
Privacy Preserving Scalable Authentication Protocol with Partially
Trusted Third Party for Distributed Internet-of-Things
Hiral S. Trivedi
a
and Sankita J. Patel
Department of Computer Engineering, Sardar Vallabhbhai National Institute of Technology, Surat 395007, India
Keywords:
Authentication, Anonymity, Security, Scyther, Scalability, Partially Trusted Third Party.
Abstract:
Internet-of-Things (IoT) has triggered substantial research in real-time applications of distributed networking
infrastructure involving disparate entities with heterogeneous protocol configuration stacks. The disparate
characteristics of diverse infrastructures elevate the need for improved authentication in distributed IoT. The
distributed environment also amplifies the requirement of effective scalability to eliminate halting or restarting
of a system whenever any fresh user joins an existing communication channel. Several security protocols
using fully trusted third party (TTP) and multi-authority based approaches have been proposed to facilitate
reliable distributed networks. These approaches while providing efficient key agreement, have issues such
as key escrow and complete rights policy of fully TTP and compulsory user coordination of multi-authority
based systems. We propose a novel privacy preserving dynamic new user addition protocol with partially TTP
to address fully TTP issues, while achieving efficient scalability to avoid resource wastage in distributed IoT.
Formal security analysis is exhibited using a real-or-random model and formal verification under a scyther
security verification tool. Finally, we present a performance evaluation to elucidate the utility of our protocol.
1 INTRODUCTION
Widespread IoT adoption has engendered connection
of physical objects with cyberspace enabling ubiq-
uitous computing through integrated disparate sys-
tems for information sharing via communication net-
works (Das et al., 2020). IoT advocacy in critical
sectors while facilitating pervasive services, has also
accentuated information security risk which necessi-
tates a robust authentication requirement for secure
and anonymous access to sensitive information. Also,
the primary challenges of efficient scalability, unin-
terrupted communication channel, and cryptographic
resource wastage in developing effective distributed
systems are higher (Trivedi and Patel, 2020). Several
authors have designed fully TTP and multi-authority
based protocols, however they rarely jointly achieve
robust security and effective privacy. Conventional
mechanisms have shortcomings such as fully TTP in-
corporating complete rights policy and key escrow,
while multi-authority based approaches have compul-
sory user coordination and random authority appoint-
ment (Trivedi and Patel, 2020). As a result, none of
the standard approaches provide an amalgamated so-
lution to completely mitigate aforementioned limita-
tions. Hence, to satisfy dynamic scalability while pro-
a
https://orcid.org/0000-0002-2152-8264
viding reasonable trade-off between security and pri-
vacy, we proffer a combined key solution in our novel
generic protocol for dynamic fresh user addition with
a partially TTP approach. We also present our novelty
in achieving dynamic system scalability without inter-
rupting on-going communication channels for fresh
node addition. The TTP has partial involvement in
performing secure authentication with a fresh node
for verification process. After successful verification,
a fresh node is granted final communication secret key
to participate in the system. We outline three major
challenges in designing our protocol as follows. Ro-
bust Security: Standard Public Key Cryptography
(PKC) has higher processing cost while, Symmetric
Key Cryptography (SKC) has secret key sharing and
trust issues. However, designing light-wight robust
authentication for IoT devices remains a challenge.
As per Ecrypt II report, a 128 bit symmetric key is
equivalent to security strength of 3,248 bit asymmet-
ric key (Babbage et al., 2009). Thereby, we prereg-
ister long-term secret for effective key sharing and
execute SKC based challenge/response game utiliz-
ing one-time dynamic alias identity, hash functions
and JSON Web Token (JWT). Privacy: An ideal
authentication protocol requires efficient trade-off to
satisfy between robust security with strong identity
and effective privacy with weaker identity to preserve
anonymity (Wang, 2018). Complete Trust Policy:
812
Trivedi, H. and Patel, S.
Privacy Preserving Scalable Authentication Protocol with Partially Trusted Third Party for Distributed Internet-of-Things.
DOI: 10.5220/0010599508120818
In Proceedings of the 18th International Conference on Security and Cryptography (SECRYPT 2021), pages 812-818
ISBN: 978-989-758-524-1
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

Fully TTP systems with complete rights over crypto-
graphic resources invoke security violations and key
escrow problems for encrypting parties.
1.1 Related Work
(Das et al., 2020) proposed elliptic curve cryptogra-
phy (ECC) based RFID authentication protocol to en-
sure tag’s security and privacy. However, the scheme
has higher computational requirements. (Gope and
Sikdar, 2018) and (Saeed et al., 2018) proposed light-
weight privacy preserving authentications. Utiliz-
ing fuzzy extractor, physically unclonable function
and PKC based certificate-less schemes result in high
processing and storage costs. (Chen et al., 2019)
and (Zhang et al., 2019) introduced light-weight pri-
vacy preserving authentication incorporating PKC
and SKC algorithms. However, complete trust and
information leakage in their schemes violate secu-
rity and privacy policies. (Kang et al., 2016) pro-
posed a zero-knowledge based mutual authentication
which overlooked secure device registration. (Vi-
jayakumar et al., 2018) utilized anonymous certifi-
cates/signatures in their protocol but overlooked cal-
culating communication cost and packet delivery ra-
tio. (Chang and Le, 2015) enhanced (Turkanovi
´
c
et al., 2014) vulnerable scheme by proposing ECC
based authentication. However, their approach is
still vulnerable to side-channel, brute-force and stolen
smart-card attacks. (Lai et al., 2014) proposed privacy
preserving authentication using PKC diffie-hellman
techniques. However, location and time-based pri-
vacy are not considered. (Lin et al., 2015) highlighted
impersonation attacks that cheat central server while
preserving anonymity in (Alcaide et al., 2013) authen-
tication protocol. (Khan et al., 2011)’s enhanced pro-
tocol version of (Wang et al., 2009) enabled insider
attack due to password based weak security level.
1.2 Our Contributions
Our contributions are: First, Partial Rights Pol-
icy: To eliminate complete rights and knowledge
sharing, we adopt partially TTP located outside the
premises of Smart Homes (SH). Second, Robust Se-
curity: Auto shared key updation in correspondence
to JWT session expiry time is designed to boost se-
curity. Third, Complete Anonymity: We calculate
one-time dynamic alias-identity over encrypted iden-
tities to preserve complete anonymity of authenticated
users. Fourth, Dynamic Scalability: Partially TTP is
responsible only for verifying fresh node legitimacy
by performing secure authentication to allow partici-
pation in the existing communication channel. This
prevents frequent halting and restarting of securely
configured systems to alleviate communication and
computational costs. To the best of our knowledge,
this paper proposes the first authentication protocol
that jointly addresses partial rights policy, robust se-
curity, complete anonymity, and dynamic scalability.
Prerequisites for our indigenous protocol model are
discussed in Section 2. Section 3 presents privacy pre-
serving secure authentication protocol with partially
TTP. Security analysis and verification are hypothe-
sized in Section 4. Performance evaluation and con-
clusions are elucidated in Section 5 and Section 6.
2 PRELIMINARIES
1. Indistinguishable Encryption Under Chosen
Plain-text Attack (IND-CPA): This formally states
that two different encryptions of same plain-text
do not produce similar cipher-text for symmetric
encryption (Trivedi and Patel, 2020): Definition 1:
This illustrates single/multiple (SI
E
/ML
E
) eaves-
dropper in a random oracle. The X encryption
oracles are (E
k
1
,E
k
2
,..,E
k
n
) with encryption keys
(Ek
1
,Ek
2
,..,Ek
N
), respectively. The advantage func-
tion of SI
E
/ML
E
is Adv
IND−CPA
SI
E
,A
(Φ) = 2 Prob
SI
E
←
E
Ek
1
: (b
0
,b
1
←
R
SI
E
);θ ←
R
{0,1};γ ←
R
E
Ek
1
(bθ) : SI
E
(γ) = θ)
− 1 and Adv
IND−CPA
ML
E
,A
(Φ) =
2Prob
ML
E
← E
Ek
1
,..,E
Ek
N
;(b
0
,b
1
←
R
ML
E
);θ ←
R
{0,1};γ ←
R
E
Ek
1
(bθ),..,γ
N
←
R
E
Ek
N
(bθ) :
ML
E
(γ
1
,..,γ
N
) = θ)
− 1. The Φ is a secure
symmetric cipher whose encryption is IND-CPA.
It safeguards against (SI
E
/ML
E
) eavesdropper if
Adv
IND−CPA
SI
E
,A
(Φ),Adv
IND−CPA
ML
E
,A
(Φ)
is negligible in
the Φ for any probabilistic polynomial time.
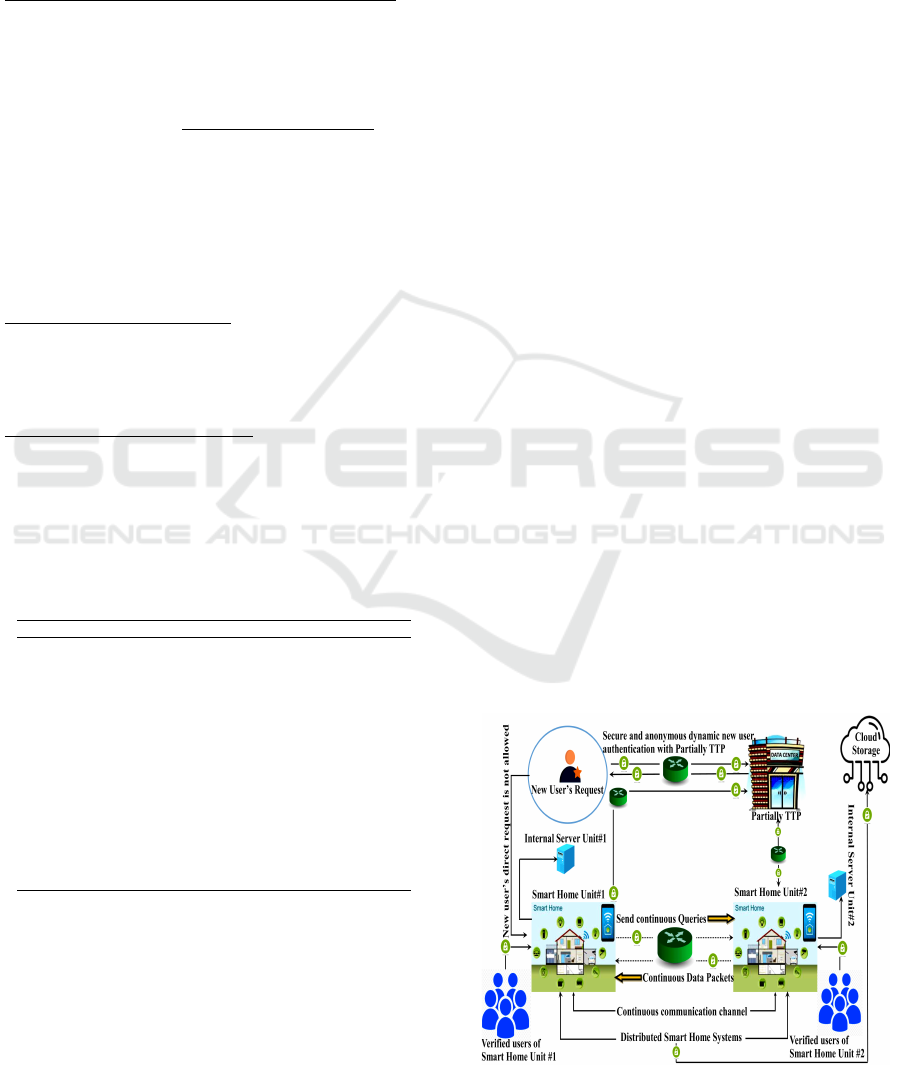
2. Architecture: Partially TTP having own private
network is located outside the premises of SH units
and a new user wishing to participate in an estab-
lished communication channel of SH units. It is as-
sumed that inter-network SH units are securely con-
nected for continuous communication. A dynamic
new user addition is executed using legitimate par-
tially TTP which holds signature long-term secret for
identity verification. In addition, we assume partially
TTP is a resource rich entity while new users have re-
source limited devices to perform authentication on a
secure channel. We restrict TTP to validate a fresh
user’ identity and maintain complete anonymous au-
thenticated user database with partial information to
constrain knowledge sharing and complete rights pol-
icy. Fig.1 illustrates our design architecture and Table
1 describes the notations.
Privacy Preserving Scalable Authentication Protocol with Partially Trusted Third Party for Distributed Internet-of-Things
813
3. Adversary Model is as follows. Confidential-
ity: An A
con f
cannot intercept, tamper or modify the
SH
k
and T
JW T
that are secure under our short term
secret r
3
and preregistered long term secret H
SD
~
id
.
T T P |= T T P
SH
k
↔ NU
~
A
id
∧ T T P |= T T P
c
C k T
0
JW T
∧
T T P
SH
k
T
0
JW T
T T P|=(T T P∪NU
~
A
id
)CkT
0
JW T
Authentication: An A
auth
cannot impersonate valid
SH
k
and a T
JW T
as r
3
is XORed using H
SD
~
id
. Semantic
security is achieved by encrypting T
JW T
with SH
k
and
XORing SH
k
with r
3
.
T T P|=T T P
SH
k
←→NU
~
A
id
SH
k
C T
0
JW T
T T P|=NU
~
A
id
SH
k
T
0
JW T
Integrity: An A
int
has negligible probability to tam-
per valid SH
k
and T
JW T
. A T
JW T
session time
will expire while brute-forcing a 128 bit SH
k
requir-
ing 5.784e+35 nanoseconds (ns) (Trivedi and Patel,
2020). Immediately after a T
JW T
expires, the TTP will
update the SH
k
and T
JW T
and discard the old values.
T T P|=(T
JW T
)∧T T PCT
0
JW T
(T )T
JW T
T T P|=#(T
0
JW T
)
Replay Attack: Data blocks are appended with
unique random numbers and time-stamps which
prevent an A
rep
to respond to old messages.
T T P|=#(T
JW T
)∧T T PC(T
JW T
)C(T
0
JW T
)
T T P|=#(T
JW T
)
Anonymity: We preserve anonymity by calculating
one-time dynamic alias identity over encrypted iden-
tities such that a new user identity remains anony-
mous for an A
anony
and TTP in the system model.
I |= θ(NU
~
A
id
,r,m) ⇒ P
j
[¬θ(i,a)]
Table 1: Notations used in our approach.
Acronym Description
r
1
/r
2
/..../r
n
Securely generated pseudo random numbers
NU
~
id
New user’s encrypted identity
NU
A
id
New user’s one-time alias identity
T T P
~
id
,T TP
A
id
TTP’s encrypted identity & alias identity
T T P
MK
TTP’s master key
NU
P
,H
NU
P
New user’s password & Hash of password
NU
SD
~
id
New user’s secret device identification
H
SD
~
id
Hash of secret device identification
H(·) One-way hash function
F
NU
Aid
Fresh anonymous identification
S
E
k
/D
k
Symmetric encryption/decryption functions
t
1
/t
2
/.../t
n
Times-stamps
SH
k
,T
JW T
Symmetric shared key & ID-based JWT
Q
1
/Q
2
/Q
3
Calculated hash values
A Adversary
⊕,k,⊥ XOR, Concatenation & Termination operations
3 PROPOSED PROTOCOL
1. Registration Phase.
• TTP Registration: T T P generates an encrypted
identity T T P
~
id
and r
1
to calculate T T P
~
MK
=
H(T T P
~
id
k r
1
) and T T P
A
id
= S
E
k
(T T P
~
id
)
T T P
~
MK
.
• New User Registration: Step 1: NU generates
NU
~
id
, NU
P
and r
2
to calculate H
NU
P
= (r
2
k NU
P
).
After that NU computes NU
~
A
id
= S
E
k
(NU
~
id
)
H
NU
P
and transmits (NU
~
A
id
,H
NU
P
) to T T P.
Step 2: After receiving (NU
~
A
id
,H
NU
P
) from NU,
TTP calculates NU
~
id
= S
D
k
(NU
~
A
id
)
H
NU
P
and veri-
fies if NU
~
id
is in the database. If yes, T T P gen-
erates F
NU
id
= H(NU
~
A
id
k H
NU
P
k H
SD
~
id
k t
1
) and
transmits (T T P
A
id
,F
NU
id
) to NU.
Step 3: Upon receiving (T T P
A
id
,F
NU
id
), NU fur-
ther retrieves F
0
NU
id
by calculating hash of legiti-
mate registered H
SD
~
id
and stores this data.
2. Secure Authentication Phase.
• Step 1: [NU → T T P (NU
A
id
,F
0
NU
id
)]: Upon ob-
taining (T T P
A
id
,F
NU
id
), NU retrieves H
SD
~
id
=
H(NU
SD
~
id
). Given the parameters (NU
~
id
,F
NU
id
),
NU calculates F
0
NU
id
= H(NU
~
A
id
k H
NU
P
k H
SD
~
id
k
t
2
) and transmits (NU
A
id
,F
0
NU
id
) to T T P.
• Step 2: T T P → NU (r
0
3
,SH
0
k
,T
0
JW T
,Q
1
): Upon re-
ceiving (NU
~
id
,F
0
NU
id
), T T P verifies F
0
NU
id
?
= F
NU
id
.
If F
0
NU
id
= F
NU
id
, NU
0
s login request is accepted,
else rejected. Assuming that NU
0
s request is ac-
cepted, T T P will generate a SH
k
, r
3
and T
JW T
.
A challenge/response game is enabled through
four stages:1) T T P computes SH
0
k
= (SH
k
⊕ r
3
).
2) T T P encrypts T
0
JW T
= S
E
k
(T
JW T
)
SH
k
. 3) r
3
is XORed with H(NU
SD
~
id
) such that r
0
3
= (r
3
⊕
H
SD
~
id
). 4) T T P computes Q
1
= H(1 k r
3
k SH
k
k
T
JW T
k t
3
) and transmits (r
0
3
,SH
0
k
,T
0
JW T
,Q
1
) to
NU.
• Step 3: [NU → T T P (NU
~
A
id
,Q
2
)]: When obtain-
ing (r
0
3
,SH
0
k
,T
0
JW T
,Q
1
), NU executes: 1) NU re-
trieves r
3
= (r
0
3
⊕ H
SD
~
id
). 2) NU retrieves SH
k
=
Figure 1: Our proposed generic distributed IoT architecture.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
814

(SH
0
k
⊕r
3
). 3) NU retrieves T
JW T
= S
D
k
(T
0
JW T
)
SH
k
.
4) NU calculates Q
2
= H(2 k r
3
k SH
k
k T
JW T
k t
4
)
and transmits (NU
~
A
id
,Q
2
) to T T P.
• Step 4: [T T P → NU (T T P
A
id
,Q
3
)]: Upon receiv-
ing NU
0
s response, T T P verifies Q
1
?
= Q
2
. If
Q
1
= Q
2
is true, all the values (r
0
3
= r
3
,SH
0
k
=
SH
k
,T
0
JW T
= T
JW T
) have been correctly retrieved.
If Q
1
6= Q
2
, then it will directly discard the values
and ⊥ the protocol. Assuming the response has
been matched and T T P has verified the NU, T T P
will transmit Q
3
= H(3 k r
3
k SH
k
k T
JW T
k t
5
) and
T T P
A
id
to complete the protocol.
4 SECURITY ANALYSIS
We prove theoretical analysis and semantic security
as per (Chang and Le, 2015). We also demonstrate
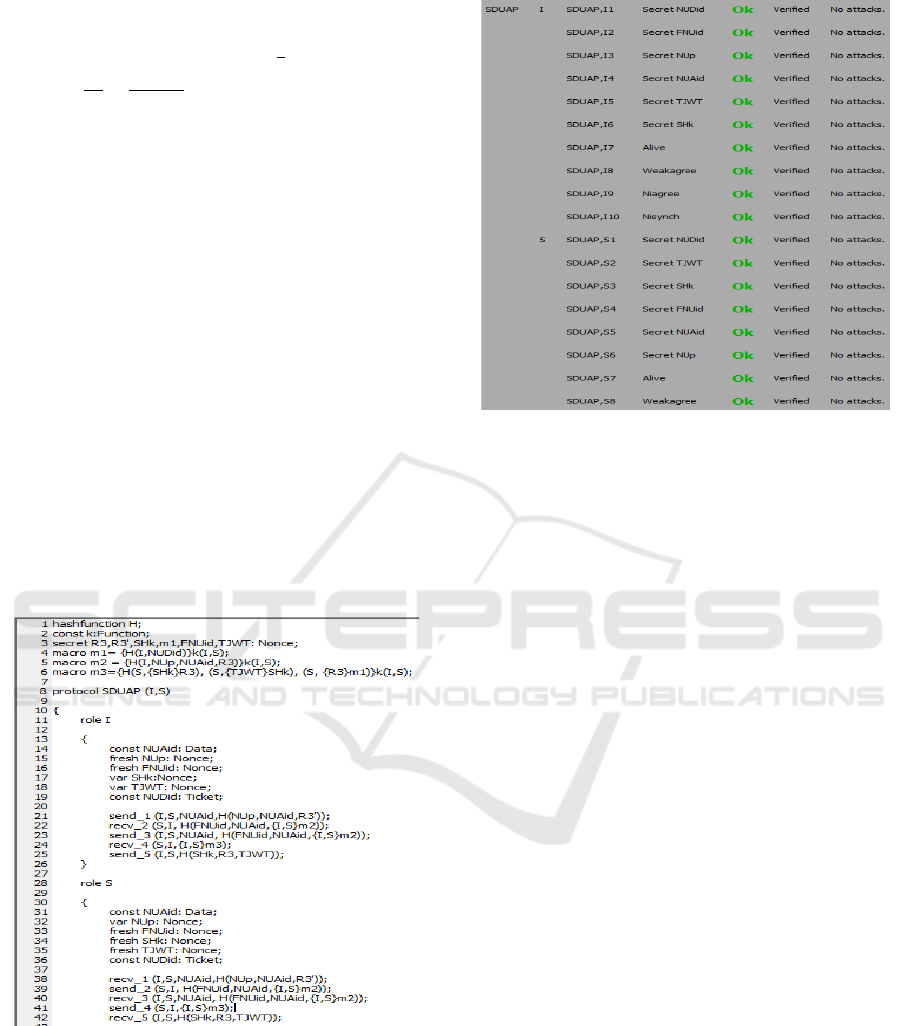
scyther results in Fig. 2 and Fig. 3 experimented on
100 runs with 10 patterns per claim which prove that
our protocol is secure against typical security attacks.
ROR Model: The components of ROR model are as
follows: i) Participants - u, p of main entities NU
and T T P identified as Π
u
NU
, Π
p
T T P
. ii) Partnering -
Π
p
T T P
of T T P is partnering with Π
u
NU
and vice-versa.
The calculated one-time alias identity NU
A
id
is unique
and anonymous for each session in which Π
u
NU
is a
participant. iii) Freshness - Assumes that for a given
reveal query Π
p
T T P
, if SH
k
is not leaked by an A, than
Π
u
NU
, Π
p
T T P
is fresh. iv) Adversary - A can access all
communicated messages to perform malicious activ-
ities. The queries executed by an A are: 1) Execute:
Π
u
, Π
p
: It is modeled when an A eavesdrops on com-
municated messages between NU and T T P. 2) Send:
Π
u
,msg: It is an active attack, where an A transmits
a msg to an instance Π
u
and accordingly gets a revert
from Π
u
. 3) Reveal: Π
u
: It reveals current SH
k
be-
tween Π
u
and partner Π
p
to an A . 4) Corrupt Π
u
NU
:
It enables an A for obtaining all the secrets such as
NU
P
,r
3
,H
SD
~
id
to leak current SH
k
. 5) Test Π
u
: It is
a request by an A to Π
u
to guess a valid SH
k
and Π
u
replies within the probabilistic polynomial time such
that it returns SH
k
if c
0
= 1, or some other random
value if c
0
= 0. 6) Hash H(·): A one-way hash func-
tion denoted as H is a random oracle accessible to
an A and all entities. 7) Semantic security SH
k
: It
is modeled for an A to guess valid SH
k
by executing
test queries from random flipping. An A wins only if
value of c
0
= c. Event S
i
is modeled if an A wins the
game. The semantic security of proposed protocol is
defined as: Adv
A
PP
= |2Prob[S] − 1|. The protocol is
secure if, Adv
A
PP
≤ ε for small ε > 0.
Theorem 1. An A running in polynomial time t
against our secure authentication protocol in a de-
fined random oracle model. Let D, q
h
,q
send
,H,|D|
and
Adv
IND−CPA
SI
E
,A
(Φ), Adv
IND−CPA
ML
E
,A
(Φ)
be uni-
formly distributed password dictionary with num-
ber of hash queries q
h
, number of send queries
q
send
, H range of hash function and |D| the size
of D as the advantage of an A breaking IND-
CPA secure Φ. We state that
Adv
IND−CPA
A
(Φ) =
Adv
IND−CPA
SI
E
,A
(Φ),Adv
IND−CPA
ML
E
,A
(Φ)
. Assuming no en-
tity is compromised to have Adv
A
PP
≤
q
2
h
|H|
+
2qsend
|D|
.
Proof: To construct G
i
: [0,4], where i : [0, 4] is the se-
quence of games demonstrating the probability of an
A’s advantage to break the security and S
i
is a seman-
tic security event of our protocol. G
0
: Illustrates an
active attack by an A choosing bit c of a coin at the
beginning in random oracle model. We define this as:
Adv
A
PP
= 2Prob
S
i
− 1.
G
1
: Illustrates an eavesdropping attack using exe-
cute query (Π
u
, Π
p
) to retrieve SH
k
. The compu-
tation of SH
k
is T T P : SH
0
k
= (SH
k
⊕ r
3
), T T P :
T
0
JW T
= S
E
k
(T
JW T
)
SH
k
, T T P : r
0
3
= (r
3
⊕ H
SD
~
id
) and
T T P : Q
1
= H(1 k r
3
k SH
k
k T
JW T
k t
3
). This requires
an A to calculate r
3
, which is secured under non-
transmitted H
SD
~
id
, to retrieve SH
k
and T
JW T
. With-
out possessing both the secrets, an A has negligible
probability of wining this game. We define this as:
Adv
A
PP
Prob(S
0
)
= Adv
A
PP
Prob(S
1
)
.
G
2
: Illustrates modification in game G
1
with q
send
and H functions. An A forwards a fabricated message
to convince the honest party to accept. This causes an
A to check collisions in the hash digest by executing
q
h
. Our protocol incorporates collision-resistant H(·)
function to safeguard H
SD
~
id
= H(NU
SD
~
id
), T T P : r
0
3
=
(r
3
⊕H
SD
~
id
), and T T P : Q
1
= H(1 k r
3
k SH
k
k T
JW T
k
t
3
). All secrets, identities and messages are appended
with random numbers and timestamps to mitigate col-
lisions using q
send
and q
h
queries. The result of birth-
day paradox is: Adv
A
PP
|Prob[S
1
] − Prob[S
2
]| ≤
q
2
h
(2|H|)
.
G
3
: Illustrates an A using dictionary attacks to eas-
ily guess low-entropy passwords NU
P
. To prevent
such illegal access, our authentication system restricts
multiple incorrect password attempts which is much
smaller than |D| in a random oracle. We define this
as: Adv
A
PP
= |Prob[S
2
] − Prob[S
3
]| ≤
q
send
(2
m
|D|)
.
G
4
: An A intercepts NU smart-device after success-
fully gaining access to NU
P
. An A cannot derive SH
k
and T
JW T
even after gaining access to NU smart de-
vice due to non-transmission of long-term secret in
the communication channel. The SH
k
and T
JW T
are
secured under symmetric encryption cipher Φ. We
state that Φ is IND-CPA secure as per Definition 1.
We define this as: Adv
A
PP
= |Prob[S
3
] − Prob[S
4
]| ≤
Privacy Preserving Scalable Authentication Protocol with Partially Trusted Third Party for Distributed Internet-of-Things
815
Adv
IND−CPA
A
(Φ)(l). Finally after computing G
i
;[0,4],
an A guesses bit c of a coin to win this game after
launching a test query Prob[s
4
] =
1
2
. Thus, we obtain
Adv
A
PP
≤
q
2
h
|H|
+
q
2
send
2
m−1
.|D|
+ 2Adv
IND−CPA
A
(Φ)(l).
Theorem 2. Our proposed protocol preserves confi-
dentiality, authenticity and anonymity.
Proof: A new user’s NU
SD
~
id
is preregistered and in-
dependently computed on both the sensing modules
such that, H
SD
~
id
= H(NU
SD
~
id
). Also, our robust secu-
rity design will enable TTP to auto-update SH
k
while
brute forcing 128 bit symmetric key which takes
5.784e+35 ns. Non-transmission of long-term secret
H
SD
~
id
prevents an A to retrieve data blocks such as
T T P : SH
0
k
= (SH
k
⊕r
3
), T T P : T
0
JW T
= S
E
k
(T
JW T
)
SH
k
,
T T P : r
0
3
= (r
3
⊕ H
SD
~
id
). This will increase compu-
tational hardness for an A to prove Q
1
= H(1 k r
3
k
SH
k
k T
JW T
k t
3
) and Q
2
= H(2 k r
3
k SH
k
k T
JW T
k t
4
).
Therefore, this will manipulate an A with invalid SH
k
key values. Furthermore, we generate one-time dy-
namic alias identity over an encrypted identity such as
T T P : T T P
A
id
= S
E
k
(T T P
~
id
)
T T P
~
MK
and NU : NU
~
A
id
=
S
E
k
(NU
~
id
)
H
NU
P
to provide sufficient randomness and
anonymity for each new user. Hence, we achieve
stated objective of theorem 2.
Figure 2: Code snippet in .spdl using scyther.
Theorem 3. Our proposed protocol safeguards
against impersonation and replay attacks.
Proof: The computational hardness in deriving
[T T P : r
0
3
= (r
3
⊕ H
SD
~
id
)] will increase the computa-
tional complexity in deciphering T
JW T
with SH
k
due
to dynamic SH
k
updation that is directly proportional
to T
JW T
session expiry time. Since time-stamps are
Figure 3: Scyther simulation results for security verifica-
tion.
appended with data blocks T T P : F
NU
id
= H(NU
~
A
id
k
H
NU
P
k H
SD
~
id
k t
1
), NU : F
0
NU
id
= H(NU
~
A
id
k H
NU
P
k
H
SD
~
id
k t
2
), T T P : Q
1
= H(1 k r
3
k SH
k
k T
JW T
k t
3
)
and NU : Q
2
= H(2 k r
3
k SH
k
k T
JW T
k t
4
). If,
t
0
− t ≤ δt, where t’ is data block received time and
t is data block generation time. If time difference is
less than δt the data block is accepted else, rejected.
Hence, we achieve stated objective of theorem 3.
5 PERFORMANCE ANALYSIS
Table 2 and Table 3 present empirical analysis with
P 1:(Das et al., 2020), P 2:(Kang et al., 2016),
P 3:(Khan et al., 2011), P 4:(Saeed et al., 2018)
and P 5:(Zhang et al., 2019). We assume com-
munication and computational parameters such as
hashing: T
H
= 0.0005 sec of 160 bit, Symmetric
encryption/decryption:T
E/D
= 0.0087 sec, shared key,
random number, JWT and pseudo random function:
T
RF
= 0.0003 sec of 128 bits, XOR: T
X
= 0.002 sec,
ECC multiplication: T
M
= 0.063075 sec of 320 bits,
identities and password of 64 bits, and timestamps
of 16 bits. Energy consumption is calculated with
3(W ) of power as (E
mJ
= Power
W
×Time
sec
). As ob-
served our performance is superior to P 2, P 4 and P 5.
P 1 and P 3 have lower costs and energy consumption
than ours. The minimal increase in overall perfor-
mance is acceptable given that our protocol achieves
dynamic system expansion, mitigates system restart-
ing and cryptographic wastage, and preserves robust
security with effective privacy.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
816

Table 2: Computation and communication costs with energy consumption.
Protocols User node Gateway node Sensor node Total running cost Messages Total cost Energy
P 1 2T
M
+ 2T
RF
— 2T
M
+ 2T
RF
4T
M
+ 4T
RF
= 0.0264 sec. 3 0384 bits 763.6 mJ
P 2 2T
E
+ T
D
+ 2T
H
+ 2T
X
T
E/D
+2T
H
+3T
X
T
E/D
+3T
H
+4T
X
4T
E
+ 3T
D
+ 7T
H
+ 9T
X
= 0.0825 sec. 4 1856 bits 247.2 mJ
P 3 2T
H
+ T
X
— 10T
H
+ 9T
X
12T
H
+ 10T
X
= 0.026 sec. 4 1200 bits 78 mJ
P 4 3T
M
+ T
E
— 3T
M
6T
M
+ T
E
= 0.38715 sec. 3 2464 bits 1166.1 mJ
P 5 7T
H
+ T
D
— 9T
H
+ T
D
+ 2T
E
16T
H
+ 2T
E
+ 2T
D
= 0.04285 sec. 4 1600 bits 128.4 mJ
Ours 3T
H
+ T
D
+ 2T
X
— 2T
H
+ T
E
+ 2T
X
5T
H
+ T
E/D
+ 4T
X
= 0.0279 sec. 4 1088 bits 83.7 mJ
Table 3: Features comparison.
Features P 1 P 2 P 3 P 4 P 5 Ours
Dynamic scalability 5 5 5 5 5 3
Anonymity 3 5 3 3 3 3
Robust security 3 5 5 3 3 3
No complete rights policy 5 5 5 5 5 3
Symmetric key cryptography 5 5 3 5 3 3
Formal analysis using ROR model 5 5 5 3 3 3
Security verification 5 5 5 5 5 3
Safe against impersonation attacks 3 3 3 3 3 3
Safe against replay attacks 3 3 3 3 3 3
IND-CPA secure 5 5 5 3 3 3
Pairing-free scheme 3 5 5 3 3 3
Efficient token updation 5 5 5 5 5 3
Efficient shared key updation 5 5 5 5 5 3
Number of factors used 2 2 2 2 2 2
6 CONCLUDING REMARKS
In this paper, we propose privacy preserving au-
thentication protocol for dynamic system expansion
with partially TTP. Our protocol achieves superior
trade-off between robust security and effective pri-
vacy by adopting one-time alias identity with dy-
namic JWT and shared key updation during authenti-
cation. To achieve dynamic and anonymous scalabil-
ity we mitigate complete rights policy and knowledge
sharing with TTP. Empirical analysis demonstrates
that our proposed protocol is light-weight with addi-
tional security features as compared to similar mod-
eled schemes.
REFERENCES
Alcaide, A., Palomar, E., Montero-Castillo, J., and Rib-
agorda, A. (2013). Anonymous authentication
for privacy-preserving iot target-driven applications.
computers & security, 37:111–123.
Babbage, S., Catalano, D., Cid, C., de Weger, B., Dunkel-
man, O., Gehrmann, C., Granboulan, L., Lange, T.,
Lenstra, A. K., Mitchell, C., et al. (2009). Ecrypt
yearly report on algorithms and keysizes. Technical
report.
Chang, C.-C. and Le, H.-D. (2015). A provably secure, ef-
ficient, and flexible authentication scheme for ad hoc
wireless sensor networks. IEEE Transactions on wire-
less communications, 15(1):357–366.
Chen, Y., Xu, W., Peng, L., and Zhang, H. (2019). Light-
weight and privacy-preserving authentication protocol
for mobile payments in the context of iot. IEEE Ac-
cess, 7:15210–15221.
Das, M. L., Kumar, P., and Martin, A. (2020). Secure and
privacy-preserving rfid authentication scheme for in-
ternet of things applications. Wireless Personal Com-
munications, 110(1):339–353.
Gope, P. and Sikdar, B. (2018). Lightweight and privacy-
preserving two-factor authentication scheme for iot
devices. IEEE Internet of Things Journal, 6(1):580–
589.
Kang, J., Park, G., and Park, J. H. (2016). Design of
secure authentication scheme between devices based
on zero-knowledge proofs in home automation ser-
vice environments. The Journal of Supercomputing,
72(11):4319–4336.
Khan, M. K., Kim, S.-K., and Alghathbar, K. (2011). Crypt-
analysis and security enhancement of a ‘more efficient
& secure dynamic id-based remote user authentication
scheme’. Computer Communications, 34(3):305–309.
Lai, C., Li, H., Liang, X., Lu, R., Zhang, K., and Shen, X.
(2014). Cpal: A conditional privacy-preserving au-
thentication with access linkability for roaming ser-
vice. IEEE Internet of Things Journal, 1(1):46–57.
Lin, X.-J., Sun, L., and Qu, H. (2015). Insecurity of
an anonymous authentication for privacy-preserving
iot target-driven applications. computers & security,
48:142–149.
Saeed, M. E. S., Liu, Q.-Y., Tian, G., Gao, B., and Li, F.
(2018). Remote authentication schemes for wireless
body area networks based on the internet of things.
IEEE Internet of Things Journal, 5(6):4926–4944.
Trivedi, H. S. and Patel, S. J. (2020). Design of secure
authentication protocol for dynamic user addition in
distributed internet-of-things. Computer Networks,
178:107335.
Turkanovi
´
c, M., Brumen, B., and H
¨
olbl, M. (2014). A novel
user authentication and key agreement scheme for het-
erogeneous ad hoc wireless sensor networks, based
on the internet of things notion. Ad Hoc Networks,
20:96–112.
Vijayakumar, P., Chang, V., Deborah, L. J., Balusamy, B.,
and Shynu, P. (2018). Computationally efficient pri-
vacy preserving anonymous mutual and batch authen-
tication schemes for vehicular ad hoc networks. Fu-
ture generation computer systems, 78:943–955.
Wang, Y.-y., Liu, J.-y., Xiao, F.-x., and Dan, J. (2009). A
more efficient and secure dynamic id-based remote
user authentication scheme. Computer communica-
tions, 32(4):583–585.
Privacy Preserving Scalable Authentication Protocol with Partially Trusted Third Party for Distributed Internet-of-Things
817

Wang, Z. (2018). A privacy-preserving and account-
able authentication protocol for iot end-devices with
weaker identity. Future Generation Computer Sys-
tems, 82:342–348.
Zhang, L., Zhao, L., Yin, S., Chi, C.-H., Liu, R., and Zhang,
Y. (2019). A lightweight authentication scheme with
privacy protection for smart grid communications. Fu-
ture Generation Computer Systems, 100:770–778.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
818
