
Anonymous Attribute-based Credentials in Collaborative Indoor
Positioning Systems
Ra
´
ul Casanova-Marqu
´
es
1,2 a
, Pavel Pascacio
2,3 b
, Jan Hajny
1 c
and Joaqu
´
ın Torres-Sospedra
2,4 d
1
Department of Telecommunications, Brno University of Technology, Brno, Czech Republic
2
Institute of New Imaging Technologies, Universitat Jaume I, Castell
´
on, Spain
3
Electrical Engineering Unit, Tampere University, Tampere, Finland
4
UBIK Geospatial Solutions S.L., Castell
´
on, Spain
Keywords:
Attribute-based Credentials, Collaborative Indoor Positioning Systems, Privacy, Anonymity, Bluetooth Low
Energy, Wearables.
Abstract:
Collaborative Indoor Positioning Systems (CIPSs) have recently received considerable attention, mainly be-
cause they address some existing limitations of traditional Indoor Positioning Systems (IPSs). In CIPSs, Blue-
tooth Low Energy (BLE) can be used to exchange positioning data and provide information (the Received
Signal Strength Indicator (RSSI)) to establish the relative distance between the actors. The collaborative mod-
els exploit the position of actors and the relative position among them to allow positioning to external actors
or improve the accuracy of the existing actors. However, the traditional protocols (e.g., iBeacon) are not yet
ready for providing sufficient privacy protection. This paper deals with privacy-enhancing technologies and
their application in CIPS. In particular, we focus on cryptographic schemes which allow the verification of
users without their identification, so-called Anonymous Attribute-based Credential (ABC) schemes. As the
main contribution, we present a cryptographic scheme that allows security and privacy-friendly sharing of
location information sent through BLE advertising packets. In order to demonstrate the practicality of our
scheme, we also present the results from our implementation and benchmarks on different devices.
1 INTRODUCTION
Wi-Fi and BLE fingerprinting are popular techniques
for providing indoor positioning. They rely on the
signal strength from multiple emitters (either Wi-Fi
Access Points (APs) or BLE beacons). However, the
Received Signal Strength (RSS) data used to estimate
the positions have a strong noise component, there-
fore having a general positioning accuracy at meter
level (i.e., a few meters) (Mautz, 2012). In addition,
the deployment complexity, as well as relying on an
infrastructure of beacons and servers, have become
a serious problem for large organizations all around
the world. Wearable-based CIPSs are increasingly be-
coming popular over the last few years as a solution
to address those problems in indoor positioning (Pas-
cacio et al., 2021). The CIPSs use the location of a
a
https://orcid.org/0000-0001-6653-867X
b
https://orcid.org/0000-0001-9206-7496
c
https://orcid.org/0000-0003-2831-1073
d
https://orcid.org/0000-0003-4338-4334
set of actors and their relative distances to 1) provide
localization to external users and/or 2) improve the
positioning accuracy of the current users that are col-
laborating (Khandker et al., 2019).
Wearable devices are equipped with built-in tech-
nologies such as Wi-Fi and Bluetooth, which are ca-
pable of estimating users’ positions and ubiquity in
indoor environments. In particular, CIPSs approaches
based on BLE are one of the most popular solutions.
Smartphones can send BLE advertisement packets
(e.g., iBeacon), which can be used later to compute
the relative distances between them with the gathered
RSS values. This alternative presents a straightfor-
ward deployment and a good trade-off between power
consumption and performance (Yang et al., 2020).
However, high inter-connectivity to unknown devices
and the lack of strong communication protocols in
terms of security and privacy represent a weakness.
Malicious actors could perform attacks such as spoof-
ing or eavesdropping in unsecured collaborative sys-
tems (Chebli et al., 2019). These issues encouraged
the development of more privacy-friendly solutions.
Casanova-Marqués, R., Pascacio, P., Hajny, J. and Torres-Sospedra, J.
Anonymous Attribute-based Credentials in Collaborative Indoor Positioning Systems.
DOI: 10.5220/0010582507910797
In Proceedings of the 18th International Conference on Security and Cryptography (SECRYPT 2021), pages 791-797
ISBN: 978-989-758-524-1
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
791

Existing CIPS are based on centralized schemes.
A server-based solution facilitates more complex at-
tacks such as user traceability or linkability of com-
munications. Thus, it is necessary to move to a decen-
tralized approach. Building a decentralized CIPS us-
ing BLE technology represents a major challenge due
to the reduced space available in BLE packets, which
depends on the Bluetooth version (Bluetooth SIG,
2019). This hinders the use of standard algorithms
such as RSA, DH or AES for information encryp-
tion and user authentication. Attribute-based authen-
tication schemes allow users to anonymously and se-
lectively prove possession of their personal attributes
such as age, citizenship, negative SARS-CoV-2 test
or location data. Elliptic curve cryptography and the
reduced size of its keys can tackle the aforementioned
problems and provide anonymity, unlinkability, un-
traceability and selective disclosure of attributes.
In light of the identified problems, in this work
we pursue the decentralization of collaborative indoor
positioning systems based on BLE beacons, while
providing, through elliptic curve cryptography and
anonymous attribute-based authentication schemes, a
secure and privacy-friendly system for exchanging lo-
cation data.
1.1 Related Work
In the literature there are several articles that address
anonymity, security, and privacy issues of IPSs from
different perspectives (e.g., Wireless Sensor Network
(WSN) or Internet of Things (IoT)). However, only
very few of them focus on collaborative positioning
and/or BLE beacon approaches. One of the most in-
teresting papers is proposed by (Kang et al., 2018),
which is based on the open-source Eddystone BLE
format proposed by (Hassidim et al., 2016). Eddy-
stone BLE format introduces a scheme to mitigate
tracking and security threats. The core of the scheme
is cloud-based Ephemeral Identifiers (EID), which en-
sures only authorized members to properly identify
the BLE standard beacons.
Up to now, far too little attention has been paid
to CIPSs. (Zidek et al., 2018) developed a scheme
named Bellrock which combines an ecosystem of
standard beacons and user-based beacons. Bell-
rock provides access control to standard beacons
and anonymity to user-based beacons by using three
techniques to generate pseudo-anonymous identifiers
(random, synchronized, and encrypted) that can be
unmasked by a server.
(Destiarti et al., 2017) proposed the Data Trans-
mission Scheme for Indoor Mobile Cooperative Lo-
calization System that works over Wi-Fi. The scheme
uses AES-128 to encrypt the message, MD5 to con-
struct the HMAC and RSA-2048 to encrypt both the
AES key and the HMAC. Their approach might not
be well suited as the system remains vulnerable to
man-in-the-middle attacks during the RSA key-pair
exchange, leading to a total loss of confidentiality and
message integrity.
A key problem with the aforementioned propos-
als lies in server-dependency, turning the system into
a centralized environment. This method could suffer
from a plethora of pitfalls such as denial of service
(DoS), spoofing, etc.
Some preliminary work on ABCs was carried
out several decades ago by (Chaum, 1985), (Brands,
2000), and (Camenisch and Lysyanskaya, 2001). In
subsequent years, much more information on ABCs
has become available about practical applications
(Arfaoui et al., 2015), revocation protocols (Ca-
menisch et al., 2010) and the use of more efficient
algebraic structures (Chase et al., 2014), (Barki et al.,
2016), and (Ringers et al., 2017). Due to the high
computational complexity required by these schemes,
practical implementation on constrained devices is
still a challenge, researchers need to find a scheme
that satisfies their specific needs. As far as we know,
no studies have been published on ABC schemes ap-
plied to CIPSs.
1.2 Our Contribution
In order to fill the gap found in the literature, we pro-
pose a new decentralized privacy-preserving user au-
thentication mechanism for CIPSs with ABC. Our
solution combines zero-knowledge proofs with a re-
vocation scheme based on lifetime and provides
anonymity, unlinkability and untraceability.
The main contributions are the following:
• To the best of our knowledge, we present the first
decentralized security scheme for CIPSs based on
BLE advertising.
• We define a scheme that provide anonymous lo-
cation data sharing, decentralized authentication
and offline revocation.
• We provide a security analysis on the proposed
solution.
• We describe the implementation results.
The rest of the paper is organized as follows. Sec-
tion 2 gives a brief overview of the system model.
Section 3 thoroughly details the cryptographic design
of the scheme. Section 4 analyzes the security. Sec-
tion 5 presents the implementation results. Finally,
Section 6 reports some conclusions.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
792
2 SYSTEM OVERVIEW
The system model is depicted in Figure 1 and consists
of the following entities:
• Issuer (I): is responsible for issuing the personal
attribute m
ID
to a user using the Issue algorithm.
The m
ID
attribute represents the user identifier
obtained during registration in the system. The
Issue algorithm provides the user with crypto-
graphically signed credentials that are valid within
the system. Access credentials consist of the val-
ues σ,σ
x
0
,σ
x
r
,σ
x
ID
.
• Revocation Authority (RA): removes invalid
users. Access control is achieved through the re-
vocation credential σ
x
r
, issued from the revoca-
tion attribute m
r
. Attempting to authenticate with
the revoked credentials will result in failure. To
reduce the complexity of the system, we will con-
sider from now on the revocation authority and the
issuer as the same entity (I).
• User (U): enrolls in the system to use the col-
laborative indoor positioning system. Every user
holds unique credentials generated by the issuer
and the revocation entity (σ,σ
x
0
,σ
x
r
,σ
x
ID
), then,
the user can anonymously prove their possession
to the verifier using the Show algorithm.
• Verifier (V): verifies the possession of the user at-
tribute using the Verify algorithm. If the attribute
ownership is verified successfully, the verifier will
be able to use the location information to position
themself. Otherwise, the information is rejected.
Issuer Revocation Authority
Show
Verify
IssueIssue
User Verifier
Figure 1: System structure.
Initially, all devices registered in the system behave as
Users. When one of them needs to improve its posi-
tion, it temporarily assumes the role of Verifier. This
role can be used to ensure that the information is pro-
vided by a valid user.
There are two modes of operation for the User and
Verifier roles: the active mode and the passive mode.
User operation modes: 1) Active mode: responds
to verifier requests and assists them with positioning
by actively participating in the system. 2) Passive
mode: remains unnoticed in the system and does not
respond to verifier requests. In this mode, the user
does not interact with the system.
Verifier operation modes: 1) Active mode: actively
requests location data from nearby users to improve
its position. 2) Passive mode: remains hidden in the
system and waits for other verifiers to request location
data. In this mode, positioning is not possible if there
are no active verifiers nearby.
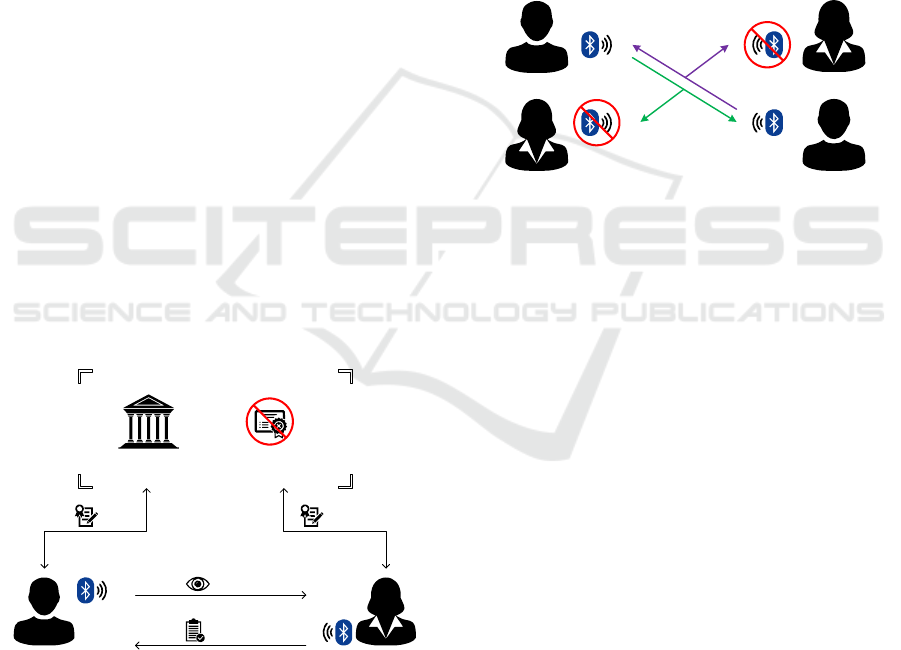
Figure 2 depicts each of these four modes. User
A acts in active mode, user B acts in passive mode,
verifier C acts in active mode, and verifier D acts in
passive mode.
º
Verifier C
User B
Verifier D
User A
Verifier request
User response
Figure 2: System roles and operation modes.
These modes of operation are useful for improving
privacy in environments where there are few devices,
and it may be easy to determine their identity. In this
case, the user or verifier can go into passive mode and
disappear from the system. We will not go into further
details because it is beyond the scope of this paper.
3 CRYPTOGRAPHIC DESIGN
This section describes the protocol for user authenti-
cation in a collaborative indoor positioning system.
3.1 Preliminaries
The symbol H denotes a secure hash function. We
write a
$
← A when a is sampled uniformly at random
from A. Let e denote a bilinear map G
1
× G
2
→ G
T
.
3.2 Protocol Specification
First, the user must be registered in the system by
sending their personal information to the issuer. The
issuer generates the credentials and sends them to the
user. The user can now legitimately participate in the
system. This algorithm will be denoted as Issue.
Anonymous Attribute-based Credentials in Collaborative Indoor Positioning Systems
793
When the verifier wants to improve their position,
a BLE advertisement packet with a timestamp will be
broadcast. The nearby users will compute the proof
of knowledge and transmit it via another BLE packet.
This algorithm will be denoted as Show.
Finally, the verifier will ensure through the proof
of knowledge that the user has valid credentials and
will use the location information to position themself.
This algorithm will be denoted as Verify.
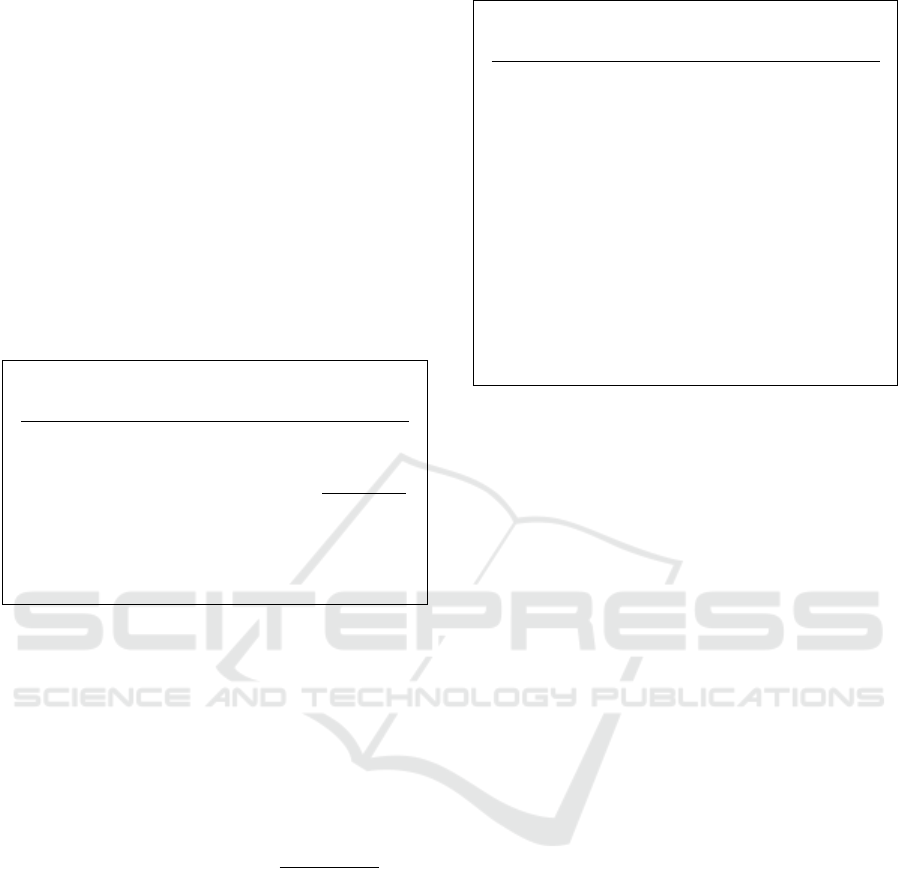
3.2.1 Issue
To register the user in the system and generate the
valid credentials, the user and the issuer perform the
algorithm shown in Figure 3.
User Issuer
q,G
1
,G
2
,G
T
,e,g
1
,g
2
← G (1
τ
), pk
I
(m
ID
) sk
I
= (x
0
,x
r
,x
ID
), pk
I
= g
x
0
2
m
r
= ww/yyyy
m
ID
−−−−−−−−−−−−−−−−−−−−→
σ = g
1
x
0
+m
r
x
r
+m
ID
x
ID
1
σ
x
0
← σ
x
0
σ
x
r
← σ
x
r
σ
x
ID
← σ
x
ID
σ,σ
x
0
,σ
x
r
,σ
x
ID
←−−−−−−−−−−−−−−−−−−−−
Store: σ,σ
x
0
,σ
x
r
,σ
x
ID
Figure 3: Definition of the Issue algorithm.
• The user U performs the following steps:
1) Introduces personal information in the app.
2) Establishes a secure communication channel
with I and sends m
ID
.
• The issuer I performs the following steps:
1) Generates the user’s private keys x
r
and x
ID
.
2) Signs the attributes m
r
and m
ID
with the is-
suer’s secret key as σ = g
1
x
0
+m
r
x
r
+m
ID
x
ID
1
; and
computes auxiliary values σ
x
0
,σ
x
r
,σ
x
ID
, where
σ
x
0
← σ
x
0
, σ
x
r
← σ
x
r
, and σ
x
ID
← σ
x
ID
.
3) Sends σ and auxiliary values σ
x
0
,σ
x
r
,σ
x
ID
to
the user U.
3.2.2 Show and Verify
To broadcast the location information and the proof
of knowledge, and subsequently verify that it comes
from a legitimate user, the user and the verifier will
run the algorithms shown in Figure 4.
• The verifier V performs the following steps:
1) Generates a nonce based on the current time.
2) Creates a BLE advertising packet with the
nonce and broadcasts it.
User Verifier
q,G
1
,G
2
,G
T
,e,g
1
,g
2
← G (1
τ
), pk
I
λ = (altitude, longitude,latitude,...) m
r
= ww/yyyy
timestamp
←−−−−−−−−−−−−−−−−−−
ρ,ρ
κ
,ρ
r
,ρ
ID
$
← Z
∗
q
ˆ
σ ← σ
ρ
,
ˆ
σ
x
0
← σ
ρ
x
0
ˆ
σ
x
r
← σ
ρ
x
r
,
ˆ
σ
x
ID
← σ
ρ
x
ID
t
κ
← g
ρ
κ
1
σ
ρ
ID
ρ
x
ID
e ← H (t
κ
,
ˆ
σ,
ˆ
σ
x
0
,
ˆ
σ
x
r
,
ˆ
σ
x
ID
,timestamp,λ)
s
κ
← ρ
κ
+ eρ
s
ID
← ρ
ID
− em
ID
ψ ← (
ˆ
σ,
ˆ
σ
x
0
,
ˆ
σ
x
r
,
ˆ
σ
x
ID
)
π ← (e,s
κ
,s
ID
)
ψ,π,λ
−−−−−−−−−−−−−−−−−→
t
0
κ
← g
s
κ
1
ˆ
σ
−e
x
0
ˆ
σ
−em
r
x
r
ˆ
σ
s
ID
x
ID
e
?
= H (t
0
κ
,
ˆ
σ,
ˆ
σ
x
0
,
ˆ
σ
x
r
,
ˆ
σ
x
ID
,timestamp,λ)
e(
ˆ
σ
x
0
,g
2
) = e(
ˆ
σ, pk
I
)
Figure 4: Definition of the Show and Verify algorithms.
• Nearby users u
i
perform the following steps after
they have received the timestamp:
1) Checks that the timestamp generated as a nonce
by the verifier is less than 2 seconds from the
current time to avoid replay attacks.
2) Generates the randomizers ρ, ρ
κ
,ρ
r
,ρ
ID
.
3) Computes
ˆ
σ,
ˆ
σ
x
0
,
ˆ
σ
x
r
,
ˆ
σ
x
ID
, where
ˆ
σ ← σ
ρ
,
ˆ
σ
x
0
← σ
ρ
x
0
,
ˆ
σ
x
r
← σ
ρ
x
r
, and
ˆ
σ
x
ID
← σ
ρ
x
ID
.
4) Computes the attribute proof of knowledge t
κ
as t
κ
← g
ρ
κ
1
σ
ρ
ID
ρ
x
ID
.
5) Calculates the cryptographic hash e as
H (t
κ
,
ˆ
σ,
ˆ
σ
x
0
,
ˆ
σ
x
r
,
ˆ
σ
x
ID
,timestamp,λ) and the
auxiliary proof of knowledge values s
κ
,s
ID
,
where s
κ
← ρ
κ
+ eρ and s
ID
← ρ
ID
− em
ID
.
6) Creates a BLE advertising packet with the lo-
cation information λ and the proof of knowl-
edge ψ ← (
ˆ
σ,
ˆ
σ
x
0
,
ˆ
σ
x
r
,
ˆ
σ
x
ID
),π ← (e,s
κ
,s
ID
),
and transmits it by broadcast.
• Nearby verifiers v
i
execute the following steps af-
ter receiving ψ, π, and λ.
1) Recomputes the attribute proof of knowledge t
0
κ
as t
0
κ
← g
s
κ
1
ˆ
σ
−e
x
0
ˆ
σ
−em
r
x
r
ˆ
σ
s
ID
x
ID
.
2) Calculates the cryptographic hash using t
0
κ
as H (t
0
κ
,
ˆ
σ,
ˆ
σ
x
0
,
ˆ
σ
x
r
,
ˆ
σ
x
ID
,timestamp,λ) and
checks if it matches the value of e.
3) Computes the bilinear pairing e(
ˆ
σ
x
0
,g
2
) =
e(
ˆ
σ, pk
I
) to verify the credentials were emitted
by the issuer.
3.3 Bluetooth Integration
The proposed scheme transmits information using
BLE advertising packets. Bluetooth 4.2 and earlier
SECRYPT 2021 - 18th International Conference on Security and Cryptography
794
defined a payload size of 31 bytes for a single BLE
advertisement packet. However, since it is impracti-
cal to pack both the positioning data and the proof of
knowledge into 31 bytes, we have considered version
5.0 of the BLE protocol. Bluetooth 5.0 introduced
a significant improvement by increasing the capacity
of advertising packets. With Low-Energy Advertising
Extensions, the advertisement payload can hold up to
254 bytes (Bluetooth SIG, 2019).
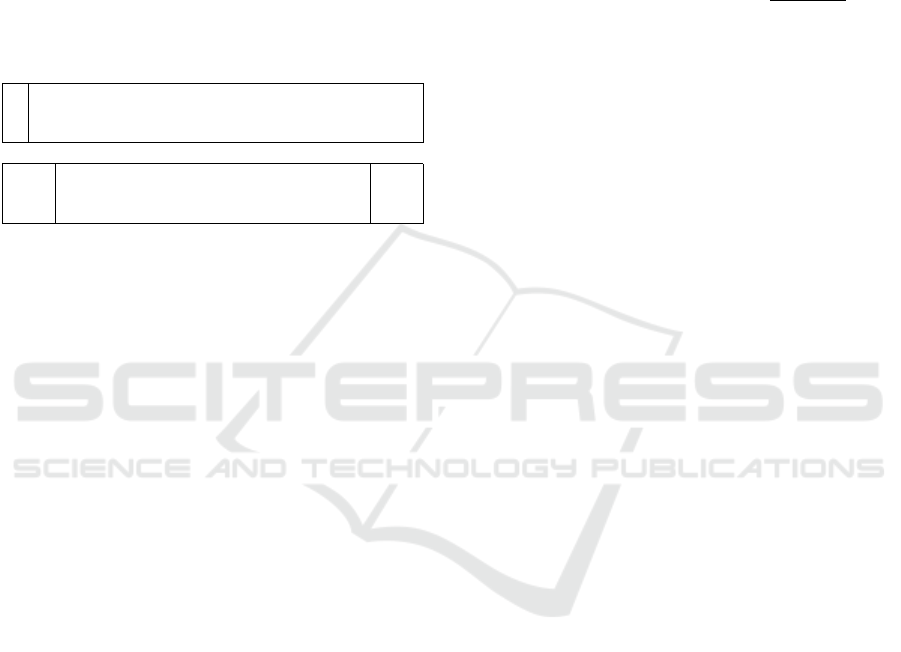
To build the structure of the BLE advertising
packet, we have assumed the structure depicted in
Figure 5.
0
1 2
3
4
5 6
7
8
9
10
11 12
13
14
15
UUID
ψ ← (
ˆ
σ,
ˆ
σ
x
0
,
ˆ
σ
x
r
,
ˆ
σ
x
ID
)
120B
16
17
18
19
20
21 22
23
24
25 26
27
28
29
30 31
ψ
12B
π ← (e,s
κ
,s
ID
)
92B
λ
22B
Figure 5: Definition of the BLE advertising payload.
The UUID field occupies 8 bytes, the proof of knowl-
edge (ψ, π) consists of 224 bytes, and there is a free
space of 22 bytes for the positioning data (λ). This
part is explained in detail in Section 5.
4 SECURITY ANALYSIS
The protocol is composed of the following parts:
the anonymous credentials scheme, the revocation
scheme and the positioning information. In this sec-
tion we provide a brief informal security analysis of
each of them.
4.1 Anonymous Credentials
Following the security model defined by (Chase et al.,
2014) for anonymous credential schemes, it is re-
quired to meet the following properties:
• Correctness: honest users can produce an accept-
ing proof.
• Unforgeability: dishonest users cannot produce an
accepting proof.
• Anonymity: users cannot be identified based on
the values of attributes.
• Key-Parameter Consistency: every public key has
a distinct private key.
Based on the random Oracle model in (Camenisch
et al., 2019), the credential scheme used in our system
has proven to be secure under the n-SCDHI assump-
tion (defined below).
Definition 1 (n-Strong Computational Diffie-Hell-
man Inversion Problem (SCDHI)). Let O
bb
(·) on in-
put (m
1
,...,m
n
) ∈ Z
∗
q
n
add (m
1
,...,m
n
) to Q and out-
put g
1/(x
0
+
∑
n
i=1
x
i
m
i
)
. Let O
dh
i
(·) on input h output h
x
i
.
Define the advantage of A as follows.
Adv
n−SCDHI
(A) = Pr
h
(G,g,q) ← GroupSetup(1
κ
),
(x
0
,...,x
n
)
$
← Z
∗
q
n+1
,(y,m
∗
1
,...,m
∗
n
) ←
A
O
bb
(·),O
dh
0
(·),...,O
dh
n
(·)
(g) : y = g
1
x
0
+
∑
n
i=1
x
i
m
∗
i
∧
(m
∗
1
,...,m
∗
n
/∈ Q
i
. (1)
SCDHI is (t,ε)-hard if no t-time adversary has ad-
vantage at least ε.
4.2 Revocation Scheme
Following the security model defined by (Camenisch
et al., 2016), it is required to meet the following prop-
erties:
• Revocation Completeness: unrevoked users will
pass the revocation check.
• Revocation Soundness: revoked users will not
pass the revocation check.
• Revocation Privacy: users will not lose privacy by
proving an unrevoked revocation handle.
The revocation scheme is based on the epoch’s ex-
piration. In our solution, we set the epoch to one
week and define the revocation attribute as follows:
m
r
← ww/yyyy. When the credentials expire, the user
must renew them, allowing weekly access control.
We assume that all users in the system have the
date correctly set on their devices. When a user tem-
porarily switches to the verifier role, they can produce
the revocation attribute without requiring the user to
disclose it.
4.3 Location Information
The positioning information is the critical component
of the system. We outline the resistance of the pro-
tocol against some of the most common attacks that
affect the integrity and confidentiality.
Eavesdropping Attack: A fraudulent user could
monitor the communications and attempt to de-
anonymize a legitimate user because the information
is sent in plain text. Capturing communications is
possible since the information is freely transmitted.
However, removing anonymity and attempting to link
a specific user to positioning data is extremely diffi-
cult. Each time a user transmits the position, the cre-
dentials are randomized.
Anonymous Attribute-based Credentials in Collaborative Indoor Positioning Systems
795
Replay Attack: A malicious user could carry out
this attack because the information is not altered.
But after two seconds, the verifier transmits a new
timestamp, invalidating the packet’s authentication.
During verification with the new timestamp, e
?
=
H (...,timestamp, . ..) will produce a different value
and the verification will fail.
Spoofing Attack: A dishonest user could attempt to
impersonate a legitimate user and try to provide fake
information to the system. This attack is impractical
because a user without valid credentials will be unable
to authenticate the data.
Tampering Attack: A malicious user could attempt
to modify an authenticated packet to alter the posi-
tioning of users. This attack is unfeasible because in
case λ is modified, e
?
= H (. . . , λ) will produce a dif-
ferent value and the verification will fail.
5 IMPLEMENTATION RESULTS
In this section, we present the results of the imple-
mentation of our protocol on different smartphones.
Table 1 shows the hardware and software specifica-
tions of the devices used.
Table 1: HW and SW specifications of the smartphones.
Device CPU OS Bluetooth RAM
Samsung Galaxy
S21+ 5G
Exynos 2100 Android 11 5.0 LE 8 GB
Samsung Galaxy
S20 FE
Exynos 990 Android 10 5.0 LE 6 GB
Samsung Galaxy
A52
SDM720G Android 11 5.0 LE 6 GB
Samsung Galaxy
A32
MTK D720 Dual
+ Hexa
Android 11 5.0 LE 4 GB
Samsung Galaxy
S8
Exynos 8895 Android 9 5.0 LE 4 GB
We have used elliptic curve cryptography for the im-
plementation and design of the protocol. The im-
plementation is based on the mcl cryptographic li-
brary (Shigeo, 2018). It allows us to create portable
applications between different devices and operating
systems and supports the optimal Ate pairing over BN
curves. We use the 256-bit Barreto-Naehrig curve
(BN254) provided by the library and compiled it
using OpenSSL (The OpenSSL Project, 2003) and
GMP (Granlund, 2014) as dependencies. We ob-
served in (Hajny et al., 2018) that the GMP library
achieves the best performance results for bilinear pair-
ing operations. With this curve size, an uncompressed
point occupies 64 bytes and a compressed point 33
bytes. The size of a scalar integer is 32 bytes. To
reduce the size of the information, we have consid-
ered transmitting the points in their compressed form.
Furthermore, we used the OpenSSL library to com-
pute cryptographic hashes. In particular, the SHA-2
function with a digest size of 224 bits.
We have implemented the protocol in C to mea-
sure the performance on a RaspberryPi 4. The execu-
tion on this device is in the order of µs. The smart-
phone application has been developed in Java and
Kotlin. The Android NDK (Native Development Kit)
allows us to implement parts of our app in native code,
using languages such as C and C++. This allows us to
call the mcl library functions through the Java Native
Interface (JNI).
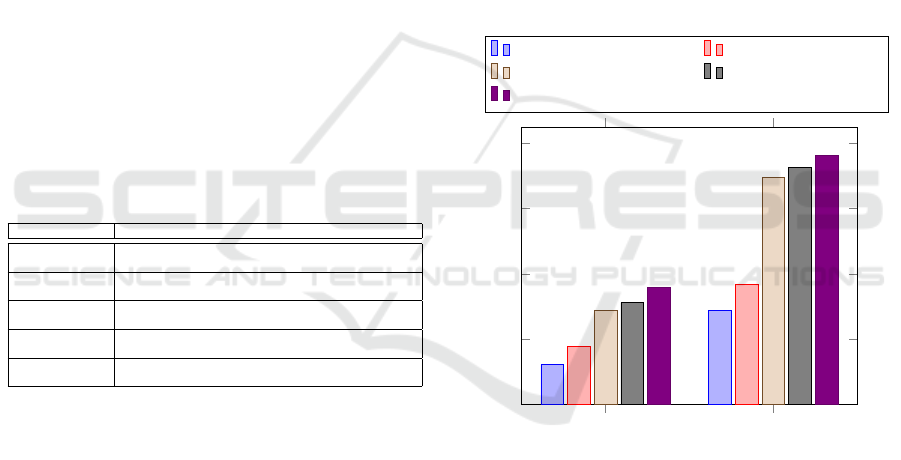
Finally, we benchmark the entire protocol without
including the communication overhead to evaluate the
performance and speed of the algorithms. The results
of the execution are shown in Figure 6. We can see the
execution of both protocols takes slightly more than
10 ms on the slowest device. During the development
we used the Energy Profiler of Android Studio and
did not detect an energy consumption impact.
Show Verify
0
2
4
6
8
1.21
2.88
1.78
3.66
2.87
6.96
3.11
7.26
3.57
7.64
Time t [ms]
S. Galaxy S21+ 5G S. Galaxy S20 FE
S. Galaxy A52 S. Galaxy A32
S. Galaxy S8
Figure 6: Speed comparison of the Show and Verify algo-
rithms.
6 CONCLUSION
Our solution allows sharing anonymous location in-
formation in CIPSs using BLE advertisement, provid-
ing real privacy in a fully decentralized system where
sources of data can be trusted. Notwithstanding the
relatively limited implementation on constrained de-
vices, this work offers valuable insights into the se-
curity and performance of implementing anonymous
ABC schemes on CIPSs. As far as we know, we
present the first fully decentralized scheme running
over BLE. Our approach has proven to be efficient on
SECRYPT 2021 - 18th International Conference on Security and Cryptography
796

mobile devices and completely feasible for real-time
environments. Next, we plan to improve the protocol
to reduce the size of the cryptographic part, improve
the revocation scheme, provide information encryp-
tion, and start deployment in real environments.
ACKNOWLEDGMENT
The authors gratefully acknowledge funding from
European Union’s Horizon 2020 Research and In-
novation programme under the Marie Sklodowska
Curie grant agreement No. 813278 (A-WEAR, http:
//www.a-wear.eu/) and from Ministry of the Inte-
rior of the Czech Republic under grant VJ01030002.
J. Torres-Sospedra acknowledges funding from IN-
SIGNIA project (ref. PTQ2018-009981, MICINN).
REFERENCES
Arfaoui, G., Lalande, J.-F., Traor
´
e, J., Desmoulins, N.,
Berthom
´
e, P., and Gharout, S. (2015). A practical set-
membership proof for privacy-preserving NFC mobile
ticketing. Proceedings on Privacy Enhancing Tech-
nologies, 2015(2):25–45.
Barki, A., Brunet, S., Desmoulins, N., and Traor
´
e, J.
(2016). Improved algebraic MACs and practical
keyed-verification anonymous credentials. In Pro-
ceedings of the 2016 Selected Areas in Cryptography
- SAC 2016.
Bluetooth SIG (2019). Core specification 5.2. Technical
Report 5.2, Bluetooth Special Interest Group.
Brands, S. A. (2000). Rethinking Public Key Infrastructures
and Digital Certificates: Building in Privacy. MIT
Press, Cambridge, MA, USA.
Camenisch, J., Drijvers, M., Dzurenda, P., and Hajny, J.
(2019). Fast keyed-verification anonymous creden-
tials on standard smart cards. In IFIP International
Conference on ICT Systems Security and Privacy Pro-
tection, pages 286–298. Springer.
Camenisch, J., Drijvers, M., and Hajny, J. (2016). Scalable
revocation scheme for anonymous credentials based
on n-times unlinkable proofs. In Proceedings of the
2016 ACM on Workshop on Privacy in the Electronic
Society, WPES ’16, pages 123–133, New York, NY,
USA. ACM.
Camenisch, J., Kohlweiss, M., and Soriente, C. (2010).
Solving revocation with efficient update of anony-
mous credentials. In Garay, J. A. and De Prisco,
R., editors, Security and Cryptography for Networks,
pages 454–471, Berlin, Heidelberg. Springer Berlin
Heidelberg.
Camenisch, J. and Lysyanskaya, A. (2001). An Efficient
System for Non-transferable Anonymous Credentials
with Optional Anonymity Revocation, pages 93–118.
Springer Berlin Heidelberg, Berlin, Heidelberg.
Chase, M., Meiklejohn, S., and Zaverucha, G. (2014). Al-
gebraic MACs and keyed-verification anonymous cre-
dentials. In Proceedings of the 2014 ACM SIGSAC
Conference on Computer and Communications Se-
curity, CCS ’14, pages 1205–1216, New York, NY,
USA. ACM.
Chaum, D. (1985). Security without identification: Trans-
action systems to make big brother obsolete. Com-
mun. ACM, 28(10):1030–1044.
Chebli, M. S., Mohammad, H., and Al Amer, K. (2019).
An overview of wireless indoor positioning systems:
Techniques, security, and countermeasures. In Inter-
national Conference on Internet and Distributed Com-
puting Systems, pages 223–233. Springer.
Destiarti, A. R., Kristalina, P., and Sudarsono, A. (2017).
Secure data transmission scheme for indoor mobile
cooperative localization system. In 2017 International
Electronics Symposium on Engineering Technology
and Applications (IES-ETA), pages 50–56. IEEE.
Granlund, T. (2014). GNU MP: The GNU Multiple Preci-
sion Arithmetic Library. https://gmplib.org.
Hajny, J., Dzurenda, P., Ricci, S., Malina, L., and Vrba,
K. (2018). Performance analysis of pairing-based el-
liptic curve cryptography on constrained devices. In
2018 10th International Congress on Ultra Modern
Telecommunications and Control Systems and Work-
shops (ICUMT), pages 1–5. IEEE.
Hassidim, A., Matias, Y., Yung, M., and Ziv, A. (2016).
Ephemeral identifiers: Mitigating tracking & spoof-
ing threats to ble beacons. url: https://developers.
google. com/beacons/eddystone-eidpreprint. pdf (vis-
ited on 06/15/2016).
Kang, J., Seo, J., and Won, Y. (2018). Ephemeral id beacon-
based improved indoor positioning system. Symmetry,
10(11):622.
Khandker, S., Torres-Sospedra, J., and Ristaniemi, T.
(2019). Improving rf fingerprinting methods by means
of d2d communication protocol. Electronics, 8(1):97.
Mautz, R. (2012). Indoor positioning technologies.
Geod
¨
atisch-geophysikalische Arbeiten in der Schweiz.
Pascacio, P., Casteleyn, S., Torres-Sospedra, J., Lohan,
E. S., and Nurmi, J. (2021). Collaborative indoor
positioning systems: A systematic review. Sensors,
21(3):1002.
Ringers, S., Verheul, E. R., and Hoepman, J.-H. (2017).
An efficient self-blindable attribute-based credential
scheme. IACR Cryptology ePrint Archive, 2017:115.
Shigeo, M. (2018). MCL library: A portable and fast
pairing-based cryptography library. https://github.
com/herumi/mcl.
The OpenSSL Project (2003). OpenSSL: The Open Source
toolkit for SSL/TLS. https://www.openssl.org.
Yang, J., Poellabauer, C., Mitra, P., and Neubecker, C.
(2020). Beyond beaconing: Emerging applications
and challenges of ble. Ad hoc networks, 97:102015.
Zidek, A., Tailor, S., and Harle, R. (2018). Bellrock:
Anonymous proximity beacons from personal de-
vices. In 2018 IEEE International Conference on Per-
vasive Computing and Communications (PerCom),
pages 1–10. IEEE.
Anonymous Attribute-based Credentials in Collaborative Indoor Positioning Systems
797
