
Game Theoretic Analysis of Ransomware: A Preliminary Study
Rudra Prasad Baksi and Shambhu Upadhyaya
Department of Computer Science & Engineering, University at Buffalo, SUNY, Buffalo, NY, U.S.A.
Keywords:
Cryptography, Computer Security, Cyber-security, Game Theory, Ransomware.
Abstract:
Ransomware attacks have been frequent and wreaking havoc of the kind never seen before. This paper presents
an analysis of a basic type of ransomware. When faced with a ransomware attack, the victim needs to address
a question whether to pay or not to pay the ransom. In this regard, we develop a game-theoretic model to
analyze the attack landscape and to determine under what conditions the defender is in a position of advantage
to successfully neutralize the attack. In this preliminary analysis, we develop strategies which would help the
victim to make an informed decision. We put forward two parameters that help the defender make an informed
decision in the face of an attack. We perform a sensitivity analysis to show how the variation of the parameters
affect the outcomes of the attacker and the defender and thereby affecting the equilibrium strategies. We then
discuss how the outcome of the model can help defenders to come up with an effective defense mechanism
against similar future attacks.
1 INTRODUCTION
Ransomware are a type of malware which encrypt
critical data of a system and hold them for a ransom.
If the ransom is paid, then the data is released, else it
is made inaccessible to the victim. There are primar-
ily three types of ransomware, the locker, the crypto,
and the hybrid (Zakaria et al., 2017). The locker locks
the entire system and denies the user any access to it.
On the other hand, crypto encrypts only critical data
found on the system. It targets specific files and/or
folders. The hybrid variant of the malware possesses
capabilities of the other two types of ransomware.
More recent variants of ransomware come with addi-
tional features like campaign abort strategy or a con-
tingency plan of attack upon being discovered prior
to the launch of attack. They qualify as advanced per-
sistent threats (APT) (Baksi and Upadhyaya, 2018).
In this paper, we limit ourselves to non-APT type
ransomware so as to obtain some preliminary results
which can later be extended to cover more sophisti-
cated malware and/or APT type ransomware.
Ransomware attacks have been wreaking havoc in
the industry and/or government organizations. It is
a nuisance which not only hampers daily working of
the government and/or industry but also makes it dif-
ficult for common people to carry out their normal
activities. Ransomware attacks may cause healthcare
facilities, schools, public transport organizations, po-
lice stations, gas stations, IoT infrastructure of many
organizations, and many more institutions to suspend
their daily services (Milosevic et al., 2016). In April
2017, Erie County Medical Center (ECMC) came un-
der ransomware attack by a ransomware named Sam-
Sam. ECMC refused to pay the ransom of $30,000 in
crypto currencies and ended up spending around $10
Million in system restoration. But they were covered
by cyber insurance (Davis, 2017) (Goud, 2017). In
March 2018, the city of Atlanta came under the Sam-
Sam attack. The officials refused to pay the ransom
of $51,000 in crypto currencies and ended up spend-
ing somewhere between $2.6 Million to $17 Million
in restoration of the systems with years of police
data lost (Deere, 2018) (Newman, 2018). Colonial
Pipeline came under attack by a ransomware called
DarkSide and they paid a ransom of $4.4 Million
(75 bitcoins) (BBC, 2021). This ransomware attack
caused fuel shortages in many areas including cities
and airports. It caused loss of business and disruption
of public life and fuel prices went up. These are some
of the examples of ransomware attacks the country
has faced recently. Many attacks go unreported for
some reason or the other. But the threat is real and
so is the damage suffered from the attacks. The af-
fected agencies and institutions would like to make a
quick decision in order to restore services so that pub-
lic life can return to normalcy. In doing so, they need
to make not only a quick decision but it should also
242
Baksi, R. and Upadhyaya, S.
Game Theoretic Analysis of Ransomware: A Preliminary Study.
DOI: 10.5220/0011006600003120
In Proceedings of the 8th International Conference on Information Systems Security and Privacy (ICISSP 2022), pages 242-251
ISBN: 978-989-758-553-1; ISSN: 2184-4356
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

be strategic. Our paper dives into the area of this deci-
sion making. The research presented here would help
a victim to make an informed decision when faced
with such an attack.
We use game theory to analyze a form of ran-
somware which we call a basic ransomware in the rest
of this paper. We design a two player sequential game.
One of the players is the attacker whereas the other is
the victim and/or defender. Through the analysis we
determine optimal strategies for both the attacker and
the defender. Then we present equilibrium solutions
for different conditions. We also perform a sensitivity
analysis to examine how the decisions of both players
are being affected when the values of the decision pa-
rameters change. The major contribution of this paper
is the presenting of a parameter to quantify the impor-
tance of the value of resources under attack and the
introduction of a new parameter to better understand
the reputation of the attacker. We, thus make the im-
portance of the resources under siege and the reputa-
tion of the attacker as quantifiable metrics and a part
of the decision making process. The paper is orga-
nized as follows. In Section 2, we discuss some back-
ground information and related work in this area. In
Section 3, we present our game theory based analysis
of the basic ransomware. We then analyze the results
in Section 4 and investigate the sensitivity of the val-
ues of the parameters while making an informed de-
cision and put forward a prescriptive solution of pre-
paredness and mitigation of the ransomware attack.
Finally, we conclude the paper in Section 5 and ex-
plore the possibilities of future research in tackling
more sophisticated ransomware attacks.
2 BACKGROUND AND RELATED
WORK
Zakaria et al. (Zakaria et al., 2017) investigated the
rise in spread of ransomware, and laid down the main
areas for research on ransomware starting with the de-
tection using indicators of compromise (IoC), signa-
tures of the malware and analysis of network traffic.
Then depending upon the type of attack mounted by
the malware, the ransomware is classified into one of
the three categories, locker, crypto, and hybrid. This
is followed by two other areas of research identified
by the authors, which are recovery from the attack and
prevention from future attack. In our paper, we inves-
tigate the strategies of the attacker as well as the de-
fender, and examine “recovery from attack” and “pre-
vention of future attacks” mentioned in (Zakaria et al.,
2017).
Baksi and Upadhyaya (Baksi and Upadhyaya,
2017) used a hardware-based defense architecture
by leveraging the capabilities of the trusted platform
module (TPM) as a defense against APTs. Cekar et
al. (C¸ eker et al., 2016) used deception to counter
denial of service (DoS) attacks. They also used a
game-theoretic model based on the signaling game
with perfect Bayesian equilibrium (PBE) to investi-
gate the implications of deception to counter the at-
tacks. Deception as a potential defense tool has been
used to lure attackers to high interaction honeypots in
(Pauna, 2012) and thereby designing an effective mal-
ware detection system. The author proposed an adap-
tive honeypot system based on game-theoretic con-
cepts to entice the attackers, leading to the detection
of the rootkit malware by the defender. Baksi and
Upadhyaya (Baksi and Upadhyaya, 2020) used a Hid-
den Markov Model (HMM) based approach to iden-
tify intrusion by a ransomware. The HMM based IDS
designed by them was aimed at tackling APT type
ransomware but works well against basic ransomware
as well. Yet, the question is, once a defender has
detected an intrusion by a ransomware, what should
be the next plan-of-action. The research reported in
Baksi and Upadhyaya (Baksi and Upadhyaya, 2017),
Cekar et al. (C¸ eker et al., 2016), and Baksi and Upad-
hyaya (Baksi and Upadhyaya, 2020) are aimed at an
APT type malware threat and have deception as a de-
fense strategy. In our paper, we use basic ransomware
as the threat model, and put forward a scheme which
would help a defender make an informed decision
when faced with an attack, especially when the de-
fenders do not have a deception based defense system
against such attacks.
Game theory opens up new avenues for malware
analysis. It has been used to analyze the strategies of
the malware and the victims and study the attack land-
scape. Khouzani et al. (Khouzani et al., 2011) used
a zero-sum dynamic game-theoretic model as a solu-
tion to malware attack. They analyzed the structural
properties of saddle-point strategies, which are simple
threshold-based policies, and showed the possibility
of a robust dynamic defense system against malware
attacks. They have investigated the network defense
landscape of mobile wireless networks. The strategies
investigated on the part of the defender were reception
and patching rates. The strategy of the attacker that
was investigated was the annihilation rate of infected
nodes. Through the formulation of a dynamic game
it was proved that threshold-based policies form an
effective robust solution to malware attacks. Spyri-
dopoulos et al. (Spyridopoulos et al., 2013) investi-
gated a game-theoretic approach for the cost-benefit
analysis of malware proliferation, and modeled it on
Game Theoretic Analysis of Ransomware: A Preliminary Study
243

the lines of epidemic spread models, namely, SIR and
SIS models. They applied their models on the Code-
Red worm. The idea was to develop a cost-benefit
game-theoretic model to apply malware proliferation
strategies including “patching” of infected nodes in a
network, “removal” of infected nodes in the network,
and/or the combination of both. They used “FLIPIT”
game as the basis for the development of their model.
In our paper, we use game theory to analyze a ba-
sic form of ransomware attack through a sequential
game. We put forward two new parameters to help the
defender make an appropriate decision when faced
with an attack.
Cartwright et al. (Cartwright et al., 2019) came up
with a game-theoretic model to analyze generic ran-
somware attacks. They used the kidnapping game as
the basis for the model (Gintis, 2009) (Selten, 1977)
(Selten, 1988). The malware was modeled as the kid-
napper whereas the database of the victim was mod-
eled as the hostage. The goal of the paper is to help
the defender to make an informed decision regard-
ing the payment of the ransom, when attacked by a
ransomware. But the limitation is that the game is
applicable to ransomware attacks wherein the attack-
ers are bound by the same law of the land as the de-
fender. The authors assume that if the attackers are
apprehended, then ransom payment as well as the en-
crypted resources could be extracted from them. In
our research, we consider that the attackers could be
anywhere in the world while staging the attack. In this
scenario, it becomes really difficult to apprehend the
attackers both in terms of legal and logistical fronts.
But, this makes the ransomware more generic in na-
ture and takes care of a vast majority of the attacks
which are staged from foreign land. We use game
theory to analyze the attack and help the defender in
making an informed decision.
3 BASIC RANSOMWARE
3.1 The Threat
A malware is a software program which is designed
with malicious intent to cause harm to the victim by
the attacker. When the intent of a malware is mon-
etary gain by hijacking victim’s resources for a ran-
som, it is called a ransomware. Depending upon the
nature and level of sophistication, a ransomware can
be of an APT type or of a basic nature. An APT type
ransomware is generally created by nation state ac-
tors. They are highly sophisticated attacks and are
mounted through multiple clandestine stages (Baksi
and Upadhyaya, 2018). For such attacks, even though
monetary gain is generally the primary goal, they may
have other concealed and/or disguised agenda. On
the other hand, in a basic ransomware attack, the at-
tacker encrypts the resources under risk and charges
a ransom. If the ransom is paid, the attacker releases
the encrypted resources, else the victim loses the re-
sources forever. Such attacks generally have only one
goal, i.e., to make the resources inaccessible to the
victim until the ransom is paid. Both the APT type
ransomware and the basic ransomware can be of three
types, namely, crypto, locker and hybrid as discussed
earlier. Attack and threat models for them exist in
the literature (Kolodenker et al., 2017) (Zimba and
Chishimba, 2019). In our paper, we restrict ourselves
to the research concerning defense against basic ran-
somware.
Parameterized attack graphs have been proposed
in the literature to model attacks that exploit vulner-
abilities. The attack graphs capture attacker’s pre-
conditions, system and network vulnerabilities, at-
tacker effects, and the impact of the attack on the
network (Sheyner et al., 2002). The attacker pre-
condition component include the attacker’s capabili-
ties and the knowledge needed to stage the attacks at
an atomic level. However, attack graphs were found
to be not very useful due to scalability concerns re-
garding both model specifications and eventual threat
analysis (Chinchani et al., 2005). Even with auto-
mated tools for attack graph generation (Sheyner and
Wing, 2003), such traditional approaches are not fea-
sible in the context of ransomware where the attacker
might use social engineering tactics and launch the at-
tack in multiple stages. Game theory can effectively
model this type of attacks and capture the interactions
between the attacker and the defender. In order to fa-
cilitate the development of the game model, we intro-
duce two parameters, that are specific to ransomware
type attacks, as described in the next section.
3.2 The Game
We now present a game to depict the ransomware at-
tack on a vulnerable and under-prepared system. We
assume that the attacker exploited some form of vul-
nerability, thereby not giving the defender any time
for preparedness. Once the attack has occurred, the
defender is left with one of two choices. The first
choice is to pay ransom and hope the decryption key
is released by the attacker, while, the other option in-
volves not paying ransom. The defender can make
these choices based on certain conditions. In this sec-
tion, we analyze two conditions which would help the
defender make an informed decision on the payment
of ransom and decryption of the encrypted resources
ICISSP 2022 - 8th International Conference on Information Systems Security and Privacy
244

held for ransom. In accordance with our assumptions,
the willingness of the defender to pay ransom primar-
ily depends on two factors, the value of recovered re-
sources under siege and the reputation of the attacker.
Figure 1 gives a pictorial representation of the
game. The game begins with the attacker choosing
either of the two strategies “Attack” or “No Attack.”
If the attacker chooses the strategy “No Attack”, then
the defender has nothing to do in order to respond to
the attack. But if the attacker chooses to mount an
“Attack”, the vulnerable resources are encrypted and
then the defender is left with one of the two choices,
“Pay” or “No Pay” of the ransom. Once the defender
has made its move, the attacker has two more strate-
gies to choose from, “Release” or “No Release” of the
decryption key. If the attacker is a rational player, it
will only release the decryption key if a ransom pay-
ment is received. If it does not receive the ransom, it
will not release the decryption key. But there can be
situations where the attacker may choose to do other-
wise. That way the attacker chooses not to be rational.
The reasons for the attacker not being rational can be
many but it is outside the scope of this paper. Since
the attacker can be rational or irrational, the reputation
of the attacker can play an important role in making
an informed decision on the part of the defender when
it is under attack.
In eq. (1), parameter r
Rec
gives the ratio of re-
covered resources after payment of the ransom to the
total value of assets of the defender. Variable R is the
value of the resources under risk and/or siege. The
ransom value charged by the attacker is denoted by β.
The value of recovered resources, once the ransom is
paid, is given by R−β. The value of total assets of the
defender is denoted by R
TotalAssets
. Therefore, r
Rec
in-
dicates the importance of the recovered resources for
the defender, given the total value of assets, once the
ransom is paid and assuming the encrypted resources
have been released.
r
Rec
=
R − β
R
TotalAssets
(1)
In eq. (2) below, parameter r
Rep
establishes the
reputation of the attacker either as a rational or irra-
tional player in the game. The higher the value of
r
Rep
, the more rational is the attacker and the higher
is its trustworthiness. In an incident, if the attacker
releases the decryption key on receiving the ransom
payment, we assign 1 as the value of reputation for
that incident. If the attacker chooses not to release
the decryption key when the defender has not made
the ransom payment, we assign 1 as the value of rep-
utation for that incident. For other cases we assign
0 as the value of reputation for that particular inci-
Table 1: Attacker Notations.
Notation Description
x
1
, x
2
Attacker’s first and second strategies, respectively
x
∗
,
b
x Optimal strategy and best response, respectively
U
A
, U
∗
A
Expected Utility and Optimal Utility, respectively
Release Decision to release the encryption keys (value 0 or 1)
(1-Release) Decision to not release the encryption keys (No Release)
Table 2: Defender Notations.
Notation Description
y Defender’s Strategy
y
∗
,
b
y Optimal strategy and best response, respectively
U
D
, U
∗
D
Expected Utility and Optimal Utility, respectively
Pay Decision to pay the ransom (value 0 or 1)
(1-Pay) Decision to not pay the ransom (No Pay)
dent. Then we take a mean of the reputation values
of all the last known reported incidents to calculate
the overall reputation of the attacker. If the attack is a
first time attack, we assign a value of 0.5 to r
Rep
for
the purpose of decision making. The attackers when
they act rationally, the r
Rep
value for them for the next
game goes up. If they act irrationally, then they incur
penalty and the r
Rep
value goes down which results in
lower willingness to pay the ransom on the part of the
defender.
r
Rep
= [Mean o f all last k nown reported incidents]
(2)
Tables 1 and 2 list the notations used for describ-
ing the utility functions and strategies of the attacker
and the defender, respectively.
With all the parameters under consideration, we
look into the strategies of both the attacker and the
defender. Variable x
1
represents the strategy for the
attacker which can take up values “Attack” or “No At-
tack.” We assign the value of the strategy “Attack” as
1 when the attacker decides to attack and 0 otherwise.
Similarly for the “No Attack” strategy, the value is 1
when there is no attack, and 0 otherwise. The strategy
variable x
2
for the attacker can take up values “Re-
lease” or “No Release.” The value of “Release” is 1
when the attacker decides to release the decryption
key, and 0 otherwise. Similarly, the value of “No Re-
lease” is 1 when the attacker decides against releas-
ing the decryption key, and 0 otherwise. The decision
variable for the defender is denoted by y. It takes up
either of the two strategies as its value, viz. “Pay”
and “No Pay.” After an attack has taken place, if the
defender decides to pay the ransom then the value of
the strategy “Pay” is 1, and 0 otherwise. Similarly, if
the defender decides against payment of the ransom,
the value of “No Pay” strategy is 1, and 0 otherwise.
Now, with x
1
= Attack, y = Pay, and x
2
= Release,
we define the utility functions of the attacker and the
defender. Equations (3) and (4) show the utility func-
tions of the defender and the attacker, respectively.
Game Theoretic Analysis of Ransomware: A Preliminary Study
245
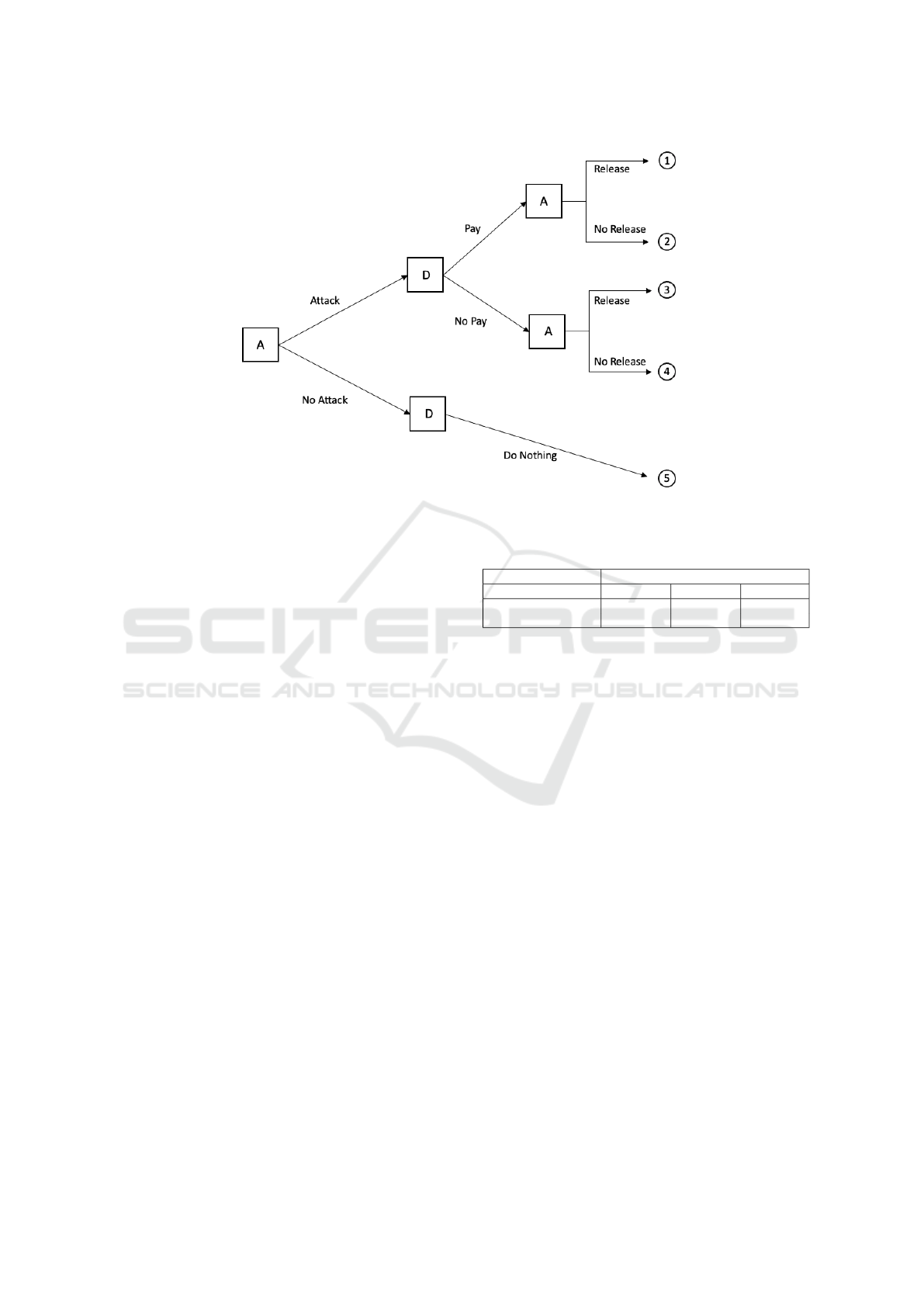
Figure 1: Basic Ransomware Attack.
U
D
≡ (x
1
) ∗ [(y) ∗{(x
2
) ∗ (R − β)
+ (1 − x
2
) ∗ (−R −β)}
+ (1 − y)∗ {(x
2
) ∗ (R) +(1 − x
2
) ∗ (−R)}]
+ (1 − x
1
) ∗ (0)
(3)
U
A
≡ (x
1
) ∗ [(y) ∗{(x
2
) ∗ (β)
+ (1 − x
2
) ∗ (β)} +(1 − y) ∗{(x
2
) ∗ (0)
+ (1 − x
2
) ∗ (0)}]
+ (1 − x
1
) ∗ (λ)
(4)
The above equations show all strategies and all
scenarios including the ones which generated a pay-
off of 0 for the player. The simplified equations are:
U
D
≡ (x
1
) ∗ [(y) ∗ {(x
2
) ∗ (R − β)+(1 − x
2
) ∗ (−R − β)}
+(1 − y) ∗ {(x
2
) ∗ (R) + (1 − x
2
) ∗ (−R)}]
(5)
U
A
≡ (x
1
) ∗ [(y) ∗{(x
2
) ∗ (β) +(1 − x
2
) ∗ (β)}]
+(1 − x
1
) ∗ (λ)
(6)
The defender makes a decision of paying the ran-
som based on the value of resource which it might get
back on payment of the ransom, and the reputation of
the malware. If the values of r
Rec
and r
Rep
are “sig-
nificantly high” then the defender should pay the ran-
som. If the values of r
Rec
and r
Rep
are “significantly
low”, then the defender should decide not to pay the
ransom. Table 3 shows the four main scenarios for
different values of r
Rec
and r
Rep
. The high and low
values of r
Rec
and r
Rep
are set by a threshold defined
by the defender. The threshold for r
Rec
is t
Rec
, value
Table 3: Recovered Resources and Reputation Value for
Defender.
Value of Affected Resources (r
Rec
)
High (H) Low (L)
Reputation (r
Rep
)
High (H) H, H H, L
Low (L) L, H L, L
of which is decided by the defender based on the total
value of assets it owns. If r
Rec
≥ t
Rec
it is said to have
a “High (H)” value. Otherwise r
Rec
is said to have a
“Low (L)” value. Similarly, If r
Rep
≥ t
Rep
it is said
to have a “High (H)” value. Otherwise r
Rep
is said to
have a “Low (L)” value. Predetermining the thresh-
old values helps the defender in attack preparedness.
This also helps in making economic decisions with
contingency plans in place.
With the strategies and utility functions in place,
we now describe how the players make strategic deci-
sions and how the game proceeds. Then we present
equilibrium solutions depending upon the various
conditions. Thereafter we conduct a sensitivity anal-
ysis so that the defender can visualize the expected
change in the decision from the change in the param-
eters. The change in the value of parameter r
Rec
sig-
nifies a change in the importance of the value of en-
crypted resources to the defender. Change in r
Rec
is
caused by a change in any of the three parameters,
viz. R, β and R
TotalAssets
. This would help defender
in attack preparedness, and as may be seen through
the sensitivity analysis, the effects of change in the
value of the parameters on the decision making pro-
cess would be vivid.
ICISSP 2022 - 8th International Conference on Information Systems Security and Privacy
246

Table 4: Pay-off table for the ransomware attack game.
Outcome Attacker Defender
1 β R − β
2 β −R − β
3 0 R
4 0 −R
5 λ 0
4 PRELIMINARY RESULTS
4.1 Decision Making Conditions
Table 4 shows the pay-off for the defender and the
attacker for each outcome. When the attacker de-
cides to attack, the maximum pay-off for the attacker
is the ransom amount it receives, as represented by
U
A
(x
1
= At tack) = β. For this ransomware, the main
goal is monetary gain from the ransom received from
the victims. If the attacker decides not to attack, then
its pay-off is the savings by avoiding the cost of attack
as represented by U
A
(x = No Attack) = λ.
For x
1
= Attack the following condition must
hold,
F
1
≡ U
A
(x = Attack) ≥ U
A
(x = No Attack) ≡ β ≥ λ
For x
1
= No Attack the following condition must
hold,
F
2
≡ U
A
(x = Attack) < U
A
(x = No Attack) ≡ β < λ
From the conditions F
1
and F
2
we get,
x
∗
1
=
(
“Attack” β≥λ
“No Attack” Otherwise
(7)
For x
2
= Release or x
2
= No Release the following
condition should hold so that it is in the best interest
of the attacker,
x
∗
2
=
(
“Release” y=“Pay”
“No Release” Otherwise
(8)
The attacker can make decisions based on the pay-
off table. The attacker starts the game by making the
first move. The first mover’s advantage goes to them.
When the attacker attacks, the defender is left with the
choice of paying or not paying the ransom. Once the
defender has made the decision, the attacker decides
to release or not release the decryption key. With this
decision, the attacker ends the game. The decision
for the defender cannot be made easily in a similar
fashion. The pay-off table does not quantify the im-
portance of the value of resources for the defender.
Moreover, the pay-off table does not guarantee or give
insight into the rationality and reputation of the at-
tacker. Consequently, the defender needs to depend
on other parameters. Considering this aspect, in this
paper we introduced two parameters to help make the
defender an informed decision, viz. r
Rec
and r
Rep
.
The defender decides the threshold for both the
parameters. If the value of the parameter is above the
threshold, then it is quantified to have a “High (H)”
value, else “Low (L)” value. Once the defender has
the values for both parameters, they need to refer to
Table 3 in order to make the decision. Therefore, the
optimal strategy is
y
∗
=
(
“Pay” r
Rec
≥ t
Rec
AND r
Rep
≥ t
Rep
“No Pay” r
Rec
< t
Rec
OR r
Rep
< t
Rep
(9)
4.2 Equilibrium Solutions
The game presents the conditions, the strategies, and
the pay-offs for each strategy. Considering these fac-
tors, Table 5 presents the best responses for both the
attacker and the defender. Given the conditions, these
best responses translate to equilibrium solutions for
the game.
Parameter λ denotes the cost of attack on the part
of the attacker. When they decide not to mount an at-
tack, i.e., the strategy is “No Attack”, the pay-off is λ.
This is the financial saving they make by avoiding the
cost of attack. If the system is harder to infiltrate, then
the value of λ is higher. For the defender it means, if
the system they build is more secure against infiltra-
tion, the value of λ increases which discourages the
attacker from mounting the attack. This information
is important because this encourages to use a stronger
encryption system to secure the database and use se-
curity best practices to lower the number of vulnera-
bilities that might exist in the system.
In the event of an attack, the defender is left with
either of the two choices, viz. “Pay” and “No Pay.”
This is where the threshold values for r
Rec
and r
Rep
comes handy in the decision making process. The de-
fender needs to decide a value for t
Rec
based on the
value of resources under siege and the total value of
resources owned by them. This helps to decide the
limit at which the defender is comfortable in paying
the ransom. For different values of the resources, ran-
som, and total assets, as r
Rec
goes below t
Rec
, the will-
ingness to pay the ransom decreases. The reason be-
ing the value of recovered resources becomes less im-
portant to the defender.
The defender shouldn’t rely on the r
Rec
parameter
alone. The reputation of the malware is also impor-
tant. If the value of r
Rec
is low, i.e., less than t
Rec
,
the resources are less important to the defender and
Game Theoretic Analysis of Ransomware: A Preliminary Study
247
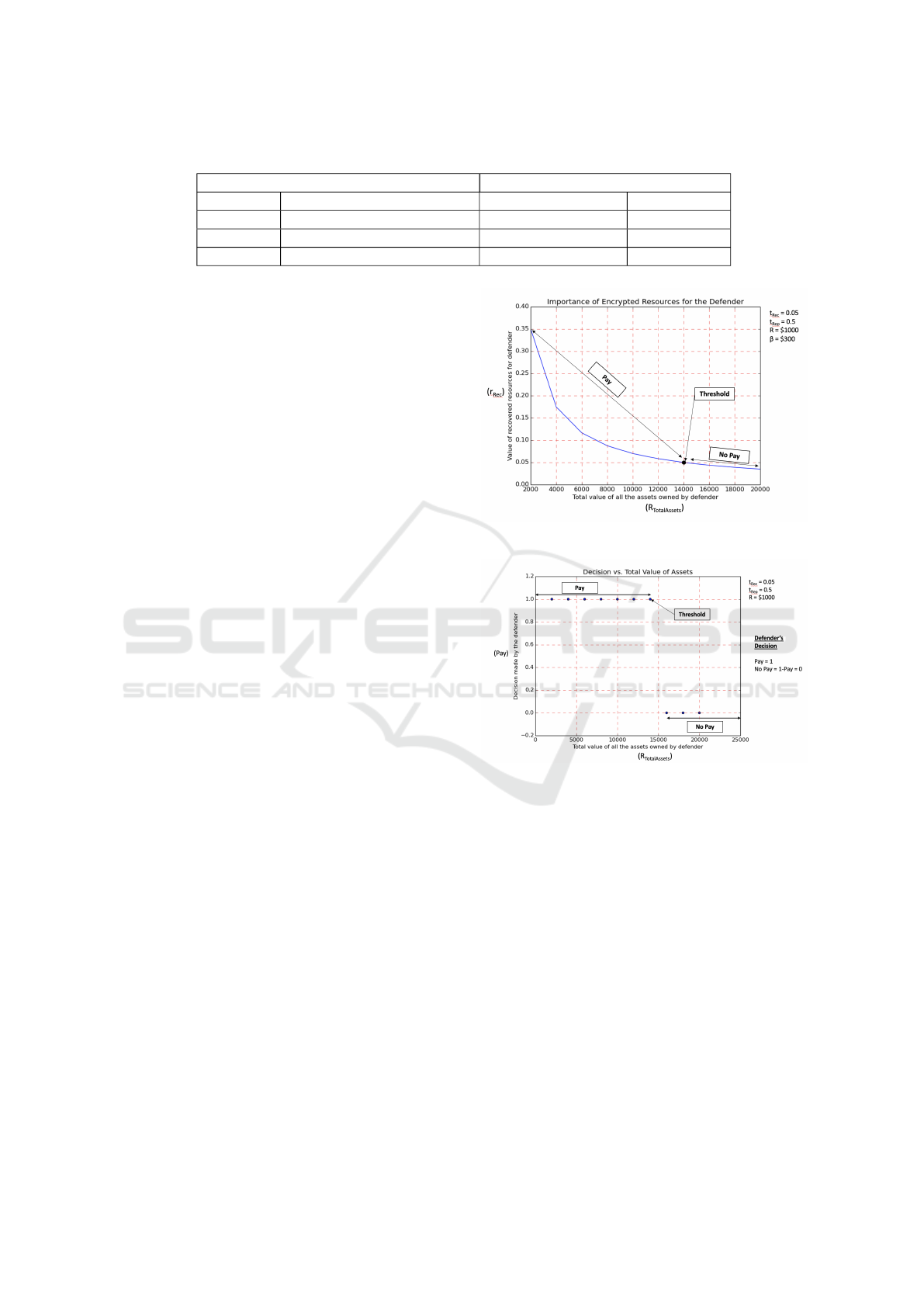
Table 5: Best Response of the Attacker and the Defender given the conditions (Equilibrium Strategies).
Conditions Strategies
Attacker Defender Attacker(
b
x
1
,
b
x
2
) Defender(
b
y)
β < λ N/A No Attack, Nothing Do Nothing
β ≥ λ r
Rep
≥ t
Rep
AND r
Rec
≥ t
Rec
Attack, Release Pay
β ≥ λ r
Rep
< t
Rep
OR r
Rec
< t
Rec
Attack, No Release No Pay
it can decide not to pay the ransom. But if it is high,
i.e., r
Rec
≥ t
Rec
, the next action the defender should
take is to check the value of r
Rep
. If r
Rep
< t
Rep
, the
reputation of the malware is low. This signifies that
if the defender pays the ransom, there is a very high
possibility that the attacker wouldn’t release the de-
cryption key either. But if r
Rep
≥ t
Rep
, the reputation
of the malware is high and it can be trusted with the
payment of the ransom. The best strategy for the de-
fender therefore would be to “Pay” the ransom when
r
Rec
≥ t
Rec
and r
Rep
≥ t
Rep
and “No Pay” otherwise.
The attacker, if feels that the pay-off is higher
when x
1
= Attack as compared to x
1
= No Attack,
then mounts the attack. For the basic ransomware
considered in this paper, with attacker being ra-
tional, it is in its best interest to release the de-
cryption key on receiving the ransom payment and
not releasing decryption key, otherwise. There-
fore, the attacker’s best strategy would be
b
x
1
,
b
x
2
=
Attack, Release on receiving the ransom payment and
b
x
1
,
b
x
2
= Attack, No Release if the ransom payment is
not made.
4.3 Sensitivity Analysis
In this section, we perform a sensitivity analysis to
determine how the values of ransom and total assets
affect the decision making of the defender.
To begin with, we assume an organization with
a value of total assets (R
TotalAssets
) of $10,000. The
value of resources (R) under siege is $1,000. The
threshold values for the recovered resources param-
eter (t
Rec
) and the reputation parameter (t
Rep
) are as-
signed 0.05 and 0.5, respectively. For the purpose of
analysis, we use the value of r
Rep
to be 0.618 (this
is obtained by randomly generating a few reputations
for past incidents and taking the mean). The ransom
value (β) was set at $300. Now in order to understand
how much the total value of all assets affect the deci-
sion making process, we vary R
TotalAssets
while keep-
ing the values of other parameters unchanged. When
the value of R
TotalAssets
is $14,000, the r
Rec
value is
at the threshold. Figure 2a shows how the value of
r
Rec
changes as we increase the value of total assets
owned by the defender. The idea is to visualize the
change in the importance of the value of resources
under siege for the defender when the value of total
(a) Importance of the resources for the defender.
(b) Decision made by the defender.
Figure 2: Sensitivity Analysis by varying R
TotalAssets
.
assets owned by them changes. The higher the value
of r
Rec
, the more important is the encrypted resources
to the defender. Figure 2b shows how the decision of
the defender changes as the importance of the value
of encrypted resources changes. The decision “Pay”
is denoted by the value 1. The decision “No Pay” or
not to pay the ransom is denoted by the value 0, i.e.,
No Pay = 1 −Pay = 0. The plot shows that when the
importance of the encrypted resources diminishes, the
willingness to pay the ransom decreases. From equa-
tion (1) and Figure 2a, it is apparent that r
Rec
is in-
versely related to R
TotalAssets
.
Now, we vary the ransom value from $100 to
$1,000. We keep the value of R at $1,000, t
Rec
0.05,
t
Rep
0.5, and r
Rep
0.618. Figure 3a shows how increas-
ing the ransom value affects the r
Rec
value. When
ICISSP 2022 - 8th International Conference on Information Systems Security and Privacy
248
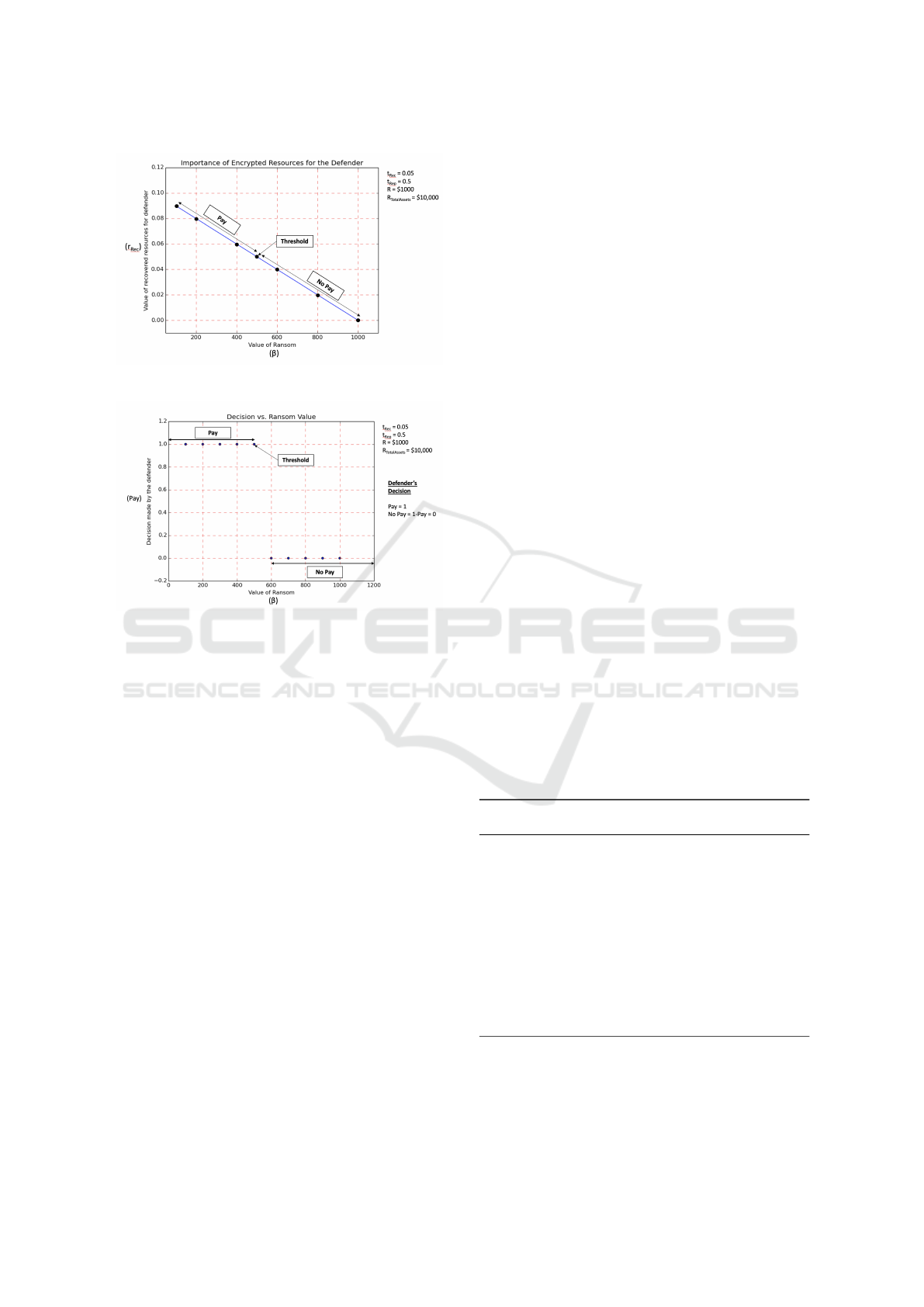
(a) Importance of the resources for the defender.
(b) Decision made by the defender.
Figure 3: Sensitivity Analysis by varying Ransom Value.
the ransom value is $500, it is the threshold value for
r
Rec
. The figure shows that as the value of ransom in-
creases, the effective value of the recovered resources
decreases. Therefore, the importance of the same to
the defender decreases and so does the willingness
to pay the ransom. Figure 3b shows how increasing
the ransom value affects the decision of the defender.
The decision “Pay” is denoted by value 1 for a ran-
som value and the decision “No Pay” is denoted by
0. With an increase in the value of the ransom, the
willingness to pay decreases owing to the fact that the
effective value of the recovered resources diminishes.
From equation (1) and Figure 3a, it is evident that the
relationship between r
Rec
and β is linear with a nega-
tive slope.
The sensitivity analysis shows how one can visu-
alize the importance of each parameter in the decision
making process. In this paper we presented an exam-
ple with synthetic data. But, this is applicable in the
real world if the defender wants to plug-in real val-
ues. This decision making process helps to make an
informed decision when faced with an attack. The
sensitivity analysis helps to visualize the effect of the
attack and helps in attack preparedness on the part of
the defender.
4.4 Prescriptive Solution
The sensitivity analysis in Section 4.3 shows how the
change in the value of ransom or change in the to-
tal value of assets owned by the defender affects the
decision made by them. The equilibrium strategies
for the attacker and the defender are shown in Table
5. The game is designed without any data and the
equilibrium strategies were obtained through back-
ward induction. Even though the sensitivity analy-
ses were performed on an example set of data, the
game would work fine for any range of data for a ba-
sic ransomware attack. Data on ransomware attacks
are hard to come by as institutions and organizations
often do not report the details fearing the leakage of
sensitive information in the public domain and/or ad-
verse effects on their reputation. Therefore, there can
be an argument here about the incomplete informa-
tion game (Harsanyi, 1994). To begin with, one can
argue that λ value is an unknown entity to the de-
fender. But through penetration testing and/or em-
ployment of ethical hackers that value can be known
with quite precision (Krishnan and Wei, 2019) (Zan-
tua et al., 2018). Another value r
Rep
may seem to
be unknown. But through media reports and brows-
ing through historical attacks by the same malware or
the same attackers, it can be calculated. If no infor-
mation is available whatsoever, then the value of r
Rep
is assumed to be 0.5. This way the game no longer
becomes an incomplete information game. With the
values under consideration and assumption, Table 5
and Algorithm 1 present a prescriptive solution to a
basic ransomware attack. The equilibrium strategies
and the algorithm present an opportunity for the de-
fender to prepare in advance and/or make an informed
decision when under attack from ransomware.
Algorithm 1: Choosing Defender’s strategy based on the
Optimized Strategy of Attacker from Table 5.
t
Rec
= # Set by Defender based on system config.
t
Rep
= # Set by Defender based on info collected
if β ≥ λ then
if r
Rec
≥ t
Rec
AND r
Rep
≥ t
Rep
then
return Pay
else
return No Pay
end if
else if β < λ AND
b
x
1
= No Attack then
return Do Nothing
end if
The basic ransomware may come with few more
features. An important feature being an early dead-
line for ransom payment. After this early deadline,
often the value of ransom demanded is doubled. If
Game Theoretic Analysis of Ransomware: A Preliminary Study
249

the defender wishes to pay the ransom, then they will
have to pay double the amount after the early dead-
line. In this scenario, the defender can simply update
the values of the parameters wherever applicable, in-
cluding the value of the ransom. Another feature in
the game can be the existence of a bargaining stage
between the attacker and the defender. After the bar-
gaining process, if the ransom value changes and/or
value of resources under siege changes, then the de-
fender can update the value of the parameters in the
game. The value of r
Rep
is calculated by observing
the ransomware attacks which have been known to the
defender and/or reported publicly as shown in the eq.
(2). If the attack is happening for the first time and/or
there exists no reports of historical occurrence of the
same, then the defender can proceed with the value
of 0.5 for r
Rep
. But through proper investigation, and
if any further clue can be found that links the ongo-
ing attack to some other attack and/or attacker, then
the defender can update eq. (2) using the values from
those attacks. Thereafter, the defender can update the
values of the parameters and tables in the game.
The defender, with the updated game can refer to
Table 5 and Algorithm 1 to make an informed deci-
sion. Having a strong security system, effective intru-
sion detection system, strong encryption system and
following proper security practices, the defender ef-
fectively increases the value of λ. This acts as a de-
terrent against probable attacks on the system.
5 CONCLUSION AND FUTURE
WORK
In this paper we used game theory to analyze the at-
tack defense scenario involving a basic ransomware
and a victim. We introduced two parameters which
would help the defender in making an informed deci-
sion when under attack. The r
Rec
parameter is the ra-
tio of the value of recovered resources after payment
of ransom to the total value of all the assets owned by
the defender. This helps the defender to quantify the
importance of the resources under siege. The higher
the value of r
Rec
, the more willing the defender is to
pay ransom. This paper presents a second parameter
for decision making so that the defender doesn’t lose
out much in the game. This parameter r
Rep
helps the
defender to guess how “trustworthy” the malware is.
The higher the reputation, the more willing is the de-
fender to pay the ransom. The algorithm presented in
this paper summarizes the process to obtain the equi-
librium solutions when the defender is under attack
from a basic ransomware. The parameters and the al-
gorithm presented in this paper would not only help
the defender in preparedness but also help in making
an informed decision when under attack.
Through a formal analysis of a basic ransomware,
our research provides a preliminary treatment of the
mitigation strategies to counter advanced threats. This
paper also provides a metric for the payment strat-
egy. The results, approach and the methodology can
be used to analyze a more sophisticated ransomware
attack, viz. the APT type ransomware. This is part of
our future work. The game theoretic analysis for such
scenarios would include elaborate games. Another
future research could be done on deciding proper
threshold values through various forms of investiga-
tions including psychological investigations, if appli-
cable. The analysis presented in this paper paves way
for future research on APT type ransomware.
ACKNOWLEDGEMENTS
This research is supported in part by the National Sci-
ence Foundation under Grant No. DGE –1754085.
Usual disclaimers apply.
REFERENCES
Baksi, R. P. and Upadhyaya, S. J. (2017). Kidemonas:
The silent guardian. Secure Knowledge Management
(SKM ‘17), Tampa, FL.
Baksi, R. P. and Upadhyaya, S. J. (2018). A comprehen-
sive model for elucidating advanced persistent threats
(APT). In Proceedings of the International Confer-
ence on Security and Management (SAM), pages 245–
251. The Steering Committee of The World Congress
in Computer Science, Computer Enigineering.
Baksi, R. P. and Upadhyaya, S. J. (2020). Decepticon: a
theoretical framework to counter advanced persistent
threats. Information Systems Frontiers, pages 1–17.
BBC (2021). Colonial pipeline boss confirms $4.4M ran-
som payment. The British Broadcasting Corporation.
Cartwright, E., Hernandez Castro, J., and Cartwright, A.
(2019). To pay or not: game theoretic models of ran-
somware. Journal of Cybersecurity, 5(1):tyz009.
C¸ eker, H., Zhuang, J., Upadhyaya, S., La, Q. D., and
Soong, B.-H. (2016). Deception-based game theoreti-
cal approach to mitigate DoS attacks. In International
conference on decision and game theory for security,
pages 18–38. Springer.
Chinchani, R., Iyer, A., Ngo, H., and Upadhyaya, S. (2005).
Towards a theory of insider threat assessment. In 2005
International Conference on Dependable Systems and
Networks (DSN’05), pages 108–117.
Davis, H. L. (2017). How ECMC got hacked by cyber extor-
tionists – and how it’s recovering. The Buffalo News.
ICISSP 2022 - 8th International Conference on Information Systems Security and Privacy
250

Deere, S. (2018). Confidential report: Atlanta’s cyber attack
could cost taxpayers $17 million. The Atlanta Journal
Constitution.
Gintis, H. (2009). Game theory evolving. Princeton univer-
sity press.
Goud, N. (2017). ECMC spends $10 million to recover
from a cyber attack! Cyber Security Insider.
Harsanyi, J. C. (1994). Games with incomplete information.
In Evolution and Progress in Democracies, pages 43–
55. Springer.
Khouzani, M., Sarkar, S., and Altman, E. (2011). A dy-
namic game solution to malware attack. In 2011 Pro-
ceedings IEEE INFOCOM, pages 2138–2146. IEEE.
Kolodenker, E., Koch, W., Stringhini, G., and Egele, M.
(2017). Paybreak: Defense against cryptographic ran-
somware. In Proceedings of the 2017 ACM on Asia
Conference on Computer and Communications Secu-
rity, pages 599–611.
Krishnan, S. and Wei, M. (2019). Scada testbed for vulner-
ability assessments, penetration testing and incident
forensics. In 2019 7th International Symposium on
Digital Forensics and Security (ISDFS), pages 1–6.
IEEE.
Milosevic, J., Sklavos, N., and Koutsikou, K. (2016). Mal-
ware in IoT software and hardware. Workshop on
Trustworthy Manufacturing and Utilization of Secure
Devices (TRUDEVICE’16), Barcelona, Spain.
Newman, L. H. (2018). Atlanta spent $2.6M to recover
from a $52,000 ransomware scare. Wired.
Pauna, A. (2012). Improved self adaptive honeypots capa-
ble of detecting rootkit malware. In 2012 9th Inter-
national Conference on Communications (COMM),
pages 281–284. IEEE.
Selten, R. (1977). A simple game model of kidnapping.
In Mathematical Economics and Game Theory, pages
139–155. Springer.
Selten, R. (1988). A simple game model of kidnapping. In
Models of strategic rationality, pages 77–93. Springer.
Sheyner, O., Haines, J., Jha, S., Lippmann, R., and Wing,
J. (2002). Automated generation and analysis of at-
tack graphs. In Proceedings 2002 IEEE Symposium
on Security and Privacy, pages 273–284.
Sheyner, O. and Wing, J. (2003). Tools for generating and
analyzing attack graphs. volume 3188, pages 344–
372.
Spyridopoulos, T., Oikonomou, G., Tryfonas, T., and Ge,
M. (2013). Game theoretic approach for cost-benefit
analysis of malware proliferation prevention. In IFIP
International Information Security Conference, pages
28–41. Springer.
Zakaria, W. Z. A., Abdollah, M. F., Mohd, O., and Ariffin,
A. F. M. (2017). The rise of ransomware. In Proceed-
ings of the 2017 International Conference on Software
and e-Business, pages 66–70.
Zantua, M. A., Popovsky, V., Endicott-Popovsky, B., and
Holt, F. B. (2018). Discovering a profile for protect
and defend: Penetration testing. In International Con-
ference on Learning and Collaboration Technologies,
pages 530–540. Springer.
Zimba, A. and Chishimba, M. (2019). Understanding the
evolution of ransomware: paradigm shifts in attack
structures. International Journal of computer network
and information security, 11(1):26.
Game Theoretic Analysis of Ransomware: A Preliminary Study
251
