
FAPRIL: Towards Faster Privacy-preserving Fingerprint-based
Localization
Christopher van der Beets
1 a
, Raine Nieminen
2 b
and Thomas Schneider
2 c
1
Department of Computer Science, Darmstadt University of Applied Sciences, Germany
2
Department of Computer Science, Technical University of Darmstadt, Germany
Keywords:
Fingerprint-based Localization, Indoor Localization, Location Privacy, Data Privacy, Secure Two-party
Computation, Smartphones.
Abstract:
Fingerprinting is a commonly used technique to provide accurate localization for indoor areas, where global
navigation satellite systems, such as GPS and Galileo, cannot function or are not precise enough. Although
fingerprint-based indoor localization has gained wide popularity, existing solutions that preserve privacy either
rely on non-colluding servers or have high communication which hinder deployment.
In this work we present FAPRIL, a privacy-preserving indoor localization scheme, which takes advantage of the
latest secure two-party computation protocol improvements. We can split our scheme into two parts: an input
independent setup phase and an online phase. We concentrate on optimizing the online phase for mobile clients
who run on a mobile data plan and observe that recurring operands allow to optimize the total communication
overhead even further. Our observation can be generalized, e.g., to improve multiplication of Arithmetic secret
shared matrices. We implement FAPRIL on mobile devices and our benchmarks over a simulated LTE network
show that the online phase of a private localization takes under 0.15 seconds with less than 0.20 megabytes of
communication even for large buildings. The setup phase, which can be pre-computed, depends heavily on
the setting but stays in the range
0.28 − 4.14
seconds and
0.69 − 16.00
megabytes per localization query. The
round complexity of FAPRIL is constant for both phases.
1 INTRODUCTION
Localization is conventionally based on Global Nav-
igation Satellite Systems (
GNSS
s), such as GPS or
Galileo. However, the downside of
GNSS
s is their de-
creased accuracy when the satellite signals are blocked
by obstacles. This is particularly a problem for in-
door areas, such as shopping malls or airports. Hence
new techniques have been developed and deployed
specifically for Indoor Localization (
IL
), see (Lan-
glois et al., 2017; Yassin et al., 2017) for surveys.
The
IL
techniques are commonly based on using Wi-
Fi (Ladd et al., 2005; Haeberlen et al., 2004), cellu-
lar (Talvitie and Lohan, 2013), RFID (Chawla et al.,
2013), Bluetooth (Chen et al., 2011), or Zigbee (Noh
et al., 2008) signals. Localization using Wi-Fi signals
is particularly tempting for public buildings having
a Wi-Fi Access Point (
AP
) infrastructure already in
a
https://orcid.org/0000-0003-3276-6142
b
https://orcid.org/0000-0002-6667-3641
c
https://orcid.org/0000-0001-8090-1316
place. Besides this, the increase in the number of
smartphones and other mobile devices capable of mea-
suring Received Signal Strengths (
RSS
s) from Wi-Fi
AP
s makes it easy for people to use these techniques
without having to buy an extra device. In the future,
even cellular signals could become interesting source
of
RSS
s via dense 5G networks (Hakkarainen et al.,
2015), providing accurate localization for both indoors
and outdoors.
Relatively cheap and accurate
IL
has gained inter-
est from different Service Providers (
SP
s) resulting
in an increase in the number of Location-Based Ser-
vices (
LBS
s) developed for indoor areas such as muse-
ums, shopping malls, airports, exhibition centers, hos-
pitals, and university campuses (see, e.g., (Guan et al.,
2017; He et al., 2017)). The most interesting services
include indoor navigation, routing to a given destina-
tion, finding nearby friends, and targeted advertising
(see, e.g., (Alletto et al., 2015; Li et al., 2017)). The re-
cent study in (Barsocchi et al., 2021) also discusses the
potentials of using different
IL
technologies for mea-
suring the distance among the users and enhancing
108
van der Beets, C., Nieminen, R. and Schneider, T.
FAPRIL: Towards Faster Privacy-preserving Finger print-based Localization.
DOI: 10.5220/0011263500003283
In Proceedings of the 19th International Conference on Security and Cryptography (SECRYPT 2022), pages 108-120
ISBN: 978-989-758-590-6; ISSN: 2184-7711
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

social distancing effectively in indoor environments.
However, location information is highly privacy
sensitive and could be exploited to predict persons’
future movements and even identify them (Bellovin
et al., 2013). In addition,
SP
s might have to comply
with privacy laws and regulations, such as the EU Gen-
eral Data Protection Regulation (
GDPR
), forcing them
to use privacy-preserving solutions. The privacy as-
pects of
LBS
s are well studied (see, e.g., (Stirbys et al.,
2017; Hallgren et al., 2017; J
¨
arvinen et al., 2018)).
However, the studies mainly focus on how the location
information is handled in the service itself after the
client has already performed the actual localization. In
our paper, the focus is on the privacy concerns of the
actual location retrieval, which is a natural prerequisite
for privacy-preserving LBSs.
Whereas
GNSS
based localization is inherently
privacy-preserving (see (Chen et al., 2017; Lohan et al.,
2017a)), for
IL
techniques privacy is harder to achieve.
In our paper, we focus on fingerprint-based localiza-
tion, which is the most prominent
IL
technique used
with Wi-Fi
AP
s (see, e.g., (Capkun et al., 2011; Guan
et al., 2017; Yin et al., 2017)). Fingerprint-based lo-
calization relies on a pre-constructed database, which
contains so called fingerprints. Each fingerprint is ba-
sically a vector, where each element is a
RSS
value
from a different source such as a Wi-Fi
AP
. The fin-
gerprints are pre-measured around the building or area
at various known locations called reference points. In
the location retrieval step, the user measures its own
fingerprint, which is then compared to the fingerprints
in the database. In a typical scenario, the Service
Provider (
SP
) holds the database on a server that com-
pares with the user’s fingerprint. However, this leaks
the user’s location to the server, and thus to the SP.
A na
¨
ıve solution against leaking the user’s location
would be to send the whole database to the user’s de-
vice. This maintains privacy for the user, since now
the location retrieval includes only local computations.
However, it violates the privacy of the server and
SP
by
leaking the database content to the users, and thus re-
leasing the database practically to the public. The rea-
sons why the database should be kept secret from the
public are already discussed in several related works
(see §1.1). The database has high value, since con-
structing it is laborious manual work. In practice,
SP
s
still tend to have the power and control over the users
on what information is leaked. Since the database is ba-
sically the only valuable asset for the
SP
in fingerprint-
based localization and might even leak delicate details
of the building construction (e.g., suspiciously thick
or thin walls), we expect that the
SP
s tend to sacrifice
users’ privacy unless better solutions are available.
Privacy-Preserving Indoor Localization (
PPIL
)
tries to solve the privacy issues regarding both the
users’ location information and the database. However,
the previously proposed
PPIL
schemes suffer from
drawbacks such as low performance and high data
transfer rates, which discourage an actual
deployment.
1.1 Related Work
One of the earliest fingerprint-based
PPIL
scheme pro-
posals in the literature for the client-server setting with-
out using trusted third parties was PriWFL (Li et al.,
2014) presented in INFOCOM’14. The scheme uses
Paillier encryption (Paillier, 1999) to preserve clients’
privacy but tries to hide the database information with
an ad hoc masking technique, which was found later
insecure (Yang and J
¨
arvinen, 2018).
The authors of (Shu et al., 2014) proposed a
PPIL
scheme using Paillier encryption and Oblivi-
ous Transfer (
OT
). The scheme relies on other mo-
bile devices with known location, which is a major
drawback in practice. Additionally, computationally
heavy operations are performed on the client’s mo-
bile device, which leads to performance and battery-
power problems.
The authors of (Ziegeldorf et al., 2014) based their
PPIL
scheme on the Hidden Markov Model and use
Homomorphic Encryption (
HE
) for the computations.
The performance of their solution is poor, since the
location retrieval takes around 10 seconds even in a
relatively small building when using powerful servers
and a fast LAN network.
The authors of (Konstantinidis et al., 2016) pro-
posed a
PPIL
scheme based on
k
-anonymity. The
downside of their scheme is that the privacy guaran-
tees become weaker if auxiliary information, such as
the building map, is provided to the adversary. On
the other hand, if the security parameter sizes are
increased, the location accuracy decreases and the
scheme becomes impractical.
J
¨
arvinen et al. proposed PILOT (J
¨
arvinen et al.,
2019), which was the first efficient solution for
PPIL
.
PILOT uses well known Secure Two-Party Computa-
tion (
STPC
) techniques and outsources the most in-
volving computations to two semi-trusted servers in
order to achieve practical performance. Their work
includes benchmarks with various combinations of
STPC
techniques. The outsourcing setting assumes
that the two servers are non-colluding, which are hard
to find (e.g., the owner of the building and the mo-
bile network operator). Their underlying protocols
are suitable also for the client-server setting, and so
we consider (J
¨
arvinen et al., 2019) as an excellent ba-
sis for developing more efficient
PPIL
schemes. The
main disadvantage of PILOT is the large communica-
FAPRIL: Towards Faster Privacy-preserving Fingerprint-based Localization
109

tion overhead, which is regularly over
100
megabytes
per localization query making it unsuitable for setups
where parties have limited data plans. In our work, we
present techniques, which reduce the total communica-
tion by factor 16× with a very efficient online phase.
The authors of (Nieminen and J
¨
arvinen, 2020) pro-
posed a
PPIL
scheme in the client-server setting using
Paillier encryption and Garbled Circuits (
GC
s). We
call their solution NJ in our paper. NJ does not rely
on trusted third parties or outsourcing, but involves
relatively expensive operations leading to online times
of
1.55 − 8.46
seconds. On top of this, their scheme
requires computationally heavy pre-computations in
the setup phase, which take
2.45 − 12.23
seconds for
each localization query. Compared to PILOT (J
¨
arvinen
et al., 2019), NJ achieves better total communication
overheads making it suitable for the mobile client set-
ting. In contrast to NJ (Nieminen and J
¨
arvinen, 2020),
we achieve online times of only
0.15
seconds and need
only
0.28 − 4.14
seconds for the setup phase without
increasing the communication overhead.
1.2 Our Contributions
We provide the following contributions in our paper:
•
We design and implement FAPRIL, a fingerprint-
based client-server Privacy-Preserving Indoor Lo-
calization (
PPIL
) scheme using
STPC
techniques
that enables fast localization for users without leak-
ing the actual location to third parties. Addition-
ally, FAPRIL provides privacy to
SP
s keeping their
database private. We show that FAPRIL achieves
practical run-times even in large settings, and when
the client is using a regular smartphone. Com-
pared to today’s best known client-server
PPIL
scheme (Nieminen and J
¨
arvinen, 2020), our pro-
tocol avoids expensive additively homomorphic
encryption and has a
8×
faster setup time,
27×
faster online time,
6×
less online communication,
and only
1.11×
more setup communication (cf.
Tab. 3). Compared to PILOT (J
¨
arvinen et al.,
2019), we achieve
16×
less communication in the
setup phase, and
20×
less communication in the
online phase.
•
Our main goal is to optimize the input-dependent
online phase which is run over a mobile data-
plan in PPIL. For this, we use the state-of-the-
art secure two-party computation protocols from
ABY2.0 (Patra et al., 2021) that allow scalar prod-
ucts with online communication independent of
the dimension of the vector. This yields an order
of magnitude better online communication than
the ABY (Demmler et al., 2015)-based PPIL pro-
tocols of PILOT (J
¨
arvinen et al., 2019) (see §5.3).
ABY2.0 focused on improving the online phase for
different functionalities like scalar product or ma-
trix multiplication, but did not consider optimized
methods to compute the corresponding correlated
randomness in the setup phase. We observe that
in our particular setting of computing squared Eu-
clidean distances we multiply the same ABY2.0
shared vector with different vectors and propose
a dedicated setup protocol to efficiently compute
special multiplication triples for this based on ob-
servations from (Mohassel et al., 2020). This in re-
turn yields an order of magnitude better setup com-
munication than PILOT, which ultimately makes
FAPRIL suitable for the mobile client setting. The
protocol uses a technique from (Mohassel et al.,
2020) which allows to efficiently multiply one
plain value with a vector of plain values using Cor-
related Oblivious Transfer (
C-OT
) (Gilboa, 1999;
Asharov et al., 2013; Demmler et al., 2015). This
can be generalized to improve the setup complex-
ity of general Arithmetic circuits where the same
value is used in several multiplications, e.g., as in
matrix multiplication which is a common operation
in Privacy-Preserving Machine Learning (PPML).
•
The design of FAPRIL divides the fingerprint-
based localization protocol into two independent
operations, namely vector-matrix multiplication
with secret shares
1
(Patra et al., 2021) and
k
-
Nearest Neighbor Algorithm (
kNN
)
2
(Songhori
et al., 2015; J
¨
arvinen et al., 2019), which also have
applications in
PPML
and hence are likely to be op-
timized further in the future. Therefore, advances
in PPML can translate to advances in PPIL.
2 PRELIMINARIES
In this section, we describe the general fingerprint-
based localization technique commonly used for In-
door Localization (
IL
) with different distance met-
rics. Thereafter, we summarize the relevant Se-
cure Two-Party Computation (
STPC
) techniques used
in FAPRIL.
1
We use an Arithmetic sharing based approach, since it
outperforms solutions relying on public key cryptography
such as (Wang et al., 2017; Mishra et al., 2021).
2
We use a Garbled Circuit (
GC
) based approach to pre-
serve accuracy. Approximate and non-constant round
k
-
Nearest Neighbor Algorithms (
kNN
s) have been studied,
e.g., in (Shaul et al., 2020; Chen et al., 2020; Zuber and
Sirdey, 2021; Mohassel et al., 2020).
SECRYPT 2022 - 19th International Conference on Security and Cryptography
110

2.1 Fingerprint-based Localization
Indoor areas, such as airports and shopping malls,
need non-Global Navigation Satellite System (
GNSS
)
based techniques for accurate localization, since ceil-
ings or other obstacles often block the satellite signals.
A common solution for Indoor Localization (
IL
) is
fingerprint-based localization (see, e.g., (Bahl and Pad-
manabhan, 2000; Liu et al., 2007)), which requires
the Service Provider (
SP
) to pre-construct a database
holding a set of pre-measured fingerprints. The fin-
gerprints contain Received Signal Strengths (
RSS
s)
measured from different Access Points (
AP
s) (e.g.,
Wi-Fi). The set of used
AP
s is fixed and public for
the localization setup and can be based on, e.g., MAC
addresses. We assume to have
N AP
s and the pre-
measured fingerprints are measured from
M
reference
points around the area or building. The database is
written as
D = {V
1
,...,V
M
}
, where
V
i
denotes the
pre-measured fingerprint from the
i
-th reference point
(denoted as
χ
i
). A pre-measured fingerprint is written
as
V
i
= {v
i,1
,...,v
i,N
}
, where
v
i, j
denotes the
RSS
at
χ
i
from the
j
-th
AP
. After the construction,
D
is
normally placed on a server
S
offering the localization
service to users, a.k.a. clients.
Location retrieval of a client
C
goes as follows:
C
measures its own fingerprint
F = { f
1
,..., f
N
}
and
compares
F
to each
V
i
,
i ∈ {1,. ..,M}
using a spe-
cific distance metric (see §2.1.1). A small distance
d
i
between
F
and
V
i
means that the fingerprints are sim-
ilar implying that
C
is likely to be near
χ
i
. For many
settings, it is beneficial (for better accuracy) to take
the average location of multiple reference points
χ
i
corresponding to
V
i
for which the distance to
F
is
the smallest. These points can be determined by the
k
-Nearest Neighbor Algorithm (
kNN
), which here out-
puts a set of nearest reference points
{χ
1
′
,...,χ
k
′
}
.
The final location output to
C
is normally the centroid
of the k reference points {χ
1
′
,...,χ
k
′
}.
2.1.1 Distance Metrics
In fingerprint-based localization, the server
S
computes distances
d
i
between
F
and
V
i
for
i ∈ {1,...,M}
. Different distance metrics
for fingerprint-based
IL
have been studied before
(see, e.g., (Richter et al., 2018; J
¨
arvinen et al., 2019)).
To optimize performance, we focus on the squared
Euclidean distance calculated as shown in Eq. (1).
We note that for fingerprint-based localization this is
equivalent to the regular Euclidean distance, since
squaring is an order preserving operation.
d
E
i
=
N
∑
j=1
( f
j
− v
i, j
)
2
(1)
2.1.2 Parameter Size Ranges
Fingerprint-based localization includes several param-
eters, which can impact the localization accuracy. Here
we give a brief overview of the most common size
ranges for these parameters.
The size of
f
j
and
v
i, j
follows directly from the
RSS
, which is normally measured in decibels. The
authors of (Richter et al., 2018) showed that a
4
-bit
quantization of
RSS
yields the same positioning accu-
racy as with unquantized
RSS
. They also discovered
that even
1
-bit quantization is feasible for certain ap-
plications. Hence, we conclude that
f
j
and
v
i, j
are
typically 1 − 4 bits long.
The best choice for
k
in
kNN
depends on the build-
ing architecture. However, typical values for
k
are
3
or 4 (Bahl and Padmanabhan, 2000; Li et al., 2005).
The parameters
N
and
M
determine the size of
the database
D
, which follows from the localiza-
tion setup and cannot be fixed for general analysis.
Several databases for Wi-Fi fingerprint-based local-
ization have been constructed from real buildings
(see, e.g., (Mendoza-Silva et al., 2018; Lohan et al.,
2017b)). In our experiments, we use
N ∈ [50,250]
and
M ∈ [100,800]
in order to cover a large variety
of different possible setups. We consider
N = 241
and
M = 505
as a special case for comparison rea-
sons with (J
¨
arvinen et al., 2019). The values are based
on a real database measured from a four-story build-
ing (Yang and J
¨
arvinen, 2018). It might be tempt-
ing to conclude that typically
M ∼ 2N
, but while this
might make sense for many settings, we emphasize
that very different setups could occur in the real world.
As a final point, we note that a general observation
was made in (Yang and J
¨
arvinen, 2018) regarding the
database:
85.4%
of all
RSS
s in the database are zero,
i.e., most of the
AP
s are out of reach from a single
reference point. While this might be interesting to
optimize certain schemes that rely on public key cryp-
tography such as NJ (Nieminen and J
¨
arvinen, 2020),
the run-times of our protocols are independent of the
input values.
2.2 Secure Two-party Computation
A Secure Two-Party Computation (
STPC
) protocol en-
ables two parties to compute a public function
f (x, y)
on their respective private inputs
x
and
y
without re-
vealing any other information except the output of the
function. In this section, we cover two well-known
STPC
protocols, namely Arithmetic sharing and Yao
sharing. Finally, we describe how to securely convert
from Arithmetic sharing to Yao sharing.
FAPRIL: Towards Faster Privacy-preserving Fingerprint-based Localization
111

2.2.1 Arithmetic and Delta Sharing
The Arithmetic sharing protocol, due to GMW (Gol-
dreich et al., 1987), enables two parties
P
0
and
P
1
to evaluate a function on secret shared values. The
function is expressed as an Arithmetic circuit con-
sisting of addition and multiplication gates and the
operations are performed in the ring
Z
2
ℓ
. We denote
the Arithmetic sharing of
x
with
[x]
and the random
shares with
[x]
0
,[x]
1
respectively for
P
0
,P
1
. In order
for
P
i
,
i ∈ {0,1}
to secret share
x ∈ Z
2
ℓ
,
P
i
chooses a
random value
r ∈
R
Z
2
ℓ
and sets
[x]
i
= x − r (mod 2
ℓ
)
and
[x]
1−i
= r
. Now
P
i
keeps
[x]
i
and sends
[x]
1−i
to P
1−i
. It is easy to see that [x]
0
+ [x]
1
= x (mod 2
ℓ
).
The authors of (Patra et al., 2021) proposed an opti-
mized variant of the general Arithmetic sharing proto-
col, which we refer to as Delta sharing protocol from
now on. With their technique, the online communica-
tion per multiplication gate is reduced in half. More
importantly for us, they present an efficient protocol
for scalar product, which achieves an online communi-
cation complexity independent of the vector dimension.
We denote the Delta sharing of
x
with
⟨
x
⟩
and the ran-
dom shares with
⟨
x
⟩
i
for
P
i
,
i ∈ {0, 1}
. Addition gates
are local computations. Multiplication requires an in-
teractive protocol and Multiplication Triples (
MT
s).
In our work, we generate the
MT
s via the Correlated
Oblivious Transfer (
C-OT
) protocol of (Asharov et al.,
2013). We refer the reader to (Patra et al., 2021) for
the details on the Delta sharing semantics.
2.2.2 Yao Sharing
Yao sharing is based on Yao’s Garbled Circuits
(
GC
s) (Yao, 1986) and enables two parties to securely
evaluate a function expressed as a Boolean circuit. The
basic idea of
GC
s is the following: one of the parties,
called the garbler, assigns two randomly chosen sym-
metric keys to all wires called garbled values. For all
gates, the garbler uses the input keys to encrypt the
corresponding output key. Next, the garbler sends the
encrypted gates (called garbled circuit) to the other
party, typically referred to as the evaluator, along with
the symmetric keys corresponding to its input bits. The
evaluator obtains the symmetric keys corresponding
to its input bits via an Oblivious Transfer (
OT
) proto-
col implemented efficiently using
OT
extension (Ishai
et al., 2003; Asharov et al., 2013). Finally, the eval-
uator evaluates the garbled circuit by decrypting the
garbled gates obtaining the garbled output values. In
order to reveal the actual output values to the evaluator,
the garbler provides the evaluator with information to
decode the output wires.
Over the years, several optimization techniques for
GC
s have been introduced. These include point-and-
permute (Beaver et al., 1990), free-XOR (Kolesnikov
and Schneider, 2008), fixed-key AES garbling (Bellare
et al., 2013), and half-gates (Zahur et al., 2015). Re-
cently, Rosulek and Roy (Rosulek and Roy, 2021)
introduced a new
GC
optimization, which defeats
half-gates (Zahur et al., 2015). However, we ex-
clude this technique from our implementation of
FAPRIL, mainly in order to have a fair comparison
with the related works, which can also benefit from
this optimization.
2.2.3 From Arithmetic/Delta to Yao Sharing
The conversion from Arithmetic shares to Yao shares
is described in (Demmler et al., 2015). The conversion
for the Delta sharing protocol is described in (Patra
et al., 2021), but follows the same idea: the Boolean
circuit for Yao’s
GC
s begins by adding the Arithmetic
shared values from both parties. With Delta sharing
the
C-OT
step can be performed in the setup phase
in contrast to Arithmetic sharing, where this is in the
online phase.
3 SYSTEM DETAILS
In this section, we give an overview of FAPRIL,
our
PPIL
scheme in the client-server setting based
on mixed-protocol Secure Two-Party Computation
(
STPC
), namely Delta and Yao sharing (see §2.2). A
high-level overview is given in §3.1 and a more de-
tailed description follows in §3.2 containing also the
complexity analysis. Finally, the security aspects are
discussed in §3.3.
3.1 Overview
Here we give a high-level overview of FAPRIL,
which uses Delta and Yao sharing to provide privacy-
preserving fingerprint-based localization. Our scheme
follows the idea from (J
¨
arvinen et al., 2019), where the
most cost efficient localization was achieved using the
combination of Arithmetic sharing, which we improve
to Delta sharing, and Yao sharing. Additionally, we
select the squared Euclidean distance to be our dis-
tance metric (see §2.1.1), since it gives arguably the
best cost-accuracy ratio for Privacy-Preserving Indoor
Localization (
PPIL
), see (J
¨
arvinen et al., 2019). We
denote the number of used Access Points (
AP
s) with
N
and the number of reference points with
M
(see §2.1).
After the client
C
has measured its finger-
print
F
, it Delta shares
F
with the server
S
such
that
⟨
F
⟩
= {
⟨
f
1
⟩
,...,
⟨
f
N
⟩
}
. Additionally,
C
Delta
shares
∑
N
j=1
f
2
j
with
S
. Similarly,
S
Delta shares
SECRYPT 2022 - 19th International Conference on Security and Cryptography
112

each pre-measured fingerprint
V
i
along with
∑
N
j=1
v
2
i, j
,
i ∈ {1, .. ., M}
from the database
D
. After the
sharing, both parties have obtained their respective
shares
⟨
F
⟩
,
D
∑
N
j=1
f
2
j
E
and
n
⟨
V
i
⟩
,
D
∑
N
j=1
v
2
i, j
Eo
M
i=1
,
where
⟨
V
i
⟩
=
⟨
v
i,1
⟩
,...,
⟨
v
i,N
⟩
.
Next, both parties compute the squared Euclidean
distances using their respective shares using Eq. (2),
which is directly derived from Eq. (1).
⟨
d
i
⟩
=
*
N
∑
j=1
f
2
j
+
+
*
N
∑
j=1
v
2
i, j
+
− 2
N
∑
j=1
f
j
·
v
i, j
(2)
Eq. (2) requires
N
multiplications, and thus the to-
tal number of multiplications to obtain all
{⟨
d
i
⟩}
M
i=1
is N · M.
We note that
∑
N
j=1
f
j
·
v
i, j
is a scalar product
between
⟨
F
⟩
and
⟨
V
i
⟩
, and thus we can compute it
with the optimized Delta sharing scalar product of (Pa-
tra et al., 2021). More generally, we can reduce the
problem of computing
{⟨
d
i
⟩}
M
i=1
down to a vector-
matrix multiplication (plus cheap addition operations
with the shares afterwards). More formally, we trans-
form the fingerprint
F
to a vector of length
N
and the
database
D
into a
M × N
matrix. The Delta shared
versions are as follows:
F
N
=
⟨
f
1
⟩ ⟨
f
2
⟩
···
⟨
f
N
⟩
,
D
M×N
=
⟨
v
1,1
⟩ ⟨
v
1,2
⟩
···
⟨
v
1,N
⟩
⟨
v
2,1
⟩ ⟨
v
2,2
⟩
···
⟨
v
2,N
⟩
.
.
.
.
.
.
.
.
.
.
.
.
⟨
v
M,1
⟩ ⟨
v
M,2
⟩
···
⟨
v
M,N
⟩
.
The distances are obtained by first computing
the vector-matrix multiplication
F
N
·
D
M×N
T
,
where
T
is the transpose operator
3
. The result is a
vector of length
M
containing
n
∑
N
j=1
f
j
·
v
i, j
o
M
i=1
.
These values are used with Eq. (2) requiring a total
of
3
additions. Note that all the operations are in
Z
2
ℓ
,
where ℓ is the bit-length of d.
The Delta shares
{⟨
d
i
⟩}
M
i=1
are converted to Yao
shares as described in §2.2.3. In FAPRIL, the server
S
takes the role of the garbler and constructs a garbled
circuit, which first adds the shares
{⟨
d
i
⟩}
M
i=1
together
(the conversion) and then runs the
k
-Nearest Neighbor
Algorithm (
kNN
) on the distances, finally returning
the
k
indices corresponding to the smallest distances.
3
Note that the parties do not actually have to perform
the transpose operator, because it only gives a different rep-
resentation of the database
D
. The reason for our initial
representation is mainly to be consistent with the literature.
An efficient circuit construction of
kNN
for Yao shar-
ing was presented in the appendix of (J
¨
arvinen et al.,
2019) and we omit further details here.
In the last step of FAPRIL, the client
C
uses the
k
indices to obtain the
k
reference points
{χ
1
′
,...,χ
k
′
}
.
Here we assume, similarly to (Nieminen and J
¨
arvi-
nen, 2020), that the server
S
has published the set of
reference points
{
χ
i
}
M
i=1
to the public.
3.2 Details and Complexity
We move on to a more precise description of the steps
of FAPRIL and the complexity of these steps. Certain
parameters, such as the list of Access Points (
AP
s) and
the security parameter
κ
, are negotiated between the
client
C
and the server
S
in a one-time initialization
step. The resulting overhead is not very interesting,
since it does not accumulate over time. Moreover, the
parameters can be included in the client application as
hard coded values.
FAPRIL uses the Oblivious Transfer (
OT
) exten-
sion protocol of (Asharov et al., 2013), which requires
so called base
OT
in the initialization step. In fact, our
implementation of FAPRIL (see §5) uses two differ-
ent
OT
flavors and we need to run two different base
OT
steps. However, the steps are independent of
M
and
N
, and require under
1
second and
30
kilobytes of
communication in total. They can also be reused for
multiple protocol runs between
C
and
S
. We conclude
that these overheads are negligible.
We separate FAPRIL into two phases, namely
setup and online phase. The setup phase is independent
of
C
’s fingerprint
F
and can be computed in advance,
e.g., multiple times overnight using a relatively fast
Wi-Fi connection. The online phase depends on
F
and must be performed only after C has measured the
Received Signal Strengths (RSSs).
3.2.1 Setup Phase
In the setup phase, we generate the Multiplication
Triples (
MT
s) for the multiplication operations with
the Delta shares as shown in Eq. (2).
MT
s can be
generated in various ways using
OT
or
HE
(Rathee
et al., 2019). Due to the necessity to implement on a
mobile device, we choose to use the
OT
-based mul-
tiplication protocol by Gilboa (Gilboa, 1999) with
Correlated Oblivious Transfer (
C-OT
) as in (Demm-
ler et al., 2015). With the optimization technique
from (Demmler et al., 2015), the total communication
needed to construct an
ℓ
-bit
MT
is
2ℓ(κ + (ℓ + 1)/2)
bits, where
κ
is the security parameter. We set
κ = 128
for FAPRIL. The multiplications are performed in
Z
2
ℓ
,
where
ℓ
is the bit-length of
d
i
,
i ∈ {1, .. ., M}
. We can
calculate
ℓ
with Eq. (3), where
ℓ
RSS
is the bit-length
FAPRIL: Towards Faster Privacy-preserving Fingerprint-based Localization
113

of
f
and
v
, i.e.,
ℓ
RSS
follows from the quantization
of RSSs.
ℓ =
l
log
2
(2
ℓ
RSS
− 1)
2
· N
m
(3)
For FAPRIL, we fix
ℓ
RSS
= 4
as it was shown to
provide the same level of accuracy as longer bit-
lengths (Richter et al., 2018) (see also §2.1.2). We
simplify Eq. (3) accordingly to get Eq. (4).
ℓ =
⌈
log
2
225N
⌉
≈ 8 +
⌈
log
2
N
⌉
(4)
As stated earlier, the total number of multiplications
needed is
N · M
. Hence, we need a total of
N · M ·
2ℓ(κ + (ℓ + 1)/2)
bits of communication. If
N = 241
and
M = 505
, we have
ℓ = 16
and the communication
needed for the
MT
generation is
63.4
megabytes. How-
ever, later in §4 we propose an optimization technique
to reduce this communication down to
4.2
megabytes
making FAPRIL more practical for smartphone clients
with limited mobile data plans. Each
MT
generation
with
C-OT
s requires
6ℓ
symmetric cryptographic op-
erations, so N · M · 6ℓ in total.
The client
C
needs to obtain its garbled input values
from the server
S
for the conversion step from Delta to
Yao sharing. This is normally performed with a
C-OT
protocol in order to comply with the free-XOR
GC
optimization technique (Kolesnikov and Schneider,
2008). In general, this step should be in the online
phase, since the inputs (the Delta shares of distances)
depend on
C
’s input. However, due to the nature of
Delta shares we can move this step in the setup phase
(as was already pointed out in (Patra et al., 2021)). The
required communication for this step is
M · 2ℓκ
(
252.5
kilobytes for
N = 241,M = 505
) and the total number
of symmetric cryptographic operations is M · 3ℓ.
The final setup phase step is the construction and
sending of the garbled circuit, which computes the
addition for the sharing conversion and
kNN
. The
communication and computation overheads follow di-
rectly from the AND-size of the circuit. The con-
version requires
M · ℓ
AND gates and the size op-
timized
kNN
based on (J
¨
arvinen et al., 2019) re-
quires
M · k(2ℓ +
⌈
log
2
M
⌉
)
AND gates. This gives
us the total number of AND gates, namely
#AND =
M · (2kℓ + k
⌈
log
2
M
⌉
+ ℓ)
. The required communica-
tion is
2κ · #AND
bits and the garbler needs to per-
form
4 · #AND
fixed-key AES operations. With
N =
241
,
M = 505
, and
k = 3
we get
#AND = 70195
,
which translates to
2.1
megabytes of communication.
We note that with the recent optimization of (Rosulek
and Roy, 2021) this communication can be reduced by
factor ≈ 2/1.5× down to 1.6 megabytes.
Finally, we note that the
MT
generation is inde-
pendent of the other steps and can be performed in
parallel in order to reduce the total run-time. The total
theoretical setup communication with state-of-the-art
optimizations (including (Rosulek and Roy, 2021) and
§4) is 6.0 megabytes, when N = 241,M = 505,k = 3.
3.2.2 Online Phase
In the online phase, the client
C
measures its finger-
print
F
and runs a private localization query with the
server
S
. The first step for
C
is to Delta share
F
and
∑
N
j=1
f
2
j
with
S
as explained in §3.1. This re-
quires communication of
(N + 1) · ℓ
bits from
C
to
S
and only simple computations. For
N = 241
, this step
requires 0.5 kilobytes of communication.
Then both parties compute the distances
{⟨
d
i
⟩}
M
i=1
(in parallel) following Eq. (2) and using the efficient
scalar product from (Patra et al., 2021). As stated in
§2.2.1, the communication is independent of the vector
length (here
N
) and the total communication is
M · 2ℓ
requiring only one round of communication. This step
also requires only simple computations when
MT
s are
pre-computed in the setup phase. For
N = 241,M =
505
, this step requires
2.0
kilobytes of communication.
Next,
S
sends its garbled input values correspond-
ing to its shares
{⟨
d
i
⟩}
M
i=1
to
C
. This step does not
require any computations and the size of the garbled
values is
κ · M · ℓ
. For
N = 241,M = 505
, this step
requires 126.3 kilobytes of communication.
In the last step,
C
evaluates the garbled circuit and
obtains
k
indices. The evaluation requires
2 · #AND
fixed-key AES operations with (Zahur et al., 2015).
This step does not require communication. The per-
mutation bits (Beaver et al., 1990) of the output gar-
bled values can be used to reveal the actual output
values. Alternatively,
S
can send the signal bits for
all output wires, requiring
k
⌈
log
2
M
⌉
bits of communi-
cation. For
M = 505, k = 3
, this step requires
27
bits
of communication.
Finally, we conclude that the communication com-
plexity of the online phase is orders of magnitude
smaller than that of the setup phase. The total the-
oretical online communication is
128.8
kilobytes,
when
N = 241,M = 505,k = 3
. FAPRIL shifts very
efficiently most of the computation and communica-
tion in the setup phase, making it very attractive for
applications which require fast location retrievals but
allow pre-computations, e.g., overnight.
3.3 Security and Privacy Discussion
In this section, we give a brief security analysis of
FAPRIL in §3.3.1. Furthermore, we discuss differ-
ent privacy aspects regarding the reference points
in §3.3.2.
FAPRIL is secure in the semi-honest adversary
SECRYPT 2022 - 19th International Conference on Security and Cryptography
114

model, a.k.a. “honest-but-curious” adversary model,
which assumes that both parties follow the protocol
specification, but try to learn additional information
from the transcript, i.e., from the received messages.
Most of the related work on Privacy-Preserving Indoor
Localization (
PPIL
) relies on the same semi-honest ad-
versary model and it is widely used in many other
applications including Privacy-Preserving Machine
Learning (PPML).
3.3.1 Security Analysis
FAPRIL uses well-known Secure Two-Party Computa-
tion (
STPC
) techniques in a rigorous way. Technique
wise, FAPRIL can be divided into three parts, namely
computation of an Arithmetic circuit in Delta sharing,
conversion from Delta to Yao sharing, and computa-
tion of a Boolean circuit in Yao sharing (see §2.2). The
latter two are based on Yao’s Garbled Circuit (
GC
)
protocol, which was proven secure for semi-honest
adversaries in (Lindell and Pinkas, 2009). For the se-
curity proof of the other parts, we refer the reader to
the full version of (Patra et al., 2021). In summary, the
security follows from the security assumptions of the
underlying primitives, which for FAPRIL is Oblivious
Transfer (
OT
), which was proven secure in (Asharov
et al., 2013). The security of FAPRIL persists for mul-
tiple sequential queries. However, auxiliary informa-
tion, such as how frequently the client makes queries
is always “leaked” outside the protocol execution to
the Service Provider (SP).
It is also important that the client communicates
with the servers over the mobile network but not via
Wi-Fi
AP
s, which are controlled by the
SP
. This would
leak the client’s location, since the
SP
can see from
which
AP
the client communicates and can use trian-
gulation to determine the location. However, this is
not related to the
RSS
values used in FAPRIL and is
not a leakage of our scheme.
In conclusion, FAPRIL utilizes all the primitives as
a black box, from which the security guarantees follow
automatically. FAPRIL guarantees passive security,
i.e., security against semi-honest adversaries. We note
that since our scheme is based on
STPC
techniques
which also have variants to withstand stronger security
models, the security guarantees of FAPRIL can be
enhanced using standard methods.
3.3.2 Privacy of Reference Points
As pointed out at the end of §3.1, FAPRIL assumes
that the set of reference points
{
χ
i
}
M
i=1
is made public
by the server. While this is the case in related works
such as (Nieminen and J
¨
arvinen, 2020; Li et al., 2014),
in (J
¨
arvinen et al., 2019) the reference points were con-
sidered “private”. More precisely, PILOT (J
¨
arvinen
et al., 2019) runs a similar protocol as FAPRIL, but
extends the garbled circuit for
kNN
with an Oblivious
Array Access (
OA
) circuit, which returns only the
k
closest coordinates
{χ
1
′
,...,χ
k
′
}
. While this seem-
ingly keeps the reference points
{
χ
i
}
M
i=1
private, we
note that an adversary could simply walk around the
building or area and obtain at least most of the coordi-
nates revealing a (almost complete) subset of
{
χ
i
}
M
i=1
.
One attractive way to prevent the previous attempt
is to compute the centroid among the
k
coordinates
also inside the garbled circuit. However, this also re-
veals information about
{
χ
i
}
M
i=1
by triangulation. We
omit the detailed description of the possible attacks,
but note that it is certainly possible to obtain at least
a close replica of
{
χ
i
}
M
i=1
in fingerprint-based local-
ization, even if the client only obtains its location co-
ordinate from the server (as it is already the case in
the general non-privacy-preserving protocol described
in §2.1).
In many real-world scenarios, the reference point
pattern could be easily guessed from the building map
(e.g., when it is based on individual rooms). The refer-
ence point coordinates basically only reveal the strat-
egy for constructing
D
, but does not help the adversary
to construct a similar database, since the adversary
does not have the same equipment for the Received
Signal Strength (
RSS
) measurements. We also note
that an attack which tries to build a replica of D labo-
riously, is not an attack against FAPRIL.
To fully hide the used distance metric and all the
parameters, one can use Private Function Evaluation
(
PFE
) (Alhassan et al., 2020) which incurs substantial
overhead compared to a public distance metric.
4 CORRELATED
MULTIPLICATION TRIPLE
GENERATION
In this section, we show how to interactively gener-
ate Multiplication Triples (
MT
s) for the special case
where one secret shared value is multiplied with sev-
eral values. More specifically, we want to gener-
ate multiplications of the form
([a]
0,i
+ [a]
1,i
) · ([b]
0
+
[b]
1
) = ([c]
0,i
+ [c]
1,i
) (mod 2
ℓ
)
for
i ∈ {1, .. ., M}
. As
sub-protocol we use a protocol from (Mohassel et al.,
2020; Demmler et al., 2015) to multiply a value known
in the clear by one party with a vector of values known
in the clear by the other party using
1
-out-of-
2
Cor-
related Oblivious Transfers (
C-OT
s). The authors
of (Mohassel et al., 2020; Demmler et al., 2015) also
considered computing squared Euclidean distances
FAPRIL: Towards Faster Privacy-preserving Fingerprint-based Localization
115

where the same value is reused, but using the old
ABY (Demmler et al., 2015)-style Arithmetic sharing
which results for
N = 241 AP
s and
M = 505
refer-
ence points in online communication of
3.7
megabytes
whereas we require only 2.5 kilobytes.
4.1 C-OT-based MT Generation
We start by giving a short overview of how
C-OT
(Asharov et al., 2013) is used to generate a
single
MT
as described in (Gilboa, 1999; Demmler
et al., 2015). We want to compute a
MT
consist-
ing of Arithmetic shares
[a]
0
,[a]
1
,[b]
0
,[b]
1
,[c]
0
,[c]
1
∈
Z
2
ℓ
,ℓ ∈ Z
such that
([a]
0
+ [a]
1
) · ([b]
0
+ [b]
1
) = [c]
0
+
[c]
1
(mod 2
ℓ
)
where party
P
i
gets to know only its re-
spective shares
[a]
i
,[b]
i
,[c]
i
. Multiplying out one sees
that the challenge is to securely compute
[[a]
0
[b]
1
]
i
where the shares are held by different parties. (By
symmetry, the other cross-term
[[a]
1
[b]
0
]
i
can be com-
puted by running the same protocol in parallel in the
opposite direction.)
The protocol starts by
P
0
randomly generat-
ing
[a]
0
∈
R
Z
2
ℓ
and
P
1
randomly generating
[b]
1
∈
R
Z
2
ℓ
. Now
P
0
and
P
1
run several
C-OT
protocols in
parallel. Without loss of generality, we assume that
P
0
is the sender and
P
1
is the receiver. For each
j
-th
bit
B
j
in
[b]
1
, the parties run a
1
-out-of-
2 C-OT
proto-
col, where
P
0
inputs the correlation function
f
∆
j
(x) =
([a]
0
· 2
j
+ x) (mod 2
ℓ
)
and obtains
(s
j,0
= r
j
,s
j,1
=
[a]
0
· 2
j
+ r
j
)
, where
r
j
∈
R
Z
2
ℓ
, and
P
1
obtains
s
j,B
j
.
Now the respective shares are
[[a]
0
[b]
1
]
0
=
∑
ℓ−1
j=0
(−r
j
)
and
[[a]
0
[b]
1
]
1
=
∑
ℓ−1
j=0
s
j,B
j
. Correctness and security
were shown in (Demmler et al., 2015).
Each
1
-out-of-
2 C-OT
protocol (Asharov et al.,
2013) requires
P
1
to send
κ
bits to
P
0
, who replies
with
ℓ
bits. As we run the protocol twice also for the
other cross-term, this yields total setup communication
per MT of 2ℓ(κ + ℓ) bits.
4.2 Correlated MT Generation
Now, the goal is to generate an additional
MT
using the same share
[b]
i
, i.e., Arithmetic shares
[a
′
]
0
,[a
′
]
1
,[b]
0
,[b]
1
,[c
′
]
0
,[c
′
]
1
that satisfy
([a
′
]
0
+
[a
′
]
1
) · ([b]
0
+ [b]
1
) = ([c
′
]
0
+ [c
′
]
1
) (mod 2
ℓ
)
. As ob-
served in (Mohassel et al., 2020),
P
1
inputs the same
values corresponding to the
[b]
1
into the
C-OT
proto-
cols for the first
MT
and hence the messages from
P
1
to
P
0
can be reused. Therefore, only the second mes-
sage from
P
0
to
P
1
consisting of
ℓ
bits has to be sent in
each
C-OT
, i.e., an additional
2ℓ
2
bits for the second
MT
. Repeating this construction in parallel
M
times
yields a total communication of
2ℓ(κ + M · ℓ)
bits for
M
multiplication triples. An additional optimization
described in (Demmler et al., 2015, §III-A5) sends
only back those bits of the second
C-OT
message that
are needed for the answer resulting in communication
2ℓ(κ + M · (ℓ + 1)/2)
bits. The benefit of this opti-
mization technique depends on the parameters and is
further discussed in the full version (van der Beets
et al., 2022).
4.3
Application to Matrix Multiplication
The improved correlated
MT
generation technique de-
scribed in §4.2 can also be applied to other applications
where values re-occur such as matrix multiplication
on Arithmetic/Delta shares, which is a very common
operation, e.g., in Privacy-Preserving Machine Learn-
ing (
PPML
) (Riazi et al., 2018; Patra et al., 2021). For
two matrices A
p×q
and B
q×r
, we need to generate
pqr
MT
s, which requires
pqr · 2ℓ(κ + ℓ)
bits of commu-
nication in the setup phase using the basic approach
of (Demmler et al., 2015). This communication cost
was also given in (Patra et al., 2021).
With the optimization, the new computation cost
is
2pqℓ(κ+rℓ)
bits in the setup phase, which can be re-
duced even further with the optimization from (Demm-
ler et al., 2015, §III-A5) to 2pqℓ(κ + r(ℓ + 1)/2) bits.
If we fix
κ = 128,ℓ = 32, p,q,r = 1000
, one matrix
multiplication with the basic approach combined with
the optimization (Demmler et al., 2015, §III-A5), i.e.,
the communication cost is
2pqrℓ(κ + (ℓ + 1)/2)
bits,
requires 1.05 terabytes of communication. This is op-
timized to only
124
gigabytes resulting in factor
8.6×
improvement in communication.
5 PERFORMANCE EVALUATION
In this section, we benchmark FAPRIL with our imple-
mentation using artificial databases of different sizes.
We start by inspecting the setup and online phase over-
heads in §5.1. In §5.2, we inspect the overheads sepa-
rately for each step of FAPRIL (described in §3.2). In
§5.3, we compare our results against the currently best
known Privacy-Preserving Indoor Localization (
PPIL
)
schemes of (J
¨
arvinen et al., 2019; Nieminen and J
¨
arvi-
nen, 2020).
We implemented the client side of FAPRIL on An-
droid smartphones. Our implementation relies on two
open source libraries, namely Mobile Private Contact
Discovery
4
, providing the basis for the Garbled Cir-
cuit (
GC
) protocol, and libOTe
5
, providing the basis
4
https://github.com/contact-discovery/mobile psi cpp
5
https://github.com/osu-crypto/libOTe
SECRYPT 2022 - 19th International Conference on Security and Cryptography
116
for the Correlated Oblivious Transfer (
C-OT
) protocol.
We develop the Delta sharing protocol based on (Pa-
tra et al., 2021). Our full implementation is publicly
available under the MIT License
6
.
We use a Huawei P20 smartphone as our client
device and a commodity server as specified in Tab. 1.
For our network setup, we simulate a real-world LTE
connection as follows: we use simulation scripts on the
server side to increase the outgoing latency to
10
mil-
liseconds (ms) and limit the bandwidth to
50
megabits
per second (Mbit/s). The smartphone uses a Wi-Fi
network to connect to the server, which increases the
total Round-Trip Time (
RTT
) to approximately
16
ms.
Table 1: The hardware details of our devices.
CPU Type Clock Rate Cores RAM
Client HiSilic. K970 1.8 GHz 8 4 GB
Server Intel i9-7960X 2.8 GHz 16 128 GB
For the following experiments, we fix the Received
Signal Strength (
RSS
) quantization to
4
bits, use
k = 3
for the
k
-Nearest Neighbor Algorithm (
kNN
), and fix
the security parameter
κ = 128
. In order to get precise
results, we run our experiments
10
times for each case
and use the averages.
5.1 Benchmarks
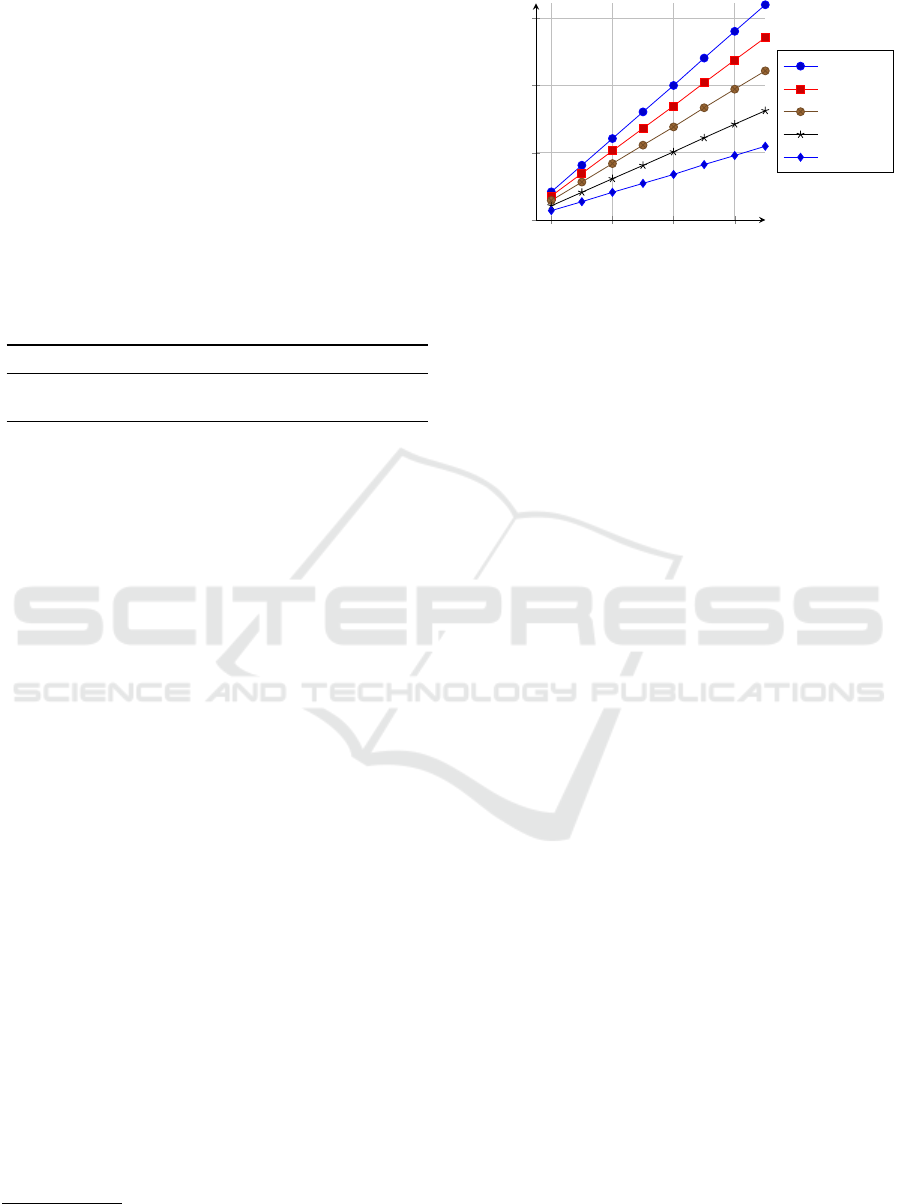
The setup phase communication is shown in Fig. 1. As
expected, it grows linearly in the number of Access
Points (
AP
s)
N
and the number of reference points
M
.
The setup run-times grow also linearly. When
N =
50,M = 100
, we only need about
0.28
seconds, but
the run-time gets up to
1.48
seconds when we in-
crease
M = 800
. For
N = 250,M = 100
, we have a run-
time of
0.59
seconds, which grows to
4.14
seconds for
the largest case, namely
N = 250,M = 800
. The online
phase is more efficient, and even for our largest setting
(
N = 250,M = 800
) we require only
0.20
megabytes
of communication and the run-time is 0.15 seconds.
5.2 Detailed Benchmarks
We move to the more detailed view of the overheads.
For this, we fix
N = 241, M = 505
as it represents a
real four-story building (see §2.1.2) and collect the
results in Tab. 2. It is clear that the setup phase domi-
nates the total costs for FAPRIL. More precisely, the
clear bottleneck is the Multiplication Triple (
MT
) gen-
eration, which requires
7.55
megabytes of communi-
cation and a run-time of
2.22
seconds. We note here
6
https://github.com/encryptogroup/
ppIndoorLocalization
100 300
500
700
0
5
10
15
Number of Reference Points M
Setup communication (MB)
N = 250
N = 200
N = 150
N = 100
N = 50
Figure 1: The setup phase communication in megabytes
(MB), when altering the number of Access Points N.
that our implementation does not take advantage of
the optimization of (Demmler et al., 2015, §III-A5)
due to integration problems with the libOTe library.
Therefore, the communication is almost doubled com-
pared to the theoretical case, which is
4.2
megabytes
(see §3.2.1). Our implementation also does not take
full advantage of parallelization, which could possi-
bly decrease the run-time significantly. FAPRIL can
benefit directly from further improvements regarding
MT
generation, e.g., the recently proposed Silent
OT
technique (Boyle et al., 2019b; Boyle et al., 2019a)
that improves communication at the expense of more
computation or
MT
generation with Ring Learning
With Errors (
RLWE
)-based additively Homomorphic
Encryption (
HE
) (Rathee et al., 2019). We leave imple-
mentation of these on mobile phones as future work.
Comparing our concrete communication overheads
from Tab. 2b with the complexity analysis, we con-
clude that our benchmarks are aligned with the theo-
retical numbers (see §3.2), except for the MT genera-
tion (as explained previously) and for Client Garbled
Inputs. The reason for the latter is that our implemen-
tation takes advantage of the more efficient “Delta-
OT” (Burra et al., 2021) as implemented in libOTe.
5.3
Performance Comparison to Related
Work
In this section, we compare the performance of
FAPRIL to the client-server scheme NJ (Nieminen and
J
¨
arvinen, 2020), and the Arithmetic and Yao sharing
(AY) based scheme using squared Euclidean distance
from (J
¨
arvinen et al., 2019). The results are collected
in Tab. 3.
We can see that FAPRIL clearly outperforms
NJ (Nieminen and J
¨
arvinen, 2020) except for the setup
phase communication, which is expected to be in the
favor of NJ even more when the number of
AP
s
N
increases. On the other hand, we argue that the run-
FAPRIL: Towards Faster Privacy-preserving Fingerprint-based Localization
117
Table 2: Detailed performance evaluation of FAPRIL
with
N = 241
Access Points (
AP
s),
M = 505
reference
points,
κ = 128
security parameter, and
k = 3
for the
k
-
Nearest Neighbor Algorithm (
kNN
). The steps are explained
in detail in §3.2.
(a) Run-times in milliseconds (ms).
Step Run-time
(ms)
Setup Phase
MT Generation 2,218.8
Client Garbled Inputs 74.7
Garbled Circuit 256.4
Total 2,549.9
Online Phase
Fingerprint Sharing 0.0
Distance Computation 16.0
Server Garbled Inputs 42.5
Garbled Circuit Eval. 37.5
Total 96.0
(b) Communication in kilobytes (kB) from client’s
perspective.
Step Uplink
(kB)
Downlink
(kB)
Setup Phase
MT Generation 3,867.3 3,867.3
Client Garbled Inputs 144.2 32 B
Garbled Circuit – 2,193.6
Total 4,011.5 6,060.9
Online Phase
Fingerprint Sharing 0.5 –
Distance Computation 1.0 1.0
Server Garbled Inputs – 126.3
Garbled Circuit Eval. – 27 B
Total 1.5 127.3
time advantages of FAPRIL makes it more attractive
for practical usage. The run-time improvements of
8×
for the setup phase and
27×
for the online phase is
significant. We also note that the improvements are
expected to be considerably greater for larger settings.
Our comparison to AY (J
¨
arvinen et al., 2019) is not
completely fair, since it was run in an outsourced set-
ting, where all the computations occur on commodity
servers. On the other hand, AY (J
¨
arvinen et al., 2019)
includes an extra step at the end to obtain the location
coordinates using Oblivious Array Access (
OA
). How-
ever, this step could be directly included in FAPRIL
(see §3.3.2). Based on their evaluations, the step re-
quires
1.3
megabytes of communication and takes
46
milliseconds. Even with this, FAPRIL achieves similar
online run-times and almost
15×
less communication
in total compared to AY (J
¨
arvinen et al., 2019).
Table 3: Performance of FAPRIL compared to the re-
lated work with
N ∈ {50,241}
Access Points (
AP
s),
M ∈
{150,505}
reference points,
κ = 128
security parameter,
and
k = 3
for the
k
-Nearest Neighbor Algorithm (
kNN
). The
most efficient values are marked in bold.
Run-time (s) Comm. (MB)
Setup
Online
Total Setup
Online
Total
N = 50,M = 150
FAPRIL
0.3 54 ms 0.4 1.0 34 kB 1.0
NJ 2.5 1.5 4.0 0.9 0.2 1.1
N = 241,M = 505
FAPRIL
2.5 96 ms 2.6 9.8 129 kB 9.9
AY
a
0.8 0.15 1.0 164.0 2.7 167.0
a
Includes Oblivious Array Access step (not in FAPRIL).
6 CONCLUSION AND FUTURE
WORK
We presented FAPRIL, a Privacy-Preserving Indoor
Localization (
PPIL
) scheme in the client-server set-
ting based on state-of-the-art Secure Two-Party Com-
putation (
STPC
). We implemented FAPRIL for An-
droid smartphones and evaluated the performance
with various benchmarks representing real world set-
tings. With our optimization technique for gener-
ating Multiplication Triples (
MT
s), we showed that
FAPRIL achieves practical run-times and communi-
cation. More precisely, for a real world university
building setting with
241
Access Points (
AP
s) and
505
reference points, we achieve a online run-time of
96
milliseconds and
129
kilobytes online communication.
The setup phase takes
2.5
seconds and requires
9.8
megabytes of communication. With these results, we
substantially outperform previously proposed solu-
tions for PPIL.
Lastly, we give a list of interesting topics for fu-
ture research:
•
Analyzing FAPRIL’s power consumption on smart-
phones.
•
Improving the efficiency of the vector-matrix mul-
tiplication with secret shares using different
MT
generation techniques, e.g., Ring Learning With Er-
rors (
RLWE
)-based additively Homomorphic En-
cryption (HE) (Rathee et al., 2019).
•
Developing protocols that hide the size of the
database, the used distance metric, and/or the ref-
erence point coordinates from the clients.
SECRYPT 2022 - 19th International Conference on Security and Cryptography
118

ACKNOWLEDGMENTS
This project received funding from the European Re-
search Council (ERC) under the European Union’s
Horizon 2020 research and innovation program (grant
agreement No. 850990 PSOTI). It was co-funded
by the Deutsche Forschungsgemeinschaft (DFG) –
SFB 1119 CROSSING/236615297 and GRK 2050 Pri-
vacy & Trust/251805230, and by the German Federal
Ministry of Education and Research and the Hessen
State Ministry for Higher Education, Research and the
Arts within ATHENE.
REFERENCES
Alhassan, M. Y., G
¨
unther, D., Kiss, A., and Schneider,
T. (2020). Efficient and scalable universal circuits.
J. Cryptology.
Alletto, S., Cucchiara, R., Del Fiore, G., Mainetti, L.,
Mighali, V., Patrono, L., and Serra, G. (2015). An
indoor location-aware system for an IoT-based smart
museum. IEEE Internet of Things Journal.
Asharov, G., Lindell, Y., Schneider, T., and Zohner, M.
(2013). More efficient oblivious transfer and exten-
sions for faster secure computation. In CCS.
Bahl, P. and Padmanabhan, V. N. (2000). RADAR: An in-
building RF-based user location and tracking system.
In INFOCOM.
Barsocchi, P., Calabr
`
o, A., Crivello, A., Daoudagh, S.,
Furfari, F., Girolami, M., and Marchetti, E. (2021).
COVID-19 & privacy: Enhancing of indoor localiza-
tion architectures towards effective social distancing.
Array.
Beaver, D., Micali, S., and Rogaway, P. (1990). The round
complexity of secure protocols. In STOC.
Bellare, M., Hoang, V. T., Keelveedhi, S., and Rogaway, P.
(2013). Efficient garbling from a fixed-key blockcipher.
In S&P.
Bellovin, S. M., Hutchins, R. M., Jebara, T., and Zimmeck,
S. (2013). When enough is enough: Location tracking,
mosaic theory, and machine learning. NYU Journal of
Law & Liberty.
Boyle, E., Couteau, G., Gilboa, N., Ishai, Y., Kohl, L.,
Rindal, P., and Scholl, P. (2019a). Efficient two-round
OT extension and silent non-interactive secure compu-
tation. In CCS.
Boyle, E., Couteau, G., Gilboa, N., Ishai, Y., Kohl, L., and
Scholl, P. (2019b). Efficient pseudorandom correlation
generators: Silent OT extension and more. In Advances
in Cryptology – CRYPTO.
Burra, S. S., Larraia, E., Nielsen, J. B., Nordholt, P. S., Or-
landi, C., Orsini, E., Scholl, P., and Smart, N. P. (2021).
High-performance multi-party computation for binary
circuits based on oblivious transfer. J. Cryptology.
Capkun, S., Ganeriwal, S., Anjum, F., and Srivastava, M.
(2011). Secure RSS-based localization in sensor net-
works. Technical Report/ETH Zurich, Department of
Computer Science.
Chawla, K., McFarland, C., Robins, G., and Shope, C.
(2013). Real-time RFID localization using RSS. In
ICL-GNSS.
Chen, H., Chillotti, I., Dong, Y., Poburinnaya, O., Razen-
shteyn, I. P., and Riazi, M. S. (2020). SANNS: Scaling
up secure approximate k-nearest neighbors search. In
USENIX Security.
Chen, L., Kuusniemi, H., Chen, Y., Pei, L., Kr
¨
oger, T., and
Chen, R. (2011). Information filter with speed detec-
tion for indoor Bluetooth positioning. In ICL-GNSS.
Chen, L., Thombre, S., J
¨
arvinen, K., Lohan, E. S., Al
´
en-
Savikko, A., Lepp
¨
akoski, H., Bhuiyan, M. Z. H., Bu-
Pasha, S., Ferrara, G. N., Honkala, S., Lindqvist, J.,
Ruotsalainen, L., Korpisaari, P., and Kuusniemi, H.
(2017). Robustness, security and privacy in location-
based services for future IoT: A survey. IEEE Access.
Demmler, D., Schneider, T., and Zohner, M. (2015). ABY –
a framework for efficient mixed-protocol secure two-
party computation. In NDSS.
Gilboa, N. (1999). Two party RSA key generation. In
Advances in Cryptology – CRYPTO.
Goldreich, O., Micali, S., and Wigderson, A. (1987). How
to play any mental game. In STOC.
Guan, T., Fang, L., Dong, W., Hou, Y., and Qiao, C. (2017).
Indoor localization with asymmetric grid-based filters
in large areas utilizing smartphones. In IEEE ICC.
Haeberlen, A., Flannery, E., Ladd, A. M., Rudys, A., Wal-
lach, D. S., and Kavraki, L. E. (2004). Practical robust
localization over large-scale 802.11 wireless networks.
In MobiCom.
Hakkarainen, A., Werner, J., Costa, M., Lepp
¨
anen, K., and
Valkama, M. (2015). High-efficiency device localiza-
tion in 5G ultra-dense networks: Prospects and en-
abling technologies. In IEEE Vehicular Technology
Conference.
Hallgren, P., Orlandi, C., and Sabelfeld, A. (2017). Pri-
vatePool: Privacy-preserving ridesharing. In IEEE
CSF.
He, S., Lin, W., and Chan, S.-H. G. (2017). Indoor localiza-
tion and automatic fingerprint update with altered AP
signals. IEEE Transactions on Mobile Computing.
Ishai, Y., Kilian, J., Nissim, K., and Petrank, E. (2003).
Extending oblivious transfers efficiently. In Advances
in Cryptology – CRYPTO.
J
¨
arvinen, K., Kiss,
´
A., Schneider, T., Tkachenko, O., and
Yang, Z. (2018). Faster privacy-preserving location
proximity schemes. In CANS.
J
¨
arvinen, K., Lepp
¨
akoski, H., Lohan, E. S., Richter, P.,
Schneider, T., Tkachenko, O., and Yang, Z. (2019).
PILOT: Practical privacy-preserving Indoor Localiza-
tion using OuTsourcing. In EuroS&P.
Kolesnikov, V. and Schneider, T. (2008). Improved garbled
circuit: Free XOR gates and applications. In ICALP.
Konstantinidis, A., Chatzimilioudis, G., Zeinalipour-Yazti,
D., Mpeis, P., Pelekis, N., and Theodoridis, Y. (2016).
Privacy-preserving indoor localization on smartphones.
In IEEE International Conference on Data Engineer-
ing.
FAPRIL: Towards Faster Privacy-preserving Fingerprint-based Localization
119

Ladd, A. M., Bekris, K. E., Rudys, A., Kavraki, L. E., and
Wallach, D. S. (2005). Robotics-based location sensing
using wireless ethernet. Wireless Networks.
Langlois, C., Tiku, S., and Pasricha, S. (2017). Indoor local-
ization with smartphones: Harnessing the sensor suite
in your pocket. IEEE Consumer Electronics Magazine.
Li, B., Wang, Y., Lee, H. K., Dempster, A., and Rizos, C.
(2005). Method for yielding a database of location
fingerprints in WLAN. IEEE Proceedings – Communi-
cations.
Li, H., Sun, L., Zhu, H., Lu, X., and Cheng, X. (2014).
Achieving privacy preservation in WiFi fingerprint-
based localization. In INFOCOM.
Li, R., Song, T., Capurso, N., Yu, J., Couture, J., and Cheng,
X. (2017). IoT applications on secure smart shopping
system. IEEE Internet of Things Journal.
Lindell, Y. and Pinkas, B. (2009). A proof of security of
Yao’s protocol for two-party computation. J. Cryptol-
ogy.
Liu, H., Darabi, H., Banerjee, P., and Liu, J. (2007). Survey
of wireless indoor positioning techniques and systems.
IEEE Transactions on Systems, Man, and Cybernetics,
Part C (Applications and Reviews).
Lohan, E. S., Richter, P., Sabola, V. L., Lopez-Salcedo, J. A.,
Seco-Granados, G., Lepp
¨
akoski, H., and Santiago, E. S.
(2017a). Location privacy challenges and solutions –
parts I and II. Inside GNSS.
Lohan, E. S., Torres-Sospedra, J., Lepp
¨
akoski, H., Richter, P.,
Peng, Z., and Huerta, J. (2017b). Wi-Fi crowdsourced
fingerprinting dataset for indoor positioning. Data.
Mendoza-Silva, G. M., Richter, P., Torres-Sospedra, J., Lo-
han, E. S., and Huerta, J. (2018). Long-term WiFi
fingerprinting dataset for research on robust indoor
positioning. Data.
Mishra, P. K., Rathee, D., Duong, D. H., and Yasuda, M.
(2021). Fast secure matrix multiplications over ring-
based homomorphic encryption. Inf. Secur. J. A Glob.
Perspect.
Mohassel, P., Rosulek, M., and Trieu, N. (2020). Practi-
cal privacy-preserving k-means clustering. Proc. Priv.
Enhancing Technol.
Nieminen, R. and J
¨
arvinen, K. (2020). Practical privacy-
preserving indoor localization based on secure two-
party computation. IEEE Transactions on Mobile Com-
puting.
Noh, A. S. I., Lee, W. J., and Ye, J. Y. (2008). Comparison
of the mechanisms of the Zigbee’s indoor localization
algorithm. In IEEE/ACIS Software Engineering, Artifi-
cial Intelligence, Networking, and Parallel/Distributed
Computing.
Paillier, P. (1999). Public-key cryptosystems based on com-
posite degree residuosity classes. In Advances in Cryp-
tology – EUROCRYPT.
Patra, A., Schneider, T., Suresh, A., and Yalame, H. (2021).
ABY2.0: Improved mixed-protocol secure two-party
computation. In USENIX Security.
Rathee, D., Schneider, T., and Shukla, K. (2019). Improved
multiplication triple generation over rings via RLWE-
based AHE. In CANS.
Riazi, M. S., Weinert, C., Tkachenko, O., Songhori, E. M.,
Schneider, T., and Koushanfar, F. (2018). Chameleon:
A hybrid secure computation framework for machine
learning applications. In ASIACCS.
Richter, P., Yang, Z., Tkachenko, O., Lepp
¨
akoski, H., J
¨
arvi-
nen, K., Schneider, T., and Lohan, E. S. (2018). Re-
ceived signal strength quantization for secure indoor
positioning via fingerprinting. In ICL-GNSS.
Rosulek, M. and Roy, L. (2021). Three halves make a whole?
beating the half-gates lower bound for garbled circuits.
In CRYPTO.
Shaul, H., Feldman, D., and Rus, D. (2020). Secure k-ish
nearest neighbors classifier. Proc. Priv. Enhancing
Technol.
Shu, T., Chen, Y., Yang, J., and Williams, A. (2014). Multi-
lateral privacy-preserving localization in pervasive en-
vironments. In INFOCOM.
Songhori, E. M., Hussain, S. U., Sadeghi, A., and Koushan-
far, F. (2015). Compacting privacy-preserving k-
nearest neighbor search using logic synthesis. In ACM
DAC.
Stirbys, S., Nabah, O. A., Hallgren, P., and Sabelfeld, A.
(2017). Privacy-preserving location-proximity for mo-
bile apps. In IEEE Parallel, Distributed and Network-
based Processing.
Talvitie, J. and Lohan, E. S. (2013). Modeling received sig-
nal strength measurements for cellular network based
positioning. In ICL-GNSS.
van der Beets, C., Nieminen, R., and Schneider, T. (2022).
FAPRIL: Towards faster privacy-preserving fingerprint-
based localization. Cryptology ePrint Archive, Report
2022/564. https://ia.cr/2022/564.
Wang, L., Aono, Y., and Phong, L. T. (2017). A new secure
matrix multiplication from Ring-LWE. In CANS.
Yang, Z. and J
¨
arvinen, K. (2018). The death and rebirth of
privacy-preserving WiFi fingerprint localization with
Paillier encryption. In INFOCOM.
Yao, A. C. (1986). How to generate and exchange secrets.
In FOCS.
Yassin, A., Nasser, Y., Awad, M., Al-Dubai, A., Liu, R.,
Yuen, C., Raulefs, R., and Aboutanios, E. (2017). Re-
cent advances in indoor localization: A survey on theo-
retical approaches and applications. IEEE Communi-
cations Surveys & Tutorials.
Yin, Z., Wu, C., Yang, Z., and Liu, Y. (2017). Peer-to-peer
indoor navigation using smartphones. IEEE Journal
on Selected Areas in Communications.
Zahur, S., Rosulek, M., and Evans, D. (2015). Two halves
make a whole - reducing data transfer in garbled cir-
cuits using half gates. In Advances in Cryptology –
EUROCRYPT.
Ziegeldorf, J. H., Viol, N., Henze, M., and Wehrle, K. (2014).
Poster: Privacy-preserving indoor localization. ACM
WiSec.
Zuber, M. and Sirdey, R. (2021). Efficient homomorphic
evaluation of k-NN classifiers. Proc. Priv. Enhancing
Technol.
SECRYPT 2022 - 19th International Conference on Security and Cryptography
120
