
A Comparison of GKE Protocols based on SIDH
Hiroki Okada
1
, Shinsaku Kiyomoto
1
and Carlos Cid
2,3
1
KDDI Research, Inc., Saitama, Japan
2
Royal Holloway, University of London, Egham, U.K.
3
Simula UiB, Norway
Keywords:
Group Key Establishment, Post-quantum Cryptography, Isogeny-based Cryptography, SIDH.
Abstract:
End-to-end encryption enables secure communication without releasing the contents of messages to the system
server. This is a crucial security technology, in particular to cloud services. Group Key Establishment (GKE)
protocols are often needed to implement efficient group end-to-end encryption systems. Perhaps the most
famous GKE protocol is the Broadcast Protocol, proposed by Burmester and Desmedt. In addition, they
also proposed the Star-based Protocol, Tree-based Protocol, and Cyclic-based Protocol. These protocols
are based on the Diffie-Hellman key exchange protocol, and therefor are not secure against attacks based on
quantum computers. Recently, Furukawa et al. proposed an efficient GKE protocol by modifying the original
Broadcast Protocol into a post-quantum GKE protocol based on the Supersingular Isogeny Diffie-Hellman key
exchange (SIDH). In this paper, we extend their work by considering the remaining DH-based GKE protocols
by Burmester and Desmedt post-quantum versions based on SIDH, and compare their efficiency. As a result,
we confirm that the Broadcast Protocol is indeed the most efficient protocol in this post-quantum setting, in
terms of both communication rounds and computation time.
1 INTRODUCTION
Secure and efficient key management is long-standing
active area of research in cryptography. In many
cases, we have a trustworthy central server in the
system, which is usually responsible for the efficient
key management. However, in the case of cloud
services, servers are not necessarily trustworthy. For
example, when using chat applications, one usually
does not want to let service providers see the contents
of chats – we do not want to give the server access to
the secret keys, thus end-to-end encryption is usually
desirable in this case. When considering end-to-end
encrypted group communication, key management is
more complicated. Group Key Establishment (GKE)
protocols enable group members to efficiently share
the group key without giving access to the server.
Perhaps the most famous GKE protocol is
Broadcast Protocol proposed by Burmester and
Desmedt (Burmester and Desmedt, 1994). The
authors also proposed the Star-based Protocol, Tree-
based Protocol, and Cyclic-based Protocol. All
these protocols area based on the Diffie-Hellman key
exchange, and are therefore insecure against attacks
based on quantum computers.
Recently, Furukawa et al. proposed an efficient
post-quantum GKE protocol (Furukawa et al., 2018)
by modifying the Broadcast Protocol of (Burmester
and Desmedt, 1994) to use the Supersingular
Isogeny Diffie-Hellman key exchange (SIDH), which
is believed to be post-quantum secure. The concept
of the isogeny-based cryptography was first proposed
in (Silverman, 1986). The first concrete isogeny-
based Diffie-Hellman type key exchange protocol was
proposed in (Rostovtsev and Stolbunov, 2006). The
protocol was defined over ordinary elliptic curves,
and was originally believed to be post-quantum
secure. However, the authors of (Childs et al.,
2014) described a subexponential quantum algorithm
to compute isogenies between ordinary curves, thus
showing that Rostovtsev et al.’s protocol is not post-
quantum secure. Jao et al. (Jao and De Feo, 2011)
proposed an isogeny-based Diffie-Hellman type key
exchange protocol defined over supersingular elliptic
curves, called SIDH, which is believed to post-
quantum secure. They are also among the authors
of the post-quantum key establishment mechanism
based on SIDH that was submitted to NIST’s
Post-Quantum Cryptography competition (National
Institute of Standards and Technology, 2020).
Okada, H., Kiyomoto, S. and Cid, C.
A Comparison of GKE Protocols based on SIDH.
DOI: 10.5220/0010547305070514
In Proceedings of the 18th International Conference on Security and Cryptography (SECRYPT 2021), pages 507-514
ISBN: 978-989-758-524-1
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
507

One important use case of GKE protocols are
group chat applications. The problem of privacy
in these applications has been receiving growing
attention from the cryptographic community. It was
sometimes suspected that providers of these services
might be able to gather the information of chats if they
do not support the End-to-End encryption. As a result,
in January 2018, Skype started testing new “private
conversations” with end-to-end encryption (Microsoft
Community, 2018), using the industry standard Signal
Protocol by Open Whisper Systems (Open Whisper
Systems, 2018). Facebook Messenger and Allo (by
Google) also use this Signal Protocol for End-to-End
encryption.
The Signal Protocol is a non-federated
cryptographic protocol, initially with no academic
security analysis publicly provided. Cohn-Gordon
et al. produced a first academic analysis of the
protocol, followed by several other works, e.g.
in (Bellare et al., 2017; Herzberg and Leibowitz,
2016; Cohn-Gordon et al., 2018; R
¨
osler et al., 2018;
Tanada et al., 2016; Cohn-Gordon et al., 2016).
Cohn-Gordon et al. reported that there were no
major flaws in the design of Signal Protocol. We
note however that their first study was focused on
Signal’s two-party key exchange protocol, and did
not include group messaging properties (since the
implementation of group messaging of the Signal
Protocol is not specified at the protocol layer (Perrin
and Marlinspike, 2016)).
Moreover, the authors reported in (Cohn-Gordon
et al., 2018) that “While these users’ two-party
communications now enjoy very strong security
guarantees, it turns out that many of these apps
provide, without notifying the users, a weaker
property for group messaging: an adversary who
compromises a single group member can intercept
communications indefinitely.”. As a result a Tree
based GKE has been proposed for adoption in
the Signal protocols. Also note that IETF MLS
WG (Barnes et al., 2020) tries to generalize the Signal
protocols to the group setting.
2 PRELIMINARY
2.1 Notation and Definition
• a ∈
R
A: a is selected from the set A uniformly and
independently at random.
• Group Key Agreement (GKA): all users
participate to key generation; group key
constructed based on all user’s secrets.
• Group Key Transfer (GKT): a privileged user
(group manager / KGC*) selects a key and
securely distributes it to the other users.
• Group Key Establishment (GKE): general term
including GKA and GKT.
2.2 SIDH Protocol
We briefly explain the SIDH protocol; for full details
see (Jao and De Feo, 2011). The fixed public
parameters of this scheme are {l
A
,l
B
, e
A
,e
B
, f , p =
l
e
A
A
l
e
B
B
f − 1, E
0
(F
p
2
), {P
A
,Q
A
}, {P
B
,Q
B
}}, where l
A
and l
B
are small primes, e
A
,e
B
, f so that p is a prime.
E
0
is a base supersingular elliptic curve, and {P
A
,Q
A
}
and {P
B
,Q
B
} are bases of E
0
[l
e
A
A
] over Z/l
e
A
A
Z and
E
0
[l
e
B
B
] over Z/l
e
B
B
Z, respectively. The key exchange
protocol is summarised as follows.
Alice chooses two random secret elements
m
A
,n
A
∈
R
Z/l
e
A
A
Z, where m
A
,n
A
are not divisible by
l
A
, and computes an isogeny φ
A
: E
0
→ E
A
whose
kernel is h[m
A
]P
A
+ [n
A
]Q
A
i. Alice also computes the
image {φ
A
(P
B
),φ
A
(Q
B
)} ⊂ E
A
of the basis {P
B
,Q
B
}
using her isogeny φ
A
. She sends {φ
A
(P
B
),φ
A
(Q
B
)}
and E
A
to Bob.
Similarly, Bob chooses two random secret
elements Z/l
e
B
B
Z, where m
B
,n
B
are not divisible by
l
B
, and computes an isogeny φ
B
: E
0
→ E
B
whose
kernel is h[m
B
]P
B
+ [n
B
]Q
B
i. Bob then computes
{φ
B
(P
A
),φ
B
(Q
A
)} ⊂ E
B
and sends {φ
B
(P
A
),φ
B
(Q
A
)}
and E
B
to Alice. With this information sent by
Bob, Alice computes an isogeny φ
0
A
: E
B
→ E
AB
whose kernel is {[m
A
]φ
B
(P
A
),[n
A
]φ
B
(Q
A
)}. Similarly,
Bob computes φ
0
B
: E
A
→ E
AB
whose kernel is
{[m
B
]φ
A
(P
B
), [n
B
]φ
A
(Q
B
)}. Alice and Bob can then
use the common j-invariant of
E
AB
= φ
0
B
(φ
A
(E
0
)) = φ
0
A
(φ
B
(E
0
))
= E
0
/{[m
A
]P
A
+ [n
A
]Q
A
,[m
B
]P
B
+ [n
B
]Q
B
},
to generate a secret shared key.
3 GROUP KEY ESTABLISHMENT
PROTOCOLS BASED ON SIDH
Burmester and Desmedt (Burmester and Desmedt,
1994; Burmester and Desmedt, 2005) and Steiner et
al. (Steiner et al., 1996) proposed several types of
GKE protocol based on the 2-party Diffie-Hellman
(DH) protocol. These protocols offer however no
security against quantum computer based attacks.
The authors of (Furukawa et al., 2018) proposed an
efficient post-quantum GKE protocol based on SIDH,
by modifying the Broadcast GKA Protocol proposed
SECRYPT 2021 - 18th International Conference on Security and Cryptography
508

Algorithm 1: Isogeny-based Star GKT Protocol.
1: Each user U
i
selects m
U
i
,n
U
i
∈
R
Z/l
e
U
U
Z and computes a tuple {E
U
i
,φ
U
i
(P
C
),φ
U
i
(Q
C
)}, then sends it to U
1
.
2: The chair C selects m
C
,n
C
∈
R
Z/l
e
C
C
Z, t ∈
R
T and a conference session key K ∈
R
{0,1}
k
. Then C computes
E
C
,φ
C
(P
U
),φ
C
(Q
U
), K
i
= H
t
( j(E
CU
i
)), c
i
= K
i
⊕ K.
3: The chair C sends a tuple {E
C
,φ
C
(P
U
),φ
C
(Q
U
),t,c
i
} to each user U
i
.
4: Each user U
i
computes K
i
= H
t
( j(E
CU
i
)), decrypts K = c
i
⊕ K
i
.
Algorithm 2: Isogeny-based Tree GKT Protocol.
1: Each user U
a
selects
m
U
a
,n
U
a
∈
R
(
Z/l
e
0
0
Z (when d = blogac is even),
Z/l
e
1
1
Z (when d = blogac is odd).
and computes a tuple
(
{E
U
a
,φ
U
a
(P
1
),φ
U
a
(Q
1
)} (when d = blogac is even),
{E
U
a
,φ
U
a
(P
0
),φ
U
a
(Q
0
)} (when d = blogac is odd).
and then sends it to U
ba/2c
,U
2a
,U
2a+1
.
2: Each U
a
computes K
a,ba/2c
= H
t
c
( j(E
U
a
U
ba/2c
)), K
a,2a
= H
t
c
( j(E
U
a
U
2a
)), and K
a,2a+1
= H
t
c
( j(E
U
a
U
2a+1
)),
where t
c
∈ T is a fixed constant. The root U
1
selects a group session key K ∈
R
{0,1}
k
and then sends
c
2
= K
2
⊕ K, c
3
= K
3
⊕ K to U
2
, U
3
, respectively.
3: for d = 1 to log n do if blog ac = d then
4: U
a
decrypts c
a
to get the conference key K = c
a
⊕ K
a,ba/2c
.
5: U
a
sends c
2a
= K ⊕ K
2a
to U
2a
and sends c
2a+1
= K ⊕ K
2a+1
to U
2a+1
.
6: end for
by Burmester and Desmedt. There are differences
between DH and SIDH we have to consider in order
to construct GKE based on SIDH:
• (Space of Ephemeral Secrets): In SIDH, Alice
chooses two ephemeral secrets m
A
,n
A
from
Z/l
e
A
A
Z, and Bob chooses two phemeral secrets
m
B
,n
B
from Z/l
e
B
B
Z. On the other hand, in the
DH protocol, Alice and Bob choose their secrets
r
A
and r
B
from the common space Z
q
.
• (Space of the Shared Key): In SIDH, the shared
secret is j(E
AB
) ∈ F
p
2
. On the other hand, in
the DH protocol, the shared secret is g
r
A
r
B
∈ Z
p
,
which similar to the ephemeral secrets, is also a
large positive integer.
Dealing with the differences above with the proper
iterative selection of the users’ ephemeral secret
space, we modify the all types of the GKE protocols
proposed in (Burmester and Desmedt, 1994) and
(Kim et al., 2004), to post-quantum protocols
based on SIDH: we consider Isogeny-based Star
GKT Protocol, Isogeny-based Tree GKT Protocol,
Isogeny-based Tree GKA Protocol, Isogeny-based
Broadcast GKA Protocol, and Isogeny-based Cyclic
GKA Protocol.
3.1 Isogeny-based Star GKT Protocol
C
U
1
U
2
U
3
...
U
n−1
Figure 1: The system for isogeny-based Star GKT Protocol.
We describe the Isogeny-based Star GKT Protocol.
This protocol is analogous to the Star based protocol
proposed in (Burmester and Desmedt, 1994), based
on the Diffie-Hellman key exchange. Algorithm 1
shows the algorithm of the protocol, and Figure 1
depicts the system. Notation used to denote the
members and fixed public parameters is as follows:
• Members:
– C (A chair)
– U (Users): {U
1
,...,U
n−1
},
• Parameters:
– p = l
e
C
C
l
e
U
U
f ± 1, E
0
, {P
C
,Q
C
}, {P
U
,Q
U
}.
– Let H = {H
t
: t ∈ T } be a hash function family
indexed by a finite set T , where each H
t
is a
function from F
p
2
to the key space {0,1}
k
.
A Comparison of GKE Protocols based on SIDH
509
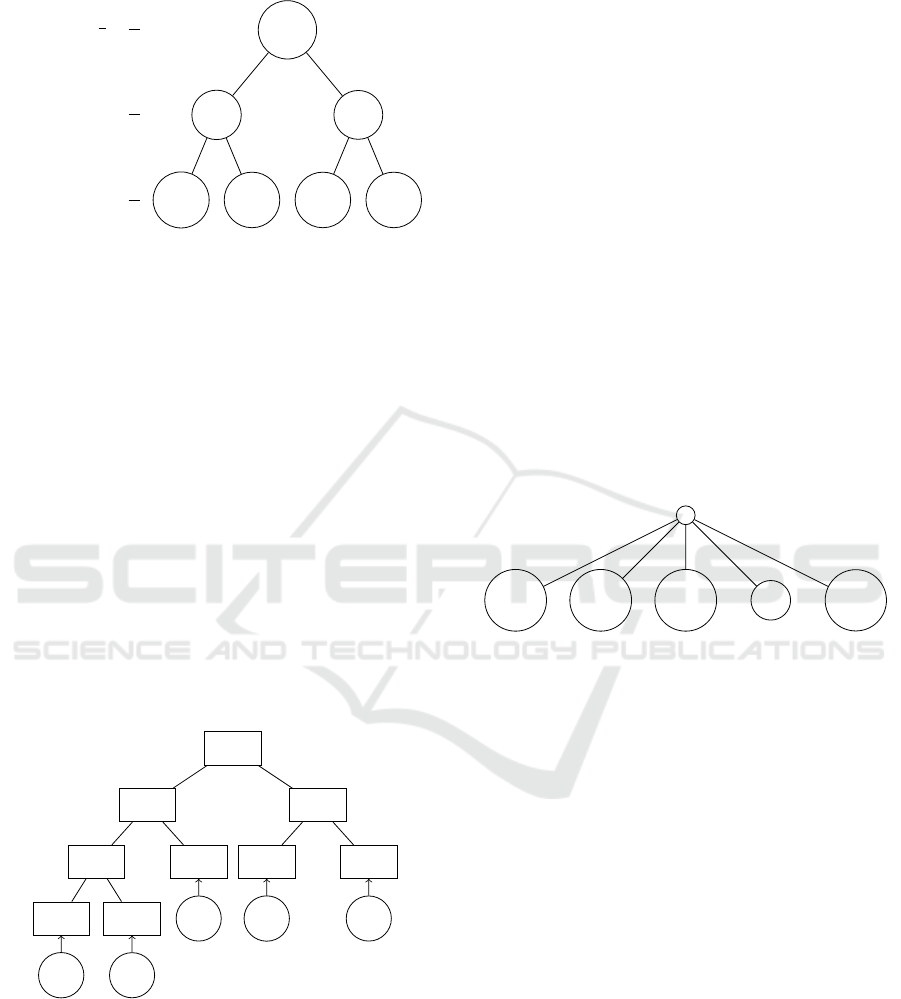
3.2 Isogeny-based Tree GKT Protocol
U
ba/2c
U
a
U
2a
U
2a+1
U
a+1
U
2a+2
U
2a+3
d = blog(
a
2
)c
d = blogac
d = blog(2a)c
Figure 2: The system for the Isogeny-based Tree GKT
Protocol.
We describe the Isogeny-based Tree GKT Protocol.
This protocol is analogous to the tree based protocol
proposed in (Burmester and Desmedt, 1994) based on
the Diffie-Hellman key exchange. Algorithm 2 shows
the algorithm of the protocol, and Figure 2 depicts
the system. Notation used to denote the members and
fixed public parameters is as follows:
• Users: {U
1
,...,U
n
}. (U
1
is the root.)
• Parameters:
– p = l
e
0
0
l
e
1
1
f ± 1, E
0
, {P
0
,Q
0
}, {P
1
,Q
1
}.
– Let H = {H
t
: t ∈ T } be a hash function family
indexed by a finite set T , where each H
t
is a
function from F
p
2
to the key space {0,1}
k
.
3.3 Isogeny-based Tree GKA Protocol
h0,0i
h1,0i
h2,0i
h3,0i
U
0
h3,1i
U
1
h2,1i
U
2
h1,1i
h2,2i
U
3
h2,3i
U
4
Figure 3: An example of the nodes tree for the isogeny-
based tree GKA protocol (n = 5).
We describe an Isogeny-based Tree GKA Protocol.
This protocol is analogous to the TGDH proposed in
(Kim et al., 2004). Algorithm 3 shows the algorithm
of the protocol, and Figure 3 depicts the system.
The notation used for the members and fixed public
parameters is as follows:
• Users: {U
0
,...,U
n−1
}.
• Nodes: hu,vi. (2
u
max
−1
≤ n ≤ 2
u
max
).
• Sponsor user(s): Every node has sponsor user(s),
which we denote as S
hu,vi
.
• Parameters:
– p = l
e
0
0
l
e
1
1
f ± 1, E
0
, {P
0
,Q
0
}, {P
1
,Q
1
}.
– Let H
0
= {H
0
t
: t ∈ T } be a hash function
family indexed by a finite set T , where each
H
0
t
is a function from F
p
2
to the (twin) space
of ephemeral secrets Z/l
e
0
0
Z × Z/l
e
0
0
Z.
– Let H
1
= {H
1
t
: t ∈ T } be a hash function
family indexed by a finite set T , where each
H
1
t
is a function from F
p
2
to the (twin) space
of ephemeral secrets Z/l
e
1
1
Z × Z/l
e
1
1
Z .
– Let H
0
= {H
0
t
: t ∈ T } be a hash function family
indexed by a finite set T , where each H
0
t
is a
function from F
p
2
to the key space {0,1}
w
3.4 Isogeny-based Broadcast GKA
Protocol
U
0
U
1
U
2
...
U
n−1
Figure 4: The system for Isogeny-based Broadcast GKA
Protocol.
This protocol is proposed in (Furukawa et al., 2018),
which is analogous to the broadcast protocol proposed
in (Burmester and Desmedt, 1994) based on the
Diffie-Hellman key exchange protocol. Algorithm 4
shows the algorithm of the protocol, and Figure 4
depicts the system. Notation used for members and
the fixed public parameters is as follows:
• User: U
0
,...,U
n−1
(For simplicity, n is even)
• p = l
e
0
0
l
e
1
1
f − 1
• {P
0
,Q
0
} is the basis of E[l
e
0
0
] and {P
1
,Q
1
} is the
basis of E[l
e
1
1
].
• define ι as follows;
ι = ι(i) :=
(
0 (when i is even),
1 (when i is odd).
• index i is always calculated modulo n
SECRYPT 2021 - 18th International Conference on Security and Cryptography
510

Algorithm 3: Isogeny-based Tree GKA Protocol.
1: for u = u
max
to 1 do
2: Denote ι = v (mod 2), and let t
c
∈ T be a fixed constant. Each S
hu,vi
(
selects m
hu,vi
,n
hu,vi
∈
R
Z/l
e
ι
ι
Z (if hu,vi is a leaf),
computes (m
hu,vi
||n
hu,vi
) = H
ι
t
c
(K
hu,vi
) (otherwise),
and computes a tuple {E
S
hu,vi
,φ
S
hu,vi
(P
ι
),φ
S
hu,vi
(Q
ι
)} and sends it to S
0
hu,vi
, where S
0
hu,vi
is the sponsor of
the node whose parent is common with S
hu,vi
.
3: Note that the parent node of hu, vi is hu − 1,bv/2ci. Each S
hu,vi
and S
0
hu,vi
obtain K
hu−1,bv/2ci
=
j(E
S
hu,vi
S
0
hu,vi
). Then, let S
hu,vi
and S
0
hu,vi
be S
hu−1,bv/2ci
.
4: end for
5: From the above steps, every user obtains K
h0,0i
= j(E
S
h1,0i
S
h1,1i
), and then computes the conference key K =
H
0
t
c
( j(E
S
h1,0i
S
h1,1i
))
Algorithm 4: Isogeny-based Broadcast GKA Protocol.
1: Every U
i
randomly chooses m
i
,n
i
∈ (Z/l
e
ι
ι
Z). Then, U
i
computes a tuple {E
U
i
,φ
U
i
(P
ι+1
),φ
U
i
(Q
ι+1
)} and
sends it to U
i−1
and U
i+1
.
2: Every U
i
computes j(E
U
i−1
U
i
), and j(E
U
i
U
i+1
). Then, Every U
i
broadcasts X
i
:= j(E
U
i
U
i+1
) · j(E
U
i−1
U
i
)
−1
.
3: Every U
i
calculates K
i
:= j(E
U
i−1
U
i
)
n
· X
n−1
i
· X
n−2
i+1
· ··· · X
i−2
. By simple arithmetic, for all i,
K = K
i
= j(E
U
1
U
2
) · j(E
U
2
U
3
) · · · · · j(E
U
n
U
1
).
U
1
U
2
U
3
U
4
U
5
U
6
U
7
U
8
Figure 5: An example of the system for the Isogeny-based
Cyclic GKA Protocol (when n = 8).
3.5 Isogeny-based Cyclic GKA Protocol
We describe an Isogeny-based Cyclic GKA Protocol.
This protocol is analogous to the Cyclic protocol
proposed in (Burmester and Desmedt, 1994) based
on the Diffie-Hellman key exchange protocol.
Algorithm 5 shows the algorithm of the protocol,
and Figure 5 depicts the system. Notation used for
members and fixed public parameters is the same as
for the broadcast protocol.
4 SECURITY
In this section we give a brief sketch of the security
reductions, relating the security of GKE protocols to
the hardness of the appropriate underlying isogeny
computation problem.
The security of GKT protocols, i.e. the isogeny-
based star GKT protocol and the isogeny-based tree
GKT protocol, follows straightforward from SIDH,
of which security proof is given in (Jao and De Feo,
2011). Therefore, we focus on the security of the
GKA protocols, i.e. the isogeny-based tree GKA
protocol, the isogeny-based broadcast GKA protocol,
and the isogeny-based cyclic GKA protocol.
Burmester and Desmedt gave a security proof of
the broadcast protocol based on the Diffie-Hellman
key exchange in (Burmester and Desmedt, 1994).
Similarly, Furukawa et al. gave a security proof of
the isogeny-based broadcast protocol based on SIDH
in (Furukawa et al., 2018). The security of the
isogeny-based tree GKA protocol, and isogeny-based
cyclic GKA protocol described in this paper can be
proven in a similar manner.
To start, assume the notation as follows:
• E
SS,p
: set of isomorphism classes of super
singular EC defined on F
p
2
A Comparison of GKE Protocols based on SIDH
511

Algorithm 5: Isogeny-based Cyclic GKA Protocol.
1: Every U
i
randomly chooses m
i
,n
i
∈ (Z/l
e
ι
ι
Z). Then, U
i
computes a tuple {E
U
i
,φ
U
i
(P
ι+1
),φ
U
i
(Q
ι+1
)} and
sends it to U
i−1
and U
i
.
2: Every U
i
computes j(E
U
i−1
U
i
), and j(E
U
i
U
i+i
). Then, Every U
i
computes X
i
:= j(E
U
i
U
i+1
) · j(E
U
i−1
U
i
)
−1
. Let
b
0
= c
0
= 1
3: for i = 1 to n do U
i
computes (b
i
,c
i
), where b
i
= X
1
· X
2
···X
i
, c
i
= X
i−1
1
· X
i−2
2
···X
i−1
= b
i−1
· c
i−1
, and
sends them to U
i+1
4: end for
5: Let d
0
= c
n
= X
n−1
1
· X
n−2
2
···X
n−1
.
6: for i = 1 to n do U
i
computes d
i
= b
n
· d
i−1
· X
−n
i
= X
n−1
i+1
· X
n−2
i+2
···X
i−1
and sends (b
n
,d
i
) to U
i+1
.
7: end for
8: Every U
i
calculates K
i
:= j(E
U
i−1
U
i
)
n
· d
i
By simple arithmetic, for all i,
K = K
i
= j(E
U
1
U
2
) · j(E
U
2
U
3
) · · · · · j(E
U
n
U
1
).
Table 1: Protocol comparison. Communication and computation are considered per user. I and H means the calculation cost
of the isogeny map (φ
A
or φ
B
) and Hash function, respectively. M means the cost of multiplication of elements in F
p
2
.
Protocol type Communication (per user) Rounds Computation (per user)
Star GKT Transfer
(chair): 2(n − 1)
2
(chair): nI + H
(users): 2 (users): 2I + H
Tree GKT Transfer 5 1 + dlog ne 4I + 3H
Tree GKA Agreement 1 + dlog ne 1 + dlogne dlogneI + dlogneH
Broadcast GKA Agreement 2 2 3I +
n(n+1)
2
M
Cyclic GKA Agreement 6 2n + 1 3I +
n(n+1)
2
M
• J
SS,p
:= { j ∈ F
p
2
| ∃ E ∈ E
SS,p
, j = j(E)}
• J
n
:= { j
1
··· j
n
| i ∈ [n], j
i
∈ J
SS,p
} ⊂ F
p
2
The definition of hard problem and security are as
follows:
Definition 1. Super Singular Decisional Diffie-
Hellman (SSDDH) problem is to distinguish the
distribution of
(E,E
A
,φ
A
(P
B
),φ
A
(Q
B
),E
B
,φ
B
(P
A
),φ
B
(Q
A
), j(E
AB
))
and
(E,E
A
,φ
A
(P
B
),φ
A
(Q
B
),E
B
,φ
B
(P
A
),φ
B
(Q
A
), j).
Definition 2. When any probabilistic polynomial
algorithm A cannot distinguish K from a random
element of J
n
, the isogeny-based broadcast protocol
provides secrecy.
Then, the statement of the theorem is as follows:
Theorem 1. Under the assumption that SSDDH
holds, the isogeny-based broadcast protocol provides
secrecy.
Proof. (sketch) Assume that the isogeny-based
broadcast protocol does not provide secrecy: then
there is a probabilistic polynomial algorithm A that
can distinguish whether K is the shared key or
a random element. One can then show that the
SSDDH problem can be solved using A; that is,
we obtain a sample (E, E
A
1
, {φ
A
1
(P
2
),φ
A
1
(Q
2
)}, E
A
n
,
{φ
A
n
(P
1
),φ
A
n
(Q
1
)}, j) from the oracle of SSDDH,
and distinguish whether j = j(E
A
1
A
n
) using the A.
Indeed, from the sample above, we can calculate
the sample for A:
(E,{E
A
1
}
n
i=1
,{φ
A
i
(P
ι−1
),φ
A
i
(Q
ι−1
)}
n
i=1
,
{φ
A
i
(P
ι+1
),φ
A
i
(Q
ι+1
)}
n
i=1
,{X
i
}
n
i=1
)
and calculate K. Then,
(
if j = j(E
A
1
A
n
), K is true shared key.
otherwise, K is random element.
Thus, A can distinguish whether j = j(E
A
1
A
n
).
5 COMPARISON
In this section, we compare theoretical and
experimental costs of the five protocols described in
Section 3.
Table 1 shows the theoretical costs of the GKE
protocols. To compare the actual performance,
we implemented the five protocols. We conducted
SECRYPT 2021 - 18th International Conference on Security and Cryptography
512
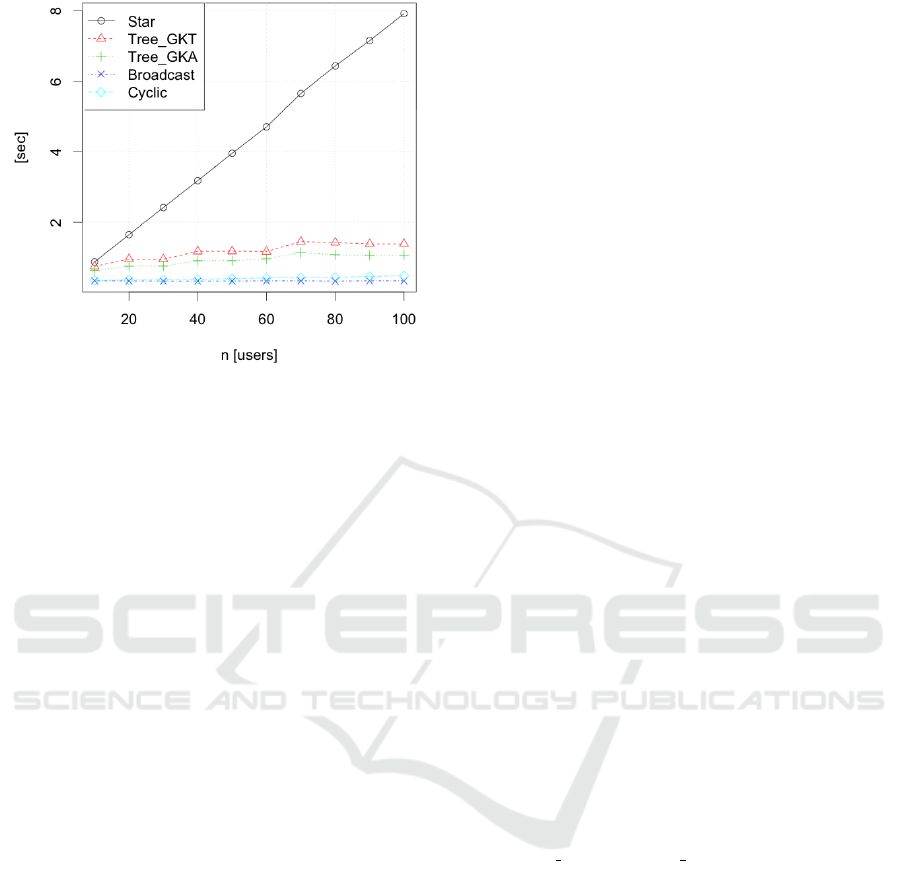
Figure 6: Experimental performance results (seconds).
experiments in one ordinary desktop PC (iMac 2017,
3.4 GHz Intel Core i5) and simulated the total
computation time, from the time when the GKE runs
to the time when all members obtain the group key.
Note that the results do not include the time for
communication. We show the experimental timing
results in Figure 6.
6 CONCLUSION
We described five types of post-quantum GKE
protocols based on SIDH. They were defined by
modifying the classical GKE protocols based on
Diffie-Hellman key exchange proposed by Burmester
and Desmedt (Star, Broadcast and Cyclic GKE) and
Kim et al. (Tree GKE). We theoretically analysed
the computational costs, and also measured their
experimental costs with a simple implementation.
The results of our simulation indicate that all
protocols, with exception of the isogeny-based star
GKT protocol, are feasible in only 2 seconds for n =
10, 20, ..., 100 users. The experiments also confirms
that the isogeny-based broadcast GKA protocol is the
most efficient (it takes less than 0.5 seconds in our
experiments).
REFERENCES
Barnes, R., Beurdouche, B., Millican, J., Omara, E.,
Cohn-Gordon, K., and Robert, R. (2020). The
Messaging Layer Security (MLS) Protocol. Internet-
Draft draft-ietf-mls-protocol-11, Internet Engineering
Task Force. Work in Progress.
Bellare, M., Singh, A. C., Jaeger, J., Nyayapati, M., and
Stepanovs, I. (2017). Ratcheted encryption and key
exchange: The security of messaging. In Katz, J. and
Shacham, H., editors, CRYPTO 2017, pages 619–650.
Burmester, M. and Desmedt, Y. (1994). A secure
and efficient conference key distribution system.
In Workshop on the Theory and Application of
Cryptographic Techniques, pages 275–286. Springer.
Burmester, M. and Desmedt, Y. (2005). A secure and
scalable group key exchange system. Information
Processing Letters, 94(3):137–143.
Childs, A., Jao, D., and Soukharev, V. (2014). Constructing
elliptic curve isogenies in quantum subexponential
time. Journal of Mathematical Cryptology, 8:1–29.
Cohn-Gordon, K., Cremers, C., and Garratt, L. (2016).
On post-compromise security. In 2016 IEEE 29th
Computer Security Foundations Symposium (CSF),
pages 164–178.
Cohn-Gordon, K., Cremers, C., Garratt, L., Millican, J.,
and Milner, K. (2018). On ends-to-ends encryption:
Asynchronous group messaging with strong security
guarantees. In CCS ’18, pages 1802–1819. ACM.
Furukawa, S., Kunihiro, N., and Takashima, K.
(2018). Multi-party key exchange protocols from
supersingular isogenies. In 2018 International
Symposium on Information Theory and Its
Applications (ISITA), pages 208–212.
Herzberg, A. and Leibowitz, H. (2016). Can johnny finally
encrypt?: Evaluating e2e-encryption in popular im
applications. In Proceedings of the 6th Workshop on
Socio-Technical Aspects in Security and Trust, STAST
’16, pages 17–28. ACM.
Jao, D. and De Feo, L. (2011). Towards quantum-
resistant cryptosystems from supersingular elliptic
curve isogenies. In Yang, B.-Y., editor, Post-Quantum
Cryptography, pages 19–34.
Kim, Y., Perrig, A., and Tsudik, G. (2004). Tree-
based group key agreement. ACM Transactions on
Information and System Security (TISSEC), 7(1):60–
96.
Microsoft Community (2018). Skype insider
preview, private conversations. https:
//answers.microsoft.com/en-us/skype/forum/
skype insiderms-skype insnewsms.
National Institute of Standards and Technology (2020).
Post-quantum cryptography. https://csrc.nist.gov/
Projects/Post-Quantum-Cryptography.
Open Whisper Systems (2018). Signal partners with
microsoft to bring end-to-end encryption to skype.
https://signal.org/blog/skype-partnership.
Perrin, T. and Marlinspike, M. (2016). The double ratchet
algorithm. https://signal.org/docs/specifications/
doubleratchet/doubleratchet.pdf.
R
¨
osler, P., Mainka, C., and Schwenk, J. (2018). More
is less: On the end-to-end security of group chats
in Signal, WhatsApp, and Threema. In 2018 IEEE
European Symposium on Security and Privacy (Euro
S & P), pages 415–429.
Rostovtsev, A. and Stolbunov, A. (2006). Public-key
cryptosystem based on isogenies. Cryptology ePrint
Archive, Report 2006/145. https://eprint.iacr.org/
2006/145.
A Comparison of GKE Protocols based on SIDH
513

Silverman, J. H. (1986). The Arithmetic of Elliptic Curves,
volume 106 of Graduate Texts in Mathematics.
Springer.
Steiner, M., Tsudik, G., and Waidner, M. (1996).
Diffie-hellman key distribution extended to group
communication. CCS ’96, pages 31–37. ACM.
Tanada, S., Suzuki, H., Naito, K., and Watanabe, A.
(2016). Proposal for secure group communication
using encryption technology. In Mobile Computing
and Ubiquitous Networking (ICMU), 2016 Ninth
International Conference on, pages 1–6. IEEE.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
514
