
Privacy-preserving Information Security for the Energy Grid of Things
Mohammed Alsaid
1 a
, Nirupama Bulusu
1
, Abdullah Bargouti
2
, N. Sonali Fernando
2
,
John M. Acken
2
, Tylor Slay
2
and Robert B. Bass
2 b
1
Maseeh College of Engineering and Computer Science, Department of Computer Science,
Portland State University, Portland, U.S.A.
2
Maseeh College of Engineering and Computer Science, Department of Electrical & Computer Engineering,
Portland State University, Portland, U.S.A.
Keywords:
Smart Grid, Security, Privacy.
Abstract:
Smart grid infrastructure relies on information exchange between multiple actors in order to ensure system
reliability. These actors include but are not limited to smart loads, grid control, and energy management
technologies. As information exchange between these actors is susceptible to cyber-attacks, security and
privacy issues are indispensable to ensure a reliable and stable grid. This position paper proposes a privacy-
preserving, trust-augmented secure scheme for a smart grid implementation.
1 INTRODUCTION
The concept of a smart electric power grid can be
defined as a network of grid-interactive generators,
storage systems, and loads that exchange informa-
tion to ensure system reliability, resource adequacy,
and economical provision of electrical power. Un-
like the traditional electrical grids, where power is
uni-directional, power within a smart grid is instead
bi-directional. Grid-interactive devices can be man-
aged efficiently to source, store, and consume power
as both demand and supply fluctuate (Adham et al.,
2022). Moreover, a smart grid relies heavily on au-
tomated digital interactions between its components.
This makes it an attractive target for all types of adver-
saries. Thus, it is of the utmost importance to address
the security of information exchanged between sys-
tem actors and ensure customer information privacy.
For critical infrastructure like electric power sys-
tems, a cyber-attack could be catastrophic. Knowing
that information exchange within a smart grid is sus-
ceptible to cyber-attacks, it is imperative that system
designers address security and privacy problems to
ensure reliable and stable power systems. Multiple
industry standards have been developed for managing
information exchange within power systems, and sev-
eral include security features, such as IEEE 2030.5
and OpenADR (Obert et al., 2019; Herberg et al.,
a
https://orcid.org/0000-0003-0792-5287
b
https://orcid.org/0000-0002-5644-4634
2014; Obi et al., 2020).
Following industry standards with little under-
standing of the system to be developed may pro-
duce a complex system with undetected vulnerabili-
ties (Myagmar et al., 2005). One systematic approach
to finding vulnerabilities of a system is through cre-
ating a threat model for the system at hand. The
creation of a threat model is an iterative process. It
requires one to repeatedly revisit the design and re-
examine the interactions between the system compo-
nents, identify the assets, and identify the threats. Im-
plementing a threat model requires identifying secu-
rity vulnerabilities and possible mitigation strategies,
which can serve as the foundation of the system’s se-
curity.
Identifying assets in threat modeling entails list-
ing all resources to protect, either abstract or con-
crete. Identifying threats requires inspecting the pos-
sible goals of the assumed adversaries. There are sev-
eral methods to identify common threats, such as re-
lying on mnemonics like Spoofing, Tampering, Re-
pudiation, Information Disclosure, Denial of Service,
Elevation of Privilege (STRIDE) or using frameworks
that utilize different metrics like Common Vulner-
ability Scoring System (CVSS) and Security Cards
(Bodeau et al., 2018). The process of drafting security
requirements necessitates reviewing all the identified
threats. For every threat, the goal is to manage its
associated risk by assessing whether to mitigate it or
accept it based on the threat’s severity and the likeli-
110
Alsaid, M., Bulusu, N., Bargouti, A., Fernando, N., Acken, J., Slay, T. and Bass, R.
Privacy-preserving Information Security for the Energy Grid of Things.
DOI: 10.5220/0011050000003203
In Proceedings of the 11th International Conference on Smart Cities and Green ICT Systems (SMARTGREENS 2022), pages 110-116
ISBN: 978-989-758-572-2; ISSN: 2184-4968
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

hood of its occurrence.
To explore how this position paper addresses secu-
rity threats and privacy-preserving features, we struc-
tured the manuscript as follows: A survey of related
work is presented in section 2. A brief overview of
Energy Grid of Things (EGoT) is presented in section
3. Adversary and thread models are considered in sec-
tion 4. Privacy aspects of the EGoT are discussed in
section 5. Security within the EGoT is discussed in
section 6, and trust modeling for unpredictable attack
scenarios is presented in section 7. This is followed
by the conclusion in section 8.
2 RELATED WORK
There exists extensive prior work within the security
community related to smart grid security over the last
decade. Such work is the foundation of many new re-
search trajectories, including ours. This section of the
paper presents closely-related work to our implemen-
tation. Moreover, we briefly discuss how our work
has been influenced by and differs from the examined
earlier work.
Salinas, Sergio, and Li propose two different al-
gorithms to detect energy theft in smart grids (Sali-
nas and Li, 2016). The authors provide a State Esti-
mation with Kalman filter (SEK) algorithm that uses
Kalman filter for theft detection. However, SEK vio-
lates users’ privacy by using their characteristic load
profiles (current and voltage). The authors also pro-
pose a Privacy-Preserving Bias Estimation (PPBE)
algorithm, which preserves users’ privacy through
loosely decoupling filters. Finally, the authors show
that PPBE converges faster than SEK regarding true-
value bias estimation. Our work does not address en-
ergy theft detection. Moreover, load profiles in EGoT
are kept local instead of being shared with external
entities.
Defend and Kursawe present a privacy-preserving
implementation of the smart grid concept (Defend and
Kursawe, 2013). Their implementation makes use of
an Low-overhead Privacy Aggregation approach. The
implementation uses data aggregation and Homomor-
phic Encryption (HE) in smart meters to preserve the
privacy of customers. It also provides an assessment
of the scalability and integration of the approach with
standards like Device Language Message Specifica-
tion and Companion Specification for Energy Meter-
ing. Finally, the authors show that their system poses
little overhead in CPU usage and the time needed to
perform encryption operations.
Wei-jing et al. present a similar approach, which
uses Paillier and El-Gamal signature algorithms to
protect user privacy (Wei-jing et al., 2019). The au-
thors show that their proposed method also protects
users’ identities and power consumption. In the EGoT
smart grid implementation, we make use of data ag-
gregation as a means of preserving privacy. We ad-
dress this more in the privacy section of this paper.
However, we are not using HE to protect privacy. In-
stead, we use randomized energy requests to obfus-
cate the user’s behavioral patterns. Nonetheless, HE
shows promise as an additional layer of privacy pro-
tection that could complement our work in the future.
Deng, Zhuang, and Liang proposed a model for
a practical False Data Injection (FDI) attack against
state estimation in distribution systems (Deng et al.,
2019). The authors show that power flow in distri-
bution systems can expose information that helps at-
tackers estimate the system state. Furthermore, an
IEEE test feeder was used to simulate the FDI attack,
and the results showed that such an attack is plausible
to compromise the system. Contrary to the proposed
smart grid implementation, the addition of grid equip-
ment requires out-of-band registration, which is out-
side the scope of EGoT scheme. Further, participat-
ing actors in EGoT must be authenticated and autho-
rized by Grid Service Provider servers before process-
ing received information. Finally, detective measures
are to be installed to validate sensors readings’ trust-
worthiness as another line of defense against such an
attack.
3 ENERGY GRID OF THINGS
Our implementation of the smart grid is referred to
as an EGoT. Three main layers make up the EGoT.
The power layer concerns the distribution of energy
to households. The network layer governs how Dis-
tributed Energy Resources (DER) within the EGoT
exchange information. And, the trust layer defines
the aggregate trust within the system. When a DER is
dispatched, the states of all three layers are affected:
through the network layer, the DER informs the ag-
gregator of its availability and its energy and power
requirements; the trust layer monitors the information
exchange between actors and adjusts the trust scores
of those involved accordingly; and, within the power
layer, requested energy exchange occurs between the
Grid Operator and the DER.
The EGoT is an implementation of the smart grid
concept. It relies on the IEEE 2030.5 protocol, known
as the Smart Energy Profile 2.0 (anon., 2018a) to
communicate energy and power information, pricing-
related information, and scheduling to arrange re-
sources for large-scale aggregated dispatch of DERs.
Privacy-preserving Information Security for the Energy Grid of Things
111
DERs are grid-enabled, customer-owned generation,
storage, and load assets. These resources are located
behind customers’ meters and are not traditionally di-
rectly managed by utilities. DERs can be dispatched
to consume energy, like water heaters (Marnell et al.,
2020), or they can be configured to inject energy back
into the grid when it is needed, like inverter-based
systems (Hossain and Ali, 2013; Hoke et al., 2018).
Households that host DERs are referred to as Service-
Provisioning Customers (SPCs).
An EGoT system allows a Grid Service Provider
(GSP) to provide grid services
1
to a Grid Operator
(GO) through the coordinated dispatch of large num-
bers of DERs. GOs use grid services to maintain
bulk power system frequency and voltages to ensure
reliable energy transfer, which can be negatively im-
pacted by changes in load or variations in renewable
energy generation (Carvalho et al., 2008; Zarina et al.,
2012).
The EGoT system follows a server-client architec-
ture, wherein the server is hosted by a GSP and the
Distributed Control Modules (DCMs) are the clients.
SPCs subscribe their DERs to GSP programs, which
can be dispatched to provide grid services based on
their availability, dispatch characteristics, and topo-
logical location. The GSP server provides a means for
a GO to requisition grid services through large-scale
aggregation and coordinated dispatch of DERs.
An Energy Services Interface (ESI) serves as a
demarcation boundary between GSP and SPCs (Lee
et al., 2013). It defines a set of rules regarding the in-
formation exchange between system actors on either
side of the boundary (Slay and Bass, 2021). These
rules define a bi-directional, service-oriented, logi-
cal interface that supports secure, trustworthy infor-
mation exchange between the GSP and the SPCs’
DERs (Widergren et al., 2019). The ESI is bidirec-
tional in that devices on the SPC-side can send re-
quests to GSP servers and receive responses.
Due to the variability of DER manufacturers and
the heterogeneity of the protocols they obey, there
must be mechanisms for ensuring interoperability. In-
teroperability in an EGoT system is accomplished
through software and hardware support. DCMs
within the EGoT are tasked with expanding DER
functionalities such as the support of IEEE 2030.5
messaging, scheduling, and network communication.
Therefore, DCMs are the realization of hardware and
software support for interoperability.
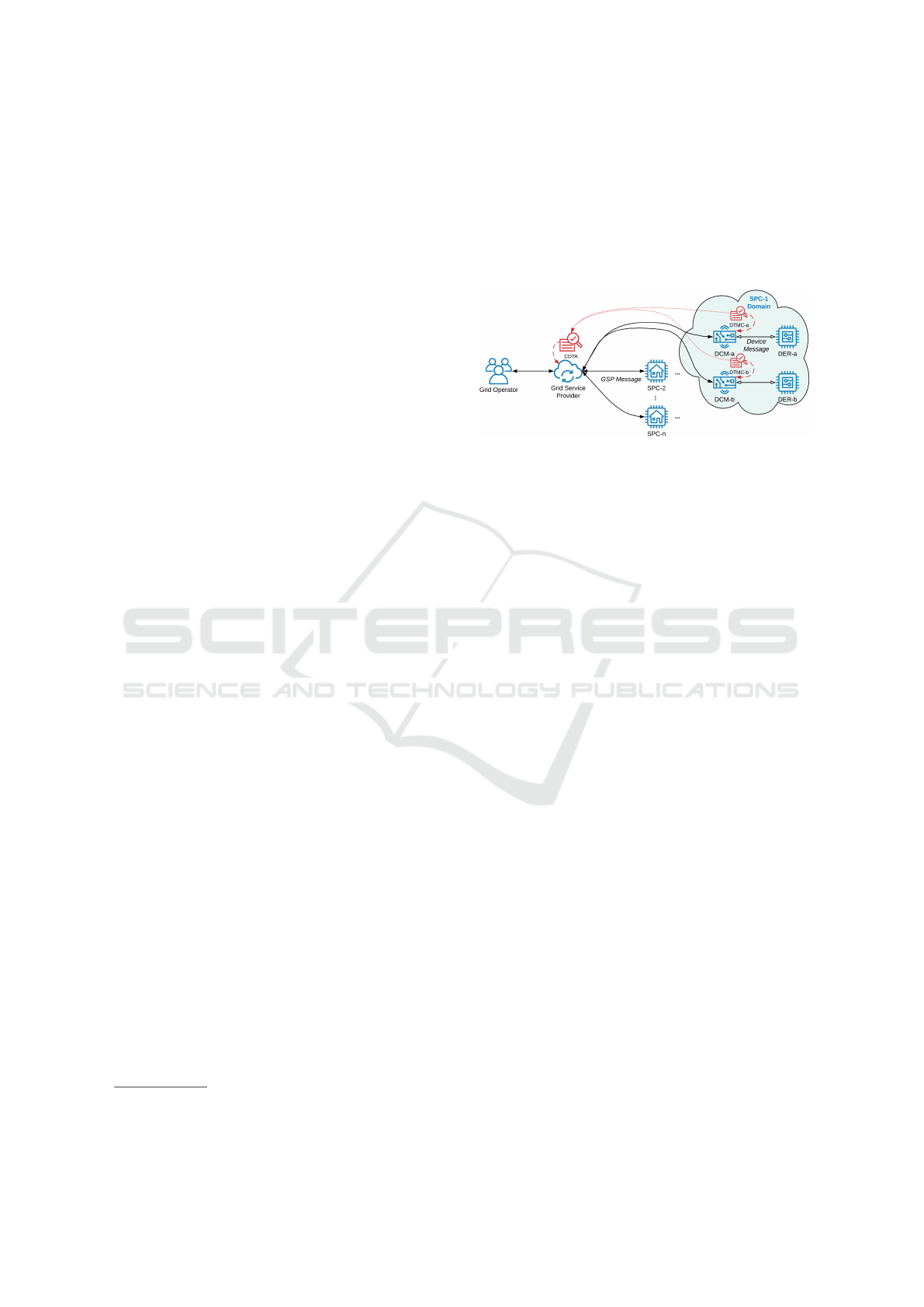
The Distributed Trust Model (DTM) System is
an augmentation to existing security for the EGoT
system. The DTM System monitors information
1
U.S. Federal Energy Regulatory Commission, “Guide
to Market Oversight Glossary”, March 15, 2016
exchange between various energy grid actors and
provides measures of trustworthiness among the ac-
tors (Fernando et al., 2021). The DTM System con-
sists of two parts: a Central Distributed Trust Ag-
gregator (CDTA), located at the GSP, and numerous
DTM clients, located along with the DCMs at each of
the SPCs, as depicted in Figure 1.
Figure 1: Shown are the communication links between the
EGoT System actors (blue), the DTM System actors (red).
The DTM System monitors information exchange between
the EGoT System actors.
The DTM system expresses trustworthiness using
a Metric Vector of Trust (MVoT). Each DTM within
the SPC maintains an MVoT for each of the actors that
communicate with its DCM host. Consider DTMC-
a on the right side of Figure 1; this DTM is paired
with a DCM, which communicates with DER-a and
the GSP. So, the DTM maintains an MVoT for each
of these actors: DCM-a, DER-a and the GSP. The
MVoT includes 17 parameters. The DTM system
evaluates the participating actors and quantifies pa-
rameters such as trust, distrust, and certainty using the
MVoT.
The DTM at the SPC is responsible for evaluat-
ing and classifying messages to and from the DCM
and to populate the MVoT parameters based on infor-
mation exchange between the DCM, its DER, and the
GSP. The DTM maintains an MVoT for each of these
actors. The CDTA is responsible for aggregating
all Distributed Trust Model Client (DTMC) MVoTs,
comparing the various MVoT parameters with thresh-
old values, and sending messages/alerts to the appro-
priate authorities. Section 7 covers the architecture of
the DTM system in detail.
4 ADVERSARY AND THREAT
MODEL
The assumed adversary categories in EGoT include
tech-savvy users and nation-backed adversaries. The
class of tech-savvy users describes a group of users
who may have malicious intentions with limited re-
sources to launch scathing attacks. Tech-savvy user
SMARTGREENS 2022 - 11th International Conference on Smart Cities and Green ICT Systems
112
skills might enable exposure of the system protocol
to identify and exploit undiscovered vulnerabilities.
The motivation for the tech-savvy users might be to
conduct further reconnaissance of a specific target or
game the system for financial incentives without re-
vealing DERs identities to the GSPs. This can be done
with falsified DER identities.
Nations-backed adversaries already have the req-
uisite expertise and resources to initiate destructive at-
tacks to the grid (Liang et al., 2017; Langner, 2011).
Unlike tech-savvy users, nation-backed adversaries
have more resources, expertise, and motives to in-
flict real damage on the grid. State-level adversaries’
are motivated to cause financial losses, blackouts, or
other political damage. The complexity of attacks
they can instigate is much higher relative to the other
two categories.
Threats for the smart grid might be malicious and
could be caused by adversaries, unfriendly entities, or
due to errors such as equipment failure and adminis-
trative errors (Li et al., 2019). The latter type of threat
is out of the scope of this analysis. The following di-
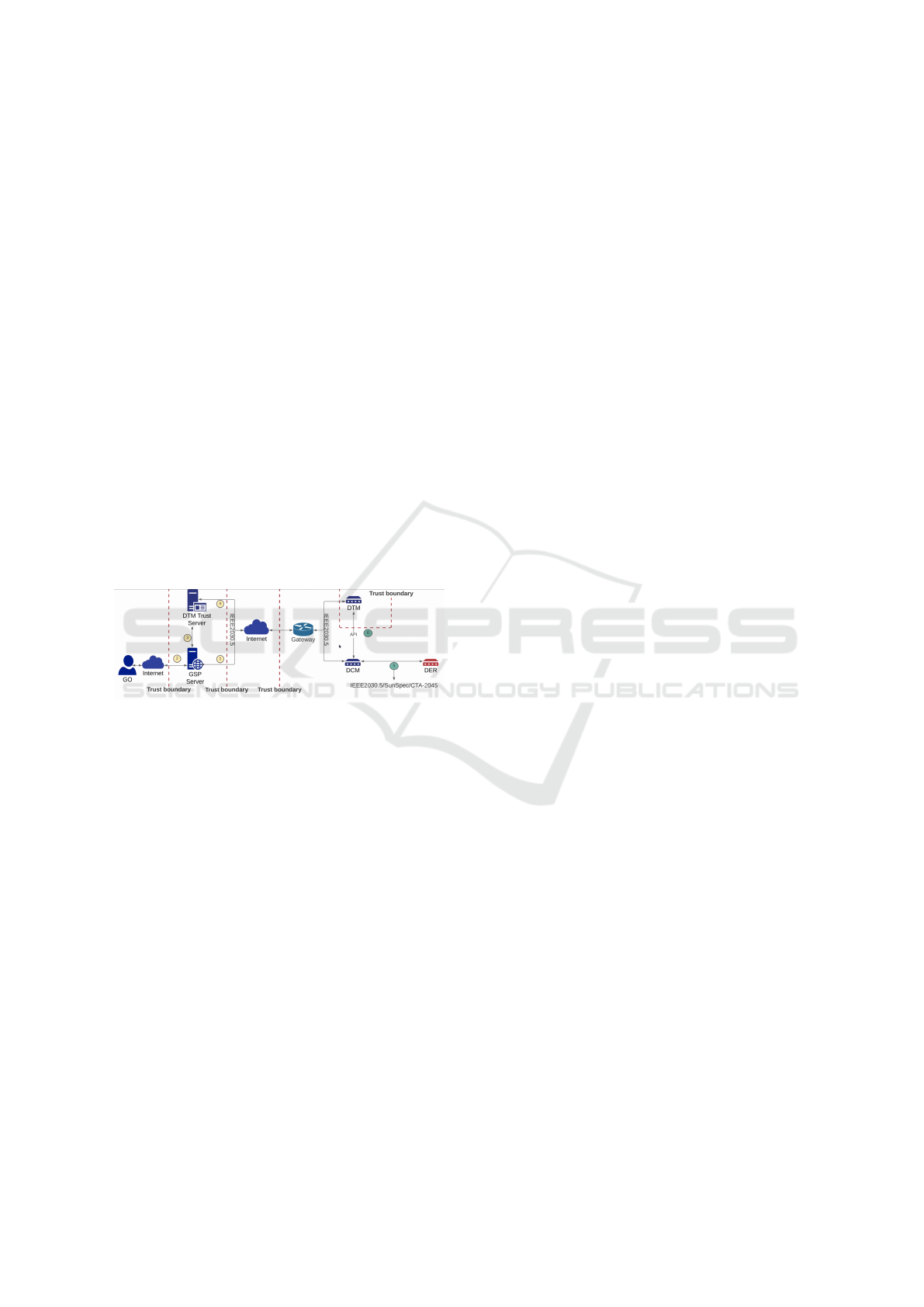
agram depicts a network model of EGoT to highlight
interactions between actors.
Figure 2: Demonstrates the communication between the
different components of EGoT. The figure shows the inter-
action between the GO (left), GSP (middle), and a single
SPC (right).
As conveyed in Figure 2, the red dotted lines in-
dicate trust boundaries with various trust levels. Fur-
ther, circled numbers indicate a data exchange point
between actors. For brevity, the data flow within the
actors’ components is out of the scope of the analysis.
Similarly, the diagram excludes data flow within the
GOs site as well.
Since the EGoT relies on the voluntary participa-
tion of DERs to fulfill grid services, DERs are con-
sidered to be assets. Furthermore, GSPs are the pri-
mary actors responsible for managing grid services
through the dispatch of DERs. Therefore, any ma-
licious attempts to target the availability of DERs or
GSPs pose a threat to the system’s stability. For ex-
ample, communication between the GSP and SPCs is
routed through the internet shown in Figure 2. A De-
nial of Service (DoS) attack targeted at either party
may prove disastrous given that adversaries are aware
of the grid state and those grid emergencies require a
timely response (Kalluri et al., 2016).
Data consistency throughout the components of
the grid is also an abstract asset. Due to a FDI at-
tack or other reasons, inconsistent data could cause
incorrect grid services to be carried out, which may
lead to an unstable electrical system (Deng et al.,
2019). Furthermore, the messages between GOs and
GSPs are routed through the internet, making them
vulnerable to cybersecurity threats (Pliatsios et al.,
2020). The corresponding point of data flow, num-
ber 2 in Figure 2, expresses a summary of grid con-
ditions sent by the GSP to the GO, and the GO sends
its needs to the GSP. Any false communication could
lead to incorrect grid services being carried out. For
instance, spoofing the GO and instructing GSPs to
continue normal operations during grid emergencies
would be catastrophic (Teixeira et al., 2014; Isozaki
et al., 2016). Likewise, updating the GOs with erro-
neous grid states may lead the GO to take misguided
decisions (Deng et al., 2017).
5 PRIVACY
The principle of least privilege declares that entities
should receive the least amount of access required to
perform their functions (Saltzer and Schroeder, 1975).
Knowledge of grid parameters and states is undoubt-
edly fundamental to GSP operation. Nonetheless,
knowledge of specific DER device information is not
crucial to GSP decisions for achieving operational ob-
jectives. For instance, knowing the energy consump-
tion of a DER is unquestionably essential to deliver
energy to the DER; however, knowing the type of the
device is a piece of supplemental, unnecessary infor-
mation to GSPs operation. Essentially, the ESI goals
are to keep DER-related information confined within
the SPC ’s personal domain and to minimize or obfus-
cate information that is needed for aggregate dispatch.
The privacy preservation goals call for ground
rules that govern actors’ interactions. As such, the
purpose of the ESI is the enactment of rules that pro-
mote privacy within the EGoT (anon., 2018b). For
instance, the ESI specifies that GSPs are to engage
with SPCs on an opt-in basis; this allows SPCs to de-
commit from a resource service at any time without
penalty. Therefore, SPCs initiates all communication
with the GSP.
The stability of the grid is partially dependent on
the GSP ’s control over resources during grid emer-
gencies (anon., 2014). The ESI rules provide accom-
modation for DER control by the GSP. However, to
conform with the ESI rules, the SPC must be the one
to instigate and grant permission for the action. Ad-
Privacy-preserving Information Security for the Energy Grid of Things
113

ditionally, the control must be temporary and not for
a non-deterministic period.
Data aggregation serves as an approach to pre-
serve privacy. A drawback of data aggregation in a
real-world setting is the need for enough parties to
participate for this measure to be effective and prac-
tical. Another helpful technique is the randomization
of energy dispatch, which would also help preserve
privacy.
Localization of private information is the primary
approach used in this research. This preserves pri-
vacy by following the logic that information that is not
shared is hard to infer. However, this does not always
work as utility companies need access to information
that is partly sensitive. For example, estimating the
energy consumption of households could be benefi-
cial for price estimation. Yet, this should not require
consumers to share their daily energy consumption
patterns. The previously mentioned example could
be expanded to an entire local area as opposed to an
individual household. This is done in the EGoT sys-
tem through data aggregation by the GSP. That is, pri-
vate data regarding the user is kept local to the SPC as
much as possible. When there is a need to share sen-
sitive information, randomization is used before con-
sumers request energy. Moreover, GSPs aggregate the
energy needs of an entire area such that utilities are
able to operate on the data in a useful manner without
infringing upon the customers’ privacy.
6 SECURING INFORMATION
EXCHANGE
Security for the EGoT is divided into two categories:
preventative measures and detective measures. The
preventive measures include encryption and authenti-
cation, as specified in IEEE 2030.5, while the DTM
System provides the detective measures. Both cate-
gories complement each other to mitigate the threats
mentioned in 4. For example, FDI behavior can be ob-
served through unexpected signatures monitored by
the DTM system via abnormal MVoT values and in-
consistencies of monitored messages. Attacks that
rely on flooding traffic are also flagged as abnormal
for violating the regular message frequency in MVoT
values. The following section expands on the detec-
tive measures provided by the DTM System.
IEEE 2030.5 protocol stack includes HTTPS with
TLS 1.2. This provides encryption and authentication
to secure messages over the internet. Certificate fin-
gerprints, which are derived from hashing the device
certificate, are required during deployment and ongo-
ing operations with GSP servers. This reduces the
system’s susceptibility to spoofing attacks. Further-
more, Access Control Lists (ACLs) are maintained by
the GSP to enforce authorization policies. Device per-
missions are verified before taking action when a re-
quest is received, which helps guard against attempts
to escalate privileges.
7 TRUST MODELING FOR
UNPREDICTABLE ATTACK
SCENARIOS
The sole responsibility of the DTM System is to mon-
itor and alert authorities of any abnormal activities. It
is an augmented security solution that enhances exist-
ing security without any interference. There are many
advantages of having a DTM due to its ability to fit
into many types of communication networks and its
customizability to address trust based on the network
location, network type, and the type of information
exchange between network nodes. Abdul-Rahman
and Halles mentioned how the existing security cov-
ers only the privacy, authenticity, and access control
methods (Abdul-Rahman and Hailes, 1997). Privacy
protects information exchange using techniques such
as cryptography. Authentication is achieved using a
digital signature to ensure authorized parties send and
receive messages. Access control ensures that only
the intended party accesses the data. In the IEEE
2030.5 protocol, those listed solutions are addressed
and accommodated. However, there is no way to en-
sure if the sender of a message is a malicious party
since there is no existing method to verify if an au-
thentic node sent the message. Hence, security needs
a fourth element: “trustworthiness.”
There are many features a DTM can have. Fer-
nando et al. presented descriptions of many trust
model characteristics and DTM design considerations
of how the DTM can be present in digital communi-
cation networks such as peer-to-peer, hierarchical, or
centralized (Fernando et al., 2021). They also pro-
vided descriptions of trust model components such as
storage solutions, trust equations, etc.
A primary goal of designing a DTM system for
the power grid is to ensure its design is fit for the dig-
ital communication network architecture. Another is
to ensure abnormalities of messages are captured cor-
rectly. Also, trust is calculated, and using historical
data or real data to calculate trust is also essential.
A dynamic DTM design can also have a trust vector
where a set of variables can independently identify a
specific abnormality as a sign of attack. For exam-
ple, a trust vector can use a variable to evaluate the
SMARTGREENS 2022 - 11th International Conference on Smart Cities and Green ICT Systems
114
changes in the frequency of communication, where
communication increase is a sign of a DoS attack.
A vital feature of the DTM System is its ability to
monitor digital communication on a network without
interference. One part of the DTM System has pre-
determined knowledge of actor behavior, the type of
messages exchanged, and the order they need to be
sent/received. With this knowledge, the DTM Sys-
tem can compare the ongoing messages exchanged
between actors and their behavior and identify abnor-
malities. The DTM System is also able to classify
messages to be indeterminate. The flexibility of the
DTM System ensures it does not make rigid classifi-
cations of indeterminate activities yet still flags them
for authority figures to evaluate.
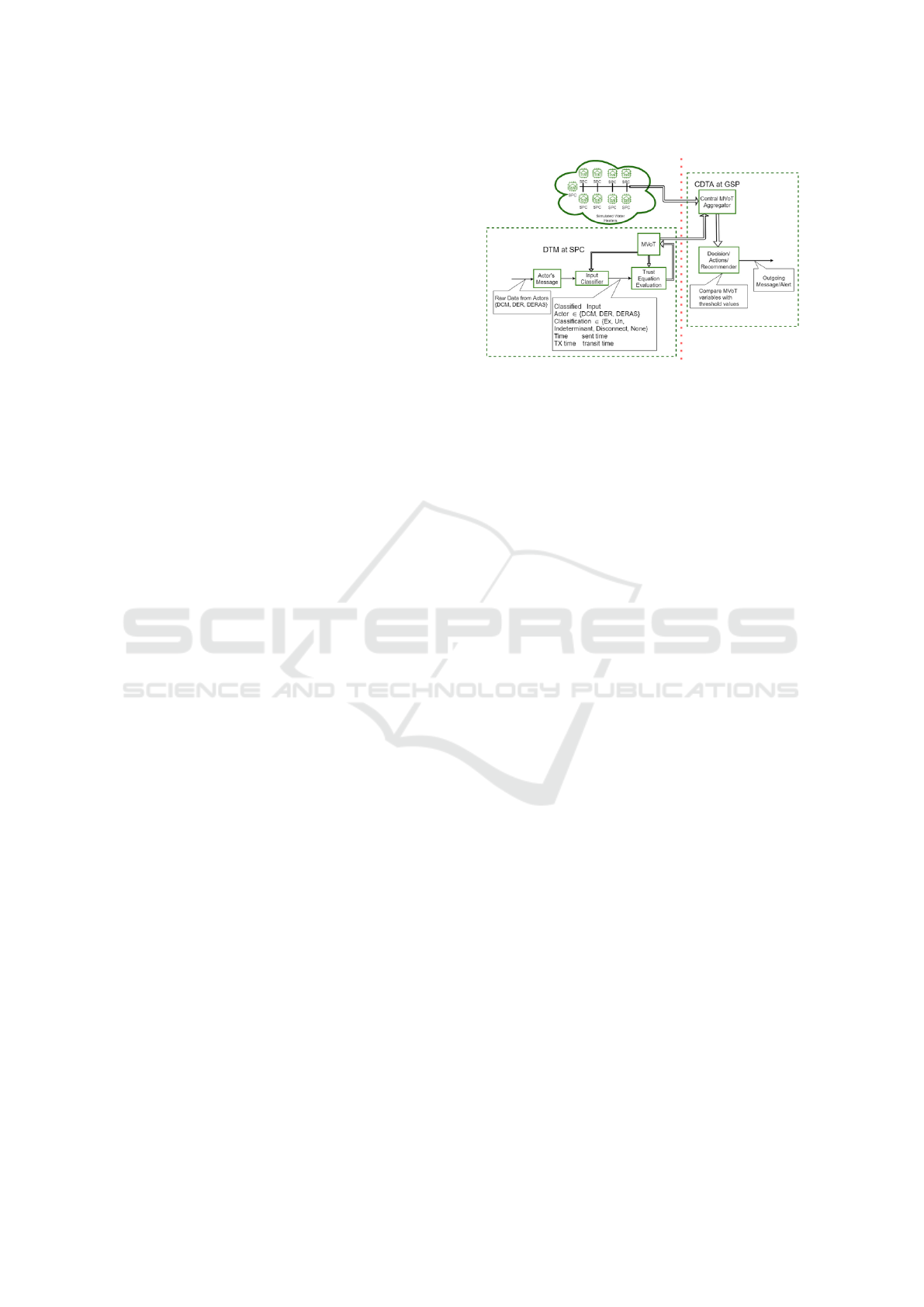
One scenario of a DTM system is shown in Fig-
ure 3 (Fernando et al., 2021). As illustrated in this
Figure, the DTM on the client side receives a raw in-
put message from an actor. The input classifier at the
DTM client processes the raw data and classifies the
message to be expected, unexpected, indeterminate,
disconnect, or none, along with the message sent time
and transit time, and information about the sender of
the message.
A message is classified as expected if the message
is in order and all the required message content is
present for a specific transaction. A message is clas-
sified as unexpected if it is out of order or contains
values out of range or message fields containing dif-
ferent data types than expected. An input message is
classified as indeterminate if the DTM is unable to
classify the message precisely. A message is classi-
fied as disconnect if a DER device does not respond
in a timely fashion. An input message is classified as
none if any of the message contents are incorrect or
missing. The classified message is processed in the
trust equation evaluation block following classifica-
tion. The trust equation evaluation block takes in the
content generated by the input classifier block and the
trust vector, MVoT.
The trust vector can contain variables such as:
• Trust Score
• Distrust Score
• Certainty
• Recent up time
where each variable of the MVoT can detect a spe-
cific abnormality, Trust Score quantifies an actor’s
overall trust, while Distrust Score quantifies the ac-
tor’s overall distrust. Certainty represents how confi-
dent the DTM is of the actor who sent the message.
The DTM MVoT can be expanded to add n number of
variables to detect additional abnormalities.
Figure 3: This figure shows the overall connection of the
DTM system. Left of the red dotted lines are components
of the DTM-Client at the SPC. Right of the red dotted lines
are components of the CDTA at the GSP.
Each variable has a corresponding equation that
the trust model uses to calculate a value for that actor
for each specific message. The DTM client updates
the new MVoT variables to the CDTA. The responsi-
bility of the CDTA is to compare against those set of
thresholds for each alert message and send out alerts
to the right authoritative figures/actors if the count ex-
ceeds the threshold value.
8 CONCLUSION
Plans to automate the electrical power grid give way
for adversaries to conduct malicious activities. Com-
munication between smart grid components is sus-
ceptible to cyber-attacks. In addition, communication
patterns could describe customers’ behavior, violat-
ing their privacy. A privacy-preserving scheme for
the smart grid was presented in this position paper.
We conducted a threat analysis to assess the secu-
rity standing of the design—finally, we discussed how
privacy is preserved through trust-augmented security
measures under the proposed strategy.
REFERENCES
Abdul-Rahman, A. and Hailes, S. (1997). A distributed
trust model. In Proc. of Workshop on New Security
Paradigms, pages 48–60, Langsdale, Cumbira, UK.
Adham, M., Obi, M., and Bass., R. (2022). A field test of
direct load control of water heaters and its implica-
tions for consumers. In IEEE PES GM. submitted for
publication.
anon. (2014). Essential Reliability Services Task Force: A
Concept Paper on Essential Reliability Services that
Characterizes Bulk Power System Reliability. Tech-
Privacy-preserving Information Security for the Energy Grid of Things
115

nical report, North American Electric Reliability Cor-
poration.
anon. (2018a). IEEE standard for smart energy profile ap-
plication protocol. IEEE Std 2030.5-2018.
anon. (2018b). Interoperability strategic vision: A GMLC
white paper. PNNL-27320. Technical report, Pacific
Northwest National Laboratory.
Bodeau, D. J., McCollum, C. D., and Fox, D. B. (2018).
Cyber threat modeling: Survey, assessment, and rep-
resentative framework. Technical report, Homeland
Security Systems Engineering & Development Insti-
tute.
Carvalho, P., Correia, P., and Ferreira, L. (2008). Dis-
tributed reactive power generation control for voltage
rise mitigation in distribution networks. IEEE Trans.
on Power Sys., 23(2):766–772.
Defend, B. and Kursawe, K. (2013). Implementation of
privacy-friendly aggregation for the smart grid. In
ACM Workshop on Smart Energy Grid Security, page
65–74, New York, NY, USA.
Deng, R., Xiao, G., Lu, R., Liang, H., and Vasilakos,
A. (2017). False data injection on state estima-
tion in power systems—attacks, impacts, and defense:
A survey. IEEE Trans. on Industrial Informatics,
13(2):411–423.
Deng, R., Zhuang, P., and Liang, H. (2019). False data
injection attacks against state estimation in power
distribution systems. IEEE Trans. on Smart Grid,
10(3):2871–2881.
Fernando, N., Acken, J., and Bass, R. (2021). Develop-
ing a distributed trust model for distributed energy re-
sources. In IEEE Conf. on Tech. for Sustainability.
Herberg, U., Mashima, D., Jetcheva, J. G., and Mirzazad-
Barijough, S. (2014). OpenADR 2.0 deployment ar-
chitectures: Options and implications. In IEEE Int.
Conf. on Smart Grid Comm., pages 782–787.
Hoke, A., Giraldez, J., Palmintier, B., Ifuku, E., Asano, M.,
Ueda, R., and Symko-Davies, M. (2018). Setting the
smart solar standard: Collaborations between Hawai-
ian Electric and the National Renewable Energy Lab-
oratory. IEEE Power & Energy Mag., 16(6):18–29.
Hossain, M. and Ali, M. (2013). Small scale energy stor-
age for power fluctuation minimization with spatially
diverged PV plants. Proc. IEEE Southeastcon.
Isozaki, Y., Yoshizawa, S., F., Y., Ishii, H., Ono, I., Onoda,
T., and Hayashi, Y. (2016). Detection of cyber attacks
against voltage control in distribution power grids
with PVs. IEEE Trans. on Smart Grid, 7(4):1824–
1835.
Kalluri, R., Mahendra, L., Kumar, R., and Prasad, G.
(2016). Simulation and impact analysis of denial-of-
service attacks on power SCADA. In National Power
Sys. Conf.
Langner, R. (2011). Stuxnet: Dissecting a cyberwarfare
weapon. IEEE Security & Privacy, 9(3):49–51.
Lee, E., Gadh, R., and Gerla, M. (2013). Energy service
interface: Accessing to customer energy resources for
smart grid interoperation. IEEE J. on Selected Areas
in Comm., 31(7):1195–1204.
Li, F., Yan, X., Xie, Y., Sang, Z., and Yuan, X. (2019). A re-
view of cyber-attack methods in cyber-physical power
system. In IEEE 8th Int. Conf. on Adv. Power Sys.
Automation & Protection, pages 1335–1339.
Liang, G., Weller, S., Zhao, J., Luo, F., and Dong, Z. (2017).
The 2015 Ukraine blackout: Implications for false
data injection attacks. IEEE Trans. on Power Sys.,
32(4):3317–3318.
Marnell, K., Eustis, C., and Bass, R. (2020). Resource study
of large-scale electric water heater aggregation. IEEE
Open Access J. of Power & Energy, 7:82–90.
Myagmar, S., Lee, A., and Yurcik, W. (2005). Threat mod-
eling as a basis for security requirements. In Proc. of
the IEEE Symp. on Requ. Eng. for Inf. Security.
Obert, J., Cordeiro, P., Johnson, J., Lum, G., Tansy, T.,
Pala, M., and Ih, R. (2019). Recommendations for
trust and encryption in DER interoperability stan-
dards. Technical report, Sandia National Laboratories,
SAND2019–1490.
Obi, M., Slay, T., and Bass, R. (2020). Distributed energy
resource aggregation using customer-owned equip-
ment: A review of literature and standards. Energy
Reports, 6:2358–2369.
Pliatsios, D., Sarigiannidis, P., Lagkas, T., and Sarigianni-
dis, A. (2020). A survey on SCADA systems: Secure
protocols, incidents, threats and tactics. IEEE Comm.
Surveys & Tutorials, 22(3):1942–1976.
Salinas, S. A. and Li, P. (2016). Privacy-preserving energy
theft detection in microgrids: A state estimation ap-
proach. IEEE Trans. on Power Sys., 31(2):883–894.
Saltzer, J. and Schroeder, M. (1975). The protection of in-
formation in computer systems. Proc. of the IEEE,
63(9):1278–1308.
Slay, T. and Bass, R. (2021). An energy service interface for
distributed energy resources. In IEEE Conf. on Tech.
for Sustainability.
Teixeira, A., D
´
an, G., Sandberg, H., Berthier, R., Bobba, R.,
and Valdes, A. (2014). Security of smart distribution
grids: Data integrity attacks on integrated volt/VAR
control and countermeasures. In American Control
Conf., pages 4372–4378.
Wei-jing, Z., He-chun, Z., Shi-ying, Y., and Tong, L.
(2019). A homomorphic encryption-based privacy
preserving data aggregation scheme for smart grid.
In 15th Int. Conf. on Comp. Intelligence & Security,
pages 315–319.
Widergren, S., Melton, R., Khandekar, A., Nordman, B.,
and Knight, M. (2019). The plug-and-play electricity
era: Interoperability to integrate anything, anywhere,
anytime. IEEE Power & Energy Mag., 17(5):47–58.
Zarina, P., Mishra, S., and Sekhar, P. (2012). Deriving in-
ertial response from a non-inertial PV system for fre-
quency regulation. IEEE Int. Conf. on Power Electr.,
Drives and Energy Sys., pages 1245–1249.
SMARTGREENS 2022 - 11th International Conference on Smart Cities and Green ICT Systems
116
