
Hashing to Prime in Zero-Knowledge
Thomas Groß
School of Computing, Newcastle University, U.K.
Keywords:
Primality Testing, Prime Hashing, RSA, Prime Encoding, Zero-Knowledge Argument.
Abstract:
We establish a set of zero-knowledge arguments that allow for the hashing of a committed secret a-bit input x to
a committed secret (k + 1)-bit prime number p
x
. The zero-knowledge arguments can convince a verifier that a
commitment indeed is the correctly generated prime number derived from x with a soundness error probability
of at most 2
−k
+ 2
−t
dependent on the number of zero-knowledge argument rounds k and the number of
primality bases t to establish primality. Our constructions offer a range of contributions including enabling
dynamic encodings for prime-based accumulator (Bari
´
c and Pfitzmann, 1997; Camenisch and Lysyanskaya,
2002), signature (Groß, 2015) and attribute-based credential schemes (Camenisch and Groß, 2008) allowing
to reduce these schemes’ public key size and setup requirements considerably and rendering them extensible.
While our new primality zero-knowledge arguments are of independent interest, we also show improvements
on proving that a secret number is the product of two secret safe primes significantly more efficient than
previously known results (Camenisch and Michels, 1999), with applications to setting up secure special RSA
moduli.
1 INTRODUCTION
Hashing to a prime number is a foundational cryp-
tographic function that enables the computation of a
(k + 1)-bit prime number p
x
from an a-bit input x. It
finds its applications in a wide range of higher-level
constructions that rely on division-intractable encod-
ing, such as in private information retrieval (Cachin
et al., 1999), verifiable random functions (Micali
et al., 1999) or verifiable computing (Ozdemir et al.,
2020).
While the hashing-to-prime primitives have been
found generally useful, a number of crypto-
graphic constructions was barred from their benefits:
Schemes that rely on prime or division-intractable
encoding while seeking to convince verifiers in
zero-knowledge of their faithful protocol execu-
tion. Such schemes include credential schemes (Ca-
menisch and Groß, 2012), special-purpose signature
schemes (Groß, 2015), as well as dynamic accumula-
tors and related revocation systems (Bari
´
c and Pfitz-
mann, 1997; Camenisch and Lysyanskaya, 2002)).
These constructions suffer from cumbersome join and
elaborate setup protocols, which bear large public key
sizes, and thereby limit their practical applications.
In this paper, we aim at creating zero-knowledge
arguments that convince a verifier that a committed
secret a-bit input x was deterministically hashed to a
committed secret (k + 1)-bit prime number p
x
.
Clearly, this goal is feasible as all NP-languages
are provable in zero-knowledge (Goldreich et al.,
1991). What we are interested in is establishing effi-
cient, flexible and practical constructions that can lift
the limitations from a wide range of other construc-
tions.
1.1 High-level Concept
We pursue two different concepts to hash-to-prime
zero-knowledge arguments. One concept operates on
the principle of elimination, the other concept on the
principle of recursive construction. Both construc-
tions have in common that they establish that a hid-
den integer p
x
is a prime derived from input x. That
is, the prover convinces a verifier of a zero-knowledge
predicate p
x
= hashToPrime(x) between two com-
mitments C
x
and C
p
x
on x and prime p
x
, respectively.
Hash-to-Prime by Elimination. Upon receiving an
a-bit bitstring x, the prover computes a (k + 1)-bit
y
i
= PRG
H (x)
(i), iterating over an index i starting
from 1 until y
u
is a probable prime. The prover com-
mits to x and all (y
i
)
u
i=1
and engages with a veri-
fier in a zero-knowledge argument showing (i) that
all computations were executed correctly, (ii) that the
final committed output p
x
:= y
u
passes a primality
test. (iii) that all committed intermediate candidates
(y
i
)
u−1
i=1
are composites. The number of eliminated
composites u is public knowledge.
62
Groß, T.
Hashing to Prime in Zero-Knowledge.
DOI: 10.5220/0010525400620074
In Proceedings of the 18th International Conference on Security and Cryptography (SECRYPT 2021), pages 62-74
ISBN: 978-989-758-524-1
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

Hash-to-Prime by Recursive Construction. Upon
receiving an a-bit bitstring x, the prover establishes
a first prime p
0
as 2
`
n
0
h
0
+ n
0
where h
0
:= H
Q
0
,z
0
(x)
and n
0
is number of iterations till the first prime is
reached. Then, the prover continues to build a Pock-
lington sequence (p
j−1
,a
j
,r
j
) where each r
j
is given
by r
j
:= 2
`
n
j
· H
Q
j
,z
j
(x) + n
j
for the current Pockling-
ton step j. In establishing each step, the prover tests in
sequence for primality integers y
j,i
:= p
j−1
·r
j,i
+1 till
one is found to be prime. Then, the prover commits to
x, all (y
j,i
), r
j
, a
j
. The prover makes the integers n
j,i
public. Then the prover engages with a verifier in a
zero-knowledge argument yielding that the base value
is prime and the preceding candidates composite, fol-
lowed by that for each Pocklington step (i) the prover
knows a Pocklington witness (p
j−1
,a
j
,r
j
), (ii) the
Pocklington criterion is fulfilled such that the subse-
quent number p
j
is prime, (iii) the intermediate can-
didates (y
j,i
) leading up to p
j
are composites. The
integer n
j
of each step is public knowledge.
1.2 Our Contributions
We offer new zero-knowledge arguments for hashing
to prime with both (i) elimination and (ii) recursive
construction methods. This inquiry yields a range
of modular, reusable zero-knowledge predicates for
primality criteria, pseudo-random number generators,
and square hashes to extend zero-knowledge speci-
fication languages in the Camenisch-Stadler frame-
work (Camenisch and Stadler, 1997) and the UC
framework (Camenisch et al., 2011). We gain a new
efficient zero-knowledge argument that an integer is
a product of two safe primes as an immediate con-
sequence of the new predicates. We further provide a
comprehensive complexity analysis that illustrates the
trade-offs for different application scenarios. These
contributions impact especially prime-encoded cre-
dential schemes and signature schemes by lifting the
encoding to bit-strings, by enabling dynamic changes
of the encoding dictionaries, and by reducing pub-
lic key size and setup requirements. They enable
identity-based accumulators.
2 RELATED WORK
Hashing to prime has been investigated and used as
a primitive in a range of constructions. For instance,
Cachin, Micali, and Stadler (Cachin et al., 1999) cre-
ated a function PrimeSeq, which would produce a
prime p
x
from an input x with a deterministic algo-
rithm in the context of private information retrieval.
Micali, Rabin, and Vadhan (Micali et al., 1999) used
an adaptation of that primitive in their first construc-
tion of a verifiable random function. Both are exam-
ples of hash-to-prime by elimination.
Ozdemir et al. (Ozdemir et al., 2020) in-
cluded a construction for division-intractable encod-
ing through a hash-to-prime primitive. They, how-
ever, chose a recursive, constructive method by es-
tablishing a sequence of primes and Pocklington wit-
nesses. They do this in the context of SNARKs and
verifiable computing. Both former approaches are not
applicable as zero-knowledge arguments discrete-log
based signature and zero-knowledge proof systems.
This work is also related to and borrows tech-
niques from Camenisch and Michels’ general zero-
knowledge arguments on the primality of a secret in-
teger and the composition of a special RSA modu-
lus from two safe primes (Camenisch and Michels,
1999).
3 PRELIMINARIES
We assume a group G with prime order Q and two
generators g and h,
h
g
i
=
h
h
i
= G, for which the dis-
crete logarithm log
g
h is not known. We assume a
commitment scheme in group G which commits mes-
sages m with commitments of the structure C
m
:=
g
m
h
r
m
, where r
m
is chosen uniformly at random,
r
m
∈
R
Z
Q
.
We assume the setup for a Square Hash
(SQH/U) (Etzel et al., 1999) family of functions from
Z
Q
to Z
Q
as: {H
Q,z
: Z
Q
−→ Z
Q
|z ∈ Z
Q
} and {H
Q,z,b
:
Z
Q
−→ Z
Q
|z,b ∈ Z
Q
} where the functions H
Q,z
and
H
Q,z,b
are defined as:
SQH: H
Q,z
(x) ≡ (x + z)
2
(mod Q)
SQHU: H
Q,z,b
(x) ≡ (x + z)
2
+ b (mod Q)
Theorem 1 (Square Hash (Etzel et al., 1999)). The
family SQH is ∆-universal. The family SQHU is
strongly universal.
We assume a setup for the Naor-Reingold
PRG (Naor and Reingold, 1997). An instance is gen-
erated with a key
h
Q,P,g, ~a
i
with prime Q, prime P di-
viding Q−1, g a generator of order P, G :=
h
g
i
⊂ Z
Q
,
and ~a a sequence of k + 1 elements of Z
P
. For an a-
bit input x with bits x
1
,...,x
n
, PRG
a
0
(x) := f
Q,P,g,~a
is
defined as:
f
Q,P,g,~a
:= (g
a
0
)
∏
x
i
=1
a
i
(mod Q).
3.1 Known Primality Criteria
We introduce in turn primality criteria related
to (i) Lehmann’s and Solovay-Strassen’s tests,
(ii) Miller’s test, and (iii) Pocklington’s test.
Hashing to Prime in Zero-Knowledge
63

Theorem 2 ((Kranakis, 2013)). An odd integer n > 1
is prime if and only if
∀a ∈ Z
∗
n
: a
(n−1)/2
≡ ±1 (mod n) and (1)
∃a ∈ Z
∗
n
: a
(n−1)/2
≡ −1 (mod n). (2)
Theorem 3 (Miller, adapted from (Kranakis, 2013)).
For any odd integer n > 1 write n − 1 = 2
e
u, with u
odd. Then, n is prime if and only if
(∀a ∈ Z
∗
n
) : a
u
6≡ 1 (mod n) =⇒
∃k < e :
a
2
k
u
≡ −1 (mod n)
.
Definition 1. We call an odd integer n > 1 in Theo-
rem 3 which fulfills both clauses with respect to base
a, a strong probable prime to base a. We call a com-
posite n fulfilling those clauses a strong pseudoprime
to base a, extending naturally to the case of pseudo-
primes to several bases (a
j
)
t
j=1
. (Pomerance et al.,
1980; Jaeschke, 1993) We write:
spsp
(a
j
)
t
j=1
,n
.
Theorem 4 (Pocklington, in an adaptation by (Brill-
hart et al., 1975; Ozdemir et al., 2020)). Let p be a
prime, and r < p and a be positive integers. Define
p
0
:= p · r + 1. Pocklington’s criterion states that if
a
pr
≡ 1 (mod p
0
) and gcd(a
r
− 1, p
0
) = 1, then p
0
is
prime. In this case, we say that (p,r,a) is a Pockling-
ton witness for p
0
.
3.2 Known Zero-Knowledge Proofs
We use the Camenisch-Stadler notation (Camenisch
and Stadler, 1997) to express known discrete-log
based proofs of representation. Therein, we use these
techniques, for instance, as employed by Camenisch
and Groß (Camenisch and Groß, 2008; Camenisch
and Groß, 2012), to prove the following predicate.
(µ 6≡ ±1): Shows that given committed value is nei-
ther one nor minus one.
S
±1
:= PK{(α,ρ,σ,ψ, ς,ϖ) :
D = g
µ
h
ρ
∧
g = (D/g)
σ
h
ψ
∧ g = (gD)
ς
h
ϖ
}.
(gcd(µ,ν) = 1). To show that two values µ and ν are
coprime, we show that (gcd(µ,ν) = 1), which is true
if and only if there exist integers α and β such that
B
´
ezout’s identity is gcd(µ,ν) = 1 = αµ + βν:
S
gcd
:= PK{(µ,ν,ρ
µ
,ρ
ν
,α,β,ρ) :
C
µ
= g
µ
h
ρ
µ
∧C
ν
= g
ν
h
ρ
ν
∧
g = C
α
µ
C
β
ν
h
ρ
}.
(µ > 0). We can show with a predicate (µ > 0) that
an integer µ is greater than zero, proving knowledge
of four integers χ
1
, χ
2
, χ
3
, χ
4
such that µ =
∑
4
i=1
χ
2
i
:
S
>0
:= PK{
χ
i
,ρ
χ
i
4
i=1
,ρ
:
C
χ
i
= g
χ
i
h
ρ
χ
i
4
i=1
∧ C
µ
=
4
∏
i=1
C
χ
i
χ
i
h
ρ
}.
a
b
≡ d (mod n)
. Camenisch and Michels (Ca-
menisch and Michels, 1999) introduced statistical
zero-knowledge arguments for secret exponentiation
we will adapt in two forms:
a
b
≡ d (mod n)
: signifies a secret modular ex-
ponentiation with secrets a, b, d, and n, real-
ized with computing a committed square-and-
multiply (mod n) with respect to the committed
bit-representation of b.
a
b
= d
: means a secret exponentiation over the in-
tegers with secrets a, b, and d, which can be easily
adapted from the former.
Both forms have in common that they produce inter-
mediary commitments C
υ
i
to either a
2
i
(mod n) in
the former case or C
υ
i
to a
2
i
over the integers in the
latter case.
Theorem 5 (Secret ModExp (Camenisch and
Michels, 1999, p. 114)). Let c
a
, c
b
, c
d
, and c
n
be
commitments on integers a, b, d, and n and let c
b
0
,
. . . , c
b
`−1
, c
v
1
,... ,c
v
`
b
−1
, c
u
0
,... ,c
u
`
b
−2
be auxiliary
commitments. Then assuming computing discrete log-
arithms in G is infeasible, the protocol S
↑
is a statisti-
cal zero-knowledge argument that the equation a
b
≡ d
(mod n) holds. The soundness error probability is
2
−k
.
(a
i
∈ Z
n
)
k
i=1
. This proof predicate governs the joint
generation of group elements a
i
∈ Z
n
, where the ver-
ifier may not be privy of n, showing that the bases
were generated correctly with randomness from both
prover and verifier. This predicate is part of the pri-
mality protocol (Camenisch and Michels, 1999). The
full version contains a modular construction.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
64

Table 1: Complexity of known PK predicates for k rounds.
Computations (mexp)
Communication (ge/bits)
Prover Verifier
(µ 6≡ ±1) 1 +3k 3k 1 +3k ge + 6 logQ bits
(gcd(µ,ν) = 1) 2 +3k 3k 2 +3k ge + 7 logQ bits
(µ > 0) 5 +5k 5k 5 +5k ge + 5 logQ bits
a
b
≡ d (mod n)
3`
b
+ (7`
b
)k (7`
b
)k 3`
b
ge + (14`
b
logQ +4`
b
ε`)k bits
a
b
= d
(µ ∈ primes
L
(t)) 2t logn +(7t logn)k (7t logn)k 2t logn ge + (14t log n log Q + 4t logn2ε`)k bits
(µ ∈ composites
L
()) 2logn +(11 + 7 log n)k (11 + 7logn)k 2log n ge + (14 log n log Q + 4`
b
ε`)k bits
Note: k = number of PK rounds; mexp = multi-base exponentiations; ge = group elements from G.
(µ ∈ primes
L
(t)). Camenisch and Michels offered a
PK predicate we call primes
L
(t) proving that a com-
mitted number is prime using a predicate S
p
for a se-
cret execution of Lehmann’s primality test (Lehmann,
1982).
Theorem 6 (Primality (Camenisch and Michels,
1999, p. 118)). Assume computing discrete log-
arithms in G is infeasible. Then, [the protocol
primes
L
(t) on a commitment c
n
] is a statistical zero-
knowledge argument that the integer committed to by
c
n
is a prime. The soundness error probability is at
most 2
−k
+ 2
−t
.
(µ ∈ composites()). This predicate proves that a
number µ is a composite by proving knowledge of an
integer a ∈ Z
∗
n
that is a Lehmann compositeness wit-
ness such that a
(n−1)/2
6≡ ±1 (mod n). We include
details of this protocol in the full version. It holds:
Theorem 7. If the discrete-logarithm problem is hard
in group G, then the protocol composites() on com-
mitment C
n
is a statistical zero-knowledge argument
that the integer n committed to by C
n
is a composite.
The soundness error probability is at most 2
−k
.
µ = H
ζ,β
(ν)
. This predicate proves that a commit-
ted value µ is the output of a square hash SQHU H
Q,z,b
with key (ζ,β) on committed input ν. A correspond-
ing predicate
µ = H
ζ
(ν)
for SQH H
Q,z
follows triv-
ially. When evaluated in Z
Q
, we omit parameter Q.
S
SQHU
:= PK{
µ,ρ
µ
,ν,ρ
ν
,ζ,ρ
ζ
, ¯µ,ρ
¯µ
,β,ρ
β
,γ,δ,η
:
C
µ
= g
µ
h
ρ
µ
∧C
ν
= g
ν
h
ρ
ν
∧
C
ζ
= g
ζ
h
ρ
ζ
∧C
¯µ
= g
¯µ
h
ρ
¯µ
∧
C
¯µ
= C
ζ
C
ν
h
γ
∧C
ˆµ
= C
¯µ
¯µ
h
δ
∧
C
β
= g
β
h
ρ
β
∧C
µ
= C
ˆµ
C
β
h
η
}.
µ = PRG
ξ
(ν)
. This predicate proves that µ is
the output of pseudo-random generator PRG on
seed ξ and input ν. We can prove predicate of
the Naor-Reingold PRG in discrete-logarithm-based
zero-knowledge proofs efficiently that the relation
µ = f
Q,P,g,~a
(ν) is fulfilled in G. We include a detailed
construction of this predicate in the full version of this
paper.
4 SECURITY REQUIREMENTS
Definition 2 (Requirements (Menezes et al., 2018)).
We expect the following properties of our interactive
proof systems.
Completeness. An interactive proof system is com-
plete if, given an honest prover and an honest
verifier, the protocol succeeds with overwhelming
probability.
Soundness. An interactive proof system is sound if
there exists an exists an expected polynomial-time
algorithm M with the following property: if a dis-
honest prover can with non-negligible probability
successfully execute the protocol with the verifier,
then M can be used to extract from this prover
knowledge which with overwhelming probability
allows successful future protocol executions.
Zero-Knowledge. A proof of knowledge has the
zero-knowledge property if there exists an ex-
pected polynomial-time algorithm (simulator)
which can produce, upon input of the assertions
to be proven but without interacting with the real
prover, transcripts indistinguishable from those
resulting from interaction with the real prover.
We will specify the protocols in the Camenisch-
Stadler framework (Camenisch and Stadler, 1997),
which naturally extends to UC proofs in the Ca-
menisch, Krenn and Shoup’s corresponding UC
framework (Camenisch et al., 2011). We take nat-
ural composition of discrete-logarithm based zero-
Hashing to Prime in Zero-Knowledge
65

knowledge proofs including their completeness and
zero-knowledge properties for granted and focus on
the soundness property and soundness error probabil-
ity quantification.
5 CONSTRUCTIONS
5.1 Miller Primality Predicate
We can execute a deterministic Miller test on a careful
selection of bases (a
j
)
t
j=1
∈ Z
∗
n
to enable a determin-
istic primality test for small positive integers n, with
fixed bitlength
˙
`
n
and a soundness error of ε
S
= 0. The
latter is based on research on strong pseudoprimes
to several bases (Pomerance et al., 1980; Jaeschke,
1993).
Prover and Verifier agree on the variant of test to
run by establishing the parameters
˙
`
n
, t, and (a
j
)
t
j=1
as follows:
µ ∈ primes
M
(
˙
`
n
,(a
j
)
t
j=1
)
: Prover and
Verifier agree on bitlength
˙
`
n
. t is set dependent on a
valid fixed base set (a
j
)
t
j=1
such that the least n
∗
with
spsp
(a
j
)
t
j=1
,n
∗
is greater than 2
˙
`
n
.
To establish PK predicate primes
M
(t), let us begin
by proving that an odd integer n > 1 has the form n =
2
e
u + 1, with u odd.
1. The prover efficiently finds e such that n −1 = 2
e
u
with u odd.
2. The prover commits to n in the form of C
n
:=
g
n
h
r
n
, to u in the form C
u
:= g
u
h
r
u
, and to con-
stant 2 in the form C
2
:= g
2
h
r
2
.
3. The prover computes the strong pseudo-prime
equation for the selected bases (a
j
)
t
j=1
:
(a) d
j
:= a
u
j
(mod n).
(b) If d
j
6≡ 1 (mod n), the prover finds the k < e
such that
d
0
j
:= a
2
k
u
j
(mod n) ∧ d
0
j
≡ −1 (mod n).
4. The prover commits to d
j
and d
0
j
in the form of
C
d
j
:= g
d
j
h
r
d
j
and C
d
0
j
:= g
d
0
j
h
r
d
0
j
.
5. The prover sends all commitments to the verifier.
Then the prover runs the following protocol with
the verifier sequentially for k times:
PK{ (ν,α,β,µ,γ, υ,ε,
(ρ
j
,ψ
j
,ϖ
j
,υ
j
,ξ
j
,κ
j
,η
j
,∆
j
,ζ
j
,τ
j
,ς
j
,δ
j
,
π
j
,δ
0
j
,π
0
j
,ϑ
j
,ϑ
0
j
t
j=1
,χ,
:
C
n
= g
ν
h
α
∧ (ν > 0) − 2
˙
`
n
< ν < 2
˙
`
n
∧ (3)
C
2
= g
2
h
β
∧C
u
= g
µ
h
γ
∧ (4)
C
a
j
= g
ρ
j
h
ϖ
j
t
j=1
∧ (5)
C
2
e
= g
υ
h
ψ
j
∧ (2
ε
= υ)∧ (6)
C
n
/g = C
µ
2
e
h
χ
∧ (gcd(µ,2) = 1)∧ (7)
C
2
k
j
= g
υ
j
h
ξ
j
∧ (2
κ
j
= υ
j
)
t
j=1
∧ (8)
C
∆
j
= g
∆
j
h
ζ
j
t
j=1
∧ (9)
C
∆
j
= g
ε
/g
κ
j
h
η
j
∧ (∆
j
> 0)
t
j=1
∧ (10)
C
2
k
j
u
= g
µ
j
h
τ
j
t
j=1
∧ (11)
C
2
k
j
u
= C
µ
2
k
j
h
ς
j
t
j=1
∧ (12)
C
d
j
= g
δ
j
h
π
j
∧C
d
0
j
= g
δ
0
j
h
π
0
j
t
j=1
∧ (13)
ρ
µ
j
≡ δ
j
(mod ν)
t
j=1
∧ (14)
ρ
µ
j
j
≡ δ
0
j
(mod ν)
t
j=1
∧ (15)
C
d
j
/g = h
ϑ
j
∨C
d
0
j
g = h
ϑ
0
j
t
j=1
(16)
}.
Clause 3 establishes the knowledge of candidate n,
that n is positive and fulfills the length restriction to
˙
`
n
. Clause 5 proves knowledge of the bases (a
j
)
t
j=1
committed to in C
a
j
for j = 1,.. .,t; in the determin-
istic case, these bases are known publicly. Clause 4
shows the representation to commitments to 2 and u
as foundation for the decomposition of n − 1 = 2
e
u.
The following clauses 6 thru 7 establish the composi-
tion of n− 1 = 2
e
u, where the second clause of Line 7
yields that u is indeed odd. Subsequent clauses es-
tablish the deterministic Miller test for fixed known
bases (a
j
)
t
j=1
. First, we prove the correct representa-
tion of C
2
k
j
, which proceeds similarly to the proof for
C
2
e
in Line 6. Secondly, we establish the difference
between 2
e
and 2
k
j
and prove that this difference is
greater than zero in Clause 6. The clauses on Line 12
establish the knowledge and structure of commitment
C
2
k
j
u
. The clauses on Line 13 establish the knowledge
of the results of the Miller test d
j
and d
0
j
. Clauses 14
and 15 establish the relations of the Miller test a
u
j
≡ d
j
(mod n) and a
2
k
j
u
j
≡ d
0
j
(mod n), where secret µ
j
rep-
resents 2
k
j
u. The final clauses on Line 16 establish the
different cases of strong probable prime test, that is,
either d
j
= 1, entailing a
u
j
≡ 1 (mod n), or d
0
j
= −1,
entailing a
2
k
j
u
j
≡ −1 (mod n). The proof sketch for
the following theorem is included in the appendix.
Theorem 8. Assuming that the discrete logarithm
problem is hard in G and that the least n
∗
with
SECRYPT 2021 - 18th International Conference on Security and Cryptography
66

Table 2: Overview of ZK primality arguments.
Name Th. § Type Form p
x
t Witnesses
Lehmann 2 Monte-Carlo n/a −log
2
ε
S
(a
j
)
t
j=1
∈
R
Z
∗
n
Det. Miller 3 §5.1 Deterministic <
˙
`
n
fixed t for
˙
`
n
fixed (a
j
)
t
j=1
Pocklington 4 §5.2 Constructive/Recursive p ·r + i ≈ log
2
(k + 1) (p
i−1
,r
i
,a
i
)
ε
S
: Soundness error.
spsp((a
j
)
t
j=1
,n
∗
) is greater than 2
˙
`
n
, then the proto-
col
µ ∈ primes
M
(
˙
`
n
,(a
j
)
t
j=1
)
is a zero-knowledge
argument that the committed integer µ is prime. The
soundness error probability is 2
−k
.
5.2 Pocklington Primality Witness
The predicate ν
j
∈ primes
P
(ν
j−1
,ρ
j
,χ
j
) convinces a
verifier that Pocklington’s criterion is fulfilled for p
j
based on a secret Pocklington witness (p
j−1
,r
j
,a
j
)
such that:
a
p
j−1
r
j
≡ 1 (mod p
j
) ∧gcd(a
r
j
j
− 1, p
j
) = 1.
We assume that a commitment to p
j−1
is given as
C
p
j−1
= g
p
j−1
h
r
p
j−1
and a commitment to r
j
is given
as C
r
j
= g
r
j
h
r
r
j
where r
p
j−1
,r
r
j
∈
R
Z
Q
.
1. The prover searches for a positive integer a
j
such
that Pocklington’s criterion is fulfilled for p
j−1
,
r
j
, a
j
and p
j
:
a
p
j−1
r
j
≡ 1 (mod p
j
) ∧gcd(a
r
j
j
− 1, p
j
) = 1.
If p
j
is prime, such an a
j
will exist.
2. The prover commits to a
j
with the structure C
a
j
=
g
a
j
h
r
a
j
with r
a
j
∈
R
Z
Q
.
3. Then the prover engages with the verifier in the
following zero-knowledge proof k times:
PK{
ν
j
,ν
j−1
,ρ
j
,χ
j
,δ
j
,∆
j
,α,β,γ,ε,ζ, η, κ, ξ, τ,π,ψ
:
C
p
j−1
= g
ν
j−1
h
α
∧C
p
j
= g
ν
j
h
β
∧ (17)
C
a
j
= g
ρ
j
h
γ
∧C
r
j
= d
χ
j
h
ε
∧ (18)
− 2
`
< ρ
j
,χ
j
,ν
j
< 2
`
∧ (19)
C
∆
j
= g
∆
j
h
ζ
∧C
∆
j
= g
ν
j−1
/g
χ
j
h
η
∧ (20)
(ρ
j
> 0) ∧ (χ
j
> 0) ∧ (∆
j
> 0)∧ (21)
C
p
j
/g = C
χ
j
p
j−1
h
κ
∧ (22)
C
d
j
= g
δ
j
h
ξ
∧ (23)
ρ
ν
j−1
χ
j
j
≡ δ
j
(mod ν
j
)
∧ (24)
C
d
j
/g = h
τ
∧ (25)
C
λ
j
= d
λ
j
h
π
∧C
λ
j
g = C
χ
j
a
j
h
ψ
∧ (26)
(gcd(λ
j
,ν
j
) = 1) (27)
}.
We assume that the length of p
j−1
has been
established by the corresponding primality zero-
knowledge argument. Clauses 17 establish the knowl-
edge of the successive Pocklington primes p
j−1
and
p
j
. Clauses 18 proves the knowledge of the remainder
of the Pocklington witness a
j
and r
j
. The clauses 19
thru 21 prove the length restrictions on p
j
, r
j
, and
a
j
, where Clause 21 ensures that a
j
and r
j
are indeed
positive integers and that r < p
j−1
as required by The-
orem 4.
Clauses 23 thru 27 prove the Pocklington cri-
terion itself. Clause 23 proves knowledge of the
committed result d
j
of the Pocklington congruence.
Clause 24 shows the structure of the key Pockling-
ton congruence: a
p
j−1
r
j
≡ 1 (mod p
j
). Subsequently,
Clause 25 shows that the result is indeed congruent
to 1. Clause 26 shows the commitment to the term
a
r
j
j
−1 and the subsequent Clause 27 yields the copri-
mality with p
j
. The proof sketch for this theorem is
in the Appendix.
Theorem 9. Assuming that ν
j−1
has been estab-
lished to be prime and assuming that the discrete
logarithm problem is hard in G, then the protocol
(ν
j
∈ primes
P
(ν
j−1
,ρ
j
,χ
j
)) is a zero-knowledge ar-
gument that the committed integer ν
j
is prime. The
soundness error probability is 2
−k
.
5.3 Special RSA Modulus
Before we turn to the main contribution of this paper,
we show how the Pocklington Witness predicate pre-
sented in Section 5.2 directly offers a more efficient
zero-knowledge argument that a number n is a prod-
uct of two safe primes. For that, by proving knowl-
edge of a Pocklington witness we can assert the struc-
ture of the constituent safe primes, improving on com-
putational and communication complexity as well as
soundness error probability of earlier methods (Ca-
menisch and Michels, 1999).
1. The Prover computes two safe primes p := 2 ˜p + 1
and q := 2 ˜q + 1, creating the RSA modulus n :=
pq.
2. The prover searches for two bases a
p
and a
q
that
complete Pocklington witnesses for the primality
Hashing to Prime in Zero-Knowledge
67

of p and q such that
a
2 ˜p
p
≡ 1 (mod p) and gcd(a
2
p
− 1, p) = 1
a
2 ˜q
q
≡ 1 (mod q) and gcd(a
2
q
− 1,q) = 1
3. We assume a commitment on integer n be given as
C
n
= g
n
h
r
n
. The prover commits to p, q as well as
a
p
and a
q
with C
p
:= g
p
h
r
p
, C
q
:= g
q
h
r
q
, C
˜p
:=
g
(p−1)/2
h
r
˜p
, C
˜q
:= g
(q−1)/2
h
r
˜q
, C
a
p
:= g
a
p
h
r
a
p
,
C
a
q
:= g
a
q
h
r
a
q
, where the corresponding random-
nesses r
p
, r
q
, r
˜p
, r
˜q
, r
a
p
, and r
a
q
∈
R
Z
Q
. Fur-
thermore, the prover computes all commitments
prescribed by ˜p ∈ primes
L
(t), ˜q ∈ primes
L
(t), p ∈
primes
P
( ˜p,2,a
p
), q ∈ primes
P
( ˜q,2, a
q
).
4. Then the prover and the verifier engage in the fol-
lowing zero-knowledge protocol k times.
PK{ (µ,ν, ˜µ,
˜
ν,ρ
p
,ρ
q
,α,β,γ, ε,ζ,η, κ,ξ) :
C
p
= g
µ
h
α
∧C
q
= g
ν
h
β
∧ (28)
C
˜p
= g
˜µ
h
γ
∧C
˜q
= g
˜
ν
h
δ
∧ (29)
C
n
= C
ν
p
h
ε
∧ (30)
C
p
/(C
2
˜p
g) = h
ζ
∧C
q
/(C
2
˜q
g) = h
η
∧ (31)
C
a
p
= g
ρ
p
h
κ
∧C
a
q
= g
ρ
q
h
ξ
∧ (32)
(˜µ ∈ primes
L
(t))∧ (33)
(
˜
ν ∈ primes
L
(t))∧ (34)
(µ ∈ primes
P
(˜µ,2,ρ
p
))∧ (35)
(ν ∈ primes
P
(
˜
ν,2,ρ
q
)) (36)
}.
The length of µ, ν, ˜µ,
˜
ν, ρ
p
and ρ
q
is constrained
by the corresponding primes
L
(t) and primes
P
(n,r, a)
protocols. While the primality of (p − 1)/2 and
(q − 1)/2 is proven by secret Lehmann primality tests
in clauses 33 and 34. We proceed with proving the
primality of the p and q with a Pocklington witness.
The following theorem is proven in the Appendix.
Theorem 10. Assuming that the discrete logarithm
problem is hard in G, then the protocol is a zero-
knowledge argument that the integer n committed to
in C
n
is the product of two safe primes p and q, for
which (p −1)/2 and (q− 1)/2 are prime as well. The
soundness error probability is at most 2
−k
+ 2
−t
.
6 SECRET HASH-TO-PRIME
Definition 3 (Hash-to-Prime).
(µ ∈ hashToPrime
F
(ν,t)) is a zero-knowledge predi-
cate stating that committed secret µ an element of the
set of prime numbers derived according to a specified
procedure F from committed secret input ν, using t
steps.
µ = hashToPrime
ϒ
F
(ν,t, u)
is a zero-knowledge
proof predicate stating that committed secret µ is ex-
actly the first prime number in sequence derived ac-
cording to a specified procedure F from committed
secret input ν, using t steps and having eliminated u
composite candidates in sequence. The parameters t
and u are public knowledge.
We offer two constructions for proving in a zero-
knowledge argument that a committed (k + 1)-bit
prime p
x
was generated via hashing from an a-bit
input x: (i) by elimination (E) and (ii) by recur-
sive construction (R). Both variants of the pred-
icate
µ = hashToPrime
ϒ
F
(ν,t, u)
have in common
that the prover is required to prove the compositeness
of u eliminated candidates in a fixed order, enforcing
that the first prime in sequence must be used.
6.1 Hash-to-Prime by Elimination
The idea of hashing-to-prime by elimination is that
the prover hashes the input x which then seeds a
PRG, evaluated in a deterministic sequence with
known indices i = 1,. ..,u until the outcome y
u
passes a test as a probable prime. To estab-
lish the predicates (µ ∈ hashToPrime
E
(ν,t)) and
µ = hashToPrime
ϒ
E
(ν,t, u)
, the prover runs a pro-
tocol with the verifier to establish a zero-knowledge
argument (i) that the hash- and PRG-computations
are executed correctly, (ii) that all committed elim-
inated candidates (y
i
)
u−1
i=1
are composites (∗), and
(iii) that the final committed value p
x
:= y
u
is
prime, where (∗) is only executed for predicate
µ = hashToPrime
ϒ
E
(ν,t, u)
.
For specified and setup pseudo-random num-
ber generator PRG(), a hash function H
Q,z,b
()
and corresponding zero-knowledge predicates
µ = PRG
χ
(ν)
and
µ = H
ζ,β
(ν)
, we establish
the ZK predicates (µ ∈ hashToPrime
E
(ν,t)) and
µ = hashToPrime
ϒ
E
(ν,t, u)
as follows, where (∗)
marks the steps transforming the former to the latter:
1. The prover computes y
i
:= PRG
H
z,b
(x)
(i) for i =
1,... ,u testing each y
i
with a Miller-Rabin test till
y
u
passes the primality test as a probable prime.
The prover calls this y
u
the outcome p
x
.
2. the prover commits to the intermediary output of
the hash function H
z,b
() as ¯y, in the form of C
¯y
=
g
¯y
h
r
¯y
and r
¯y
∈
R
Z
Q
.
3. The prover computes commitments on all elim-
inated composite values y
i
as C
y
i
:= g
y
i
h
r
y
i
with
i = 1,. ..,u − 1 and r
y
i
is ∈
R
Z
Q
. (∗) The prover
commits to the determined prime p
x
= y
u
in the
form of C
p
x
:= g
p
x
h
r
p
x
, where r
p
x
∈
R
Z
Q
.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
68

4. The prover sends all commitments, including ones
of sub-ordinate predicates to the verifier.
5. Finally, the prover engages with the verifier in
a zero-knowledge argument sequentially for k
times:
PK{
ν,ζ,β,µ, ρ,ρ
0
, ¯µ,
¯
ρ,(µ
i
)
u−1
i=1
:
C
x
= g
ν
g
ρ
∧C
p
x
= g
µ
h
ρ
0
∧ (37)
(C
y
i
= g
µ
i
h
ρ
i
)
u−1
i=1
∧ (38)
C
¯y
i
= g
¯µ
i
h
¯
ρ
i
u
i=1
∧ (39)
¯µ = H
ζ,β
(ν)
∧ (40)
(µ = PRG
µ
u
(u))∧ (41)
(µ ∈ primes
L
(t))∧ (42)
(µ
i
= PRG
µ
i
(i))
u−1
i=1
(∗)∧ (43)
(µ
i
∈ composites())
u−1
i=1
(∗) (44)
}.
The first three clauses 37 thru 39 establish the rep-
resentation of the commitments. Clause 40 yields the
correct computation of the hash function H
Q,z,b
() with
respect to the secret input x, while the following two
clauses 43 and 41 give the correct computation of the
PRG. Clause 42 shows the primality of the resulting
output p
x
. Clause 44 establishes the elimination of
intermediary composites (∗). The size constraints are
governed in the corresponding subordinate ZK predi-
cates.
Theorem 11. Assuming that the discrete logarithm
and the decisional Diffie-Hellman problems are hard
in G. Then the protocol (µ ∈ hashToPrime
E
(ν,t))
is a zero-knowledge argument that the committed
integer µ is prime and was derived as hash-to-
prime from committed integer ν. The protocol
µ = hashToPrime
ϒ
E
(ν,t, u)
is a zero-knowledge ar-
gument that the committed integer µ is exactly the first
prime in sequence succeding u eliminated candidates
derived as hash-to-prime from committed integer ν,
where the integer u is publicly known. The soundness
error probability is at most 2
−k
+ 2
−t
.
6.2 Hash-to-Prime by Recursion
For a recursive construction, we draw inspira-
tion from Ozdemir et al.’s approach to hashing
to primes (Ozdemir et al., 2020) to estab-
lish predicates (µ ∈ hashToPrime
R
(ν,t)) and
µ = hashToPrime
ϒ
R
(ν,t, (n
j
)
t
j=0
)
, (∗) marking
the steps to transform the former to the latter. The
recursion has has t steps, each doubling the size of
the prime established, using a setup of collection of
SQHUs
H
Q
j
,z
j
,b
j
(·)
t
j=0
.
We start with establishing a first small prime p
0
based on the result of H
Q
0
,z
0
,b
0
(x). From this first
prime, we recursively establish Pocklington steps
with their corresponding proofs with predicate ν
j
∈
primes
P
(ν
j−1
,ρ
j
,χ
j
), while each step roughly dou-
bles the bitlength of the prime p
j
. Finally, the prover
convinces the verifier (i) that the initial value p
0
is
prime with a deterministic Miller predicate, while
showing that intermediate candidates were compos-
ite (∗), (ii) that, for each subsequent value p
j
, it is
prime with a Pocklington primality witness predicate
ν
j
∈ primes
P
(ν
j−1
,ρ
j
,χ
j
) relating it to the previous
prime p
j−1
, (iii) that, for each primes p
j
, the candi-
dates eliminated in finding r
j
to complete p
j
are com-
posite (∗). For clarity, we shall explain the base case
and the recursion step separately, even if the protocol
is executed as one compound zero-knowledge argu-
ment.
Base Case ( j = 0). We establish the first prime p
0
with a bitlength arbitrarily set to 32 bits. This prime
will be derived from input secret x as p
0
:= 2
`
n
0
h
0
+n
0
with h
0
:= H
Q
0
,z
0
,b
0
(x) and an integer counter n
0
. The
primality is established with a deterministic Miller
primality predicate (cf. Section 5.1) and constant 3
bases.
1. The prover computes H
Q
0
,z
0
,b
0
(x) and establishes
the first integer n
0
in the sequence 1,.. .,n
0
such that p
0
= 2
`
n
0
· h
0
+ n
0
is probable prime.
The prover stores all intermediate values y
0,i
=
2
`
n
0
h
0
+i for 1,. ..,n
0
−1 that are composites. (∗)
2. The prover commits to p
0
as C
p
0
= g
p
0
h
r
p
1
with
r
p
0
∈
R
Z
Q
and to the eliminated composites as
C
y
0,i
= g
y
0,i
h
r
y
0,i
for i = 1, ..., n
0
− 1 and with
r
y
0,i
∈
R
Z
Q
(∗) and sends the commitments to the
verifier.
3. Then the prover runs the following protocol with
the verifier sequentially k times:
PK{
µ,α,β
0
, ¯µ,
¯
α,ν
0
,ρ
0
,(ν
0,i
,ρ
0,i
γ
0,i
,)
u
i=1
,γ
:
C
x
= g
µ
h
α
∧C
¯µ
= g
¯µ
h
¯
α
∧ (45)
C
p
0
= g
ν
0
h
ρ
0
∧ (46)
C
y
0,i
= g
ν
0,i
h
ρ
0,i
n
0
−1
i=1
∧ (47)
¯µ = H
ζ
0
,β
0
(µ)
∧ (48)
C
p
0
= C
2
`
n
0
¯µ
g
n
0
h
γ
∧ (49)
ν
0
∈ primes
M
(t)∧ (50)
C
y
0,i
= C
2
`
n
0
¯µ
g
i
h
γ
0,i
n
0
−1
i=1
(∗)∧ (51)
(ν
i
∈ composites())
n
0
−1
i=1
(∗) (52)
}.
Hashing to Prime in Zero-Knowledge
69
Recursion Step ( j − 1 → j). The prover constructs
the subsequent prime p
j
of the form p
j−1
·r
j,i
+1 and
established a Pocklington Witness zero-knowledge
argument on is primality.
1. Given p
j−1
and input x committed in C
x
, the
prover computes y
j,i
:= p
j−1
· r
j,i
+ 1 where the
positive integer r
j,i
:= 2
`
n
j
· H
Q
j
,z
j
,b
j
(x) + i, iter-
ating over i = 1, .. .,u till p
j
:= y
j,u
is a probably
prime. The integer u is stored as n
j
, the corre-
sponding r
j,u
is called r
j
.
2. The prover searches for a positive integer a
j
such
that Pocklington’s criterion is fulfilled:
a
p
j−1
r
j
≡ 1 (mod p
j
) ∧ gcd(a
r
j
j
− 1, p
j
) = 1.
3. The prover commits to p
j
, a
j
, r
j
as well as all
intermediate values y
j,i
for i = 1,... ,u − 1 (∗).
The commitments have the forms C
p
j
:= g
p
j
h
r
p
j
,
C
a
j
:= g
a
j
h
r
a
j
, C
r
j
:= g
r
j
h
r
r
j
, C
y
j,i
:= g
y
j,i
h
r
y
j,i
,
where r
p
j
, r
a
j
, r
r
j
, and (r
y
j,i
)
u−1
i=1
are all ∈
R
Z
Q
.
4. The prover sends commitments to the verifier.
5. Then the prover engages with the verifier in the
following protocol sequentially k times:
PK{
¯µ,
¯
α,β
j
(χ
j,i
,β
j,i
,γ
j,i
,ψ
j,i
,ϕ
j,i
,ε
j,i
)
u
i=1
,ρ
j
,δ
j
:
C
¯µ
= g
¯µ
h
¯
α
∧
¯µ = H
ζ
j
,β
j
(µ)
∧ (53)
C
r
j,i
= g
χ
j,i
h
β
j,i
u
i=1
∧ (54)
C
r
j,i
= C
2
`
n
j
¯µ
g
i
h
γ
j,i
u
i=1
∧ (55)
C
y
j,i
= g
ψ
j,i
h
ϕ
j,i
u
i=1
∧ (56)
C
a
j
= g
ρ
j
h
δ
j
∧ (57)
(ν
j
∈ primes
P
(ν
j−1
,ρ
j
,χ
j,i
))∧ (58)
C
y
j,i
/g = C
χ
j,i
p
j−1
h
ε
j,i
u
i=1
(∗)∧ (59)
(ψ
j,i
∈ composites(t))
u−1
i=1
(∗) (60)
}.
Theorem 12. Assuming that the discrete loga-
rithm problem is hard in G. Then the protocol
(µ ∈ hashToPrime
R
(ν,t)) is a zero-knowledge argu-
ment that the committed integer µ is prime and was
derived as hash-to-prime from committed integer ν.
The protocol
µ = hashToPrime
ϒ
R
(ν,t, (n
j
)
t
j=0
)
is a
zero-knowledge argument that the committed integer
µ is the prime created by choosing the first prime in
sequence in each of the t steps succeeding (n
j
)
t
j=0
eliminated candidates, derived as hash-to-prime from
committed integer ν, where the integers (n
j
)
t
j=0
are
publicly known. The soundness error probability is
2
−k
.
0
2500000
5000000
7500000
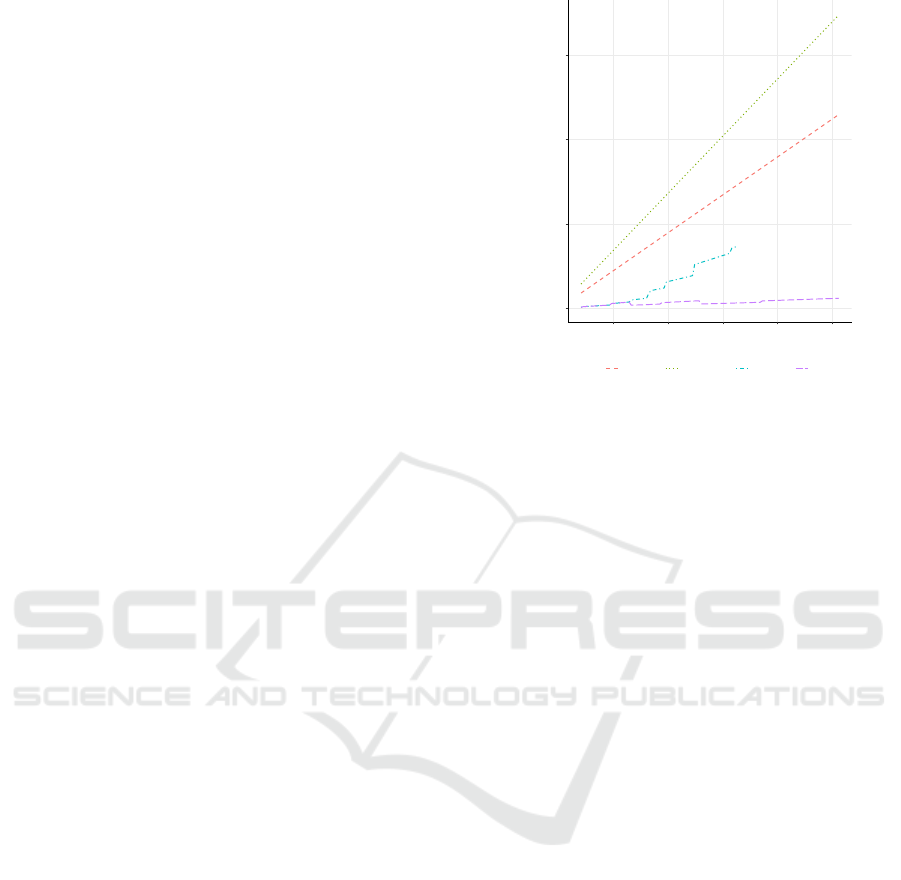
25 50 75 100 125
Bitlength(n)
#MExp
Scheme
Lehmann Miller−Rabin Det.Miller Pocklington
Figure 1: Number of multi-base exponentiations by
bitlength of n for a primality ZK argument on small primes
n,|n| ≤ 128, with a fixed number of rounds k = 80 and a
soundness error probability of at most 2
−80
+ 2
−80
.
7 COMPLEXITY EVALUATION
We have analyzed the computation complexity of
proving the primality of a secret integer n in num-
ber of multi-base exponentiations by the bitlength
of n and the maximum soundness error probability
ε
S
allowed, which in turn determines the number of
primality-test bases used t and the number of ZKP
rounds k executed. All simulations are computed in
the statistics software R.
7.1 Primality ZK Arguments
We have computed an simulation in R pitting the
growth of the number of multi-base exponentiations
for different primality predicates by bitlength of n
against each other. Figure 1 displays this com-
plexity analysis graphically for small primes; Fig-
ure 2 shows the secret primality proof for primes n
up to a bitlength of `
n
= 1024. Therein, we no-
tice that the secret primality test with probabilis-
tic Lehmann and Miller-Rabin tests ((µ ∈ primes
L
(t))
and (µ ∈ primes
MR
(t))) dominate the complexity,
where the Lehmann test proposed by Camenisch and
Michels (Camenisch and Michels, 1999) is the more
efficient of the two for equal soundness error proba-
bilities. Their complexity is largely dictated by the
number of rounds t.
For the new primality predicates proposed in this
work, we find that they excel at proving the primality
of small primes. While the deterministic Miller test
((µ ∈ primes
M
(t))) realized here only allows proving
SECRYPT 2021 - 18th International Conference on Security and Cryptography
70
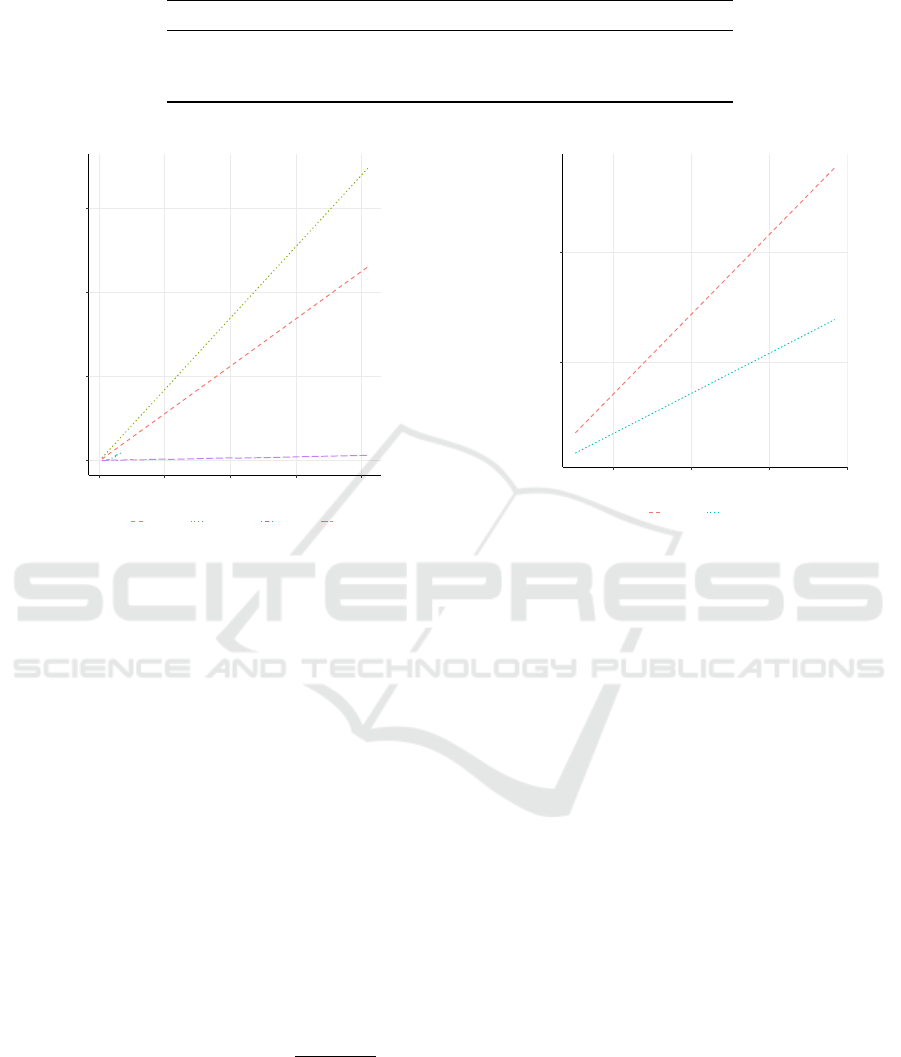
Table 3: Computation complexity of constituent predicates for k rounds.
Computations (mexp)
(µ ∈ primes
L
(t)) 2t logn +(7t logn)k
(µ ∈ primes
M
(t)) 4 +6 log n + (13 + 12t +(3t + 1)(7log n))k
ν
j
∈ primes
P
(ν
j−1
,ρ
j
,χ
j
)
18 +3 log n + (29 + 7log n)k
Note: mexp = multi-base exponentiations.
0e+00
2e+07
4e+07
6e+07
0 250 500 750 1000
Bitlength(n)
#MExp
Scheme
Lehmann Miller−Rabin Det.Miller Pocklington
Figure 2: Number of multi-base exponentiations by
bitlength of n for a primality ZK argument on primes n,
with a fixed number of rounds k = 80 and a soundness error
probability of at most 2
−80
+ 2
−80
.
the primality of primes of a max bitlength of 81,
it can be computed with a small number of fixed
based for each bitlength. The Pocklington witness
sequence employs (ν
j
∈ primes
P
(ν
j−1
,ρ
j
,χ
j
)) recur-
sively from a threshold bitlength of 32 bits yielding
the recursion base with a deterministic Miller test
(µ ∈ primes
M
(t)). Each recursion step doubles the
bitlength of the intermediate prime, which leads to a
logarithmic growth of the length t of the Pocklington
sequence in the bitlength of n.
To put the recursive Pocklington sequence simu-
lation on even footing with the other primality predi-
cates, we included an estimate of the cost that each
Pocklington step j needs to find by trial-and-error
a new integer r
j
to construct the subsequent prime
p
j
. Given ` as bitlength of that prime, we use as
expected number of intermediary Miller-Rabin (MR)
tests computed per recursion step
1−1/(ln(2)`)
1/(ln(2)`)
. We
account for two multi-base exponentiations per MR
trial.
5e+08
1e+09
2000 4000 6000 8000
Bitlength(n)
#MExp
Scheme
Lehmann Lehmann−Pocklington
Figure 3: Number of multi-base exponentiations by
bitlength of n for the proof that a number n is the product of
two safe primes, with a fixed number of rounds k = 80 and
a soundness error probability of at most 2
−80
+ 2
−80
.
7.2 SRSA ZK Arguments
We simulated the zero-knowledge argument that a
number n is product of two safe primes, compar-
ing Camenisch and Michels’ method based on the
Lehmann primality criterion and our new construc-
tion using a Pocklington witness from Section 5.3.
Figure 3 shows the comparison in number of multi-
base exponentiations by bitlength of the product n. In
the figure, we can clearly see that new Pocklington-
Lehmann ZK argument is more efficient and its com-
plexity in mexp growing more slowly that the ZK ar-
gument by Camenisch and Michels. It is, thereby,
more suitable to compute large special RSA moduli
for strong key strengths. For instance, the number of
mexp the CM-algorithm uses to establish a ZK argu-
ment that a 2048-bit number is a special RSA modu-
lus is roughly the same as to make an equivalent ZK
argument for a 4096-bit number with our new method,
maximum soundness error probabilities being equal.
7.3 Hash-to-Prime ZK Arguments
We simulated the expected computational complex-
ity of the hash-to-prime zero-knowledge arguments.
Hashing to Prime in Zero-Knowledge
71
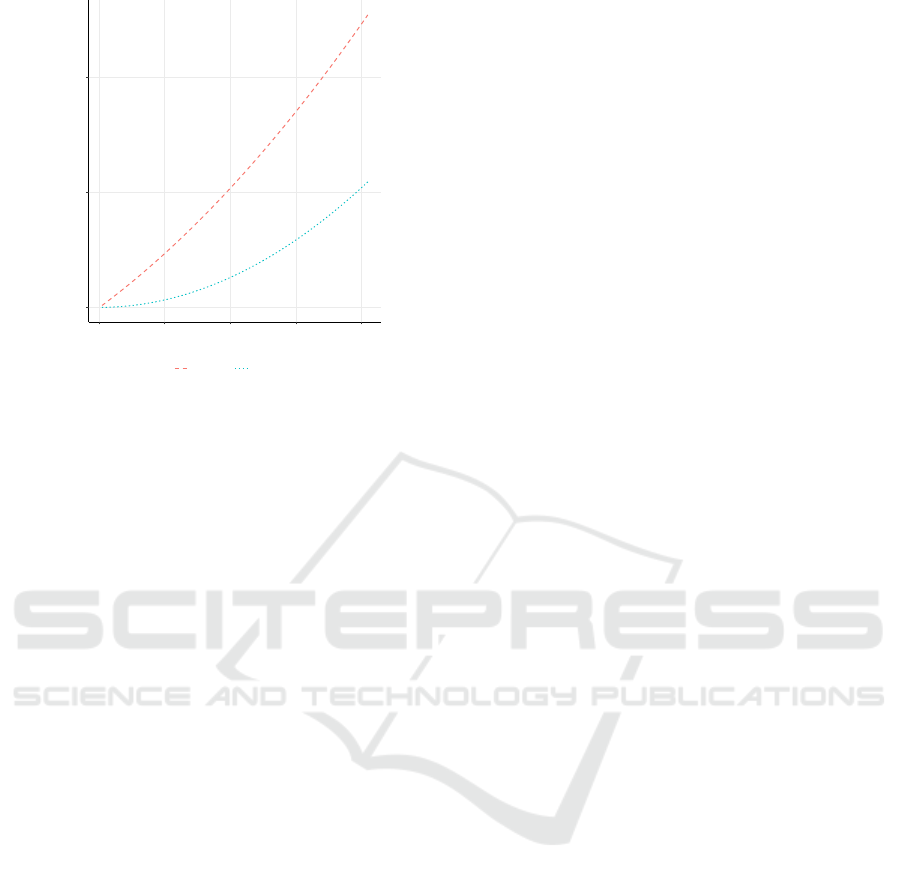
0e+00
5e+08
1e+09
0 250 500 750 1000
Bitlength(n)
#MExp
Scheme
Exclusion Recursive Construction
Figure 4: Expected number of multi-base exponentiations
for prove predicate (µ = hashToPrime(ν)) by bitlength of
the output prime p
x
.
We computed the expected number of multi-base ex-
ponentiations for making a zero-knowledge argument
that a committed prime p
x
is the outcome of a hash-to-
prime operation on a committed input x. We evaluate
that based on the bitlength of the output prime p
x
. The
simulation takes into account the expected number of
eliminated prime candidates at each stage and thereby
the expected number of calls to the composite() pred-
icate. Figure 4 illustrates the outcome of the complex-
ity simulation.
We observe in this analysis that the predicate
µ = hashToPrime
ϒ
F
(ν,t, u)
is considerably more
efficient when realized by recursive construction (R)
than by elimination (E). This efficiency comes with a
trade-off in prime distribution. Whereas the elimina-
tion method yields primes that are statistically closely
distributed to uniform at random, the recursive con-
struction method yields primes with less entropy and
not uniformly distributed. We note that the recursive
construction method is quite efficient for hashing to
primes with less than 256 bits.
8 CONCLUSION
We showed zero-knowledge arguments for determin-
istic Miller and Pocklington witness primality, as well
as Special RSA modulus correctness. We constructed
hash-to-prime zero-knowledge arguments by elimina-
tion and recursion.
ACKNOWLEDGMENT
The author would like to thank Ioannis Sfyrakis
and Syh-Yuan Tan for the discussions on hashing-to-
prime primitives. This work was funded by the ERC
Starting Grant CASCAde (GA n
o
716980).
REFERENCES
Bari
´
c, N. and Pfitzmann, B. (1997). Collision-free accumu-
lators and fail-stop signature schemes without trees.
In International Conference on the Theory and Appli-
cations of Cryptographic Techniques, pages 480–494.
Springer.
Brillhart, J., Lehmer, D. H., and Selfridge, J. L. (1975).
New primality criteria and factorizations of 2ˆ{m}±1.
Mathematics of computation, 29(130):620–647.
Cachin, C., Micali, S., and Stadler, M. (1999). Compu-
tationally private information retrieval with polylog-
arithmic communication. In International Confer-
ence on the Theory and Applications of Cryptographic
Techniques, pages 402–414. Springer.
Camenisch, J. and Groß, T. (2008). Efficient attributes for
anonymous credentials. In Proceedings of the 15th
ACM conference on Computer and communications
security (CCS 2008), pages 345–356. ACM Press.
Camenisch, J. and Groß, T. (2012). Efficient attributes
for anonymous credentials. ACM Transactions on In-
formation and System Security (TISSEC), 15(1):4:1–
4:30.
Camenisch, J., Krenn, S., and Shoup, V. (2011). A
framework for practical universally composable zero-
knowledge protocols. In International Conference on
the Theory and Application of Cryptology and Infor-
mation Security, pages 449–467. Springer.
Camenisch, J. and Lysyanskaya, A. (2002). Dynamic
accumulators and application to efficient revocation
of anonymous credentials. In Annual International
Cryptology Conference, pages 61–76. Springer.
Camenisch, J. and Michels, M. (1999). Proving in zero-
knowledge that a number is the product of two safe
primes. In International Conference on the Theory
and Applications of Cryptographic Techniques, pages
107–122. Springer.
Camenisch, J. and Stadler, M. (1997). Efficient group signa-
ture schemes for large groups. In Annual International
Cryptology Conference, pages 410–424. Springer.
Etzel, M., Patel, S., and Ramzan, Z. (1999). Square hash:
Fast message authentication via optimized universal
hash functions. In Annual International Cryptology
Conference, pages 234–251. Springer.
Goldreich, O., Micali, S., and Wigderson, A. (1991). Proofs
that yield nothing but their validity or all languages in
np have zero-knowledge proof systems. Journal of the
ACM (JACM), 38(3):690–728.
Groß, T. (2015). Signatures and efficient proofs on commit-
ted graphs and NP-statements. In 19th International
Conference on Financial Cryptography and Data Se-
curity (FC 2015), pages 293–314.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
72

Jaeschke, G. (1993). On strong pseudoprimes to several
bases. Mathematics of Computation, 61(204):915–
926.
Kranakis, E. (2013). Primality and cryptography. Springer-
Verlag.
Lehmann, D. J. (1982). On primality tests. SIAM Journal
on Computing, 11(2):374–375.
Menezes, A. J., Van Oorschot, P. C., and Vanstone, S. A.
(2018). Handbook of applied cryptography. CRC
press.
Micali, S., Rabin, M., and Vadhan, S. (1999). Verifiable
random functions. In 40th annual symposium on foun-
dations of computer science (cat. No. 99CB37039),
pages 120–130. IEEE.
Naor, M. and Reingold, O. (1997). Number-theoretic con-
structions of efficient pseudo-random functions. In
Proceedings 38th Annual Symposium on Foundations
of Computer Science, pages 458–467. IEEE.
Ozdemir, A., Wahby, R., Whitehat, B., and Boneh, D.
(2020). Scaling verifiable computation using efficient
set accumulators. In 29th USENIX Security Sympo-
sium (USENIX Security 20), pages 2075–2092.
Pomerance, C., Selfridge, J. L., and Wagstaff, S. S. (1980).
The pseudoprimes to 25 · 10
9
. Mathematics of Com-
putation, 35(151):1003–1026.
APPENDIX
We offer proof sketches for the theorems presented in
the paper. The full version of this paper contains the
corresponding proofs.
Miller Primality Predicate. Let us consider the
proof sketch for Theorem 8:
Proof Sketch. The proof is based on the zero-
knowledge properties of the underlying predicates.
Using standard techniques a knowledge extractor can
extract integers for the secrets in the protocol. Given
that the discrete-logarithm problem in G is assumed
hard and provided that the log
g
h is unknown, then the
equations encoded on generator g hold in the expo-
nent (mod Q). The knowledge extractor gains the
integer ˆn and integers ˆu and ˆe for which it establishes
the relation ˆn −1 = 2
ˆe
ˆu and that ˆu is odd. The knowl-
edge extractor gains bases ( ˆa
j
)
t
j=1
. We are interested
which relations hold for these extracted secrets, espe-
cially the Miller primality relations ˆa
ˆu
j
≡
ˆ
d
j
(mod ˆn)
and ˆa
2
ˆ
k
j
ˆu
j
≡
ˆ
d
0
j
(mod ˆn). That these relations hold
in zero-knowledge follows from Theorem 5.
ˆ
d
j
= 1
and
ˆ
d
0
j
= −1 is established with standard techniques.
Finally, we have that ˆn < 2
˙
`
n
< n
∗
, where n
∗
is the
least integer such that spsp
( ˆa
j
)
t
j=1
,n
∗
. Therefore,
ˆn fulfilling the established relations must be prime.
The primality relation established by the extracted se-
crets are deterministic. Therefore the soundness error
probability is 2
−k
, gained from the number of zero-
knowledge proof rounds k.
Pocklington Primality Witness. The proof sketch
for Theorem 9 is as follows:
Proof Sketch. With standard techniques the knowl-
edge extractor extracts integers for the secrets in the
protocol. Assuming the hardness of the discrete log-
arithm and that log
g
h is unknown, equations encoded
on g hold in the exponent (mod Q). Especially, it
gains ˆp
j−1
, ˆr
j
, ˆp
j
, and ˆa
j
. In the relations it is as-
sured that ˆr
j
and ˆa
j
are positive and that ˆr
j
< ˆp
j
.
Thereby, the conditions for the Pocklington criterion
named in Theorem 4 are fulfilled. Two aspects re-
main to show: First, ˆa
ˆp·ˆr
≡ 1 (mod ˆp
0
j
), which fol-
lows from Theorem 5 and the standard comparison
of
ˆ
d with 1. Second, gcd( ˆa
ˆr
i
− 1, ˆp
i
) is shown with
the predicate (gcd(x, y) = 1). Provided that ˆp
j−1
is
prime and that these two relations have been estab-
lished, by ˆp
j
is prime by Theorem 4. The soundness
error probability of 2
−k
stems from the k rounds of
the zero-knowledge proof.
Special RSA Modulus. We sketch the proof for
Theorem 10:
Proof Sketch. It is standard to construct knowledge
extractors for the given protocol and to establish the
relation between the secrets showing that the follow-
ing relations between extracted integers hold hold:
ˆp = 2
˜
ˆp + 1, ˆq = 2
˜
ˆq +1, and ˆn = ˆp ˆq.
The primality of ( ˆp − 1)/2 and ( ˆq − 1)/2 is estab-
lished as a zero-knowledge argument governed by
Theorem 6, yielding a soundness error probability of
2
−k
+ 2
−t
with t being the number of Lehmann pri-
mality bases employed. The primality of ˆp and ˆq is
given by the Pocklington witness zero-knowledge ar-
gument established in Theorem 9. The latter proven
with one base only per predicate and has a soundness
error probability of 2
k
.
Secret Hash-to-Prime. Let us consider the proof
sketch for the Theorems 11 and 12.
Proof Sketch. For the secrets derived by the knowl-
edge extractor, the Theorems 6, 8, and 9 govern
that the committed integer ˆp
x
is indeed prime with
a primality soundness error probability of at most
2
−t
. Furthermore, proof predicates
µ = H
ζ,β
(ν)
and
Hashing to Prime in Zero-Knowledge
73

µ = PRG
ξ
(ν)
govern that the outputs of hash func-
tion and PRG were computed correctly. It remains
to show that the prime ˆp
x
is indeed the first prime
in the sequence ˆy
i
established by the known indices
i = 1,.. .,u. For each ˆy
i
with i = 1,... ,u−1, the pred-
icate (µ ∈ composites()) establishes that ˆy
i
is com-
posite by Theorem 7. By contradiction, if ˆy
i
were
prime, it holds by Theorem 2, Clause 1, that ∀a ∈ Z
∗
n
:
a
(n−1)/2
≡ ±1 (mod n). Hence, an extracted base ˆa ∈
Z
∗
Q
such that ˆa
( ˆn−1)/2
6≡ ±1 (mod ˆn) does not exist.
Consequently, the sequence ( ˆy
i
)
u−1
i=1
does not contain
a prime. Therefore, the overall soundness error prob-
ability of (µ = hashToPrime
E
(ν,t)) is at most 2
−k
+
2
−t
and of (µ = hashToPrime
R
(ν,t)) is 2
−k
. We note
that the predicates
µ = hashToPrime
ϒ
E
(ν,t, u)
and
µ = hashToPrime
ϒ
R
(ν,t, (n
j
)
t
j=0
)
declare as pub-
lic knowledge the number of eliminated prime can-
didates u and (n
j
)
t
j=0
, respectively, in the predicate
specification.
SECRYPT 2021 - 18th International Conference on Security and Cryptography
74
