
On the Impacts of Transitive Indirect Reciprocity on P2P Cloud
Federations
Eduardo L. Falc
˜
ao
1
, Ant
ˆ
onio A. Neto
2
, Francisco Brasileiro
1
and Andrey Brito
1
1
Department of Computing and Systems, Federal University of Campina Grande, Campina Grande, Brazil
2
Department of Exact Sciences, Federal University of Para
´
ıba – Campus IV, Rio Tinto, Brazil
Keywords:
Reciprocity Mechanisms, Resource and Availability Asymmetry, Transitive Reciprocity, Cloud Federations.
Abstract:
Several P2P systems of resource sharing use cooperation incentive mechanisms to identify and punish free
riders, i.e., non-reciprocal individuals. A widespread approach is to use the levels of reciprocity, either di-
rectly or indirectly, to decide the extent to which an individual should trust other partners. One restriction
of direct reciprocity mechanisms is the inability to foster cooperation between individuals with asymmetrical
resources or availability incompatibility. In this work, we evaluate the performance of cloud federations ruled
by the combination of the well-known direct reciprocity with transitive reciprocity, a strategy that allows direct
reciprocity mechanisms to deal with asymmetry between individuals, while still keeping the benefits of direct
reciprocity. For this, we implemented a simulator of resource bartering in cloud federations and experimented
it with workloads synthesized from traces of real systems. Our best results showed an average increase of
12.83% and 26.38% on the sharing level of the federation, in an optimistic but unrealistic mechanism setup.
When configured in a feasible and realistic manner, the transitive reciprocity was able to increase the sharing
level up to an average of 6.02% and 7.53%.
1 INTRODUCTION
One of the challenges with respect to the implemen-
tation of a cloud federation is to design a fair mar-
ket model that satisfies the participants and incen-
tivizes cooperation within the community. In gen-
eral, this resource exchange can be mediated through
monetary markets (Dhuria et al., 2017) or in a barter-
based approach that is often ruled by the tenets of reci-
procity (Haddi and Bencha
¨
ıba, 2015).
Reciprocity mechanisms are categorized by the
way a resource provider assesses the resource re-
questers, which can be via a direct or indirect ap-
proach. In the direct reciprocity, a participant uses
the knowledge she acquired from her own experiences
to assess the past behavior (level of reciprocity) of the
requester. In the indirect reciprocity, however, third
party information can be used for this assessment as
well. Both approaches have advantages and disadvan-
tages that make them suitable for particular scenarios.
It is reasonable to state that the main advantage of di-
rect reciprocity is the integrity of the information an
individual keeps about the behavior of other partic-
ipants, which prevents peer collusion (Ciccarelli and
Cigno, 2011). Since it uses private history, direct reci-
procity mechanisms are more appropriate for small
and mid-sized communities, where repeated interac-
tion among peers is more likely, and also for com-
munities in which the type of resource provided is
the same as the one required, such as CPU, GPU and
storage – the case of cloud federations. On the other
hand, indirect reciprocity mechanisms are commonly
used in large-sized P2P systems with wide-ranging re-
sources (e.g., file sharing systems), where the chances
of a peer meeting another specific peer and satisfy its
requests are rather small.
However, scenarios with availability asymmetry
(Chuang, 2004) (when two peers can not cooperate
because the moments they are consumer and provider,
or vice versa, do not match) or with resource asymme-
try (Feldman et al., 2004) (or conflicts of interests –
when two peers can not cooperate because the type
of resource supplied by the provider is different from
the one required by the consumer) may lead to the
creation of credit chains
1
among some participants,
and thus some form of indirect reciprocity should be
1
Credit chains are created when, somehow, the re-
sources received by a peer are never reciprocated via direct
reciprocity, but may be returned indirectly (through another
peer), which yields a cyclic debt.
292
Falcão, E., Neto, A., Brasileiro, F. and Brito, A.
On the Impacts of Transitive Indirect Reciprocity on P2P Cloud Federations.
DOI: 10.5220/0007686402920299
In Proceedings of the 9th International Conference on Cloud Computing and Services Science (CLOSER 2019), pages 292-299
ISBN: 978-989-758-365-0
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

taken into consideration in such cases, even if the par-
ticipants cooperate repeatedly.
In order to deal with this particular source of prob-
lem some other works (cf. Section 3) conceived dif-
ferent forms of indirect reciprocity. In this work we
leverage the notion of transitive reciprocity, pre-
sented by Falc
˜
ao et al. (2016), suggested as com-
plement to direct reciprocity. Transitive reciprocity is
a more restricted type of indirect reciprocity that can
be used in tandem with direct reciprocity mechanisms
with the purpose of mitigating the problems (credit
chains) arising from availability or resource asymme-
try but keeping the advantages of direct reciprocity.
Simulation results (Falc
˜
ao et al., 2016) suggest
that the combination of transitive and direct reci-
procity increases the levels of cooperation among the
participants when compared to communities in which
only direct reciprocity is used. Yet, only scenarios
with simple workloads that cover a narrow spectrum
of the interesting cases were evaluated. The main re-
sults are that, when combined, transitive reciprocity
always enhance the performance of direct reciprocity.
However, the workloads experimented were too
simplistic and the results may not be representative
for real workload scenarios. This study extends such
investigation conducted by Falc
˜
ao (2016), still in sim-
ulation lane, through the assessment of the impact
of transitive reciprocity in P2P cloud federations, but
this time using representative workloads that are syn-
thesized from traces of real systems. In addition, we
also investigate the impacts of transitivity in credit
chains involving different numbers of peers.
Our main outcomes are the actual performance
improvements a cloud federation may experience
through transitive reciprocity, and also that in some
specific setups, the transitive reciprocity may degrade
the overall federation performance (in contrast to re-
sults presented earlier). In face of that, this work high-
lights the main care the member of a cloud federation
should take to setup its transitive mechanism properly,
to avoid performance degradation.
The rest of this paper is organized as follows. Next
section presents the existing reciprocity mechanisms,
detailing their main features and drawbacks, to em-
phasize in what they differ from transitive reciprocity.
In Section 3 we show the most relevant related work.
The transitive reciprocity is described in Section 4.
Section 5 details the reciprocity mechanism used in
our simulations, the Transitive FD-NoF. In Section 6
we present the simulation model and the description
of the evaluated scenario. The simulation results and
their corresponding analysis are presented in Section
7. Finally in Section 8 we put forward the main con-
clusions.
2 RECIPROCITY MECHANISMS
Reciprocity-based incentive mechanisms are strate-
gies that aid providers in prioritizing the most re-
ciprocal consumers for granting its resources. Obvi-
ously, this encourages cooperation because free rid-
ers (i.e., individuals that consume resources from the
community with no compensation) will hardly suc-
ceed when there is contention on resources. This de-
cision is made in accordance with the transactions his-
tory, which indicates the level of reciprocity of a given
peer. Such mechanisms are categorized as direct reci-
procity or indirect reciprocity.
Direct reciprocity takes place on interactions be-
tween two individuals – B helps A because A has
helped B before, or because B expects A to return
this favor in the future (Haddi and Bencha
¨
ıba, 2015).
On the other hand, indirect reciprocity takes place
on interactions involving at least three individuals,
and may happen via pay-it-forward (Floyd, 2017) or
reputation-based systems (Li and Su, 2018). Pay-it-
forward reciprocity is a so called altruistic strategy
that, in face of free riders, is quite utopic and unfea-
sible: A donates to B and B returns this favor to C,
which is a third party chosen randomly. Note that, in
this case, either A, B or C are not expecting something
in return. Reputation systems are often used in large-
scale P2P systems. In these systems, individuals are
encouraged to cooperate in order to render itself as a
collaborative and valuable member, and thus be recip-
rocated by its reputation. Therefore, if A helps B, C
will indirectly know that A is cooperative and reward
her for her good reputation. The direct reciprocity and
pay-it-forward reciprocity can take place via immedi-
ate or delayed exchange, whereas reputation systems
rely mainly on a delayed exchange since all the in-
formation about the reputation of the other peers is
collected in the past. Figure 1 illustrates a summary
of both types of reciprocity.
The main drawback of reputation systems is that
an individual will base their donation decisions on
third party information, which may be tampered with
by malicious peers to benefit themselves. If on the
one hand, the way this information is collected in rep-
utation systems can give room for peer collusion as
a disadvantage, on the other hand, the speed in which
these pieces of information are diffused by the partici-
pants of the system is its main advantage. This feature
enables newcomers to collect a reasonable amount of
information about the behavior of other participants
in a short period of time so that they can properly se-
lect whom they should cooperate with. In addition,
this speed in which the information is spread enables
the community members to swiftly discover the repu-
On the Impacts of Transitive Indirect Reciprocity on P2P Cloud Federations
293
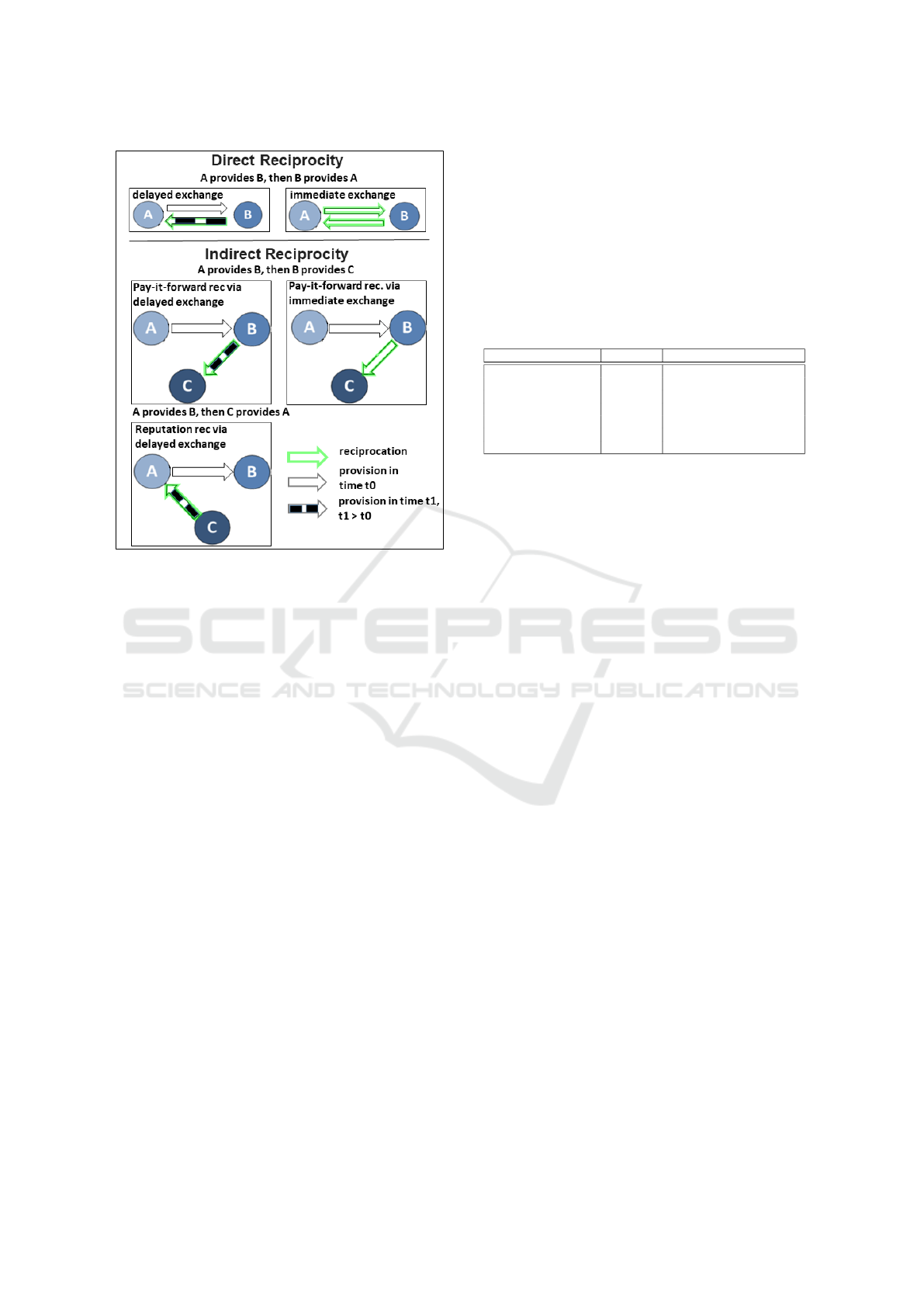
Figure 1: Types of reciprocity mechanisms.
tation of other peers they have never interacted with,
what may allow cooperation with unknown peers in
a less vulnerable way, as opposed to only interacting
with known peers as recommended by the direct reci-
procity. Therefore, it is possible to state that indirect
reciprocity is also suitable for communities with high
levels of resource asymmetry, and not only for com-
munities in which the participants have common in-
terests as required in direct reciprocity — if repeated
interaction is not necessary, common interests should
not be mandatory after all.
Two closely related problems common to both
reciprocity mechanisms are: i) how to treat newcom-
ers and ii) how to mitigate the advantages obtained by
whitewashers (individuals that leave and return to the
system with a new identity in order to dodge from the
consequences of a past in which they acted in a non-
cooperative way (Haddi and Bencha
¨
ıba, 2015)). If the
rules to join the system are too strict, the individuals
may feel discouraged to join the community, but if, in
contrast, these rules are too liberal, the participants
would be able to leave the system and appear as a
newcomer. Alternatives to this issue could be an entry
fee or a proof of work that newcomers should be sub-
mitted to be able to join the system (da Costa Cordeiro
et al., 2016). Another solution is to disregard negative
values for credit/reputation systems (Andrade et al.,
2007), thus making no sense for any peer to leave and
return to the system since this fact does not change
the way other participants value him.
In general, it is possible to state that the main
advantage of the indirect reciprocity is the quick
growth of the database containing information about
the behavior of other participants. On the other hand,
the main advantage of direct reciprocity is the in-
tegrity of this same information kept in database. Ta-
ble 1 presents the characteristics of both mechanisms
thus allowing a quick comparison between the main
features of each one.
Table 1: Characteristics of direct and indirect reciprocity.
Characteristic Direct Rec. Indirect Rec.
database growth slow fast
database integrity guaranteed not guaranteed
supply and demand symmetrical symmetrical and asymmetrical
frequency of interactions repeated repeated and occasional
bootstrapping speed slow fast
collusion impossible possible
identity changing possible possible
2.1 The Asymmetry Problem
Direct reciprocity presents the following two restric-
tions when put into practice individually: time and
resources asymmetry. In order to better understand
this issue, one must picture a federation consisting of
3 peers (A, B and C) with a conflict of interest, as fol-
lows: A has a high processing capacity but insufficient
storage, B has enough storage but often needs an extra
bandwidth, and C has bandwidth but often needs more
processing capacity. This cooperation setup, concern-
ing the types of resource required and offered, leads
to the following situation: A always provides to C,
B always provides to A, and C always provides to B.
In such cases, no resource is directly returned to the
providers, and even though all participants involved
in this cooperation chain receive what they request,
some of them may be seen as free riders.
For explanation purposes, one must consider that
peers A, B and C cooperate through a direct reci-
procity mechanism in which the balance of B from the
perspective of A would be computed by the function
γ(A, B,t) = υ(B, A, t)− υ(A, B, t),
where υ(A, B, t) denotes the total amount of resources
A provided to B until time t. Figure 2 depicts the
interactions via immediate exchange between three
peers with conflicts of interest (the case described on
the previous paragraph), and their corresponding bal-
ances. It is assumed that γ(A, B, t
0
) = γ(B,C,t
0
) =
γ(C, A, t
0
) = 0, t
0
< t
1
< t
2
, and that each peer receives
and provides 10 units of resource per time unit.
As shown in Figure 2, as the individuals interact
with one another the balances decrease to negative
values, what naturally brings distrust. In such cases, it
is extremely hard to distinguish between cooperators
CLOSER 2019 - 9th International Conference on Cloud Computing and Services Science
294
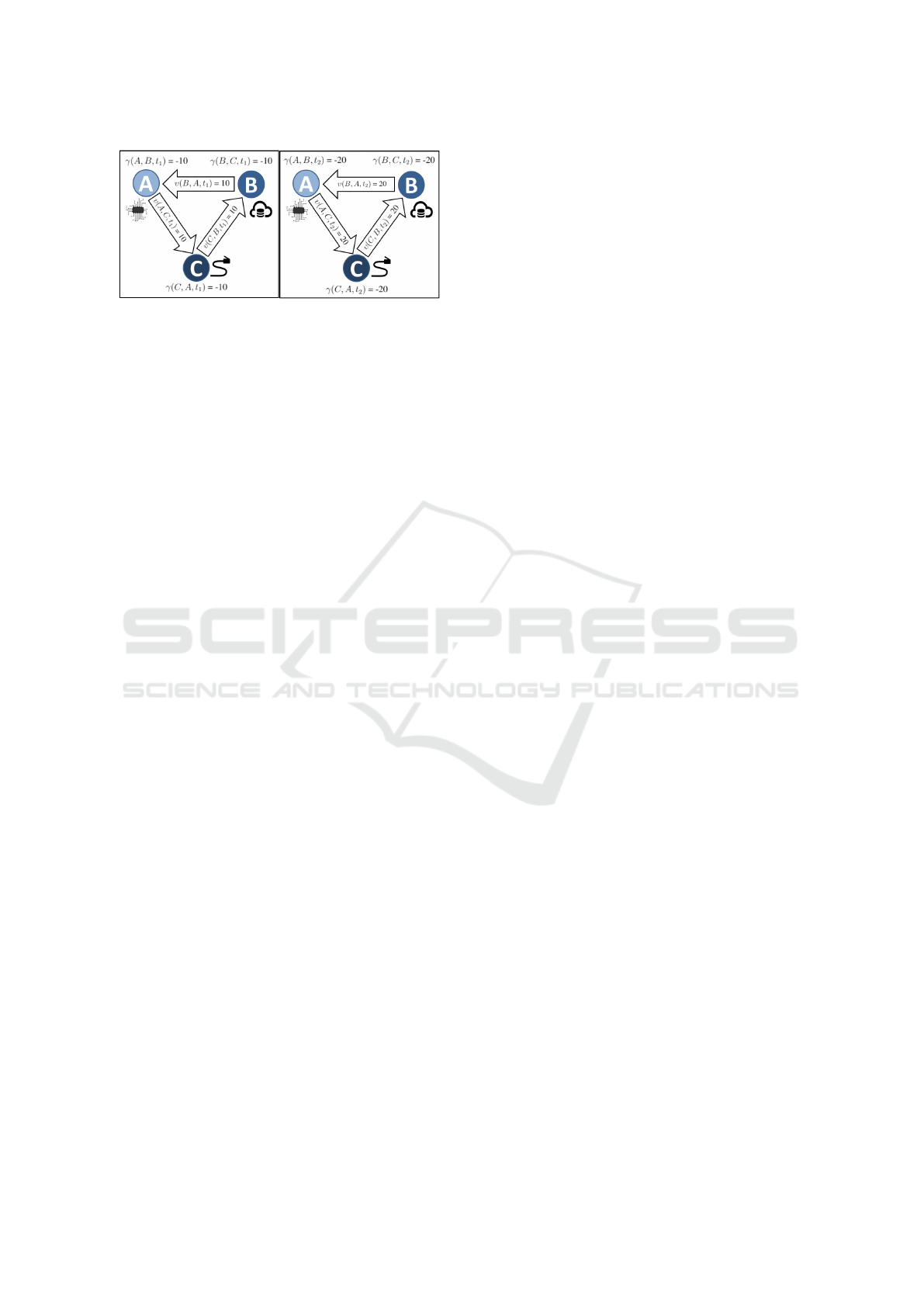
Figure 2: The interests asymmetry problem.
and free riders, since both will have a negative bal-
ance for returning no favors, either intentionally (free
riders) or unintentionally (asymmetry).
Next section depicts how some related work ad-
dress this issue.
3 RELATED WORK
The main indirect reciprocity mechanisms typically
use reputation systems, transitive credit systems, or
the pay-it-forward principle.
Regarding the cryptography technique, there ex-
ists Dandelion (Sirivianos et al., 2009) and T-Chain
(Shin et al., 2017), based respectively on a global
credit system with tit-for-tat and on pay-it-forward,
both thought for file sharing systems. The cryptog-
raphy applied on Dandelion and T-Chain is efficient
in promoting cooperation even in the face of free rid-
ers. However, this idea is only feasible for file sharing
systems, since files are encryptable.
Apart from the cryptography strategy, which
clearly is not applicable to cloud federations, we may
also cite, still in the context of file sharing, the Clus-
ter Based Incentive Mechanism (CBIM) (Zhang and
Antonopoulos, 2013), the K-Cycle (Eidenbenz et al.,
2012) and Menasch
´
e et. al. (2010). CBIM and K-
Cycle organize peers with asymmetric resources in
what the authors call barter rings or barter cycles,
forcing the peers comprising the ring to cooperate be-
fore consuming. Menasch
´
e et. al. (2010) suggest that
cycles of indirect reciprocity cooperation should be
converted into direct reciprocity.
When it comes to mechanisms that could be
straightforwardly applied to P2P cloud federations
and computational grids, but without relying indis-
criminately on third-parties (such as the transitive
reciprocity we rely on), there are the following rel-
evant work: CompactPSH (Bocek et al., 2009),
PledgeRoute (Landa et al., 2009) and Scrivener
(Nandi et al., 2005). In these mechanisms, in-
direct reciprocity is broken down into two steps:
credit transfer and direct reciprocity. The idea is to
strengthen the economy of the system since the trans-
fer of credits allows interactions that would not hap-
pen between peers with asymmetric resources.
4 TRANSITIVE RECIPROCITY
Transitive reciprocity is a more limited form of in-
direct reciprocity, which is designed to be put into
practice in tandem with direct reciprocity but while
still keeping the integrity of database with transac-
tions history (which is not the case for reputation sys-
tems). For instance, when A requests resources from
B, and somehow the latter can not meet A’s request, B
can ask other peers that are in debt with him (e.g., C)
to do A this favor as a kind of repayment to B. Further,
once A receives the resources, she must be informed
by C that that favor was done under B’s request. Also,
A will increase the balance of B in proportion to the
time period and amount of resources provided by C,
but obviously A will not credit C and C will not debt
A.
With the aid of transitive reciprocity, the distrust
raised by the asymmetry problem (Fig. 2) would
be solved. The decrease of balances that took place
on each time period due to the cooperation chain
(A → C → B → A) would give place, in face of transi-
tive reciprocity, to a balance stability. At the end of t
1
,
γ(A, B, t
1
) = γ(B,C, t
1
) = γ(C, A,t
1
) = 0, as well as at
the end of t
2
, γ(A, B, t
2
) = γ(B,C,t
2
) = γ(C, A, t
2
) = 0,
instead of −10 and −20 for t
1
and t
2
respectively,
since for each time period the resource provision
would be indirectly reciprocated and all the debts
would be paid.
From the related work we may note that the
main differences are the protocol to enable cooper-
ation among peers with asymmetry, and the appli-
cation context, which may require special treatment.
The change of the protocol may not entail significant
changes in the results of the performed simulations,
since the protocols are only enablers of the same in-
teraction through different approaches/idea of indirect
reciprocity. However, transitive reciprocity is more
efficient in terms of amount of exchanged message –
to allow interaction through transitive reciprocity be-
tween three peers, its protocol only needs 5 messages,
while Scrivener and CompactPSH needs respectively
6 and 10 messages (cf. (Nandi et al., 2005; Bocek
et al., 2009)).
On the Impacts of Transitive Indirect Reciprocity on P2P Cloud Federations
295

5 THE TRANSITIVE FD-NoF
In the Fairness-Driven Network of Favors (or FD-
NoF, for short), the most reciprocal participants are
prioritized for the concession of favors through a sys-
tem of balances that, considering functions defined in
Section 2.1, are calculated by the following equation:
γ(A, B, t) = max
{
0, υ(B, A, t) − υ(A, B, t) + log υ(B, A, t)
}
.
By preventing the balances from being negative, this
definition does not allow malicious peers to manipu-
late their balances by changing their identity to pre-
tend to be a newcomer. Furthermore, it takes into
consideration an amortized and historical portion of
donations that A has received from B in the past. This
enables A to distinguish a peer C that has never pro-
vided resources from a cooperative peer B that has
provided to A in the past but has received from A at
least the same amount of resources provided.
In order to assure fairness, the ratio between
the total amount of resources received and the to-
tal amount of resources provided up to a particular
point in time, the FD-NoF suggests that each par-
ticipant should manage the amount of resources of-
fered to other peers of the federation. Each partici-
pant is provided with a feedback control loop mech-
anism and must define a minimum (τ
min
) and max-
imum threshold (τ
max
), thus determining an interval
[τ
min
, τ
max
] that represents the desired levels of fair-
ness. One must assume that the amount of resources
that A offers to any other peer B in time t is expressed
by the function α(A, B, t). If at any moment the fair-
ness of A in relation to a peer B is lower than τ
min
,
the controller will continuously subtract a fixed value
∆ from α(A, B,t) over the subsequent periods of time
until the fairness of B under the perspective of A gets
higher than τ
min
. On the other hand, if the fairness
of A in relation to B is superior to τ
max
, the controller
will add ∆ to the value of α(A, B,t) over the subse-
quent periods of time until the fairness of A in relation
to B assumes an inferior value to τ
max
— at this stage,
once the desired level of fairness is reached, A will try
to have an accumulated balance in the perspective of
this participant. Finally, when the fairness of A in re-
lation to B is within the interval [τ
min
, τ
max
], the con-
troller will run a Hill Climbing algorithm that uses
the latest values of fairness to decide whether there
should be an increase or decrease in α(A, B,t + 1) to
maximize the fairness of B perceived by A within the
interval [τ
min
, τ
max
].
This brief discussion aims to make this work self-
contained with respect to the the FD-NoF mechanism.
Additional information about the algorithm and its
performance can be found in (Falc
˜
ao et al., 2016).
The goal of transitive reciprocity is to enable co-
operation between participants that show any type
of asymmetry. Therefore, whenever a peer has idle
resources and the FD-NoF mechanism suggests this
peer should not share them, the transitive reciprocity
must be put into practice to verify if there is any credit
chain between the requester and the provider, what
could enable cooperation through transitivity. Each
peer is free to setup its own mechanism autonomously
by choosing the maximum allowed length of chain
(χ ∈ N
≥3
) and also the percentage of peers consid-
ered for trying cooperation at each level of the chain,
η ∈ [0, 1]. Obviously, the higher are χ and η the higher
will be the probability of cooperation, but also more
congested will be the federation network.
The FD-NoF mechanism with this additional en-
abler is what we call the Transitive FD-NoF.
6 EVALUATION OF THE
TRANSITIVE FD-NoF
In order to assess the performance of the Transitive
FD-NoF in P2P cloud federations, we advanced the
simulator built by Falc
˜
ao et. al. (2016) to allow the
experimentation of realistic workloads, and also to en-
able cooperation in transitive chains with more than
three peers. The simulation model with these addi-
tional features is described next.
6.1 Simulation Model
The federation F consists of a community comprised
by N peers. The simulation proceeds in discrete steps
and, therefore, the balance (γ : F × F × N → R
≥0
) and
quota (α : F × F × N → R
≥0
) functions are best de-
scribed in the form of step functions.
Assume that each peer has a total resource capac-
ity of C ∈ R
≥0
. A peer in consumer state at any step
t will have a total resource demand D
total
= D + C ,
of which C units are provided by the local resources
and D units are requested to the federation. A peer is
in provider state when D
total
< C , which means that
it can provide up to C resource units to the federation.
For two-party interactions, a peer A in a provider state
at time step t may provide up to α(A, B,t) units of re-
sources to any peer B in consumer state at step t.
When cooperating through transitive reciprocity
and the number of peers involved in the credit chain
is three (χ = 3), the amount of resources provided is
computed as follows. A peer C in a provider state at
step t may provide to a peer A in a consumer state
on behalf of a peer B up to the minimum between
α(C, B, t) (the amount that C would provide directly
to B) and α(B, A, t) (the amount that B would provide
CLOSER 2019 - 9th International Conference on Cloud Computing and Services Science
296

to A, since B would not require C to provide more re-
sources to A than B itself would provide). The same
logic is applied for χ > 3. Roughly, this means that
the peers involved in the transitive reciprocity never
donate more than the limit imposed by the controller.
Whenever a peer is in a consumer state, first she
will send requests to participants she knows she has
credit with, in a direct reciprocity basis. If none of
them can meet her request, then she will send requests
to peers that could meet requests via transitive reci-
procity, with the aid of any credit chain. Let us call
these intermediate individuals the transitive peers.
Then, each transitive peer, which will denote one level
of the chain, should forward this request only to a por-
tion (η) of the participants of the federation. Finally,
if none of these requests are met, the consumer sends
direct requests to unknown peers, randomly chosen,
for establishing new links. At each time step, upon
receiving the requests from consumer peers, the sim-
ulator randomly selects a peer in a provider state,
and this peer prioritizes the granting of resources to
consumer peers according to the protocol established
by the NoF — peers with higher balances are prior-
itized, and if there is more than one requester with
the same balance, the provider distributes its idle re-
sources equanimously among them.
In simulations in which χ > 3, the consumer will
always try to find the credit chain with lowest length
possible to the provider. In other words, if for instance
χ = 5, the consumer will first try to find a provider
through a chain with a single level (χ = 3), and in case
it is not possible, she will increment χ until she finds a
chain to a provider. This process is repeated until her
demand has been fully met or until the requester has
explored chains of length χ = 5 and no credit chain
has been found.
The source code of the Transi-
tive FD-NoF simulator is available at
https://github.com/antonionetto20/Transitive-FD-
NoF.git.
6.2 Workload Synthesized from Real
Traces
In terms of client applications, cloud federations may
have similar applicability to that of P2P opportunis-
tic computational grids, suitable for fault tolerant ap-
plications such as Bag-of-Tasks (BoT). Therefore, we
used a workload generator presented by Carvalho and
Brasileiro (2012), a software that uses traces from real
systems, provided by the Grid Workload Archive at
http://gwa.ewi.tudelft.nl/, in order to synthesize real-
istic workloads based on parameters such as number
of peers, users, maximum duration of a job and dura-
tion of the whole workload.
With the aid of this software, we generated a
workload of 72 hours, comprising a federation of 60
organizations (peers) and 10 users per organization.
Since the simulator models the exchange of re-
sources in discrete turns, it was necessary to map the
jobs generated by the workload to the turns of the sim-
ulation. This was done considering time grains, i.e.,
mapping all jobs that start and/or finish in a given time
slot for one turn of the simulation. In our simulations,
to approximate the duration of a turn to the jobs run-
ning time, the grain was defined as the average of the
total duration of all jobs: 942 seconds. The factors
are the reciprocity mechanism (direct or transitive),
the total resource capacity of each peer (C ) and, if
the transitivity is enabled, the maximum length of the
credit chain (χ) and the percentage of peers consid-
ered at each level of the chain (η) – recall that the
peers’ demands comes from the workload generator.
We varied the resource capacity of the peers to under-
stand the impact of the transitivity in scenarios with
different levels of resource contention. In addition,
we also changed χ and η to analyze the trade-off be-
tween the cost of increasing the number of peers in-
volved in the transitive cooperation (which would in-
crease the amount of messages sent, possibly congest-
ing the network) and its benefits (which would be the
increase in the amount of shared resources thanks to
the number of transitive peers).
Once the difference in performance between the
FD-NoF and the Transitive FD-NoF in a turn tends
to be marginal, the evaluation metric is computed by
the total amount of resources donated in the Transitive
FD-NoF minus the total amount of resources donated
in the FD-NoF, in all turns of the simulation. With this
value we can measure the percentage of increase in
donation brought by the transitive reciprocity.
In all simulations, the FD-NoF mechanism is set
with ∆ = 0.05 · C , τ
min
= 0.75 and τ
max
= 0.95, values
suggested by Falc
˜
ao et. al. (2016) for performing
well in wide range of scenarios.
7 RESULTS AND DISCUSSION
Figure 3 presents the percentage of increase in to-
tal donation when comparing the same scenarios ran
with Transitive FD-NoF and the FD-NoF. We simu-
lated scenarios in which all the peers are set only with
C = 50 and scenarios in which they are all set with
C = 100. In addition, we also changed the maximum
chain length when the transitive reciprocity is enabled
between χ ∈ {3, 4, 5}. We first explore transitivity to
its edge — the percentage of peers tried on each chain
On the Impacts of Transitive Indirect Reciprocity on P2P Cloud Federations
297
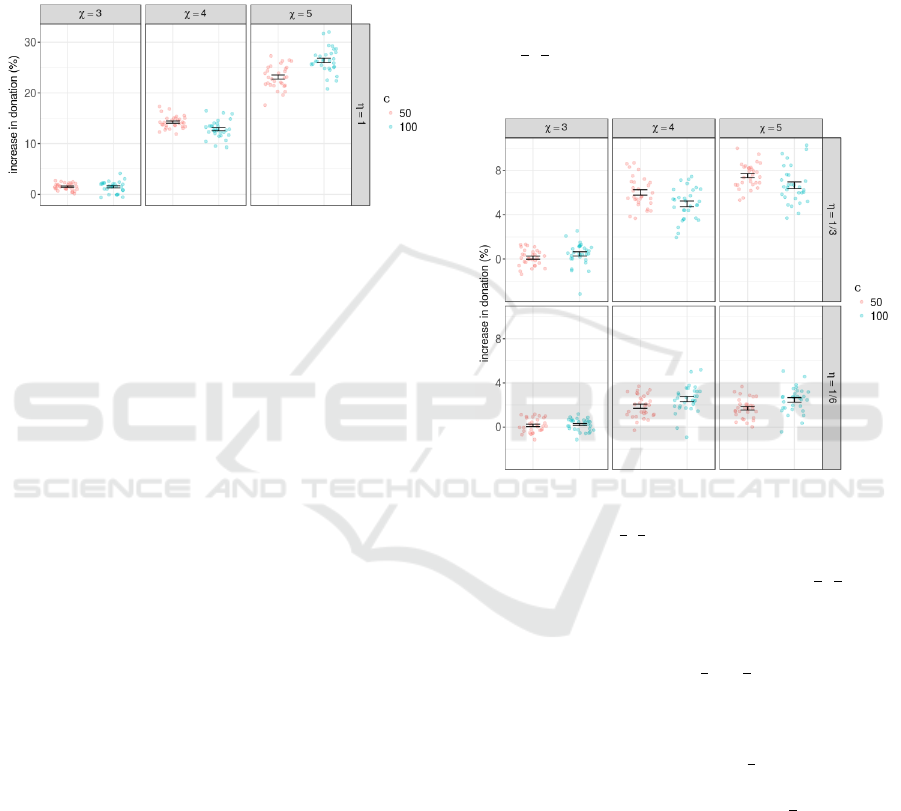
level is 100% (η = 1). Each box-plot presents the dis-
tribution of the percentage of increase in donation
in 30 replications, where the seed for generating ran-
dom numbers is modified, which affects the order in
which providers and consumers are selected by the
simulator for the provision of resources. The confi-
dence intervals for these distributions are plot with a
95% confidence level.
Figure 3: Distribution and confidence intervals of percent-
age increase in resource donation provided by transitivity in
scenarios with χ ∈ {3, 4, 5}, C ∈ {50, 100} and η = 1.
From Figure 3 one may observe that the transi-
tive reciprocity increased the percentage of donation
in vast majority of the scenarios simulated with η = 1,
specifically, 97.2%. The remaining scenarios, config-
ured with C = 100 and χ = 3, showed performance
degradation as can be seen on Figure 3 (a few blue
points below zero). This fact was not perceived before
in (Falc
˜
ao et al., 2016), perhaps because it was used
a very simple workload that didn’t generate coopera-
tion scenarios with higher complexity. This degrada-
tion may be experienced when specific interactions,
that occur at a given moment, depend on the oc-
currence of previous interactions, since the existence
(or not) of a past interaction that happened through
the presence (or absence) of the transitive reciprocity
may alter the disposition of balances and quotas be-
tween the peers, in such a way that prevents certain
donations. However, when the length of the transi-
tive chain (χ) is increased, augmenting the chances
of transitive cooperation, there is a considerable in-
crease in the amount of resources shared. For sce-
narios in which the peers have C = 100, the aver-
age increase in donation was 12.83% and 26.38% for
χ ∈ {4, 5}. Finally, we observed that the increase in
donation brought by the transitive reciprocity in sce-
narios with different resource contention (different C )
may differ significantly for χ ∈ {4, 5}, although with
no clear pattern since for χ = 4, C = 100 underper-
formed scenarios with C = 50 but for χ = 5, C = 100
overperformed C = 50.
However, exploiting all possibilities of transitive
chains between the provider and the consumer may
not be realistic depending on N , χ, and η. Scenarios
with N = 60, χ = 5 and η = 1 allow a number of com-
binations up to 59+ (59· 58)+ (59· 58· 57) = 198530
between a single provider and all the other partici-
pants. Considering all the providers at a given time,
the amount of messages sent would surely congestion
the network, besides the delay on decision of each in-
termediate peer on whether it should cooperate or not.
For this reason, we also evaluated scenarios in
which the transitive reciprocity considered a reduced
amount of participants at each level of the chain,
η ∈ {
1
6
,
1
3
}. The increase in donation of such simu-
lations are presented in the box-plots of the Figure 4.
Figure 4: Percentage increase in resource donation provided
by transitive reciprocity in scenarios with χ ∈ {3, 4, 5}, C ∈
{50, 100} and η ∈ {
1
6
,
1
3
}.
In scenarios setup with χ = 3 and η ∈ {
1
6
,
1
3
} there
were some scenarios with performance degradation
due to the low value of η. Further, we may also
note that when χ = 3, there is no meaningful differ-
ence on increasing η from
1
6
to
1
3
. However, when
χ ∈ {4, 5} the amount of peers considered for coop-
eration increases substantially, and then increasing η
incurred in a higher level of resource provision. Sce-
narios set with χ ∈ {4, 5} and η =
1
3
, for instance, had
solely performance improvements, 6.02% and 7.53%,
on average. Therefore, χ = 4 and η =
1
3
can be con-
sidered and interesting setup for presenting a good
cost-benefit, at least for the workload experimented,
since to explore all cooperation possibilities a con-
sumer would only need to send 420 messages.
CLOSER 2019 - 9th International Conference on Cloud Computing and Services Science
298

8 CONCLUSIONS
This work evaluates the impact of transitive reci-
procity in P2P cloud federations with workload syn-
thesized from traces of real systems. To this goal,
a simplified simulation model was conceived to al-
low the investigation of the performance of transitive
reciprocity in different scenarios. To the best of our
knowledge, only the present work evaluates the im-
pacts of the chain length and the amount of peers con-
sidered for cooperation on each level of the chain.
Simulation results showed that in some scenarios
(2.8%) in which all interactions are tried (η = 1) tran-
sitive reciprocity may degrade the federation overall
performance – the amount of shared resources is de-
creased, a result not seen in any related work. How-
ever, our main findings are that transitive reciprocity
can actually increase the sharing level in a more re-
alistic scenario in which less transitive combinations
between consumer and provider are considered —
Transitive FD-NoF increased the percentage donation
in 6.02% and 7.53% in scenarios setup with η =
1
3
and χ ∈ {4, 5}, respectively.
ACKNOWLEDGMENT
This research was partially funded by the EU-BRA
SecureCloud project (EC, MCTIC/RNP, and SERI,
3rd Coordinated Call, H2020 Grant agreement no.
690111) and by the EU-BRA ATMOSPHERE project
(EC and MCTIC/RNP, 4th Coordinated Call, H2020
Grant agreement no. 777154).
REFERENCES
Andrade, N., Brasileiro, F., Cirne, W., and Mowbray, M.
(2007). Automatic grid assembly by promoting col-
laboration in peer-to-peer grids. Journal of Parallel
and Distributed Computing, 67(8):957 – 966.
Bocek, T., Hecht, F. V., Hausheer, D., Stiller, B., and El-
khatib, Y. (2009). Compactpsh: An efficient transi-
tive tft incentive scheme for peer-to-peer networks. In
2009 IEEE 34th Conf. on Local Computer Networks,
pages 483–490.
Carvalho, M. and Brasileiro, F. (2012). A user-based model
of grid computing workloads. In 2012 ACM/IEEE
13th International Conference on Grid Computing,
pages 40–48.
Chuang, J. (2004). Designing incentive mechanisms for
peer-to-peer systems. In 1st IEEE International Work-
shop on Grid Economics and Business Models, 2004.
GECON 2004., pages 67–81.
Ciccarelli, G. and Cigno, R. L. (2011). Collusion in peer-
to-peer systems. Computer Networks, 55(15):3517 –
3532.
da Costa Cordeiro, W. L., Santos, F. R., Barcellos, M. P.,
Gaspary, L. P., Kavalionak, H., Guerrieri, A., and
Montresor, A. (2016). Making puzzles green and use-
ful for adaptive identity management in large-scale
distributed systems. Computer Networks, 95:97 – 114.
Dhuria, S., Gupta, A., and Singla, R. (2017). Resource
pricing in cloud federation: A review. International
Journal of Innovations & Advancement in Computer
Science, 6(12).
Eidenbenz, R., Locher, T., Schmid, S., and Wattenhofer,
R. (2012). Boosting market liquidity of peer-to-peer
systems through cyclic trading. In 2012 IEEE 12th
International Conference on Peer-to-Peer Computing
(P2P), pages 155–166.
Falc
˜
ao, E. L., Brasileiro, F., Brito, A., and Vivas, J. L.
(2016). Enhancing p2p cooperation through transitive
indirect reciprocity. In 2016 IEEE 36th International
Conference on Distributed Computing Systems.
Falc
˜
ao, E., Brasileiro, F., Brito, A., and Vivas, J. (2016). En-
hancing fairness in p2p cloud federations. Computers
& Electrical Engineering, 56:884 – 897.
Feldman, M., Lai, K., Stoica, I., and Chuang, J. (2004). Ro-
bust incentive techniques for peer-to-peer networks.
In Proc. of the 5th ACM Conf. on Electronic Com-
merce, pages 102–111, New York, NY, USA. ACM.
Floyd, R. E. (2017). Pay it forward. IEEE Potentials,
36(2):5–47.
Haddi, F. L. and Bencha
¨
ıba, M. (2015). A survey of in-
centive mechanisms in static and mobile {P2P} sys-
tems. Journal of Network and Computer Applications,
58:108 – 118.
Landa, R., Griffin, D., Clegg, R. G., Mykoniati, E., and Rio,
M. (2009). A sybilproof indirect reciprocity mecha-
nism for peer-to-peer networks. In INFOCOM 2009,
IEEE, pages 343–351.
Li, S. and Su, W. (2018). The research of reputation incen-
tive mechanism of p2p network file sharing system.
International Journal of Information and Computer
Security, 10(2-3):149–169.
Menasch
´
e, D. S., Massouli
´
e, L., and Towsley, D. (2010).
Reciprocity and barter in peer-to-peer systems. In
Proc. of the 29th Conf. on Information Communica-
tions, pages 1505–1513, NJ, USA. IEEE Press.
Nandi, A., Ngan, T.-W., Singh, A., Druschel, P., and Wal-
lach, D. S. (2005). Scrivener: Providing incentives
in cooperative content distribution systems. In Mid-
dleware, volume 3790 of Lecture Notes in Computer
Science, pages 270–291. Springer.
Shin, K., Joe-Wong, C., Ha, S., Yi, Y., Rhee, I., and Reeves,
D. S. (2017). T-chain: A general incentive scheme for
cooperative computing. IEEE/ACM Transactions on
Networking, 25(4):2122–2137.
Sirivianos, M., Yang, X., and Jarecki, S. (2009). Robust
and efficient incentives for cooperative content distri-
bution. IEEE/ACM Trans. Netw., 17(6):1766–1779.
Zhang, K. and Antonopoulos, N. (2013). A novel bartering
exchange ring based incentive mechanism for peer-to-
peer systems. Future Generation Computer Systems,
29(1):361 – 369.
On the Impacts of Transitive Indirect Reciprocity on P2P Cloud Federations
299
