
Comparison-based MPC in Star Topology
Gowri R. Chandran
1
, Carmit Hazay
2
, Robin Hundt
1
and Thomas Schneider
1
1
TU Darmstadt, Germany
2
Bar-Ilan University, Israel
Keywords:
Secure Multi-party Computation, k
th
Ranked Element, Scheduling Problems, Optimisation Problems.
Abstract:
With the large amount of data generated nowadays, analysis of this data has become eminent. Since a vast
amount of this data is private, it is also important that the analysis is done in a secure manner. Comparison-based
functions are commonly used in data analysis. These functions use the comparison operation as the basis.
Secure computation of such functions have been discussed for median by Aggarwal et al. (EUROCRYPT’04)
and for convex hull by Shelat and Venkitasubramaniam (ASIACRYPT’15).
In this paper, we present a generic protocol for the secure computation of comparison-based functions. In order
to scale to a large number of participants, we propose this protocol in a star topology with an aim to reduce the
communication complexity. We also present a protocol for one specific comparison-based function, the
k
th
ranked element. The construction of one of our protocols leaks some intermediate values but does not reveal
information about an individual party’s inputs. We demonstrate that our protocol offers better performance than
the protocol for k
th
ranked element by Tueno et. al. (FC’20) by providing an implementation.
1 INTRODUCTION
Data is being constantly generated by organisations as
well as individuals. To leverage this massive volume
of unstructured data, organisations seek to use data
analysis techniques. Data analysis can benefit organi-
sations in various ways. For example, businesses can
learn more about their target group by running analy-
sis on the consumers trends, multiple companies can
run analysis on their combined data to compare vari-
ous data points such as salaries of employees, the key
performance indicator, etc., hospitals and healthcare
companies analyse their data using artificial intelli-
gence and machine learning to obtain faster and more
accurate diagnosis. In addition to using the data for
analytics, these organisations, at times, wish to keep
the data private as it contains sensitive information. In
all the above mentioned examples the data being anal-
ysed is sensitive. In cases such as that of healthcare
companies, the sharing of patient’s data is forbidden by
law. The analysis therefore has to be done in a manner
which does not reveal the inputs. This is where secure
Multiparty Computation (MPC) comes into play.
For the past couple of decades, MPC has been a
prominent field of research. Starting with the seminal
works of (Yao, 1982; Goldreich et al., 1987; Beaver
et al., 1990) it is still a widely researched topic with re-
cent works like (Lindell et al., 2015; Wang et al., 2017;
Choudhuri et al., 2020). The problem of secure MPC
focuses on a group of parties that do not trust each
other, but still wish to compute a function
f
of their
inputs while keeping their inputs private. Namely, it
allows a set of mutually distrusting parties to securely
compute a function on their joint inputs without re-
vealing anything about their inputs except what can
be inferred by the output. In the real world, there are
adversaries present that may act maliciously to gain
more information than they are supposed to. Semi-
honest adversaries follow the protocol as it is but try
to learn more information from the messages. In cases
where companies or organisations run the protocol,
semi-honest security is a realistic assumption, as the
organisations would not deviate from the protocol for
their reputation’s sake. Another factor that is consid-
ered for the construction of an MPC protocol is the
number of parties that are corrupted by the adversary.
In our work, we consider semi-honest adversaries and
a dishonest majority, i.e.,
n−1
parties can be corrupted
by the adversary.
One of the standard approaches to implement con-
stant round MPC used in (Beaver et al., 1990; Ben-
David et al., 2008; Kolesnikov et al., 2009; Lindell
et al., 2015; Lindell et al., 2016) is by using Garbled
Circuits proposed by Yao (Yao, 1982), by converting
the function to be computed to a boolean circuit and
privately evaluating the gates. Alternatively, the MPC
protocol by Goldreich, Micali and Wigderson (Gol-
dreich et al., 1987), which also uses a boolean rep-
Chandran, G., Hazay, C., Hundt, R. and Schneider, T.
Comparison-based MPC in Star Topology.
DOI: 10.5220/0011144100003283
In Proceedings of the 19th International Conference on Security and Cryptography (SECRYPT 2022), pages 69-82
ISBN: 978-989-758-590-6; ISSN: 2184-7711
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
69

resentation, works by secret sharing the wire values
amongst the parties. This protocol has been improved
and implemented in (Choi et al., 2012; Boyle et al.,
2021). All the aforementioned protocols are generic
MPC protocols which can be used to implement any
function f by converting it to a boolean circuit.
Another line of works considers the development
of protocols for specific functions to achieve im-
proved efficiency by exploiting the properties of the
underlying function and optimising the concrete pro-
tocols accordingly. Several works have proposed
protocols for specific functions such as private set-
intersection (Hazay and Venkitasubramaniam, 2017;
Inbar et al., 2018; Pinkas et al., 2018; Rosulek and
Trieu, 2021) for finding the intersection of multiple
sets, secure pattern matching (Hazay and Lindell,
2008; Hazay and Toft, 2010; Yasuda et al., 2013; Faust
et al., 2013) for finding matching patterns in texts and
RSA key generation (Frederiksen et al., 2018; Hazay
et al., 2019; Chen et al., 2021) for generation of the
RSA modulus. Relevant to our work, in (Garay et al.,
2007; Damg
˚
ard et al., 2007; Damg
˚
ard et al., 2008;
Kolesnikov et al., 2009; Couteau, 2016), protocols for
the secure comparison of integers have been proposed
using various techniques.
The computation of these specific functions can be
optimised by reducing the function
f
to the compu-
tation of smaller/easier computable primitives. One
method is to reduce the secure computation of
f
into
the secure evaluation of a boolean circuit. Another
technique is to reduce the function
f
to multiple in-
stances of a smaller function and perform a secure
computation of this primitive. The latter reduction
technique is used in (Shelat and Venkitasubramaniam,
2015) to reduce
f
to the comparison function, which
takes two integer inputs and returns
1
if the first input
is smaller than the second and
0
otherwise. Here the
authors present a two-party protocol for the compu-
tation of a class of functions, where the parties only
interact for implementing the comparison function.
This reduction results in a much more efficient proto-
col, as the parties only communicate to evaluate the
comparison function.
The comparison-based functions considered
in (Shelat and Venkitasubramaniam, 2015) are widely
used for various data analytic purposes. They include
functions such as finding the convex hull, finding the
median, job scheduling problems, matroid optimisa-
tions and many more optimisation problems. One of
the functions that we discuss in detail in our work is
the convex hull. The convex hull of a set of points is
the smallest convex set which contains all the points
in that set. We also discuss job scheduling, which is
an optimisation algorithm where multiple parties have
jobs that require the use of a common resource and the
jobs are assigned to the resource at a specific time.
These functions have important real world appli-
cations. For instance, the secure computation of the
convex hull of a set is useful in tracking a disease epi-
demic, where the extent of the spread of a disease can
be monitored without revealing all the locations of the
infected patients. A two-party variant of this problem
is discussed in (Shelat and Venkitasubramaniam, 2015)
where the authors use the Gift Wrapping Algorithm
for computing the convex hull. Scheduling problems,
such as job scheduling, have many applications in set-
tings where the resources are limited and more than
one user wishes to use them. Secure job scheduling
can be used in applications where the details of the job
(e.g. duration, amount of resource used etc.) are to be
kept private, for instance in booking appointments at a
doctor’s, where the time taken is kept private.
Another functionality that we consider is finding
the
k
th
ranked element of the union of multiple sorted
sets. This function has applications in financial and
medical analysis. (Aggarwal et al., 2004) present a
secure protocol for the computation of the
k
th
ranked
element, where the
k
th
ranked element is computed
using the binary search algorithm. Following that, a
constant round protocol for this function is presented
in (Tueno et al., 2020), where the protocol is presented
in a star topology with all the parties communicating
only with a dedicated server.
In instances where multiple organisations wish to
jointly analyse their data, often the communication
occurs via WAN connections, making communication
the bottleneck for running the protocol, as most organ-
isations have high computational power. Therefore,
protocols with low communication complexity are cru-
cial. One method to achieve this is by constructing
the protocols in a star network topology. The parties
would then only need to communicate to one central
party. The central party has its own input for the com-
putation and also interacts with all the other parties in
a series of secure two-party computations. This elimi-
nates the need for broadcast channels, thus reducing
the communication complexity.
1.1 Our Contribution and Outline
In this paper, we explore the concrete efficiency of
comparison-based functions, i.e. a class of functions
that can be reduced to a secure computation of compar-
ison of integers. We present two different protocols for
this class of functions. The first is a generic protocol
(see §3) for secure computation of a class of functions
called the Greedy Compatible functions (see §2.1)
where we extend the two-party protocol from (She-
SECRYPT 2022 - 19th International Conference on Security and Cryptography
70

lat and Venkitasubramaniam, 2015). We implement a
reduction technique to reduce the computation of the
function to a multi-party computation of the minimum
of
n
integers and propose an efficient new method
for computing the minimum. Next, we give concrete
instantiations (see §3.2) of a few functions demonstrat-
ing the practical applications of our protocol. To the
best of our knowledge, there have not been any pre-
vious works on specific multi-party protocols for the
other two problems, i.e. convex hull and job schedul-
ing. We show that our multi-party protocol can be used
for the computation of these functions and that it has
better performance compared to specific approaches
and to generic MPC protocols that can be used for any
of these functions.
Lastly, we present an alternative way of comput-
ing the
k
th
ranked element (see §4) by using reduction
techniques similar to the generic protocol. Our proto-
col is the first that uses these reduction techniques to
compute this function in a star topology. If the proto-
col is instantiated in a star topology, the computation
of this function can be reduced to a secure computation
of a summation function. Then communication only
occurs during the computation of the summations, and
the remaining computations are done locally by the
parties and the comparisons are done locally by the
central party. In particular, we reduce the computation
of the
k
th
ranked element to a computation of secure
summation which is instantiated using a threshold ho-
momorphic encryption scheme and is implemented in
a star topology where one of the participating parties
plays the central party which interacts with the rest of
the parties.
We note that our protocol for the
k
th
ranked ele-
ment leaks the intermediate result of the summations
to the central party. This leakage can reveal the dis-
tribution of the data in the union of sets. For some
applications, revealing the distribution of data is a
tolerable leakage. A potential approach for protect-
ing this leakage can be by using differential privacy
by revealing only the differentially private leakage.
Combining MPC with differentially private tools has
been used previously in (Groce et al., 2019) to achieve
cheaper private set intersection by allowing differen-
tially private leakage. In (He et al., 2017) the problem
of private record linkage with differentially private
leakage is studied. Sometimes, allowing some leakage
can result in a more efficient protocol. There have
been many works that discuss this trade-off on privacy
for better performance. In (Cash et al., 2013; Pappas
et al., 2014) some information related to the search
queries is leaked in order to achieve more efficient
database search functionalities. We leave the idea of
using differentially private leakage for future work.
1.2 Related Work
Here, we mention several closely related works.
The development of general-purpose MPC started
with (Goldreich et al., 1987) and is still a major area of
research with seminal works like (Franklin and Haber,
1996; Cramer et al., 2001; Ben-Efraim et al., 2016; Lin-
dell et al., 2016; Ananth et al., 2019). These protocols
can be used to instantiate the function for finding the
minimum integer, which is one of the major underly-
ing computations of our generic protocol. If we use the
multi-party protocol in (Ananth et al., 2019) to instan-
tiate the computation of minimum function, the result-
ing communication complexity is
O(κnd log nlogd)
with
2
rounds, where
κ
is the security parameter,
n
is
the number of parties, and
d
is the input size. This pro-
tocol uses functional encryption combiners to achieve
a constant round multi-party computation protocol,
and although introducing good asymptotic results, it is
not practical enough for an implementation.
Often specific purpose protocols are developed to
replace the use of generic MPC and improve the per-
formance. There has been abundant work done to de-
velop protocols specifically for the secure comparison
of two integers. In (Damg
˚
ard et al., 2007; Damg
˚
ard
et al., 2008), homomorphic encryption is used to build
a protocol for the two-party comparison of integers.
Using either of these protocols for computing the mini-
mum, a communication complexity of
O(nd(d +κ))
is
achieved with
O(logn)
rounds. In (Garay et al., 2007),
a two-party protocol for the comparison of integers
is presented using the encryption scheme of (Cramer
et al., 2001). Using this protocol to implement the min-
imum function the online communication complexity
is
O(nd)
with a round complexity of
O(logn logd)
.
In (Couteau, 2016), the authors use a block decompo-
sition technique to compare the blocks of the integer
and execute the comparison with Oblivious Transfer
as a building block. By implementing the minimum
function using (Couteau, 2016), an online communi-
cation complexity of
O(nd)
is achieved with a round
complexity of
O(logn loglogd)
. We compare the effi-
ciency of our implementation of the minimum function
with that of instantiating it with any of the above pro-
tocols in Tab. 1.
In (Tueno et al., 2020), a constant round protocol
for the computation of the
k
th
ranked element is pre-
sented. The protocol is presented in a star network
topology where the clients interact with a server. Un-
like this setup, the central party in our protocol is one
of the parties participating in the protocol and also
provides input. Tueno et al. present several protocols
in (Tueno et al., 2020), using different building blocks.
The protocol using the garbled circuit approach has a
Comparison-based MPC in Star Topology
71

Table 1: Comparison of complexities for the computation of minimum function for
n
parties, using generic multi-party protocols
((Franklin and Haber, 1996; Ananth et al., 2019)) or two-party comparison protocols ((Garay et al., 2007; Damg
˚
ard et al., 2007;
Damg
˚
ard et al., 2008; Couteau, 2016)) with our garbled circuit-based approach. Here,
κ
is the security parameter,
d
is the
length of the input and n is the number of parties.
(Franklin and Haber, 1996) (Garay et al., 2007) (Damg
˚
ard et al., 2007; Damg
˚
ard et al., 2008) (Couteau, 2016) (Ananth et al., 2019) This work
Offline comm. — O(κnd/logκ) — O(κd/logκ) — O(κd)
Online comm. O(n
2
) O(nd) O(nd(d + κ)) O(nd) O(κnd logn logd) O(κnd)
Rounds O(logn) O(log nlog d) O(logn) O(logn loglog d) 2 O(logn)
Assumption DDH OT DGK OT LWE OT
Table 2: Comparison of protocols for secure computation
of the
k
th
ranked element. We compare our protocol with
the one in (Aggarwal et al., 2004) and the three protocols
presented in (Tueno et al., 2020) that are based on Yao’s
garbled circuit (YGC) and additively homomorphic encryp-
tion(AHE).
n
is the number of parties,
κ
is the security pa-
rameter,
d
is the bit-length of the input,
t
is the threshold
of the additive homomorphic scheme, and
S
is the range of
elements in the database.
(Aggarwal et al., 2004) (Tueno et al., 2020) This work
YGC AHE1 AHE2
Comm. O(n
2
logS) O(κn
2
) O(κn
2
dt) O(κn
2
dt) O(nlog S)
Rounds logS 4 4 4 logS
total communication complexity of
O(κn
2
)
, while the
protocol using an additively homomorphic encryption
scheme has a communication complexity of
O(κn
2
dt)
,
where
t
is the threshold of the homomorphic encryp-
tion scheme. Our work achieves a communication
complexity of
O(κnlog S)
, where
S
is the range of el-
ements in the database, and a round complexity of
O(logS)
rounds. We provide a comparison of our
work and the previous works on the
k
th
ranked ele-
ment in Tab. 2.
2 PRELIMINARIES
In this section we define some basic cryptographic
primitives that are used in our protocols.
2.1 Greedy Compatible Functions
A function
f
is said to be Greedy Compatible (Shelat
and Venkitasubramaniam, 2015), if
f
on the union of
given sets can be defined using two functions
F
MIN
and
F
UPT
, such that these functions have a few specific
properties as specified in definition 1.
Definition 1 (Greedy Compatible Functions). The nec-
essary and sufficient conditions for a function
f
to be
Greedy Compatible are:
1.
Unique solution: Given inputs
X
i
,
i = [1,n]
there
is a unique solution.
2.
Unique order: The output
(c
1
,...c
l
)
is released in
a unique order, i.e.,
f (X
1
,...,X
n
) = (c
1
,...c
l
)
where
c
1
= F
UPT
(⊥,
S
X
i
)
and
c
i+1
=
F
UPT
((c
1
,...,c
j
),
S
X
i
) for i = [1,l − 1].
3.
Local updatability: The function
F
UPT
on the union
of all sets can be computed by computing the func-
tion
F
UPT
on each set individually and then com-
puting F
MIN
on its result. Namely,
F
UPT
((c
1
,...,c
j
),
[
X
i
) =
F
MIN
(F
UPT
((c
1
,...,c
j
),X
1
),...,F
UPT
((c
1
,...,c
j
),X
n
)).
2.2 Oblivious Transfer
1-out-of-2 Oblivious Transfer (OT) is a two-party pro-
tocol run between a sender
S
and a receiver
R
. The
sender
S
inputs a pair of
l
-bit strings
s
0
,s
1
∈ {0,1}
l
and
R
inputs a choice bit
b ∈ {0, 1}
. At the end of
the protocol,
R
learns the chosen string
s
b
, but noth-
ing about the unchosen string
s
1−b
, whereas
S
learns
nothing about the choice bit b.
Oblivious Transfer Extension. OT protocols require
costly public-key cryptography, but their performance
can be improved using OT extension (Ishai et al., 2003;
Asharov et al., 2013). OT extension allows extending a
few public key-based base OTs using only symmetric
cryptography and a constant number of rounds.
2.3 Garbled Circuits
An efficient way to evaluate a boolean circuit
C
in
a constant number of rounds is Yao’s garbled cir-
cuit (Yao, 1986; Lindell and Pinkas, 2004). In this
approach, the circuit constructor
S
creates a garbled
circuit
e
C
as follows: for each wire
W
i
of the circuit,
S
randomly chooses two garbled values
e
w
0
i
,
e
w
1
i
, where
e
w
j
i
represents the value
j
of
W
i
. Further, for each gate
G
i
,
S
creates a garbled table
e
T
i
with the following prop-
erty: given a set of garbled values of
G
i
’s inputs,
e
T
i
allows to recover the garbled value of the correspond-
ing
G
i
’s output, but nothing else.
S
sends these garbled
tables, called garbled circuit
e
C
to the evaluator
C
. Ad-
ditionally,
C
obliviously (via OT) obtains the garbled
inputs
e
w
i
corresponding to the inputs of both parties.
Now
C
can evaluate the garbled circuit by evaluating
e
C
gate by gate, using the garbled tables
e
T
i
. Finally,
C
SECRYPT 2022 - 19th International Conference on Security and Cryptography
72

translates the garbled output into the output values
given for the respective parties.
2.4 Gift-Wrapping Algorithm
The Gift Wrapping algorithm (Jarvis, 1973) for finding
the convex hull of a set works as follows: the first point
in the convex hull is the leftmost point of the set. From
this point a vertical line is considered. Then this line is
rotated in a clockwise direction until it touches another
point in the set. The first point that touches this line
is the second point of the convex hull. Then a vertical
line is considered from this point and again rotated in
a clockwise direction. This process continues till the
last point that falls on the rotation line is the first point
of the convex hull.
3 COMPARISON-BASED
FUNCTIONS
Here we propose an extension to the two-party proto-
col in (Shelat and Venkitasubramaniam, 2015), where
a secure protocol to compute a class of functions called
Greedy Compatible functions(cf. §2.1) is discussed.
We extend their protocol to the multi-party setting and
propose optimisations for the multi-party computation
of the minimum function.
The Greedy Compatible functions can be defined in
an iterative manner with all the computations done lo-
cally by each party except for computing the minimum.
After each iteration, the output is slowly released so
that the final output of the computation is the tuple of
outputs from each iteration. Furthermore, the output
of each iteration is given as the input for the next it-
eration. The only step where the parties interact with
each other is for computing the minimum. We propose
to reduce the communication between the parties by
constructing the protocol in a star topology. Thus the
parties only communicate with one central party which
eliminates the need for broadcast channels.
As discussed above, the parties first compute a
part of the function locally and then the minimum
together. Consequently, the protocol
π
GP
(Fig. 3)
for computing the function
f
involves instantiating
two sub-functionalities: first, the local update func-
tion
F
UPT
(Fig. 1) and second, the minimum function
F
MIN
(Fig. 2). The functionality
F
UPT
updates the in-
put of each party for the computation of the minimum
functionality. The output of
F
UPT
is the input of
F
MIN
for the next iteration of the protocol.
F
UPT
is computed
locally by each party, where its inputs are the party
P
i
’s
set of elements
X
i
and the output of
F
MIN
. The output
of
F
UPT
is the pair
(x
i
,δ
i
)
.
F
MIN
takes
(x
i
,δ
i
)
as input
and computes the minimum of all values
δ
i
and then
returns the x
i
corresponding to the smallest δ
i
.
Now, combining these two functionalities we de-
scribe the protocol
π
GP
for securely computing
f
. In
the initialisation step, the parties locally compute their
first input pair by calling the functionality
F
UPT
on the
set
X
i
. Then the iteration begins; for the first iteration,
the parties send their input pair
(x
1
i
,δ
1
i
)
to the func-
tionality
F
MIN
, which computes
min{δ
1
1
,δ
1
2
,...,δ
1
n
}
and
returns some
c
1
= x
1
t
corresponding to the smallest
δ
1
t
. Then the parties update their inputs for the next
iteration by calling
F
UPT
on
c
1
and
X
i
. The protocol
runs for
j = 1,...,l
iterations, with
l
depending on the
computed function. As mentioned earlier, the protocol
releases the output slowly, i.e., after each iteration, the
parties receive
c
j
, which is a part of the final output
(c
1
,c
2
,...,c
l
).
Functionality F
UPT
This functionality is computed locally by each party P
i
.
Input: The set of elements
X
i
and the outputs
(c
1
,...,c
j
)
obtained by the previous iterations.
•
In the initial step, given input
(⊥,X
i
)
,
F
UPT
computes
party
P
i
’s input for
F
MIN
for the first iteration denoted
by (x
1
i
,δ
1
i
).
•
In the
j
th
iteration, given input
((c
1
,...,c
j
),X
i
)
,
F
UPT
computes party
P
i
’s input for
F
MIN
for the
( j + 1)
th
iteration denoted by (x
j+1
i
,δ
j+1
i
).
Output:
(x
j+1
i
,δ
j+1
i
)
where
x
j+1
i
∈ X
i
and
δ
j+1
i
is the
associated index.
Figure 1: Local update function.
Functionality F
MIN
Parties P
1
,..., P
n
participate in this computation.
Input: Each party
P
i
sends the pair
(x
i
,δ
i
)
, where
δ
i
is
an integer.
• Compute δ
t
= min{δ
1
,...,δ
n
}.
•
Sets
c = x
t
, where
x
t
has the corresponding index
δ
t
.
Output: c.
Figure 2: Minimum function.
Security. We state and prove the security of this proto-
col next.
Theorem 1. The class of Greedy Compatible func-
tions (cf. definition 1) is securely computed by protocol
π
GP
(Fig. 3) in the presence of semi-honest adversaries
for n ≥ 2 in the F
MIN
-hybrid.
Proof.
We prove the security of the protocol in a hy-
brid model, where the function
F
MIN
is computed by
Comparison-based MPC in Star Topology
73
Protocol π
GP
Input: Each party P
i
has a set of distinct elements X
i
.
The Protocol:
1.
Each party
P
i
locally computes
(x
1
i
,δ
1
i
) ←
F
UPT
(⊥,X
i
).
2. For j = [1,l] :
(a)
The parties call functionality
F
MIN
for inputs
(x
j
i
,δ
j
i
) to obtain output c
j
.
(b)
Each party
P
i
locally applies functionality
F
UPT
on its input
((c
1
,...,c
j
),X
i
)
, computing the output
(x
j+1
i
,δ
j+1
i
)
, which will serve as its input in the
next iteration.
Output: c
1
,...,c
l
.
Figure 3: Semi-honest protocol for a greedy compatible
function f .
a trusted third party. Consider
A
to be an adversary
that corrupts a subset
I
of the parties. Let
(c
1
,...c
l
)
be the final output of the computation. We construct
a simulator
S
that generates the view of
P
i
,
i ∈ I
.
S
is
given
P
i
’s input
X
i
and the output
(c
1
,...,c
l
)
, then
S
works as follows:
1.
Given
X
i
,
i ∈ I
and
(c
1
,...,c
l
)
, the simulator
S
in-
vokes the corrupted parties on their corresponding
inputs.
2. S
plays the honest parties’ role against the cor-
rupted parties on arbitrary sets of inputs.
3.
In the
j
th
iteration, given the inputs
{(x
j
i
,δ
j
i
)}
i∈I
to F
MIN
, S simulates c
j
as the output of F
MIN
.
In this case, the view of the corrupted party in the
simulation is identical to that in the real execution of
the protocol. From the unique ordering property of
the solution, the two views are identical. Hence, the
protocol
π
GP
securely computes any function
f
in the
presence of semi-honest adversaries.
Complexity. In protocol
π
GP
, communication occurs
only during the execution of
F
MIN
. Let
O(C)
be the
communication complexity of
F
MIN
and
l
be the num-
ber of rounds of the protocol. Since the parties execute
F
MIN
once per round, the total communication com-
plexity is
O(lC)
. We discuss the total complexity of
the protocol in §3.1.
3.1 Realising F
MIN
Recall that during the execution of
π
GP
, communica-
tion between the parties only occurs during the in-
stantiation of
F
MIN
. To reduce this communication,
we propose an efficient way of computing the mini-
mum function by splitting the multi-party computation
of
F
MIN
into a series of two-party computations. We
achieve this by performing the comparisons pairwise.
Thus, we implement
F
MIN
in a star network topology
where all the parties interact with one central party
(say
P
1
) and not with any other party. This implies that
the protocol
π
GP
can be implemented in a star topology
as well. We define the pairwise computation of
F
MIN
in Fig. 4.
Protocol F
2
MIN
Parties P
1
,..., P
n
participate in this computation.
Input: Each party
P
i
sends the pair
(x
i
,δ
i
)
, where
δ
i
is
an integer.
Let a and b be variables.
• (a,b) = (x
1
,δ
1
).
• For i = [2, n],
(a,b) = (x
i
,δ
i
), i f δ
i
< b
• c = a
Output: Each party receives
c = x
t
such that
δ
t
=
min{δ
1
,...,δ
n
} for t ∈ [1,n].
Figure 4: Protocol for minimum function using pairwise
comparisons.
Correctness. The correctness follows directly from a
linear search algorithm.
Instantiation. We instantiate the pairwise compar-
isons using garbled circuits and construct the protocol
in a star topology. Therefore, all communications be-
tween the parties happen via party P
1
.
Our protocol is based on the idea of mobile
agents (Cachin et al., 2000) that chains together mul-
tiple garbled circuit computations. We consider party
P
1
to be the originator of the mobile agents protocol.
Then the remaining parties are the hosts. The proto-
col works as follows:
P
1
generates the message for
n − 1
parallel OTs. The next party, i.e.,
P
2
constructs
a circuit using the output of
P
1
and sends it to
P
3
via
P
1
.
P
3
then generates a circuit using
P
2
’s output and
sends it to
P
4
via
P
1
. The parties continue similarly
till the last party
P
n
sends the circuit to
P
1
and
P
1
eval-
uates the final circuit to obtain the final output. This
construction can be modified to a binary tree based
structure, where parties
P
2i
, for
i = 1,...,⌊n/2⌋
can par-
allely run the second step and send the circuits to
P
2i+1
,
for
i = 1, ...,⌊(n−1)/2⌋
. In the third step, parties
P
2i+1
construct their circuits based on the received circuits
and send it to party
P
4i+1
, for
i = 1,..., ⌊n/4⌋
. We can
also view this communication pattern as an evaluation
of a hypercube, as presented in (Inbar et al., 2018),
where each party represents a vertex of the cube.
SECRYPT 2022 - 19th International Conference on Security and Cryptography
74

Complexity. We first discuss the complexity for com-
puting F
MIN
and then compute the total complexity of
the protocol π
GP
.
The number of rounds required for the computation
of the minimum is
O(logn)
. To increase the computa-
tion efficiency, we use OT extensions instead of plain
OTs. As the precomputation for the OT extensions can
be done in parallel, the communication complexity of
the precomputation is
O(κd)
, where
d
is the size of
the input. The total number of comparisons performed
for each minimum function is
n − 1
, hence the total
communication complexity is O(κnd).
We can instantiate the minimum functionality us-
ing either specific two-party protocols, or specific
multi-party protocol or even using generic multi-party
protocols. We now compare our results with those
of using existing protocols. If we instantiate the pair-
wise comparisons using a two-party protocol for in-
teger comparison (Couteau, 2016), it would require
O(logn loglogd)
rounds and would have a communi-
cation complexity of
O(nd)
. Using a generic MPC pro-
tocol (Ananth et al., 2019), we can compute the mini-
mum value in a constant number of rounds, with a com-
munication complexity of
O(κnd log nlogd)
. In Tab. 1,
we give a detailed comparison of the protocols.
Thus, we see that our garbled circuit-based ap-
proach gives the most efficient instantiation of
F
2
MIN
in
terms of communication complexity.
3.2 Concrete Instantiations of f
As discussed in §3, the protocol
π
GP
computes a class
of functions
f
. The main challenge in implementing
π
GP
is to define the functionalities
F
UPT
and
F
MIN
, such
that correctness still holds. For each
f
, the definition
of these functionalities changes according to
f
. Now
we discuss some examples of
f
in detail and show
how we can define
F
UPT
and
F
MIN
to realise the func-
tions. Specifically, we consider the following func-
tions: convex hull of a set and job scheduling. Two-
party protocol for computation of convex hull have
been given in (Shelat and Venkitasubramaniam, 2015).
We give the multi-party protocol for this function and
also present a new protocol for secure job schedul-
ing. We also discuss the computation of median of the
union of n sets in the full version of our paper.
3.2.1 Convex Hull
The convex hull of a set of points is the smallest convex
set, which contains all the points in that set. Suppose
there are
n
parties, each having a set of points. Then
the convex hull of the union of these sets is the small-
est convex set that contains all the points of all the
sets. There are various algorithms that are used to find
the convex hull of a set. Here we consider the Gift
Wrapping algorithm (Jarvis, 1973) (see §2.4) which is
the most efficient algorithm for this function.
Now, consider
n
parties and suppose each party
P
i
has a set
X
i
, then our objective is to compute the convex
hull of the union of these sets. Each element in
X
i
is
a point on a plane which is represented as
p
i
= (x
i
,y
i
)
where
x
i
and
y
i
are the
X
and
Y
coordinate of the
point, respectively. Now we apply the Gift Wrapping
Algorithm and define the functionality F
UPT
.
•
For
j = 1
,
F
UPT
(⊥,X
i
) = (p
1
i
,δ
1
i
)
, where
p
1
i
is the
leftmost point in the set
X
i
(i.e., the point with the
smallest
X
-coordinate) and
δ
1
i
is the
X
-coordinate
of p
1
i
.
•
For
j > 1
, if
p
i
∈ {c
1
,...,c
j−1
}
, then
P
i
sends
terminate
to
F
MIN
. Else,
F
UPT
((c
1
,..,c
j−1
),X
i
) =
(p
j
i
,δ
j
i
)
, where
p
j
i
is the point that makes the small-
est clockwise angle (larger than zero) with the ver-
tical dropped from
c
j−1
and
δ
j
i
is the magnitude
of the angle between the line joining
c
j−1
and
p
j
i
and the vertical from
c
j−1
. (The next point in the
convex hull is the point that makes the least clock-
wise angle with the point
p
j−1
. Hence, each party
sets its input for the next iteration by comparing
the angles.)
The functionality
F
MIN
is defined exactly as in Fig. 2.
Thus, the final output is
(c
1
,...,c
l
)
, where each
c
j
is
a point of the convex hull. The number of iterations
of the protocol is equal to the number of points on
the convex hull.
If there are three collinear points in
S
X
i
, the ro-
tation line will touch two points at the same time,
which will give the same angle
δ
i
for two points
p
i
,
which does not satisfy the properties of
f
in defini-
tion 1. Hence, we assume that no three points in the
set are collinear.
3.2.2 Job Scheduling
Job scheduling is an optimisation algorithm where
multiple parties have jobs that require the use of a
common resource and these jobs are assigned to the
resource at a particular time. Secure job scheduling
can be used in applications where the details of the job
(e.g., duration, amount of resource used, etc.) are to
be kept private, for example in a car-sharing service
where the clients would like to protect the information
about the usage of the car.
Here we consider a job scheduling problem with
one shared resource and multiple jobs. Consider
n
par-
ties, each party
P
i
having a set of jobs
J
i
= {b
1
i
,...,b
t
i
}
.
The goal is to find the order in which to assign these
jobs to a common resource
R
. We consider the Short-
est Job First (SJF) algorithm for the scheduling as this
Comparison-based MPC in Star Topology
75
algorithm gives the best average waiting time for the
parties. We instantiate the generic protocol in Fig. 3
to realise the function. The functionality
F
MIN
runs
exactly like in Fig. 2 and we define the functionality
F
UPT
as follows:
•
For
j = 1
,
F
UPT
(⊥,X
i
) = (b
i
,δ
i
)
, where
b
i
is the
shortest job in
J
i
and
δ
i
is the completion time
for b
i
.
•
For
j > 1
, if
J
i
⊆ {c
1
,...c
j−1
}
, then
F
UPT
((c
1
,...c
j−1
),J
i
) = (⊥,δ
i
)
where
δ
i
= ∞
.
If
b
t
i
∈ {c
1
,...c
j−1
}
, then
F
UPT
((c
1
,...c
j−1
),J
i
) =
(b
i
,δ
i
)
where
b
i
∈ J
i
\ {b
t
i
}
is the smallest job with
completion time
δ
i
. Else if
jb
t
i
∈ {c
1
,...c
j−1
}
,
then
F
UPT
((c
1
,...c
j−1
),J
i
) = (b
i
,δ
i
)
where
b
i
∈ J
i
is the shortest job and its completion time is δ
i
.
The final output is
(c
1
,...,c
j
)
, which gives the or-
der in which to assign the jobs to the resource
R
. The
protocol runs for N =
∑
i
|J
i
| iterations.
4 LEAKY k
th
RANKED ELEMENT
Now we focus on one specific comparison-based func-
tion, namely finding the k
th
ranked element of a set.
Recalling that protocol
π
GP
(in §3) computes
comparison-based functions that possess the proper-
ties specified in definition 1, it can therefore be im-
plemented for computing the
k
th
ranked element of a
union of sets. In this section, we construct a special
protocol for the computation of the
k
th
ranked element.
The protocol discussed here has a smaller communica-
tion complexity than a generic protocol computing this
function, as well as previous protocols for the com-
putation of this function. We also see that using this
specific protocol is more efficient than
π
GP
(from §3)
for computing the k
th
ranked element.
The functionality for finding the
k
th
ranked element
for
N
parties is defined by
F
k
(D
1
,...D
N
) 7→ (x
k
,...,x
k
)
,
where
x
k
is the
k
th
element of the union over all input
sets
D
i
. We present a Leaky
k
th
Ranked Element pro-
tocol
π
Leaky
k
(Fig. 7) that securely realises functionality
F
Leaky
k
(Fig. 6). We use the binary search algorithm for
finding the
k
th
element. This protocol works iteratively
and requires two summations and two comparisons per
iteration. We construct the protocol in a star network
topology, hence splitting the computations into a series
of secure two-party computations. By doing this, we
reduce the communication complexity, but leak the
result of the summations to the parties. This leakage
is discussed in detail in §4.1.
Now we present the Leaky protocol in detail. The
functionality
F
Leaky
k
(Fig. 6) computes the
k
th
ranked
Functionality F
k
Functionality
F
k
communicates with all parties
P
1
,...,P
n
and an adversary Sim.
•
Upon receiving
D
i
from each party, compute
x
k
,
where
x
k
is the
k
th
ranked element in
n
S
i=1
D
i
. Send
x
k
to the adversary
Sim
. If
Sim
responds OK, transmit
x
k
to all parties.
Figure 5: Functionality for computing the
k
th
ranked element
of a union of n sets.
Functionality F
Leaky
k
Functionality
F
Leaky
k
communicates with all parties
P
1
,...,P
n
and an adversary Sim.
• Receives (x
i
,y
i
) from each party.
•
Upon receiving
m
from party
P
1
, if
m = x
k
, where
x
k
is the
k
th
ranked element, the functionality sends
x
k
to all parties. If
m > x
k
, then
F
Leaky
k
sends
1
to all the
parties. Else, if m < x
k
, F
Leaky
k
sends 0 to all parties.
Figure 6: Leaky functionality for computing the
k
th
ranked
element of a union of n sets.
element of the union of
N
sets. It takes inputs from
the parties for computing the sum. The result of this
addition is then returned to all the parties. Next, the
functionality receives an input from party
P
1
. If this
input is equal to the
k
th
ranked element, then
F
Leaky
k
sends
x
k
(the
k
th
ranked element) to all the parties.
Otherwise, if the input is smaller than
x
k
,
F
Leaky
k
sends
1
to all the parties and if the input is greater, it sends
0
.
The functionality is called
leaky
as it reveals the inter-
mediate sum in each iteration to all the parties. This
provides additional information to the parties which
otherwise an adversary could not compute from the
output alone.
The protocol
π
Leaky
k
, which realises functionality
F
Leaky
k
, works in iterations and as follows: in the pre-
computation phase, each party computes
m = [a+b/2]
and counts the number of elements in its database that
are smaller than
m
(and larger than
m
). The parties
encrypt inputs using a threshold homomorphic encryp-
tion scheme and send them to
P
1
. Party
P
1
computes
the sum of these encrypted inputs and all the parties
jointly decrypt the result and obtain the plaintext. Next,
P
1
compares the result of the sum to conclude whether
the
k
th
ranked element is smaller than
m
(or larger than
m
). Based on the result of the comparison, the value
of
m
is updated for the next iteration. Note that each
party only communicates with party
P
1
throughout the
execution. This reduces the communication cost as
compared to the multi-party protocol given in (Aggar-
SECRYPT 2022 - 19th International Conference on Security and Cryptography
76

wal et al., 2004) that computes the same functionality.
Leaky k
th
Ranked Element (π
Leaky
k
)
Input: Each party
P
i
has a database
D
i
. The rank
k
, the
range of elements in the union of databases (
[a,b]
) and
the size of each database (|D
i
|) are public.
Primitives: A homomorphic encryption scheme
(Gen,Enc,Dec) having a key generation protocol π
Gen
.
Initial Phase: Each party
P
i
ranks its elements in ascend-
ing order.
N = Σ
i
|D
i
|
is the total number of elements in
S
D
i
.
Key Generation Phase: The parties engage in a semi-
honestly secure protocol
π
Gen
to generate a public key
pk
and their respective shares of secret key sk
i
of sk.
Local Computation Phase: Each party
P
i
does the fol-
lowing:
1. Computes m = ⌊(a + b)/2⌋.
2.
Computes the number of elements
(l
i
)
less than
m
and the number of elements (g
i
) greater than m.
Multi-party Phase:
4.
Each party
P
i
encrypts its masked inputs,
c
i
=
Enc
pk
(l
i
)
and
c
′
i
= Enc
pk
(g
i
)
, and sends the cipher-
texts to P
1
.
5. P
1
computes [L] =
n
∑
i=1
c
i
and [G] =
n
∑
i=1
c
′
i
.
6.
The parties jointly decrypt
[L]
and
[G]
to obtain the
sums
L
and
G
, respectively. Party
P
1
receives the
decrypted values L and G.
7. P
1
does the following comparisons
(a)
If
L < k
and
G ≤ N − k
, then
m
is the
k
th
ranked
element and P
1
sends Foundk to all the parties.
(b)
If
L ≥ k
, then
P
1
sends
1
to all parties. Then each
party sets
b = m − 1
and repeats the protocol from
the local computation phase.
(c)
If
G > N − k
, then
P
1
sends
0
to all parties and
each party sets
a = m +1
and repeats the protocol
from the local computation phase.
Output: x
k
(the k
th
element of
S
D
i
).
Figure 7: Leaky protocol for passively secure computation
of the k
th
ranked element.
Correctness. We prove the correctness of the protocol
in the following argument. Let
[a,b]
be the range
of elements in the union of all the sets and
N
be the
number of elements in the union. Let
x
k
be the element
at the
k
th
position in the union of the sets where the
elements are arranged in ascending order. Let
m
i
be
the value of
m
in the
i
th
iteration. In the
i
th
iteration,
each party counts the number of elements smaller than
m
i
and the number of elements greater than
m
i
and the
sum of these values from all the parties is computed
respectively. Let
L
i
and
G
i
be the total number of
elements smaller than and larger than
m
i
respectively,
in the i
th
iteration. Then three cases arise.
•
If
x
k
< m
i
, then
x
k
∈ [a,m
i
− 1]
. Then the number
of elements smaller than
m
i
is greater than the
number of elements smaller than
x
k
, i.e.,
L
i
> k −1
.
Thus,
m
i+1
will be computed as
a + m
i
− 1
2
and
the procedure is repeated.
•
If
x
k
> m
i
, then
x
k
∈ [m
i
+ 1,b]
. Then, the number
of elements larger than
m
i
will be greater than the
number of elements larger than
x
k
, i.e.,
G
i
> N − k
.
Thus,
m
i+1
is computed as
m
i
+ 1 + b
2
and the
procedure is repeated with m
i+1
.
•
Now if
L
i
< k
and
G
i
≤ N −k
, then
x
k
̸∈ [a, m
i
−1]
and x
k
̸∈ [m
i
+ 1,b], which implies x
k
= m
i
.
Hence, the protocol correctly computes the
k
th
ele-
ment.
Security. The protocol
π
Leaky
k
securely realises
F
Leaky
k
in the presence of semi-honest adversaries for
n ≥ 2
.
We discuss the proof of security in detail in §B.
Instantiations of the threshold PKE. The thresh-
old homomorphic encryption in protocol
π
Leaky
k
can
be instantiated using any homomorphic encryption
schemes (see §A). In the implementation of our pro-
tocol, described in §4.3, we use the threshold Paillier
PKE (Paillier, 1999). The threshold Paillier can be im-
plemented with distributed RSA modulus generation,
as discussed in (Hazay et al., 2019).
4.1 Leakage
Now we discuss the leakage mentioned above in pro-
tocol
π
Leaky
k
. In each iteration of
π
Leaky
k
, the sum of the
number of elements smaller than
m
(
L
) and the sum of
the number of elements greater than
m
(
G
) is leaked to
party
P
1
. Therefore for each
m
, the number of elements
greater or smaller than
m
in the union of all databases,
i.e.,
S
D
i
, is revealed. Using this leakage from each
iteration, an adversary can calculate the number of
elements that lie between two values of
m
. This shows
the distribution of the elements in
S
D
i
and
S
D
j
, for
j = [2,n]
. However, this leak only reveals a collec-
tive information about the union of the databases, and
the distribution of elements in each individual set
D
j
cannot be computed from this leakage.
In some applications certain leakage may be tol-
erable as a tradeoff between privacy and efficiency.
This can be demonstrated by several works like (Cash
et al., 2013; Pappas et al., 2014; Kolesnikov et al.,
2015; Schoppmann et al., 2018) that leak some infor-
mation in order to obtain more efficient protocols. For
instance, in (Cash et al., 2013; Pappas et al., 2014;
Schoppmann et al., 2018) DBMS search protocols
Comparison-based MPC in Star Topology
77

are presented that allow leakage of some information
to improve the efficiency of the search. (Kolesnikov
et al., 2015) studies the dual-execution paradigm (Mo-
hassel and Franklin, 2006) where the efficiency of
two-party computation is improved by revealing a sin-
gle bit of the honest party’s input to the adversary.
These works demonstrate tradeoffs between privacy
and efficiency, where some leakage may be accepted
in order to achieve higher efficiency. Moreover, if the
leakage is to be reduced, a potential solution may be
to use differential privacy. Then the leakage in the
protocols would be the differentially private leakage
as demonstrated in (Groce et al., 2019).
4.2 Complexity
Let
S = b − a+ 1
, where
[a,b]
is the range of elements
in
S
D
i
. Then, the maximum number of rounds is
logS
. The communication occurs at the setup phase for
generating correlated randomness and the multi-party
phase for finding the
k
th
element. The communication
complexity of the key generation phase is
O(κ · n
2
)
where
n
is the number of parties participating. In the
multi-party phase, in each round, the communication
occurs for:
n
encryptions,
1
decryption and
1
broadcast
by
P
1
. Hence, the communication complexity of the
online phase protocol is
O(κnd log S)
, where
d
is the
length of the inputs.
The protocol in (Aggarwal et al., 2004) also
uses the binary search algorithm and requires
logS
rounds. The circuit consists of two summations and
two integer comparisons, therefore the circuit size
is
O(nlog S)
. Hence, using an efficient MPC proto-
col (Ananth et al., 2019) for the computation of the
circuit, the total complexity for the protocol becomes
O(κnd log nlogd logS).
The protocol in (Tueno et al., 2020) uses a star
topology to achieve a constant round protocol. Using
the additively homomorphic encryption as the basis,
they obtain a
4
round protocol. They compute the
rank of the element by comparing each element with
every other element. The communication complexity
of their protocol is therefore quadratic in the number
of participating parties, i.e.,
O(κn
2
d)
. We give the
comparison of the complexities of the above protocols
with our work in Tab. 2.
4.3 Implementation
We implemented the protocol
π
Leaky
k
in the Rust pro-
gramming language and instantiated the threshold ho-
momorphic encryption with the threshold Paillier PKE
using a 3072 bit modulus
N
. The implementation
of the threshold encryption is based on the C library
libhcs (Tiehuis, 2018) and the Java library Paillier
Threshold Encryption Toolbox (UTD Data and Privacy
Lab, 2010).
4.4 Benchmarks
Benchmark Environment: We ran our benchmarks
on a server with 2
×
Intel Xeon Gold 6144
@
3.5 GHz
(8 physical cores) and
16 × 32 = 512
GB DDR4 RAM.
We created 20 containers, each with 32 GB RAM and
one core. The containers, running Arch Linux, were
connected via a simulated WAN with a bandwidth of
100 Mbits and latency of 100 ms.
For our benchmarks, we consider the worst-case
scenario for our protocol, i.e., when
k = 1
. We assume
that each party holds a set of elements and the range of
the elements in the union of these sets is S. Therefore,
the protocol runs for
logS
rounds. We benchmark
values of S from 10
4
to 10
14
. We benchmark the total
communication of the protocol execution for 3 to 19
parties, where each party’s database has a size of 1 GB
(Fig. 8b). To emulate the setting of (Tueno et al., 2020),
we also evaluate the runtime for 20 to 200 parties
with a single element each (Fig. 8a). The results are
averaged over 10 runs for each configuration.
4.4.1 Results
Our experimental results match with the expected
asymptotic complexities. We see that the total com-
munication scales linearly with the number of par-
ties, and increasing the number of parties does not
affect the individual communication. Moreover, the
communication increases logarithmically with the
range of the database.
The outliers in Fig. 8a are due to thread scheduling
issues on the container executing party P
1
.
Table 3: Performance comparison of our protocol
π
Leaky
k
(Fig. 7) for computing the
k
th
ranked element among
100 parties connected via WAN with the numbers reported
in (Tueno et al., 2020) based on Yao’s garbled circuit (YGC)
and additively homomorphic encryption (AHE). Comm. is
the communication from the client to the server in MB.
S
is
the range of elements in the database.
(Tueno et al., 2020) (no leakage) This work (leaky)
YGC AHE1 AHE2 S = 10
4
S = 10
14
Time (s) 197 1749 441 112.6 222.2
Comm. (MB) 0.31 1.11 0.32 0.040 0.143
Comparison: We compare our results with the exper-
imental results of the previous work in (Tueno et al.,
2020). The comparison of results for 100 parties with
a database range of either
10
4
or
10
14
is given in Tab. 3.
In the case of
S = 10
14
, our protocol reduces the client
communication by more than a factor of two compared
SECRYPT 2022 - 19th International Conference on Security and Cryptography
78
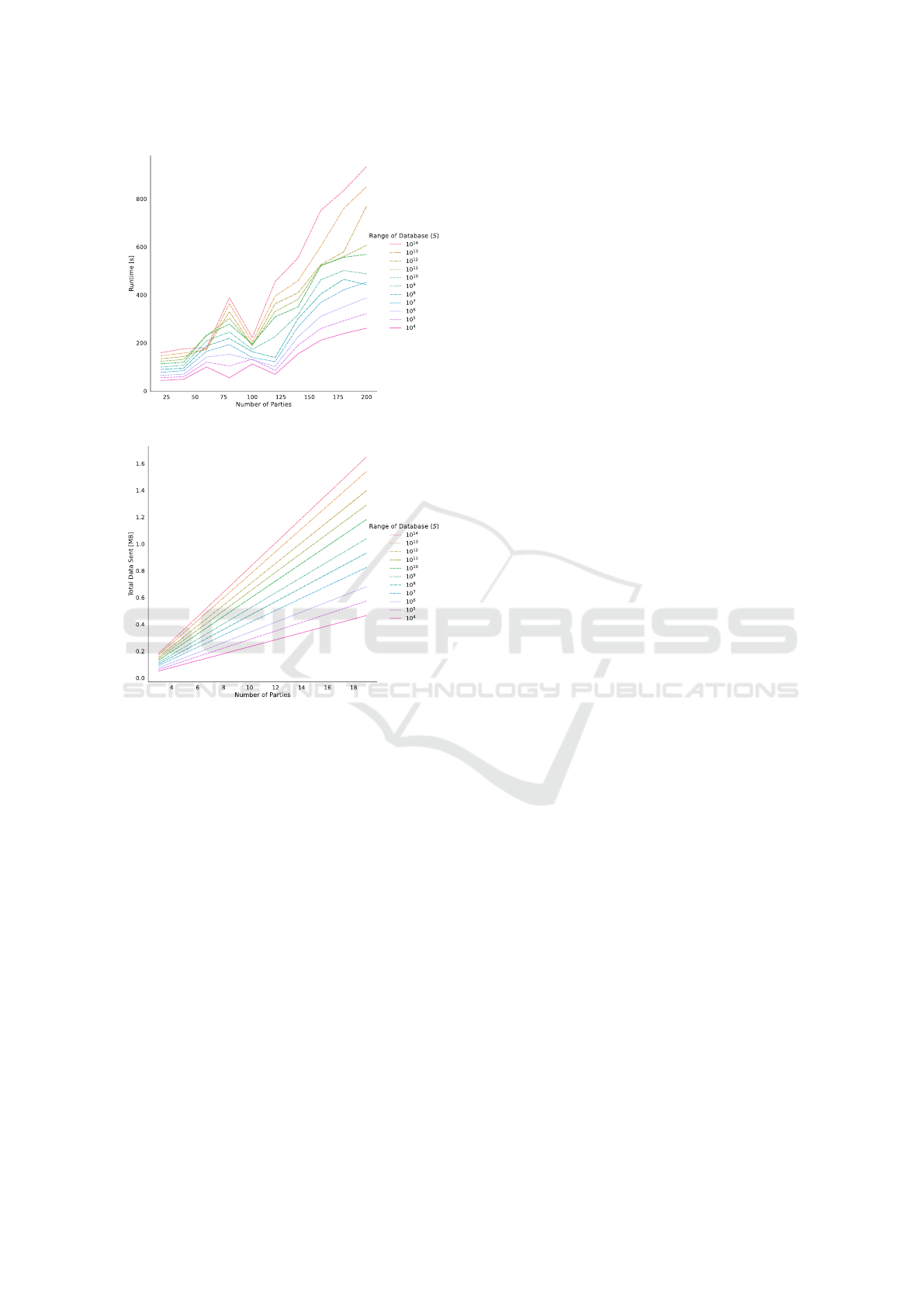
(a) Runtime
(b) Communication
Figure 8: Experimental analysis of protocol
π
Leaky
k
(Fig. 7),
which computes the
k
th
ranked element of the union of
n
sets, for varying number of parties
n
. The plots show the
results for different ranges of values in the database.
to the best protocol of (Tueno et al., 2020).
5 CONCLUSION
In this paper, we have presented two multi-party pro-
tocols, one for computing a class of comparison-based
functions and the second for computing the
k
th
ranked
element. The protocols that we constructed have better
communication complexities as compared to the previ-
ous works on these specific functions, and to generic
multi-party protocols that can be used for these func-
tions. We reduce the functions to a computation of
some high-level primitives and perform the compu-
tations in a star network topology, where one party
communicates with every other party to execute a se-
ries of two-party computations. We show that such
a design improves the efficiency of the protocols as
the communication between parties during the execu-
tion are reduced to a minimum. Our protocols have
communication complexities linear in the number of
parties, which makes it easily scalable.
ACKNOWLEDGEMENTS
This project received funding from the European Re-
search Council (ERC) under the European Union’s
Horizon 2020 research and innovation program (grant
agreement No. 850990 PSOTI). It was co-funded by
the Deutsche Forschungsgemeinschaft (DFG) within
SFB 1119 CROSSING/236615297 and GRK 2050 Pri-
vacy & Trust/251805230, and by the German Federal
Ministry of Education and Research and the Hessen
State Ministry for Higher Education, Research and the
Arts within ATHENE.
This project was also supported by the BIU Cen-
ter for Research in Applied Cryptography and Cyber
Security in conjunction with the Israel National Cy-
ber Bureau in the Prime Minister’s Office, and by ISF
grant No. 1316/18.
REFERENCES
Aggarwal, G., Mishra, N., and Pinkas, B. (2004). Secure
computation of the k th-ranked element. In EURO-
CRYPT.
Ananth, P., Badrinarayanan, S., Jain, A., Manohar, N., and
Sahai, A. (2019). From FE combiners to secure MPC
and back. In TCC (1).
Asharov, G., Lindell, Y., Schneider, T., and Zohner, M.
(2013). More efficient oblivious transfer and exten-
sions for faster secure computation. In CCS.
Beaver, D., Micali, S., and Rogaway, P. (1990). The round
complexity of secure protocols (extended abstract). In
STOC.
Ben-David, A., Nisan, N., and Pinkas, B. (2008). Fair-
playMP: a system for secure multi-party computation.
In CCS.
Ben-Efraim, A., Lindell, Y., and Omri, E. (2016). Optimiz-
ing semi-honest secure multiparty computation for the
internet. In CCS.
Boyle, E., Gilboa, N., Ishai, Y., and Nof, A. (2021). Sublin-
ear GMW-style compiler for MPC with preprocessing.
In CRYPTO (2).
Cachin, C., Camenisch, J., Kilian, J., and M
¨
uller, J. (2000).
One-round secure computation and secure autonomous
mobile agents. In ICALP.
Cash, D., Jarecki, S., Jutla, C. S., Krawczyk, H., Rosu, M.,
and Steiner, M. (2013). Highly-scalable searchable
Comparison-based MPC in Star Topology
79

symmetric encryption with support for boolean queries.
In CRYPTO (1).
Chen, M., Hazay, C., Ishai, Y., Kashnikov, Y., Micciancio,
D., Riviere, T., Shelat, A., Venkitasubramaniam, M.,
and Wang, R. (2021). Diogenes: Lightweight scalable
RSA modulus generation with a dishonest majority. In
S&P.
Choi, S. G., Hwang, K., Katz, J., Malkin, T., and Ruben-
stein, D. (2012). Secure multi-party computation of
boolean circuits with applications to privacy in on-line
marketplaces. In CT-RSA.
Choudhuri, A. R., Ciampi, M., Goyal, V., Jain, A., and
Ostrovsky, R. (2020). Round optimal secure multiparty
computation from minimal assumptions. In TCC (2).
Couteau, G. (2016). Efficient secure comparison protocols.
IACR Cryptol. ePrint Arch., page 544.
Cramer, R., Damg
˚
ard, I., and Nielsen, J. B. (2001). Mul-
tiparty computation from threshold homomorphic en-
cryption. In EUROCRYPT.
Damg
˚
ard, I., Geisler, M., and Krøigaard, M. (2007). Efficient
and secure comparison for on-line auctions. In ACISP.
Damg
˚
ard, I., Geisler, M., and Krøigaard, M. (2008). Ho-
momorphic encryption and secure comparison. Int. J.
Appl. Cryptogr.
Damg
˚
ard, I., Jurik, M., and Nielsen, J. B. (2010). A general-
ization of Paillier’s public-key system with applications
to electronic voting. Int. J. Inf. Sec.
Faust, S., Hazay, C., and Venturi, D. (2013). Outsourced
pattern matching. In ICALP (2).
Franklin, M. K. and Haber, S. (1996). Joint encryption and
message-efficient secure computation. J. Cryptol.
Frederiksen, T. K., Lindell, Y., Osheter, V., and Pinkas, B.
(2018). Fast distributed RSA key generation for semi-
honest and malicious adversaries. In CRYPTO (2).
Gamal, T. E. (1985). A public key cryptosystem and a
signature scheme based on discrete logarithms. IEEE
Trans. Inf. Theory.
Garay, J. A., Schoenmakers, B., and Villegas, J. (2007).
Practical and secure solutions for integer comparison.
In PKC.
Gilboa, N. (1999). Two party RSA key generation. In
CRYPTO.
Goldreich, O., Micali, S., and Wigderson, A. (1987). How
to play any mental game or A completeness theorem
for protocols with honest majority. In STOC.
Groce, A., Rindal, P., and Rosulek, M. (2019). Cheaper pri-
vate set intersection via differentially private leakage.
PoPETs.
Hazay, C. and Lindell, Y. (2008). Efficient protocols for set
intersection and pattern matching with security against
malicious and covert adversaries. In TCC.
Hazay, C., Mikkelsen, G. L., Rabin, T., Toft, T., and Ni-
colosi, A. A. (2019). Efficient RSA key generation and
threshold Paillier in the two-party setting. J. Cryptol.
Hazay, C. and Toft, T. (2010). Computationally secure pat-
tern matching in the presence of malicious adversaries.
In ASIACRYPT.
Hazay, C. and Venkitasubramaniam, M. (2017). Scalable
multi-party private set-intersection. In PKC (1).
He, X., Machanavajjhala, A., Flynn, C. J., and Srivastava,
D. (2017). Composing differential privacy and secure
computation: A case study on scaling private record
linkage. In CCS.
Inbar, R., Omri, E., and Pinkas, B. (2018). Efficient scalable
multiparty private set-intersection via garbled Bloom
filters. In SCN.
Ishai, Y., Kilian, J., Nissim, K., and Petrank, E. (2003).
Extending oblivious transfers efficiently. In CRYPTO.
Jarvis, R. A. (1973). On the identification of the convex hull
of a finite set of points in the plane. Inf. Process. Lett.
Kolesnikov, V., Mohassel, P., Riva, B., and Rosulek, M.
(2015). Richer efficiency/security trade-offs in 2PC. In
TCC (1).
Kolesnikov, V., Sadeghi, A., and Schneider, T. (2009). Im-
proved garbled circuit building blocks and applications
to auctions and computing minima. In CANS.
Lindell, Y. and Pinkas, B. (2004). A proof of Yao’s protocol
for secure two-party computation. Electron. Collo-
quium Comput. Complex.
Lindell, Y., Pinkas, B., Smart, N. P., and Yanai, A. (2015).
Efficient constant round multi-party computation com-
bining BMR and SPDZ. In CRYPTO (2).
Lindell, Y., Smart, N. P., and Soria-Vazquez, E. (2016). More
efficient constant-round multi-party computation from
BMR and SHE. In TCC (B1).
Mohassel, P. and Franklin, M. K. (2006). Efficiency tradeoffs
for malicious two-party computation. In PKC.
Paillier, P. (1999). Public-key cryptosystems based on com-
posite degree residuosity classes. In EUROCRYPT.
Pappas, V., Krell, F., Vo, B., Kolesnikov, V., Malkin, T., Choi,
S. G., George, W., Keromytis, A. D., and Bellovin,
S. M. (2014). Blind Seer: A scalable private DBMS.
In S&P.
Pinkas, B., Schneider, T., and Zohner, M. (2018). Scalable
private set intersection based on OT extension. ACM
Trans. Priv. Secur.
Rosulek, M. and Trieu, N. (2021). Compact and malicious
private set intersection for small sets. In CCS.
Schoppmann, P., Gasc
´
on, A., and Balle, B. (2018). Private
nearest neighbors classification in federated databases.
IACR Cryptol. ePrint Arch.
Shelat, A. and Venkitasubramaniam, M. (2015). Secure
computation from millionaire. In ASIACRYPT (1).
Tiehuis, M. (2018). libhcs. https://github.com/tiehuis/libhcs.
Accessed: 29.11.2021.
Tueno, A., Kerschbaum, F., Katzenbeisser, S., Boev, Y., and
Qureshi, M. (2020). Secure computation of the k
th
-
ranked element in a star network. In FC.
UTD Data and Privacy Lab (2010). Paillier threshold en-
cryption toolbox. http://cs.utdallas.edu/dspl/cgi-bin/
pailliertoolbox/index.php. Accessed: 29.11.2021.
Wang, X., Ranellucci, S., and Katz, J. (2017). Global-scale
secure multiparty computation. In CCS.
Yao, A. C. (1982). Protocols for secure computations (ex-
tended abstract). In FOCS.
Yao, A. C. (1986). How to generate and exchange secrets
(extended abstract). In FOCS.
SECRYPT 2022 - 19th International Conference on Security and Cryptography
80

Yasuda, M., Shimoyama, T., Kogure, J., Yokoyama, K., and
Koshiba, T. (2013). Secure pattern matching using
somewhat homomorphic encryption. In CCSW.
A Additively Homomorphic
Encryption
A public key encryption (PKE) scheme is said to
be additively homomorphic if for two ciphertexts
c
1
= Enc
pk
(m
1
;r
1
)
and
c
2
= Enc
pk
(m
2
;r
2
)
, we can
efficiently compute
Enc
pk
(m
1
+ m
2
;r)
with an inde-
pendent
r
and without the knowledge of the secret
key sk.
Threshold PKE. In a distributed scheme, shares of the
secret key are held by the parties so that the combined
key remains secret. In order to decrypt, the parties use
their shares to compute intermediate values, which are
combined eventually to form the decrypted plaintext.
Threshold encryption scheme thus comprises of two
functionalities: a generate functionality to generate
the shares of the secret key and share among the par-
ties, and a decryption functionality where the parties
perform the decryption together.
Homomorphic Encryption Schemes. A popular in-
stantiation of the homomorphic encryption is the Pail-
lier encryption scheme (Paillier, 1999), which is based
on the Decisional Composite Residuosity (DCR) hard-
ness assumption for its security. In (Gilboa, 1999;
Damg
˚
ard et al., 2010) threshold variant of the Paillier
scheme is presented. Another instantiation of homo-
morphic encryption is the El Gamal scheme (Gamal,
1985). Its security is implied by the Decisional Diffie-
Hellman hardness assumption.
B Security of π
Leaky
k
Theorem 2. (Security of
π
Leaky
k
). Assume that
(Gen,Enc,Dec)
is an IND-CPA secure threshold ho-
momorphic encryption scheme. Then the proto-
col (Fig. 7) securely realises
F
Leaky
k
in the presence
of semi-honest adversaries for n ≥ 2.
Proof.
We construct a simulator
S
, where
S
is provided
with the inputs of the corrupted parties and the output
of the computation. Let
A
be an adversary corrupting
a subset of the parties, then two cases arise:
Case 1:
A
corrupts a strict subset
I
of the parties
excluding
P
1
. Let
x
k
be the
k
th
ranked element in the
union of all the sets. The simulator
S
has input
D
i
,
i ∈ I and x
k
, and is defined as follows:
1.
Given
D
i
, i ∈ I
and
x
k
, the corrupted parties are
invoked by S on their corresponding inputs.
2. S
generates
(pk,sk) ← Gen(1
κ
)
and invokes
S
Gen
for the key generation phase.
3. S
plays the role of
P
1
on an arbitrary set of inputs,
against the corrupted parties.
4.
For each iteration
j
, let
m
j
= [a + b/2]
be the me-
dian of the range as computed by each party. If
x
k
< m
j
, then
S
returns
1
to all parties. If
x
k
> m
j
,
S returns 0 to the parties.
In this case, the view generated by the simulator is
identical to the view of the honest parties in the real
protocol. In the case when
x
k
< m
, it implies that
L
(number of elements less than
m) ≥ k
, then in the
real execution as well as in the simulation,
b = m −
1
. When
x
k
> m
, it implies that
G
(the number of
elements greater than
m) ≥ N − k + 1
, then in the real
execution and in the simulation,
a = m + 1
. When
x
k
= m
,
L
(number of elements less than
m) ≤ k − 1
and
G
(number of elements greater than
m) ≤ N −k
,
then in both executions
m
is the
k
th
element. Hence,
the view of the honest parties in both executions are
identical.
Case 2:
A
corrupts a strict subset
I
of parties including
P
1
. Let
x
k
be the
k
th
ranked element of the union of all
databases
D
j
. Here the simulator
S
has input sets
D
i
,
i ∈ I and x
k
, and is defined as follows:
1.
Given
D
i
, i ∈ I
and
x
k
, the corrupted parties are
invoked by the simulator on their corresponding
inputs.
2. S
generates
(pk,sk) ← Gen(1
κ
)
and invokes the
simulator
S
Gen
(pk)
for
π
SH
Gen
in the key generation
phase.
3. S
plays the honest parties’ role against
P
1
in the
protocol. For the
j
th
iteration, let
m
j
= [a+b/2]
be
computed by
S
. The simulator sends encryptions
of two arbitrary inputs to
P
1
and
P
1
computes two
sets of sums
(a)
If
m
j
< x
k
, the simulator invokes
S
Dec
(r
1
)
for
the decryption of
C
and
S
Dec
(N − k +r
2
)
for the
decryption of
C
′
, where
r
1
,r
2
∈ Z
k
. Then
P
1
returns 0 and the simulator sets a = m
j
+ 1.
(b)
If
m
j
> x
k
, the simulator invokes
S
Dec
(k + r
1
)
for the decryption of
C
and
S
Dec
(r
2
)
for the de-
cryption of
C
′
, where
r
1
,r
2
∈ Z
k
. Then
P
1
re-
turns 1 and the simulator sets b = m
j
− 1
(c) If m
j
= x
k
, then m
j
is the k
th
element.
In this case the difference lies in the encryptions sent to
P
1
. In the real execution, the parties send encryptions
Comparison-based MPC in Star Topology
81

of their input to
P
1
whereas the simulator sends en-
cryptions of arbitrary inputs to
P
1
. Hence, the indistin-
guishability of the two views follows from the privacy
of the threshold homomorphic encryption scheme.
Thus, the above protocol securely computes the
k
th
ranked element of the union of n sets.
SECRYPT 2022 - 19th International Conference on Security and Cryptography
82
