
New Energy Efficient and Fault Tolerant Methodology based on a
Multi-agent Architecture in Reconfigurable Wireless Sensor Networks
Hanene Rouainia
1 a
, Hanen Grichi
2,4 b
, Laid Kahloul
3 c
and Mohamed Khalgui
4,5 d
1
Faculty of Sciences of Tunis, El-Manar University, Tunis, Tunisia
2
Faculty of Sciences of Bizerte (FSB) - University of Carthage, Bizerte, Tunisia
3
LINFI Laboratory, Computer Science Department, Biskra University, Biskra, Algeria
4
School of Electrical and Information Engineering, Jinan University, Zhuhai, China
5
INSAT Institute, University of Carthage, Tunis, Tunisia
Keywords:
Reconfigurable Wireless Sensor Networks, Multi-agent Architecture, Mobility, Resizing, Mobile Sink Node,
Hardware/Software Failures, Test Packet Technique, Harvesting Energy.
Abstract:
Reconfigurable wireless sensor networks became more complex and dynamic systems. Their importance
increases with time and more challenges appear. The most important challenges in RWSNs are the energy
and software/hardware failure problems. In this paper, we propose a new methodology composed of a set of
solutions summarized in the application of the mobility, resizing, and mobile sink nodes using a multi-agent
architecture and an energy efficient routing protocol. It contains also a test packet technique to detect the
malfunctioning entities and isolate them. Moreover, we develop a simulator named RWSNSim which allows
simulating WSNs and RWSNs with and without application of the proposed methodology. It permits also
to compare the different results using line charts. Finally, we simulate a case study with RWSNSim in a 3D
environment to evaluate the performance of the proposed methodology.
1 INTRODUCTION
Wireless sensor networking is an important wireless
technology that has a wide variety of applications
from small-size to large-scale systems and provides
unlimited future potentials. A wireless sensor net-
work (WSN) is composed of a set of very small
battery-operated devices (SNs). It can be used in
many areas such as medical, military, environmen-
tal monitoring, forecasting, and intelligent home (Vi-
jayalakshmi and Muruganand, 2018). Sensor nodes
(SNs) are the principal devices in WSNs. They com-
municate with each other through wireless communi-
cation to transmit a volume of data to a central station
and to execute a set of tasks that may involve data
processing (Agrawal, 2017).
In WSNs, we have several challenges such as lack
of energy, real-time and hardware/software failures
(Hafidi et al., 2020), (Allouch et al., 2019). These
a
https://orcid.org/0000-0001-7544-988X
b
https://orcid.org/0000-0002-4601-3574
c
https://orcid.org/0000-0002-9739-7715
d
https://orcid.org/0000-0001-6311-3588
problems occur because of several factors such as
WSNs work under many types of renewable energy
resources which are not frequently available, SNs
use limited energy resources, communication volume,
SNs are fragile and prone to failures, harsh environ-
mental conditions, and human effect (Ghribi et al.,
2018), (Rouainia et al., 2020). Many solutions are
proposed to resolve these problems such as reconfig-
uration, mobile sink nodes, mobility, resizing, energy
efficient routing protocols, and fault tolerant routing
protocols (Salem, 2017), (Housseyni et al., 2018).
A reconfigurable wireless sensor network (RWSN)
is a WSN allowing reconfiguration scenarios (Grichi
et al., 2018). In WSNs, all sensor nodes are fixed.
However, sensor nodes in RWSNs can be fixed or mo-
bile (Rouainia et al., 2020).
The originality of this paper lies in the use of
a set of solutions in a unified methodology accord-
ing to a set of rules in energy and time-saving man-
ner. These solutions are effective and inexpensive in
terms of time and cost such as reconfiguration, mo-
bile sink nodes, mobility, and resizing. Each solution
has proven its effectiveness in previous related works
Rouainia, H., Grichi, H., Kahloul, L. and Khalgui, M.
New Energy Efficient and Fault Tolerant Methodology based on a Multi-agent Architecture in Reconfigurable Wireless Sensor Networks.
DOI: 10.5220/0011061300003176
In Proceedings of the 17th International Conference on Evaluation of Novel Approaches to Software Engineering (ENASE 2022), pages 405-416
ISBN: 978-989-758-568-5; ISSN: 2184-4895
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
405

(Rouainia et al., 2020), (Grichi et al., 2018). We
also added a test packet technique to treat the hard-
ware/software failures. It has proven its effectiveness
in detecting failures and treating them as quickly as
possible. Besides the previous novelties in this paper,
we provide also a new tool called RWSNSim. It al-
lows simulating our case studies using the proposed
methodology applying the two well-known routing
protocols: LEACH and WBM-TEEN (Zagrouba and
Kardi, 2021). Our developed simulator provides for
the use of a comprehensive and accurate view of
the proposed methodology’s impact on the network,
which is estimated by a 625% increase in network
lifetime and the failures are discovered and treated
when they occur.
This paper is structured as below. After the intro-
duction section, we present the related works in sec-
tion 2. Then, we resume the background of WSNs,
RWSNs, and the energy issue in Section 3. A new
energy efficient and fault tolerant methodology in
RWSNs is reported in Section 4. Section 5 presents
the experiment simulated using RWSNSim to vali-
date and evaluate the performance of the proposed
methodology. Finally, the conclusion is drawn in sec-
tion 6.
2 RELATED WORKS
The authors of (Housseyni et al., 2018) propose an in-
telligent multi-agent distributed architecture using the
three forms of reconfiguration (software, hardware,
and protocol reconfiguration). Moreover, in (Grichi
et al., 2018), the reconfiguration is considered as an
efficient solution to the energy problem in WSNs be-
cause it makes the WSN satisfy the real-time and en-
ergy constraints taking into consideration the system
performance optimization.
The paper (Chao et al., 2019) considers the un-
manned aerial vehicles (UAVs) as mobile sink nodes
in WSN water monitoring. It proposes a mobile data
collection scheme based on the high maneuverabil-
ity of UAVs. While the paper (Wang et al., 2019)
presents an energy efficient routing schema com-
bined with clustering and sink mobility technologies
in WSNs. Finally, the paper (Zhong and Ruan, 2018)
studies the energy efficient routing method with sup-
port for multiple mobile sink nodes to effectively al-
leviate the hot spot problem.
The papers (Raj et al., 2021) and (Nguyen and
Nguyen, 2020) use the mobility to minimize the to-
tal distance between sensor nodes in the network
and consequently decrease the energy consumption to
keep the network alive as long as possible. Otherwise,
the works in (Ji et al., 2014) and (Erman et al., 2012)
take the geographic resizing of zones as a solution to
energy and coverage problems in WSNs. While the
paper (Grichi et al., 2018) proposes 3D mobility and
dynamic resizing of zones into a new run-time power-
oriented methodology to reduce the energy consump-
tion by sensor nodes.
Several researches suggest energy efficient routing
protocols as effective solutions to the energy prob-
lem in WSNs. Indeed, we have many energy ef-
ficient routing protocols such as e-NL BEENISH,
IQAR, MBC, and WBM-TEEN (Shalini and Vasude-
van, 2021), (Khediri et al., 2021). Many fault tol-
erant protocols are also proposed to treat the soft-
ware/hardware failures such as HDMRP, PFTP, and
FTCP-MWSN (Moussa et al., 2020), (Zagrouba and
Kardi, 2021).
3 BACKGROUND
We present in this section a semi-formal description
of WSNs and RWSNs components and architectures.
We also describe the energy issue detailing the energy
model and problem. Finally, we discuss and detail the
software/hardware problems in WSNs.
3.1 Wireless Sensor Networks
We consider that W is a wireless sensor network in
a 3D environment. It contains a base station BS
and a set of zones S
Z
(W ) = {
Nb
Z
(W )
S
k=1
{Z
k
}}, where
Z
k
is a zone in W and Nb
Z
(W ) is the total num-
ber of zones in W. Each zone Z
k
contains a gateway
{G
k
,k ∈ [1..Nb
Z
]} and a set of fixed sensor nodes for-
malized by S
N
(Z
k
) = {
Nb
N
(Z
k
)
S
i=1
{N
i,k
}}, where N
i,k
is a
node in Z
k
and Nb
N
(Z
k
) is the total number of nodes
in Z
k
.
Each sensor node has a sensing unit
contains a set of sensors formalized by
S
N
i,k
Sens
= {Sens
j,N
i,k
| i ∈ [1..Nb
N
(Z
k
)], k ∈
[1..Nb
Z
(W )] and j ∈ [1..Nb
Sens
(N
i,k
)]}, where
Sens
j,N
i,k
is a sensor in N
i,k
and Nb
Sens
(N
i,k
) is the
total number of sensors in N
i,k
. These sensors are
designed for sensing the chemical and physical
conditions in the surrounding environment such
as temperature, gases, humidity, pressure, etc. It
contains also a power unit composed of two batteries;
the first one is the principal battery B
pr
(N
i,k
) and the
second one is the additional battery B
add
(N
i,k
). The
principal battery is rechargeable by the additional
ENASE 2022 - 17th International Conference on Evaluation of Novel Approaches to Software Engineering
406

battery and this last one is rechargeable from the
harvesting energy (Ramasamy, 2017).
3.2 Reconfigurable Wireless Sensor
Networks
We consider that R is a reconfigurable wireless sen-
sor network in a 3D environment. Firstly, R is based
on a multi-agent architecture used to handle the exe-
cution of the reconfiguration scenarios. We have four
types of agents with different roles: i) The controller
agent Ag
Ctrl
which is designed to control the whole
network. ii) The zone agents {Ag
k
| k ∈ [1..NbZ]}
which control the zones. These two types of agents
are servers with high charge level batteries allowing
them to make important and crucial decisions in the
network such as applying the resizing of zones, pro-
cessing the sensing data, and applying the mobility.
iii) The sink agents {SA
m,k
| m ∈ [1..Nb
SN
(Z
k
)] k ∈
[1..NbZ]} which control the sinks. iv) The node
agents {Ag
i,k
| i ∈ [1..NbN(Z
k
)] k ∈ [1..NbZ]} which
control the sensor nodes. These two types of agents
are software agents installed on the sensor nodes and
mobile sink nodes themselves. They can make a set
of decisions like activation/deactivation and mobil-
ity of sinks and mobile nodes (Grichi et al., 2018),
(Rouainia et al., 2020).
Indeed, R contains a base station BS, a con-
troller agent Ag
Ctrl
, and a set of zones formalized
by S
Z
(R) = {
Nb
Z
(R)
S
k=1
{Z
k
}}, where Z
k
is a zone in R
and Nb
Z
(R) is the total number of zones in R. Each
zone Z
k
contains a zone agent Ag
k
, a set of mo-
bile sink nodes formalized by S
SN
(Z
k
) = {SN
m,k
| k ∈
[1..Nb
Z
] m ∈ [1..Nb
SN
(Z
k
)]}, where SN
m,k
is a mo-
bile sink node in Z
k
and Nb
SN
(Z
k
) is the num-
ber of mobile sink nodes in Z
k
, and a set of
sensor nodes formalized by S
N
(Z
k
) = {N
i,k
| k ∈
[1..Nb
Z
] i ∈ [1..Nb
N
(Z
k
)]}. We have two types
of sensor nodes: fixed and mobile ones. The
fixed sensor nodes are formalized by S
FN
(Z
k
) =
{N
i,k
| k ∈ [1..Nb
Z
] i ∈ [1..Nb
N
(Z
k
)]}. The mobile
sensor nodes are formalized by S
MN
(Z
k
) = {N
i,k
| k ∈
[1..Nb
Z
] i ∈ [1..Nb
N
(Z
k
)]}. We denote that S
MN
∪
S
FN
= S
N
and S
MN
∩ S
FN
= ∅}.
Otherwise, in R the fixed sensor nodes are the
same in W, but the mobile sensor nodes differ in terms
of the existence of a mobilizer and a location finder.
The mobilizer permits to mobile sensor node to move
easily in the network. The location finder is used to
identify its position (Tzounis et al., 2017), (Robinson
et al., 2017). The mobile sink nodes play the role
of gateways between sensor nodes and zone agents.
They have the same components of mobile sensor
nodes without the sensing unit and with two high-
charge level batteries (Ramasamy, 2017).
Each entity in W and R has three coordinates
representing its position. These coordinates are for-
malized by {(x
E
,y
E
,z
E
)|E ∈ {S
N
,S
SN
,S
G
,S
Ag
,BS}},
where S
G
is the set of gateways in W.
The total charge of each entity E in W and R is for-
malized by C(E) = C(B
pr
(E)) + C(B
add
(E)). While
the charge capacity of each entity E in W and R
is formalized by capacity(E) = capacity(B
pr
(E)) +
capacity(B
add
(E)).
3.3 Energy Issue
In the following, we present an energy model, the
most energy-consuming tasks and we formalize the
energy problem in R. We define also the software and
hardware failure problems in R.
3.3.1 Energy Model
We consider that in each period ρ, each entity in R
can execute a set of tasks. These tasks are formalized
by T = {τ
1
,τ
2
,...,τ
Nb
τ
(E)
}|E ∈ {S
N
,S
SN
,S
Ag
}, where
Nb
τ
(E) is the total number of tasks that can be exe-
cuted by E in ρ. Each task τ
a
is linked to a trilogy for-
malized by Tr
E,ρ
= (t
exec
(τ
a
(E)),e
c
(τ
a
(E)), p
τ
a
(E)),
where t
exec
(τ
a
(E)) is the execution time of τ
a
(E),
e
c
(τ
a
(E)) is the energy consumed by E to execute τ
a
and p
τ
a
(E) is a function formalized by:
p
τ
a
(E) = n i f τ
a
is executed n times
p
τ
a
(E) = 0 i f not
(1)
In order to predict the approximate value of the en-
ergy produced by the additional battery in each entity
E in R in a period ρ, we formalize it in the following
formula:
EP
[ρ]
(E) =
Z
t
y
t
x
t
j
∑
t
i
[e
prod
× (t
j
−t
i
)] (2)
where e
prod
is the produced energy in each time unit,
t
x
≤ t
i
≤ t
y
,t
x
≤ t
j
≤ t
y
and ρ = |t
y
−t
x
|.
Table 1 presents a set of the most energy-
consuming tasks executed by different entities in R.
In order to predict the approximate value of the
energy consumed by each entity E in R in a period ρ,
we formalize it by:
EC
[ρ]
(E) =
Z
t
y
t
x
Nb
E
τ
∑
a=1
(p
τ
a
(E) × e
c
(τ
a
(E)))dt + ε (3)
such that ρ = |t
y
−t
x
|, Nb
E
τ
is the number of tasks ex-
ecuted by E in the period ρ.
New Energy Efficient and Fault Tolerant Methodology based on a Multi-agent Architecture in Reconfigurable Wireless Sensor Networks
407
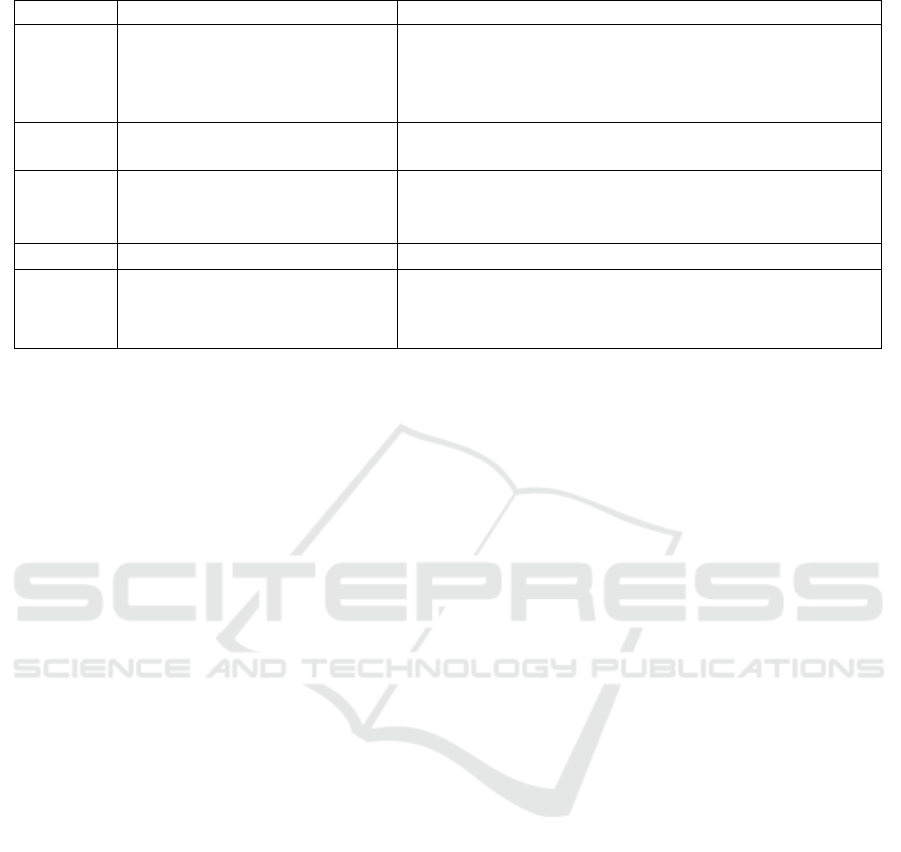
Table 1: Set of the most energy-consuming tasks executed by different entities in R.
E τ
a
(E) Description
τ
1
(E) = ReceptFrom() Receiving packets from predecessors.
E ∈ {S
Ag
, τ
2
(E) = SendTo() Sending packets to successors.
S
SN
,S
N
} τ
3
(E) = Deactivate() Deactivate the entity E.
τ
4
(E) = Activate() Activate the entity E.
Ag
Ctrl
τ
5
(Ag
Ctrl
) = Resizing() Apply the resizing of zones.
τ
6
(Ag
Ctrl
) = Isolate(Ag
k
) Isolate the zone agent Ag
k
.
τ
5
(Ag
k
) = ApplyMobility() Apply the mobility of mobile entities.
Ag
k
τ
6
(Ag
k
) = Isolate(E) Isolate the entity E where E ∈ {S
N
,S
SN
}.
τ
7
(Ag
k
) = OrganizeNodes() Organize the sensor nodes in Z
k
into clusters in subzones.
SN
m,k
τ
5
(SN
m,k
) = MoveTo() Moving to another position in Z
k
.
N
i,k
τ
5
(N
i,k
) = SensingBy(Sens
j,N
i,k
) Sensing the physical and chemical conditions of the
surrounding environment by Sens
j,N
i,k
.
τ
6
(N
i,k
) = MoveTo() Moving to another position where N
i,k
∈ S
MN
.
3.3.2 Energy Problem
Considering that R operates under a renewable en-
ergy characterized by the oscillating presence in the
surrounding environment. We assume that the energy
consumption times can interfere with energy produc-
tion times. However, many times the renewable en-
ergy is not available.
We consider that renewable energy is not available
in the time interval [t
a
,t
b
] which can be a long time.
In the meantime, a set of entities in R still working
and executing the most energy-consuming tasks men-
tioned in Table 1. So the energy produced in each
entity is almost equal to zero (i.e., EP
[t
a
,t
b
]
≈ 0). On
the other side, the charge of entities will reach the β
threshold (i.e., C(E) ≤ β ).
Therefore, as more time passes, more entities will
be deactivated. As a result, the distance between
entities that stay alive will be expanded. So, the
consumed energy by these entities will be increased
which speeds up their deactivation. Finally, the num-
ber of remaining active entities will be decreased and
the network can stop working until harvesting energy
returns or human intervention which is unpleasant.
3.4 Software & Hardware Failure
Problems
We know that the sensor nodes are fragile and prone
to software or hardware failures, especially if they
were placed in dangerous environments. They may
fail because of several reasons such as lack of energy,
failure of one of the sensor node components. Be-
cause of environmental effects the sensor nodes may
also sense and transmit incorrect data. Otherwise,
some delays in data communication can occur be-
cause of link failures which can affect network topol-
ogy. In RWSNs that do not use software/hardware
failure detection techniques, every failure affects the
efficiency of the network by disrupting the execution
of reconfiguration scenarios and the data transmission
process. In this paper, we treat the software/hardware
failures that disrupt the receiving and sending tasks
executed by the different network entities.
4 CONTRIBUTION: NEW
ENERGY EFFICIENT AND
FAULT TOLERANT
METHODOLOGY IN RWSNs
In this section, we present our motivation which
resumes the energy challenge and the hard-
ware/software failures problem in RWSNs under
harvesting energy constraints. We present also the
formalization of the proposed methodology and the
used algorithms to apply it.
4.1 Motivation
In WSNs, the principal challenge is to keep the net-
work alive as long as possible without human inter-
vention. In order to keep up with this challenge, it is
important to reduce the consumed energy by network
entities, detect the failures when they happened, treat
them by isolation, and repair them as soon as possible.
So, to do that, we propose a new methodology com-
posed of a set of solutions and techniques. Firstly, we
use a multi-agent architecture to manage the different
reconfiguration scenarios. We use also mobile sink
nodes in each zone, which collect the sensing data
ENASE 2022 - 17th International Conference on Evaluation of Novel Approaches to Software Engineering
408
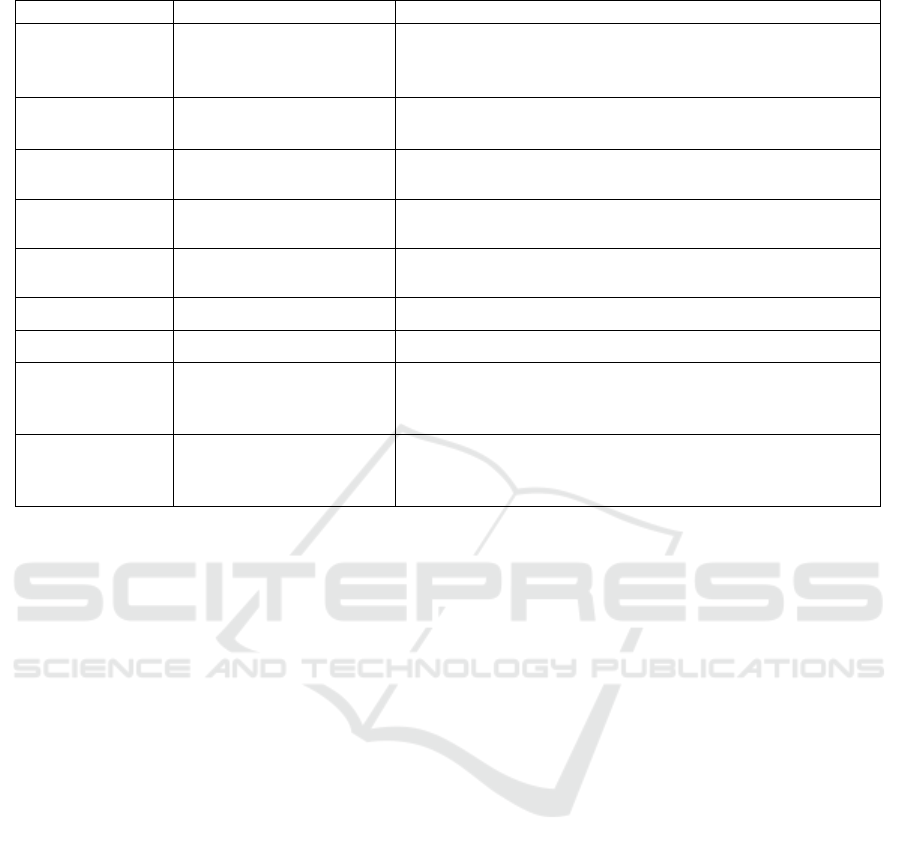
Table 2: Variables and functions used to resolve the energy problem.
Var/Fun Value Definition
α Constant* is a threshold for the energy charge in sensor nodes.
0.15 × capacity(N
i,k
) ≤ It is used by Ag
k
to apply the mobility.
α ≤ 0.2 × capacity(N
i,k
)
β EC
[ρ]
(E) | is a threshold for the energy charge in each entity E
E ∈ {S
Ag
,S
N
,S
SN
} in the network. It is used to deactivate the entity E.
state(E) [0,1] | if E is active it equals 1 else it equals 0.
E ∈ {S
N
,S
SN
,S
Ag
}
isFree(E) [0,1] | if E has moved recently as close to a sensor node
E ∈ {S
MN
,S
SN
} N
a,k
it equals 0 else it equals 1.
EPres(N
i,k
) [0,1] if the energy problem is resolved recently
it equals 1 else it equals 0.
Nb
Act
(N
i,k
,Z
k
)
∑
Nb
N
(Z
k
)
i=1
state(N
i,k
) is the total number of active nodes in Z
k
.
Nb
Act
(SN
m,k
,Z
k
)
∑
Nb
N
(Z
k
)
i=1
state(SN
m,k
) is the total number of active mobile sink nodes in Z
k
γ Constant* is a threshold for the number of active sensor nodes in Z
k
.
0.3 × NbN(Z
k
) ≤ γ It is used by Ag
k
to apply the mobility.
≤ 0.4 × NbN(Z
k
)
λ Constant* is a threshold for the number of active sensor nodes in Z
k
.
0.15× ≤ NbN(Z
k
)λ It is used by Ag
Ctrl
to apply the resizing.
≤ 0.2 × NbN(Z
k
)
from sensor nodes and send them to zone agents. We
also apply the mobility and the resizing of zones to re-
duce the consumed energy and to guarantee the cover-
age of the largest possible area in the network. To re-
solve the hardware/software failures problem, we use
a test packet technique. In order to prove the perfor-
mance of the proposed methodology, we use two rout-
ing protocols which are LEACH and WBM-TEEN.
The first one is characterized as an energy-wasting
routing protocol compared with WBM-TEEN proto-
col, but it guarantees early failure detection using the
test packet technique. The second one is an energy
efficient protocol, but the failure detection may be de-
layed or not ensured. Finally, we develop a simula-
tor named RWSNSim which permits simulating WSNs
and RWSNs using the proposed methodology.
4.2 Formalization
Table 2 defines a set of variables and functions which
are used to describe the energy problem in RWSN.
We present in the following a set of variables used
to detect the malfunctioning entities and isolate them:
• δ ∈ [0..1]: is a percentage factor used to fix the
waiting time to receive the sensing data or the ac-
knowledge messages.
• t
rep
1
(N
i,k
): is a response time of N
i,k
if it receives
a request of sensing data from its predecessors. It
is used by SN
m,k
to detect the cluster containing
the malfunctioning node. It is formalized by:
t
rep
1
(N
i,k
) = Nb
pred
(N
i,k
) × t
exec
(τ
1
(N
i,k
))
+Nb
Sens
(N
i,k
) × t
exec
(τ
5
(N
i,k
))
+|N
i,k
E| ×t
exec
(τ
2
(N
i,k
))]
(4)
where Nb
pred
(N
i,k
) is the number of active pre-
decessors of N
i,k
, E is the successor of N
i,k
and
|N
i,k
E| is the distance between N
i,k
and E.
• dl
1
(N
i,k
,SN
m,k
): is a receiving task deadline used
by SN
m,k
to receive the sensing data from N
i,k
,
where N
i,k
is a cluster head. It is formalized by:
dl
1
(N
i,k
,SN
m,k
) = (1 + δ) × (
Nb
succ
(SN
m,k
)
∑
i=1
(t
exec
(τ
2
(SN
m,k
)) × |V Succ
SN
m,k
[i]SN
m,k
|))
+
Nb
N
(SZ
m,k
)
∑
j=1
(t
rep
1
(V NAct
SZ
m,k
[ j]))
+Nb
pred
(SN
m,k
) × t
exec
(τ
1
(SN
m,k
))
(5)
where Nb
succ
(SN
m,k
) is the number of active suc-
cessors of SN
m,k
, V Succ
SN
m,k
is the vector which
contains them, and V NAct
SZ
m,k
is the list of active
sensor nodes in SZ
m,k
.
• t
rep
1
(SN
m,k
): is a response time of SN
m,k
if it re-
ceives a request of sensing data from Ag
k
. It is
formalized by:
New Energy Efficient and Fault Tolerant Methodology based on a Multi-agent Architecture in Reconfigurable Wireless Sensor Networks
409
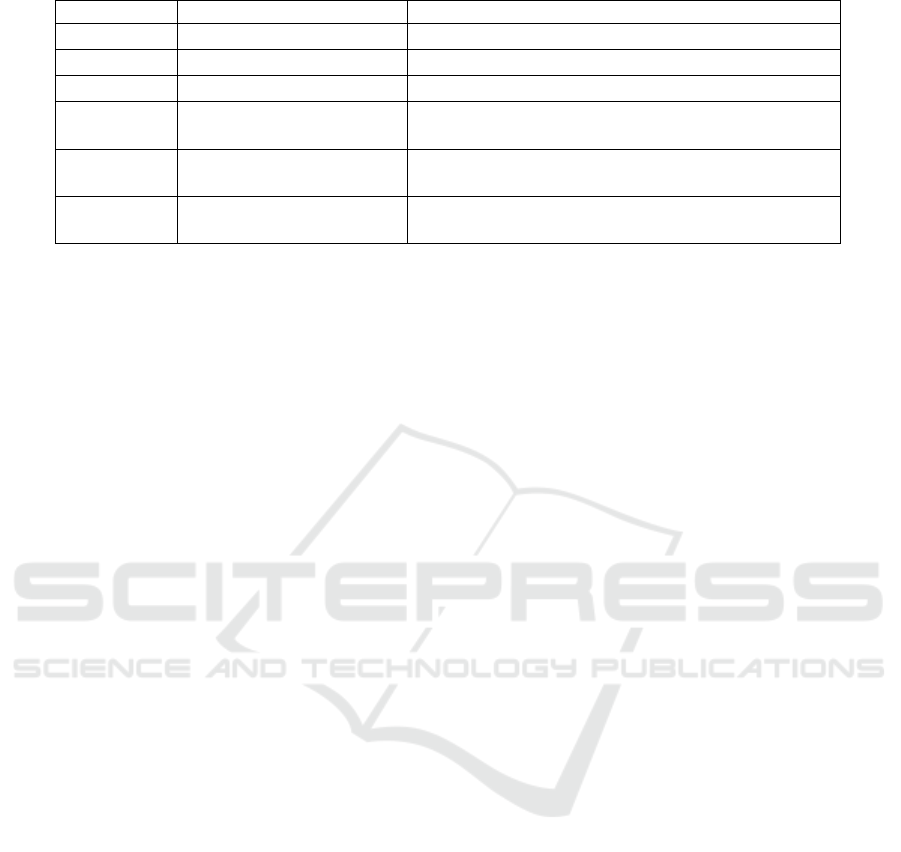
Table 3: Variables used to send alert messages to Ag
Ctrl
and BS to calling a human intervention.
Var Value Definition
Nb
f lrN
(Z
k
) [0..Nb
N
(Z
k
)] is the number of malfunctioning sensor nodes in Z
k
Nb
f lrSN
(Z
k
) [0..Nb
SN
(Z
k
)] is the number of malfunctioning sink nodes in Z
k
Nb
f lrAg
(R) [0..Nb
Z
(R)] is the number of malfunctioning zone agents in R
f lrN Constant* is a threshold for the number of malfunctioning
f lrN ≥ 0.1 × NbN(Z
k
) sensor nodes in each zone.
f lrSN Constant* is a threshold for the number of malfunctioning
f lrSN ≥ 0.2 × NbSN(Z
k
) sink nodes in each zone.
f lrAg Constant* is a threshold for the number of malfunctioning
f lrAg ≥ 0.1 × NbZ zone agents in R.
t
rep
1
(SN
m,k
) = t
exec
(τ
1
(SN
m,k
)) +
Nb
succ
(SN
m,k
)
∑
i=1
(t
exec
(τ
2
(SN
m,k
)) × |V Succ
SN
m,k
[i]SN
m,k
|)
+
Nb
NAct
(SZ
m,k
)
∑
j=1
(t
rep
1
(V NAct
SZ
m,k
[ j]))
+Nb
pred
(SN
m,k
) × t
exec
(τ
1
(SN
m,k
))
+|SN
m,k
Ag
k
| × t
exec
(τ
2
(SN
m,k
))
(6)
where Nb
NAct
(SZ
m,k
) is the number of active sen-
sor nodes in the subzone SZ
m,k
, V N
SZ
m,k
is the vec-
tor which contains them and Nb
pred
(SN
m,k
) is the
number of active predecessors of SN
m,k
.
• dl
1
(SN
m,k
,Ag
k
): is a receiving task deadline used
by Ag
k
to receive sensing data from SN
m,k
. It is
formalized by:
dl
1
(SN
m,k
,Ag
k
) = (1 + δ)×
(|Ag
k
SN
m,k
| × t
exec
(τ
2
(Ag
k
))
+t
rep
1
(SN
m,k
) + t
exec
(τ
1
(Ag
k
)))
(7)
• t
rep
1
(Ag
k
): is a response time of Ag
k
if it receives
a request of sensing data from Ag
Ctrl
. It is formal-
ized by:
t
rep
1
(Ag
k
) = t
exec
(τ
1
(Ag
k
)) +
Nb
SN
(Z
k
)
∑
m=1
(t
rep
1
(SN
m,k
) + (|Ag
k
SN
m,k
| × t
exec
(τ
2
(Ag
k
))))
+Nb
SNAct
(Z
k
) × t
exec
(τ
1
(Ag
k
))
+|Ag
k
Ag
Ctrl
| × t
exec
(τ
2
(Ag
k
))
(8)
where Nb
SNAct
(Z
k
) is the number of active mobile
sink nodes in Z
k
.
• dl
1
(Ag
k
,Ag
Ctrl
): is a receiving task deadline used
by Ag
Ctrl
to receive sensing data from Ag
k
. It is
formalized by:
dl
1
(Ag
k
,Ag
Ctrl
) = (1 + δ)×
(|Ag
Ctrl
Ag
k
| × t
exec
(τ
2
(Ag
Ctrl
))
+t
rep
1
(Ag
k
) + t
exec
(τ
1
(Ag
Ctrl
)))
(9)
• t
rep
2
(E
1
): is a response time of E
1
if it receives a
test packet from E
2
. It is formalized by:
t
rep
2
(E
1
) = t
exec
(τ
1
(E
1
))
+|E
1
E
2
| × t
exec
(τ
2
(E
1
))
(10)
• dl
2
(E
1
,E
2
): is a receiving task deadline used by
E
2
to receive acknowledge messages from E
1
. It
is formalized by:
dl
2
(E
1
,E
2
) = (1 + δ)×
(|E
1
E
2
| × t
exec
(τ
2
(E
2
))
+t
rep
2
(E
1
) + t
exec
(τ
1
(E
2
)))
(11)
where E
1
∈ {S
N
,S
SN
,Ag
k
} and E
2
∈ {S
SN
,S
Ag
}
Table 3 defines the variables used to send alert
messages to Ag
Ctrl
and BS to calling a human inter-
vention.
(*) All the constant values of thresholds must be
defined by the administrator of the network.
We propose a set of rules to regulate the ap-
plication of different reconfiguration scenarios, the
proposed techniques and to distribute the different
responsibilities in the network. Rule 1 tunes the
application of the mobility. Rule 2 regulates the
application of the resizing of zones. On the other
hand, Rule 3 is used to detect the malfunctioning
entities. While we use Rule 4 to isolate them. Figures
1, 2, 3 and 4 show the illustration diagrams of these
rules.
Rule 1: Application of the mobility of mobile entities
(mobile sensor nodes and mobile sink nodes).
Cdt 1: if (state(N
i,k
) = 1 & C(N
i,k
) ≤
α & EPres(N
i,k
) = 0 & Nb
Act
(N
i,k
,Z
k
) > γ & N
i,k
∈
SZ
m,k
) then Ag
k
decides to apply the mobility of
SN
m,k
considering the following subconditions:
ENASE 2022 - 17th International Conference on Evaluation of Novel Approaches to Software Engineering
410
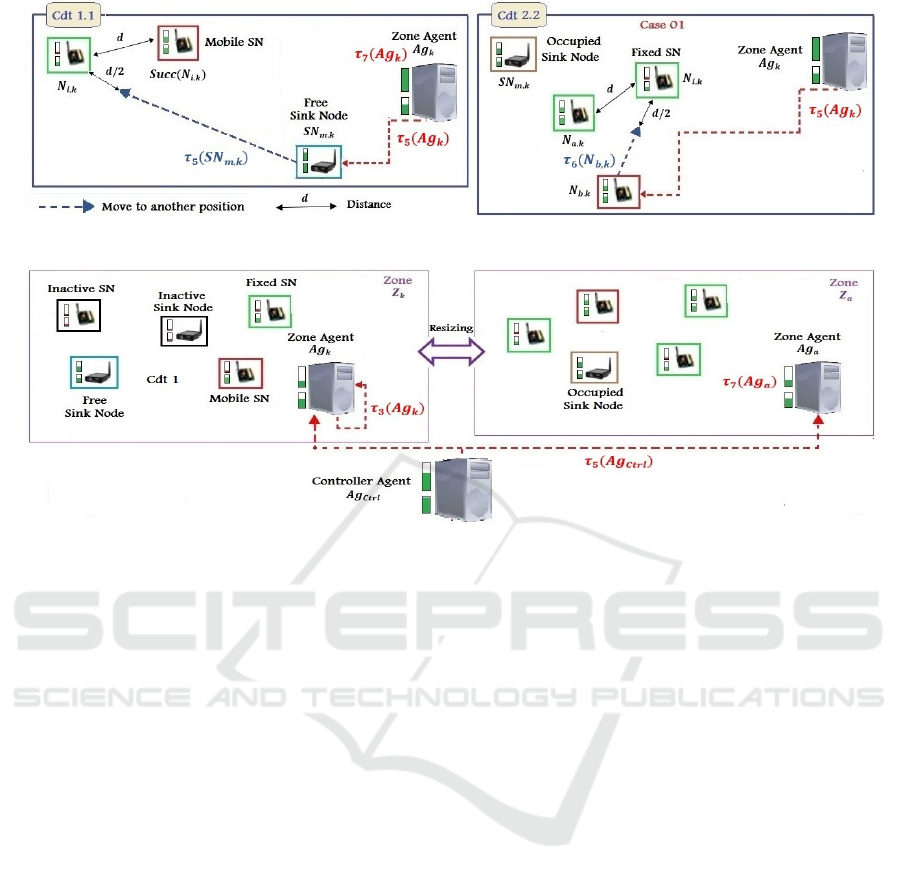
Figure 1: Rule 1 illustration diagram.
Figure 2: Rule 2 illustration diagram.
Cdt 1.1: if (isFree(SN
m,k
) = 1) then the follow-
ing tasks will be executed by Ag
k
and SN
m,k
:
τ
5
(Ag
k
) = ApplyMobility()
τ
5
(SN
m,k
) = MoveTo()
Cdt 1.2: if (isFree(SN
m,k
) = 0) then N
i,k
must
continue its execution at the same pace until the en-
ergy problem is solved or until the deactivation.
Cdt 2: if (state(N
i,k
) = 1 & C(N
i,k
) ≤
α & EPres(N
i,k
) = 0 & Nb
Act
(N
i,k
,Z
k
) ≤ γ & N
i,k
∈
SZ
m,k
) then Ag
k
decides to apply the mobility of SN
m,k
or of the closest mobile sensor node to N
i,k
in SZ
m,k
considering the following subconditions:
Cdt 2.1: if (|N
i,k
SN
m,k
| ≤ |N
i,k
E| where E ∈
{SN
m,k
,N
b,k
} such that N
b,k
is the closest mobile sen-
sor node to N
i,k
) then Ag
k
has the following two cases:
case 1: if (isFree(SN
m,k
) = 1) then Ag
k
decides
to apply the mobility of SN
m,k
(Cdt 1.1 without con-
sidering the Cdt 1 conditions).
case 2: if (isFree(SN
m,k
) = 0) then Ag
k
decides
to apply the mobility of N
b,k
(Cdt 2.2 without consid-
ering the Cdt 2 conditions).
Cdt 2.2: if (|N
i,k
SN
m,k
| > |N
i,k
N
b,k
|) then Ag
k
has
the following two cases:
case 1: if (isFree(N
b,k
= 1) & C(N
b,k
) > α +
[
R
t
y
t
x
(e
c
(τ
6
(N
b,k
))dt + ε)]) where:
e
c
(τ
6
(N
b,k
)) = (|N
i,k
N
b,k
| − |N
i,k
N
a,k
|/2) × e
Mob
where N
a,k
is the successor of N
i,k
and e
Mob
is the en-
ergy consumed by N
b,k
to move one meter.
In this case, Ag
k
decides to apply the mobility of
N
b,k
. Therefore the following tasks will be executed
by Ag
k
and N
b,k
:
τ
5
(Ag
k
) = ApplyMobility()
τ
6
(N
b,k
) = MoveTo()
τ
7
(Ag
k
) = OrganizeNodes()
Case 2: if (isFree(N
b,k
= 0) or
C(N
b,k
) ≤ α + [
R
t
y
t
x
(e
c
(τ
6
(N
b,k
))dt + ε)]) then
Ag
k
decides to apply the mobility of SN
m,k
(Cdt 1
without considering the Cdt 1 conditions).
Rule 2: Application of the resizing of zones in R.
Cdt 1: if (Nb
Act
(N
i,k
,Z
k
) ≤ λ) then Ag
Ctrl
de-
cides to apply the resizing between Z
k
and the neigh-
bor zone Z
a
which contains the minimum number of
active sensor nodes and active sink nodes, or only the
zone which contains the minimum number of active
sink nodes in case of equality of active sensor nodes
and vice versa. Therefore, the following tasks will be
executed by Ag
Ctrl
and Ag
k
:
τ
5
(Ag
Ctrl
) = Resizing()
τ
3
(Ag
k
) = Deactivate()
τ
7
(Ag
k
) = OrganizeNodes()
Rule 3: Detecting the malfunctioning entities in R.
Cdt 1: if ((t
rep
1
(N
i,k
) > dl
1
(N
c,k
,SN
m,k
)) where
N
c,k
is a cluster head) then SN
m,k
sends a test packet to
New Energy Efficient and Fault Tolerant Methodology based on a Multi-agent Architecture in Reconfigurable Wireless Sensor Networks
411

N
c,k
cluster sensor nodes from the closest one to the
malfunctioning one to detect it.
Cdt 1.1: if((t
rep
2
(N
i,k
) > dl
2
(N
i,k
,SN
m,k
))) then
SN
m,k
sends an alert message to Ag
k
to inform it of
a failure in N
i,k
to isolate it. Therefore the following
tasks will be executed by Ag
k
:
τ
6
(Ag
k
) = Isolate(N
i,k
)
τ
7
(Ag
k
) = OrganizeNodes()
Cdt 2: if ((t
rep
1
(SN
m,k
) > dl
1
(SN
m,k
,Ag
k
))) then
Ag
k
decides to send a test packet to SN
m,k
to detect if
it is a malfunctioning sink node.
Cdt 2.1: if ((t
rep
2
(SN
m,k
) > dl
2
(SN
m,k
,Ag
k
)))
then Ag
k
decides to isolate SN
m,k
. Therefore the fol-
lowing tasks will be executed by Ag
k
:
τ
6
(Ag
k
) = Isolate(SN
m,k
)
τ
7
(Ag
k
) = OrganizeNodes()
Cdt 3: if ((t
rep
1
(Ag
k
) > dl
1
(Ag
k
,Ag
Ctrl
))) then
Ag
Ctrl
decides to send a test packet to Ag
k
to detect if
it is a malfunctioning zone agent.
Cdt 3.1: if ((t
rep
2
(Ag
k
) > dl
2
(Ag
k
,Ag
Ctrl
))) then
Ag
Ctrl
decides to isolate Ag
k
and apply the resizing of
zones (Rule 2). Therefore the following tasks will be
executed by Ag
Ctrl
:
τ
6
(Ag
Ctrl
) = Isolate(Ag
k
)
τ
5
(Ag
Ctrl
) = Resizing()
Rule 4: Resolve the hardware/software failures
problem in R.
Cdt 1: if (Nb
f lrN
(Z
k
) ≥ f lrN || Nb
f lrSN
(Z
k
) ≥
f lrSN) then Ag
k
sends an alert message to Ag
Ctrl
that
sends it to the base station BS for human intervention.
Cdt 2: if Nb
f lrAg
(R) ≥ f lrAg then Ag
Ctrl
sends
an alert message to the base station BS for human in-
tervention.
4.3 Algorithms
To apply the mobility in Z
k
, Ag
k
must execute Algo-
rithm 1 according to the Rule 1 conditions. Other-
wise, the controller agent Ag
Ctrl
executes Algorithm
2 to apply the resizing task according to the Rule 2
conditions. Finally, each zone agent Ag
k
must exe-
cute Algorithm 3 & 4 to detect and isolate the mal-
functioning sinks.
5 EXPERIMENTATION
In the following, we will describe the RWSNSim sim-
ulator mentioning the services it provides. Then, we
will present a case study of WSN and RWSN desig-
nated to protect the forests against fires to preserve the
lives of animals and humans. Finally, we will evaluate
the performance of the proposed methodology.
Algorithm 1: Apply the mobility in Z
k
.
Input: Set of sensor nodes and mobile sink nodes.
Output: Minimize the total distance be-
tween sensor nodes and mobile sink
nodes.
for i = 0 to V SZ.size() do
for j = 0 to V SZ.get(i).vnactive.size() do
N ← V SZ.get(i).vnactive.get( j)
if (Rule 1.Cdt 1.Cdt 1.1) || (Rule 1.Cdt 2.Cdt
2.1.case 1) || (Rule 1.Cdt 2.Cdt 2.2.case 2) &
(Rule 1.!(Cdt 1.Cdt 1.1)) then
S ← V SZ.get(i).getSink()
S.moveascloseTo(N)
end if
if ((Rule 1.Cdt 2.Cdt 2.1.case 2) & (Rule
1.Cdt 2.!(Cdt 2.2).case 1)) || (Rule 1.Cdt
2.Cdt 2.2.case 1) then
M ← N.getclosestMN()
M.moveascloseTo(N)
end if
end for
end for
Algorithm 2: Resizing of zones in R.
Input: Set of active zones.
Output: Cover the possible largest zones in
R.
for i = 0 to NbZ do
Z ← V Z.get(i)
if Rule 2.Cdt 1 then
Z1 ← f indAppropriateNeigh()
end if
if Z 6= null AND Z1 6= null then
Z.Ag.deactivate()
for j = 0 to Z.Ag.NbNAct do
Z1.Ag.V N.add(Z.Ag.V NAct.get( j))
for k = 0 to Z.NbSink do
S ← Z.Ag.V SZ.get(k).getSink()
if S.state = 1 then
Z1.Ag.V SZ.add(Z.Ag.V SZ.get(k))
end if
end for
end for
f indNeigh(Z1)
end if
end for
ENASE 2022 - 17th International Conference on Evaluation of Novel Approaches to Software Engineering
412
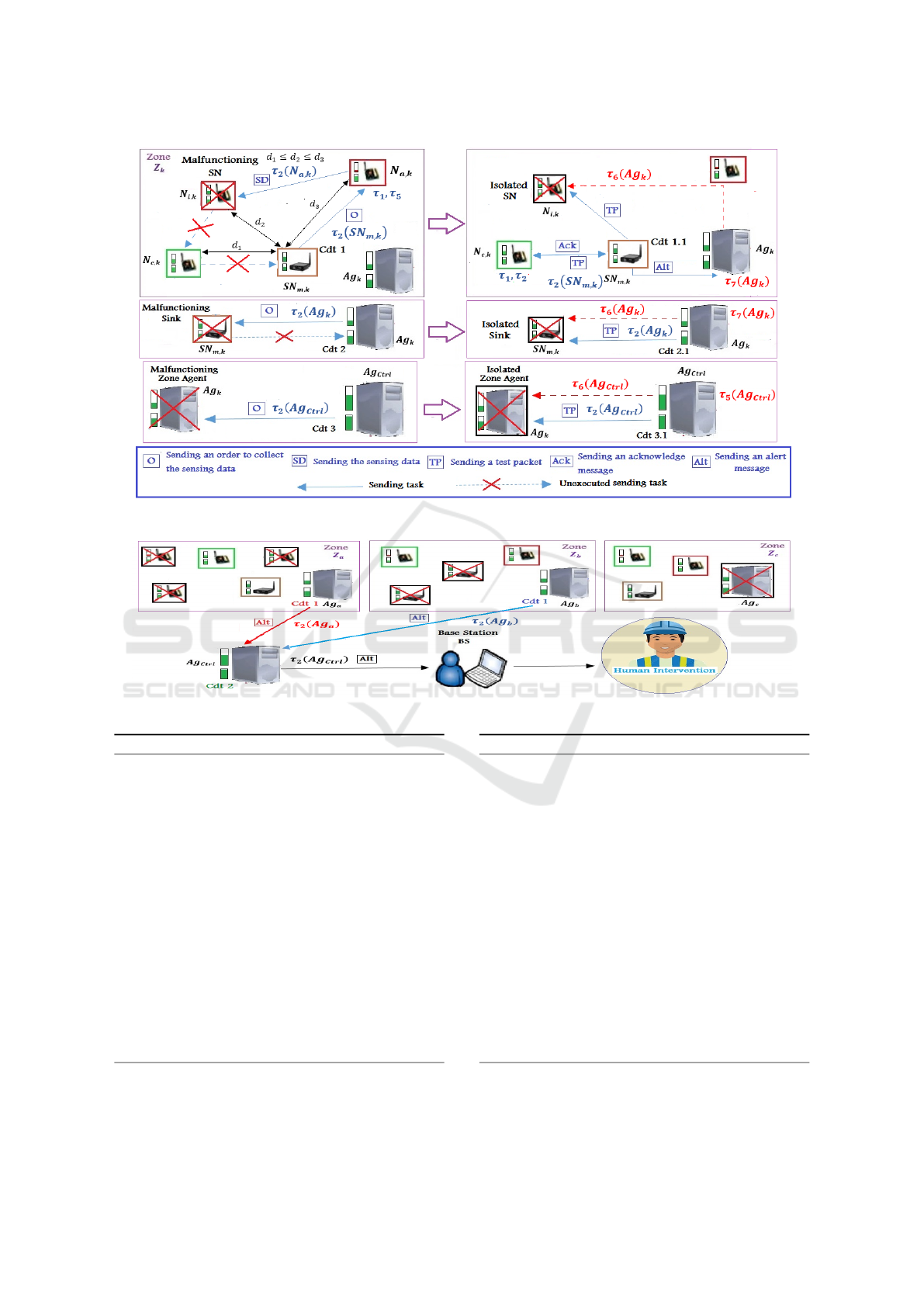
Figure 3: Rule 3 illustration diagram.
Figure 4: Rule 4 illustration diagram.
Algorithm 3: Detect the malfunctioning sinks by Ag
k
.
Input: Set of active sink nodes.
Output: Detect the malfunctioning
sinks.
sendT stPck ← f alse
AllSinksVeri f ← f alse
startTime ← currentTime()
while AllSinksVeri f = f alse do
endTime ← currentTime()
waitTime ← endTime − startTime
for i = 0 to V S.size() do
if waitTime > dl1(V S.get(i),Ag) then
V ST stPck.add(V S.get(i))
sendT stPckTo(V S.get(i))
sendT stPck ← true
end if
end for
end while
Algorithm 4: isolate the malfunctioning sinks by Ag
k
.
Input: Set of active sink nodes.
Output: Isolate the malfunctioning sink
nodes.
AllSinksVeri f ← f alse
if sendT stPck = true then
startTime ← currentTime()
while AllSinksVeri f = f alse do
endTime ← currentTime()
waitTime ← endTime − startTime
for i = 0 to V ST stPck.size() do
S ← V ST stPck.get(i)
if waitTime > dl2(S, Ag) then
isolate(S)
end if
end for
end while
end if
New Energy Efficient and Fault Tolerant Methodology based on a Multi-agent Architecture in Reconfigurable Wireless Sensor Networks
413

5.1 RWSNSim Simulator
To be able to evaluate the proposed methodology, we
develop a simulator named RWSNSim using Java. It
permits creating WSNs and RWSNs and save them in
a database using hsqldb. It provides two routing pro-
tocols (LEACH and WBM-TEEN) and executes the
simulation graph using jgraph, jgraphx, and jgrapht
libraries. It provides also an execution report for each
monitoring time, drawing the resulting line charts af-
ter the simulation using jfreechart library. Finally, It
permits comparing the different networks and simula-
tions.
5.2 Case Study
In order to clarify the performance of the proposed
methodology, we use in this case study a small WSN
(W) and a small RWSN (R) designated to protect the
forests against fires.
(W) consists of i) a base station BS, ii) 4 zones
{Z
1
, Z
2
, Z
3
, Z
4
}, iii) each zone is composed of a gate-
way G
k
, where k ∈ [1..4] and a set of 20 nodes defined
by S
N
(Z
k
) = {N
i,k
i ∈ [1..20] and k ∈ [0..4]}, and
iv) each node N
i,k
has a temperature and a CO
2
sensor.
(R) is composed of i) a base station BS, ii) a con-
troller agent Ag
Ctrl
, iii) 4 zones {Z
1
, Z
2
, Z
3
, Z
4
}, iv)
each zone contains a zone agent Ag
k
, where k ∈ [1..4],
a set of 3 mobile sink nodes defined by S
SN
(Z
k
) =
SN
j,k
j ∈ [1..3] and k ∈ [1..4] and a set of 20 nodes
(12 fixed and 8 mobile ones) defined by S
N
(Z
k
) =
{N
i,k
i ∈ [1..20] and k ∈ [1..4]}, and v) each node
N
i,k
has a temperature and a CO
2
sensor.
5.3 Evaluation of Performance
To figure out the performance of the proposed
methodology, we execute the proposed case study in
RWSNSim. In the following, we will show the ob-
tained results in the worst case. That is, during the
months when the energy production by each entity E
is negligible (EP
[ρ]
(E) ≈ 0) and the consumed energy
is high (EC
[ρ]
(E) > 0). Figure 5 shows the obtained
line charts. Table 4 resumes the obtained results as
percentages of success.
Table 4: The obtained results as percentages of success.
(a) & (c) (b) & (d) % success
(a) & (b) 16 days 21 days 31.25%
(c) & (d) 88 days 116 days 31,82%
% success 450% 452.38% 625%
Through Figure 5 and Table 4, we remark that
the effectiveness of the use of WBM-TEEN proto-
col achieves a success rate approx 32%. While, the
effectiveness of the proposed methodology with the
use of a same routing protocol achieves a success rate
approx 450%. Otherwise, the proposed methodol-
ogy achieves a success rate of 625% with the use of
WBM-TEEN protocol compared to the case when we
use LEACH protocol without the proposed methodol-
ogy.
On the other side, when a software/hardware fail-
ure is committed in an entity in case (a) or (b), the
packets dropping problem will occur in W. The prob-
lem may reach a complete network shutdown. While
in case (c), the failure will be detected and isolated.
Thus, eliminating the packets dropping problem and
R will still work without problems.
According to the obtained results, we can come
up with an important inference which is the choosing
of the appropriate routing protocol. We can choose
LEACH protocol as an appropriate routing protocol
in two cases. The first one is if the network needs pe-
riodic monitoring and the sensor nodes are required to
send the sensing data periodically. The second one is
if the network needs to detect the failures quickly and
isolate the malfunctioning entities when they happen.
Otherwise, we can choose WBM-TEEN protocol as
an appropriate routing protocol in two cases. The first
one is if the network doesn’t need periodic monitor-
ing and the sensor nodes are required to send the sens-
ing data only when their values exceed the thresholds.
The second one is if the network needs more to reduce
the energy consumption than the failure detection.
To show the benefits of the proposed methodology
compared to related works, we make two comparison
scenarios. In the first scenario, we compare between
different simulations of R defined as follows:
• Simulation 1: with an energy efficient routing pro-
tocol.
• Simulation 2: with resizing of zones.
• Simulation 3: with mobility of mobile nodes.
• Simulation 4: with mobility of mobile entities.
• Simulation 5: with proposed methodology.
Figure 6 shows the results of these simulations.
Based on the first scenario, we conclude that the
use of only one or two solutions to resolve the cited
problems, as in some related works, can extend the
lifetime of the network. In fact, this network lifetime
extension is by a small percentage compared to the
achieved extension using the proposed methodology.
In the second scenario, we compare the percentage
of success of this work with related works. We have
three contributions defined as follows:
• Cont 1: is the contribution of the paper (Grichi
et al., 2018).
ENASE 2022 - 17th International Conference on Evaluation of Novel Approaches to Software Engineering
414
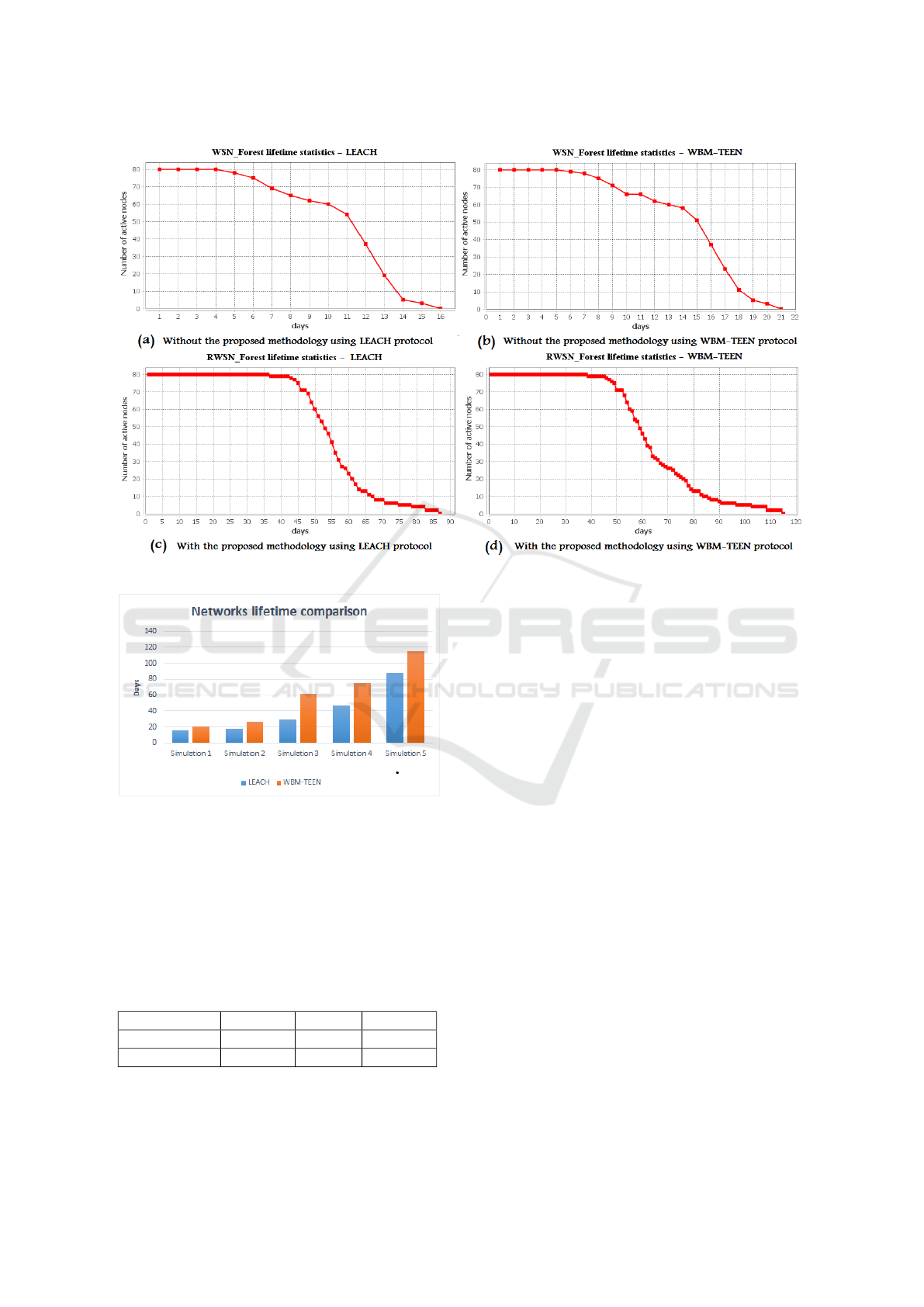
Figure 5: Simulation results.
Figure 6: Networks lifetime comparison.
• Cont 2: is the contribution of the paper (Rouainia
et al., 2020).
• Cont 3: is the proposed contribution of this paper.
To ensure an accurate comparison between these three
contributions, we simulated the proposed case study
using the proposed methodology in each contribution.
Table 5 presents the obtained results.
Table 5: The obtained results of the three contributions.
Cont 1 Cont 2 Cont 3
LEACH 136.36% 248% 450%
WBM-TEEN 172.09% 288.2% 452.38%
Looking at previous comparisons, we remark that
by using the proposed methodology we can keep the
network alive two to three times as long as compared
to related works whatever the used routing protocol.
Finally, taking into consideration that this experi-
mentation was executed by low batteries charged to
avoid extending the simulation time. We conclude
that the proposed methodology proves its efficacy in
keeping the network alive for very long periods that
may reach decades without human intervention.
6 CONCLUSION
In this paper, we propose a new methodology to re-
solve the energy and hardware/software failure prob-
lems in RWSNs to keep the network alive as long as
possible. It consists of the use of mobile sink nodes,
the application of mobility and resizing of zones, and
using the test packet technique to detect the malfunc-
tioning entities and isolate them. It is based on a
multi-agent architecture and an energy efficient pro-
tocol taking into consideration a set of rules. Other-
wise, we develop a simulator named RWSNSim which
permits the construction of WSNs and RWSNs with
and without using the proposed methodology. It also
provides two routing protocols LEACH and WBM-
TEEN. We have proven the efficacy of the proposed
methodology, which reached a success rate of 625%.
In the future, we will strive to improve the effective-
ness of the proposed methodology. We aim also to
New Energy Efficient and Fault Tolerant Methodology based on a Multi-agent Architecture in Reconfigurable Wireless Sensor Networks
415

improve the simulator RWSNSim and make it include
more options and routing protocols.
REFERENCES
Agrawal, D. P. (2017). Sensor nodes (sns), camera sensor
nodes (c-sns), and remote sensor nodes (rsns). In Em-
bedded Sensor Systems, pages 181–194. Springer.
Allouch, A., Cheikhrouhou, O., Koub
ˆ
aa, A., Khalgui, M.,
and Abbes, T. (2019). Mavsec: Securing the mavlink
protocol for ardupilot/px4 unmanned aerial systems.
In 2019 15th International Wireless Communications
Mobile Computing Conference (IWCMC), pages 621–
628.
Chao, F., He, Z., Pang, A., Zhou, H., and Ge, J. (2019).
Path optimization of mobile sink node in wireless
sensor network water monitoring system. Complex.,
2019:5781620:1–5781620:10.
Erman, A. T., Dilo, A., and Havinga, P. J. M. (2012). A
virtual infrastructure based on honeycomb tessellation
for data dissemination in multi-sink mobile wireless
sensor networks. EURASIP J. Wirel. Commun. Netw.,
17:1–27.
Ghribi, I., Abdallah, R. B., Khalgui, M., Li, Z., Alnowibet,
K. A., and Platzner, M. (2018). R-codesign: Code-
sign methodology for real-time reconfigurable embed-
ded systems under energy constraints. IEEE Access,
6:14078–14092.
Grichi, H., Mosbahi, O., Khalgui, M., and Li, Z. (2018).
New power-oriented methodology for dynamic re-
sizing and mobility of reconfigurable wireless sen-
sor networks. IEEE Trans. Syst. Man Cybern. Syst.,
48(7):1120–1130.
Hafidi, Y., Kahloul, L., Khalgui, M., Li, Z., Alnowibet, K.,
and Qu, T. (2020). On methodology for the verifica-
tion of reconfigurable timed net condition/event sys-
tems. IEEE Transactions on Systems, Man, and Cy-
bernetics: Systems, 50(10):3577–3591.
Housseyni, W., Mosbahi, O., Khalgui, M., Li, Z., and
Yin, L. (2018). Multiagent architecture for distributed
adaptive scheduling of reconfigurable real-time tasks
with energy harvesting constraints. IEEE Access,
6:2068–2084.
Ji, S., Beyah, R. A., and Cai, Z. (2014). Snapshot and con-
tinuous data collection in probabilistic wireless sen-
sor networks. IEEE Trans. Mob. Comput., 13(3):626–
637.
Khediri, S. E., Nasri, N., Khan, R. U., and Kachouri, A.
(2021). An improved energy efficient clustering pro-
tocol for increasing the life time of wireless sensor
networks. Wirel. Pers. Commun., 116(1):539–558.
Moussa, N., Alaoui, A. E. B. E., and Chaudet, C. (2020). A
novel approach of WSN routing protocols comparison
for forest fire detection. Wirel. Networks, 26(3):1857–
1867.
Nguyen, L. and Nguyen, H. T. (2020). Mobility based net-
work lifetime in wireless sensor networks: A review.
Comput. Networks, 174:107236.
Raj, S. N., Bhattacharyya, D., Midhunchakkaravarthy, D.,
and Kim, T. (2021). Multi-hop in clustering with
mobility protocol to save the energy utilization in
wireless sensor networks. Wirel. Pers. Commun.,
117(4):3381–3395.
Ramasamy, V. (2017). Mobile wireless sensor networks:
An overview. Wireless Sensor Networks—Insights and
Innovations, pages 1–12.
Robinson, Y. H., Julie, E. G., and Balaji, S. (2017). Band-
width and delay aware routing protocol with schedul-
ing algorithm for multi hop mobile ad hoc networks.
Academy of Science, Engineering and Technology,
10(8):1512–1521.
Rouainia, H., Grichi, H., Kahloul, L., and Khalgui, M.
(2020). 3d mobility, resizing and mobile sink nodes
in reconfigurable wireless sensor networks based on
multi-agent architecture under energy harvesting con-
straints. In Proceedings of ICSOFT 2020, volume 97,
pages 394–406. ScitePress.
Salem, M. O. B. (2017). BROMETH: Methodology
to Develop Safe Reconfigurable Medical Robotic
Systems: Application on Pediatric Supracondylar
Humeral Fracture. PhD thesis, Saarland University,
Saarbr
¨
ucken, Germany.
Shalini, V. B. and Vasudevan, V. (2021). e-nl beenish:
extended-network lifetime balanced energy efficient
network integrated super heterogeneous protocol for
a wireless sensor network. Int. J. Comput. Aided Eng.
Technol., 15(2-3):317–327.
Tzounis, A., Katsoulas, N., Bartzanas, T., and Kittas, C.
(2017). Internet of things in agriculture, recent ad-
vances and future challenges. Biosystems engineering,
164:31–48.
Vijayalakshmi, S. and Muruganand, S. (2018). Wireless
Sensor Network: Architecture - Applications - Ad-
vancements. Mercury Learning & Information, 1 edi-
tion.
Wang, J., Gao, Y., Liu, W., Sangaiah, A. K., and Kim, H.
(2019). Energy efficient routing algorithm with mo-
bile sink support for wireless sensor networks. Sen-
sors, 19(7):1494–1512.
Zagrouba, R. and Kardi, A. (2021). Comparative study of
energy efficient routing techniques in wireless sensor
networks. Inf., 12(1):1–28.
Zhong, P. and Ruan, F. (2018). An energy efficient multi-
ple mobile sinks based routing algorithm for wireless
sensor networks. In IOP Conference Series: Materi-
als Science and Engineering, volume 323, pages 1–4.
IOP Publishing.
ENASE 2022 - 17th International Conference on Evaluation of Novel Approaches to Software Engineering
416
