
Storage Friendly Provably Secure Multivariate Identity-Based Signature
from Isomorphism of Polynomials Problem
Ratna Dutta
1
, Sumit Kumar Debnath
2
and Chinmoy Biswas
1
1
Indian Institute of Technology Kharagpur, Kharagpur, 721302, India
2
National Institute of Technology Jamshedpur, Jamshedpur, India
Keywords:
Identity Based Signature, Multivariate Cryptography, Isomorphism of Polynomial Problem, Signature of
Knowledge, EUF-CMA Security.
Abstract:
Multivariate public key cryptosystem (MPKC) is one of the promising candidates for post-quantum cryptog-
raphy (PQC) as it features fast and efficient computation with security under the NP hardness of solving a
system of multivariate quadratic (MQ) polynomial equations over a finite field. In the last two decades, there
have been remarkable development in MPKC specially in signature and encryption scheme. In this work, we
have developed a multivariate identity-based signature (MV-IBS) scheme employing a specialized version of
non-interactive zero-knowledge proofs of knowledge (NIZK). Our construction is existentially unforgeable
against chosen message and chosen identity attack (EUF-CMA) in the random oracle model (ROM) under
the hardness of the isomorphism of polynomials (IP) problem. An IP problem tests the equivalence of two
polynomial maps. It says that given access to two quadratic functions which are equal up to linear changes
of coordinates, it is difficult to compute these changes of coordinates. We emphasize that unlike most of the
MPKC, our scheme achieves provable security in an existing security framework. Additionally, the proposed
IBS performs better over the existing works in terms of user’s secret key size, master public key size and
master secret key size.
1 INTRODUCTION
Multivariate Public Key Cryptograpy (MPKC). In
the last few decades, public key cryptography (PKC)
has become an inevitable part of our global commu-
nication infrastructure. Most of our important com-
munication protocols utilize public key cryptosys-
tems like RSA, Diffe-Hellman key exchange, digi-
tal signature algorithms and elliptic curve algorithms
which rely on number theoretic assumptions like in-
teger factorization and discrete logarithm problem.
(Shor, 1999) came up with an algorithm which can
break these number theoretic problems by quantum
computer in polynomial time. Consequently, a suf-
ficiently powerful quantum computer will put many
forms of modern communication from key exchange
to encryption to digital authentication in danger. Post-
quantum cryptography (PQC) assures the cryptogra-
phy community that secure communication is possi-
ble even in the presence of quantum computer. In lit-
erature, the five well studied PQC variants are lattice-
based, multivariate-based, code-based, hash based
and isogeny-based cryptography. A working group of
the National Institute of Standards and Technologies
(NIST) is exploring the standardization of PQC since
2013. In addition, a regular Quantum-Safe-Crypto
Workshop is organized by the European Telecommu-
nications Standards Institute (ETSI). Among the dif-
ferent PQC variants, multivariate public key cryptog-
raphy (MPKC) catches the special attention to the
researchers and have been seen to be alternative to
the widely used PKC like RSA, digital signature, el-
liptic curve, etc. The main advantages of MPKC
are significant speed and cost-effective computation,
making it worthy for low-cost devices. In Eurocrypt
1988, (Matsumoto and Imai, 1988) introduced MPKC
whose security is based on solving a set of multi-
variate quadratic equations over a finite field which
is known to be NP hard problem. To solve a set of
multivariate polynomial equations, quantum comput-
ers have not yet been efficient so far and are unlikely
to provide any advantage against such a problem. In
the last few years, there has been an enormous de-
velopment of designing multivariate schemes (Kipnis
et al., 1999; Ding and Schmidt, 2005; Patarin, 1997)
in several directions. The MPKC schemes are compu-
Dutta, R., Debnath, S. and Biswas, C.
Storage Friendly Provably Secure Multivariate Identity-Based Signature from Isomorphism of Polynomials Problem.
DOI: 10.5220/0010580505950602
In Proceedings of the 18th International Conference on Security and Cryptography (SECRYPT 2021), pages 595-602
ISBN: 978-989-758-524-1
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
595

tationally efficient than other PQC variants. However,
they have large key sizes.
Identity Based Cryptography (IBC). IBC is an
alternative framework of public-key infrastructure
(PKI) which is simple and efficient. PKI is devel-
oped in order to map users’ public keys to real life
identities such as names, email addresses, etc. using
certifying authority (CA). For example, CA may link
public keys of users with real life identities using dig-
ital certificates. This linking procedure makes PKI in-
efficient and complicated. IBC provides a solution by
eliminating the requirement of digital certificates. In
1984, the concept of IBC was introduced by (Shamir,
1984) where one can directly derive user’s public key
from its identity. In IBC, a trusted private key gen-
erator (PKG) utilizes a msk to derive users’ secret
keys and issues them to the corresponding users. Note
that only the PKG has the knowledge of the msk. In
the field of IBC, identity based signature (IBS) plays
an important role for its widespread use in real life
scenarios. For instance, in a company there are sev-
eral departments and each department is having an au-
thority to sign on behalf of the company in the docu-
ments related to that department only. One may use
IBS to deal with this instance. In IBS, each user gets
a signing key corresponding to his/her identity from
a trusted authority via a confidential channel so that
signed documents can be verified using the identity of
the user. In the literature, there are several works on
IBS. However, most of them are cryptosytems based
on “number theoretic problem” (Rivest et al., 1978;
Kravitz, 1993). Due to (Shor, 1999), these are vulner-
able to quantum computer attacks. Consequently, re-
searchers are looking for post-quantum IBS that may
resist quantum computer attacks.
Related Works on IBS. The notion of IBS was
proposed by (Shamir, 1984) for reducing the com-
plexity of managing the PKI. After its introduction
many variants of IBS with different security notions
have been proposed (Barreto et al., 2005; Choon
and Cheon, 2003; Debiao et al., 2011). These are
all vulnerable to quantum attacks. To withstand
against quantum attacks, various IBS (Xinyin, 2015;
Ducas et al., 2014; Hung et al., 2017; Xie et al.,
2020) schemes have been presented depending on the
hard problems on lattices such as Gap-SVP and SIS
problems.
In resisting quantum attacks, MPKC is another
widely known post quantum variant where we rely
on the hardness of MQ problem (Huang et al., 2012).
The first IBS scheme in the area of multivariate cryp-
tography, named IBUOV, relied on the UOV scheme
of (Kipnis et al., 1999) was constructed in (Shen
et al., 2013). They showed the forward security of
the IBUOV depending on the security of the underly-
ing UOV. However, the IBUOV does not attain EUF-
CMA security as the underlying UOV protocol does
not provide such security guarantee. Subsequently,
(Luyen et al., 2019) built an IBS, which is EUF-CMA
secure and is called IBS-Rainbow. Recently, a gen-
eral construction of multivariate IBS was proposed by
(Chen et al., 2019). Their scheme is compatible with
any MPKC.
Our Contribution. MPKC attracts considerable
attention to the NIST PQC standardization (Alagic
et al., 2020) because of its high speed computation
and decent computational resource requisite making
it suitable for resource constrained devices like
Radio Frequency Identifications (RFIDs) or smart
cards. Moreover, most of the MPKC schemes in
the literature claim their security either theoreti-
cally or experimentally and parameters are selected
accordingly. This work concentrates on designing
a secure and efficient multivariate IBS scheme
with a concrete security analysis in the existing
security models instead of using heuristic arguments.
Integrating a specialized version of non-interactive
zero-knowledge proofs of knowledge, called the
signature of knowledge, we develop an identity-based
multivariate signature scheme, namely MV-IBS.
The proposed scheme is existentially unforgeable
against chosen message and chosen identity attack
(EUF-CMA) secure in the ROM under the difficulty
of solving isomorphism of polynomials (IP) problem.
At a high level, the proposed IBS involves four
algorithms Setup,Extract,Sign,Verify. A PKG runs
Setup on input 1
κ
to generate the public parameters
params and the master secret key msk. The algorithm
Extract is extracted by the PKG for generating user’s
secret key usk
id
for the user with identity id ∈ {0,1}
∗
.
The user holding the secret key usk
id
, invokes the
algorithm Sign to generate a signature µ on a message
u. Finally, the algorithm Verify is run by a verifier
on input (params,u, id, µ) to check the validity of the
message-signature pair (u,µ). Our scheme is storage
efficient compared to the existing schemes (Chen
et al., 2019; Shen et al., 2013).
We have proved the security of our IBS following
an existing security framework. More preciously, we
have the following theorem.
Theorem 1.1. (Informal) Our multivariate IBS
scheme MV-IBS = (Setup,Extract,Sign, Verify) is
SECRYPT 2021 - 18th International Conference on Security and Cryptography
596

EUF-CMA secure under the hardness of IP problem
in random oracle model.
We summarize bellow our contributions in this paper
– The main technical difference of our approach from
the existing approaches (Chen et al., 2019; Luyen
et al., 2019; Shen et al., 2013) of designing mul-
tivariate IBS is that the signature of knowledge is
the underlying primary primitive for our construc-
tion. The multivariate IBS of (Shen et al., 2013)
uses UOV whereas that of (Luyen et al., 2019) uses
Rainbow together with UOV. The general construc-
tion of (Chen et al., 2019) is compatible for any
MPKC.
– Our scheme is provable secure unlike most of the
existing MPKC schemes whose security are argued
theoretically or experimentally and parameters are
selected accordingly. More preciously, we achieve
EUF-CMA security under the hardness of the IP
problem which is known to be a problem harder
than the Graph Isomorphism problem (which is NP
hard). The multivariate IBS of (Shen et al., 2013)
does not exhibit EUF-CMA security and has large
key sizes. Although the multivariate IBS of (Luyen
et al., 2019) achieves EUF-CMA security similar
to our MV-IBS, it has formidable huge key sizes.
The work of (Chen et al., 2019) also features sig-
nificantly large key sizes. In contrast, our approach
helps to reduce the key sizes considerably although
the signature size in our MV-IBS remains large.
– The multivariate IBS schemes (Chen et al., 2019;
Luyen et al., 2019; Shen et al., 2013) derive their
security from the hardness of MQ problem whereas
our scheme relies on the hardness of IP problem.
Organization. The rest of the work is structured in
the following way. Section 2 gives the necessary pre-
liminaries. The proposed IBS is described in Section
3 followed by its security in Section 4 and efficiency
analysis in Section 5. Finally, the work is concluded
in Section 6 with possible future direction of work.
2 PRELIMINARIES
Notations. In this work, “K stands for Galois
field GF(p) of prime order p” and “K
n
= {x =
(x
1
,x
2
,. .., x
n
)|x
i
∈ K for i = 1,2,. .., n}”. Denote
“ f ◦ g as composition of two functions f and g”. By
“A||B, we mean concatenation of A and B”. For a
positive integer q, define “the set [1, 2,.. . ,q] as [q]”.
By “[[B]], we denote the bit that is 1 if the boolean
statement B is true and 0 otherwise”. We say that
“ f : N → R is a negligible function of n if it is O(n
−c
)
for all c > 0” and we use “negl(n) to denote a negli-
gible function of n”.
Definition 2.1. Isomorphism of Polynomi-
als (IP): Let A : K
n
→ K
m
and B : K
n
→ K
m
be two sets of “m quadratic multivariate
polynomials in n variables x
1
,x
2
,. .., x
n
”:
A = (A
1
(x
1
,x
2
,. .., x
n
),A
2
(x
1
,x
2
,. .., x
n
),. ..,
A
m
(x
1
,x
2
,. .., x
n
))
B = (B
1
(x
1
,x
2
,. .., x
n
),B
2
(x
1
,x
2
,. .., x
n
),. ..,
B
m
(x
1
,x
2
,. .., x
n
)) where
A
i
(x
1
,x
2
,. .., x
n
) =
n
∑
j=1
n
∑
k=1
α
i
jk
x
j
x
k
+
n
∑
j=1
β
i
j
x
j
+ γ
i
B
i
(x
1
,x
2
,. .., x
n
) =
n
∑
j=1
n
∑
k=1
ˆ
α
i
jk
x
j
x
k
+
n
∑
j=1
ˆ
β
i
j
x
j
+
ˆ
γ
i
for i = 1, 2 .. .,n and α
i
jk
, β
i
j
, γ
i
,
ˆ
α
i
jk
,
ˆ
β
i
j
,
ˆ
γ
i
, x
i
∈ K =
GF(p). If we can find a pair of invertible affine trans-
formations S : K
m
→ K
m
and T : K
n
→ K
n
satisfying
B = S ◦ A ◦ T , then we say that A and B are isomor-
phic and (S, T ) is an isomorphism from A to B. Given
isomorphic sets A and B of m quadratic multivariate
polynomials in n variables over K, the IP problem
asks to find an isomorphism (S,T ) from A to B.
The IP problem is NP-hard (Yang et al., 2011).
Signature of Knowledge from IP (Yang et al.,
2011). SoK is a specialized version of non-
interactive zero-knowledge proof (NIZK). In a
signature of knowledge (SoK), a signer (SG) wishes
to assure a verifier (VK) about the fact that he is
having secret signing key and the verifier intends to
verify the correctness of the claim. The SG is able
to prove the VK that the claim is correct without
disclosing the secret. We define in Figure 1 the
signature of knowledge SoK = (Setup, KeyGen,
SigKnowledge, VerKnowledge) of (Yang et al., 2011)
is a signature scheme that relies on the isomorphism
of polynomials (IP) problem.
• Correctness: The scheme SoK = (Setup,Key
Gen,SigKnowledge,VerKnowledge) described in
Figure 1 satisfies the following correctness re-
quirement: For all κ, all pp ← Setup(1
κ
), all
(pk,sk) ← KeyGen(pp), all V ← SigKnowledge
(pp,u, sk,pk), all message u ∈ {0, 1}
∗
, it holds
that VerKnowledge(pp,u,V, pk) = 1. Note that
for all i ∈ [q], C
i
= S
i
◦ A ◦ T
i
= S
0
i
◦ A ◦ T
0
i
= C
i
when H[i] = 0 and C
i
= S
i
◦ B ◦ T
i
= S
0
i
◦ S
−1
◦ B ◦
T
−1
◦ T
0
i
= S
0
i
◦ A ◦ T
0
i
= C
i
when H[i] = 1. Conse-
quently, H (u kC
1
k · · · kC
q
) = H
0
= H and hence
VerKnowledge(pp, u,V,pk) = 1.
Storage Friendly Provably Secure Multivariate Identity-Based Signature from Isomorphism of Polynomials Problem
597

pp ← SoK.Setup(1
ˇ
) A trusted authority runs this algorithm on
input 1
ˇ
and generates the public parameter pp = (H , K, m,n)
by choosing a cryptographically secure collision-resistant hash
function H :{0, 1}
∗
→ {0,1}
q
where q,m,n are positive integers
and K = GF(p) for some prime p.
(pk,sk) ← SoK.KeyGen(pp). On input the public parameter pp =
(H ,K, m,n), a signer chooses a pair (A,B) of isomorphic sets
of m quadratic multivariate polynomials in n variables with the
isomorphism (S,T ) over K satisfying B = S ◦ A ◦ T as defined in
Definition 2.1. Here A : K
n
→ K
m
, B : K
n
→ K
m
and S : K
m
→
K
m
, T : K
n
→ K
n
are two invertible affine transformation. It then
sets the public key pk = (A, B) and the secret key sk = (S,T ).
V ← SoK.SigKnowledge(pp,u, sk,pk). The signer, with the
knowledge of the isomorphism sk = (S,T ) between A and B
where pk = (A,B), performs the following steps to generate a
signature of knowledge for a message u ∈ {0, 1}
∗
:
(i) Chooses randomly q invertible affine transformation pairs
(S
0
1
,T
0
1
),(S
0
2
,T
0
2
),. .. ,(S
0
q
,T
0
q
) where T
0
i
: K
n
→ K
n
, S
0
i
:
K
m
→ K
m
for i ∈ [q].
(ii) Computes C
i
= S
0
i
◦ A ◦ T
0
i
for i ∈ [q] (i.e. C
i
and A are
isomorphic with the isomorphism (S
0
1
,T
0
i
)).
(iii) Evaluates H (u k C
1
k · ·· k C
q
) = H = H[q]H[q −
1]· ·· H[1] ∈ {0,1}
q
where H[i] ∈ {0,1}.
(iv) For i ∈ [q], sets (S
i
,T
i
) =
(S
0
i
,T
0
i
) if H[i] = 0
(S
0
i
◦ S
−1
,T
−1
◦ T
0
i
) if H[i] = 1.
(v) Outputs V = {H,(S
1
,T
1
),. .. ,(S
q
,T
q
)} as signature of
knowledge.
0/1 ← SoK.VerKnowledge(pp,u,V, pk). Given the public param-
eter pp, message u ∈ {0, 1}
∗
, public key pk = (A,B) and sig-
nature of knowledge V = {H,(S
1
,T
1
),. .. ,(S
q
,T
q
)}, the verifier
does the following:
(i) Parse H ∈ {0, 1}
q
as H = H[q]H[q−1] ·· · H[1] where H[i] ∈
{0,1}.
(ii) For i ∈ [q], evaluates C
i
=
S
i
◦ A ◦ T
i
if H[i] = 0
S
i
◦ B ◦ T
i
if H[i] = 1
(iii) Computes H (u kC
1
k ·· · kC
q
) = H
0
.
(iv) Outputs 1 if H = H
0
; otherwise 0.
Figure 1: Signature of Knowledge from IP.
2.1 Identity Based Signature (Paterson
and Schuldt, 2006)
We recall the definition of (IBS) which is a tuple of
algorithms IBS = (Setup, Extract, Sign, Verify) satis-
fying the following requirements:
(params , msk) ← IBS.Setup(1
κ
). A trusted PKG
runs this algorithm on input 1
κ
and generates pub-
lic parameter params and a master secret key msk.
usk
id
← IBS.Extract(params,id,msk). The PKG
generates user secret key usk
id
for the user with
identity id ∈ {0,1}
∗
using the master secret key
msk and public parameter params.
µ ← IBS.Sign(params,u,usk
id
). Given a message
input u, the user with public parameter params
and secret key usk
id
runs this algorithm and output
a signature µ on the message u.
0/1 ← IBS.Verify(params,u, id,µ). On input
params, message u, user identity id and a signa-
ture µ, a verifier returns 1 if the signature is valid,
0 otherwise.
• Correctness: The aforementioned IBS must at-
taining the following correctness requirement:
For all κ, all (params,msk) ← Setup(1
κ
), all
usk
id
← Extract(params,id,msk), all message u,
it holds that Verify(params,id,u, Sign(params,u,
usk
id
)) = 1.
• Security: We define the EUF-CMA advan-
tage function of a forger F against IBS as
ADV
EUF-CMA
IBS
(F ) = Pr[EXP
EUF-CMA
IBS,F
(1
κ
) = 1]
where experiment EXP
EUF-CMA
IBS,F
(1
κ
) is described
below. An IBS scheme is said to satisfy
EUF-CMA security if, for all PPT forger F ,
there exists a negligible function negl such that
ADV
EUF-CMA
IBS
(F ) = Pr[EXP
EUF-CMA
IBS,F
(1
κ
) = 1] <
negl(κ).
Definition 2.2. EUF-CMA security: An IBS
scheme is said to satisfy the existential un-
forgeability against chosen message and chosen
identity attack (EUF-CMA) security if, for all
probabilistic polynomial time (PPT) forger F ,
there exists a negligible function negl such that
ADV
EUF-CMA
IBS
(F ) = Pr[EXP
EUF-CMA
IBS,F
(1
κ
) = 1] <
negl(κ).
3 OUR PROTOCOL MV-IBS
We describe below the construction of our
proposed multivariate IBS scheme MV-
IBS = (Setup,Extract,Sign, Verify) that uses
the signature of knowledge SoK = (Setup, KeyGen,
SigKnowledge, VerKnowledge) described in Sec-
tion 2 which is based on the IP problem.
(params,msk) ← MV -IBS.Setup(1
κ
). The private
key generator PKG does the following:
(i) Runs SoK.Setup(1
κ
) (see Figure 1) to gen-
erate pp = (H , K,m,n) by choosing a cryp-
tographically secure collision-resistant hash
function H : {0,1}
∗
→ {0,1}
q
where q,m,n are
positive integers and K = GF(p) for some
prime p.
(ii) Generates (pk
R
,sk
R
) ← SoK.KeyGen(pp)
(see Figure 1) where sk
R
= (L
1
,L
2
) and pk
R
=
SECRYPT 2021 - 18th International Conference on Security and Cryptography
598
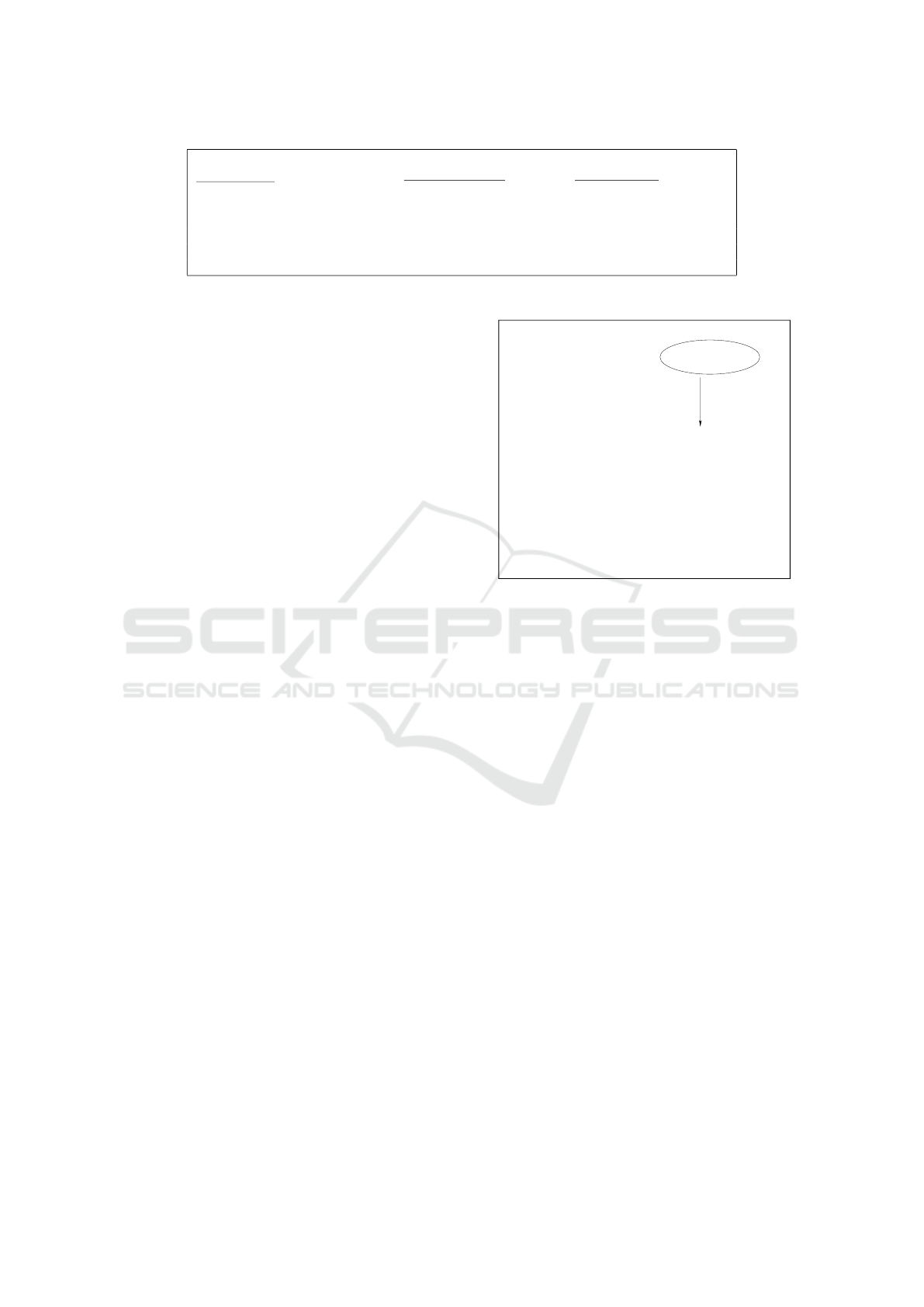
EXP
EUF-CMA
IBS,F
(1
κ
) Oracle EXTRACT(id) Oracle SIGN(id,u)
(params,msk) ← Setup(1
κ
) usk
id
← Extract(params,id,msk) SList = SList ∪ {id, u}
(id
∗
,u
∗
,µ
∗
) ← F
EXTRACT,SIGN
(pp) SList = SList ∪ {id} usk
id
← Extract(params,id,msk)
return [[(id
∗
,u
∗
) 6∈ SList]] ∧ [[id
∗
6∈ XList]] return usk
id
XList = XList ∪ {id}
∧ [[Verify(params,id
∗
,u
∗
,µ
∗
) = 1]] µ ← Sign(params,u, usk
id
)
return µ
Figure 2: EUF-CMA security game with EXTRACT and SIGN oracle.
(P,Q). Here (P,Q) is a pair of isomorphic sets
of m quadratic multivariate polynomials in n
variables with the isomorphism (L
1
,L
2
) over
the fields K satisfying Q = L
1
◦P ◦L
2
as in Def-
inition 2.1 and L
1
: K
m
→ K
m
, L
2
: K
n
→ K
n
are
two invertible affine transformations, P : K
n
→
K
m
and Q : K
n
→ K
m
.
(iii) Picks k ∈ {0,1}
q
at random, a cryptograph-
ically secure collision-resistant hash function
b
H : {0, 1}
∗
→ K
d
and sets MAC
k
(y) =
b
H (k||y)
for y ∈ {0,1}
∗
(iv) Selects invertible affine map X as follows
where z = (z
1
,z
2
,. .., z
d
) ∈ K
d
:
X = X (x
1
,x
2
,.. .,x
m
;z)
= (X
1
(x
1
,x
2
,.. .,x
m
;z),. .., X
m
(x
1
,x
2
,.. .,x
m
;z))
with
X
i
(x
1
,x
2
.. .,x
m
;z) =
m
∑
j=1
X
i, j
(z)x
j
+ X
i,0
(z)
for i ∈ [m] where each X
i, j
(z) is a linear function
of z = (z
1
,z
2
,. .., z
d
) ∈ K
d
and x
1
,x
2
,. .., x
m
∈
K. Thus X is a function of m + d variables
x
1
,x
2
,. .., x
m
,z
1
,z
2
,. .., z
d
over K.
(v) Chooses invertible affine map Y as follows
where z = (z
1
,z
2
,. .., z
d
) ∈ K
d
:
Y = Y (x
1
,x
2
... ,x
n
;z)
= (Y
1
(x
1
,x
2
,.. .,x
n
;z),. ..,Y
n
(x
1
,x
2
,.. .,x
n
;z))
with
Y
i
(x
1
,x
2
,. .., x
n
;z) =
n
∑
j=1
Y
i, j
(z)x
j
+Y
i,0
(z)
for i ∈ [n] where each Y
i, j
(z) is a linear function
of z = (z
1
,z
2
,. .., z
d
) ∈ K
d
and x
1
,x
2
,. .., x
n
∈
K. Thus Y is a function of n + d variables
x
1
,x
2
,. .., x
n
,z
2
,z
2
,. .., z
d
over K.
(vi) Sets public parameter as params = (pp =
(H , K,m,n), pk
R
= (P,Q),
b
H ) and master se-
cret key as msk = (sk
R
= (L
1
,L
2
),k,X,Y )(see
Figure 3).
PKG
publishes params
keeps msk as secret
pp = (H , K,m, n)
pk
R
= (P,Q), sk
R
= (L
1
,L
2
)
Q = L
1
◦ P ◦ L
2
, X, Y , k,
b
H
msk = (sk
R
= (L
1
,L
2
),k,X,Y )
params = (pp = (H ,K, m, n),pk
R
= (P,Q),
b
H )
Figure 3: The algorithm MV-IBS.Setup(1
ˇ
).
usk
id
← MV-IBS.Extract(params,id, msk). Given
the identity id ∈ {0,1}
∗
of a user
U
id
, the PKG works as follows us-
ing msk = (sk
R
= (L
1
,L
2
),k,X,Y ) and
params = (pp = (H ,K,m, n),pk
R
= (P,Q),
b
H ):
(i) Computes
seed
id
= MAC
k
(id) =
b
H (k||id) ∈ K
d
sk
id
= (X
id
,Y
id
)
where
X
id
= X (x
1
,x
2
,. .., x
m
;seed
id
)
= (X
1
(x
1
,. .., x
m
;seed
id
),. ..,
X
m
(x
1
,. .., x
m
;seed
id
))
with
X
i
(x
1
,x
2
,. .., x
m
;seed
id
)
=
m
∑
j=1
X
i, j
(seed
id
)x
j
+ X
i,0
(seed
id
) for i ∈ [m]
and
Y
id
= Y (x
1
,x
2
,. .., x
n
;seed
id
) =
(Y
1
(x
1
,x
2
,. .., x
n
;seed
id
),. ..,Y
n
(x
1
,x
2
,. .., x
n
;
seed
id
)) with
Y
i
(x
1
,x
2
,. .., x
n
;z = seed
id
) =
n
∑
j=1
Y
i, j
(seed
id
)x
j
+Y
i,0
(seed
id
) for i ∈ [n].
Storage Friendly Provably Secure Multivariate Identity-Based Signature from Isomorphism of Polynomials Problem
599
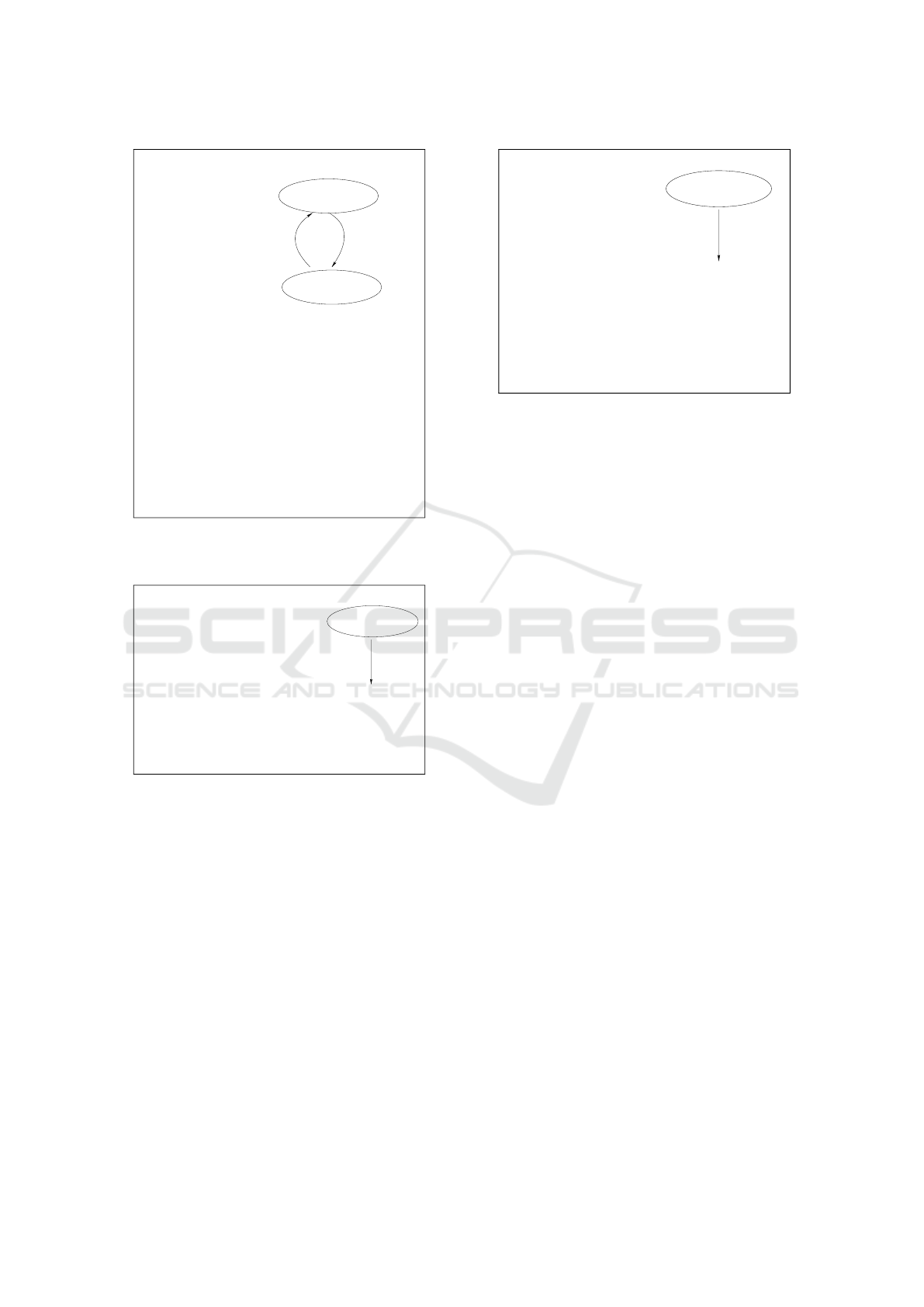
usk
id
User U
communication through
id
msk=(sk , k, X, Y)
params=(pp, pk )
R PKG
id
R
a secure channel
seed
id
=
b
H (k||id)
X
id
= X(x
1
,x
2
,. .. ,x
m
;seed
id
)
Y
id
= Y (x
1
,x
2
,. .. ,x
n
;seed
id
)
sk
id
= (X
id
,Y
id
)
B
id
= X
id
◦ Q ◦Y
id
V
id
← SoK.SigKnowledge(pp,id||B
id
,sk
R
,pk
R
)
pp = (H , K,m, n),pk
R
= (P,Q),sk
R
= (L
1
,L
2
)
usk
id
= (sk
id
= (X
id
,Y
id
),B
id
,V
id
)
Figure 4: The algorithm MV-IBS.Extract
(params,id,msk).
usk = (sk , B , V )
params=(pp, pk )
message u
signature
id
R
id
µ
Signer U
id id id
on message u
V
u
← SoK.SigKnowledge(pp,u,sk
id
,pk
id
)
µ = (V
u
,B
id
,V
id
)
Figure 5: The algorithm MV-IBS.Sign (params,u,usk
id
).
Here X ,Y are obtained from msk where
X is a function of m + d variables
x
1
,x
2
,. .., x
m
,z
1
,z
2
,. .., z
d
and Y is a function
of n + d variables x
1
,x
2
,. .., x
n
,z
1
,z
2
,. .., z
d
.
The PKG calculates X
id
and Y
id
by
evaluating X and Y respectively at
z = seed
id
= MAC
k
(id) =
b
H (k||id) ∈ K
d
extracting k from msk and
b
H from params.
(ii) Evaluates B
id
= X
id
◦ Q ◦Y
id
where Q is ob-
tained from params and sets sk
id
= (X
id
,Y
id
).
Note that B
id
and Q are isomorphic sets of mul-
tivariate quadratic polynomials with the iso-
morphism (X
id
,Y
id
).
(iii) Generates V
id
← SoK.SigKnowledge(pp =
(H , K,m,n), id||B
id
,sk
R
= (L
1
,L
2
),pk
R
=
(P,Q))
params=(pp, pk )
R
message u
identity id
Verifier
b =1 and b =1
accepts if both
signature µ = (V , B , V )
u idid
1 2
b
1
← SoK.VerKnowledge(pp, id||B
id
,V
id
,pk
R
= (P,Q))
b
2
← SoK.VerKnowledge(pp, u,V
u
,pk
id
) by setting
pk
id
= (B
id
,Q)
Verifier returns 1 iff b
1
= 1 and b
2
= 1
Figure 6: The algorithm MV-IBS.Verify (params,u, id,µ).
(iv) Sends usk
id
= (sk
id
= (X
id
,Y
id
),B
id
,V
id
) to
the user U
id
(see Figure 4).
µ ← MV-IBS.Sign(params,u,usk
id
). Given a
message u ∈ {0,1}
∗
, the user U
id
with its
secret key usk
id
= (sk
id
= (X
id
,Y
id
),B
id
,V
id
)
computes the signature of knowledge V
u
←
SoK.SigKnowledge(pp,u, sk
id
,pk
id
) (see Figure
1) using (B
id
,Q) as pk
id
which is a pair of iso-
morphic sets of m quadratic multivariate polyno-
mials in n variables with the isomorphism sk
id
=
(X
id
,Y
id
) over K satisfying B
id
= X
id
◦ Q ◦ Y
id
.
Here pp and Q are extracted from params =
(pp = (H ,K,m, n),pk
R
= (P,Q),
b
H ). The user
U
id
outputs the signature of the message u as
µ = (V
u
,B
id
,V
id
) (see Figure 5).
0/1 ← MV -IBS.Verify(params,u,id, µ). Given a
message u ∈ {0,1}
∗
, signature µ =
(V
u
,B
id
,V
id
), public parameter params =
(pp = (H ,K,m,n), pk
R
= (P,Q),
b
H ) and
an identity id, the verifier first runs
SoK.VerKnowledge(pp, id||B
id
,V
id
,pk
R
= (P,Q)).
If the output is 1 then the verifier runs
SoK.VerKnowledge(pp, u,V
u
,pk
id
) (see Fig-
ure 1) by setting pk
id
= (B
id
,Q) and checks
whether the output is 1. If it is so then the
verifier accepts the message signature pair
and outputs 1. On the other hand, if out-
put of SoK.VerKnowledge is 0 for either of
the inputs (pp,id||B
id
,V
id
,pk
R
= (P,Q)) and
(pp,u,V
u
,pk
id
= (B
id
,Q)) then the verifier rejects
the message-signature pair and outputs 0 (see
Figure 6).
• Correctness: The correctness of our scheme
MV-IBS follows from the following argument:
Let (params, msk) ← MV-IBS.Setup(1
κ
),
usk
id
← MV-IBS.Extract(params,id, msk),
SECRYPT 2021 - 18th International Conference on Security and Cryptography
600
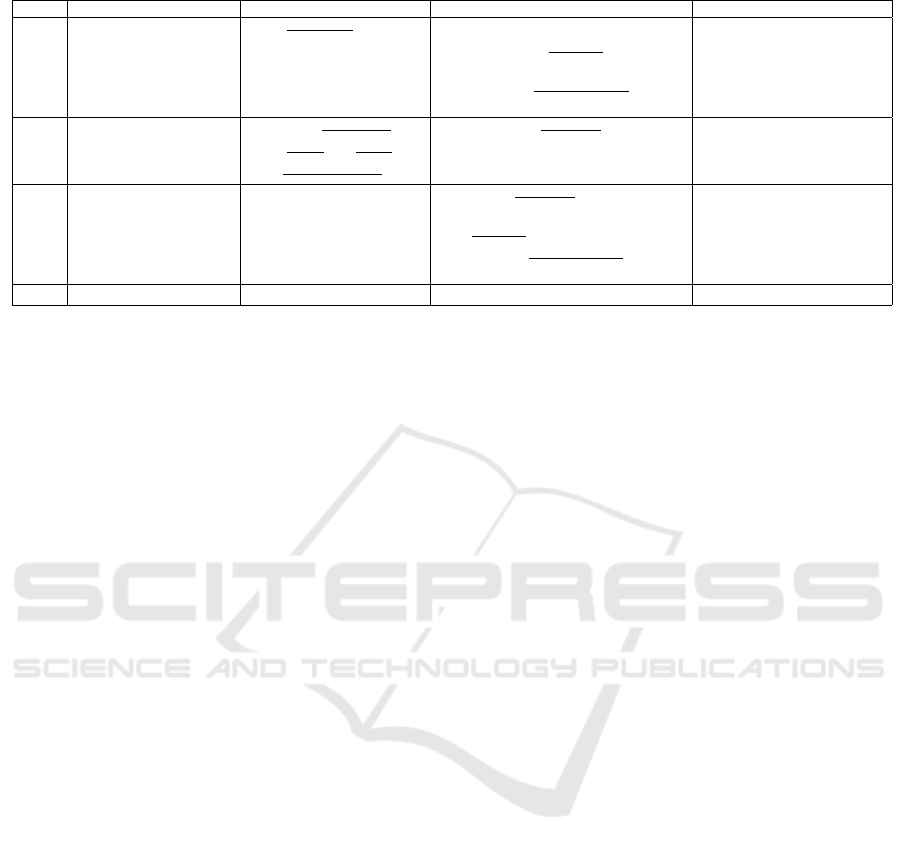
Table 1: Comparison summary of multivariate IBS.
Our MV-IBS IBS of (Chen et al., 2019) IBS-Rainbow of (Luyen et al., 2019) IBUOV of (Shen et al., 2013)
|msk| n
2
+ m
2
+ m + n m · ((
n(n+1)(n+2)
2
) · d) + m
2
m · (m + 1) + n · (n + 1)+ n
2
+ m
n+2
2
+n
2
+ m · (m + 1) · d o
1
· (
(v
1
)(v
1
+1)
2
+n · (n + 1) · d +v
1
· o
1
+ v
1
+ o
1
+ 1)
+o
2
· (
(v
1
+o
1
)(v
1
+o
1
+1)
2
+(v
1
+ o
1
) · o
2
+ n + 1)
|pk
R
| m ·
n+2
2
m · (n · (
d(d+1)(d+2)
3!
) m · (
(n+1)(n+2)
2
) m
n+2
2
+(
d(d+1)
2
) + (
n(n+1)
2
)·
(
d(d+1)(d+2)(d+3)
4!
))
|usk| n
2
+ m
2
+ m + n n
2
+ m
2
+ m + n + m ·
n+2
2
m · (
(n+1)(n+2)
2
) + n + 2l n
2
+ n + 2m
n+2
2
+m · (m + 1) + n · (n + 1)+
o
1
· (
(v
1
)(v
1
+1)
2
+ v
1
· o
1
+ v
1
+ o
1
+ 1)+
o
2
· (
(v
1
+o
1
)(v
1
+o
1
+1)
2
+(v
1
+ o
1
) · o
2
+ n + 1)
|sig| 2(n
2
+ m
2
)q + m
n+2
2
+δ m 2m + m
n+2
2
+ η 2n + m
n+2
2
n = v
1
+ o
1
+ o
2
, m = o
1
+ o
2
, δ = 2q/log p, η = l/log p, q and l are security parameters, d indicates the size of user’s ID, v
1
is the number of vinegar variables
and o = o
1
+ o
2
is the number of oil variables in a 2-layer UOV scheme.
µ ← MV -IBS.Sign(params,u, usk
id
) where
params = (pp = (H ,K,m, n),pk
R
= (P,Q),
b
H ),
msk = (sk
R
= (L
1
,L
2
),k,X,Y ),
usk
id
= (sk
id
= (X
id
,Y
id
),B
id
,V
id
)),
µ = (V
u
,B
id
,V
id
)).
Note that pk
R
= (P,Q) is a pair of isomor-
phic sets with isomorphism sk
R
= (L
1
,L
2
)
as Q = L
1
◦ P ◦ L
2
. Consequently, if
V
id
← SoK.SigKnowledge(pp, id||B
id
,sk
R
,pk
R
)
then by the correctness of SoK, we have
SoK.VerKnowledge(pp, id||B
id
,V
id
,pk
R
) = 1.
Also pk
id
= (B
id
,Q) is a pair of isomor-
phic sets with isomorphism sk
id
= (X
id
,Y
id
)
as B
id
= X
id
◦ Q ◦ Y
id
. Hence, if V
u
←
SoK.SigKnowledge(pp,u, sk
id
,pk
id
= (B
id
,Q))
then SoK.VerKnowledge(pp, u,V
u
,pk
id
=
(B
id
,Q)) = 1 by the correctness of SoK. Conse-
quently, MV-IBS.Verify(params,u,id, µ) = 1.
4 SECURITY ANALYSIS
Theorem 4.1. If the IP problem is hard then the MV-
IBS described above is EUF-CMA secure as defined
in Definition 2.2 when the hash function H is de-
signed as a random oracle.
Proof: Due to page limit, the full proof will be ap-
peared in the full version of this paper.
5 EFFICIENCY ANALYSIS
In the literature of MPKC, several practical encryp-
tion and signature schemes can be found like MI
(Matsumoto and Imai, 1988), HFE (Patarin, 1996),
UOV (Kipnis et al., 1999), Rainbow (Ding and
Schmidt, 2005), etc. Although, there are several IBS
schemes (Zhang et al., 2019; R
¨
uckert, 2010; Xie
et al., 2020; Wang et al., 2017) based on other can-
didates of PQC, there are only a few multivariate IBS
schemes. (Shen et al., 2013) designed the first IBS,
namely IBUOV, employing standard UOV (Kipnis
et al., 1999) as a building block. Later, (Luyen et al.,
2019) used the technique of (Sakumoto et al., 2011)
to develop IBS-Rainbow a multivariate IBS by mod-
ifying UOV and Rainbow (Ding and Schmidt, 2005).
Recently, (Chen et al., 2019) proposed a general con-
struction of multivariate IBS which is compatible with
any MPKC. On the other hand, we use signature of
knowledge as the underlying primitive in our MV-IBS
design.
We refer Table 1 for a comparison summary of our
IBS with the existing multivariate IBS schemes (Chen
et al., 2019; Luyen et al., 2019; Shen et al., 2013).
All the schemes use finite field K = GF(p) and the
sizes are compared by counting the number of field
elements. As explain in Table 1 our IBS scheme has
smaller master secret key size (|msk|), master pub-
lic key size (|pk
R
|) and user’s private key size (|usk|).
However, the size of the signature remains large. The
IBUOV of (Shen et al., 2013) is not EUF-CMA secure
in contrast to IBUOV our MV-IBS.
6 CONCLUSION
This paper presented a provably secure multivariate
identity based signature (IBS) utilizing the signature
of knowledge as the underlying primitive which is a
variant of non-interactive zero knowledge proof. Our
proposed IBS performs significantly better over the
Storage Friendly Provably Secure Multivariate Identity-Based Signature from Isomorphism of Polynomials Problem
601

existing MPKC based IBS in terms of master secret
key size, master public key size and user secret key
size with a trade-off in signature size. Moreover,
our scheme does not claim it security theoretically
or experimentally as opposed to most of the MPKC
schemes in the literature. Rather, it achieves EUF-
CMA security in the random oracle model under the
hardness of the IP problem which is known to be
harder than Graph Isomorphism problem. Extending
our work to achieve security in the standard model
and reducing the signature size while retaining simi-
lar key sizes is an interesting open problem and our
future direction of work.
REFERENCES
Alagic, G., Alperin-Sheriff, J., Apon, D., Cooper, D., Dang,
Q., Kelsey, J., Liu, Y.-K., Miller, C., Moody, D., Per-
alta, R., et al. (2020). Status report on the second
round of the nist post-quantum cryptography stan-
dardization process. US Department of Commerce,
NIST.
Barreto, P. S., Libert, B., McCullagh, N., and Quisquater,
J.-J. (2005). Efficient and provably-secure identity-
based signatures and signcryption from bilinear maps.
In International conference on the theory and appli-
cation of cryptology and information security, pages
515–532. Springer.
Chen, J., Ling, J., Ning, J., and Ding, J. (2019). Identity-
based signature schemes for multivariate public key
cryptosystems. The Computer Journal, 62(8):1132–
1147.
Choon, J. C. and Cheon, J. H. (2003). An identity-based
signature from gap diffie-hellman groups. In Inter-
national workshop on public key cryptography, pages
18–30. Springer.
Debiao, H., Jianhua, C., and Jin, H. (2011). An id-
based proxy signature schemes without bilinear pair-
ings. Annals of telecommunications-annales des
t
´
el
´
ecommunications, 66(11-12):657–662.
Ding, J. and Schmidt, D. (2005). Rainbow, a new mul-
tivariable polynomial signature scheme. In Interna-
tional Conference on Applied Cryptography and Net-
work Security, pages 164–175. Springer.
Ducas, L., Lyubashevsky, V., and Prest, T. (2014). Efficient
identity-based encryption over ntru lattices. In Inter-
national Conference on the Theory and Application
of Cryptology and Information Security, pages 22–41.
Springer.
Huang, Y.-J., Liu, F.-H., and Yang, B.-Y. (2012). Public-
key cryptography from new multivariate quadratic as-
sumptions. In International Workshop on Public Key
Cryptography, pages 190–205. Springer.
Hung, Y.-H., Tseng, Y.-M., and Huang, S.-S. (2017). Revo-
cable id-based signature with short size over lattices.
Security and Communication Networks, 2017.
Kipnis, A., Patarin, J., and Goubin, L. (1999). Unbalanced
oil and vinegar signature schemes. In International
Conference on the Theory and Applications of Cryp-
tographic Techniques, pages 206–222. Springer.
Kravitz, D. W. (1993). Digital signature algorithm. US
Patent 5,231,668.
Luyen, L. V. et al. (2019). An improved identity-based mul-
tivariate signature scheme based on rainbow. Cryptog-
raphy, 3(1):8.
Matsumoto, T. and Imai, H. (1988). Public quadratic
polynomial-tuples for efficient signature-verification
and message-encryption. In Workshop on the The-
ory and Application of of Cryptographic Techniques,
pages 419–453. Springer.
Patarin, J. (1996). Hidden fields equations (hfe) and iso-
morphisms of polynomials (ip): Two new families
of asymmetric algorithms. In International Confer-
ence on the Theory and Applications of Cryptographic
Techniques, pages 33–48. Springer.
Patarin, J. (1997). The oil and vinegar signature scheme.
In Dagstuhl Workshop on Cryptography September,
1997.
Paterson, K. G. and Schuldt, J. C. (2006). Efficient identity-
based signatures secure in the standard model. In Aus-
tralasian Conference on Information Security and Pri-
vacy, pages 207–222. Springer.
Rivest, R. L., Shamir, A., and Adleman, L. (1978). A
method for obtaining digital signatures and public-
key cryptosystems. Communications of the ACM,
21(2):120–126.
R
¨
uckert, M. (2010). Strongly unforgeable signatures
and hierarchical identity-based signatures from lat-
tices without random oracles. In International Work-
shop on Post-Quantum Cryptography, pages 182–200.
Springer.
Sakumoto, K., Shirai, T., and Hiwatari, H. (2011). On prov-
able security of uov and hfe signature schemes against
chosen-message attack. In International Workshop on
Post-Quantum Cryptography, pages 68–82. Springer.
Shamir, A. (1984). Identity-based cryptosystems and sig-
nature schemes. In Workshop on the theory and ap-
plication of cryptographic techniques, pages 47–53.
Springer.
Shen, W., Tang, S., and Xu, L. (2013). Ibuov, a prov-
ably secure identity-based uov signature scheme. In
2013 IEEE 16th International Conference on Com-
putational Science and Engineering, pages 388–395.
IEEE.
Shor, P. W. (1999). Polynomial-time algorithms for prime
factorization and discrete logarithms on a quantum
computer. SIAM review, 41(2):303–332.
Wang, Z., Chen, X., and Wang, P. (2017). Adaptive-id se-
cure identity-based signature scheme from lattices in
the standard model. IEEE Access, 5:20791–20799.
Xie, C., Weng, J., Weng, J., and Hou, L. (2020). Scalable
revocable identity-based signature over lattices in the
standard model. Information Sciences, 518:29–38.
Xinyin, X. (2015). Adaptive secure revocable identity-
based signature scheme over lattices. Computer En-
gineering, 10:25.
Yang, G., Tang, S., and Yang, L. (2011). A novel group sig-
nature scheme based on mpkc. In International Con-
ference on Information Security Practice and Experi-
ence, pages 181–195. Springer.
Zhang, Y., Hu, Y., Gan, Y., Yin, Y., and Jia, H. (2019). Ef-
ficient fuzzy identity-based signature from lattices for
identities in a small (or large) universe. Journal of
Information Security and Applications, 47:86–93.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
602
