
Design Strategies for Mobile Ad-hoc Network to Prevent from Attack
Puneeta Singh
1
, Atma Prakash Singh
1
and Abhilasha Gupta
2
1
BBDNIIIT, AKTU University, Lucknow, India
2
Department of Computer Science, AKTU University, Lucknow, India
Keywords: LEACH Protocol, Adhoc, Clustering, Steady Phase.
Abstract: LEACH protocol is the low energy adaptive clustering hierarchy protocol consume less energy and
improved the performance of data transmission from cluster head to the base station. . In this paper
discussed about the alive nodes, data transmission. Leach protocol was the earliest protocol where try to
reduce the energy consumption of each node in every round. Achieve load balancing, energy efficient,
coverage and connectivity, scalability, robustness, data fusion, security and minimum delay. It increases the
lifespan of the network under the wireless sensor network where it reduces the energy consumption of the
network to ensure that our nodes to be created and maintained it. Compare this data with attack and without
attack if any malicious nodes come.
1 INTRODUCTION
Ad hoc network is the self-conferring, infrastructure
less (ad-hoc) network where no wired connections
between source to destination. In Networking,
actually there are so many nodes they all are linked
and communicate to each other and transfer the
information from one node to another node. In the
part of networking, we are having infrastructure
based network and infrastructure-less (ad-hoc)
network. Basically, we are having three kinds of
networks LAN (Local area network), MAN
(metropolitan area network) and WAN (Wide area
network). Local area network is that kind of network
when same kind of network will work together. In
Metropolitan area network is that kind of network
when we can communicate in the organization like
university, hospitals etc. Wide area network is the
network when we communicate with across the
world. Mobile ad-hoc network i.e. decentralized type
of network where there is no centralized network.
Ad-hoc networks is having two types i.e. Wireless
Mesh Networks (WMN), Mobile ad-hoc network
(MANET) and Wireless Sensor Network. Mobile ad
hoc network is the multi-hop wireless links where all
nodes are communicating to each other in multi-hop
manner, we also called as distributed routing. Ad-
hoc node worked on Packet-switched while cellular
network working on circuit-switching. With the help
of mobility frequency path will be break, they are
also called cooperative nodes.
2 CHARACTERISTICS OF
MANET (MOBILE AD-HOC
NETWORK)
Self-configuring: In this we configure each and
every node dynamically communicate or connected
to each other, no need of router to send the
information from one node to another node.
Configure automatically connect with some other
node without the need of any router.
Dynamic network topology: In mobile ad-hoc
network, topology created and automatically they
can find their route with the help of some routing
algorithm. So, it’s dynamic in nature. It
automatically find the path to go.
Light weight terminal: In Mobile ad-hoc network
the devices are mobile devices these are having
small capability of CPU processing, less memory
storage. Have capability to optimize the
mathematical functions themselves.
Autonomous terminal: In Manet terminal, each and
every node acts as a router or a host. Each and every
mobile terminal is an autonomous node. These
mobile nodes work as a switching function instead as
a router.
F
IG.1. depicts that all nodes are connected to each
other and sending the information from one node
the another node as a mesh topology with the help
194
Singh, P., Singh, A. and Gupta, A.
Design Strategies for Mobile Ad-hoc Network to Prevent from Attack.
DOI: 10.5220/0010566800003161
In Proceedings of the 3rd International Conference on Advanced Computing and Software Engineering (ICACSE 2021), pages 194-201
ISBN: 978-989-758-544-9
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
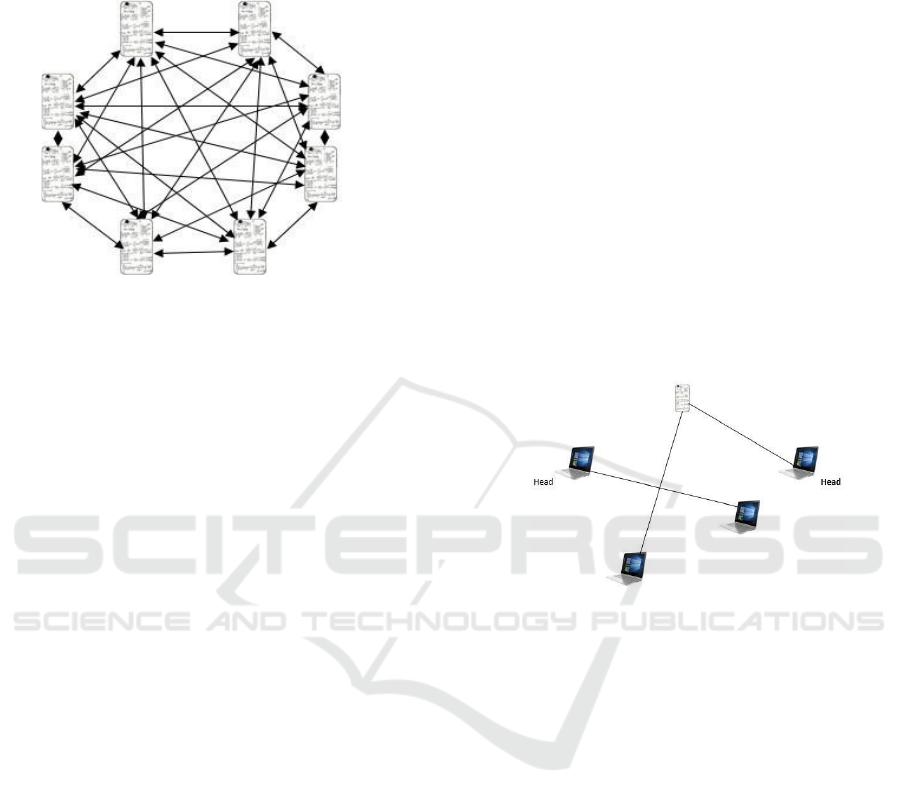
of sensors they are communicating to each other
and forwarding or sending the data packet from one
node to another node.
Figure1. Representation of Mobile Ad-hoc network
3 ARCHITECTURE MODEL OF
MANET
The model of Manet is about to preserves the
integrity of ip-addresses of every particular in this
model. Basically in wireless networking, we are
having two types Single hop and multiple hop. In
single hop we are having Infrastructure based (hub
and spoke) including 802.11, Cellular networks and
802.16 and infrastructure-less (ad-hoc) i.e. 802.11
and Bluetooth.
In multi-hop again we are having infrastructure-
based (Hybrid) multi-hop including Wireless Sensor
Networks and Wireless Mesh Networks and in
infrastructure- less (Manet) including Car-to-Car
Networks (VANETs). Basically, ad-hoc and mobile
ad-hoc network both are different ad-hoc is single
hop and mobile ad-hoc network is multi-hop. In
Multi-hop we can forward the data from one node to
another node.
3.1 Types of MANET
Vehicular Ad hoc Network (Vanet): We can
communicate with another vehicles with the help of
some equipment’s which are placed on roadside.
Intelligent vehicular ad hoc networks plays a major
role for giving me some precautions on some
collisions.
Hub-spoke Manet: All the sub-networks of Manet
are connected to each other and they can create the
geographically distributed type of network. It looks
like a network where one spoke will tell to the hub
and hub will give the answer via in which it looks
like a hybrid kind of structure.
Internet based Mobile Ad hoc network (iManets):
They can take protocols and through these protocols
they are to communicate to each other. Internet based
mobile ad hoc network can take and supports the
TCP/UDP and IP protocols. With the help of these
routing protocols we can establish the route path
distributed automatically.
Smart Phone Ad hoc network (SPANC): Smart
phone ad hoc network will be used without the help
of any cellular network we can create the peer to peer
connection. As a Bluetooth or Wi- Fi works which
comes under the Smart phone ad hoc network?
Flying Ad hoc Network (FANET): with the help of
drones, we can create or able to communicate in rural
areas. FANET is the part of ad hoc network where
their mobility was so increased as compared to
MANET or VANET.
Figure 2. Architecture view of Manet (Mobile ad-hoc
network)
FIG.2. depicts as a node that is able to communicate
without any central device and sharing the
information from one to other. It automatically or
dynamically changing the topology. They have
sensors and these sensors play one of the major role
in mobile ad hoc network. It’s has the capability of
self- configure, automatically connected with
neighbor nodes and starts communication.
3.2 Attacks Performed on MANET
Generally attacks means any unauthorized user can
disturbed the link or tries to take the original data. In
Manet, having two types of attacks.
Active attack: Any attacker or hacker or any
unauthorized user tries to hack the data or tries to
modify the data or disrupts the service. There are so
many examples of active attack like masquerade,
denial of service and replay etc. Black hole type of
attack is the example of active attack.
Design Strategies for Mobile Ad-hoc Network to Prevent from Attack
195
Passive attack: passive attack is the attack when it
monitors the data, there is no modification in their
data. Passive attack is not much as dangerous as
active attack. Third party only monitors the data it
can never change or alter the data. Traffic analysis
and traffic monitoring type of attack is the example
of passive attack.
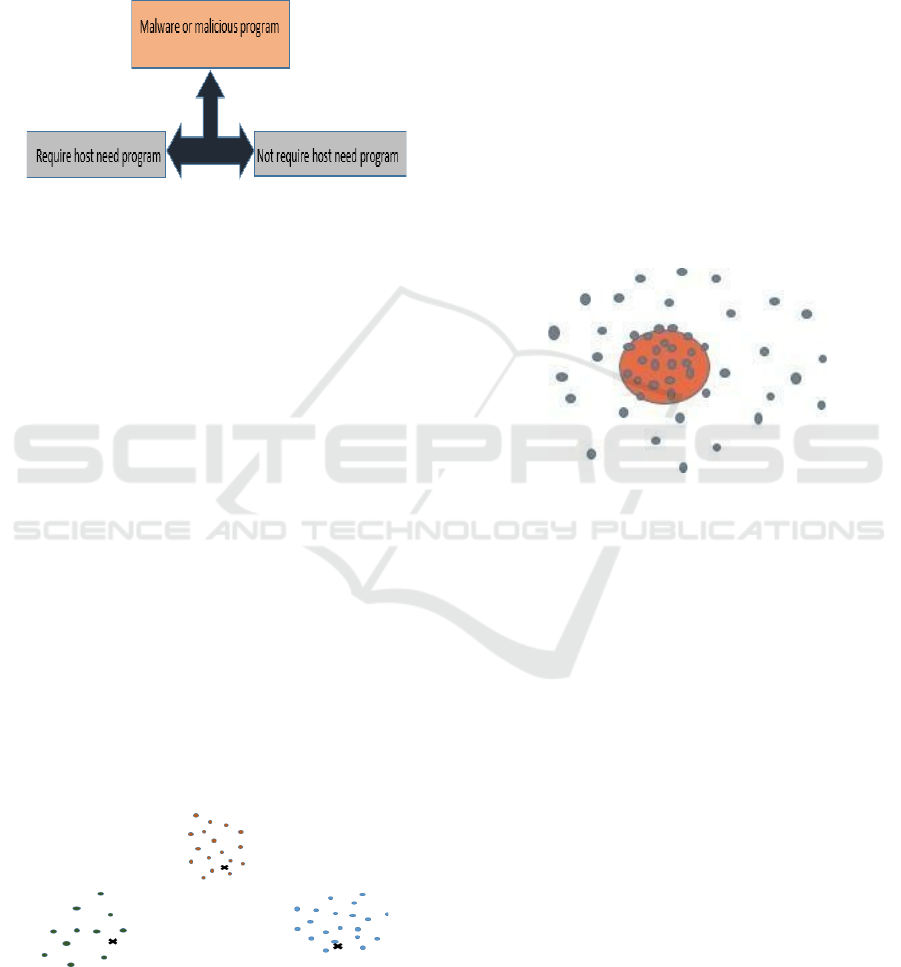
Figure 3. Representation of requirement of Malware
program
Fig.3 about the malware or malicious program wants
requirement of host need program to execute the
program.
Threshold decision making: In this phase, we see the
threshold value and fix it, after see the malicious
node we will rectify via some algorithm and that
algorithm is threshold decision making. There are
two parameters in the network: RREQ and RREP.
RREQ: When we send the packets from source to
destination then that route called as RREQ (route
request). RREP: When we are sending the data
packets from destination to source then that route
path called as RREP.
3.3 Different Clustering Algorithm
K-Means Clustering: In K-Means algorithm, we
choose a number of groups (number of nodes) and
choose accordingly distinct points or groupings.
In this we see the closest distance between the
centers of the group. This K-Means clustering is
the unsupervised learning and here also it
checks the points from the group.
Figure 4. Representation of K-Means clustering
Fig.4 Representation of k-means clustering in which
those items whose functionality was same they are
placed in one group which was named as cluster.
There are so many cluster and they are to be talked
with the help of cluster head. Steps of K-Means
clustering:
First we choose k points, we also called means
of that.
We calculates the value of coordinates of mean
those items which are nearest.
We do recursion means call many times until
we cannot achieve our goal.
3.4 Mean Shift Clustering
This clustering which was based on sliding window,
it will work on centroid based. It will see the center of
the group in the network. At every time it will check
the procedure where their density of data is high.
Figure 5: Representation of Mean shift clustering
Fig.5 tells that it sees the center of the group in the
cluster, it always sees the maximum value from the
nodes. It always calculate the mean from the cluster.
4 LITERATURE REVIEW
Prasanna, S. it tells about how any node attack the
any node in network. It also tells about the how
wormhole attack, black-hole attack, attacks the
malicious node. They all are discussing about
routing protocol i.e. routing protocols are of two
types one reactive routing protocol, the other one is
proactive protocol and the third one is the hybrid
protocol. For achieving network security we will get
three things in that: Confidentiality, availability,
authentication and integrity. The data is protected
from un authorised user. Availability means the
resources and services are to be available, DOS that
attack under the availability. Authentication means
the data is should be authenticated. Integrity means
whatever the message is being transmitted is not be
altered.
ICACSE 2021 - International Conference on Advanced Computing and Software Engineering
196

Arulkumaran, G., & Gnanamurthy, R. K. this
strategy used in military services where they want
secure the data and would be transmitting in a secure
channel. MANET is the dynamic topology and it
create the fuzzy logic concept, with the help of this
strategy we reduce the black hole attack and it
improves a speed of AODV (Ad-hoc on demand
vector) protocol.
Amru, M., Jabirullah, M., & Krishna, A. C. tells
about the improvement of those failed nodes which
are cluster head. Cluster head are to chosen when
their energy is maximum. It uses LEACH protocol
in which it tries to reduce the energy consumption or
power consumption. Sensors are very small insize,
their memory is also limited. It proposed a scheme
which is based on rank.
Kassan, S., Lorenz, P., & Gaber, J. it talks about
the wireless sensor nodes in which it works with the
help of number of nodes, software etc. Sensors
nodes are depend on limited battery but wireless
sensors nodes are having unlimited energy for the
usage of network.
Netyorks, V. S., Krishnakumar, A., & Anuratha,
V. in this paper discuss about the cluster head in the
wireless sensor network through which whatever the
method was using for choosing the cluster head, it
can change or modified the cluster head. It helps to
increase to life of the network, we choose the
highest data or value from the cluster head. Uses the
concept of Fuzzy logic (FL) from super head of
cluster.
Kundu, S., Karthikeyan, S., &Karthikeyan, A it
studies and tell that the one algorithm QBEECH and
it compare with other LEACH like Multiple
LEACH, C- LEACH etc. There are disadvantage in
these protocols. This algorithm tells that it will
increase or enhance the life of the network.
Rahmadhani, M. A., Yovita, L. V., &Mayasari,
R proposed a method of Delay tolerant network
(DTN) in which when network is traffic in nature
then those data packet which are transferring it will
be loss. Basically LEACH algorithm will be divided
into two phases set up phase and steady phase. This
method will very helpful for the use of busy network
and data will be dropped, reached successfully. This
DTN was added into the LEACH-WSN in which
data will not dropped.
Vaseer, G., Ghai, G., &Ghai, D. talks about the
novel intrusion detection system and prevention for
mobile ad hoc networks. Generallywe built a novel
techniques to counter set of attacks i.e. active attacks
like denial of service (DOS), vampire, user to root
attack etc. The user give the lot of request to the
system then the server blocks the whole process it
causes crashes in the system. These kind of attacks
can be detected using single attack and multi-attack.
They are using AODV protocol Ad hoc on demand
distance vector in NS2 environment Hussain, K.,
Hussain, S. J., Jhanjhi, N. Z., & Humayun, M. about
the energy consumption it uses many approaches
such as scheduling for optimal route path. In this it
uses the concept of clustering algorithm in which it
will decrease the distance between the two nodes in
the cluster and it will optimize the energy
consumption of all nodes in that cluster. It also use
the concept of fundamentals of clustering i.e. set-up
phase and steady phase. They also follow the routing
algorithm when data should be reached to the node.
It can use the concept clustering algorithm which is
using to choose the routing path from one node to
othernode.
Mukherjee, P. describes the functionality of
smaller nodes, these smaller nodes are cheaper in
cost. These smaller nodes are the reason for
transmission. For calculating the shortest path
between two nodes we need Dijkstra algorithm for
finding the shortest path. It will calculate value
between active cluster head. It uses LEACH-VD
helps for reducing the power consumption and
increasing the energy with the help of dijkstra
algorithm. Network will divide into clusters.
Clusters make with groups of nodes. The probability
of each cluster has same. These cluster head will
directly connect to the base station.
Hassan, A. A. H., Shah, W. M., Othman, M. F.
I., & Hassan, H. A. H. it will talk about the K-
Means and fuzzy C-means algorithm to help the
cluster who are removed with their position and it
also increase the network life like to save the battery
of sensors. When we deploy the sensors on dense
area. It introduce the concept of KM and FCM with
which it will improve the balanced cluster. Take
several parameter for calculating and improving
when we take lot of scenario together. It also tells
that by their calculation it got to know that FCM is
more powerful as compare to KM which is less
beneficial as compare to FCM if we deploy lot of
sensor on widearea.
Haque, M. E., &Baroudi, U. tells about the
guarantee delivery from source to destination in
which it uses energy efficient protocol with the help
of this definitely data should reached. It uses the
concept of DEER i.e. Dynamic energy efficient
routing and they have the capability to improve or to
increase the session time of the network and addition
to that it is having one of the functionality added that
it can easily deployed from any distance. This
technique also helpful to reduce the energy
Design Strategies for Mobile Ad-hoc Network to Prevent from Attack
197
consumption and power consumption. As compare
to dijkstra algorithm this DEER routing was so
much helpful.
Rajesh, D., & Jaya, T. give the mathematical
model for secure the cluster mobile ad hoc network.
It also increase the life of network. In this very
difficult to save the battery for a long time. It
contains the method of shifting the cluster head of
the network. It uses the methodology of ME2SC
using with LEACH-C, DMSR andDMSR.
Prasad, A. Y., & Balakrishna, R. this will tell
about the low energy consumption, power
consumption due to when we transmit the data it
wants more energy, the rate at which user transmit
the data from source to destination. In this they will
try to improve the energy. It will find the most
suitable routing algorithm for communication. It
describes the LEACH (low energy adaptive cluster
hierarchy) protocol which will take low energy and
power consumption between source todestination.
Kaushik, M., Gupta, S. H., & Balyan, tells about
advancement in wireless sensor network. There is
one technology i.e. Wireless body area network.
That WBAN technology used in pets and human. In
this Wireless body area network would be inserted
into human body, this technology would be
beneficial, it also take less energy and it’s reliable.
In this paper it also calculate the end to end delay,
throughput etc.
Kumar, H., Chahal, V. P., &Verma, P. R. this
paper tells about the advantages and disadvantages of
Leach protocol. In this paper it can take the security
was the main task in the network. Leach is the low
energy adaptive clustering hierarchy it takes low
energy from the whole nodes. Wireless sensor nodes
wasthe collection of maximum number of nodes via
which we are doing communication.
Rajesh, D., & Jaya, T. in this it is talking about
this LEACH protocol which is implemented on dry
soil i.e. the part of homogeneous. It will calculate
the value of part of heterogeneous. It design a model
which is using for calculating the energy. In this
paper it develops a cluster head which is depend on
threshold value. It calculates the value of threshold
in each round. It gives the simulation which is based
on performance of life in the network and how much
nodes are alive ordead.
Takele, A. K., Ali, T. J., & Yetayih, K. A. in this
paper they are describing how to improve the
performance of small sensors which are cheap, low
cost battery and small CPU. Battery are to be
deployed most probably in remote locations which
was the main cause of this problem. Most of the
energy are to be consumed when data should be
transmitted and some of the energy will lost to
decide where to be deployed thenodes.
5 RESEARCH METHODOLOGY
Leach protocol is the Low energy adaptive
clustering hierarchy. It will monitor the
environmental type of conditions i.e. moving,
temperature etc. This protocol defines reduce the
energy consumption of the nodes and reduce the
data transmission to the other node.
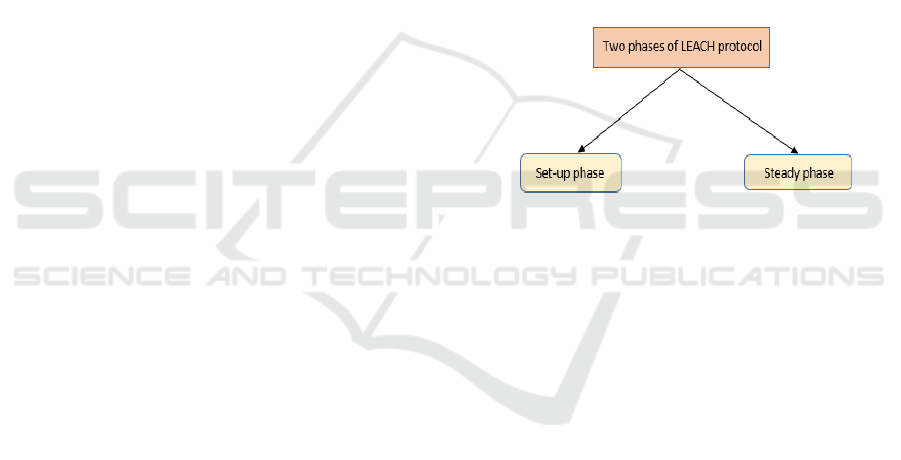
LEACH protocol based on Time Division
Multiple Access (TDMA) which will divide the
frequency in different time slots under the MAC
protocol. The goal of LEACH protocol is that it will
increase the lifetime of the network. There are two
phases of LEACH protocol i.e. Set- up phase and
Steady phase.
Figure 6. Representation of Phases
5.1 Operation on Leach Protocol
Leach protocol contains so many rounds and in each
round include these two phases i.e. Set- up phase
and steady phase which is used for reducing the
energy consumption.
In Fig.6. In the case of set-up phase, the aim is to
discover the cluster, we select the cluster on the
basis of that nodewhoseenergy is maximum. In this
phase, we send the packet to inform the all the nodes
which are clustered that our own self is also a
cluster, calculate on the basis of thisformula:
T (n) = R/ 1-R*(r mod R-1)
where R is the probability of cluster head, n is the
number of nodes, T (n) is the threshold valueThe
number (n) which is lessor than threshold value, then
that value will be cluster head. When that cluster
becomes cluster head, then it never becomes cluster
head again. It give only one chance in the network
that node will become cluster head once. In this case
set-up phase has 3 fundamentals i.e. cluster head
advertisement, cluster set up and creation of
transmission line.
ICACSE 2021 - International Conference on Advanced Computing and Software Engineering
198
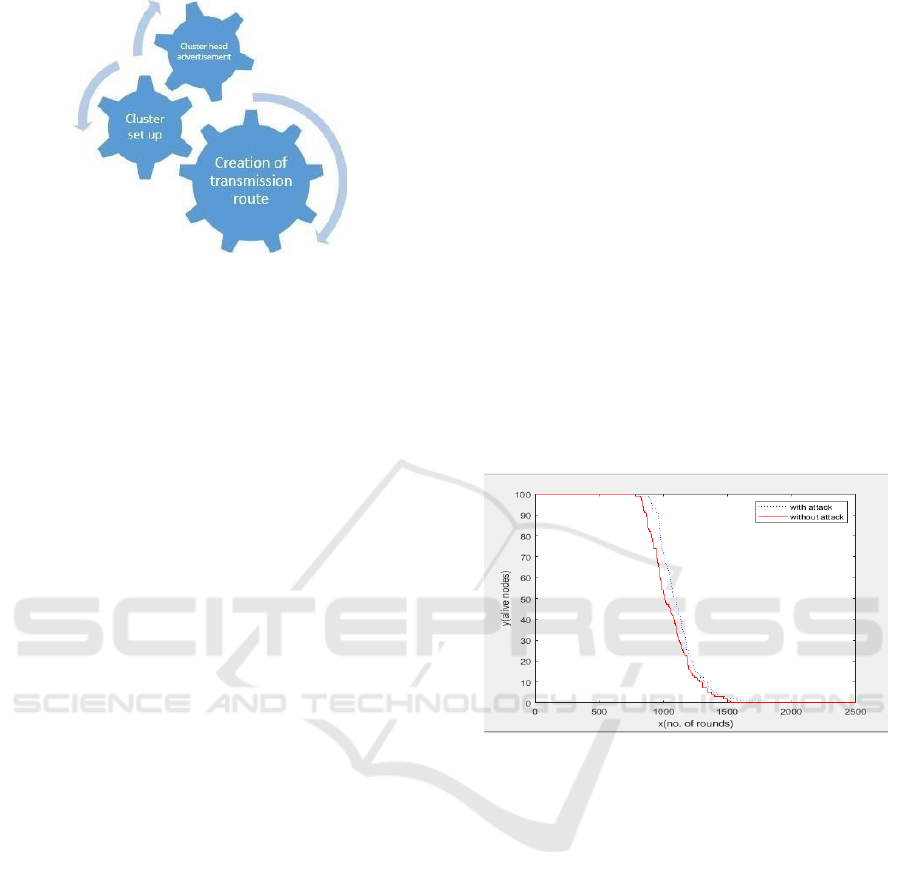
Figure 7. Representation of three fundamentals set- up
phase
SET-UP PHASE:
In Fig.7. In cluster head advertisement, the packet is
forwarded to all the nodes with the help of this
advertisement, it will advertise to all the nodes. If
that node whose energy is maximum then that
energy will become the cluster head. All the nodes is
having only one chance for making cluster node.
This strategy is useful for saving the energy
consumption. Those nodes which are not cluster
head in the current round, it will send the join
request to the cluster head and tell that we are the
parts of cluster head because of this reason in the
second round they will also get a chance to
makecluster.
In the last step in the set-up phase that the cluster
head will maintain the route path with the other
nodes of that cluster. TDMA based MAC protocol
will work on those nodes which are in cluster.
S
TEADY PHASE:
In the case of steady phase, those nodes which are in
cluster i.e. cluster nodes were only talk to cluster
head. There is no multi-hop routing allowed only
single hop routing possible. With the help of this if
one cluster node can communicate to other cluster
node reach up to base stations. The working of
cluster head is that it will collect all data in their
cluster head and afterwards they are able to transmit
with otherdata.
All the nodes in one cluster, from that cluster one
node is cluster head which is deciding with the help
maximum energy in first round. In the second round
all those nodes who do not participate in first round
to make cluster head in the second round. With the
help of cluster node we are able to transmitting the
data from one cluster node to another cluster node.
In the network there are so many clusters, data
should be transmitted in a secure channel.
Machine learning has a clustering technique in
which it has so many data points with the helpof this
algorithm we can easily find out the which node in
which group it belongs. Those nodes which are in
same cluster there are having similar properties and
functionalities. As compare to other cluster it is
having different functionalities. In machine learning,
we have two things supervised learning and
unsupervised learning. Supervised learning is useful
for data collection and it give the output from our
previous experience but in the case of unsupervised
learning it will find out the unknown data patterns.
Clustering is the unsupervised learning and it also
helps in the field of data analysis and this was used
in many otherfields.
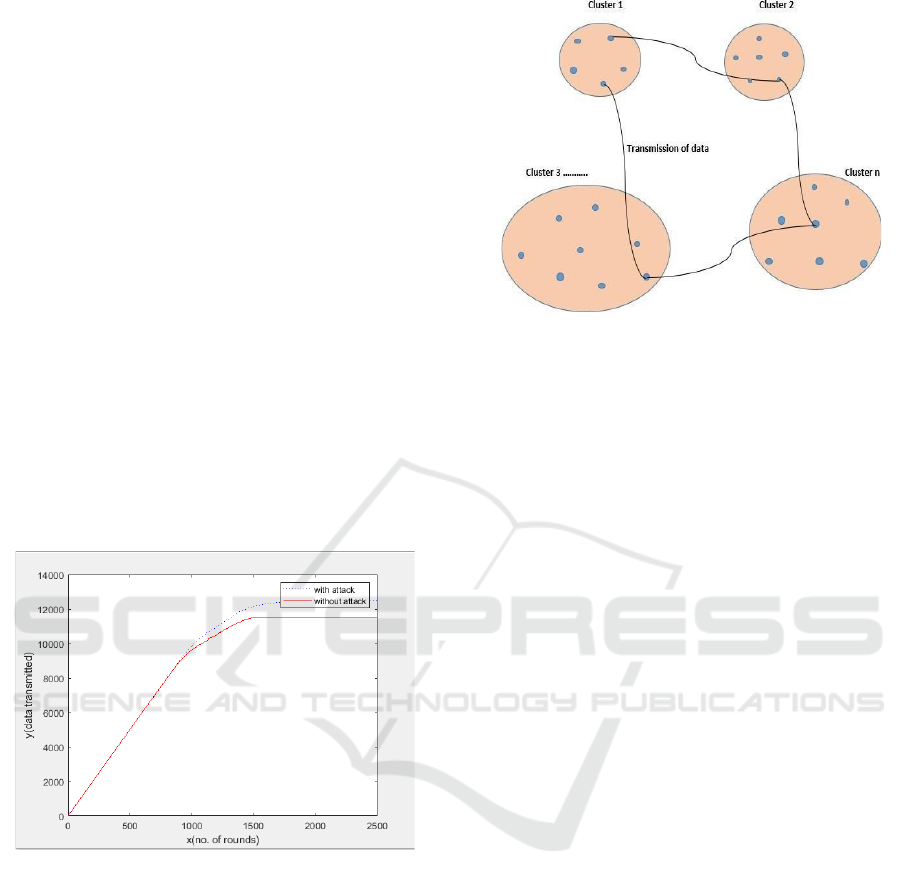
In Figure 8, was the representation of clusters in
which data should be transmitted from one to
another node. It will use clustering algorithm in
which we are able to reduce the energy consumption
and transmissiondelay.
Clustering algorithm using set-up phase and
steady phase:
Figure 8. Representation of clusters In the case of Set-up
phase:
Contention of cluster head: From this, it works
from base station, in the starting stage base station or
sink was provide some percentage (per), from this
percentage it will calculate the cluster head (ch)
from each round. Any kind of number or random
number (ran num) will be generated in between 0
and 1. We will see the percentage if it is less, then it
will be choosing a cluster head otherwise it was just
a node which is sensing node. Those nodes who
cleared this phase send a data packet to all with a
value called threshold (n). The calculated value
based on some sensor nodes and their average speed.
The speed was based on some transmission range.
All those nodes are in pattern and it should receive
some signal within that pattern it will help to choose
a cluster node. It is the solution of this to take
coverage ofnetwork.
Design Strategies for Mobile Ad-hoc Network to Prevent from Attack
199
ran number (0, 1) < per
threshold (n) = (
W1 *Sn) + (W2 * Ern)
Election of cluster head: In the phase of cluster
head (ch) those who follow the statement of (2) will
participate in the process of cluster head. It calculate
the value of threshold (n) based on (3) and it also
sees the any data packet it received from other
sensing nodes. If the value of threshold (n) will be
less than those nodes who are receiving packet, then
those nodes as elected as a cluster head.
5.2 Association Ofcluster Head
In the based on this, sensor nodes are the responsible
to make cluster head on the basis of criteria of
association of cluster head. Whatever the speed
comes from other cluster head and it will calculate
the distance and their speed, then it will be the part
of cluster head.
6 RESULTS AND DISCUSSION
Figure 9. Representation of alive nodes with attack and
without attack
The values are in tabular format and take the
values of alive nodes with attack and without attack.
All are the GUI form of LEACH implementation
and in panel of Implementing Leach Protocol there
are three block, first is Leach Implementation, Leach
GUI Implementation and GUI Implementation. In
this section we are having the result of alive nodes,
data transmission, energy consumption and cluster
head using the matlab simulation tool and compare
with attack and without attack.
Figure 10. Data transmission from nodes to cluster head
7 CONCLUSION
Leach protocol contains so many rounds and in each
round include these two phases i.e. Set- up phase
and steady phase which is used for reducing the
energy consumption. In wireless sensor network,
there are small nodes and these small nodes having
limited energy. Leach protocol was the earliest
protocol and it works on energy consumption. This
will reduce the energy who has maximum energy. In
leach protocol there are having two phases we
already described and there are having so many
rounds and in each round cluster head will changed
via each cluster head will get chance once. In this
protocol there is having some pros and cons via this
we can try to modify the leach protocol like c-leach,
q-leachetc.
REFERENCES
Aboalneel, M., Abd-Elnaby, M., & El-Sayed, A. (2019).
Quality-based LEACH protocol with enhanced
cluster- head selection for wireless
sensornetworks.MenoufiaJournal of Electronic
Engineering Research.
Amru, M., Jabirullah, M., & Krishna, A. C. (2020). An
Improved Network Coding Based LEACH Protocol
for Energy Effectiveness in Wireless Sensor
Networks. In Recent Trends and Advances in
Artificial Intelligence and Internet of Things, Springer,
Cham.
Arulkumaran, G., &Gnanamurthy, R. K. (2019). Fuzzy
trust approach for detecting black hole attack in
mobile adhoc network. Mobile Networks and
Applications.
Bhagat, A., &Geetha, G. (2020). Optimization of LEACH
for Developing Effective Energy-Efficient Protocol in
ICACSE 2021 - International Conference on Advanced Computing and Software Engineering
200

WSN. In International Conference on Innovative
Computing and Communications, Springer, Singapore.
Gowda, S. B., &Subramanya, G. N. (2019). DUCA: An
Approach to Elongate the Lifetime of Wireless Sensor
Nodes. In Engineering Vibration, Communication and
Information Processing, Springer, Singapore.
Haque, M. E., &Baroudi, U. (2020). Dynamic energy
efficient routing protocol in wireless sensor
networks.Wireless Networks.
Hassan, A. A. H., Shah, W. M., Othman, M. F. I., &
Hassan, H. A. H. (2020). Evaluate the performance of
K- Means and the fuzzy C-Means algorithms to
formation balanced clusters in wireless sensor
networks. International Journal of Electrical &
Computer Engineering.
Jaradat, Y., Masoud, M., Jannoud, I., Abu-Sharar, T.,
&Zerek, A. (2019, March). Performance Analysis of
Homogeneous LEACH Protocol in Realistic Noisy
WSN. In 2019 19th International Conference on
Sciences and Techniques of Automatic Control and
Computer Engineering (STA),IEEE.
Kassan, S., Lorenz, P., & Gaber, J. (2018, May). Low
energy and location based clustering protocol for
wireless sensor network. In 2018 IEEE International
Conference on Communications (ICC).
Kaushik, M., Gupta, S. H., &Balyan, V. (2019,
September). Implementation and Reliability Analysis
of LEACH and SIMPLE protocols in WBAN for
Health Monitoring of Canine. In 2019 International
Conference on Issues and Challenges in Intelligent
Computing Techniques (ICICT), IEEE.
Kumar, H., Chahal, V. P., &Verma, P. R. (2019).
Improvement on LEACH Protocol in Wireless Sensor
Networks.
Kundu, S., Karthikeyan, S., &Karthikeyan, A. (2018,
December). QBEECH: Multi-hop clustering of
cognitive based sensor nodes in the administration of
queen nodes. In International Conference on
Intelligent Systems Design and Applications,Springer,
Cham.
Mittal, M., & Kumar, S. (2019). Performance Evaluation
of LEACH Protocol Based on Data Clustering
Algorithms. In Proceedings of 2nd International
Conference on Communication, Computing and
Networking, Springer, Singapore.
Mukherjee, P. (2020). LEACH-VD: A Hybrid and
Energy-Saving Approach for Wireless Cooperative
Sensor Networks. In IoT and WSN Applications for
Modern Agricultural Advancements: Emerging
Research and Opportunities,IGI Global.
Netyorks, V. S., Krishnakumar, A., &Anuratha,V. (2017).
FEELP: Fuzzy-Based Energy-Efficient LEACH
Protocol in. Journal of Engineering and Applied
Sciences.
Prasad, A. Y., &Balakrishna, R. (2019). Implementation
of optimal solution for network lifetime and energy
consumption metrics using improved energy efficient
LEACH protocol in MANET. Telkomnika.
Prasanna, A. L., & Kumar, V. (2020). Modified Cluster
Head Election Scheme Based on LEACH Protocol for
MI-Driven UGWSNs. In Advances in VLSI,
Communication, and Signal Processing, Springer,
Singapore.
Prasanna, A. L., & Kumar, V. (2020). Modified Cluster
Head Election Scheme Based on LEACH Protocol for
MI-Driven UGWSNs. In Advances in VLSI,
Communication, and Signal Processing,Springer,
Singapore.
Prasanna, S. (2018). Complete Analysis Of Various
Attacks In Manet. International Journal of Pure and
Applied Mathematics.
Rahmadhani, M. A., Yovita, L. V., &Mayasari, R. (2018,
July). Energy Consumption and Packet Loss Analysis
ofLEACH Routing Protocol on WSN Over DTN. In
2018 4th International Conference on Wireless and
Telematics (ICWT), IEEE.
Rajesh, D., & Jaya, T. (2020). A Mathematical Model for
Energy Efficient Secured CH Clustering Protocol for
Mobile Wireless Sensor Network. Wireless Personal
Communications.
Rakhi, &Pahuja, G. L. (2019). A reliable solution of path
optimisation in LEACH protocol by implementing
trust- based neural network. International Journal of
Communication Networks and Distributed Systems.
Rashid, M. M., & Al-Jamali, N. A. S. (2019). Modified
W- LEACH Protocol in Wireless Sensor Network.
Journal of Engineering.
Takele, A. K., Ali, T. J., &Yetayih, K. A. (2019, May).
Improvement of LEACH Protocol for Wireless Sensor
Networks. In International Conference on Information
and Communication Technology for Development for
Africa, Springer, Cham.
Takele, A. K., Ali, T. J., &Yetayih, K. A. (2019, May).
Improvement of LEACH Protocol for Wireless Sensor
Networks. In International Conference on Information
and Communication Technology for Development for
Africa Springer, Cham.
Thiagarajan, R. (2020). Energy consumption and network
connectivity based on Novel-LEACH-POS protocol
networks. Computer Communications.
Vaseer, G., Ghai, G., &Ghai, D. (2019). Novel Intrusion
Detection and Prevention for Mobile Ad Hoc
Networks: Single-and Multiattack Case Study. IEEE
Consumer ElectronicsMagazine.
Wang, Z. X., Zhang, M., Gao, X., Wang, W., & Li,X.
(2019). A clustering WSN routing protocol based on
node energy and multipath. Cluster Computing.
Yousaf, A., Ahmad, F., Hamid, S., & Khan, F. (2019,
March). Performance Comparison of Various LEACH
Protocols in Wireless Sensor Networks. In 2019 IEEE
15th International Colloquium on Signal Processing
&ItsApplications(CSPA),IEEE.
Design Strategies for Mobile Ad-hoc Network to Prevent from Attack
201
