
Key Encapsulation Mechanism in Ciphertext-policy Attribute based
Setting Featuring Revocation and Key-homomorphic Property
Anushree Belel, Ratna Dutta and Sourav Mukhopadhyay
Indian Institute of Technology Kharagpur, Kharagpur, 721302, India
Keywords:
Attribute-based Key Encapsulation, Revocation, Key-homomorphism.
Abstract:
Cloud computing is a paradigm shift from traditional computing to process, store and share data in an untrusted
environment with emerging applications in medical fields, online data storage, social network, big data analysis
and online learning platforms. As more and more organizations, business platforms, individuals are choosing
cloud, it is very urgent to ensure data security and privacy in the cloud. To safeguard data breaches, it is
important to provide fine-grained access control on encrypted data in the cloud. Ciphertext-policy attribute
based encryption (CP-ABE) is a promising advanced cryptographic primitive that monitors fine-grained access
control of sensitive data in untrusted cloud environment. The revocable CP-ABE (RCP-ABE) is an extension
of CP-ABE which facilitates direct user revocation from the system. In this work, we introduce a refined
encapsulated version of RCP-ABE, called key-homomorphic revocable ciphertext-policy attribute based key
encapsulation mechanism (RCP-ABKEM). Interesting features of this primitive is that it supports extended
correctness and key-homomorphism along with normal correctness requirement. Our work is inspired by the
work of Sun et al. (PKC 2020) who introduced the notion of key-homomorphic identity based revocable key
encapsulation mechanism (IRKEM). We generalize the notion of key-homomorphic IRKEM in attribute based
setting and provide an instantiation of key-homomorphic RCP-ABKEM. We support the conjectured security of
our candidate by analysis and prove that the scheme achieves selective security against chosen plaintext attack
(CPA) under the q-decisional bilinear Diffie-Hellman exponent (q-DBDHE) assumption in the standard model.
More interestingly, when contrasted with existing similar scheme, our scheme exhibits better performance over
the existing similar schemes in terms of communication overhead and master secret key size and is the first
scheme in attribute setting that preserves key homomorphic property. As a refined primitive, key-homomorphic
RCP-ABKEM is of independent interest and may be utilized as a building block for generic construction of new
cryptographic primitive.
1 INTRODUCTION
Identity based encryption (IBE) is an appealing alter-
native to public key encryption (PKE) that removes
the requirement of public key infrastructure (PKI) by
using user’s identity like email or IP address as pub-
lic key. Since the first proposal of IBE by Boneh
and Franklin (Boneh and Franklin, 2001), several new
advanced cryptographic encryption techniques have
been studied extensively by research community in-
cluding hierarchical IBE, attribute based encryption
(ABE), predicate encryption (PE), functional encryp-
tion (FE), inner product encryption (IPE) and so on.
ABE is a promising cryptographic primitive to fix the
issue of fine-grained access control on encrypted data
in one-to-many communications. Ciphertext policy
ABE (CP-ABE) has huge applications in the context of
cloud security, health-record access control, network
privacy, data security on mobile devices, Internet of
Things (IoT) and many more.
Designing efficient and practical revocation tech-
niques in ABE has been considered to be very impor-
tant because no organization wants its revoked users
to be able to decrypt the data. In general, there are two
mechanisms to revoke users in ABE − indirect revoca-
tion (Boldyreva et al., 2008) ; (Sahai et al., 2012) and
direct revocation (Attrapadung and Imai, 2009); (Liu
and Wong, 2015). In indirect revocation approach,
an authority periodically updates the secret key only
for non-revoked users to enable them to decrypt the
encrypted data whereas the revoked users are not al-
lowed to update their secret key. As a consequence,
the revoked users fail to decrypt newly generated ci-
phertext. However, one shortcoming of this approach
Belel, A., Dutta, R. and Mukhopadhyay, S.
Key Encapsulation Mechanism in Ciphertext-policy Attribute based Setting Featuring Revocation and Key-homomorphic Property.
DOI: 10.5220/0011271600003283
In Proceedings of the 19th International Conference on Security and Cryptography (SECRYPT 2022), pages 349-356
ISBN: 978-989-758-590-6; ISSN: 2184-7711
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All r ights reserved
349

is that it cannot realize instant user revocation. On the
contrary, direct revocation lets a public revocation list
to be specified during encryption so that the ciphertext
can be decrypted only by the users not in the revoca-
tion list and whose attributes satisfy the access policy
− thus facilitating instant user revocation. Balu and
Kuppusamy (Balu and Kuppusamy, 2013) proposed a
revocable CP-ABE using direct revocation technique
from the hardness of the decisional bilinear Diffie-
Hellman (DBDH) problem. Wang et al. (Wang et al.,
2017) provided a construction of revocable CP-ABE
using identity-based revocation from the modified de-
cisional q-parallel bilinear Diffie-Hellman exponent
(M-q-parallel BDHE) assumption. Liu et al. (Liu
et al., 2018) proposed a revocable CP-ABE based on
direct revocation approach from the q-decisional bi-
linear Diffie-Hellman exponent (q-DBDHE) assump-
tion employing a secret key time validation technique
to resolve the issue of growth of the revocation list.
Liu et al. (Liu et al., 2020) constructed a revoca-
ble CP-ABE with ciphertext update from M-q-parallel
BDHE problem.
Very recently in 2020, Sun et al. (Sun et al., 2020)
proposed an encapsulated version of revocable iden-
tity based broadcast encryption (IBBE) called key-
homomorphic identity based revocable key encapsu-
lation mechanism (IRKEM) that satisfies extended cor-
rectness and key-homomorphism apart from the nor-
mal correctness requirement. Their revocation mech-
anism can be seen as direct revocation in the sense
that their approach enables the sender to perform
revocation by providing a list of revoked users di-
rectly in the ciphertext. This approach does not re-
quire any key update procedure and therefore very
convenient for regular use. Precisely, they came up
with four modular and compact constructions of key-
homomorphic IRKEM based on the q-decisional bi-
linear Diffie-Hellman exponent (q-DBDHE) problem,
the decisional bilinear Diffie-Hellman (DBDH) prob-
lem, the q-decisional multi-exponent bilinear Diffie-
Hellman (q-MEBDH) problem and the decisional lin-
ear (DLIN) problem in the standard security model.
Merging key-homomorphic IRKEM with the idea of
distributed key-distribution, they also provided a
generic construction of puncturable key encapsula-
tion mechanism (PKEM) to achieve fine-grained re-
vocation of decryption capability. To support un-
bounded punctures, their main idea is to generate a
share of the encapsulated key on-the-fly and to re-
cover this key from all shares for successful decryp-
tion. Key-homomorphism property is required for dis-
tributing the encapsulated key and extended correct-
ness is crucial to compute shares of the encapsulated
key.
Our Contribution. There has been a natural trend
in research community to extend any advanced
cryptographic primitive from identity based to more
flexible and practical attribute based framework.
In this paper, we introduce a refined version of
revocable ciphertext policy attribute based key
encapsulation mechanism (RCP-ABKEM) motivated
by key-homomorphic IRKEM of Sun et al. (Sun
et al., 2020). We define extended correctness and
key-homomorphism in attribute based setting. The
new primitive with these additional properties can
be plugged into various privacy preserving proto-
cols. However, this realization is non-trivial. The
challenge lies in the requirement of introducing the
additional properties in an RCP-ABKEM. We provide
an instantiation of RCP-ABKEM which is proven to
be selectively secure against chosen plaintext attack
(CPA). The underlying hardness of our construction is
q-DBDHE problem and security proof of our scheme
is in the standard model. Our design differs from
the work of Liu et al. (Liu et al., 2018) in the sense
that we do not consider secret key time validation
technique. Our security model allows an adversary
to ask secret key of a user whose identity is in the
revocation list or whose attribute set does not satisfy
the challenge access structure. We briefly summarize
the comparison of communication banwidth, storage
and other functionality of our scheme in reference
to the existing work of Balu and Kuppusamy (Balu
and Kuppusamy, 2013) and Wang et al. (Wang et al.,
2017) in Table 1. Similar to the work of (Balu and
Kuppusamy, 2013) and (Wang et al., 2017), we use
symmetric bilinear pairing e : G × G → G
1
where G,
G
1
are cyclic groups of prime order p. We emphasize
that the master secret key size (|msk|) of our scheme
is less than those in (Balu and Kuppusamy, 2013)
and (Wang et al., 2017). Moreover, our ciphertext
size is significantly shorter than those in (Balu and
Kuppusamy, 2013) and (Wang et al., 2017). The
ciphertext size in our construction is (l +2)|G| which
does not depend on number of revoked users r while
that of (Balu and Kuppusamy, 2013), (Wang et al.,
2017) are respectively (1 + 2r + l)|G|, (1 + 2lr)|G|
which grows as the number of revoked user grows.
Here l is number of attributes present in the ac-
cess structure Γ = (N,η). Our public key size is
|pk| = (n
rev
+ n
att
+ 2)|G| + |G
1
| which includes
public parameter size |pp| = (n
rev
+ n
att
+ 2)|G| and
master public key size |mpk| = |G
1
| where (n
rev
− 1)
denotes maximum number of revoked users in the
system and n
att
is the cardinality of the attribute space
associated with system. However, size of public key
(|pk|) and secret key |sk| are more in our design as
compared to that of (Balu and Kuppusamy, 2013) and
SECRYPT 2022 - 19th International Conference on Security and Cryptography
350
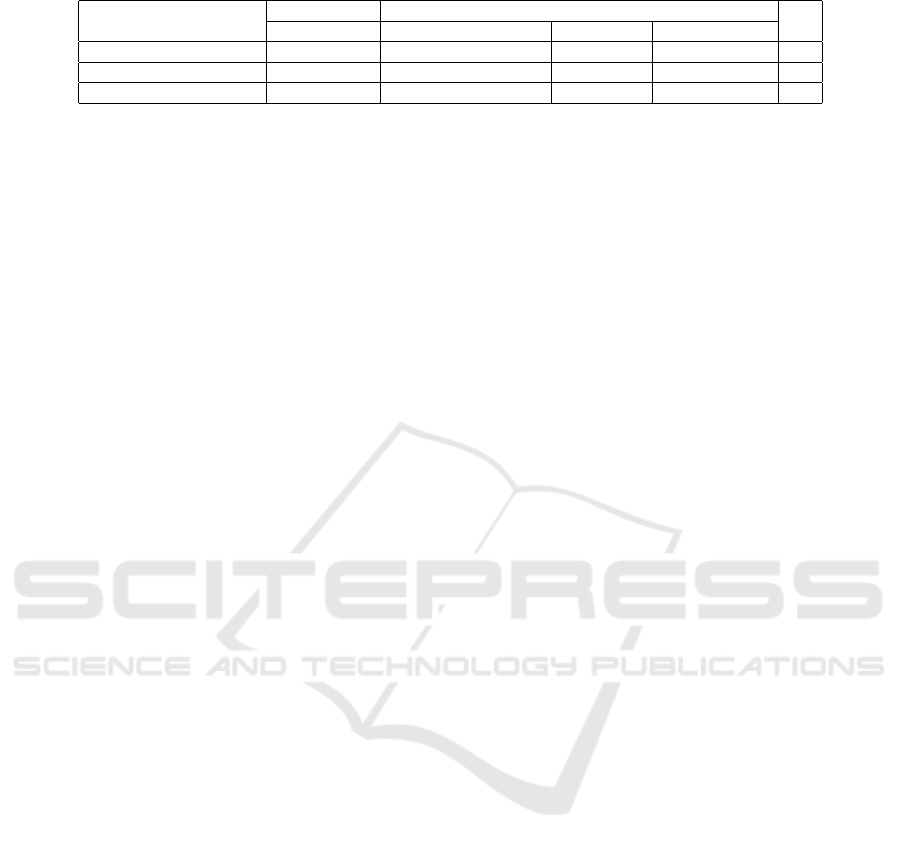
Table 1: Comparison of communication bandwidth, storage overhead and key-homomorphic property.
Scheme Communication Storage KH
|ct| |pk| |msk| |sk|
(Balu and Kuppusamy, 2013) (1 + 2r + l)|G| (n
att
+ 2)|G| + |G
1
| (n
att
+ 2)|Z
p
| (|S| +3)|G| No
(Wang et al., 2017) (1 + 2lr)|G| (n
att
+ 3)|G| + |G
1
| 2|Z
p
| (|S| +2)|G| No
Our (l + 2)|G| (n
rev
+ n
att
+ 2)|G| + |G
1
| |Z
p
| (n
rev
+ |S|+ 2)|G| Yes
|ct| = ciphertext size, |pk| = public key size, |msk| = master secret key size, |sk| = secret key size of a user with identity id and attribute set S, KH = Key-
homomorphic, HA = hardness assumption, |G| = bit size of an element of G, |G
1
| = bit size of an element of G
1
, l = number of attributes present in the access
structure, r = number of revoked users specified at encryption phase, n
att
= the cardinality of the attribute space AS associated with system, (n
rev
−1) = maximum
number of revoked users in our system
(Wang et al., 2017). With this tradeoff, we achieve
the first revocable encapsulation scheme preserving
key-homomorphic property in attribute based setting.
A Sample Application. RCP-ABKEM with key-
homomorphism property and extended correctness
can enable numerous powerful cryptographic appli-
cation. For instance, we can extend the notion of
PKEM in attribute based setting and employ the key-
homomorphism and extended correctness of RCP-
ABKEM to puncture a set of attributes using tag based
approach following (Sun et al., 2020). Precisely, this
variant of PKEM in attribute based setting consists of
a tuple (KeyGen, Puncture, Encaps, Decaps). A user
Alice runs the algorithm KeyGen to generate public
key PK and secret key SK. She publishes PK and
keeps SK secret to herself. Alice runs the algorithm
Puncture taking input a tag t which is an attribute set,
secret key SK
i−1
where SK
0
= SK and generates a
new secret key SK
i
. An encryptor executes Encaps
on input public key PK and a list of tags T consist-
ing of access structures to generate encapsulated key
K and ciphertext CT. On input secret key SK
i
, ci-
phertext CT along with tag list T , Alice performs the
algorithm Decaps to recover the encapsulated key K.
The correctness requirement is that SK
i
can decap-
sulate all the ciphertexts decapsulated by SK
i−1
ex-
cept for those encrypted under tag t. In other words,
for any l times of invoking SK
i
← Punc(SK
i−1
,t)
such that t does not satisfy any of the access struc-
tures in T, decapsulation will be successful with over-
whelming probability on input SK
l
,CT,T . For ex-
ample, consider a scenario where Alice has applied
for mail subscription to a group of companies for
job updates where each company owns a set of at-
tributes. Suppose it has been exposed that “companies
which are private and foreign” sends malware to re-
cipients. For safety, Alice can ultilize Puncture on tag
S ={“foreign”, “private”} to generate a new secret key
so that using key-homomorphism and extended cor-
rectness, she can decapsulate only those ciphertexts
CT with associated tag list T such that S does not
satisfy any of the access structures in the tag list T .
Again if there is any threat regarding tag S
′
= {“sports
medicine”,“multinational”}, she can again Puncture
on tag S
′
so that she can decapsulate only those ci-
phertexts CT with associated tag list T such that S, S
′
satisfy none of the access structures in the tag list T .
2 PRELIMINARIES
2.1 Notation
Let λ denotes the security parameter. By x
u
←− S we
mean that x is chosen uniformly from the set S. Let
∅ stands for the empty set and [n] represents the set
{1,2,.. . ,n} for any n ∈ N. We say f : N → R is a
negligible function of n if it is O(n
−c
) for all c > 0
and we use negl(n) for negligible function of n. Let
the symbol ⊥ indicates failure or null value, P (A)
denotes the power set of a set A and ⟨·, ·⟩ represents
inner product of two vectors.
2.2 Access Structure
Let P = {P
1
,P
2
,... , P
n
} be a set of parties. A collec-
tion Γ ⊆ P (P ) is monotone if for any sets B,C satis-
fying B ∈ Γ, B ⊆ C ⊆ P , we have C ∈ Γ. A monotone
access structure on P is a monotone collection Γ of
non-empty subsets of P , that is Γ ⊆ P(P ) \ ∅. The
sets in Γ are called the authorized sets and the sets in
P(P ) \ Γ are called the unauthorized sets. We say
that a set S satisfies the access structure Γ if S is an
authorized set i.e. S ∈ Γ. Unless otherwise stated,
by an access structure we indicate monotone access
structure throughout this paper.
2.3 Linear Secret Sharing Scheme
A secret sharing scheme Λ over a set of parties P is
called linear over Z
p
if
1. The shares of each party form a vector over Z
p
.
2. There is a matrix N having l rows and d columns
called the share generating matrix for Λ and a
Key Encapsulation Mechanism in Ciphertext-policy Attribute based Setting Featuring Revocation and Key-homomorphic Property
351

function η that associates each row of the matrix
N to a corresponding party. For i ∈ [l], the i-th
row N
i
of N is labeled by a party η(i) where η is
a function from [l] to P . Given the column vector
v = (s,z
2
,... , z
d
) where s is the secret to be shared
and z
2
,z
3
,... , z
d
are chosen uniformly at random,
Nv is the vector of l shares of the secret s accord-
ing to Λ. The share λ
i
= (Nv)
i
= ⟨N
i
,v⟩ belongs
to party η(i).
As exhibited by Beimel et al. (Beimel et al., 1996),
any linear secret sharing scheme (LSSS) satisfies the
linear reconstruction property stated in the following
Theorem:
Theorem 1. Let Λ = (N,η) be an LSSS for access
structure Γ and S ∈ Γ be an authorized set. Let I ⊂ [l]
be defined as I = {i : η(i) ∈ S}. Then there exists con-
stants {w
i
∈ Z
p
}
i∈I
satisfying
∑
i∈I
w
i
N
i
= (1, 0,..., 0)
so that when λ
i
are valid shares of a secret s ac-
cording to Λ,
∑
i∈I
w
i
λ
i
= s. Moreover, these constants
{w
i
∈ Z
p
}
i∈I
can be computed in time polynomial in
the size of the share generating matrix N.
2.4 Revocable Ciphertext-policy
Attribute-based Key Encapsulation
Mechanism with Key-homomorphic
Property
In this section, we recall the syntax and security of
revocable ciphertext-policy attribute based key en-
capsulation mechanism (RCP-ABKEM) from (Liu and
Wong, 2015) and introduce a new concept − key-
homomorphic property in RCP-ABKEM. An RCP-
ABKEM scheme with master public key space M P K ,
master secret key space M SK , secret key space SK ,
encapsulated key space EK , identity space I D, at-
tribute space AS and randomness spaces R S,R S
′
consists of a tuple of polynomial time algorithms
RCP-ABKEM=(Setup, MKGen, KeyExt, Encaps, De-
caps) satisfying the following requirements.
• Setup(1
λ
,n
att
,n
rev
) → pp : A trusted authority
runs this probabilistic algorithm on input the se-
curity parameter λ, number of attributes n
att
∈ N,
an integer n
rev
∈ N and generates public parame-
ter pp. Here (n
rev
−1) is the maximum number of
revoked users is in the system.
• MKGen(pp)→ (mpk,msk) : The trusted authority
takes input the public parameter pp and proba-
bilistically outputs a master public key mpk ∈
M P K and a master secret key msk ∈ M S K . It
publishes mpk and keeps msk secret to itself.
• KeyExt(pp, msk, id, S ; τ)→ sk
id,S
: On input the
public parameter pp, a user identity id ∈ I D with
attribute set S ⊆ AS, the trusted authority chooses
randomness τ
u
←− R S
′
and runs this algorithm to
generate a private key sk
id,S
∈ S K using the mas-
ter secret key msk. It issues sk
id,S
to the iden-
tity holder id with attribute set S through a secure
channel between them.
• Encaps(pp,mpk, R ,Γ;{r
i
}
i∈[n]
) → (k,ct,R ,Γ) :
An encapsulator takes as input the public parame-
ter pp, the master public key mpk, a list R ⊆ I D
of revoked users identity with |R | < n
rev
, an ac-
cess structure Γ over the attribute space AS and
probabilistically outputs a symmetric key k and a
ciphertext ct. It publishes ct along with descrip-
tion of R ,Γ and keeps k secret to itself. Here
r
i
∈ R S for i ∈ [n] are randomness used in the
algorithm where n is a positive integer.
• Decaps(pp,sk
id,S
,ct,R ,Γ) → k/ ⊥: On input the
public parameter pp, a private key sk
id,S
for an
identity id with attribute set S and a ciphertext ct
associated with the revocation list R and access
structure Γ over the attribute space AS, a decap-
sulator recovers the encapsulated key k or ⊥.
Correctness. For correctness, we require that
any user with private key sk
id,S
for id /∈ R ,S ∈
Γ can retrieve the encapsulated key k. More for-
mally, an RCP-ABKEM scheme is said to be cor-
rect if for all λ, n
att
,n
rev
∈ N, R ⊆ I D with
|R | < n
rev
, Γ ⊆ P(AS ) \ ∅ with |AS | = n
att
, pp
← Setup(1
λ
,n
att
,n
rev
), (mpk,msk) ← MKGen(pp),
(k, ct,R , Γ) ← Encaps(pp,mpk,R , Γ; {r
i
}
i∈[n]
) and
sk
id,S
← KeyExt(pp,msk,id,S;τ) for id /∈ R , S ∈ Γ, it
holds that
Pr[Decaps(pp,sk
id,S
,ct,R ,Γ) = k] ≥ 1 − negl(λ)
Security. We describe the selective security model
of RCP-ABKEM against chosen plaintext attack (CPA)
following the security model of Liu et al. (Liu and
Wong, 2015). The game played between an adversary
B and a challenger C is detailed below.
• Init: The adversary B submits the challenge revo-
cation list R
⋆
and the challenge access structure
Γ
⋆
to the challenger C .
• Setup: The challenger C generates pp ←
Setup(1
λ
,n
att
,n
rev
), (mpk,msk) ← MKGen(pp)
and provides pp, mpk to B.
• Query Phase 1: The adversary makes polynomi-
ally many private key queries. The challenger C
responds with sk
id,S
← KeyExt(pp, msk, id, S; τ)
to B corresponding to the query on the identity id
and the attribute set S if id ∈ R
⋆
or S /∈ Γ
⋆
.
SECRYPT 2022 - 19th International Conference on Security and Cryptography
352

• Challenge: The challenger C flips a ran-
dom coin b ∈ {0,1}, selects k
⋆
1
u
←− EK and
computes (k
⋆
0
,ct
⋆
,R
⋆
,Γ
⋆
) ← Encaps(pp, mpk,
R
⋆
,Γ
⋆
; {r
i
}
i∈[n
⋆
]
) where n
⋆
∈ N. The challenger
C sends (k
⋆
b
,ct
⋆
) to the adversary B.
• Query Phase 2: Same as phase 1.
• Guess: At the end, B outputs a guess bit b
′
and
wins the game if b
′
= b.
Advantage of B in this game is defined as:
Adv
CPA
RCP−ABKEM,B
(λ) =
Pr[b
′
= b] −
1
2
We say that an RCP-ABKEM scheme is CPA-secure if
Adv
CPA
RCP−ABKEM,B
(λ) ≤ negl(λ).
Extended Correctness. An RCP-ABKEM is said to
satisfy extended correctness if the following holds.
Let λ,n
att
,n
rev
∈ N, for i ∈ {1,2} let R
i
⊆ I D with
|R
i
| ≤ n
rev
, Γ
i
⊆ P (AS) \ ∅ with |AS | = n
att
, pp
← Setup(1
λ
,n
att
,n
rev
), (mpk
i
,msk
i
) ← MKGen(pp),
(k
i
,ct
i
,R
i
,Γ
i
) ← Encaps(pp,mpk
i
,R
i
,Γ
i
;{r
i j
}
j∈[n
i
]
)
where n
i
∈ N, {r
i j
}
j∈[n]
is a set of ran-
domness used in encapsulation algorithm,
sk
i
← KeyExt(pp,msk
i
,id
i
,S
i
;τ
i
), (
b
k,
b
ct,R
2
,Γ
2
) ←
Encaps(pp,mpk
1
, R
2
,Γ
2
;{r
2 j
}
j∈[n
2
]
). Then for
id
1
/∈ R
2
,S
1
∈ Γ
2
it holds that Pr[Decaps(pp,sk
1
=
sk
id
1
,S
1
,ct
2
,R
2
,Γ
2
) =
b
k] ≥ 1 − negl(λ).
Key-homomorphism. We let that the randomness
space R S
′
(associated with KeyExt), master secret
key space M SK , secret key space S K and encap-
sulated key space EK of an RCP-ABKEM scheme
form four groups (R S
′
,∗), (M SK , +), (SK ,⊗),
(EK ,⊙). Furthermore, we assume that the encap-
sulated key k is of the form f (msk,s) where s is one
of the randomness used in encapsulation algorithm.
Then the RCP-ABKEM scheme is said to satisfy
key-homomorphic property if extended correctness
holds and for all id ∈ I D, msk, msk
′
∈ M SK ,
τ,τ
′
∈ R S
′
the following two conditions hold.
1. KeyExt(pp, msk, id, S; τ) ⊗ KeyExt(pp,msk
′
, id,
S; τ
′
) = KeyExt(pp, msk + msk
′
, id, S; τ ∗ τ
′
).
2. f (msk,s) ⊙ f (msk
′
,s) = f (msk + msk
′
,s).
2.5 Symmetric Bilinear Map and
Hardness Assumption
Definition 2.5.1. (Symmetric Bilinear Map). Let
G,G
1
be multiplicative cyclic groups of prime order
p and Let g be a generator of G. A symmetric bilin-
ear mapping e : G × G → G
1
is a function having the
following properties.
1. e(u
a
,v
b
) = e(u,v)
ab
∀ u,v ∈ G and ∀a,b ∈ Z
p
.
2. The map is non degenerate, i.e., e(g,g) is a gener-
ator of G
1
.
The tuple (p, G, G
1
,e) is called a prime order
symmetric bilinear group system.
Definition 2.5.2. (q-Decisional Bilinear Diffie-
Hellman Exponent (DBDHE) Problem). Let G,G
1
be
cyclic groups of prime order p and e : G × G → G
1
be a symmetric bilinear pairing generated by a
bilinear group generator on input a security pa-
rameter λ. Let s,b
u
←− Z
p
, g be a random generator
of G, z
1
= (g,g
s
,g
b
,g
b
2
,... , g
b
q
,g
b
q+2
,... , g
b
2q
)
and z
2
∈ G
1
. Given (z
1
,z
2
), the q-DBDHE prob-
lem is to determine whether z
2
is e(g,g)
sb
q+1
or
a random element of G
1
. The advantage of a
distinguisher B is defined as Adv
q−DBDHE
B
(λ) =
|Pr[B(z
1
,e(g,g)
sb
q+1
) → 1]− Pr[B(z
1
,z
2
) → 1]|.
3 CONSTRUCTION OF
RCP-ABKEM FEATURING
KEY-HOMOMORPHIC
PROPERTY
Our construction of key-homomorphic revocable
ciphertext-policy attribute-based key encapsulation
mechanism RCP-ABKEM = (Setup, MKGen, KeyExt,
Encaps, Decaps) uses bilinear setup and has identity
space I D = Z
p
, master public key space M P K =
G
1
, master secret key space M S K = Z
p
, secret key
space SK = G
n
for some n ∈ N, randomness space
R S = Z
p
,R S
′
= Z
2
p
and encapsulated key space
EK = G
1
, where G, G
1
are two cyclic groups of
prime order p as defined in Def. 2.5.1 above. The
scheme is described below.
• Setup(1
λ
,n
att
,n
rev
) → pp : A trusted authority
takes as input the security parameter λ, two posi-
tive integers n
att
and n
rev
where n
att
is the number
of attributes, (n
rev
− 1) is the maximum number
of revoked users in the system. It generates a pair
of bilinear groups G, G
1
of prime order p > 2
λ
with bilinear pairing e : G × G → G
1
. It ran-
domly picks g, p
1
, p
2
,... , p
n
att
∈ G, γ
0
∈ Z
p
,γ =
(γ
1
,γ
2
,... , γ
n
rev
)
⊤
∈ Z
n
rev
p
, computes g
γ
0
,c
i
= g
γ
i
for i ∈ [n
rev
] and publishes
pp =
g,g
γ
0
,c
1
,c
2
,... , c
n
rev
, p
1
, p
2
,... , p
n
att
• MKGen(pp) → (mpk,msk) : On input the pub-
lic parameter pp, the trusted authority randomly
chooses α ∈ Z
p
, sets master secret key msk = α ∈
Z
p
and master public key mpk = e(g,g)
α
∈ G
1
. It
publishes mpk and keeps msk secret to itself.
Key Encapsulation Mechanism in Ciphertext-policy Attribute based Setting Featuring Revocation and Key-homomorphic Property
353

• KeyExt(pp, msk, id, S; τ = (u,a)) → sk
id,S
:
Taking input the public parameter pp, the mas-
ter secret key msk = α, attribute set S ⊆
AS of a user with identity id ∈ I D, the
trusted authority chooses (u, a) ∈ Z
2
p
at ran-
dom and computes sk
id,S
as sk
id,S
=
ψ
0
=
g
a
,ψ
′
0
= g
u
,ψ
1
= g
α
g
γ
0
a
g
γ
1
u
,{h
x
= p
a
x
}
x∈S
,{δ
i
=
(c
1
−id
i−1
c
i
)
u
}
n
rev
i=2
.
It issues the secret key sk
id,S
to the identity holder
id with attribute set S through a secure channel
between them.
• Encaps(pp,mpk, R ,Γ;{s, z
2
,... , z
d
}) →
(k, ct,R , Γ): Given the public parameter
pp =
g,g
γ
0
,c
1
,c
2
,... , c
n
rev
, p
1
, p
2
,... , p
n
att
,
master public key mpk = e(g,g)
α
, a revocation
list R = {id
1
,id
2
,... , id
r
} for some positive
integer r < n
rev
, an LSSS access structure
Γ = (N, η) where N is an l × d matrix over
Z
p
and η associates rows of N to attributes,
an encapsulator randomly chooses a vec-
tor v = (s,z
2
,... , z
d
) ∈ Z
d
p
, computes share
λ
i
= ⟨v, N
i
⟩ of s for i ∈ [l] where N
i
denotes the
i-th row of N and generates the encapsulated key
k and ciphertext ct = (C
′
0
,C
′′
0
,C
1
,C
2
,... ,C
l
) by
executing the following steps:
1. Defines a polynomial f
R
(Z) = (Z − id
1
)(Z −
id
2
)··· (Z − id
r
) = y
1
+ y
2
Z + ··· + y
r
Z
r−1
+
y
r+1
Z
r
and sets y
r+2
= y
r+3
= ... = y
n
rev
= 0
2. Calculates k = (e(g,g)
α
)
s
and sets
ct = (C
′
0
,C
′′
0
,C
1
,... ,C
l
) with C
′
0
=
g
s
,C
′′
0
= (
n
rev
∏
i=1
c
y
i
i
)
s
,C
1
= g
γ
0
λ
1
p
−s
η(1)
,... ,C
l
=
g
γ
0
λ
l
p
−s
η(l)
where mpk = e(g,g)
α
and
g,c
1
,c
2
,... , c
n
rev
,g
γ
0
, p
η(1)
, p
η(2)
,... , p
η(l)
are extracted from pp. Note that
{η(1),η(2),.. .,η(l)} ⊂ {1,2,. ..,n
att
}.
It publishes ct along with the description of R , Γ
and keeps k secret to itself.
• Decaps(pp,sk
id,S
,ct,R ,Γ) → k/ ⊥: On input the
public parameter pp, a private key sk
id,S
for an
identity id with attribute set S and a ciphertext ct
= (C
′
0
,C
′′
0
,C
1
,... ,C
l
) under the revocation list R
and access structure Γ = (N,η), a decapsulator
proceeds as follows:
1. Defines a vector x = (1,id,id
2
,... , id
n
rev
−1
)
from the identity id and a vector y =
(y
1
,y
2
,... , y
n
rev
) from the revoked list R =
{id
1
,id
2
,... , id
r
} where y
i
, i ∈ [r + 1], are co-
efficients of Z
i−1
in the polynomial f
R
(Z) =
r
∏
i=1
(Z − id
i
) =
r+1
∑
i=1
y
i
Z
i−1
and y
r+2
= y
r+3
=
... = y
n
rev
= 0 if r + 1 < n
rev
.
2. Returns ⊥ if either id ∈ R i.e. f
R
(id) = ⟨x,y⟩ =
0 or S does not satisfy the access structure Γ =
(N, η).
3. Otherwise, computes
C =
n
rev
∏
i=2
δ
y
i
i
and
κ
1
=
e(C,C
′
0
)
e(ψ
′
0
,C
′′
0
)
−1
⟨x,y⟩
by extracting ψ
′
0
and δ
i
, i = 2, . ..,n
rev
from
sk
id,S
and C
′
0
,C
′′
0
from ct.
4. Defines I = {i ∈ [l] : η(i) ∈ S} ⊂ [l], finds a set
of constants {w
i
∈ Z
p
}
i∈I
satisfying
∑
i∈I
w
i
λ
i
= s
where λ
i
= ⟨N
i
,v⟩ are valid shares of the secret
s according to Γ = (N,η), N
i
being the i-th row
of the matrix N, s being the secret randomness
picked to compute ct during encapsulation and
v = (s,z
2
,... , z
d
) ∈ Z
d
p
. Since S satisfies the ac-
cess structure Γ = (N,η), the set of constants
{w
i
∈ Z
p
}
i∈I
can be computed in polynomial
time by Theorem 1.
5. Computes
κ
2
=
∏
i∈I
e(C
i
,ψ
0
)e(C
′
0
,h
η(i)
)
w
i
and recovers
k =
e(ψ
1
,C
′
0
)
κ
1
κ
2
where ψ
0
, ψ
1
and h
η(i)
,i ∈ I are extracted from
sk
id,S
and C
′
0
,C
i
,i ∈ I are obtained from ct.
Table 2: Computation cost of our scheme.
Algorithm # exp # pair
Setup (n
rev
+ 1)|G| 0
MKGen |G
1
| 1
KeyExt (2n
rev
+ |S|+ 3)|G| 0
Encaps (n
rev
+ 2l +1)|G| +|G
1
| 0
Decaps (n
rev
− 1)|G| + |I||G
1
| (3 + 2|I|)
Correctness. The correctness follows as
C =
n
rev
∏
i=2
δ
y
i
i
=
n
rev
∏
i=2
c
1
−id
i−1
c
i
uy
i
=
c
1
−⟨x,y⟩+y
1
n
rev
∏
i=2
c
i
y
i
u
=
c
1
−⟨x,y⟩
n
rev
∏
i=1
c
i
y
i
u
SECRYPT 2022 - 19th International Conference on Security and Cryptography
354

κ
1
=
e(C,C
′
0
)
e(ψ
′
0
,C
′′
0
)
−1
⟨x,y⟩
=
e((c
1
−⟨x,y⟩
n
rev
∏
i=1
c
i
y
i
)
u
,g
s
)
e(g
u
,(
n
rev
∏
i=1
c
y
i
i
)
s
)
−1
⟨x,y⟩
=
e(c
1
−u⟨x,y⟩
,g
s
)e((
n
rev
∏
i=1
c
y
i
i
)
u
,g
s
)
e(g
u
,(
n
rev
∏
i=1
c
y
i
i
)
s
)
−1
⟨x,y⟩
=
e(c
1
−u⟨x,y⟩
,g
s
)
−1
⟨x,y⟩
= e(c
u
1
,g
s
) = e(g,g)
γ
1
su
κ
2
=
∏
i∈I
e(C
i
,ψ
0
)e(C
′
0
,h
η(i)
)
w
i
=
∏
i∈I
e(g
γ
0
λ
i
p
−s
η(i)
,g
a
)e(g
s
, p
a
η(i)
)
w
i
=
∏
i∈I
e(g,g)
γ
o
λ
i
a
e(p
η(i)
,g)
−sa
e(g, p
η(i)
)
sa
w
i
=
∏
i∈I
e(g,g)
γ
0
λ
i
aw
i
= e(g,g)
γ
0
a
∑
i∈I
w
i
λ
i
= e(g,g)
γ
0
as
Therefore,
k =
e(ψ
1
,C
′
0
)
κ
1
κ
2
=
e(g
α
g
γ
0
a
g
γ
1
u
,g
s
)
e(g,g)
γ
1
su
e(g,g)
γ
0
as
=
e(g
α
,g
s
)e(g
γ
0
a
,g
s
)e(g
γ
1
u
,g
s
)
e(g,g)
γ
1
su
e(g,g)
γ
0
as
= e(g,g)
αs
Extended Correctness. Let (mpk
0
,msk
0
) =
(e(g,g)
α
0
,α
0
) ← MKGen(pp) be another mas-
ter public and secret key pair and sk
id
0
,S
0
=
(ζ
0
= g
a
0
,ζ
′
0
= g
u
0
,ζ
1
= g
α
0
g
γ
0
a
0
g
γ
1
u
0
,{h
′
x
=
p
a
0
x
}
x∈S
0
,{δ
′
i
= (c
1
−id
i−1
0
c
i
)
u
0
}
n
rev
i=2
) generated by
running KeyExt(pp,msk
0
,id
0
,S
0
;τ
0
= (u
0
,a
0
))
be a secret key corresponding to the identity
id
0
∈ Z
p
with attribute set S
0
⊆ AS where
(u
0
,a
0
)
u
←− Z
2
p
. We observe that if id
0
/∈ R and
S
0
∈ Γ = (N,η) then Decaps(pp,sk
id
0
,S
0
, ct, R , Γ )=
b
k = e(g,g)
α
0
s
as follows where (
b
k,
b
ct,R , Γ) ←
Encaps(pp,mpk
0
,R , Γ; {s,z
2
,... , z
d
}) and
(k, ct,R , Γ) ← Encaps(pp, mpk, R ,Γ; {s,z
2
,... , z
d
}).
1. A decapsulator with secret key sk
id
0
,S
0
defines a
vector x
0
= (1, id
0
,id
2
0
,... , id
n
rev
−1
0
) from the iden-
tity id
0
and a vector y = (y
1
,y
2
,... , y
n
rev
) from
the revoked list R = {id
1
,id
2
,... , id
r
} where y
i
,
i ∈ [r + 1], are coefficients of Z
i−1
in the polyno-
mial f
R
(Z) =
r
∏
i=1
(Z −id
i
) =
r+1
∑
i=1
y
i
Z
i−1
and y
r+2
=
y
r+3
= . .. = y
n
rev
= 0 if r + 1 < n
rev
. As id
0
/∈ R ,
⟨x
0
,y⟩ ̸= 0. It computes
C
′
=
n
rev
∏
i=2
δ
′y
i
i
=
c
1
−⟨x
0
,y⟩
n
rev
∏
i=1
c
i
y
i
u
0
and
κ
′
1
=
e(C
′
,C
′
0
)
e(ζ
′
0
,C
′′
0
)
−1
⟨x
0
,y⟩
= e(g,g)
γ
1
su
0
similarly as described in the Correctness part .
2. It defines I
′
⊂ [l] such that I
′
= {i : η(i) ∈ S
0
},
finds a set of constants {w
′
i
∈ Z
p
}
i∈I
′
satisfying
∑
i∈I
′
w
′
i
λ
i
= s where λ
i
= ⟨N
i
,v⟩ are valid shares of
the secret s according to Γ = (N,η), N
i
being the
i-th row of the matrix N, s being the secret ran-
domness picked to compute ct during encapsula-
tion and v = (s,z
2
,... , z
d
) ∈ Z
d
p
. Since S
0
satisfies
the access structure Γ = (N,η), the set of con-
stants {w
′
i
∈ Z
p
}
i∈I
can be computed in polyno-
mial time by Theorem 1.
3. Computes
κ
′
2
=
∏
i∈I
′
e(C
i
,ζ
0
)e(C
′
0
,h
′
η(i)
)
w
′
i
= e(g,g)
γ
0
a
0
s
and recovers
e(ζ
1
,C
′
0
)
κ
′
1
κ
′
2
=
e(g
α
0
g
γ
0
a
0
g
γ
1
u
0
,g
s
)
e(g,g)
γ
1
su
0
e(g,g)
γ
0
a
0
s
= e(g,g)
α
0
s
in a similar way as described in the Correctness
part. Here ζ
0
, ζ
1
and h
′
η(i)
,i ∈ I
′
are extracted from
sk
id
0
,S
0
and C
′
0
,C
i
,i ∈ I
′
are obtained from ct.
Key-homomorphism. Note that each of (R S
′
,∗),
(M S K ,+), (S K ,⊗) and (E K ,⊙) in our scheme
RCP-ABKEM form a group where the operation ∗
on R S
′
is defined as τ ∗ τ
0
=(u + u
0
,a + a
0
) for τ =
(u,a) ∈ Z
2
p
and τ
0
= (u
0
,a
0
) ∈ Z
2
p
, the operation ⊗ on
SK = G
n
rev
+|S|+2
is defined as coordinate-wise mul-
tiplication over G, the operation ⊙ on EK = G
1
is
defined as multiplication over G
1
. The encapsulated
key in our scheme is k = f (msk, s)=e(g,g)
msk.s
where
s is one of the randomness used in encapsulation al-
gorithm. We also observe that for any identity id ∈ Z
p
with attribute set S ⊆ AS, master secret keys msk = α,
msk
0
= α
0
∈ Z
p
and randomness τ = (u,a) ∈ Z
2
p
,
τ
0
= (u
0
,a
0
) ∈ Z
2
p
, s ∈ Z
p
, the following holds.
Key Encapsulation Mechanism in Ciphertext-policy Attribute based Setting Featuring Revocation and Key-homomorphic Property
355

KeyExt
pp,msk = α, id,S;τ = (u,a)
⊗ KeyExt
pp,msk
0
= α
0
,id,S; τ
0
= (u
0
,a
0
)
=
g
a
,g
u
,g
α
g
γ
0
a
g
γ
1
u
,{p
a
x
}
x∈S
,{(c
1
−id
i−1
c
i
)
u
}
n
rev
i=2
⊗
g
a
0
,g
u
0
,g
α
0
g
γ
0
a
0
g
γ
1
u
0
,{p
a
0
x
}
x∈S
,{(c
1
−id
i−1
c
i
)
u
0
}
n
rev
i=2
=
g
a+a
0
, g
u+u
0
, g
α+α
0
g
γ
0
(a+a
0
)
g
γ
1
(u+u
0
)
, {p
a+a
0
x
}
x∈S
,
{(c
1
−id
i−1
c
i
)
u+u
0
}
n
rev
i=2
=KeyExt
pp,msk + msk
0
= α + α
0
,id,S; τ ∗ τ
0
= (u +
u
0
,a + a
0
)
and
f (msk = α,s) ⊙ f (msk
0
= α
0
,s)
= k ⊙
b
k
= e(g,g)
αs
⊙ e(g,g)
α
0
s
= e(g,g)
(α+α
0
)s
= f (msk + msk
0
= α + α
0
,s)
Besides, our scheme satisfies extended correctness as
shown above. Hence, it achieves key-homomorphic
property as defined in Section 2.4.
4 SECURITY ANALYSIS
Theorem 2. Assuming that q-Decisional Bilinear
Diffie-Hellman Exponent Problem (DBDHE) is hard,
no probabilistic polynomial time adversary can selec-
tively break the revocable ciphertext-policy attribute-
based key encapsulation mechanism (RCP-ABKEM)
decribed in section 3 with a challenge matrix of size
l
⋆
× d
⋆
where l
⋆
,d
⋆
≤ q, a challenge revocation list
R
⋆
where |R
⋆
| ≤ q − 2.
Proof. Due to page limit, the full proof will be ap-
peared in the full version of this paper.
5 CONCLUSIONS
In this work, we have designed a refined version of
RCP-ABKEM that satifies two additional properties
extended correctness and key-homomorphism. We
have provided an instantiation of this primitive from
the hardness of q-DBDHE problem. Moreover, our
scheme outperforms the existing similar schemes in
terms of master secret key and ciphertext size.
REFERENCES
Attrapadung, N. and Imai, H. (2009). Conjunctive broadcast
and attribute-based encryption. In International con-
ference on pairing-based cryptography, pages 248–
265. Springer.
Balu, A. and Kuppusamy, K. (2013). Ciphertext-policy
attribute-based encryption with user revocation sup-
port. In International Conference on Heterogeneous
Networking for Quality, Reliability, Security and Ro-
bustness, pages 696–705. Springer.
Beimel, A. et al. (1996). Secure schemes for secret sharing
and key distribution.
Boldyreva, A., Goyal, V., and Kumar, V. (2008). Identity-
based encryption with efficient revocation. In Pro-
ceedings of the 15th ACM conference on Computer
and communications security, pages 417–426.
Boneh, D. and Franklin, M. (2001). Identity-based encryp-
tion from the weil pairing. In Annual international
cryptology conference, pages 213–229. Springer.
Liu, J. K., Yuen, T. H., Zhang, P., and Liang, K.
(2018). Time-based direct revocable ciphertext-policy
attribute-based encryption with short revocation list.
In International Conference on Applied Cryptography
and Network Security, pages 516–534. Springer.
Liu, Z., Wang, F., Chen, K., and Tang, F. (2020). A new user
revocable ciphertext-policy attribute-based encryption
with ciphertext update. Security and Communication
Networks, 2020.
Liu, Z. and Wong, D. S. (2015). Practical ciphertext-policy
attribute-based encryption: traitor tracing, revocation,
and large universe. In International Conference on
Applied Cryptography and Network Security, pages
127–146. Springer.
Sahai, A., Seyalioglu, H., and Waters, B. (2012). Dynamic
credentials and ciphertext delegation for attribute-
based encryption. In Annual Cryptology Conference,
pages 199–217. Springer.
Sun, S., Sakzad, A., Steinfeld, R., Liu, J. K., and Gu, D.
(2020). Public-key puncturable encryption: Modular
and compact constructions. Public Key Cryptography
(1), 1210:309–308.
Wang, W., Wang, Z., Li, B., Dong, Q., and Huang, D.
(2017). Ir-cp-abe: Identity revocable ciphertext-policy
attribute-based encryption for flexible secure group-
based communication. IACR Cryptol. ePrint Arch.,
2017:1100.
SECRYPT 2022 - 19th International Conference on Security and Cryptography
356
