net-
work devices. Second is to think of assigning pair-
wise distinct (symmetric) keys for every pair of de-
vices. Former method is completely vulnerable to
single point failure (compromise of even one sensor
reveals this single system key). Whereas, the second
strategy overloads the memory of each sensor; since
N − 1 keys are required to be stored per sensor for
a network of size N . This is particularly impractical
Dalai D. and Sarkar P.
Sensornet - A Key Predistribution Scheme for Distributed Sensors using Nets.
DOI: 10.5220/0006132700490058
In Proceedings of the 6th International Conference on Sensor Networks (SENSORNETS 2017), pages 49-58
ISBN: 421065/17
Copyright
c
2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
49

for large networks (i.e., large value of N ).
Treating a node (or a few) as Trusted Authority
(TA) is risky. This also makes the network prone to
single point failure as capture of this authority (sen-
sor) acting as a TA makes the system vulnerable.
Thereby schemes like Kerberos are avoided while de-
signing secure key management schemes for DSN.
These facts emphasizes the importance of employ-
ing an adequate key management scheme for such
networks. This stalemate situation was wittily over-
come in 2002 by Eschenauer and Gligor by introduc-
ing the concept of key predistribution that involves ap-
plications of SKC to sensor networks. Any key pre-
distribution scheme primarily execute the following:
• Key Distribution: Prior to deployment, keys are
preloaded into sensors to form their keyrings or
key chains from the collection of all network keys,
called key pool. Each system key is marked with
an unique identifier (key id). Certain schemes (Ruj
and Roy, 2008) consider (node id) as an unique
function of all the key ids. These key or, node id
are used during key establishment.
• Key Establishment: The preloaded keys are es-
tablished by a two steps process, described below:
(i) Shared key discovery phase establishes
the shared common key(s) among the participant
nodes. This may be achieved by broadcasting the
key ids of all keys contained in the nodes (or node
id). On receiving each other’s key ids, the sensors
tally (or equate) them to trace their mutual shared
key id(s), hence common shared key(s).
(ii) Path key establishment phase establishes
an optimized path key between a pair of nodes that
do not share a common key. This process involves
intermediate nodes. Refer to common intersection
designs in Section 3.
Depending on whether the above processes are
probabilistic or deterministic, such schemes are clas-
sified into two types: (a) random and (b) determinis-
tic. Sections 2.1 and 2.2 present a brief overview of
individual type of schemes.
1.2 Paper Organization
Observing the significant advantages of deterministic
KPS during key management for low cost distributed
networks, we set out to propose one such scheme. Our
proposal uses net partial spreads (or, nets) in a finite
vector space that have been well studied combinato-
rially and as such, we name the scheme as sensornet.
After a brief literature survey on KPS in Section 2, we
present preliminaries of combinatorial set systems in
KPS, partial spreads and nets in Section 3. Section 4
presents the design of our scheme sensornet that ad-
here to the desirable criteria set out in Section 2.4.
We analyze sensornet in terms of various performance
metrics set out in Section 5 and thereby establish our
scheme’s efficiency in comparison to prominent pro-
posals. We briefly summarize our work in Section 6
while stating related future research directions.
2 A BRIEF SURVEY OF KPS
This section presents a state-of-the art survey of
prominent KPS. We split survey into three stage:
(i) first generation random KPS, (ii) deterministic
KPS, and (iii) advantages of later type over former.
Thereby, we justify proposal of our new deterministic
KPS adhering to design criteria set out in Section 2.4.
2.1 Random Key Predistribution
Schemes (RKPS)
First generation KPS rely on random graph theory
pioneered by Erd
˝
os and R
´
enyi (Erd
˝
os and R
´
enyi,
1960) to preload (symmetric) cryptographic keys into
sensors. Therefore, keyrings are formed randomly.
This leads to probabilistic key sharing and establish-
ment. Later is achieved by either broadcast of key ids
or challenge and response Refer to (Eschenauer and
Gligor, 2002, Section 2.1). Earlier, Blom proposed
the first key distribution scheme (Blom, 1985) in pub-
lic key settings meant for resourceful ad hoc net-
works. Blom’s schemes uses pairs of public-private
matrices for key distribution. It cannot be applied to
resource constraint sensor networks due to its heavy
memory requirement to store huge vectors. Several
researchers use variants of Blom’s schemes to pro-
pose both random and deterministic KPS for DSN.
C¸ amptepe and Yener (C¸ amtepe and Yener, 2005) pro-
vides an excellent survey of the random KPS.
2.2 Deterministic Key Predistribution
Schemes (DKPS)
First deterministic KPS were proposed simultaneous
by C¸ amtepe and Yener (C¸ amtepe and Yener, 2004),
Lee and Stinson (Lee and Stinson, 2005) and Wei
and Wu (Wei and Wu, 2004) in 2004. Wei and Wu
(Wei and Wu, 2004) combines subset-based schemes
with existing key distribution schemes such as (Blom,
1985) to obtain multiple key spaces. C¸ amtepe and
Yener (C¸ amtepe and Yener, 2004) exploits combi-
natorial designs like symmetric Balanced Incomplete
Block Designs (BIBD), generalized quadrangles and
SENSORNETS 2017 - 6th International Conference on Sensor Networks
50

projective planes (see (Lee and Stinson, 2005; Lee
and Stinson, 2008; Paterson and Stinson, 2014)). The
scheme of Lee and Stinson (Lee and Stinson, 2005)
uses quadratic equation solving and can be viewed
as a scalable extension of their later proposal us-
ing Transversal Design (T D(k, p)). This work fur-
ther summarizes the necessary conditions for a com-
binatorial design to yield a deterministic KPS. Cer-
tain KPS exploit special structures like Reed Solomon
code based KPS (Ruj and Roy, 2008) that permit alter-
nate combinatorial description (Bag et al., 2012; Pa-
terson and Stinson, 2014). In the same light, we show
our scheme derived from the net of partial spreads (or
nets) can yield nice combinatorial properties meant
for designing deterministic KPS.
2.3 Advantages of DKPS over RKPS
Deterministic schemes have certain advantages over
their random counterparts. For instance, a desired
property of a randomized scheme may occur only
with a certain probability whereas they can be proven
to hold in a deterministic scheme (refer to (Lee and
Stinson, 2005; Lee and Stinson, 2008; Paterson and
Stinson, 2014)). This led to proposals of numer-
ous deterministic KPS (Lee and Stinson, 2005; Lee
and Stinson, 2008; Bag et al., 2012) etc. using vari-
ous combinatorial tricks. Further the predictable na-
ture of these combinatorial structures has been effi-
ciently exploited to address design weaknesses of cer-
tain prominent KPS. For instance (Dhar and Sarkar,
2011; Bag et al., 2012) primarily address the connec-
tivity aspect of (Ruj and Roy, 2008) by deterministic
and random approaches respectively.
Contrary to these observations, Ruj and Pal (Ruj
and Pal, 2016) state that random graph models are
well suited for ‘scalability’ and ‘resilience’. Thereby,
they justify their proposals of random graph based
preferential attachment models with degree bounds.
They design various network using their model. All
of their designs suffers from highly skewed load dis-
tribution, poor connectivity and resiliency; and hence,
are inappropriate for (distributed) IoT applications.
In fact, sensitive IoT applications require proto-
cols to yield equal distribution of tasks among peers.
Moreover, to reduce hops and hence potential risks
from node capture, it is more important to have con-
nected networks that can not be guaranteed by ran-
dom schemes. So we opt for deterministic protocols
for security applications in IoT networks that assure
predictable (high) connectivity; despite most of them
having restricted scaling operations. This is a major
area of study for most (deterministic) KPS proposals,
including ours (recalled in Section 6).
Observe that the structure of the combinatorial ob-
jects used to design deterministic KPS can not di-
rectly model networks of any specified size N . Usu-
ally, such structures result in designs having a specific
pattern in the number of resultant blocks; viz. a prime
power etc. Since N can be any number, a standard
strategy is to consider the least prime power that is
greater than the network size (i.e., p
r
≥ N ). Then N
subset are randomly selected to form the key rings of
the resultant network nodes. Bose et al. (Bose et al.,
2013) speculate that random removal of blocks may
have a disadvantageous affect on the underlying de-
sign properties and hence become an issue of concern.
Fortunately, this claim of Bose et al. has been suc-
cessfully challenged by Henry et al. (Henry et al.,
2014). Through practical experiments, they establish
that random removal of key rings of a combinatorial
KPS has negligible effect with overwhelming proba-
bility. This work reestablishes the importance of com-
binatorial schemes.
2.4 Desirable Design Criteria
Devices of an IoT (for instance, sensors of a DSN) are
highly prone to damage and/or physical capture. This
is a crucial consideration while designing any KPS.
Primary objectives of any KPS is to ensure that the
resulting network:
1. has less number of keys per node, i.e., sizes of
individual keyrings are less;
2. have large node support, i.e., support large num-
ber of network nodes;
3. has good (ideally full secure) connectivity. Secure
connectivity (or, simply connectivity) is the ratio
of number of (secure) links in eventual network to
all possible links. A pair of nodes are said to be
connected by a (secure) link if there exists at least
one secret key between them;
4. is resilient against adversarial attacks. A pre-
vailing method adopted in most existing works
(C¸ amtepe and Yener, 2004; Lee and Stinson,
2005; Bag et al., 2012; Paterson and Stinson,
2014) is to show that the standard resiliency co-
efficient fail(t) is minimized. Our work will fol-
low suit. The quantifier fail(t) measures the ra-
tio of links broken after compromise of t sensors
to the total number of links in the remaining net-
work. Notationally, fail(t) =
b
t
u
t
, where b
t
is the
number of links broken when t nodes are compro-
mised and u
t
is the total number of links among
uncompromised nodes of remaining network.
Sensornet - A Key Predistribution Scheme for Distributed Sensors using Nets
51

Ideally a KPS should have small keyrings, and
yet support large number of nodes with appreciable
resiliency, scalability and communication probabil-
ity (or connectivity). However, renowned scientists
proved the impossibility of constructing a perfect KPS
that meets all these criteria (Lee and Stinson, 2005;
Paterson and Stinson, 2014). This motivates several
designs that are robust for specific purpose.
3 PRELIMINARY
This section introduces the definitions and notations
that are required to describe our scheme; sensornet.
3.1 Combinatorial Set Systems and KPS
Use of different combinatorial designs to obtain de-
terministic KPS was primarily presented in the pa-
per (Lee and Stinson, 2005). After that there have
been several KPS proposals based on combinatorial
designs. A survey on KPS in WSN is available
in (Chen and Chao, 2011). Recently in a more tech-
nical survey, Paterson and Stinson (Paterson and Stin-
son, 2014) present an unified treatment of prominent
combinatorial designs in terms of partially balanced
t−design. Basic design theoretic concepts are below:
Let X be a finite set. The elements of X are called
varieties. Each subset of X is termed as a block. Con-
sider A to be a collection of blocks of X . Then the
pair (X ,A) is said to be a set system or, a design.
(X ,A) is regular (of degree r ) if each point is con-
tained in r blocks. (X ,A) is uniform (of rank k) if all
blocks have the same size, say k.
A design (X ,A) is said to form a (v, b,r,k)−design if
• |X | = v and |A| = b;
• it is regular of degree r and uniform of rank k.
A (v, b,r,k)−design forms a (v,b, r, k)−configuration
if any arbitrary pair of blocks intersect in at most
one point. Moreover, if any pairs of varieties occur
in exactly λ block, then a (v,b,r, k)−design forms a
(v, b,r, k, λ)−BIBD (Balanced Incomplete Block De-
signs). These designs can be used to construct various
KPS(see (Lee and Stinson, 2005)) by mapping:
1. the v varieties of X to the set of keys in the scheme
(:=key pool),
2. b to the number of nodes in the system (:=network
size),
3. k to the number of keys per node (:=size of key
rings), and
4. r to the number of nodes sharing a key (:=degree
of the resultant KPS).
The target is to construct KPS with identical burden
on each sensor. This leads to opting for design with
uniform rank (k) and regular degree (r); so that every
key ring is of equal size (k) and same number of nodes
(r) share each key for the resultant network.
The block graph Γ
A
of the set design (X ,A) is de-
fined with the vertex set A and edge set E
A
= {(A,B) :
A,B ∈ A and A∩B 6=
/
0}. If the set design is regular of
degree r and uniform of rank k, then the block graph
Γ
A
is k(r −1)−regular.
A (v,b,r,k)−configuration (X ,A) is said to form
a µ−common intersection design (µ−CID) in case:
|{A
α
∈ A : A
i
∩ A
α
6=
/
0 and A
j
∩ A
α
6=
/
0}| ≥ µ
whenever A
i
∩ A
j
=
/
0, ∀ i 6= j. It is important to con-
struct design that maximize the value of µ.
3.2 Partial Spread and Net
Let IF
p
be the finite field on p elements where p is a
prime. Denote V
n
= IF
n
p
to be the vector space over the
field IF
p
with zero vector 0. Since the finite field IF
p
n
is a vector space over IF
p
which is isomorphic to IF
n
p
(see (Lidl and Niederreiter, 1997)), we interchange
the notation as per its suitability. The isomorphism
mapping can be considered as any mapping from a
basis set of IF
p
n
(e.g., {1,α,· ·· ,α
n−1
} where α is a
primitive root in IF
n
p
) to a basis set of IF
n
p
. We consider
n = 2m to be an even integer throughout the paper.
A partial spread Σ of order s in V
n
is a set
of pairwise supplementary m−dimensional subspaces
E
1
,E
2
,·· · ,E
s
of V
n
i.e., E
i
∩ E
j
= {0} for all 1 ≤ i <
j ≤ s. A partial spread Σ is a spread if ∪
s
i=1
E
i
= V
n
.
It is well known that a spread of V
n
exists since m
divides n (Lu, 2008); in which case |Σ| = p
m
+ 1.
Therefore, from a given spread Σ each of the
p
m
+1
s
choices of s members of Σ provides a partial spread
of V
n
. Note that a partial spread might not be a sub-
set of a spread (Eisfeld and Storme, 2000). A de-
tailed combinatorial study of spread can be found in
the book (Johnson, 2010; Johnson et al., 2007).
Let E be a subspace of the vector space V
n
. A
coset of E in V
n
is of the form α+E = {α+v : v ∈V
n
}
for an α ∈ V
n
. The set of cosets make a disjoint par-
tition of V
n
. The element α is called a coset rep-
resentative of the coset α + E. Since E is an ad-
ditive group, any element from the α + E can be a
coset representative the coset. Given a partial spread
Σ = {E
1
,E
2
,·· · ,E
s
} in V
n
, let E
i
be a set of coset rep-
resentatives of subspace E
i
for 1 ≤ i ≤ s. Then the
set A = {α + E
i
: α ∈ E
i
and 1 ≤ i ≤ s} i.e., set of all
cosets of subspaces E
i
,1 ≤ i ≤ s is called a net in V
n
.
See the book (Johnson et al., 2007) for the combina-
torial study of net.
SENSORNETS 2017 - 6th International Conference on Sensor Networks
52

4 SENSORNET
Sensornet is a proposal for a KPS for distributed
(wireless) sensors. The design of sensornet results
from the forthcoming set design and Theorem 1.
Given a partial spread Σ = {E
1
,E
2
,·· · ,E
s
} in V
n
,
let E
i
be a supplementary subspace of E
i
in V
n
for
1 ≤ i ≤ s (i.e., their direct sum E
i
⊕ E
i
= V
n
and
E
i
∩ E
i
= {0}). It can be checked that E
i
is a set of
coset representatives of E
i
for 1 ≤ i ≤ s. Note that the
subspaces E
i
’s in a partial spread are pairwise supple-
mentary. So, any E
j
, j 6= i can be chosen as E
i
. Con-
sider the set system (X , A) such that X = V
n
and and
the set of blocks A = {α + E
i
: α ∈ E
i
and 1 ≤ i ≤ s}
which is a net in V
n
.
Theorem 1. Given any partial spread Σ, the set de-
sign (X , A) is a µ(p
n
,sp
m
,s, p
m
)−CID where µ =
(s − 1)p
m
.
Proof. Here v = |X | = p
n
. Consider two blocks α +
E
i
and β + E
j
. Now we have the following cases.
1. If i = j, then
(a) α + E
i
= β + E
j
if α = β or,
(b) (α + E
i
) ∩ (β + E
j
) =
/
0 if α 6= β.
2. If i 6= j, then we shall show that |(α + E
i
) ∩ (β +
E
j
)| = 1. Since E
i
and E
j
are supplementary to
each other, the element α−β ∈V
n
can be uniquely
expressed as -u+ v where u ∈ E
i
and v ∈ E
j
. That
is, α−β = −u + v which implies, α +u = β + v is
the unique element in (α + E
i
) ∩ (β + E
j
).
Therefore, the number of blocks i.e., the number of
cosets is b = sp
m
and each block contains k = p
m
el-
ements. Given a subspace E
i
,i ∈ {1,2,· ·· , s}, each
element u ∈ V
n
belongs to exactly one coset of E
i
.
So, each u ∈ V
n
belongs to exactly s many blocks
in A. The set design (X ,A) is regular with r = s.
Here, every two distinct blocks intersect each other
by at most one element which implies that (X ,A) is a
(p
n
,sp
m
,s, p
m
)−configuration.
We see that two blocks α+E
i
and β+E
j
do not in-
tersect iff i = j and α 6= β i.e., both are distinct cosets
of same subspace E
i
. For the case of non intersecting
blocks α + E
i
and β + E
i
, α 6= β, both blocks inter-
sect all other blocks of the form γ + E
j
where j 6= i.
Since there are µ = (s−1)p
m
such blocks γ +E
j
in A,
(X ,A) is a (s − 1)p
m
(p
n
,sp
m
,s, p
m
)−CID.
Here, the set of blocks (i.e., A) of the scheme
(X ,A) forms a net in a vector space. We denote the
scheme as sensornet.
It can be checked that the block graph of (X ,A)
is a strongly regular graph with parameters (n =
sp
m
,r = (s − 1)p
m
,λ = (s − 2)p
m
,µ = (s − 1)p
m
).
Moreover, the block graph is a complete s−partite
graph. In the study of finite geometry, the varieties
together with the blocks (i.e., cosets) form the points
and lines of an affine plane. Since two non-parallel
lines (i.e., α + E
i
and β + E
j
for i 6= j) intersects at
one point, this set of cosets is called net.
4.1 Example of NETS
There are numerous constructions of spreads and par-
tial spreads that can be found in literature, see (John-
son et al., 2007). Now we present a few spreads S
in IF
n
p
, where p is a prime. For a given s, any Σ ⊆ S
such that |Σ| = s forms a partial spread of order s. By
Theorem 1, this partial spread yields a KPS.
Spread I: This is a classical example of a spread
from the additive group of the finite field F
p
n
. Since
n = 2m, IF
p
m
is a subspace of IF
p
n
with respect to a
basis. Let {α
i
: 1 ≤ i ≤ p
m
+ 1} be a set of coset rep-
resentative of the cosets of the subgroup IF
∗
p
m
of the
multiplicative group IF
∗
p
n
. Then the set S
I
= {S
i
=
α
i
IF
p
m
,1 ≤ i ≤ p
m
+ 1} is a spread in IF
p
n
.
Spread II: This example of spread is represented in
bivariate form (Bu, 1980). For each α ∈ IF
p
m
, define a
subspace U
α
of IF
p
m
×IF
p
m
by U
α
= {(αu,u)|u ∈ IF
m
p
}
and U
∞
= {(u,0)|u ∈ IF
m
p
}. The set S
II
= {U
α
: α ∈
IF
p
m
} ∪U
∞
constitute a spread in IF
p
m
× IF
p
m
' IF
p
n
.
Spread III: This example of spread is generated from
pre-quasifield, which is defined as following. A sys-
tem Q = (V, +,◦), with |V | finite, is a pre-quasifield
if the following axioms hold:
(1) (V, +) is an abelian group, with identity 0.
(2) (V
∗
,◦) is a quasigroup where V
∗
= V \ {0}. That
is, for any a ∈ V
∗
, the left multiplication operator
a ◦ x and the right multiplication operator x ◦ a are
both bijective from V
∗
to V
∗
.
(3) ∀x,y,z ∈ V : (x + y) ◦ z = x ◦ z + y ◦ z.
(4) x ◦ 0 = 0, ∀x ∈ V .
Now assuming (IF
p
m
,+,◦) is a pre-quasifield, set
E
a
= {(x,a ◦ x) : x ∈ IF
p
m
} for any a ∈ IF
p
m
and E
∞
=
{(0,x) : x ∈ IF
p
m
}. Then it can be checked that S
III
=
{E
a
: a ∈ IF
p
m
∪{∞}} is a spread in IF
p
m
×IF
p
m
(John-
son et al., 2007). Many pre-quasifields are available in
literature. Refer to (Wu, 2013) for three types of pre-
quasifields on set IF
2
m
and (C¸ es¸melio
˘
glu et al., 2015)
for a pre-quasifield on set IF
p
m
.
Example 1. Here, we present a simple KPS from the
spread of type S
I
. Take V
n
= IF
3
2
= IF
3
[x]/(x
2
+ 1).
Consider the subspace IF
3
= {0,1,2} and {1, x,x +
1,x + 2} a set of coset representatives of IF
∗
3
in
IF
3
2
. Then S
I
= {{0,1,2},{0, x,2x},{0,x + 1,2x +
2},{0,x + 2, 2x + 1}} is a spread in IF
2
3
. Consider
Sensornet - A Key Predistribution Scheme for Distributed Sensors using Nets
53

a partial spread Σ = {E
1
= {0,1,2}, E
2
= {0,x, 2x}}
with E
1
= E
2
and E
2
= E
1
. Therefore, by Theorem 1,
the set X = IF
2
3
and the net A = {{0,1, 2},{x, x +
1,x +2},{2x,2x +1,2x +2},{0, x,2x},{1,x +1,2x +
1},{2,x + 2,2x + 2}} forms a KPS (X ,A). The block
graph of (X , A) is the K
3,3
.
5 ANALYSIS OF SENSORNET
In this section we present the values of some impor-
tant metrics involved in our proposed scheme; sensor-
net.
5.1 Time and Space Complexities for
Key Establishment (T
k
,M
k
)
For the key establishment between two nodes, the
nodes need to discover a common key stored between
them. For this purpose the nodes need to broadcast
some data, which is required to trace the common
key between two nodes. Since the sensor nodes have
low memory and computation power, data and time
requirement for key establishment are two very im-
portant factors to design a KPS. In this subsection
we discuss the process of key establishment between
two nodes and associated time and data requirement
of the process. In case of path key establishment (re-
fer to Section 1.1, both the concerned nodes have to
find a common neighbor node with whom they dis-
cover their share key and establish connection via this
neighbor. Let denote T
k
and M
k
be the time and mem-
ory complexity function for the key establishment in
vector space V
n
.
The blocks of sensornet forms a net, i.e., they are
affine spaces. Hence, the nodes can be identified by
their basis vectors and the key establishment is done
using the node id. Let β
1
i
,β
2
i
,·· · ,β
m
i
be a basis set of
the subspace E
i
for 1 ≤ i ≤ s. Then, the node α + E
i
can be identified by the node id (α,β
1
i
,β
2
i
,·· · ,β
m
i
).
When the nodes α + E
i
and β + E
j
need key estab-
lishment between them the following process can be
followed.
Step 1: The nodes α + E
i
and β + E
j
compare the
last m vectors (i.e., the basis vectors) in their node
id. If they are same then follow Step 3 otherwise
follow Step 2.
Step 2: In this case, we have E
i
6= E
j
i.e., they
share a common key. Let the common key is
α + u = β + v where u ∈ E
i
and v ∈ E
j
. Now we
need to find u and v in terms of the basis vectors of
E
i
and E
j
respectively. Here, α − β = v − u ∈ V
n
.
Since E
i
and E
j
are supplementary subspaces in
V
n
, α − β can be uniquely expressed as a linear
combination of the basis vectors of E
i
and E
j
. Let
α−β = b
1
β
1
i
+·· ·+ b
m
β
m
i
+b
m+1
β
1
j
+·· ·+ b
n
β
m
j
,
where b
i
∈ IF
p
. That is, α − b
1
β
1
i
− · ·· − b
m
β
m
i
=
β + b
m+1
β
1
j
+ · ·· + b
n
β
m
j
. Hence, the common
key is α − b
1
β
1
i
− ··· − b
m
β
m
i
∈ E
i
which is β +
b
m+1
β
1
j
+ · ·· + b
n
β
m
j
∈ E
j
. The time complexity
in this step is the time complexity to express α −β
in terms of the basis vectors in a basis i.e., O(n
3
).
Step 3: In this case, the E
i
= E
j
i.e., they do not
share any common key. In this case, they have e
to establish connection through another node with
whom they share a key. That is, they have to find a
node γ + E
k
where k 6= i. The probability of find-
ing such a node using a random pick up is
s−1
s
which is very high. Since both α + E
i
and β + E
j
share a key with γ+E
k
, each one do the same pro-
cess described in Step 2 with γ + E
k
to discover
their common key. After that α + E
i
and β + E
j
can establish connection through γ + E
k
. Hence,
the time complexity in this case is too O(n
3
).
Therefore, each node has to spend M
k
= (m + 1) ∗ n ∗
log
2
p = O(n
2
) bits of data for broadcasting of their
identification and the time complexity to discover the
common key(s) is T
k
= O(n
3
). Note that in sensor-
net scheme, nodes have to broadcast only node id i.e.,
O(n
2
) bits instead of all (i.e., O(rp
n
2
) many) key ids
as broadcast by many other proposed schemes.
5.2 Key-node Ratio (σ)
The key-node ratio is defined as σ =
k
b
. This ratio
provides idea about the storage requirement of the
scheme at each node with respect to the total num-
ber of nodes. With this metric we can compare the
storage requirement of the schemes from different de-
signs. It is desirable for this ratio σ to be as small as
possible as lesser amount of memory required for key
storage at each node. In sensornet (X ,A), key-node
ratio σ =
p
m
sp
m
=
1
s
=
1
|Σ|
. If the size of partial spread
is larger, then the storage requirement to store keys in
sensornet is lesser.
5.3 Resiliency(fail(t))
The schemes need to be well equipped to perform
against adversarial attacks. To this end, the standard
resiliency metric fail(t) need to be minimized. This
is prevalent method adopted by most existing works
(Bag et al., 2012; C¸ amtepe and Yener, 2004; Lee and
Stinson, 2004; Lee and Stinson, 2005; Paterson and
Stinson, 2014). The quantifier fail(t) measures the
SENSORNETS 2017 - 6th International Conference on Sensor Networks
54

probability that a random link between two sensor
nodes is broken due to the compromise of t other ran-
dom nodes. Notationally, fail(t) =
b
t
u
t
, where b
t
is
the number of links broken when t nodes are compro-
mised and u
t
is the total number of links among un-
compromised nodes of remaining network. Theorem
2 is due to Lee and Stinson (Lee and Stinson, 2005,
Section VIII) provides the formula to compute fail(t)
for any (v,b,r,k,1)−configuration.
Theorem 2. For any (v,b, r,k,1)−configuration, the
value of the metric fail(t) on random compromise of
t nodes is given by:
fail(t) = 1 −
b − r
b − 2
t
. (1)
Corollaries 1 is an immediate outcomes of substi-
tuting in Equation 1, the values of b and r, that sen-
sornet achieves.
Corollary 1. The value of the resilience fail(t) for
the set design (X ,A) of the scheme sensornet, which
is a (p
n
,sp
m
,s, p
m
)−configuration is
fail(t) = 1 −
sp
m
− s
sp
m
− 2
t
.
In particular,
fail(1) =
s − 2
sp
m
− 2
=
1
p
m
−
2p
m
− 2
p
m
(sp
m
− 2)
≈ p
−m
.
The metric fail(1) = O(p
−m
) i.e., if a node N is
compromised, then the probability that a link (which
is not incident with N) fails is O(p
−m
). Here, the size
of the partial spread (i.e., s) has no significant effect
on fail(1). As an example, if n = 10 and p = 2 (i.e.,
there are 2
10
≈ 1000 many nodes) then the value of
fail(1) ≈ 0.03.
5.4 Connectivity(p
e
)
We say two blocks in a set system are connected by
e−links (or, are at a distance e) if the shortest path
between them in the block graph includes e edges.
Hence, we define the metric connectivity (or, connec-
tion probability) p
e
of the network to be the probabil-
ity that two nodes (placed in physical neighborhood)
are connected by e−links for a positive integer e.
Observe that the value of e for a µ−CID with µ > 1
is either 1 (if they share a key) or 2 (if they do not
share a key). The formulae for p
1
and p
2
are pro-
vided in (Lee and Stinson, 2005, Section VI), which
are being formally restated in the following theorem.
Let η denote the number of nodes in the intersection
of the physical neighborhood of two given nodes.
Theorem 3. The value of the metric connectivities of
a µ(v, b,r, k)−CID are given by p
1
=
k(r−1)
b−1
and p
2
≈
(1 − p
1
) ×
1 −
b−µ−2
b−2
η
.
The following corollary is an immediate outcome
for our scheme by substituting the values of b, r,k and
λ in Theorem 3.
Corollary 2. The value of the metric connectivities
for the set system (X ,A), which is a (s − 1)p
m
−
(p
n
,sp
m
,s, p
m
)−CID are
p
1
≈ 1 −
1
s
and p
2
≈
s
η
− 1
s
η+1
.
Proof. Now putting the value of b = sp
m
,r = s,k =
p
m
and µ = (s − 1)p
m
in p
1
and p
2
, we have
p
1
=
p
m
(s − 1)
sp
m
− 1
=
sp
m
− p
m
sp
m
− 1
= 1 −
p
m
− 1
sp
m
− 1
≈ 1 −
1
s
and p
2
≈
1
s
1 −
sp
m
− (s − 1)p
m
− 2
sp
m
− 2
η
=
1
s
1 −
p
m
− 2
sp
m
− 2
η
≈
1
s
1 −
1
s
η
=
s
η
− 1
s
η+1
.
The metric p
1
≈ 1 −
1
s
i.e., the connectivity in-
creases if the size of spread increases. Here, the size
of base field (i.e., the value of p) has no significant
effect on p
1
. As an example, if n = 10, p = 2 (i.e.,
there are 2
10
≈ 1000 many nodes) and s = 2
5
then the
value of p
1
= 1 − 2
−5
.
5.5 Comparative Study
This subsection presents a comparative study of sen-
sornet with prominent existing works with respect to
connectivity, resilience and network scaling. Perfor-
mance of sensornet with respect to other metric like
storage, etc. has been discussed in previous section.
5.5.1 Connectivity and Resiliency Tradeoff
The schemes with high connectivity (i.e., p
1
) and re-
siliency (i.e., fail(1)) as small as possible are pre-
ferred. As unfortunately, both the metrics behave in
opposite way, it is a fundamental problem of trading
off connectivity against resiliency. In (Dong et al.,
2011; Paterson and Stinson, 2014), the ratio ρ =
p
1
fail(1)
is considered for the comparison of several
combinatorial designs. Therefore, the larger value
of ρ confirms of higher connectivity and lower re-
siliency. It is desirable that the ratio ρ be as large as
possible.
Sensornet - A Key Predistribution Scheme for Distributed Sensors using Nets
55
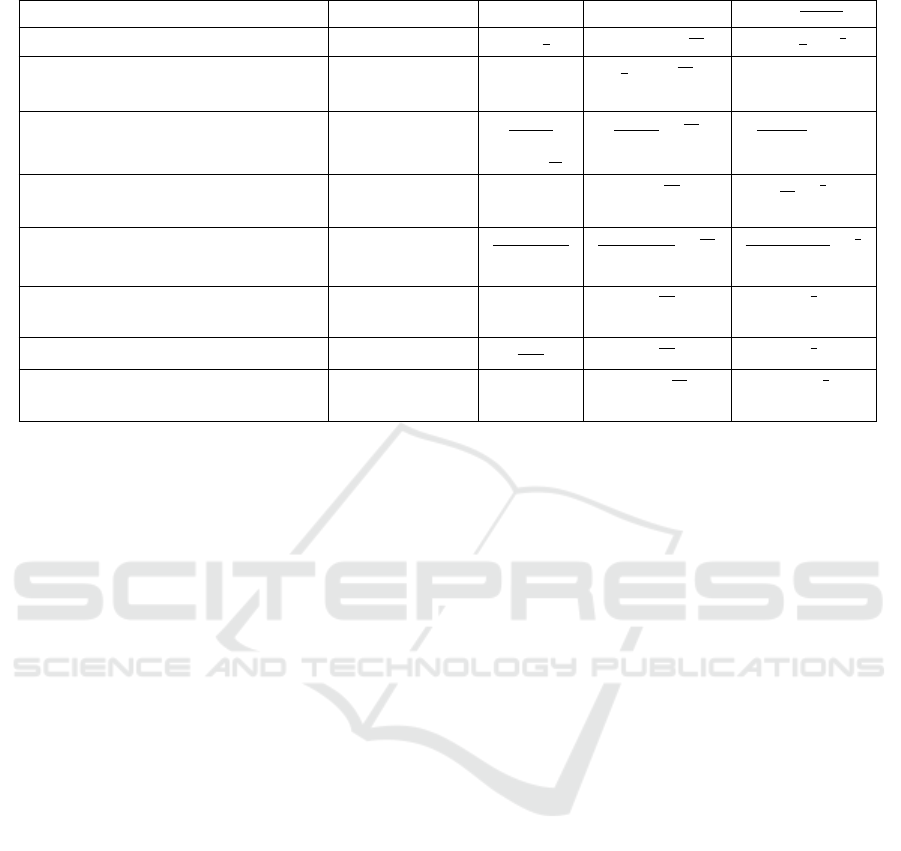
Table 1: Comparison of asymptotic behavior of different schemes.
Scheme No. of nodes p
1
fail(1) ρ =
p
1
fail(1)
(X ,A) (sensornet) N = sp
m
1 −
1
s
p
−m
= N
−1
2
(1 −
1
s
)N
1
2
T D(2,k,q), k = cq N = q
2
c
1
q
= N
−1
2
cN
1/2
(Paterson and Stinson, 2014)
T D(3,k,q), k = cq,c < 1 N = q
3
c(2−c)
2
2(1−c)
(2−c)
N
−1
3
c(2−c)
2
4(1−c)
N
1/3
(Paterson and Stinson, 2014) = c −
c
2
2
T D(3,k,q),k = q N = q
3
1/2 5N
−2
3
1
10
N
2
3
(Paterson and Stinson, 2014)
T D(4,k,q),k = cq N = q
4
c(c
2
−3c+6)
6
3(c
2
−2c+2)
c
2
−3c+6
N
−1
4
c(c
2
−3c+6)
2
18(c
2
−2c+2)
N
1
4
(Paterson and Stinson, 2014)
Symmetric BIBD N = q
2
+ q + 1 1 N
−1
2
N
1
2
(C¸ amtepe and Yener, 2004)
RS code based (Ruj and Roy, 2008) N = q
2
q−1
q+1
N
−1
2
N
1
2
MB designs for T D(2kq) or N = q
2
/2 1 (2N )
−1
2
(2N )
1
2
RS code (Bag et al., 2012)
There have been several proposals for determin-
istic key predistribution schemes for wireless sen-
sor networks based on various types of combinatorial
structures such as designs and codes. The paper (Pa-
terson and Stinson, 2014) proposes a general frame-
work by unifying those structures into a new design,
termed as “partially balanced t-designs(PBtD)”. Al-
though, our scheme sensornet falls into 2 − (v, k, λ
0
=
b,λ
1
= r)−PBtD as a configuration, the generaliza-
tion does not consider µ−CIDs. Hence, being a
µ−CID, sensornet does not classify as PBtD by their
description (Paterson and Stinson, 2014). There are
few comparison tables of different schemes are pro-
vided in (Paterson and Stinson, 2014). In the fol-
lowing, we take data of TD(t,k, Q) with intersection
threshold η = 1 from the paper (Paterson and Stin-
son, 2014) along with other designs to compare with
the scheme sensornet.
Let consider the number of nodes in all the com-
pared scheme is N . Now we shall compare the
asymptotic behavior of metrics p
1
,fail(1) and the ra-
tio ρ. The comparison is displayed in Table 1.
From this comparison table it is clear that the
asymptotic behavior of the ratio ρ of sensornet (X , A)
is similar or better than all other schemes except the
scheme T D(3, k,q),k = q and Merging Block (MB)
design of (Bag et al., 2012). Former scheme needs
computation of some number theoretic problems dur-
ing key agreement; while the later has significantly
less (merging) block support (halved). Moreover, in
our scheme (X ,A), the shared key discovery is done
with time complexity O((log
p
N )
3
) and the amount
of data need to be broadcast is O((log
p
N )
2
). This is
an added advantage over most KPS that require key
id comparisons during key discovery.
5.5.2 Scalability Comparison
Sensornet (X , A) can support large networks. This is
because the choice n and respectively m and/or s are
unbounded in theory. This may help in scaling net-
works designed by our schemes (prefix large values).
Scalability, otherwise is a major challenge in
most deterministic KPS. For instance the schemes
(C¸ amtepe and Yener, 2004; Lee and Stinson, 2004;
Lee and Stinson, 2005; Lee and Stinson, 2008; Ruj
and Roy, 2008) have restricted scaling. This owes
to the fact that key establishment for these network
require general solutions of polynomials. Therefore
the complexity of the key establishment process in-
creases with increment in degree of these polynomi-
als. Random schemes can scalable arbitrarily (Ruj
and Pal, 2016); at the expense of desirable parameters
like connectivity, resilience, storage (key-node ratio),
etc. Therefore we opt deterministic schemes while de-
signing KPS (Paterson and Stinson, 2014). Also refer
to Section 2.3.
6 CONCLUSION
Realizing the need of deterministic KPS with desir-
able properties (set out in Section 2.4) to address the
problem of key management in low cost networks,
we propose one such scheme. Since the scheme is
constructed using nets in a vector space, we named
as sensornet. Key establishment of sensornet is a
SENSORNETS 2017 - 6th International Conference on Sensor Networks
56

great advantage over many other schemes. Although
sensornet suffers from lack of full connectivity, it is
very close to full connectivity for large size of par-
tial spread. Moreover, the generic computations in
Section 5.4 establish that connectivity of sensornet is
good (either direct or 1−hop path connectivity), it is
preferable to have full connectivity or at least a de-
terministic path in case of 1−hop connectivity. The
sophisticated MB designs of (Bag et al., 2012; Dhar
and Sarkar, 2011) establishes a deterministic 1−hop
connectivity for the Reed Solomon code based KPS
(Ruj and Roy, 2008). These heavily design dependent
works can certainly open the doors for future research
by considering similar constructions over sensornet in
place of other combinatorial design based schemes.
REFERENCES
Bag, S., Dhar, A., and Sarkar, P. (2012). 100% connectivity
for location aware code based kpd in clustered wsn:
Merging blocks. In Information Security Conference,
ISC 2012, number 7483 in Lecture Notes in Computer
Science, pages 136–150. Springer-Verlag.
Blom, R. (1985). An optimal class of symmetric key gener-
ation systems. In Advances in Cryptology - Eurocrypt
1984, number 209 in Lecture Notes in Computer Sci-
ence, pages 335–338. Springer-Verlag.
Bose, M., Dey, A., and Mukerjee, R. (2013). Key pre-
distribution schemes for distributed sensor networks
via block designs. Design, Codes and Cryptography,
67(1):111–136.
Bu, T. (1980). Partitions of a vector space. Discrete Math-
ematics, 31:79–83.
C¸ amtepe, S. A. and Yener, B. (2004). Combinatorial design
of key distribution mechanisms for wireless sensor
networks. In 9th European Symposium on Research
Computer Security, ESORICS 2004, number 3193 in
Lecture Notes in Computer Science, pages 293–308.
Springer-Verlag.
C¸ amtepe, S. A. and Yener, B. (2005). Key distribution
mechanisms for wireless sensor networks: a sur-
vey. Technical report, Rensselaer Polytechnic In-
stitute. Available at www.cs.rpi.edu/research/pdf/05-
07.pdf.
C¸ es¸melio
˘
glu, A., Meidl, W., and Pott, A. (2015). Bent func-
tions, spreads, and o-polynomials. SIAM Journal of
Discrete Mathematics, 29(2):854–867.
Chen, C. Y. and Chao, H. C. (2011). A survey of key pre-
distribution in wireless sensor networks. Security and
Communication Networks, 7(12).
Dhar, A. and Sarkar, P. (2011). Full communication in a
wireless sensor network by merging blocks of a key
predistribution using reed solomon code. In Proceed-
ings of CCSEA 2011, CS & IT 02, pages 389–400.
Dong, J. W., Pei, D. Y., and Wang, X. L. (2011). A class
of key predistribution schemes based on orthogonal
arrays. Journal of Computer Science and Technology,
23:825–831.
Eisfeld, J. and Storme, L. (2000). (partial) t-spreads and
minimal t-covers in finite projective spaces. In Lec-
ture notes for the Socrates Intensive Course on Finite
Geometry and its Applications, University of Ghent.
Erd
˝
os, P. and R
´
enyi, A. (1960). On the evolution of random
graphs. Publication of the Mathematical Institute of
the Hungarian Academy of Sciences.
Eschenauer, L. and Gligor, V. (2002). A key-management
scheme for distributed sensor networks. In Proceed-
ings of 9th ACM conference on computer and commu-
nications security, pages 41–47. ACM press.
Henry, K. J., Paterson, M. B., and Stinson, D. R. (2014).
Practical approaches to varying network size in com-
binatorial key predistribution schemes. In Selected
Areas in Cryptography (SAC) 2013, number 8282 in
Lecture Notes in Computer Science, pages 89–117.
Springer-Verlag.
Johnson, N. L. (2010). Combinatorics of Spreads and Par-
allelisms. CRC Press.
Johnson, N. L., Jha, V., and Biliotti, M. (2007). Handbook
of Finite Translation Planes, volume 289 of Pure and
Applied Mathematics. Chapman & Hall/CRC.
Lee, J. and Stinson, D. R. (2004). Deterministic key pre-
distribution schemes for distributed sensor networks.
In Selected Areas in Cryptography (SAC) 2004, num-
ber 3357 in Lecture Notes in Computer Science, pages
294–307. Springer-Verlag.
Lee, J. and Stinson, D. R. (2005). A combinatorial approach
to key predistribution for distributed sensor networks.
In IEEE Wireless Communications and Networking
Conference, WCNC-2005, pages 1200–1205.
Lee, J. and Stinson, D. R. (2008). On the construc-
tion of practical key predistribution schemes for dis-
tributed sensor networks using combinatorial designs.
ACM Transactions on Information and System Secu-
rity, 11(2):854–867.
Lidl, R. and Niederreiter, H. (1997). Finite fields. Ency-
clopaedia of mathematics and its applications. Cam-
bridge University Press.
Lu, H. Y. (2008). Partial spreads and hyperbent functions
in odd characteristic. Master’s thesis, Simon Fraser
University.
Paterson, M. B. and Stinson, D. R. (2014). A unified ap-
proach to combinatorial key predistribution schemes
for sensor networks. Design, Codes and Cryptogra-
phy, 71(3):433–457.
Ruj, S. and Pal, A. (2016). Preferential attachment model
with degree bound and its application to key predistri-
bution in WSN. In IEEE Conference on Advanced In-
formation Networking and Applications, AINA 2016,
pages 677–683.
Ruj, S. and Roy, B. K. (2008). Key predistribution schemes
using codes in wireless sensor networks. In Informa-
tion Security and Cryptology, Inscrypt 2008, number
5487 in Lecture Notes in Computer Science, pages
275–288. Springer-Verlag.
Wei, R. and Wu, J. (2004). Product construction of key
distribution schemes for sensor networks. In Selected
Sensornet - A Key Predistribution Scheme for Distributed Sensors using Nets
57

Areas in Cryptography (SAC) 2004, number 3357 in
Lecture Notes in Computer Science, pages 280–293.
Springer-Verlag.
Wu, B. (2013). Ps bent functions constructed from fi-
nite pre-quasifield spreads. Available at http://arxiv.
org/pdf/1308.3355.pdf.
SENSORNETS 2017 - 6th International Conference on Sensor Networks
58
