
A Systematic Literature Review on Technological Solutions to Fight
Bullying and Cyberbullying in Academic Environments
Priscila Cedillo
1a
, Alexandra Bermeo
2b
, Alexa Betancourth
1c
, Francisco Espinosa
1d
,
Lourdes Illescas
1e
and Janio Jadán
3f
1
Computer Science Department, Universidad de Cuenca, Cuenca, Ecuador
2
Computer Science Research & Development Lab-LIDI, Universidad del Azuay, Cuenca, Ecuador
3
Universidad Tecnológica Indoamérica, Quito, Ecuador
alexbermeo@uazuay.edu.ec, janio.jadan@uti.edu.ec
Keywords: Bullying, Cyberbullying, Technology Tools, Education.
Abstract: Nowadays, the world is more connected than ever; the use of internet, social networks and platforms allows
for people of all ages to have constant communication. During the past year, due to the COVID-19 pandemic,
children and teenagers have had to spend most of their time using a technological device, for educational and
recreational purposes. This constant connection has carried on several issues, one of them being cyberbullied.
This is when a person intentionally and repeatedly harms another one, on a virtual environment. Even with
its downside, technology has many advantages; it has allowed for children and teenagers to engage in
educational communities and applications. Then, studies on bullying and the ways to fight it exist from many
years prior, however, there are little literature about the technological solutions to help in the fight against
cyberbullying and bullying. Therefore, the objective of this research is to perform a Systematic Literature
Review (SLR) about technological solutions for education and to fight bullying and cyberbullying in children
and teenagers. To perform a trustworthy, rigorous and repeatable SLR, the methodology proposed by
Kitchenham was used. The presented SLR, uses studies from 2009 to 2021. To start, a group of primary
studies was selected, which met the characteristics to answer the research question “What technological tools,
methods and models are used to educate about bullying and cyberbullying?” The primary studies were
obtained from the most used digital libraries, prominent journals, and most representative conferences in the
area. In conclusion, this study provides a global vision of the state of the art in this area, which represents a
helpful tool for researchers to detect weaknesses and gaps and open new horizons regarding the use and design
of technology to fight bullying and cyberbullying.
1 INTRODUCTION
The closure of schools due to the COVID-19
pandemic and the increase in using technological
tools, social networks, and digital platforms brought
along the need to adopt technologies in education. (E.
Onyema et al., 2020). Nowadays, most academic
stages have become digitized (e.g., Online courses,
MOOCs, digital learning methods) (Onyema, 2019).
a
https://orcid.org/0000-0002-6787-0655
b
https://orcid.org/0000-0002-2697-7528
c
https://orcid.org/0000-0002-4790-5996
d
https://orcid.org/0000-0003-2242-4130
e
https://orcid.org/0000-0002-0027-439X
f
https://orcid.org/0000-0002-3616-2074
This technological change has also turned bullying
behaviours that affect the welfare of children and
adolescents, into cyberbullying (e.g., attacking peers
through harmful text messages, photos, or videos)
(Pedreira et al., 2011, Washington, 2014).
Bullying and cyberbullying are quite prevalent
behaviours among children and adolescents at school
(Cedillo L, 2020). These behaviours are primarily
related to the difference in power between victims
Cedillo, P., Bermeo, A., Betancourth, A., Espinosa, F., Illescas, L. and Jadán, J.
A Systematic Literature Review on Technological Solutions to Fight Bullying and Cyberbullying in Academic Environments.
DOI: 10.5220/0011091800003182
In Proceedings of the 14th International Conference on Computer Supported Education (CSEDU 2022) - Volume 1, pages 413-420
ISBN: 978-989-758-562-3; ISSN: 2184-5026
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
413

and victimizers and can lead to psychological
consequences for the victims (Monks & Smith, 2006;
Foody et al., 2015).
In this sense, due to cyberbullying being caused
during the use of Information and Communication
Technologies (ICTs), technological tools are being
created to counteract this problem, such as vigilance
software, serious games, artificial intelligence within
e-learning tools, among others (Calderón & Ruiz,
2015). Besides, social networks, internet providers,
and other e-learning tools have implemented
functionalities for detecting when a person is virtually
assaulted.
Furthermore, those intervene by monitoring and
filtering parents, blocking an account, deleting
content, reporting, and redirecting to online resources
and safety centers in a preventive manner (Topcu-
Uzer & Tanrikulu, 2018). Therefore, the use of ICTs
as a strategy for intervention and prevention of
bullying and cyberbullying is an excellent benefit to
the emotional, psychological and social well-being of
children and teenagers (Nocentini et al., 2015).
In this context, due to the use increase of
prevention tools against bullying and cyberbullying,
it is necessary to know the state of the art in this
domain in order to determine the research lines and
tools implemented and detect investigation gaps.
Therefore, this research aims to conduct a
Systematic Literature Review (SLR) on technological
solutions for education and the fight against bullying
and cyberbullying in children and teenagers due to its
importance in today's society, following the guidelines
established by Barbara Kitchenham (2007). For this
reason, there is a need to know the technology tools
developed currently to prevent this problem and
intervene in the different social and educational fields.
Also, it will allow us to know which tools are the most
used and in which areas they develop. Furthermore, the
writing will serve as a basis for further research and
technological solutions to fight this problem in schools,
colleges, and universities.
Finally, this document has the following structure:
Section 2 presents the related works; it mentions
secondary studies related to technological tools to
fight against bullying and cyberbullying. Section 3
describes the core of the SLR, its protocol execution,
and results; and finally, Section 4 presents the
conclusions and future works.
2 RELATED WORK
To define the need for the performing of this SLR,
existing reviews on topics related to the use of tools
to fight against bullying and cyberbullying were
found. They are presented in the following sections.
The study conducted by Topcu-Uzer & Tanrikulu
(2018) presents the fact that technological tools are
not 100% focused on bullying and cyberbullying.
Although, there are still no scientific studies that can
prove the effectiveness of new technological
solutions against bullying and cyberbullying, with the
exception of stop systems such as text-based
detection (Dinakar et al., 2011; Soundar & Ponesakki,
2016), participant-vocabulary coherence (Raisi &
Huang, 2016) or morphosemantic patterns
(Ptaszynski et al., 2016). Moreover, there are recent
studies such as the Rethink software and an empathy-
enhancing video movie being conducted to combat
these problems. They will be a key element in the
development of new technological solutions to fight
bullying and cyberbullying and in future research to
demonstrate their effectiveness.
Calvo, A. et al., (2020) present a SLR of serious
games as technological tools of prevention and
detection to fight bullying and cyberbullying, through
the use of video games. The study had several
objectives: a) to see the benefits of using video
games, b) to determine the users on which these will
focus and, c) to assess the extent to which a given
population can benefit. At present, these games are
not yet available, but the idea is to create spaces of
awareness, empathy and teaching for students,
teachers and parents.
On the other hand, Nocentini et al., (2015) present
a SLR on ICT used to prevent and intervene bullying,
based on anti-bullying programs. Although it has
relation to the presented proposal, however, this
research will cover the solutions and technological
tools that currently exist to prevent and intervene
bullying and cyberbullying. Therefore, it will also be
an important contribution for future research on this
problem.
3 RESEARCH METHOD
In order to carry out the SLR in the framework of this
paradigm, it is necessary to follow a structured
procedure. The purpose of the SLR is to extract
previously conducted studies according to a specific
topic, to evaluate them and interpret the results
obtained in each one of them in an objective and
reliable way, so that it can be repeatable and
applicable in the future.
This study was conducted using the methodology
of Kitchenham (2007), the process has three stages.
First, the planning of the review, where the research
CSEDU 2022 - 14th International Conference on Computer Supported Education
414

questions are established and the protocol is started.
Second, conduct of the review, in this section the
primary studies are chosen, their quality is evaluated
and then the data obtained in the first stage are
extracted and traced in order to synthesize them.
Finally, the third stage refers to the review report,
which will enable the selection of the dissemination
mechanisms and thus, the presentation of the SLR.
3.1 Planning the Review
This SLR focuses on technological solutions that help
in the promotion against bullying and cyberbullying
in children and teenagers. According to UNESCO
(2019), bullying affects 1 in every 3 children, and
cyberbullying globally affects 1 in 10 children,
therefore, the main research question that has been
raised is: What technological tools, methods and
models are used to educate about bullying and
cyberbullying?
Therefore, to answer the research question, the
following research sub-questions have been proposed
a) In what population and environment will
technological tools be used to address the problem of
bullying and cyberbullying b) What are the tools,
technological methods, solutions, and deployment
platforms to fight Bullying and cyberbullying? and c)
How is the research conducted in relation to Bullying
and cyberbullying technology?
3.1.1 Identification of Data Sources and
Search Strategy
To obtain the primary studies, several digital libraries
were used, such as: Redalyc, IEEEXplore, Scielo,
ACM Digital Library, SpringerLink, Science Direct,
PUBMED.
The milestone date established for the search is
2009 (U.S. Department of Education, 2021), because
from that year, almost everyone in the United States
had access to technology and Internet. According to
Purdue University, one out of every five students had
a computer, 83% had laptops, 50% had a cell phone
and 97% of the classrooms had one or more
computers with internet (Department of Education,
2021).
For the first phase, a search string was established
to facilitate the retrieval of publications related to
technology used for bullying and cyberbullying. The
string used to obtain these publications and then
review the title and abstract was: (Bullying OR
Cyberbullying) AND (tech*) AND (tool* OR
program*), it is important to note that the syntax
varies in each digital library. In addition, for the
search to be complete, it was searched in conferences
and journals.
3.1.2 Criteria for Selecting Primary Studies
To select the primary studies, a complementary
semantic check was performed in addition to a
syntactic inquiry. The title and abstract of the
documents were analysed and, if necessary, the
complete article was read to corroborate that it was
useful for the research and that it met the extraction
and inclusion criteria.
The authors evaluated and retrieved each study
from the automated or manual search in order to
decide whether or not it should be included by
considering its title, abstract and keywords.
Discrepancies in the selection were solved by
consensus among the authors after scanning the entire
paper.
The studies that met at least one of the following
inclusion criteria were included.
a) Studies presenting tools to fight bullying and
cyberbullying
b) Studies presenting technological methodologies
to reduce bullying and cyberbullying.
c) Studies presenting effective psychological
models through technologies to fight bullying
and cyberbullying.
The studies that met at least one of the following
exclusion criteria were excluded.
a) Non-English or non-Spanish language papers.
b) Papers that do not feature technologies to fight
bullying and cyberbullying.
c) Papers that are less than five pages.
d) Documents published before the milestone date
(2009), in which the first technological tools
appeared.
e) Introductory papers, short papers, books and
workshops.
f) Duplicate reports of the same study in different
sources.
3.1.3 Data Extraction Strategy
In order to answer the sub-questions, extraction
criteria have been defined for each of them. These are
shown in Table 1.
A Systematic Literature Review on Technological Solutions to Fight Bullying and Cyberbullying in Academic Environments
415
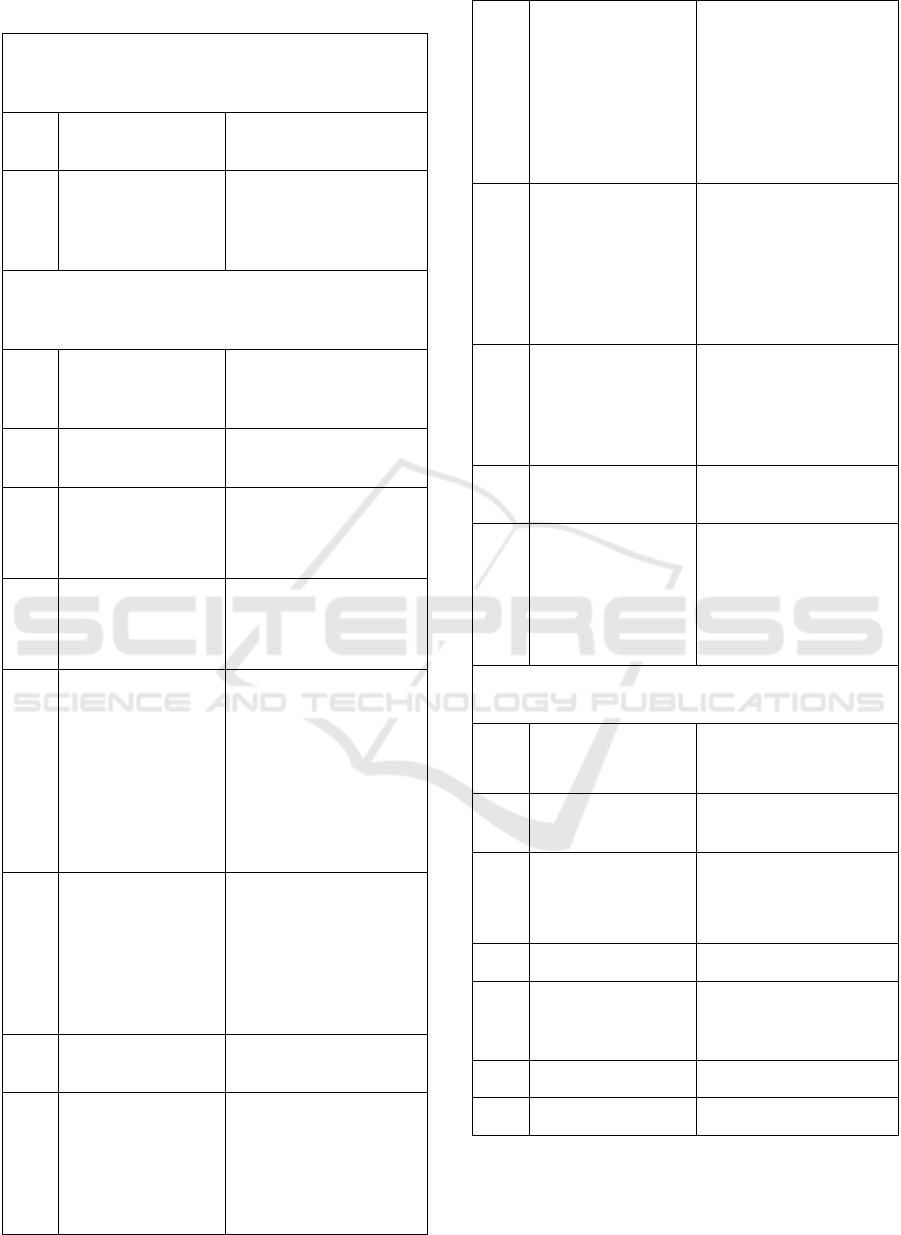
Table 1: Criteria for extraction of research sub-questions.
RQ1: In what population and environment will
technological tools be used to address the problem of
bullying and cyberbullying?
EC1 Environment School, Home, Social
environment
EC2 Population
(Calvo-Morata et
al., 2019)
Students, Teacher,
School Authorities,
Parents, General
Population
RQ2: What are the tools, technological methods,
solutions, and deployment platforms to fight bullying and
cyberbullying?
EC3 Type of gadgets Computers, Tablets, Cell
phone, Laptops, I-pads,
Others, None
EC4 Area of study Psychology, Electronics,
Informatics, Education
EC5 Type of interaction
(Garnica Bautista &
Tepán Mita, 2019)
Visual, Touch, Auditory,
Other
EC6 Type of Application
(Sousa & Goncalves,
2021)
MOOCs, 3D virtual,
Serious Game, Apps,
Others
EC7 Artificial
Intelligence
(Fernández, n.d.)
Data mining, Machine
Learning, Automatic
speech recognition,
Natural language
processing, Text
recognition, Deep
learning, Emotion
Recognition, Motion
Recognition
EC8 Types of
harassment
(Donegan, 2012)
Bullying,
Cyberbullying, Physical
Bullying, Psychological
Bullying, Verbal
Bullying, Sexual
Bullying, Social
Bullying
EC9 Types of
development
Software, None
EC10 Usability features
(ISO 25010, n.d.)
Functional adaptation,
Performance efficiency,
Compatibility,
Usability, Reliability,
Security,
Maintainability
EC11 Technology
suppliers
(Topcu-Uzer &
Tanrikulu, 2018)
Social networking
companies, Internet
service providers, E-
mail service providers
instant, Messaging
applications,
Cyberbullying
applications, Others
EC12 Solutions for
Cyberbullying
(Topcu-Uzer &
Tanrikulu, 2018)
Parental control and
filtering, Account
locking, Content
removal, Reporting,
Redirecting to online
resources, Security
centers
EC13 Technology
solutions
(Topcu-Uzer &
Tanrikulu, 2018)
Online Cyberbullying
detection systems,
Software, Video film,
Positive messages by
technical means, Others
EC14 Software
(Educba, n.d.)
Website, Application,
Mobile Systems, Others
EC15 Forms of Bullying
(Botell, 2017)
Social blocking,
Harassment,
Manipulation, Coercion,
Social exclusion,
Intimidation,
Aggressions, Threats
RQ3: How is the research conducted in relation to
bullying and cyberbullying technology?
EC16 Phases
(Wasson, n.d.)
Analysis, Design,
Implementation, Testing
EC17 Validation Experiment, Prototype,
Proof of Concept, Others
EC18 Approach scope
(Mårtensson et al.,
2016)
Industry, Academy
EC19 Methodology New, Extension
EC20 Area of study Informatics, Medicine,
Psychology, Electronics,
Others
EC21 Country
EC22 Year
3.2 Conducting the Review
The planning, execution and identification of the
primary studies was performed on December 17,
CSEDU 2022 - 14th International Conference on Computer Supported Education
416
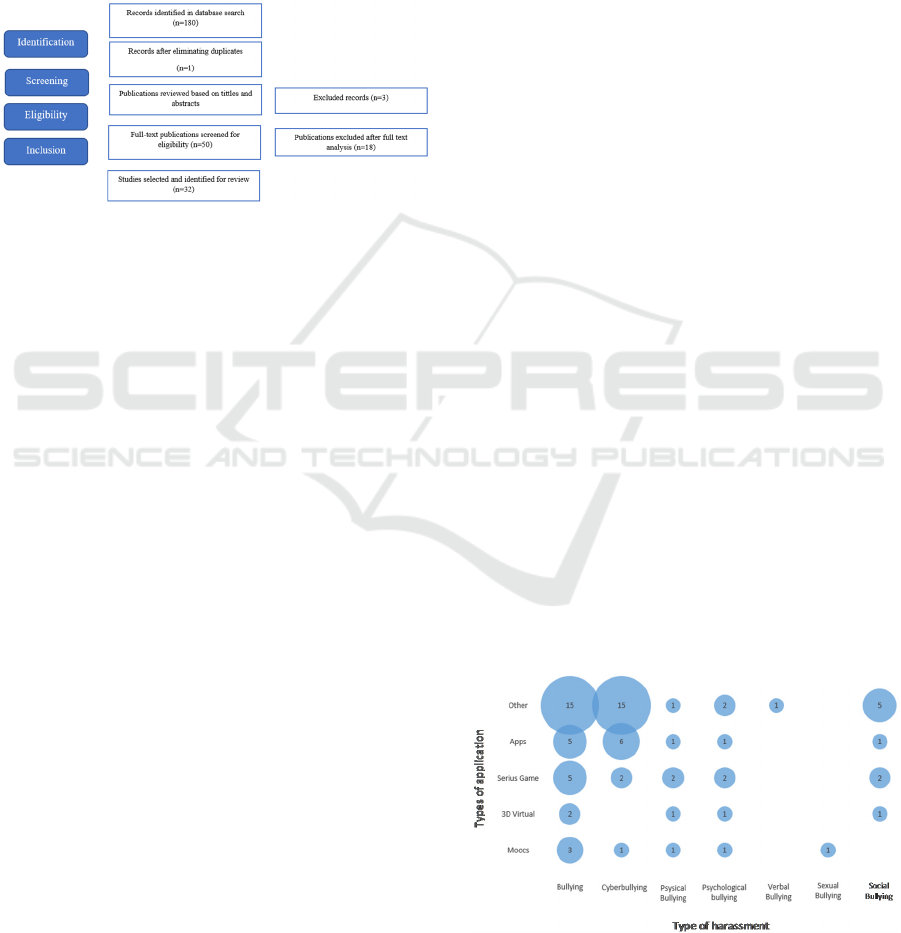
2021. Here, 180 research papers were identified from
the databases, based on the automatic search.
In addition, a manual search was performed, from
which 50 research papers were selected. The papers
were carefully read and inclusion and exclusion
criteria were applied. Several studies were read in
detail and, finally, 32 were selected to be part of this
secondary study, for the complete list of selected
papers, see shorturl.at/cvwRT. Figure 1 summarizes
the entire process, up to the final selection of articles.
Figure 1: Articles selection.
4 DISCUSSION
4.1 Environment and Population
Most of the studies found in the SLR were conducted
in the school setting, where there are various
technological tools to prevent and intervene in
children and teenagers. It is very important to note
that they were carried out in this population, as
presented by Cedillo, L (2020), based on a report of
the United Nations International Children's
Emergency Fund (UNICEF), it stated that between 50
and 70% of students in Latin America and the
Caribbean had been involved in some type of
bullying.
On the other hand, a lack of studies in school
authorities and parents can be noted, which would be
fundamental to educate the most affected populations.
However, it can be seen that there are technological
tools for teachers to identify the nature of the
psychological impact experienced by students, such
as automated speech emotion recognition (Iliou &
Paschalidis, 2011), video games, MOOCs and 3D
Virtual Reality (Sousa & Goncalves, 2021).
4.2 Types of Application and Artificial
Intelligence
This study found that Machine Learning (ML) is one
of the most widely used Artificial Intelligence (AI)
techniques in the creation of technological tools to
fight bullying and cyberbullying. Its use is found in
apps and other types of applications to detect
language patterns used by victims and bullies, and in
systems for the identification of profiles in social
networks. It is important to emphasize that some AIs
are combined, such as CbPIS: Cyberbullying Profile
Identification System with Users in Loop (Chatzakou
et al., 2019) and Cyberbullying Detection and
Prevention: Data Mining and Psychological
Perspective (Parime & Suri, 2014).
On the other hand, there is only one study on
speech emotion recognition, which is very important
in the branch of psychology. It allows to identify the
psychological impact and understand the emotions of
bystanders and consequently their coping styles in
bullying episodes. It could introduce strategies that
provide students, who witness bullying, with positive
roles to counteract it (Iliou & Paschalidis, 2011).
4.3 Types of Application and Types of
Harassment
Figure 2 compares the criteria EC6: Types of
Application and EC8: Types of harassment, in order
to know the tools to fight the different types of
harassment. The obtained results indicate that there
are many tools that use artificial intelligence to fight
bullying, cyberbullying and social bullying, such as
the studies of Dinakar et al., (2011); E. M. Onyema,
(2019); Reynolds et al., (2011); Soundar &
Ponesakki, (2016) it can be seen it in using machine
learning to detect cyberbullying.
Moreover, to a lesser extent, there are tools such
as serious games and MOOCs, to fight psychological
abuse, verbal and social bullying, as presented in the
work of Raminhos et al. (2015). However, very little
information was found on tools to fight sexual
bullying and verbal bullying.
Figure 2: Comparison between EC6: Types of Application
and EC8: Types of harassment.
A Systematic Literature Review on Technological Solutions to Fight Bullying and Cyberbullying in Academic Environments
417
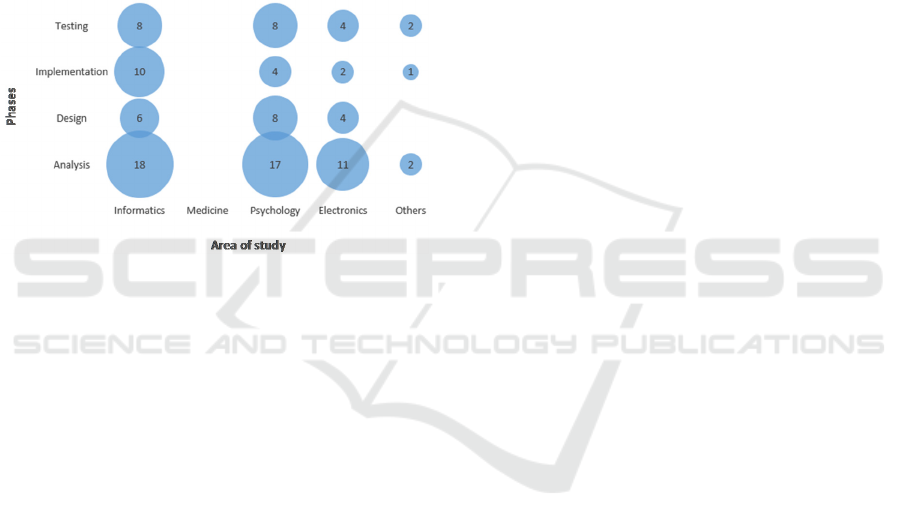
4.4 Phases and Area of Study
Figure 3 compares the criteria EC16: Phases and
EC22: Area of study, in order to know how research
is being carried out in relation to the technology
developed for bullying and cyberbullying. As a result,
the area of computer science, psychology and
electronics, are conducting multiple researches that
are mostly in the phase of analysis, implementation
and testing, as presented by Cohen et al. (2014) and
Silva et al., (2018). The education area presents, to a
lesser extent, studies in the analysis and testing phase.
On the other hand, in the area of medicine, no
research, promoting new technologies has been
found.
Figure 3: Comparison between EC16: Phases and EC22:
Area of study.
5 CONCLUSIONS
Nowadays, bullying and cyberbullying have
increased due to the use of technological devices,
causing severe consequences for the victims and the
surrounding community. For this reason, there is a
need to create tools and technical solutions to fight
this problem.
This research is an advance in state of the art in
this domain, which can help to define what types of
tools are currently being developed and which are not,
to identify research gaps and to create new solutions
or improve existing ones, to obtain greater
effectiveness when used with children and
adolescents in the school and social environment.
The methodology proposed by Barbara
Kitchenham was used to perform the review, which
consists of three phases: planning, conducting, and
reporting the review. This SLR was conducted with
32 primary studies from several digital libraries such
as Redalyc, IEEEXplore, Scielo, ACM Digital
Library, SpringerLink, Science Direct, PUBMED.
Most of the created tools are used in the school
environment for students and teachers (MOOCS,
Apps, Serious Games). However, there are few tools
aimed at other environments and users (parents and
authorities). On the other hand, for the creation of
detection systems, artificial intelligence such as data
mining and machine learning are used to detect
bullying and cyberbullying, especially in social
networks. In addition, this SLR has found that there
are not many tools to combat sexual and verbal
harassment. Therefore, most studies are in the
analysis phase in computer science, psychology, and
electronics.
This work has made it possible to know the state
of the art of this problem and the variety of tools
aimed at different populations to reduce bullying and
cyberbullying in other areas of daily life, especially in
children and adolescents.
ACKNOWLEDGEMENTS
This work is part of the research project “Fog
Computing applied to monitoring devices used in
assisted living environments. Case study: platform
for the elderly”, hence, the authors thank to DIUC of
Universidad de Cuenca for its academic and financial
support. Also, the authors would like to thank to
CEDIA for the academic support given to the present
research, development, and innovation work through
its CEPRA program, especially for the
“Implementation and Deployment of Learning
Capsules to Combat Bullying and cyberbullying in
Boys, Girls and Adolescents” fund.
REFERENCES
Botell, M. L. (2017). Bullying: aspectos históricos,
culturales y sus consecuencias para la salud. Revista
Cubana de Medicina General Integral, 33(1).
http://www.revmgi.sld.cu/index.php/mgi/article/view/
277/132
Calderón, A., & Ruiz, M. (2015). A systematic literature
review on serious games evaluation: An application to
software project management. Computers and
Education, 87, 396–422. https://doi.org/10.10
16/j.compedu.2015.07.011
Calvo-Morata, A., Alonso-Fernández, C., Freire, M.,
Martínez-Ortiz, I., & Fernández-Manjón, B. (2020).
Serious games to prevent and detect bullying and
cyberbullying: A systematic serious games and
literature review. Computers and Education, 157.
https://doi.org/10.1016/j.compedu.2020.103958
CSEDU 2022 - 14th International Conference on Computer Supported Education
418

Calvo-Morata, A., Freire-Morán, M., Martínez-Ortiz, I., &
Fernández-Manjón, B. (2019). Applicability of a
Cyberbullying Videogame as a Teacher Tool:
Comparing Teachers and Educational Sciences
Students. IEEE Access, 7, 55841–55850.
https://doi.org/10.1109/ACCESS.2019.2913573
Cedillo, L. (2020). Bullying as a risk factor for depression
and suicide. Revista Chilena de Pediatria, 91(3), 432–
439. https://doi.org/10.32641/rchped.v91i3.1230
Chatzakou, D., Leontiadis, I., Blackburn, J., de Cristofaro,
E., Stringhini, G., Vakali, A., & Kourtellis, N. (2019).
Detecting Cyberbullying and cyberaggression in social
media. ACM Transactions on the Web, 13(3).
https://doi.org/10.1145/3343484
Cohen, R., Lam, D. Y., Agarwal, N., Cormier, M., Jagdev,
J., Jin, T., Kukreti, M., Liu, J., Rahim, K., Rawat, R.,
Sun, W., Wang, D., & Wexler, M. (2014). Using
Computer Technology to Address the Problem of
Cyberbullying.
Department of Education, N. C. for E. S. (2021). The
Condition of Education 2021. National Center for
Education Statistics. https://nces.ed.gov/fastfacts/
display.asp?id=46&_ga=2.45730599.2083730396.164
3241977-479983204.1642562341
Dinakar, K., Reichart, R., & Lieberman, H. (2011).
Modeling the Detection of Textual Cyberbullying.
www.aaai.org
Donegan, R. (2012). Bullying and cyberbullying: History,
Statistics, Law, Prevention and Analysis.
Educba. (n.d.). Software Classification | Various
Classification of Software. Retrieved January 19, 2022,
from https://www.educba.com/software-classification/
Fernández, A. (n.d.). Artificial Intelligence Technologies
and their categories • AuraQuantic. Retrieved January
19, 2022, from https://www.auraquantic.com/artificial-
intelligence-technologies-and-their-categories/
Foody, M., Samara, M., & Carlbring, P. (2015). A review
of Cyberbullying and suggestions for online
psychological therapy. In Internet Interventions (Vol. 2,
Issue 3, pp. 235–242). Elsevier. https://doi.org/10.1016/
j.invent.2015.05.002
Garnica Bautista, F. X., & Tepán Mita, E. X. (2019).
Creación de una arquitectura enfocada en la
interacción hombre-computador para aplicaciones de
internet de las cosas en ambientes de vida asistidos.
Iliou, T., & Paschalidis, G. (2011). Using an automated
speech emotion recognition technique to explore the
impact of bullying on pupils’ social life. Proceedings -
2011 Panhellenic Conference on Informatics, PCI
2011, 18–22. https://doi.org/10.1109/PCI.2011.20
ISO 25010. (n.d.). Retrieved January 19, 2022, from
https://iso25000.com/index.php/normas-iso-25000/iso-
25010
Kitchenham, B. (2007). Guidelines for performing
Systematic Literature Reviews in Software
Engineering. https://www.researchgate.net/publicati
on/302924724
Mårtensson, P., Fors, U., Wallin, S. B., Zander, U., &
Nilsson, G. H. (2016). Evaluating research: A
multidisciplinary approach to assessing research
practice and quality. Research Policy, 45(3), 593–603.
https://doi.org/10.1016/J.RESPOL.2015.11.009
Monks, C. P., & Smith, P. K. (2006). Definitions of
bullying: Age differences in understanding of the term,
and the role of experience. In British Journal of
Developmental Psychology (Vol. 24, Issue 4, pp. 801–
821). https://doi.org/10.1348/026151005X82352
Nocentini, A., Zambuto, V., & Menesini, E. (2015a). Anti-
bullying programs and Information and
Communication Technologies (ICTs): A systematic
review. Aggression and Violent Behavior, 23, 52–60.
https://doi.org/10.1016/J.AVB.2015.05.012
Nocentini, A., Zambuto, V., & Menesini, E. (2015b). Anti-
bullying programs and Information and
Communication Technologies (ICTs): A systematic
review. Aggression and Violent Behavior, 23, 52–60.
https://doi.org/10.1016/J.AVB.2015.05.012
Onyema, E. M. (2019). Integration of Emerging
Technologies in Teaching and Learning Process in
Nigeria: the challenges. https://www.researchgate.net/
publication/336278814
Onyema, E., Nwafor, C., Obafemi, F., Sen, S., Atonye, F.,
Sharma, A., & Alsayed, A. (2020). Impact of
Coronavirus Pandemic on Education. Journal of
Education and Practice. https://doi.org/10.7176/jep/
11-13-12
Parime, S., & Suri, V. (2014). Cyberbullying detection and
prevention: Data mining and psychological perspective.
2014 International Conference on Circuits, Power and
Computing Technologies, ICCPCT 2014, 1541–1547.
https://doi.org/10.1109/ICCPCT.2014.7054943
Pedreira, A., Bernardino, B., Bonet De Luna, C., &
Pedreira, P. (2011). Acoso escolar. Revista Pediatría de
Atención Primaria •, 52, 661–670.
Ptaszynski, M., Masui, F., Nakajima, Y., Kimura, Y.,
Rzepka, R., & Araki, K. (2016). Detecting
Cyberbullying with Morphosemantic Patterns.
https://doi.org/10.1109/SCIS&ISIS.2016.89
Raisi, E., & Huang, B. (2016). Cyberbullying Identification
Using Participant-Vocabulary Consistency. Undefined.
http://www.endCyberbullying.org
Raminhos, C., Cláudio, A. P., Beatriz Carmo, M.,
Carvalhosa, S., de Jesus Candeias, M., & Gaspar, A.
(2015, July 28). A serious game to prevent bullying and
promote empathy. 2015 10th Iberian Conference on
Information Systems and Technologies, CISTI 2015.
https://doi.org/10.1109/CISTI.2015.7170404
Reynolds, K., Kontostathis, A., & Edwards, L. (2011).
Using machine learning to detect Cyberbullying.
Proceedings - 10th International Conference on
Machine Learning and Applications, ICMLA 2011, 2,
241–244. https://doi.org/10.1109/ICMLA.2011.152
Silva, Y. N., Hall, D. L., & Rich, C. (2018). BullyBlocker:
toward an interdisciplinary approach to identify
Cyberbullying.
Social Network Analysis and Mining,
8(1). https://doi.org/10.1007/s13278-018-0496-z
Soundar, K., & Ponesakki, P. (2016). Cyberbullying
Detection Based on Text Representation.
Sousa, S. F., & Goncalves, V. (2021, June 23). MOOC on
bullying for primary school teachers. Iberian
A Systematic Literature Review on Technological Solutions to Fight Bullying and Cyberbullying in Academic Environments
419

Conference on Information Systems and Technologies,
CISTI. https://doi.org/10.23919/CISTI52073.2021.94
76525
Topcu-Uzer, C., & Tanrikulu, I. (2018). Technological
solutions for Cyberbullying. In Reducing
Cyberbullying in Schools: International Evidence-
Based Best Practices (pp. 33–47). Elsevier Inc.
https://doi.org/10.1016/B978-0-12-811423-0.00003-1
Washington, E. T. (2014). An Overview of Cyberbullying
in Higher Education: https://doi.org/10.1177/10451595
14558412, 26(1), 21–27. https://doi.org/10.1177/
1045159514558412
Wasson, C. S. (n.d.). System engineering analysis, design,
and development: concepts, principles, and practices.
Retrieved January 19, 2022, from https://www.wiley.
com/en-us/System+Engineering+Analysis%2C+Desig
n%2C+and+Development%3A+Concepts%2C+Princi
ples%2C+and+Practices%2C+2nd+Edition-p-9781118
967157
CSEDU 2022 - 14th International Conference on Computer Supported Education
420
