
Adopting Formal Verification and Model-Based Testing Techniques for
Validating a Blockchain-based Healthcare Records Sharing System
Rateb Jabbar
1,2
, Moez Krichen
3
, Noora Fetais
1
and Kamel Barkaoui
2
1
KINDI Center for Computing Research, College of Engineering, Qatar University, Doha, Qatar
2
Cedric Laboratory, Computer Science Department, Conservatoire National des Arts et Metiers, France
3
ReDCAD Laboratory, University of Sfax, Tunisia
Keywords:
Health Records, Sharing System, Blockchain, Etherum, BiiMED, Formal Verification, Model-Based Testing.
Abstract:
The Electronic Health Records (EHR) sharing system is the modern tool for delivering efficient healthcare
to patients. Its functions include tracking of therapies, monitoring of the treatment effectiveness, prediction
of outcomes throughout the patient’s lifespan, and detection of human errors. For all the stakeholders, in-
tegrity and interoperability of the care continuum are paramount. Yet, its implementation is challenging due
to the heterogeneity of healthcare information systems, security threats, and the enormousness of EHR data.
To overcome these challenges, this work proposes BiiMED: a Blockchain framework for Enhancing Data
Interoperability and Integrity regarding EHR-sharing. This solution is innovative as it contains an access
management system allowing the exchange of EHRs between different medical providers and a decentral-
ized Trusted Third Party Auditor (TTPA) for ensuring data integrity. This paper also discusses two validation
techniques for enhancing the quality and correctness of the proposed solution: Formal Verification and Model-
Based Techniques. The first one checks the correctness of a mathematical model describing the behavior of the
given system prior to the implementation. The second technique derives test suites from the adopted model,
performs them, and assesses the correctness.
1 INTRODUCTION
According to the National Alliance for Health Infor-
mation Technology (NAHIT), interoperability repre-
sents the capacity of different software applications
and information technology systems to communicate
and share data consistently, effectively, and accurately
(K. Heubusch, 2006). In this study, we propose an
institution-driven interoperability, called BiiMED, in
order to improve data interoperability (W. J. Gor-
don and C. Catalini, 2018) and enable the exchange
of data between different medical providers. Our
Blockchain-based framework allows establishment of
the communication between medical providers who
store medical data in the cloud and exchange Elec-
tronic Health Records. The study uses Decentral-
ized Trusted Third Party Auditor (TTPA) to validate
shared data and ensure data integration. The proposed
solution aims at minimizing costs while enhancing
immutability, integrity, and interoperability.
Moreover, our work deals with the so-called
model-based testing (MBT) and formal verification
(FV) which may be seen as a formal methods and may
be used for validating the proposed solution. Gen-
erally, MBT and FV are likely to face the famous
state explosion challenge. The latter corresponds to
the fact that test generation and system formal veri-
fication may need an immense amount of time and a
enormous space to produce and save the set of test
scenarios. To solve this problem, we propose to adopt
a set of methods borrowed from our previous works
and the literature aimed at diminishing the duration,
complexity and cost of verification and test genera-
tion.
The rest of this document in structured as follows.
In Section 2, we provide some preliminaries about
formal methods, model based testing, the timed au-
tomaton model and the diff rent kinds of testers. In
Section 3, we provide an overview about our adopted
solution. Section 4 deals with evaluation metrics. In
Section 5, we outline the several techniques to adopt
for improving formal verification methods. Simi-
larly, details about the techniques to use for improving
model based testing techniques are given in Section 6.
Finally Section 7 concludes the paper and gives direc-
tions for future work.
Jabbar, R., Krichen, M., Fetais, N. and Barkaoui, K.
Adopting Formal Verification and Model-Based Testing Techniques for Validating a Blockchain-based Healthcare Records Sharing System.
DOI: 10.5220/0009592102610268
In Proceedings of the 22nd International Conference on Enterprise Information Systems (ICEIS 2020) - Volume 1, pages 261-268
ISBN: 978-989-758-423-7
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
261

2 PRELIMINARIES
2.1 Formal Methods
During the last years of the 20th century, scientists
started developing more accurate and sophisticated
computerized systems verification methods (Clarke
and Emerson, 1982; Queille and Sifakis, 1982).
The first formal verification methodologies appeared
with the emergence of mathematical formalisms for
the specification of computerized systems (Kripke,
1963). There are tow main categories of formal veri-
fication techniques, namely: model checking (Clarke
and Emerson, 1982; Queille and Sifakis, 1982) and
automated theorem proving (Gordon and Melham,
1993; Nipkow et al., 2002; Bertot and Castran, 2010).
2.2 Model Based Testing
Model-Based Testing (MBT) (Krichen, 2012;
Krichen, 2018; Krichen and Tripakis, 2006a; Krichen
and Tripakis, 2004) is a methodology where the sys-
tem of interest is described by a mathematical model
which encodes the behavior of the considered system.
This methodology consists in using this mathematical
model to compute abstract test scenarios. These
sequences are then transformed into concrete test
sequences which are executed on the considered
system under test. The verdict of this testing activity
is provided by comparing the observed outputs from
the system with the outputs generated by the model.
2.3 Timed Automata
Timed Automata (TA) (Sifakis and Yovine, 1996) rep-
resents an expressive and simple tool for describing
the behavior of computer systems which combines
continuous and discrete mechanisms. TA may be rep-
resented as finite graphs enriched with a finite set of
clocks defined as real entities whose value progresses
continuously over time.
3 PROPOSED SOLUTION
The work presents the proposed health information
system (HIS) and reviews the Blockchain framework
BiiMED.
3.1 Health Information System (HIS)
The purpose of developing a part of the informa-
tion system HIS is to examine the interactions be-
tween different health care compounds. Its functions
include collections, storage, and share of electronic
medical records (EMR), management of hospital op-
erations, and improvement of healthcare policy de-
cisions. The HIS respect ICD 10 standard proposed
by the World Health Organization’s (WHO). ICD 10
provides codes for abnormal cases, complaints, social
context, external causes of diseases or injuries, signs,
symptoms, and illnesses. The developed system also
applies DICOM - Digital Imaging and COMmunica-
tions in Medicine, which is an accepted standard for
communicating and managing medical imaging infor-
mation and transmission and storing of images. The
HIS also complies with a standard electronic health
record data model called the virtual Medical Record
(vMR). The vMR backs up the interfacing of clini-
cal decision support (CDS) systems and the sharing
of EHRs among healthcare providers.
The proposed architecture the HIS consists of two
layers Front-end and the Back-end layers as described
below:
The Front-end: contains web portals for healthcare
providers, such as the Medical Staff portal and the
Admin portal. Figure 1 illustrates how the medi-
cal staff interacts with the healthcare system through
these portals.
The Back-end Layer: enables communication and
sharing of the data among different software compo-
nents of the system through the web service. The
Back-end layer also includes a Medical Record server
for storing Binary Large Objects (BLOB), such as CT
Images and radio images, and the database server for
storing relational data.
3.2 BiiMED
BiiMED is responsible for management and vali-
dation of data sharing between medical facilities.
The Ethereum platform was used to construct the
Blockchain Framework by 10 Ethereum nodes, and
the Solidity language was employed to build smart
contracts. Two nodes in charge of mining were de-
ployed in Amazon servers. The Blockchain Frame-
work is composed of the following modules:
Access Management System: allows hospitals to
connect to each other in order to exchange EHR and to
validate the shared data with the Trusted Third Party
Auditor (TTPA).
• User Management Module: includes the medical
facility Management contract that allows the ad-
dition, the modification and the suppression of a
new medical facility in the system.
ICEIS 2020 - 22nd International Conference on Enterprise Information Systems
262
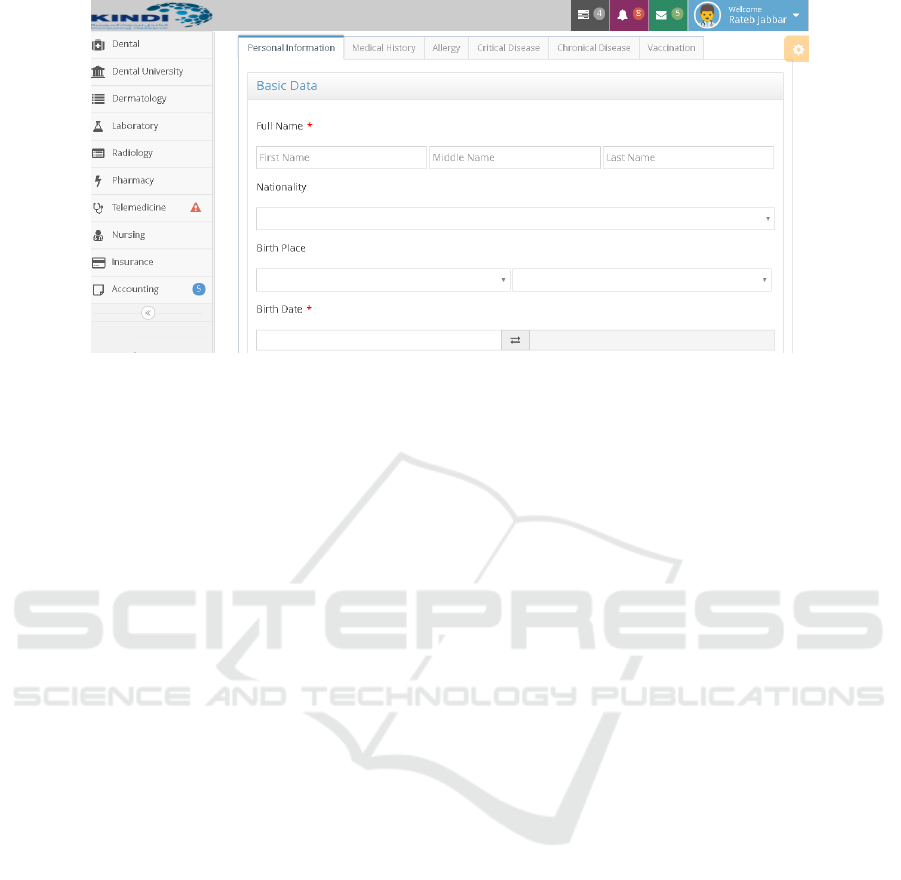
Figure 1: Screenshot from the Medical Staff Portal- HIS.
• Exchange Management Module: includes two
types of contracts: The Medical Facility Access
management contract and the Trusted Third Party
Auditor Access management contract. The first
contract is responsible for access management
for shared data. In order to retrieve a patient
data from the shared data, the access manage-
ment contract must be called to provide a key
that allows the HIS of the medical facility to ac-
cess the shared data. The second contract allows
the Medical Facility System to access the Trusted
Third Party Auditor, responsible for validating the
shared data.
Trusted Third Party Auditor (TTPA). This work
also introduces the Trusted Third-Party Auditor
(TTPA) based on Blockchain technologies, which val-
idates the shared data. The TTPA stores the medi-
cal records of patients. The EHR folder is managed
by the patient management contract. First, HIS re-
trieves shared data from another medical facility. Sec-
ond, it compares the hash of shared data with the
stored hash to verify the integrity. The Blockchain
layer and the API server construct decentralized ap-
plications (Dapp, dApp, or DApp) - distributed Inter-
net Apps operating on a decentralized P2P network
(Blockchain). The front-end layers are the API and
the medical portal, while the Blockchain layer in De-
centralized Apps is the back-end layer. The smart
contract function deployed in every Ethereum node
is called when the API sends a message through the
Blockchain network.
3.3 Nominal Scenario
This part introduces the nominal scenario of sharing
EHRs between medical facilities. In the HIS, the
data access management module uses the function
“AddMedicalFacility” in the smart contract “Medi-
calFacilityManagement” to perform the medical fa-
cility authentication and authorization management.
This function receives the name and the address of
the medical facility and gives it a unique ID to man-
age the patient’s record in the API server. Moreover,
the function “MedicalFacilityManagement” updates
and removes Medical Facilities and adds authorities.
Once the Medical Facility is added to the BiiMED, it
has permission to add a patient record.
The patient provides personal data, including
medical history, personal information, vital sign mea-
surement, analyses and diagnostics, and any new in-
formation is added to the EHR. Subsequently, the
EHR is hashed and delivered to the Blockchain frame-
work. The smart contract of the Trusted Third-Party
Auditor (TTPA) allows adding, updating, and remov-
ing records. The function “AddPatientRecord” holds
information such as a medical facility ID, a unique
patient’s ID, date and time, and hash, and incorpo-
rates them into the Blockchain network. The function
“UpdatePatientRecord” updates the EHR. The Medi-
cal Facility Management System receives the unique
patient’s ID and sends a request to the Exchange
Management Contract in the Blockchain layer by
“GetMedicalFacilityAccess” data. The access man-
agement system verifies the access request from the
medical provider and sends a key that enables the
communication with Medical Providers HIS and the
Read/Write of the patient’s medical folder. Subse-
quently, the received data is hashed and compared to
Adopting Formal Verification and Model-Based Testing Techniques for Validating a Blockchain-based Healthcare Records Sharing System
263

the hash in the Trusted Third-Party Auditor (TTPA)
system obtained by “GetPatientRecord”.
4 EVALUATION METRICS
We used a set of evaluation metrics proposed by
Zhang et al(P. Zhang, et al., 2017) . To assess the
performance of DApps. The assessment revealed
that the framework ensures Turing-complete opera-
tions, user identification and authentication, scalabil-
ity across large populations of patients, structural in-
teroperability at the minimum and cost-effectiveness.
4.1 Support Turing-completeness
Blockchain platforms are primarily used for commod-
ity exchange, as Bitcoin (S. Nakamoto, 2008) is pri-
marily a cryptocurrency for buying and selling com-
modities in a safe marketplace pseudo-anonymously.
Likewise, Litecoin (Reed, 2017) represents digi-
tal cash for merchandise. Thus, the purpose of
Blockchain-based Cryptocurrencies is not to support
Turing-Completeness since it does not allow the ex-
change of data models in different formats. The un-
derlying Blockchain platform of cutting-edge health-
care applications must support Turing-complete op-
erations. More precisely, it must accept smart con-
tract and include programming features for solving
computation problems in order to allow the transfer
of sensitive patient information and communication
between stakeholders. BiiMEd was developed on the
Ethereum platform, which supports Turing-complete
operations.
4.2 Support User Identification and
Authentication
Zhang et al.(P. Zhang, et al., 2017) argue that cut-
ting edge healthcare DApp must support individual
and organizational user identification and authenti-
cation. Receiving information on new accounts and
access to the accounts is critical for ensuring secu-
rity. To resolve this issue, BiiMED contains authen-
tication techniques in the access management module
for managing the identification and authentication of
users and institutions.
4.3 Support of Structural
Interoperability at the Minimum
DApp alone cannot ensure semantic interoperability.
Therefore, it is essential to ensure that a DApp sup-
ports minimum structural interoperability and poten-
tially semantic interoperability to fulfill the require-
ments of the healthcare system. The sharing of clin-
ical data and their interpretations concerning imple-
mented formats and structures is critical. Neverthe-
less, as the diverging of data models within the DApp
can lead to excessive complexity, it is necessary to
comply with widely accepted data standards. The
HIS supports contemporary standards such as virtual
Medical Record (vMR) for electronic health records,
DCOM for communication and management of med-
ical imaging information, and ICD-10 for Classifica-
tion of Diseases and Related Health Problems. Fur-
thermore, BiiMED supports structural interoperabil-
ity at a minimum to exchange data with HIS.
4.4 Scalability across Large Populations
of Patients
Furthermore, scalability is essential as DApp provides
services to millions of patients, and it must handle
enormous traffic on the Blockchain, which in this
case, are the patient information stored by a DApp.
BiiMED, a server with a configuration of 8 GB Ram
and a Core i7-000, was used to carryout the perfor-
mance test of the system capability. The average
server’s response time of each function was calcu-
lated on 10,000 users. Figure 2 illustrates the shorter
response time of the server of the ”GetMedicalFa-
cilityInformation,” ”GetMedicalFacilityInformation,”
and ”GetPatientRecord” functions in comparison to
the other functions as they do not require mining for
interacting with the smart contract. BiiMED is proven
as scalable as calling any function requires between 4
millisecond and 20 milliseconds.
4.5 Cost-effectiveness Compared to
Current Approaches
The Testnet of the Ethereum network was used to
deploy the smart contract’s prototype and to test the
cost-effectiveness of the BiiMED. The following val-
ues were used, as valid in November 2019: 1 gas
1 wei (0.000000001 ETH) and 1 ETH 142.77 US.
The transactions use the minimum gas value of 1
wei, while the typical gas value was approximately
0.008026 Ethereum at the moment of analysis. Figure
3 shows the execution costs of various functions of the
BiiMED. The analysis revealed that “UpdatePatien-
tRecord”, “GetMedicalFacilityAccess”, and “GetPa-
tientRecord” are the most frequent functions. The av-
erage cost of “UpdatePatientRecord” is $0.00958 US
on average, while the functions “GetMedicalFacility-
Access”, and “GetPatientRecord” do not incur further
ICEIS 2020 - 22nd International Conference on Enterprise Information Systems
264
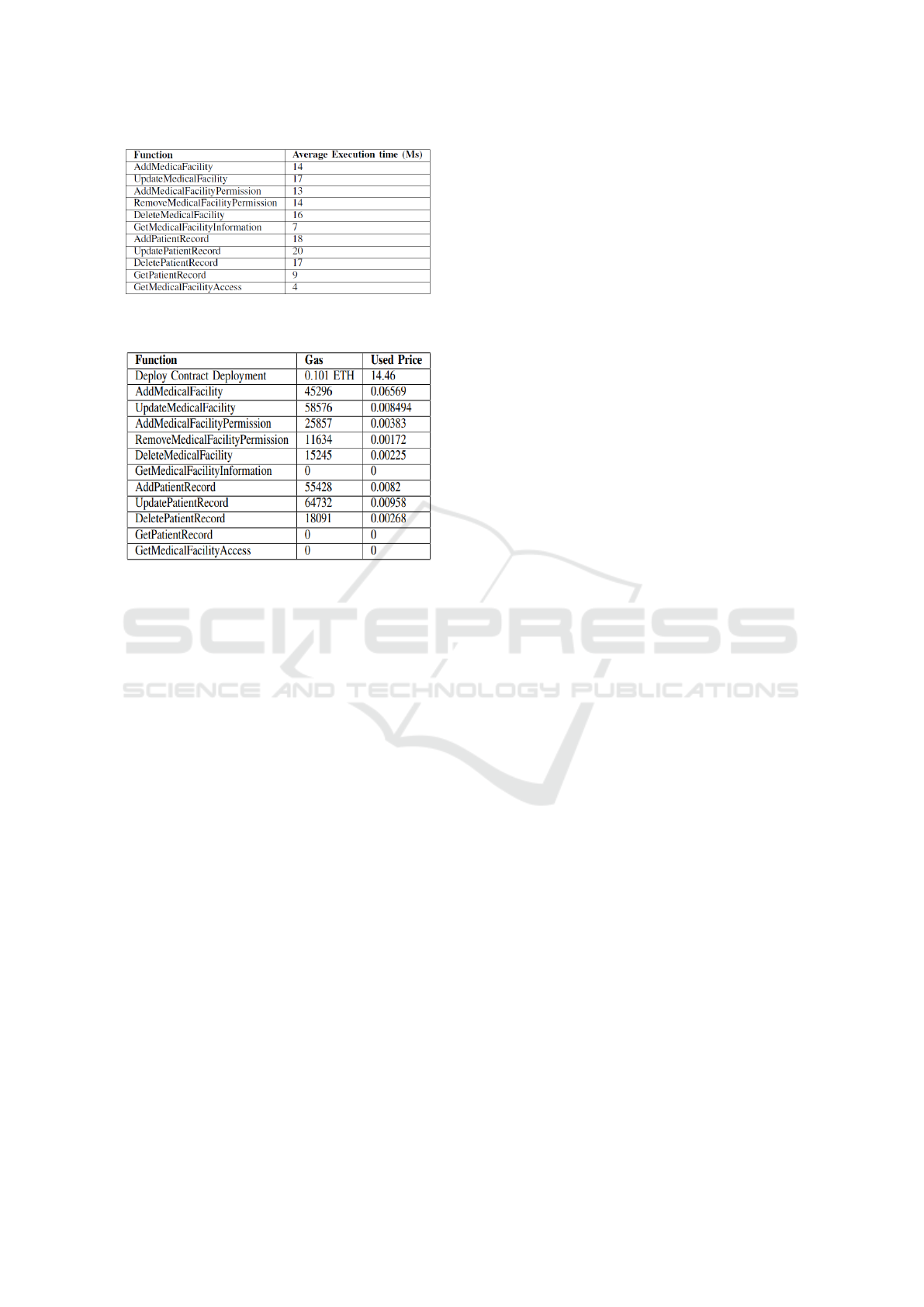
Figure 2: Execution time of the different functions in the
BiiMED in milliseconds.
Figure 3: Costs of the BiiMED functions based on 1 ETH
=142.77 USD.
costs as no mining is required.
5 IMPROVING FORMAL
VERIFICATION METHODS
In this section, we outline several techniques for
adoption in order to improve FV methods.
5.1 Abstraction
The authors of (Thacker et al., 2010) focused on ver-
ifying cyber-physical systems. Fundamentally, they
applied specific transformations to remove details ir-
relevant to the properties of interest. Similarly, the
authors of (Andraus and Sakallah, 2004) proposed a
collection of languages for modelling hardware sys-
tems. Wide datapaths were abstracted away and low-
level details corresponding to the control logic were
kept.
5.2 Symmetry Identification
Symmetry identification (Wahl and Donaldson, 2010;
Kwiatkowska et al., 2006; Emerson and Wahl, 2005;
Iosif, 2002; Norris IP and Dill, 1996) is a method
based on using symmetries which occur during the
execution of the system, for the purpose of minimiz-
ing the considered state space. This method enables
a computation of a mapping between the set of states
of the system and the representatives of the classes of
equivalences.
5.3 Data Independence Identification
Data independence identification (Benalycherif and
McIsaac, 2009; Momtahan, 2005) is another method
to be be adopted for reducing the complexity of for-
mal verification. This method can be used in the case
where the designer of the system under verification
identifies the fact that the behavior of the system is
independent of some particular inputs. In this situa-
tion, the designer can reduce the size of the model of
the considered system significantly.
5.4 Removing Functional Dependencies
In (Chih-Chun Lee et al., 2007) functional depen-
dency is detected using Craig interpolation methods
SAT solving and SAT solving. In (Jiang and Brayton,
2004), the authors detected functional dependencies
from transition functions and not from the computa-
tion of the reachable states.
5.5 Exploiting Reversible Rules
This method (Ip, 1998) allows the collapse of the sub-
graphs of the state graph into abstract states (named
progenitors). This operation is performed by defining
generation principles which may be reversed.
6 IMPROVING TESTING
METHODS
In this section, we explain several techniques for
adopting to improve formal model-based techniques.
6.1 Refinement Techniques
These techniques consist in converting high-level
symbols into sequences of lower-level symbols. In
(Bensalem et al., 2007), the authors proposed a refine-
ment based methodology for testing timed systems.
6.2 Diminishing the Size of Testers
Digital testers may become very large since they may
contain very long sequences of tick actions. A possi-
ble solution to tackle this problem is to extend testers
Adopting Formal Verification and Model-Based Testing Techniques for Validating a Blockchain-based Healthcare Records Sharing System
265

with more sophisticated variables and data structures
(Krichen, 2007).
6.3 Producing Timed Automata Testers
In general, one cannot transform a non-deterministic
timed automaton into deterministic one by using a fi-
nite number of resources (i.e., nodes, transitions, ac-
tions and clocks). Alternatively, it is possible to pro-
duce a deterministic approximation of the tester in
the form of a timed automaton using appropriate al-
gorithms and heuristics such as the ones presented
in (Bertrand et al., 2015; Bertrand et al., 2011b;
Bertrand et al., 2012; Bertrand et al., 2011a; Krichen,
2007; Krichen, 2018).
6.4 Upgrading Test Scenarios after
System Update
This method (Lahami et al., 2016; Lahami et al.,
2015b; Lahami et al., 2015a; Lahami et al., 2012)
enables the optimization of the test synthesis phase
when a dynamic evolution of the considered system
occurs. The model of the system may change either
completely or partially after a behavioral evolution
occurs. As a consequence, an upgrade of the col-
lection of available test scenarios either by producing
new test scenarios or updating old ones is required.
6.5 Coverage Techniques
Several coverage techniques, such as statement cov-
erage and branch cover- age, can be used in the test-
ing field (Myers, 1979). Similarly, for timed systems
existing methodologies (Krichen, 2007; Hessel et al.,
2003) can be used for the coverage of specific enti-
ties of the considered system in order to diminish the
number of generated test cases significantly.
6.6 State Identification
The state identification problems (Krichen and Tri-
pakis, 2006b; Krichen and Tripakis, 2005b; Krichen
and Tripakis, 2005a) were initially introduced for the
case of finite state machines (FSMs). The solution for
this problem consists in identifying either the initial
or the final state of the considered machines.
7 CONCLUSION & FUTURE
WORK
This paper introduced BiiMED, a Blockchain frame-
work for Enhancing Data Interoperability and In-
tegrity concerning EHR sharing. The solution used
a prototype of the smart contract on the Testnet of
Ethereum. BiiMED incorporates the access man-
agement system to allow sharing of EHRs among
healthcare providers. It also contains a decentral-
ized Trusted Third Party Auditor (TTPA) for ensur-
ing data integrity. Finally, the Health Information
System (HIS) supervises the interactions of various
health care compounds. The following properties
were tested to assess the proposed solution: cost-
effectiveness, structural interoperability at the mini-
mum, user identification and authentication, scalabil-
ity across large populations of patients, and Turing-
complete operations. Furthermore, this paper pro-
posed a set of techniques to facilitate the solving of
the state explosion problem that may be encountered
when adopting FV and/or MBT techniques during the
validation process of the adopted solution.
In the future, our priority will be to implement
the different proposed techniques in order to vali-
date them. Moreover we may need to combine both
Load and Functional testing procedures as proposed
in (Krichen et al., 2018; Ma
ˆ
alej and Krichen, 2016;
Ma
ˆ
alej and Krichen, 2015; Ma
ˆ
alej et al., 2013; Ma
ˆ
alej
et al., 2012b; Ma
ˆ
alej et al., 2012a) in order to take
into account the correlation existing between these
two types of testing methods.
ACKNOWLEDGEMENTS
This publication was made possible by QUCP-
CENG-2019-1 grant from the Qatar University. The
statements made herein are solely the responsibility
of the authors.
REFERENCES
Andraus, Z. S. and Sakallah, K. A. (2004). Automatic ab-
straction and verification of verilog models. In Pro-
ceedings of the 41st Annual Design Automation Con-
ference, DAC ’04, pages 218–223, New York, NY,
USA. ACM.
Benalycherif, L. and McIsaac, A. (2009). A semantic con-
dition for data independence and applications in hard-
ware verification. Electronic Notes in Theoretical
Computer Science, 250(1):39 – 54. Proceedings of the
Seventh International Workshop on Automated Verifi-
cation of Critical Systems (AVoCS 2007).
Bensalem, S., Krichen, M., Majdoub, L., Robbana, R.,
and Tripakis, S. (2007). A simplified approach for
testing real-time systems based on action refinement.
In ISoLA, volume RNTI-SM-1 of Revue des Nou-
velles Technologies de l’Information, pages 191–202.
C
´
epadu
`
es-
´
Editions.
ICEIS 2020 - 22nd International Conference on Enterprise Information Systems
266

Bertot, Y. and Castran, P. (2010). Interactive Theorem Prov-
ing and Program Development: Coq’Art The Calcu-
lus of Inductive Constructions. Springer Publishing
Company, Incorporated, 1st edition.
Bertrand, N., J
´
eron, T., Stainer, A., and Krichen, M.
(2011a). Off-line test selection with test purposes for
non-deterministic timed automata. In Tools and Algo-
rithms for the Construction and Analysis of Systems -
17th International Conference, TACAS 2011, Held as
Part of the Joint European Conferences on Theory and
Practice of Software, ETAPS 2011, Saarbr
¨
ucken, Ger-
many, March 26-April 3, 2011. Proceedings, pages
96–111.
Bertrand, N., J
´
eron, T., Stainer, A., and Krichen, M. (2012).
Off-line test selection with test purposes for non-
deterministic timed automata. Logical Methods in
Computer Science, 8(4):1–33.
Bertrand, N., Stainer, A., J
´
eron, T., and Krichen, M.
(2011b). A game approach to determinize timed au-
tomata. In International Conference on Foundations
of Software Science and Computational Structures,
pages 245–259. Springer, Berlin, Heidelberg.
Bertrand, N., Stainer, A., J
´
eron, T., and Krichen, M. (2015).
A game approach to determinize timed automata. For-
mal Methods in System Design, 46(1):42–80.
Chih-Chun Lee, Jiang, J. R., Chung-Yang Huang, and
Mishchenko, A. (2007). Scalable exploration of func-
tional dependency by interpolation and incremental
sat solving. In 2007 IEEE/ACM International Con-
ference on Computer-Aided Design, pages 227–233.
Clarke, E. M. and Emerson, E. A. (1982). Design and syn-
thesis of synchronization skeletons using branching-
time temporal logic. In Logic of Programs, Workshop,
pages 52–71, Berlin, Heidelberg. Springer-Verlag.
Emerson, E. A. and Wahl, T. (2005). Dynamic symmetry
reduction. In Halbwachs, N. and Zuck, L. D., editors,
Tools and Algorithms for the Construction and Anal-
ysis of Systems, pages 382–396, Berlin, Heidelberg.
Springer Berlin Heidelberg.
Gordon, M. J. C. and Melham, T. F., editors (1993). In-
troduction to HOL: A Theorem Proving Environment
for Higher Order Logic. Cambridge University Press,
New York, NY, USA.
Hessel, A., Larsen, K., Nielsen, B., Pettersson, P., and Skou,
A. (2003). Time-optimal real-time test case generation
using UPPAAL. In FATES’03.
Iosif, R. (2002). Symmetry reduction criteria for software
model checking. In Bo
ˇ
sna
ˇ
cki, D. and Leue, S., edi-
tors, Model Checking Software, pages 22–41, Berlin,
Heidelberg. Springer Berlin Heidelberg.
Ip, C. N. (1998). Generalized reversible rules. In Pro-
ceedings of the Second International Conference on
Formal Methods in Computer-Aided Design, FMCAD
’98, pages 403–420, London, UK, UK. Springer-
Verlag.
Jiang, J.-H. R. and Brayton, R. K. (2004). Functional de-
pendency for verification reduction. In Alur, R. and
Peled, D. A., editors, Computer Aided Verification,
pages 268–280, Berlin, Heidelberg. Springer Berlin
Heidelberg.
K. Heubusch (2006). Interoperability: What it Means, Why
it Matters. Journal of AHIMA, 77(1):26–30.
Krichen, M. (2007). Model-Based Testing for Real-Time
Systems. PhD thesis, PhD thesis, Universit Joseph
Fourier (December 2007).
Krichen, M. (2012). A formal framework for black-box
conformance testing of distributed real-time systems.
IJCCBS, 3(1/2):26–43.
Krichen, M. (2018). Contributions to Model-Based Test-
ing of Dynamic and Distributed Real-Time Systems.
Habilitation
`
a diriger des recherches,
´
Ecole Nationale
d’Ing
´
enieurs de Sfax (Tunisie).
Krichen, M., Ma
ˆ
alej, A. J., and Lahami, M. (2018). A
model-based approach to combine conformance and
load tests: an ehealth case study. IJCCBS, 8(3/4):282–
310.
Krichen, M. and Tripakis, S. (2004). Black-box confor-
mance testing for real-time systems. In 11th Interna-
tional SPIN Workshop on Model Checking of Software
(SPIN’04), volume 2989 of LNCS. Springer.
Krichen, M. and Tripakis, S. (2005a). State identification
problems for finite-state transducers. Technical Re-
port TR-2005-5, Verimag.
Krichen, M. and Tripakis, S. (2005b). State identification
problems for timed automata. In The 17th IFIP Intl.
Conf. on Testing of Communicating Systems (Test-
Com’05), volume 3502 of LNCS. Springer.
Krichen, M. and Tripakis, S. (2006a). Interesting properties
of the conformance relation tioco. In ICTAC’06.
Krichen, M. and Tripakis, S. (2006b). State identification
problems for finite-state transducers. In Formal Ap-
proaches to Testing and Runtime Verification (FATES-
RV’06), LNCS. Springer. To appear.
Kripke, S. A. (1963). Semantical considerations on modal
logic. Acta Philosophica Fennica, 16(1963):83–94.
Kwiatkowska, M., Norman, G., and Parker, D. (2006).
Symmetry reduction for probabilistic model check-
ing. In Ball, T. and Jones, R. B., editors, Computer
Aided Verification, pages 234–248, Berlin, Heidel-
berg. Springer Berlin Heidelberg.
Lahami, M., Fakhfakh, F., Krichen, M., and Jma
¨
ıel, M.
(2012). Towards a TTCN-3 Test System for Run-
time Testing of Adaptable and Distributed Systems.
In Proceedings of the 24th IFIP WG 6.1 International
Conference Testing Software and Systems (ICTSS’12),
pages 71–86.
Lahami, M., Krichen, M., Barhoumi, H., and Jmaiel, M.
(2015a). Selective test generation approach for testing
dynamic behavioral adaptations. In Testing Software
and Systems - 27th IFIP WG 6.1 International Confer-
ence, ICTSS 2015, Sharjah and Dubai, United Arab
Emirates, November 23-25, 2015, Proceedings, pages
224–239.
Lahami, M., Krichen, M., and Jma
¨
ıel, M. (2015b). Run-
time testing approach of structural adaptations for dy-
namic and distributed systems. International Journal
of Computer Applications in Technology, 51(4):259–
272.
Lahami, M., Krichen, M., and Jma
¨
ıel, M. (2016). Safe and
Efficient Runtime Testing Framework Applied in Dy-
namic and Distributed Systems. Science of Computer
Programming (SCP), 122(C):1–28.
Adopting Formal Verification and Model-Based Testing Techniques for Validating a Blockchain-based Healthcare Records Sharing System
267

Ma
ˆ
alej, A. J., Hamza, M., Krichen, M., and Jmaiel, M.
(2013). Automated significant load testing for WS-
BPEL compositions. In Sixth IEEE International Con-
ference on Software Testing, Verification and Vali-
dation, ICST 2013 Workshops Proceedings, Luxem-
bourg, Luxembourg, March 18-22, 2013, pages 144–
153.
Ma
ˆ
alej, A. J. and Krichen, M. (2016). A model based ap-
proach to combine load and functional tests for service
oriented architectures. In VECoS, pages 123–140.
Ma
ˆ
alej, A. J., Krichen, M., and Jmaiel, M. (2012a). Con-
formance testing of WS-BPEL compositions under
various load conditions. In 36th Annual IEEE Com-
puter Software and Applications Conference, COMP-
SAC 2012, Izmir, Turkey, July 16-20, 2012, page 371.
Ma
ˆ
alej, A. J., Krichen, M., and Jmaiel, M. (2012b). Model-
based conformance testing of WS-BPEL composi-
tions. In 36th Annual IEEE Computer Software
and Applications Conference Workshops, COMPSAC
2012, Izmir, Turkey, July 16-20, 2012, pages 452–457.
Ma
ˆ
alej, A. J. and Krichen, M. (2015). Study on the limita-
tions of ws-bpel compositions under load conditions.
The Computer Journal, 58(3):385–402.
Momtahan, L. (2005). Towards a small model theorem
for data independent systems in alloy. Electronic
Notes in Theoretical Computer Science, 128(6):37 –
52. Proceedings of the Fouth International Workshop
on Automated Verification of Critical Systems (AV-
oCS 2004).
Myers, G. (1979). The art of software testing. Wiley.
Nipkow, T., Paulson, L. C., and Wenzel, M. (2002). Is-
abelle/HOL — A Proof Assistant for Higher-Order
Logic, volume 2283 of LNCS. Springer.
Norris IP, C. and Dill, D. L. (1996). Better verification
through symmetry. Formal Methods in System Design,
9(1):41–75.
P. Zhang, et al. (2017). Metrics for assessing blockchain-
based healthcare decentralized apps. IEEE 19th Inter-
national Conference on e-Health Networking, Appli-
cations and Services (Healthcom).
Queille, J.-P. and Sifakis, J. (1982). Specification and ver-
ification of concurrent systems in cesar. In Proceed-
ings of the 5th Colloquium on International Sympo-
sium on Programming, pages 337–351, London, UK,
UK. Springer-Verlag.
Reed, J. (2017). Litecoin: An introduction to litecoin cryp-
tocurrency and litecoin mining.
S. Nakamoto (2008). Bitcoin: A peer-to-peer electronic
cash system.
Sifakis, J. and Yovine, S. (1996). Compositional specifica-
tion of timed systems. In 13th Annual Symposium on
Theoretical Aspects of Computer Science, STACS’96,
volume 1046 of LNCS. Spinger-Verlag.
Thacker, R. A., Jones, K. R., Myers, C. J., and Zheng,
H. (2010). Automatic abstraction for verification
of cyber-physical systems. In Proceedings of the
1st ACM/IEEE International Conference on Cyber-
Physical Systems, ICCPS ’10, pages 12–21, New
York, NY, USA. ACM.
W. J. Gordon and C. Catalini (2018). Blockchain tech-
nology for healthcare: facilitating the transition to
patient-driven interoperability. Computational and
structural biotechnology journal, 16:224–230.
Wahl, T. and Donaldson, A. (2010). Replication and ab-
straction: Symmetry in automated formal verification.
Symmetry, 2(2):799–847.
ICEIS 2020 - 22nd International Conference on Enterprise Information Systems
268
