
On the Influence of Image Settings in Deep Learning-based Malware
Detection
Francesco Mercaldo
1,2
, Fabio Martinelli
2
, Antonella Santone
1
and Vinod P.
3
1
University of Molise, Campobasso, Italy
2
Institute of Informatics and Telematics, National Research Council of Italy, Pisa, Italy
3
Cochin University of Science & Technology, Kerala, India
Keywords:
Malware, Deep Learning, Security, Android, Classification.
Abstract:
Considering the inadequacy of signature-based approaches for detecting malware, especially in the mobile
environment, the research community is developing methodologies for detecting malware, especially using
deep learning techniques, modeling applications like images. In state-of-the-art, several methods are proposed,
each of one using a different kind of images and a different dimension of images: currently these are not
standard settings for image preprocessing in Android malware detection. The aim of this paper is to compare
different deep learning models performances to understand the best settings in terms of kind of image and
image dimension. The idea is to trace a path in order to indicate the optimal settings for processing a dataset
for malware detection using deep learning.
1 INTRODUCTION
Mobile devices quickly attracted the interest of the at-
tackers, and it is easy to understand the reason why
if compared with PC platforms, in our smartphones
are stored more and more sensitive and private infor-
mation (Gandotra et al., 2014; Fasano et al., 2019;
Ciobanu et al., 2019; Martinelli et al., 2019). Fur-
thermore, smartphones manage the SIM card in which
there is our credit, also for this reason mobile surface
is appealing from malicious software writer’s point of
view (Xiao et al., 2019).
Mobile operating systems producers tried to rem-
edy to this rampant spread of malicious software
aimed to spy infected users. For instance, Google in
order to consent the publication of a new app on Play
Store (the official market for Android users) requires a
deep scan of the app aimed to find possible malicious
activities. Indeed, the new app must be submitted to
Bouncer (Oberheide and Mille, 2012), an automatic
application scanning system introduced in 2012 with
following distinctive features.
Bouncer performs a static analysis using the anti-
malware provided by VirusTotal (a service able to
evaluate the application simultaneously with 60 dif-
ferent anti-malware) but, considering the signature-
based detection approach offered by current anti-
malware technologies, it is possible to mark a ma-
licious sample as malware only if their signature is
present into the anti-malware repository (and conse-
quently it is not possible to detect zero-day threats.
(Mercaldo et al., 2016b), (Mercaldo et al., 2016a)).
With regard to the dynamic analysis, the app is
ran for a limited time window (5 minutes): in case the
app does not exhibit the malicious behaviour in this
period passes this test (Mercaldo and Santone, 2021).
Furthermore, usually malware is able to understand
whether it is executed on a virtual environment (in
this case it will not perform the malicious action, to
avoid the detection on sandbox (Petsas et al., 2014)).
The current defense mechanism from malicious
software is represented by anti-malware software,
currently based on the extraction of the so-called sig-
nature. Basically the anti-malware vendor release a
repository of signature, each signature is related to
a specific malicious behaviour. The signature is ob-
tained from information gathered from the samples,
and they are in form of string. This mechanism has
two principal drawbacks: first of all the signature ex-
traction is a laborious and time-consuming process
performed by security analysts, symptomatic that a
threat to be recognized must be widespread; the sec-
ond point is related to the generated signature, that
is easy to circumvent also when trivial obfuscation
techniques are applied, as demonstrated in (Rastogi
et al., 2013; Rastogi et al., 2014) (for this reason
Mercaldo, F., Martinelli, F., Santone, A. and P., V.
On the Influence of Image Settings in Deep Learning-based Malware Detection.
DOI: 10.5220/0010890600003120
In Proceedings of the 8th International Conference on Information Systems Security and Privacy (ICISSP 2022), pages 669-676
ISBN: 978-989-758-553-1; ISSN: 2184-4356
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
669

malware writers produce several variants exhibiting
the same malicious behavior by applying obfuscation
techniques, usually with automatic framework).
Considering the weaknesses of the defense
mechanisms (for example, Bouncer and the cur-
rent signature-based anti-malware technologies), re-
searchers boosted the development of methods and
tools aimed to stem this mobile malware phe-
nomenon, but currently the main issue in the adop-
tion of the proposed solutions is the presence of false
positives.
Considering this situation, there are a plethora of
techniques proposed by current state-of-the-art litera-
ture aimed to detect malware, with particular regard
to the Android operating systems.
The techniques currently employed are basically
based on static (i.e., the application is analysed with-
out the need to analysed it) and dynamic (i.e., the ap-
plication must be run to analyse the behaviour). With
the advent of the deep learning techniques, that are
mainly working of images, also in malware analysis
research field, we are witnessing an increase in the
adoption of applications modeled as images in order
to generate deep learning models.
Most of these methods extract an image directly
from the binary code of the application, some meth-
ods propose a grayscale image, others methods pro-
pose color images. Another parameter is given by the
size of the input image. In this paper we propose a
comparison between different deep learning models,
in particular we evaluate the effectiveness of models
trained with both greyscale and color images, also us-
ing different input image sizes, in order to find the
ideal settings in terms of image size and type of im-
ages for the malware detection task in the Android
environment.
Image based malware detection considers the rep-
resentation of mobile binaries as gray-scale or RGB
images, the rationale is that images related to sam-
ples belonging to the same malicious family should
appear very similar in layout and texture. Contrarily,
different images are expected from benign and mali-
cious samples. Typically these techniques are applied
starting from the malware binary, thus it is platform-
independent i.e., there is no need to reverse engineer
the application code to extract some kind of feature
from the source code.
In this paper we propose a set of experiments
aimed to show the best preprocessing settings. In a
nutshell we design a deep learning network and we in-
put this network with different image configurations.
The main aim is to indicate the best image settings for
experiments in malware detection by images in An-
droid environment.
The paper proceeds as follows: in the next section
we present the proposed deep learning network, Sec-
tion 3 shows the results of the different experiments
we performed, in Section 4 current state-of-the-art in
mobile malware detection is discussed and, finally, in
last section conclusion and future research directions
are drawn.
2 METHOD
In this section we describe the proposed method
aimed to detect Android malware from images, with
the aim to understand the best preprocessing settings.
Figure 1 shows the workflow of the proposed ap-
proach.
To convert a binary to an image we treat the se-
quence of bytes representing the binary as the bytes
of a gray-scale and RGB PNG image (Bhodia et al.,
2019; Nataraj et al., 2011). We consider a predefined
width of 256, and a variable length, depending on the
size of the binary. We developed a script to encode
any binary file into two different lossless (greyscale
and RGB) PNG.
In detail the script, developed by authors, is based
on following steps:
1. each bytes of the binary file are converted to num-
bers (0-255), which will then define a pixel color;
2. for each bytes will be a grayscale and RGB pixel
in the final PNG image.
An implementation of the script to encode a binary
file into a PNG is available at the following url: https:
//github.com/leeroybrun/Bin2PNG.
The most common pixel format is the byte image,
where this number is stored as an 8-bit integer giv-
ing a range of possible values from 0 to 255. Typi-
cally zero is taken to be black, and 255 is taken to be
white. Values inbetween make up the different shades
of gray.
In Figure 2 we show the architecture of the pro-
posed deep learning network.
The proposed network is composed by 12 differ-
ent layers, in detail we exploit a combination of fol-
lowing layers:
• Conv2D: this layer represents a 2D convolution
layer (e.g. spatial convolution over images). This
layer creates a convolution kernel that is con-
volved with the layer input with the aim to pro-
duce a tensor of outputs.
• MaxPooling2D: Max pooling operation for 2D
spatial data. Downsamples the input along its spa-
tial dimensions (height and width) by taking the
ForSE 2022 - 6th International Special Session on FORmal methods for Security Engineering
670

Figure 1: The proposed method.
Figure 2: The deep learning network.
maximum value over an input window (of size de-
fined by pool size) for each channel of the input.
• Flatten: The Flatten layer is used to ”flatten” the
input, that is, to multidimensionalize the multidi-
mensional input, often in the transition from the
convolutional layer to the fully connected layer.
Flatten does not affect the size of the batch.
• Dropout: Applies Dropout to the input. The
Dropout layer randomly sets input units to 0 with
a frequency of rate at each step during training
time, which helps prevent overfitting. Inputs not
set to 0 are scaled up by 1/(1 - rate) such that the
sum over all inputs is unchanged.
• Dense: The dense layer is a neural network layer
that is connected deeply, which means each neu-
ron in the dense layer receives input from all neu-
rons of its previous layer. The dense layer is found
to be the most commonly used layer in the mod-
els. In the background, the dense layer performs
a matrix-vector multiplication. The values used
in the matrix are actually parameters that can be
trained and updated with the help of backpropa-
gation.
The first step, the Training, starting from the data (in
this case the images obtained from the Android ex-
ecutable), an inferred function is generated. The in-
ferred function provided by the deep learning network
should be able to discriminate between different fea-
tures belonging to several classes i.e., the function
should define the boundaries between the numeric
vectors belonging to several classes. In our case the
classes are malware and trusted.
One limit about the quality of the inferred func-
tion, and therefore of the supervised machine learning
techniques, is related to the training data: it is impor-
tant that the data used to build models are free of bias,
in order to generate models able to predict the right
class for unseen instances.
With bias we are referring to applications consid-
ered in the training set but with the wrong label: this is
a situation that can be conduct to classifier with poor
performances (Parnas, 2017). To avoid these situa-
tions we carefully labelled the real-world Android ap-
plications considered in the analysis, as described in
the Experimental Evaluation section.
The second step, once generated the models is
the evaluation of their effectiveness: the Testing one,
aimed to evaluate the performances of the model con-
sidering a set of well-known state-of-the-art metrics.
The effectiveness of the models built using the in-
ferred functions is measured using well-know infor-
mation retrieval metrics. It is important to evaluate
instances not included into the training data in order
to evaluate the (real) performance of the built models,
in the next section more details about the evaluation
are provided.
On the Influence of Image Settings in Deep Learning-based Malware Detection
671

3 EXPERIMENTAL RESULTS
In this section we present the dataset we exploit to
perform experiments and the experimental analysis
results.
3.1 The Dataset
We built a dataset composed of 5560 trusted and 5560
malware Android applications.
The trusted applications were automatically col-
lected from Google Play (Google, 2015), by using
a script which queries an unofficial python API (pyt,
2014) to search and download applications from An-
droid official market. The applications retrieved were
among the most downloaded from different categories
(call & contacts, education, entertainment, GPS &
travel, internet, lifestyle, news & weather, produc-
tivity, utilities, business, communication, email &
SMS, fun & games, health & fitness, live wallpa-
pers, personalization) were downloaded from Google
Play (Google, 2015) (and then controlled by Google
Bouncer (Oberheide and Mille, 2012)) from January
2021 to June 2021, while malware applications of dif-
ferent nature and malicious intents (premium call &
SMS, selling user information, advertisement, SMS
spam, stealing user credentials, ransom) from Drebin
Dataset (Arp et al., 2014; Spreitzenbarth et al., 2013).
We analysed the trusted dataset with the VirusTo-
tal service (vir, 2015). This service run 52 different
antivirus software (e.g., Symantec, Avast, Kasperky,
McAfee, Panda, and others) on each application:
the output confirmed that the trusted applications in-
cluded in our dataset did not contain malicious pay-
load.
Malware dataset is also partitioned according to
the malware family: each family contains samples
which have in common several characteristics, like
payload installation, the kind of attack and events that
trigger malicious payload (Zhou and Jiang, 2012). Ta-
ble 1 shows the 10 malware families with the largest
number of applications in our malware dataset with
installation type, kind of attack and event activating
malicious payload.
We briefly describe the malicious payload action
for the top 10 populous families in our dataset. The
dataset includes malicious payload related to 178 ma-
licious families.
1. The samples of FakeInstaller family have the
main payload in common but have different code
implementations, and some of them also have an
extra payload. FakeInstaller malware is server-
side polymorphic, which means the server could
Table 1: Number of samples for the top 10 families with
installation details (standalone, repackaging, update), kind
of attack (trojan, botnet) and events that trigger malicious
payload.
Family Inst. Attack Activation Apps
FakeInstaller s t,b 925
DroidKungFu r t boot,batt,sys 667
Plankton s,u t,b 625
Opfake r t 613
GinMaster r t boot 339
BaseBridge r,u t boot,sms,net,batt 330
Kmin s t boot 147
Geinimi r t boot,sms 92
Adrd r t net,call 91
DroidDream r b main 81
provide different .apk files for the same URL re-
quest. There are variants of FakeInstaller that not
only send SMS messages to premium rate num-
bers, but also include a backdoor to receive com-
mands from a remote server. There is a large
number of variants for this family, and it has dis-
tributed in hundreds of websites and alternative
markets. The members of this family hide their
malicious code inside repackaged version of pop-
ular applications. During the installation process
the malware sends expensive SMS messages to
premium services owned by the malware authors.
2. DroidKungFu installs a backdoor that allows at-
tackers to access the smartphone when they want
and use it as they please. They could even turn
it into a bot. This malware encrypts two known
root exploits, exploit and rage against the cage, to
break out of the Android security container. When
it runs, it decrypts these exploits and then contacts
a remote server without the user knowing.
3. Plankton uses an available native functionality
(i.e., class loading) to forward details like IMEI
and browser history to a remote server. It is
present in a wide number of versions as harmful
adware that download unwanted advertisements
and it changes the browser homepage or add un-
wanted bookmarks to it.
4. The Opfake samples make use of an algorithm that
can change shape over time so to evade the anti-
malware. The Opfake malware demands payment
for the application content through premium text
messages. This family represents an example of
polymorphic malware in Android environment: it
is written with an algorithm that can change shape
over time so to evade any detection by signature
based antimalware.
5. GinMaster family contains a malicious service
with the ability to root devices to escalate priv-
ileges, steal confidential information and send
to a remote website, as well as install applica-
ForSE 2022 - 6th International Special Session on FORmal methods for Security Engineering
672

tions without user interaction. It is also a tro-
jan application and similarly to the DroidKungFu
family the malware starts its malicious services
as soon as it receives a BOOT COMPLETED
or USER PRESENT intent. The malware can
successfully avoid detection by mobile anti-virus
software by using polymorphic techniques to hide
malicious code, obfuscating class names for each
infected object, and randomizing package names
and self-signed certificates for applications.
6. BaseBridge malware sends information to a re-
mote server running one ore more malicious ser-
vices in background, like IMEI, IMSI and other
files to premium-rate numbers. BaseBridge mal-
ware is able to obtain the permissions to use Inter-
net and to kill the processes of antimalware appli-
cation in background.
7. Kmin malware is similar to BaseBridge, but does
not kill antimalware processes.
8. Geinimi is the first Android malware in the wild
that displays botnet-like capabilities. Once the
malware is installed, it has the potential to receive
commands from a remote server that allows the
owner of that server to control the phone. Gein-
imi makes use of a bytecode obfuscator. The mal-
ware belonging to this family is able to read, col-
lect, delete SMS, send contact informations to a
remote server, make phone call silently and also
launch a web browser to a specific URL to start
files download.
9. Adrd family is very close to Geinimi but with less
server side commands, it also compromises per-
sonal data such as IMEI and IMSI of infected de-
vice. In addiction to Geinimi, this one is able to
modify device settings.
10. DroidDream is another example of botnet, it
gained root access to device to access unique iden-
tification information. This malware could also
downloads additional malicious programs without
the user’s knowledge as well as open the phone up
to control by hackers. The name derives from the
fact that it was set up to run between the hours of
11pm and 8am when users were most likely to be
sleeping and their phones less likely to be in use.
3.2 Performances
Below we present the experimental results we ob-
tained for different dataset preprocessing.
Table 2 show the analysis results. For the eval-
uation following metrics are considered: Loss, Pre-
cision, Recall, Accuracy and Area under the curve
(AUC).
We split the dataset into three parts: Training, Val-
idation and Testing. In the training dataset there are
the sample of data used to fit the model. In the val-
idation dataset there are the sample of data used to
provide an unbiased evaluation of a model fit on the
training dataset while tuning model hyperparameters.
The evaluation becomes more biased as skill on the
validation dataset is incorporated into the model con-
figuration. In the test dataset there are the sample of
data used to provide an unbiased evaluation of a final
model fit on the training dataset.
Table 2 shows the experimental results for differ-
ent kind of images (Greyscale and RGB) and for dif-
ferent size of RGB images.
As shown from Table 2 the best performances are
obtained by exploited the Greyscale images. In fact
by exploiting this data format the precision, the recall
and the accuracy obtained is equal to 0.99. We evalu-
ated the classification performances exploiting RGB
images of different dimensions i.e., 32x32, 64x64,
128x128 and 256x256. All the RGB experiments
show a decrease in the classification performances, if
compared to the ones obtained by the Greyscale im-
ages. In fact, the accuracy is ranging from 0.9818
(with RGB images with a size of 32x32) to 0.985
(using the RGB images with a dimension equal to
256x256).
4 RELATED WORK
Current state-of-the-art literature is discussed in this
section.
AndroDialysis (Feizollah et al., 2017) proposes a
classifier that exploits the rich semantics of Intents,
i.e., a messaging object of the Android communica-
tion system describing the operations that an applica-
tion intends to perform and that can be extracted from
the code. The cited paper shows that the use of An-
droid Intents allows obtaining a better detection ratio
that the use of permissions (Canfora et al., 2013).
Methods based on static analysis do not require
infecting any device nor do they require any instru-
mented platform for collecting data during execution
in a controlled environment. On the other hand, static
methods may be circumvented by code obfuscation
techniques rather easily (Canfora et al., 2015; Cim-
itile et al., 2017; Mercaldo et al., 2016b; Martinelli
et al., 2018; Mercaldo et al., 2016c).
A classification method based on features col-
lected both statically and dynamically is proposed
in (Lindorfer et al., 2015) designed a tool able to as-
sess the maliciousness of Android applications. The
authors employ a machine learning technique with the
On the Influence of Image Settings in Deep Learning-based Malware Detection
673
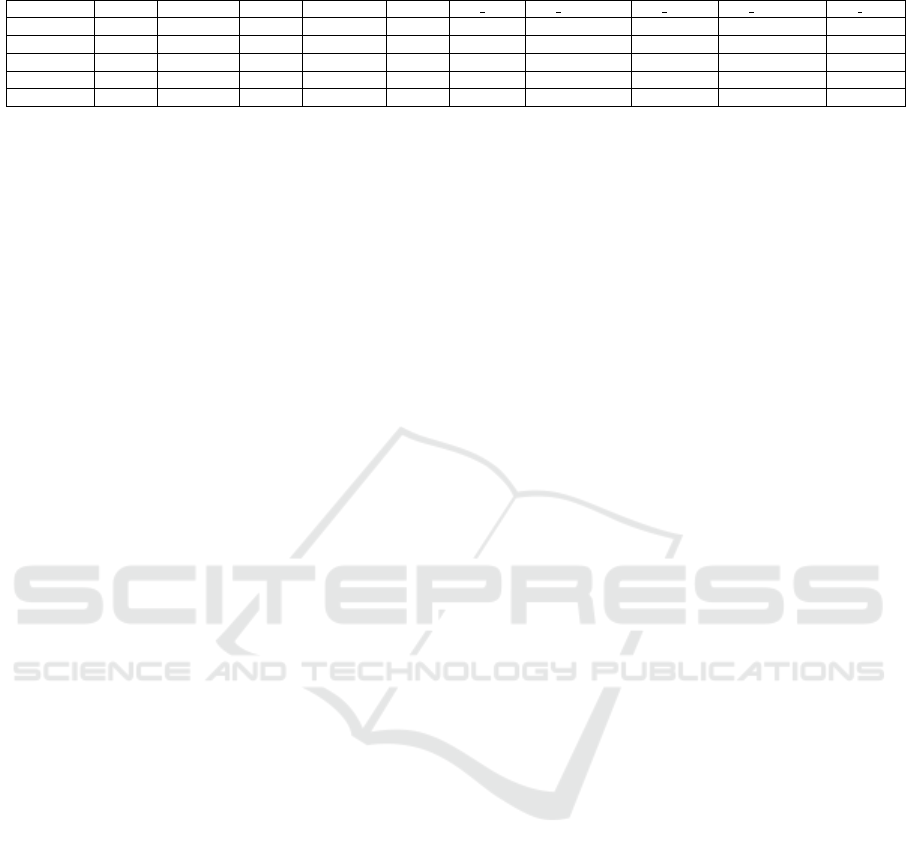
Table 2: Experimental Results.
Model Loss Precision Recall Accuracy AUC val Loss val Precision val Recall val Accuracy val AUC
Greyscale 0.0128 0.9955 0.9955 0.9955 0.9997 0.4027 0.9361 0.9361 0.9361 0.9642
Colour32 0.0428 0.9818 0.9818 0.9818 0.9985 0.5847 0.9137 0.9137 0.9137 0.9461
Colour64 0.0381 0.9854 0.9854 0.9854 0.9991 0.3953 0.9326 0.9326 0.9326 0.9654
Colour128 0.0385 0.985 0.985 0.985 0.999 0.4669 0.9396 0.9396 0.9396 0.9606
Colour256 0.0385 0.985 0.985 0.985 0.999 0.4669 0.9396 0.9396 0.9396 0.9606
aim of classifying Android applications using a fea-
ture set gathered from static and dynamic analysis of
a set of known malicious and legitimate mobile appli-
cations. The BRIDEMAID (Martinelli et al., 2017;
Faiella et al., 2017) framework advocates a similar
hybrid approach and includes a multi-level monitor-
ing of device, app and user behavior in order to de-
tect malicious behaviors at run time. The Andromaly
framework (Shabtai et al., 2012) proposes a classifi-
cation based solely on dynamic features. The frame-
work consists of a form of Host-based Malware De-
tection System able to monitor features (i.e., CPU
consumption, number of packets sent through the net-
work, number of running processes and battery level)
and events obtained from the mobile device during
execution.
A combination of static and dynamic techniques is
used in (Blasing et al., 2010) for analyzing suspicious
Android applications. The approach consists, essen-
tially, in executing the application within a sandbox
and catching all potentially dangerous events, i.e., file
open operations, connections to remote server and so
on. The method is assessed on an example applica-
tion that implements a form of Denial of Service, i.e.,
a fork bomb which uses Runtime.Exec() to start an
external binary program and creates sub-processes of
itself in an infinite loop.
Several techniques for dynamic analysis have
been proposed that consider power consumption as
the discriminating feature between benign and mali-
cious mobile applications. Authors in (Dixon et al.,
2011) hypothesized that there is a strong correla-
tion between mobile devices power consumption pat-
tern and location and studied power consumption data
from twenty smartphone users collected over a period
of three months. They tested the method on a Nokia
5500 Sport to evaluate real-world mobile malware.
Method proposed in reference (Kim et al., 2008) con-
sists in a power-aware malware-detection framework
monitoring and detecting unknown energy-depletion
threats. Their solution is composed of (1) a power
monitor which collects power samples and builds a
power consumption history from the collected sam-
ples, and (2) a data analyzer which generates a power
signature from the constructed history. To generate a
power signature, noise-filtering and data-compression
are applied, with the aim to reduce the detection over-
head. They conducted the experiment using an HP
iPAQ running a Windows Mobile OS.
Researchers in (Shabtai et al., 2010) detect suspi-
cious temporal patterns to decide whether an intrusion
is found, using patterns predefined by security ex-
perts. They use several features to perform this task,
for instance memory, CPU and power consumption,
keyboard usage and so on. Their data-set was formed
by five Android malicious applications, which were
developed by the authors.
The approach presented in (Ferrante et al., 2016)
exploits supervised and unsupervised classification in
order to identify the moment in which an application
exhibits a malware behavior. Despite the general idea
and aim are similar to those of this work, the cited pa-
per lacks the visualization component and hence can
hardly be used directly by the analyst.
Furthermore, several methods of static analysis
have been proposed for identifying the pattern of in-
teraction among the modules of an application and
obtaining indications about possible privacy leaks.
Amandroid (Wei et al., 2014) executes an ICC (i.e.,
the Inter-Component Communication) analysis by
constructing a Data Flow Graph and a Data Depen-
dence Graph. FlowDroid (Arzt et al., 2014) includes
in the ICC analysis both the code and configuration
files of the examined app, which may help in reduc-
ing both missed leaks and false positives.
5 CONCLUSION AND FUTURE
WORKS
Recently, researchers from both the academic and in-
dustrial word are proposing methods to detect mal-
ware, with particular regard to the Android environ-
ment, exploiting images and deep learning. Differ-
ent authors typically perform a preprocessing of the
dataset using different size of images and different
format (i.e., Greyscale and RGB). For this reason in
this paper we input a deep learning architecture with
images obtained from the same dataset of Android
applications. In particular we consider two different
types of images (i.e., Greyscale and RGB) and dif-
ferent sizes for the RGB images (i.e., 32x32, 64x64,
128x128 and 256x256). We compute different met-
rics to evaluate the best setting for the dataset prepro-
cessing. From the experimental results it emerges that
ForSE 2022 - 6th International Special Session on FORmal methods for Security Engineering
674

the Greyscale image is able to outperform the RGB
ones, regardless of the size used by the latter. As
future work, we are currently investigating whether
the same considering emerging from the experimen-
tal analysis we presented can be demonstrated on mal-
ware working on different operating systems i.e., iOS
and Microsoft Windows.
REFERENCES
(last visit 09 April 2015). Virustotal. https://www.virustotal.
com/.
(last visit 25 November 2014). Google play un-
official python api. https://github.com/egirault/
googleplay-api.
Arp, D., Spreitzenbarth, M., Huebner, M., Gascon, H., and
Rieck, K. (2014). Drebin: Efficient and explainable
detection of android malware in your pocket. In Pro-
ceedings of 21th Annual Network and Distributed Sys-
tem Security Symposium (NDSS).
Arzt, S., Rasthofer, S., Fritz, C., Bodden, E., Bartel, A.,
Klein, J., Le Traon, Y., Octeau, D., and McDaniel, P.
(2014). Flowdroid: Precise context, flow, field, object-
sensitive and lifecycle-aware taint analysis for android
apps. ACM SIGPLAN Notices, 49(6):259–269.
Bhodia, N., Prajapati, P., Di Troia, F., and Stamp, M.
(2019). Transfer learning for image-based malware
classification. arXiv preprint arXiv:1903.11551.
Blasing, T., Schmidt, A.-D., Batyuk, L., Camtepe, S. A.,
and Albayrak, S. (2010). An android application
sandbox system for suspicious software detection. In
Proceedings of 5th International Conference on Mali-
cious and Unwanted Software.
Canfora, G., Di Sorbo, A., Mercaldo, F., and Visag-
gio, C. A. (2015). Obfuscation techniques against
signature-based detection: a case study. In 2015
Mobile Systems Technologies Workshop (MST), pages
21–26. IEEE.
Canfora, G., Mercaldo, F., and Visaggio, C. A. (2013). A
classifier of malicious android applications. In Pro-
ceedings of the 2nd International Workshop on Secu-
rity of Mobile Applications, in conjunction with the In-
ternational Conference on Availability, Reliability and
Security.
Cimitile, A., Mercaldo, F., Nardone, V., Santone, A., and
Visaggio, C. A. (2017). Talos: no more ransomware
victims with formal methods. International Journal of
Information Security, pages 1–20.
Ciobanu, M. G., Fasano, F., Martinelli, F., Mercaldo, F.,
and Santone, A. (2019). A data life cycle modeling
proposal by means of formal methods. In Proceedings
of the 2019 ACM Asia Conference on Computer and
Communications Security, pages 670–672. ACM.
Dixon, B., Jiang, Y., Jaiantilal, A., and Mishra, S. (2011).
Location based power analysis to detect malicious
code in smartphones. In Proceedings of the 1st ACM
workshop on Security and privacy in smartphones and
mobile devices.
Faiella, M., La Marra, A., Martinelli, F., Mercaldo, F.,
Saracino, A., and Sheikhalishahi, M. (2017). A
distributed framework for collaborative and dynamic
analysis of android malware. In 2017 25th Euromi-
cro International Conference on Parallel, Distributed
and Network-Based Processing (PDP), pages 321–
328. IEEE.
Fasano, F., Martinelli, F., Mercaldo, F., and Santone, A.
(2019). Energy consumption metrics for mobile de-
vice dynamic malware detection. Procedia Computer
Science, 159:1045–1052.
Feizollah, A., Anuar, N. B., Salleh, R., Suarez-Tangil, G.,
and Furnell, S. (2017). Androdialysis: analysis of an-
droid intent effectiveness in malware detection. com-
puters & security, 65:121–134.
Ferrante, A., Medvet, E., Mercaldo, F., Milosevic, J., and
Visaggio, C. A. (2016). Spotting the malicious mo-
ment: Characterizing malware behavior using dy-
namic features. In Availability, Reliability and Secu-
rity (ARES), 2016 11th International Conference on,
pages 372–381. IEEE.
Gandotra, E., Bansal, D., and Sofat, S. (2014). Malware
analysis and classification: A survey. Journal of In-
formation Security, 5(02):56.
Google (2015). Play. https://play.google.com/store.
Kim, H., Smith, J., and Shin, K. G. (2008). Detecting
energy-greedy anomalies and mobile malware vari-
ants. In Proceedings of the 6th international confer-
ence on Mobile systems, applications, and services.
Lindorfer, M., Neugschwandtner, M., and Platzer, C.
(2015). Marvin: Efficient and comprehensive mobile
app classification through static and dynamic analy-
sis. In Computer Software and Applications Confer-
ence (COMPSAC), 2015 IEEE 39th Annual, volume 2,
pages 422–433. IEEE.
Martinelli, F., Mercaldo, F., Nardone, V., Santone, A., San-
gaiah, A. K., and Cimitile, A. (2018). Evaluating
model checking for cyber threats code obfuscation
identification. Journal of Parallel and Distributed
Computing, 119:203–218.
Martinelli, F., Mercaldo, F., and Santone, A. (2019). So-
cial network polluting contents detection through deep
learning techniques. In 2019 International Joint Con-
ference on Neural Networks (IJCNN), pages 1–10.
IEEE.
Martinelli, F., Mercaldo, F., and Saracino, A. (2017). Bride-
maid: An hybrid tool for accurate detection of android
malware. In Proceedings of the 2017 ACM on Asia
Conference on Computer and Communications Secu-
rity, pages 899–901. ACM.
Mercaldo, F., Nardone, V., and Santone, A. (2016a). Ran-
somware inside out. In Availability, Reliability and
Security (ARES), 2016 11th International Conference
on, pages 628–637. IEEE.
Mercaldo, F., Nardone, V., Santone, A., and Visaggio, C. A.
(2016b). Hey malware, i can find you! In Enabling
Technologies: Infrastructure for Collaborative Enter-
prises (WETICE), 2016 IEEE 25th International Con-
ference on, pages 261–262. IEEE.
On the Influence of Image Settings in Deep Learning-based Malware Detection
675

Mercaldo, F., Nardone, V., Santone, A., and Visaggio,
C. A. (2016c). Ransomware steals your phone. for-
mal methods rescue it. In International Conference
on Formal Techniques for Distributed Objects, Com-
ponents, and Systems, pages 212–221. Springer.
Mercaldo, F. and Santone, A. (2021). Audio signal process-
ing for android malware detection and family identi-
fication. Journal of Computer Virology and Hacking
Techniques, 17(2):139–152.
Nataraj, L., Karthikeyan, S., Jacob, G., and Manjunath, B.
(2011). Malware images: visualization and automatic
classification. In Proceedings of the 8th international
symposium on visualization for cyber security, page 4.
ACM.
Oberheide, J. and Mille, C. (2012). Dissecting the android
bouncer. In SummerCon.
Parnas, D. L. (2017). The real risks of artificial intelligence.
Communications of the ACM, 60(10):27–31.
Petsas, T., Voyatzis, G., Athanasopoulos, E., Polychronakis,
M., and Ioannidis, S. (2014). Rage against the virtual
machine: hindering dynamic analysis of android mal-
ware. In Proceedings of the Seventh European Work-
shop on System Security, page 5. ACM.
Rastogi, V., Chen, Y., and Jiang, X. (2013). Droid-
chameleon: evaluating android anti-malware against
transformation attacks. In Proceedings of the 8th
ACM SIGSAC symposium on Information, computer
and communications security, pages 329–334. ACM.
Rastogi, V., Chen, Y., and Jiang, X. (2014). Catch me if you
can: Evaluating android anti-malware against trans-
formation attacks. IEEE Transactions on Information
Forensics and Security, 9(1):99–108.
Shabtai, A., Kanonov, U., and Elovici, Y. (2010). Intrusion
detection for mobile devices using the knowledge-
based, temporal abstraction method. In Journal of Sys-
tems and Software, 83(8):1524–1537.
Shabtai, A., Kanonov, U., Elovici, Y., Glezer, C., and Weiss,
Y. (2012). “andromaly”: a behavioral malware detec-
tion framework for android devices. Journal of Intel-
ligent Information Systems, 38(1):161–190.
Spreitzenbarth, M., Echtler, F., Schreck, T., Freling, F. C.,
and Hoffmann, J. (2013). Mobilesandbox: Looking
deeper into android applications. In 28th International
ACM Symposium on Applied Computing (SAC).
Wei, F., Roy, S., Ou, X., et al. (2014). Amandroid: A
precise and general inter-component data flow anal-
ysis framework for security vetting of android apps.
In Proceedings of the 2014 ACM SIGSAC Conference
on Computer and Communications Security, pages
1329–1341. ACM.
Xiao, X., Zhang, S., Mercaldo, F., Hu, G., and Sangaiah,
A. K. (2019). Android malware detection based on
system call sequences and lstm. Multimedia Tools and
Applications, 78(4):3979–3999.
Zhou, Y. and Jiang, X. (2012). Dissecting android mal-
ware: Characterization and evolution. In Proceed-
ings of 33rd IEEE Symposium on Security and Privacy
(Oakland 2012).
ForSE 2022 - 6th International Special Session on FORmal methods for Security Engineering
676
