
BLT+L: Efficient Signatures from Timestamping and Endorsements
Denis Firsov
1,2 a
, Henri Lakk
1 b
, Sven Laur
3 c
and Ahto Truu
1 d
1
Guardtime, A. H. Tammsaare tee 60, 11316 Tallinn, Estonia
2
Tallinn University of Technology, Tallinn, Estonia
3
University of Tartu, Tartu, Estonia
Keywords:
Digital Signatures, Timestamping, Hash Functions, Endorsements.
Abstract:
We propose a new digital signature scheme based on combining cryptographic timestamping with an endorse-
ment scheme, both of which can be constructed from one-way and collision-resistant hash functions. The
signature scheme is efficient and allows balancing of key generation and signing time for signature size and
verification time. The security analysis is based on a realistic model of timestamping. As part of our construc-
tion, we introduce the novel concept of endorsements, which may be of independent interest.
1 INTRODUCTION
In server-assisted digital signature schemes, sign-
ers can’t produce signatures on their own, but
have to co-operate with servers. Historically, the
two main motivations for such schemes have been:
(a) performance—costly computations can be of-
floaded from an underpowered device to a more ca-
pable server; and (b) security—risks of key misuse
can be reduced by either keeping the keys in a server
environment (which can presumably be managed bet-
ter than an end-user’s personal device) or having the
server perform additional checks (such as getting out-
of-band confirmations) as part of the signature gener-
ation protocol.
A trivial solution would be to just let the server
handle the signing operations based on requests from
the users, but then the server would have to be com-
pletely trusted. To address this, Asokan et al. pro-
posed a method where a user can prove the server’s
misbehavior when presented with a signature that
the server created without the user’s request (Asokan
et al., 1997). However, such signatures appear valid
to a verifier until challenged by the signer. Thus, this
protocol is usable in contexts where a dispute reso-
lution process exists, but unsuitable for applications
with immediate and irrevocable effects, such as au-
thentication for access control purposes or commit-
a
https://orcid.org/0000-0003-1267-7898
b
https://orcid.org/0000-0001-8356-2540
c
https://orcid.org/0000-0002-9891-3347
d
https://orcid.org/0000-0001-7427-5005
ting transactions to append-only ledgers. This also
applies to later improvements of the approach (Bi-
cakci and Baykal, 2004; Goyal, 2004).
Several methods have been proposed for outsourc-
ing the more expensive computation steps of specific
signature algorithms, notably RSA, but most early
schemes have been shown to be insecure. Due to
increasing computational power of handheld devices
and wider availability of hardware-accelerated imple-
mentations, attention has now shifted to splitting keys
between end-user devices and back-end servers to im-
prove the security of the private keys (Camenisch
et al., 2016; Buldas et al., 2017a).
Motivated by the legally binding electronic signa-
ture use case and the lack of post-quantum security
of underlying algebraic signature schemes Buldas,
Laanoja, and Truu recently constructed the new type
of server-assisted hash-based signature schemes (BLT
schemes in the following) from backdating resistant
cryptographic timestamping (Buldas et al., 2017b;
Buldas et al., 2018; Buldas et al., 2019). Their pro-
tocols produce small signatures with efficient signing
and verification, but suffer from expensive key gener-
ation.
In this work, we propose the BLT+L signature
scheme that improves on their results as follows:
• In contrast with the existing BLT schemes, where
key generation phase is expensive by design, our
BLT+L scheme defers the key generation costs;
additionally, the BLT+L scheme is a framework
that allows key generation and signing time to be
balanced for signature size and verification time,
Firsov, D., Lakk, H., Laur, S. and Truu, A.
BLT+L: Efficient Signatures from Timestamping and Endorsements.
DOI: 10.5220/0010530000750086
In Proceedings of the 18th International Conference on Security and Cryptography (SECRYPT 2021), pages 75-86
ISBN: 978-989-758-524-1
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
75

depending on the priorities of the use case.
• Our security analysis is based on a more realis-
tic model of timestamping. In particular, we han-
dle the need for timestamping aggregation lay-
ers which improve the performance of hash-then-
publish timestamping services. In our analysis,
we assume only the publisher to be trusted while
treating the aggregation layers as black-box and
potentially adversarial.
• We carry out our construction and security analy-
sis in the concurrent model and explicitly account
for network delays that may be controlled by the
adversary.
To support our constructions, we developed the notion
of endorsement schemes, which may be of indepen-
dent interest. Endorsements (Sect. 3) share similari-
ties with signatures and accumulators, and can be con-
structed from either of those. However, endorsements
have strictly weaker security requirements, and there-
fore allow more efficient specialized constructions.
2 BACKGROUND
Definition 2.1. A signature scheme is a triple
of probabilistic polynomial-time (PPT) algorithms
(G
S
,S
S
,V
S
), where G
S
is a key pair generation al-
gorithm, S
S
a signing algorithm, and V
S
a signature
verification algorithm.
The signature scheme is correct if the algorithm
V
S
agrees with S
S
for all valid key pairs and messages:
Pr [(pk,sk) ← G
S
: V
S
(pk,S
S
(sk, m), m) = 1] = 1.
The signature scheme is existentially unforgeable un-
der the chosen message attack (EUF-CMA) if the
probability
Pr
(pk,sk) ← G
S
, (s,m) ← A
S
S
(sk,·)
(pk) :
V
S
(pk,s,m) = 1, m /∈ S
S
.log
is negligible for any PPT adversary A. That is, A has
negligible chance of winning the following game:
• The environment generates a key pair (pk,sk).
• The adversary learns the public key pk and gets
access to a signing oracle S
S
which contains the
secret key sk. The adversary is then allowed to
query the oracle for signatures on messages of his
choice. The oracle S
S
keeps an internal variable
log which records the queries.
• The adversary wins if the produced signature-
message pair (s, m) verifies and the message m is
fresh (was not previously submitted to the oracle).
In a one-time signature scheme (OTS), a secret key
can be used to sign at most one message and key re-
use may result in catastrophic security loss. In a state-
ful scheme, the signer has an internal state that must
be updated by the signing algorithm; rolling back to
an earlier state may result in security loss. A signature
scheme is server-assisted if the signer needs support
of an external service to generate signatures.
For an offline and stateless signature scheme,
its security in sequential computational model im-
plies also security in concurrent setting. The situa-
tion is different in case of server-assisted signature
schemes, since adversaries could take advantage of
asynchronous calls to the server and combine infor-
mation from different execution threads.
In this work, we build a signature scheme assisted
by a timestamping service (cf. Sec. 2.1) and this
motivates us to interpret the existential unforgeabil-
ity stated in Def. 2.1 in the concurrent model. More
specifically, we assume that the adversary can call
the signing oracle asynchronously and also manipu-
late network delays between the signer and the times-
tamping service.
Definition 2.2. A message authentication code
(MAC) is a triple of PPT algorithms (G
M
,S
M
,V
M
),
where G
M
is a key generation algorithm, S
M
a tag-
ging algorithm, and V
M
a tag verification algorithm.
Similarly to a signature scheme, a MAC is correct if
Pr [sk ← G
M
: V
M
(sk, S
M
(sk, m), m) = 1] = 1
and existentially unforgeable under the chosen mes-
sage attack (EUF-CMA) if
Pr
sk ← G
M
, (s,m) ← A
S
M
(sk,·)
:
V
M
(sk, s, m) = 1, m /∈ S
M
.log
is negligible for any PPT adversary A.
Definition 2.3. A cryptographic accumulator A is
a quadruple (G
A
,D
A
,P
A
,V
A
) of PPT algorithms,
where G
A
outputs a public key pk, D
A
(pk,S) com-
putes a digest (compressed representation) of the set
S, P
A
(pk,S,m) outputs a membership proof p of m
in S, and V
A
is a membership verification algorithm,
so that V
A
(pk,D
A
(pk,S),P
A
(pk,S,m),m) outputs 1 if
m ∈ S, and 0 if m /∈ S. The accumulator is collision-
resistant if the following probability is negligible for
any PPT adversary A:
Pr
pk ← G
A
, (S, p,m) ← A(pk) :
V
A
(pk,D
A
(pk,S), p,m) = 1, m /∈ S
.
Definition 2.4. A hash function h : D → R is preimage
resistant (one-way) if the probability
Pr
h
x
$
← D, x
0
← A(h(x)) : h(x
0
) = h(x)
i
is negligible for any PPT adversary A.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
76

Definition 2.5. A family H of hash functions is col-
lision resistant if the probability
Pr
h
h
$
← H , (x
1
,x
2
) ← A(h) : x
1
6= x
2
, h(x
1
) = h(x
2
)
i
is negligible for any PPT adversary A.
2.1 Cryptographic Timestamping
Cryptographic timestamping allows users to prove
that some data existed at some moment in the past.
Haber and Stornetta introduced the first protocol
which did not rely on trusted service providers. They
proposed a scheme where each timestamp would in-
clude a hash of the immediately preceding one and a
reference to the immediately succeeding one (Haber
and Stornetta, 1991). Benaloh and de Mare showed
how to increase the efficiency by operating in rounds,
where the messages to be timestamped within one
round would be aggregated into an accumulator (Be-
naloh and de Mare, 1991).
All bounded binding commitment schemes
(D
C
,T
C
,V
C
) can be used to construct timestamping
services. Practical instantiations of such services
usually involve a timestamping aggregation server X
and a publisher P . It is assumed that the publisher
is an append-only trusted party whose resources are
limited and very expensive (e.g., public blockchain,
newspaper, etc.). Module 1 presents an ideal imple-
mentation of publisher which keeps the current time
value in variable t and m is a mapping of previous
time values to data items.
The server X operates in rounds. During each
round, it collects requests y
1
,...,y
n
from the users.
When the t-th round is over, X computes the digest
d
t
← D
C
(y
1
,...,y
n
) and sends it in an authenticated
manner to P , who then makes it public. After that,
X computes certificates (c
1
,...,c
n
) ← T
C
(y
1
,...,y
n
)
and issues (t, c
i
) as a timestamp for y
i
. Intuitively,
this proves that y
i
existed at the time t when d
t
was published. To verify a timestamp (t, c) on y,
the user queries the publisher for digest d
t
and runs
V
C
(d
t
,c,y). Note that for this scenario to be practical,
the digest must be reasonably small.
In this work, we will be interested in times-
tamping servers based on bounded and binding tag-
commitment schemes, where each committed input is
accompanied by a user-chosen tag value.
Definition 2.6. A tag-commitment scheme C consists
of a triple of PPT algorithms (D
C
,T
C
,V
C
):
• D
C
((a
1
,x
1
),...,(a
n
,x
n
)) outputs a digest d which
is a compressed representation of its input. The
input to D
C
consists of data items x
i
, each paired
with a tag a
i
. If the input list contains multiple x’s
for a tag a, the first such pair is kept and remaining
ones are ignored.
• T
C
((a
1
,x
1
),...,(a
n
,x
n
)) outputs (c
1
,...,c
n
),
where c
i
is a certificate (opening) for the pair
(a
i
,x
i
).
• V
C
(d, c, (a, x)) checks whether the certificate c is
a valid proof of inclusion of the pair (a,x) in the
digest d.
The tag-commitment scheme is binding if any PPT
adversary A is unable to open the item associated with
the tag a in two different ways, i.e., the following
probability is negligible:
Pr
(d, a, c
1
,x
1
,c
2
,x
2
) ← A : x
1
6= x
2
,
V
C
(d, c
1
,(a,x
1
)) = V
C
(d, c
2
,(a,x
2
)) = 1
.
The tag-commitment scheme is bounded if every di-
gest d contains a natural d
b
which limits the number
of elements in it. The opening c is valid for (a,x) iff
V
C
(d, c, (a, x)) = 1 and loc(a) ≤ d
b
, where loc(·) is a
fixed injective mapping to naturals.
Module 1: Publisher implementation.
1: module P
2: var t : N, m : map
3: fun publish(t
0
,d) = {
4: if t < t
0
then
5: t ← t
0
6: m[t] ← d
7: end if
8: }
9: fun get(t) = {return m[t]}
10: end
If a timestamping server X is built from a tag-
commitment scheme then each request it serves must
be a tuple y = (a,x), where a is a user-picked tag and
x is the document to be timestamped.
We consider the model where the commitment
scheme C = (D
C
,T
C
,V
C
) is publicly known and the
publisher P is a trusted party with limited and expen-
sive resources, but the server X which implements
the scheme C is black-box and possibly adversarial.
Moreover, the server potentially receives a large num-
ber of queries per round from multiple users and then
every user only gets the timestamps for her queries
and does not see the queries the other users submitted
in that round. As a result, the user has no way of ver-
ifying that the server is honest and publishes digests
which are indeed computed by D
C
. The last point
makes it non-trivial to formally define the security of
timestamping services.
The main security property associated with times-
tamping servers is backdating resistance. Buldas
BLT+L: Efficient Signatures from Timestamping and Endorsements
77

and Laur studied different variations of this property
to capture the idea that once a user of timestamp-
ing server receives a timestamp on her “fresh” docu-
ment and the associated digest is reliably published,
then no adversary will be able to present a times-
tamp for “similar” document and earlier time (Bul-
das and Laur, 2006). We skip the technical defini-
tion of backdating resistance, but mention that every
bounded binding commitment scheme induces a se-
cure backdating resistant timestamping service (Bul-
das and Laur, 2007). For our purposes, we only need
the binding property of the underlying bounded tag-
commitment schemes.
3 ENDORSEMENT SCHEME
Endorsement scheme is a novel concept motivated by
the design of the BLT+L signature scheme. The main
goal of endorsement schemes is to allow users to au-
thenticate (or endorse) elements from a public list M.
If M is reasonably small then an obvious solution is
to include M into the public key of the user. This ap-
proach is not practical if M is large.
Each BLT+L key pair includes an activation and
an expiration time. The design of BLT+L requires the
user to authenticate a tuple of hash values for each
time slot (i.e., round of timestamping service) within
the entire lifespan of a key pair. Hence, if the round
duration of the timestamping server is one second,
and we need to generate a key pair with a lifespan of
ten years then |M| > 3 · 10
8
and announcing M as part
of the public key is not a feasible solution. Instead, we
propose an endorsement scheme which comes with its
own succinct public key and can be used to endorse
elements of the list M.
Definition 3.1. An endorsement scheme E is a triple
of PPT algorithms (G
E
,E
E
,V
E
), where for any input
list M:
• G
E
(M) is a key-generation algorithm that pro-
duces a public key pk and a secret key sk.
• E
E
(sk, M,t) is an endorsement-generation algo-
rithm that, given as input the secret key sk, the
list M, and an index 1 ≤ t ≤ |M|, produces an en-
dorsement of message M
t
.
• V
E
(pk,e,m,t) is a verification algorithm that,
given a public key pk, an endorsement e, a mes-
sage m, and an index t, returns either 0 or 1.
The endorsement scheme is correct if V
E
agrees with
E
E
for all valid inputs:
Pr
(pk,sk) ← G
E
(M), t ← {1, ..., |M|} :
V
E
(pk,E
E
(sk, M,t),M
t
,t) = 1
= 1.
The endorsement scheme is collision-resistant if the
following probability is negligible for any PPT adver-
sary A:
Pr
M ← A, (pk,sk) ← G
E
(M),
(e,m,t) ← A
E
E
(sk,M,·)
(pk) :
V
E
(pk,e,m,t) = 1, 1 ≤ t ≤ |M|, m 6= M
t
.
Here, A chooses the list M and then receives the public
key pk, and access to the oracle E
E
initialized with
the secret key sk and the list M. The adversary then
tries to produce an endorsement e, a message m, and
an index t which verify with pk, so that M
t
exists, but
m is different from it.
Theorem 3.1. Every collision-resistant accumula-
tor A gives rise to a collision-resistant endorsement
scheme E as follows:
• G
E
(M): Generate the public key of A by pk ←
G
A
. Compute the digest d ← D
A
(pk,M
0
), where
M
0
= {(t,M
t
) : 1 ≤ t ≤ |M|}. Return (pk,d) as the
public key and pk as the “secret” key.
• E
E
(pk,M,t) := P
A
(pk,M
0
,M
0
t
).
• V
E
((pk,d), e,m,t) := V
A
(pk,d, e,(t, m)).
It is straightforward to verify that whenever the adver-
sary breaks collision resistance of the accumulator-
induced endorsement scheme, he also breaks collision
resistance of the underlying accumulator.
The main disadvantage of accumulators is that the
computations can become inefficient for large lists.
For example, Merkle trees (Merkle, 1979) are hash-
based collision-resistant accumulators, but the com-
plexities of public key and inclusion proof genera-
tion are proportional to the size of M, which is pro-
hibitively slow for the BLT+L use case.
Every signature scheme also induces an endorse-
ment scheme in a trivial way. However, the security
requirement, namely collision-resistance, associated
with endorsements is much lighter than the existential
unforgeability of signatures, and we expect specifi-
cally designed endorsements to be more efficient than
the more general signatures or commitments.
3.1 Goldreich-Merkle Endorsement
Goldreich proposed a stateless many-time signature
scheme (GSS) using a binary authentication tree (cf.
Sec. 6). Here we combine the top-down (assuming
root is “up”) authentication mechanism of Goldreich
signatures with the bottom-up mechanism of Merkle
trees to design an efficient and secure hash-based en-
dorsement scheme.
More specifically, we build a tree with two types
of inner nodes: a Goldreich node has an associated
OTS key pair and authenticates its children with a
SECRYPT 2021 - 18th International Conference on Security and Cryptography
78
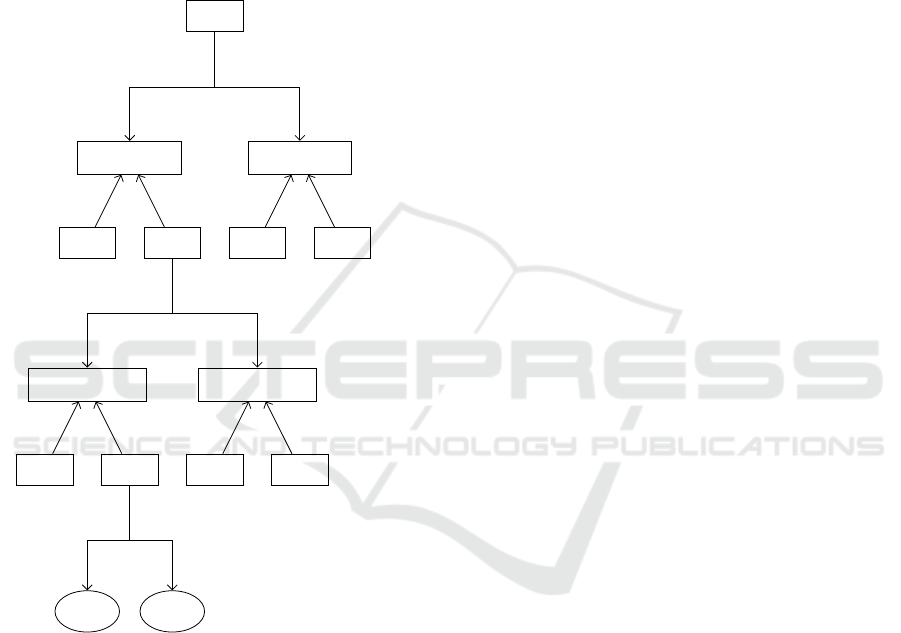
one-time signature; a Merkle node authenticates its
children with a hash value of their concatenation.
We then define the Goldreich-Merkle endorsement
scheme based on a complete binary tree where all
nodes are numbered top-down left-to-right and leaves
contain the elements of M. It should be easy to see
that to accommodate |M| leaves, the tree must have
2|M| − 1 nodes in total, so the height of such a tree is
dlog
2
(|M|)+1e, and M
t
is located in the node number
t + |M| − 1.
pk
1
s
1
:= S
Ω
(sk
1
,(pk
2
, pk
3
))
h(pk
4
, pk
5
)
pk
2
:=
pk
4
pk
5
s
5
:= S
Ω
(sk
5
,(pk
10
, pk
11
))
h(pk
20
, pk
21
)
pk
10
:=
pk
20
pk
21
s
21
:= S
Ω
(sk
21
,(M
11
,M
12
))
M
11
M
12
h(pk
22
, pk
23
)
pk
11
:=
pk
22
pk
23
h(pk
6
, pk
7
)
pk
3
:=
pk
6
pk
7
Figure 1: The tree slice needed to endorse M
11
and M
12
.
Definition 3.2. Let Ω be a one-time signature scheme
and H a hash function family. Fix a coloring function
f : N → {G, M}. The Goldreich-Merkle endorsement
scheme induced by Ω, H , and f is defined as follows.
Key Generation. Pick a hash function h ← H . Gen-
erate a list K of 2|M| − 1 tuples (pk
i
,sk
i
), where
(pk
i
,sk
i
) ←
(M
i−(|M|−1)
,⊥) if i ≥ |M|,
(h(pk
2i
, pk
2i+1
),⊥) if f (i) = M,
G
Ω
if f (i) = G.
The public key of the endorsement scheme is
(pk
1
,|M|,h) and the secret key is K, which is the list
of the tree nodes. The coloring function defines which
of the inner nodes of the endorsement tree are Goldre-
ich nodes and which are Merkle nodes, and presents
an optimization opportunity, as discussed in Sec. 5.
Endorsing. To endorse the t-th element of the list
M, construct the authentication path from the root of
the endorsement tree to the leaf containing M
t
. For
every Goldreich node i on the path, add to the en-
dorsement its public key pk
i
, the one-time signature
S
Ω
(sk
i
,(pk
2i
, pk
2i+1
)), and pk
j
of the child j (where
j = 2i or j = 2i + 1) that is not on the path to M
t
. For
every Merkle node i on the path, add pk
j
of the child
j that is not on the path to M
t
.
Verification. To verify the triple (e,m,t) with respect
to the public key (pk
0
,|M|,h), where pk
0
is the public
key of the root of the endorsement tree, first check
that 1 ≤ t ≤ |M|. Next, verify that e represents the
path going from the root to the node t + |M| − 1 in
the complete binary tree with 2|M| −1 nodes using h.
Then, verify that every node in e is authenticated by
its parent node. Finally, check that the public key in
the first element in e is pk
0
.
Example. Let |M| = 32. Then Fig. 1 illustrates
the tree slice needed to endorse the message M
12
.
The authentication tree is based on coloring func-
tion which assigns Goldreich type to nodes at odd
levels and Merkle type to nodes at even levels.
The resulting endorsement consists of the following
records: (pk
1
,s
1
, pk
3
), (pk
4
), (pk
5
,s
5
, pk
11
), (pk
20
),
and (pk
21
,s
21
,M
11
). This can be verified against
(pk
0
,|M|,h) bottom-up as follows:
• check that V
Ω
(pk
21
,s
21
,(M
11
,M
12
)) = 1;
• compute pk
10
← h(pk
20
, pk
21
);
• check that V
Ω
(pk
5
,s
5
,(pk
10
, pk
11
)) = 1;
• compute pk
2
← h(pk
4
, pk
5
);
• check that V
Ω
(pk
1
,s
1
,(pk
2
, pk
3
)) = 1;
• check that pk
1
= pk
0
.
Theorem 3.2. Let Ω be a one-time signature scheme
and H a collision-resistant hash function family.
Then for any adversary A and list M, the probabil-
ity of A breaking collision-resistance of the induced
Goldreich-Merkle endorsement scheme does not ex-
ceed p
H
+ p
Ω
·w, where p
H
is the adversary’s proba-
bility of breaking collision resistance of H , p
Ω
the ad-
versary’s probability of breaking existential unforge-
ability of Ω, and w is the number of Goldreich nodes
in the authenticaton tree.
3.2 Lazy Evaluation and Caching
The storage complexity of the entire Goldreich-
Merkle endorsement tree can be very high. However,
BLT+L: Efficient Signatures from Timestamping and Endorsements
79

only a slice of the tree is needed to produce an en-
dorsement. The exact size of the slice is determined
by the underlying coloring function (see Sec. 5).
Also, note that the key generation phase of the
Goldreich-Merkle endorsement scheme requires the
user to populate the list K (i.e., secret key) with OTS
key pairs computed by G
Ω
. To defer the cost of key
generation, the elements of the list K may be lazily
evaluated on demand from a pseudo-random function
(PRF). More specifically, during the key generation
phase instead of producing all entries of the secret
key K we only compute the key pair associated with
the root node of the endorsement tree. The remaining
keys are evaluated on demand during the endorsing
phase.
On the other hand, the key pairs of the nodes
which are close to the root of the authentication tree
are needed frequently, and it may be more efficient to
pre-generate and cache them, as discussed in Sec. 5.
4 BLT+L SIGNATURE SCHEME
The main idea behind the BLT+L signature scheme is
to sign messages by timestamping them together with
time-related tags. We must take into account that a
client device may send multiple asynchronous times-
tamping requests at time t and the responses can ar-
rive in any order and may be associated with differ-
ent times of the form t + `, where ` is an adversary-
controlled lag (network delay).
Throughout the lifespan of a BLT+L key pair, the
scheme uses many one-time key pairs (pk
i
,sk
i
), one
for each round of the timestamping service. To toler-
ate network lags up to L rounds, we let each user have
a list of tuples of the form sk
i
= (r
0
i
,...,r
L
i
) as the se-
cret key and a list of tuples pk
i
= (h(r
0
i
),...,h(r
L
i
))
as the public key, where each r
j
i
is sampled from an
unpredictable distribution, and i corresponds to a time
when the key should be usable for signing.
To sign a message m at time t, timestamp the hash
h(m) under the tag r
0
t
. If the timestamp on h(m) is
c and the respective digest d was published by P at
time t + ` then reveal the `-th component of the tuple
sk
t
, namely r
`
t
, and let the signature be (t,`,c,r
0
t
,r
`
t
).
To verify such a signature, the user must query
the publisher d ← P .get(t + `), verify the timestamp
by checking that V
C
(d, c, (r
0
t
,h(m))) = 1, and verify
the tokens r
0
t
and r
`
t
against the public key component
pk
t
= (pk
0
t
,..., pk
L
t
) by checking that h(r
0
t
) = pk
0
t
and
h(r
`
t
) = pk
`
t
.
The signature scheme described above is secure,
but if we want the key pair to have the lifespan of n
timestamping rounds then both sk and pk must con-
tain n of the L + 1-element tuples, which would make
the size of the key pair proportional to its lifespan.
This problem can be solved by generating the ele-
ments of sk and pk on demand from a PRF and using
an endorsing mechanism on the list pk.
Another complication is that since we have only
one tag for every time t, namely r
0
t
, then the described
signature scheme can sign no more than one message
per round of the timestamping service. We solve this
complication by introducing an aggregator service.
Definition 4.1. Let X be a timestamping service
based on the tag-commitment scheme C . We say that
Q is an aggregator for X if it offers the put query
implemented in the following way:
• Q is based on accumulator scheme A and the re-
spective public-key is pk
Q
.
• Q works in rounds.
• During a round the aggregator receives from users
tagged messages (a,m
1
),(a,m
2
),...
• Once the round ends, the pairs are accumulated
into sets S
a
,S
b
,..., where the set S
x
contains all
the messages which were paired with the tag x.
• Q timestamps the tagged digests of the accumu-
lators (a,D
A
(S
a
)),(b,D
A
(S
b
)),... with X and re-
ceives respective timestamps (t,c
a
),(t,c
b
),...
• Finally, the user who sent the request (a, m) re-
ceives the triple (t, c
a
,S
a
), where (t, c
a
) is the
timestamp on D
A
(S
a
).
In practical deployments, the aggregator can be im-
plemented as an independent server, as part of the
client’s software, or be coupled with the timestamp-
ing service. In our security model, we assume that it
is black-box and therefore potentially adversarial.
Now, we are ready to put it all together and define
the BLT+L signature scheme.
Definition 4.2. Let U be a uniform unpredictable dis-
tribution, H a hash function family, E an endorse-
ment scheme, Q an aggregator (based on an accu-
mulator A) for the timestamping service X (based
on a tag-commitment scheme C ), and M a message
authentication code (MAC). They induce the BLT+L
signature scheme as follows:
Key Generation. The key generation algorithm re-
ceives the parameters C, E, and L, where C is the time
from which the key pair is active, E is the number of
rounds of X until the key pair expires, and L is the
highest tolerable network delay. The key pair is gen-
erated as follows:
1. Generate a MAC key sk
M
← G
M
.
2. Sample r
j
i
$
← U for 0 ≤ i < E and 0 ≤ j ≤ L.
3. Sample a hash function h from H .
SECRYPT 2021 - 18th International Conference on Security and Cryptography
80
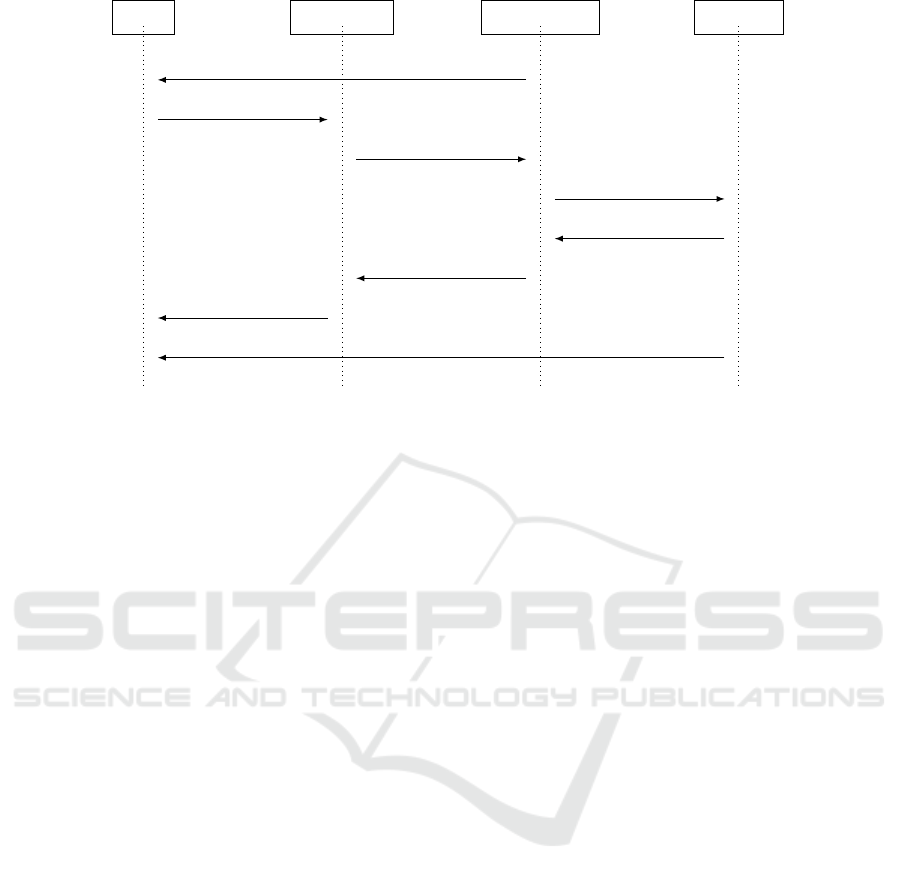
Client
Timestamper
Aggregator
Publisher
t
(a,m
1
),(a,m
2
),...
(a,D
A
(S
a
)),...
d
t
0
t
0
,c
t
0
,c,S
a
d
Figure 2: Data flows of the BLT+L signing process.
4. Generate an endorsement scheme key pair
(pk
E
,sk
E
) ← G
E
(M), where M is a list such that
M
i
= (h(r
0
i
),...,h(r
L
i
)) for 0 ≤ i < E.
5. Store the tuple (sk
M
,sk
E
,r) as the secret key, and
make (pk
E
,h,C, E,L) available as the public key.
Signing. To sign a message m:
1. Query the time t ← X .clock.
2. If C ≤ t < C + E then set i ← t −C else abort.
3. Compute the endorsement e ← E
E
(sk
E
,M,i) on
M
i
.
4. Compute the MAC p ← S
M
(sk
M
,h(m)) on the
hash of m.
5. Send a request to the aggregator Q and receive the
triple (t
0
,c,S) ← Q .put(r
0
i
,h(m)kp).
6. Verify that t < t
0
≤ t + L; then query the di-
gest d ← P .get(t
0
) for time t
0
; then verify that
V
C
(d, c, (r
0
i
,D
A
(S))) = 1 and h(m)kp ∈ S.
7. Verify that each element in S has a valid MAC
according to V
M
(sk
M
,·).
8. Output (e,M
i
,i,`,r
0
i
,r
`
i
,c,q,z, p) as the signa-
ture on m, where ` = t
0
− t, q = D
A
(S), z =
P
A
(pk
Q
,S,h(m)kp), where pk
Q
is the public key
of the aggregator Q .
Verification. To verify the message m against the sig-
nature (e,w,i,`,a,r,c,q,z, p) with respect to the pub-
lic key (pk
E
,h,C, E,L):
1. If V
E
(pk
E
,e,w, i) 6= 1 then return 0.
2. If ` ≤ 0 or ` > L then return 0.
3. Set t ← C + i and t
0
← t + `; if t < C or t ≥ C + E
then return 0.
4. If w
0
6= h(a) or w
`
6= h(r) then return 0.
5. Query the digest d ← P .get(t
0
) for time t
0
; if
V
C
(d, c, (a, q)) 6= 1 then return 0.
6. If V
A
(q,z,h(m)kp) 6= 1 then return 0.
7. Otherwise, return 1.
Fig. 2 shows the data flows of the signing process.
Note that the timestamping server and BLT+L ag-
gregators do not need to accumulate any data for
long-term storage and are only expected to receive
and compress the user queries into respective digests
which is then sent for a long-term storage to a pub-
lisher. The computational complexity of the user is
analyzed in Sec. 5.
4.1 Security Analysis
Theorem 4.1. Let X be a black-box timestamping
service based on tag-commitment scheme C and pub-
lishing its digests via the publisher P . Let Q be a
black-box aggregator based on accumulator scheme
A timestamping accumulators (A digests) via X . If
the highest tolerable network delay is L and the life-
span of the key pair is E then for any adversary the
probability of breaking the existential unforgeability
of BLT+L in asynchronous setting does not exceed
p
C
+ p
E
+ p
A
+ p
M
+ p
H
+ E · (L + 1) · p
0
H
,
where p
C
is the probability of breaking the bind-
ing property of C , p
E
the probability of breaking
collision-resistance of the endorsement scheme E,
p
A
the probability of breaking collision-resistance of
A, p
M
the probability of breaking unforgeability of
the MAC scheme M , p
H
the probability of break-
ing collision-resistance of the hash-function family
H , and p
0
H
the probability of breaking preimage re-
sistance of H .
BLT+L: Efficient Signatures from Timestamping and Endorsements
81

Proof. Let the public key be (pk
E
,h,C, E,L) and the
secret key (sk
M
,sk
E
,r). Let A be an adversary who
presents a BLT+L forgery (e,w,i,`,a,r, c, q, z, p) for a
fresh message m. Let t ← C + i and t
0
← t + ` when
we analyze the following cases:
• If w 6= M
i
then A must have broken collision resis-
tance of the endorsement scheme E.
• If w = M
i
, but a 6= r
0
t
or r 6= r
`
t
, then A broke col-
lision resistance of the hash function family H .
• The remaining analysis is for the case when w =
M
i
, a = r
0
t
, and r = r
`
t
.
– Let Q = {m
1
,...,m
k
} be the set of messages
that the adversary submitted to the signing ora-
cle at time t and Z ⊆ Q be the subset of Q for
which the signing oracle successfully finalized
the signatures corresponding to time t
0
.
– If Q is empty then A broke preimage resistance
of h, as he observed h(r
0
t
) and found the pre-
image a.
– If Z is empty then also A broke preimage resis-
tance of h, as he observed h(r
`
t
) and found the
preimage r.
– Otherwise, pick a message m
j
∈ Z and let S
j
be
the list of messages with which the aggregator
Q replied to the put query of the signing oracle.
– If q 6= D
A
(S
j
) then A broke the binding prop-
erty of the tag-commitment scheme C .
– If q = D
A
(S
j
) and h(m)kp /∈ S
j
then A broke
collision resistance of A.
– Otherwise, q = D
A
(S
j
) and h(m)kp ∈ S
j
and
therefore p is a valid MAC for h(m), since we
assumed that signature was finalized for m
j
.
– If the MAC p on h(m) was not generated by
the signing oracle then A broke unforgeability
of M .
– Otherwise, h(m) must equal to h(m
0
) for some
m
0
submitted to the signing oracle and therefore
m and m
0
is a collision of h.
In cases when preimage resistance of h is attacked, the
adversary has the choice of E ·(L+1) hashes to invert.
Therefore, the unforgeability of BLT+L in these cases
is upper-bounded by preimage resistance of h scaled
up by E · (L + 1).
4.2 Discussion
It is important to understand the roles and limitations
of servers in BLT+L. More specifically, the publisher
P is a trusted party with expensive resources who can
publish no more than a single (short) digest per round.
The timestamper X is a black box which produces
a digest from a large number of queries of indepen-
dent clients. The server Q aggregates tagged requests
into accumulators per tag. We assume that (P ,X )
is a widely available timestamping service. The ag-
gregator Q can be an independent server, or run on
the client device, or be coupled with the timestamp-
ing service. In the following, we highlight the main
traits of the scheme:
• The standard approach of producing legally bind-
ing signatures is to produce “cryptographic sig-
nature” first and timestamp it afterwards. The
BLT+L framework offers an alternative design
where the final signature consists of an endorse-
ment and a timestamp. We expect this design to
induce more efficient signatures since the security
property of endorsements is weaker than existen-
tial unforgeability of cryptographic signatures and
the cryptographic properties of the timestamping
are taken into account and contribute to existential
unforgeability of the resulting BLT+L signature.
• All the cryptographic primitives used in BLT+L
(including timestamping services and endorse-
ment schemes) can be constructed from secure
hash functions. In this case, we can upper-bound
the probability of existential forgery by the proba-
bility of breaking collision resistance or preimage
resistance of the hash function.
• We conjecture that BLT+L is secure in the post-
quantum setting, since our proofs do not rely on
rewinding or state-copying techniques.
• In the signing procedure, we let the user query
the current time from the adversary (timestamp-
ing service X ) to highlight that the received value
need not be correct. This means that in practice,
the user can rely on her local clock without wor-
rying whether it might be inaccurate.
• Observe that BLT+L key generation phase seems
to require a user to produce a list r containing
E ·(L +1) random values and generate an endose-
ment key pair for a list M which contains hashes
of elements of r. However, if the endorsement
key-generation algorithm G
E
(M) does not require
the values of M to be evaluated eagerly (as is the
case with the Goldreich-Merkle scheme) then the
elements of r and M can remain unevaluated un-
til they are needed to form a signature. This al-
lows us to defer key generation costs. Moreover,
in practice, truly random values are replaced with
PRF-generated pseudo-random values. In this
case the security of the signature scheme drops by
the indistinguishability of the used PRF.
• Computing endorsements is the main computa-
tional effort of the BLT+L scheme. However,
SECRYPT 2021 - 18th International Conference on Security and Cryptography
82

since the value of the endorsement does not de-
pend on the message being signed, it is pos-
sible to share it across all the signatures pro-
duced during the same L-round interval. Our
preliminary analysis suggests that this will al-
low us to asynchronously produce hundreds of
signatures per second on devices that can only
compute 20–30 thousand hashes per second and
have 500 KB/s download bandwidth (e.g., smart-
phones). This compares favorably with the cur-
rent state-of-the-art hash-based signature scheme
SPHINCS, which is offline, but requires hun-
dreds of thousands of hash operations per signa-
ture (Bernstein et al., 2015).
• We also note that, although our endorsements use
one-time signatures, these signatures are not ap-
plied to signed documents directly. As a result,
the number of signatures that can be securely pro-
duced per round of timestamping service is lim-
ited only by security parameters of used MAC,
accumulator, and tag-commitment schemes (i.e.,
virtually unlimited for practical purposes).
• In our security proof we assumed that there is only
one publisher. If we allow a user to choose a pub-
lisher at a signing time then for the signature to
remain secure the “time values” of the publishers
must be synchronized.
• The security proof for BLT+L relies on the fact
that at most one digest of the tag-commitment
scheme can be associated with a time slot by
the publisher. If this property is violated then
the signature becomes forgeable by an adversar-
ial timestamping service by creating a second di-
gest that the user is unaware of. This can be
solved by timestamping a message binding of the
form h(mkr
1
t
),...,h(mkr
L
t
)kp instead of h(m)kp.
In this case BLT+L is secure even when the pub-
lisher can associate multiple digests with the same
time value, but the security will depend on non-
malleability of the hash function h.
• In BLT+L, an unpredictable token r
0
t
is associ-
ated with every time t, and used as a tag for the
timestamping requests. The value r
0
t
is kept secret
until time t to prevent unauthorized parties from
submitting requests that would be aggregated to-
gether with the user’s genuine requests.
5 PERFORMANCE ANALYSIS
In this section we analyze the performance parameters
of BLT+L and propose an optimization strategy that
accounts for availability of computational resources.
Both the user’s computational effort and the size
of the resulting signatures are dominated by the un-
derlying endorsement scheme, which in turn is de-
termined by the coloring function. For a perfect bi-
nary tree of height H, the number of different color-
ing functions is 2
2
H
−1
. For uniform complexity of en-
dorsing (and thus BLT+L signing), we are only inter-
ested in coloring functions that assign the same type
to all nodes on the same tree level:
Definition 5.1. The coloring function f : N → {G,M}
is level-uniform iff
f (i) = f ( j) for all blog
2
(i)c = blog
2
( j)c.
Every level-uniform coloring function for a tree of
height H can be represented by a string of the form
T
x
1
1
T
x
2
2
...T
x
n
n
, where Σ
n
i=0
x
i
= H, and T
i
∈ {G,M}.
In this representation, G
x
(M
x
) stands for Goldreich
(Merkle) tree of height x.
Previously we already mentioned that in practical
deployments the key pair generation of endorsement
and BLT+L schemes should be done by using secure
PRFs. In particular, this allows us to generate the OTS
key pairs for Goldreich nodes on-demand instead of
having to pre-generate and store large amounts of
confidential data.
However, with this approach the topmost OTS key
pairs of Goldreich nodes of the endorsement tree are
regenerated on every run of the endorsing algorithm.
We noticed that for hash-based OTS schemes, it is
computationally cheaper to generate secret keys, but
more expensive to derive the corresponding public
keys. Therefore, we propose a further optimization
where the most frequently used public keys of the top-
most Goldreich nodes are pre-computed during the
initialization phase and cached for later use. In the
following analysis, the cache is computed once dur-
ing the initialization phase, it consists of OTS public
keys only, and is never updated. The maximal avail-
able memory for cache is given as a parameter.
To sum it up, if we know the BLT+L parame-
ters (E and L) and the available computational re-
sources, we can optimize BLT+L performance by
finding the fittest level-uniform coloring function for
the Goldreich-Merkle endorsement scheme. We con-
sider the following performance metrics:
1. Initialization Complexity: is the total computa-
tional effort needed to produce a BLT+L public
key and the cache of OTS public keys up to the
maximal allowed size.
2. Signing Complexity: is the total computational ef-
fort of a signer needed to produce a signature. The
signer’s computations are dominated by endorse-
ment generation.
BLT+L: Efficient Signatures from Timestamping and Endorsements
83

3. Verification Complexity: is the total computa-
tional effort needed to verify a signature. It is
composed of endorsement verification, accumu-
lator inclusion proof verification, and timestamp
verification.
4. Signature Size: is the sum of the sizes of the
endorsement, accumulator inclusion proof, and
timestamp.
5.1 Case Study
We base our analysis on the performance parameters
of hash-based KSI timestamping service which aggre-
gates user queries into Merkle trees and has round du-
ration equal to one second. The size of a KSI times-
tamp is 1–2 KB and its verification takes less than
40 hash function evaluations (Buldas et al., 2013).
We consider BLT+L key pairs with lifespans of 10
years which induce lists of size E = 3.154 · 10
8
and,
therefore, the height of the endorsement tree for our
use case is H = log
2
(E) = 29. For tree of that height
there are 2
29
level-uniform coloring functions. This is
a reasonably small space and we can use exhaustive
search to find the optimal function for each parameter
set.
We further assume 256-bit hash functions and
implement the Goldreich nodes of the endorsement
tree using the Winternitz hash-based OTS (Merkle,
1987). The used variant of Winternitz OTS requires
532 hashing operations for PRF-based key generation
and signing, and generates 4256-byte signatures. We
also replace the Winternitz OTS public keys with their
hash values as the OTS verification recreates the pub-
lic key value. This significantly reduces the signature
size, but adds only one extra hashing operation per
OTS generation and verification.
Table 1 presents several sets of BLT+L perfor-
mance parameters. The initialization, signing, and
verification times are given in thousands of hashing
operations required on the client side, beause hash-
ing performance may differ radically between de-
vices, from a few hundred operations per second for
smart-cards to several million for “full-size” CPUs.
The cache and signature sizes are given in kilobytes.
The initialization consists of generation of the BLT+L
public key and pre-computation of the cache of OTS
public keys for the endorsement scheme. The scenar-
ios listed highlight the adaptability of the scheme—
key generation and signing time can be traded for sig-
nature size and verification time in very wide ranges.
The signing complexity is shown for a single
thread of execution. In case of n parallel signing
threads, the per-signature signing complexity is in-
creased by D(n)/n+P(n) operations, where D(n) and
P(n) are the number of operations needed to compute
the digest and an inclusion proof of an accumulator
of size n, respectively. The verification complexity
increases by V(n), the number of operations needed
to verify the inclusion proof.
6 RELATED WORK
Merkle proposed a signature scheme based on a hash
tree which aggregates a large number of inputs into
a single hash value so that any of the N inputs can
be linked to it with a proof consisting of log
2
(N)
hash values. This allowed many instances of a one-
time signature scheme to be combined into a many-
time scheme by placing one-time public keys into the
leaves of the tree (Merkle, 1979). This scheme is im-
practical if the number of one-time key pairs is large,
as the whole tree has to be built during key generation.
To defer the key generation costs, Goldreich pro-
posed a scheme based on authentication trees where
each node contains a one-time key pair. The key pairs
in leaf nodes are used to sign messages while the key
pair in a non-leaf node is used to authenticate (sign)
the public keys of both of its children. The public
key of this scheme is the public key of the root node
and the secret key consists of secret keys of all tree
nodes, possibly pseudorandomly generated from a se-
cret seed value (Goldreich, 2004).
Since these schemes are based on one-time signa-
tures, it is crucial that no leaf node is ever used more
than once. One way to prevent this would be to in-
troduce state that keeps track of spent one-time keys.
However, management of such state is a significant
security risk (McGrew et al., 2016). To remove state
management, the one-time key to be used could be se-
lected by time, but this would prevent asynchronous
parallel signing and would limit signing to only one
message per time unit. For Merkle signatures, this
would also waste keys when signing is performed in-
frequently. An alternative for Goldreich signatures is
to set the tree height equal to the length of the mes-
sages (or their hashes) and use the message itself (or
its hash) as the leaf index. Unfortunately, this would
result in impractically large signatures. For example,
with 256-bit hashes and the efficient Winternitz OTS,
Goldreich signatures would be larger than 1 MB.
Yet another approach would be to use random se-
lection in a sufficiently large tree so that the probabil-
ity of using the same leaf twice becomes negligible.
SPHINCS is a family of stateless signature schemes
based on this idea that produces significantly smaller
signatures (e.g. 41 KB for SPHINCS-256). This is
achieved by reducing the tree height, combined with
SECRYPT 2021 - 18th International Conference on Security and Cryptography
84

Table 1: BLT+L performance metrics for some parameter sets. We assume 10-year lifespan of the BLT+L key pair, network
lag up to 3 seconds, Winternitz OTS, and 256-bit hash function. Computation times are given in thousands of hash function
evaluations, cache and signature sizes in kilobytes.
Init. Cache Sig. Ver. Sig. Coloring
time size time time size function
1. 1 0 35 3.0 36 M
1
G
1
M
1
G
1
M
1
G
1
M
2
G
1
M
2
G
1
M
2
G
1
M
2
G
1
M
2
G
1
M
8
2. 555 33 9 5.0 55 M
10
G
13
M
6
3. 1200 70 14 2.0 26 M
11
G
1
M
2
G
1
M
2
G
1
M
2
G
1
M
2
G
1
M
2
G
1
M
2
4. 4500 270 80 0.6 10 M
13
G
1
M
7
G
1
M
7
5. 9000 524 215 0.4 5 M
14
G
1
M
14
the use of Merkle trees (Bernstein et al., 2015). To
mitigate the risk of reusing a one-time key in such re-
duced tree, the key pairs in the leaf nodes are from a
few-time sheme (Reyzin and Reyzin, 2002).
Although our work does not rely on few-time sig-
natures, it is also based on combining the ideas of
Goldreich and Merkle. It differs from SPHINCS in
the tree size (that is much smaller in BLT+L) and in
the leaf node selection mechanism. Another major
difference is the property that BLT+L key pairs have
a validity time after which the key can no longer be
used for signing. The signing and verification time
and signature size for SPHINCS are mainly depen-
dent on the number of messages that can be signed
without significant loss of security. In contrast, the
same values for BLT+L mainly depend on the length
of the validity time of the key pair.
The motivational work for our paper are the recent
results by Buldas et al. They proposed two schemes,
BLT-TB and BLT-OT, both based on combining a
backdating resistant timestamping service with a for-
ward resistant tag system, and both producing small
signatures. As the stateless BLT-TB variant uses large
Merkle trees, it suffers from slow key generation (ap-
proximately 96 million hashing operations to gener-
ate a key that would allow signing once per second
for a year, for example), and as it uses time to select
the one-time key to use, it is wasteful if signing is
performed infrequently. The scheme does not specifi-
cally address the lag in the timestamping process and
the authors suggest several parallel signing attempts
for different time values as a remedy (Buldas et al.,
2017b). The BLT-OT scheme addresses these issues
(in particular, reducing the key generation costs for
personal signing devices that are used only occasion-
ally), but at the cost of introducing stateful client-side
computations and thus making it more complicated to
handle asynchronous calls (Buldas et al., 2019).
Our work is most related to the BLT variant pro-
posed by Firsov et al. which uses the internal one-
time signature values in the Goldreich authentication
tree as tag values. The scheme has both efficient
key generation and signing time without introducing
a client side state, but it does not address the network
lag and produces considerably larger signatures com-
pared to BLT-TB and BLT-OT (Firsov et al., 2021).
BLT+L addresses several shortcomings of the pre-
ceding variants of BLT: the network lag is directly and
efficiently addressed, and parallel asynchronous sign-
ing is supported. Our scheme is parametrized so that
signature size and verification time can be traded for
key generation and signing time depending on the pri-
orities of the use case.
A property that the BLT+L scheme shares with
other members of the BLT family is that each BLT+L
signature is inherently timestamped. This is a bene-
fit in the context of legally binding signature frame-
works such as eIDAS (European Commission, 2014),
but the timestamping service call is an additional ex-
pense compared to other signature schemes in con-
texts where proof of signing time is not needed. As
a result, we expect BLT+L to be practical for sign-
ing legally binding documents and transactions by hu-
mans as opposed to, for example, authenticating SSH
sessions.
7 CONCLUSIONS AND FUTURE
WORK
We have presented a new digital signature scheme
based on combining timestamping with an endorse-
ment scheme, both of which can be constructed from
one-way and collision-resistant hash functions.
To account for the server-assisted nature of the
signature scheme, our security analysis is conducted
in a realistic black-box model where only the pub-
lisher component of the timestamping service is
trusted. Also, the design of the signature takes into
account concurrent requests and network delays.
Finally, we showed that the signature scheme is ef-
ficient and allows trading of key generation and sign-
ing time for signature size and verification time. For
example, our analysis suggests that BLT+L can pro-
BLT+L: Efficient Signatures from Timestamping and Endorsements
85

duce hundreds of 26–55-KB signatures per second on
devices with limited computational resources. Alter-
natively, BLT+L can produce 5-KB signatures on de-
vices with sufficient computational power.
As the next steps, we plan to use theorem provers
(e.g., EasyCrypt) to formally verify our correctness
and security claims. Also, we want to address the se-
curity of BLT+L in the post-quantum setting.
ACKNOWLEDGEMENTS
This work was partially supported by the ESF-funded
Estonian IT Academy research measure (project
2014-2020.4.05.19-0001) and the Estonian Centre
of Excellence in ICT (EXCITE) research measure
TAR16013 (TK148) (1.09.2016–1.03.2023).
REFERENCES
Asokan, Tsudik, G., and Waidner, M. (1997). Server-
supported signatures. Journal of Computer Security,
5(1):91–108.
Benaloh, J. and de Mare, M. (1991). Efficient broadcast
time-stamping. Technical report, Clarkson University.
Bernstein, D. J., Hopwood, D., H
¨
ulsing, A., Lange, T.,
Niederhagen, R., Papachristodoulou, L., Schneider,
M., Schwabe, P., and Wilcox-O’Hearn, Z. (2015).
SPHINCS: Practical stateless hash-based signatures.
In EUROCRYPT 2015, Proceedings, Part I, volume
9056 of LNCS, pages 368–397. Springer.
Bicakci, K. and Baykal, N. (2004). Server assisted signa-
tures revisited. In CT-RSA 2004, Proceedings, volume
2964 of LNCS, pages 143–156. Springer.
Buldas, A., Firsov, D., Laanoja, R., Lakk, H., and Truu,
A. (2019). A new approach to constructing digital
signature schemes. In Attrapadung, N. and Yagi, T.,
editors, Advances in Information and Computer Se-
curity, pages 363–373, Cham. Springer International
Publishing.
Buldas, A., Kalu, A., Laud, P., and Oruaas, M. (2017a).
Server-supported RSA signatures for mobile devices.
In ESORICS 2017, Proceedings, Part I, volume 10492
of LNCS, pages 315–333. Springer.
Buldas, A., Kroonmaa, A., and Laanoja, R. (2013). Key-
less signatures’ infrastructure: How to build global
distributed hash-trees. In NordSec 2013, Proceedings,
volume 8208 of LNCS, pages 313–320. Springer.
Buldas, A., Laanoja, R., and Truu, A. (2017b). A server-
assisted hash-based signature scheme. In NordSec
2017, Proceedings, volume 10674 of LNCS, pages 3–
17. Springer.
Buldas, A., Laanoja, R., and Truu, A. (2018). A blockchain-
assisted hash-based signature scheme. In NordSec
2018, Proceedings, volume 11252 of LNCS, pages
138–153. Springer.
Buldas, A. and Laur, S. (2006). Do broken hash func-
tions affect the security of time-stamping schemes?
In Zhou, J., Yung, M., and Bao, F., editors, Applied
Cryptography and Network Security, pages 50–65,
Berlin, Heidelberg. Springer Berlin Heidelberg.
Buldas, A. and Laur, S. (2007). Knowledge-binding com-
mitments with applications in time-stamping. In PKC
2007, Proceedings, volume 4450 of LNCS, pages
150–165. Springer.
Camenisch, J., Lehmann, A., Neven, G., and Samelin, K.
(2016). Virtual smart cards: How to sign with a pass-
word and a server. In SCN 2016, Proceedings, volume
9841 of LNCS, pages 353–371. Springer.
European Commission (2014). Regulation no 910/2014 of
the European Parliament and of the Council of 23 July
2014 on electronic identification and trust services for
electronic transactions in the internal market and re-
pealing directive 1999/93/EC (eIDAS regulation). Of-
ficial Journal of the European Union, L 257:73–114.
Firsov, D., Lakk, H., and Truu, A. (2021). Verified multiple-
time signature scheme from one-time signatures and
timestamping. Cryptology ePrint Archive, Report
2021/528.
Goldreich, O. (2004). The Foundations of Cryptography -
Volume 2: Basic Applications. Cambridge University
Press.
Goyal, V. (2004). More efficient server assisted one
time signatures. Cryptology ePrint Archive, Report
2004/135.
Haber, S. and Stornetta, W. S. (1991). How to time-stamp
a digital document. Journal of Cryptology, 3(2):99–
111.
McGrew, D. A., Kampanakis, P., Fluhrer, S. R., Gazdag,
S.-L., Butin, D., and Buchmann, J. A. (2016). State
management for hash-based signatures. In SSR 2016,
Proceedings, volume 10074 of LNCS, pages 244–260.
Springer.
Merkle, R. C. (1979). Secrecy, Authentication and Public
Key Systems. PhD thesis, Stanford University.
Merkle, R. C. (1987). A digital signature based on a conven-
tional encryption function. In CRYPTO’87, Proceed-
ings, volume 293 of LNCS, pages 369–378. Springer.
Reyzin, L. and Reyzin, N. (2002). Better than BiBa: Short
one-time signatures with fast signing and verifying.
In ACISP 2002, Proceedings, volume 2384 of LNCS,
pages 144–153. Springer.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
86
