
NFC vs QR Code: A Comparison in Flight Boarding Transaction
Mikhael Bagus Renardi
1
, Noor Cholis Basjaruddin
2*
, Supriyadi
2
, Saufik Ramadhan
2
and Umar
Zaenal Abidin
2
, Kuspriyanto
1
1
School of Electrical Engineering and Informatics - Bandung Institute of Technology, Bandung, Indonesia
2
Department of Electrical Engineering – Bandung State Polytechnic, Bandung, Indonesia
kuspriyanto@yahoo.com
Keywords: QR Code on Boarding, NFC on Boarding, Boarding Transaction, Mobile Transaction
Abstract: The development of smartphone technology has led to a more convenient and faster digital transactions.
One of the transactions that has been affected by the change of business process is the boarding transaction
in airports. The conventional boarding process requires a printed boarding pass and an identity card. The use
of smartphones enables the data to be stored digitally, supporting paperless transactions. Both boarding pass
and identity card can only be used by the right holder. Hence, passengers need to take care of their boarding
pass, so that it can only be used once. Types of technology often utilised for transactions are Near Field
Communication (NFC) and QR Code. However, these tools may be vulnerable to security gaps. For
example, the data might be transferable easily using the screenshot feature in digital smartphones. The
advantage of using NFC technology is that the data can be encrypted and sent using peer-to-peer
networking, therefore, the data cannot be read without a set of encryption methods. This study concluded
that NFC technology had an advantage of security compared to QR Code. Further research may investigate
the application of biometric data as a security enhancement in digital transactions.
1 INTRODUCTION
The advancement of digital technology has
prompted the development of more efficient
transaction methods. One of the transaction methods
has been implemented in airports. Airports have a
high level of transactions, thus, time efficiency is
very essential. One of the methods which can be
applied is by using a faster transaction which can
reduce the interaction between airport staff and
passengers. Some of the common methods which
have been utilised include Quick Response Code
(QR code) (Lee, 2014) and Near Field
Communication (NFC) (Suparta, 2012). More
recently, QR code and NFC have been applied in
various transactions such as, electronic-ticketing (e-
ticketing) (Kolte, 2017), point of sale (Husni, 2012),
and fast access in posters (NFC smart posters).
These methods have also been implemented in
airport transactions, e.g. the boarding process.
Boarding process encompasses the verification
process, hence, all the data used in transactions
should be secured and the ownership of the data
should be guaranteed. The data used in the boarding
process include passengers’ identity and flight data.
One of possible issues is that how to ensure that
tickets can only be used by passengers whose names
are stated on e-tickets (Ceipidor, 2013). Another
issue is that the durability of the data and the media,
and the accuracy of the data also need to be ensured.
QR Code and NFC have different characteristics
of interactions, thus, these methods also have
different security gaps. This research aimed to
compare the application of QR Code and NFC in the
boarding transaction in airports (Sunday, 2016). The
comparison was made in terms of the advantages,
the security gaps, and the limitations of their
implementation in the boarding.
2 RESEARCH METHOD
In general, NFC and QR Code have certain
similarities in their application. Both are utilised to
ease data transmission to recipients. One of the
significant differences is that while QR Code
enables the transmitted data to be seen, but the data
cannot be read without decryption; NFC does not
allow the data to be read, but the data are stored in
Renardi, M., Basjaruddin, N., Supriyadi, ., Ramadhan, S., Abidin, U. and Kuspriyanto, .
NFC vs QR Code: A Comparison in Flight Boarding Transaction.
DOI: 10.5220/0009009502590266
In Proceedings of the 7th Engineering International Conference on Education, Concept and Application on Green Technology (EIC 2018), pages 259-266
ISBN: 978-989-758-411-4
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
259
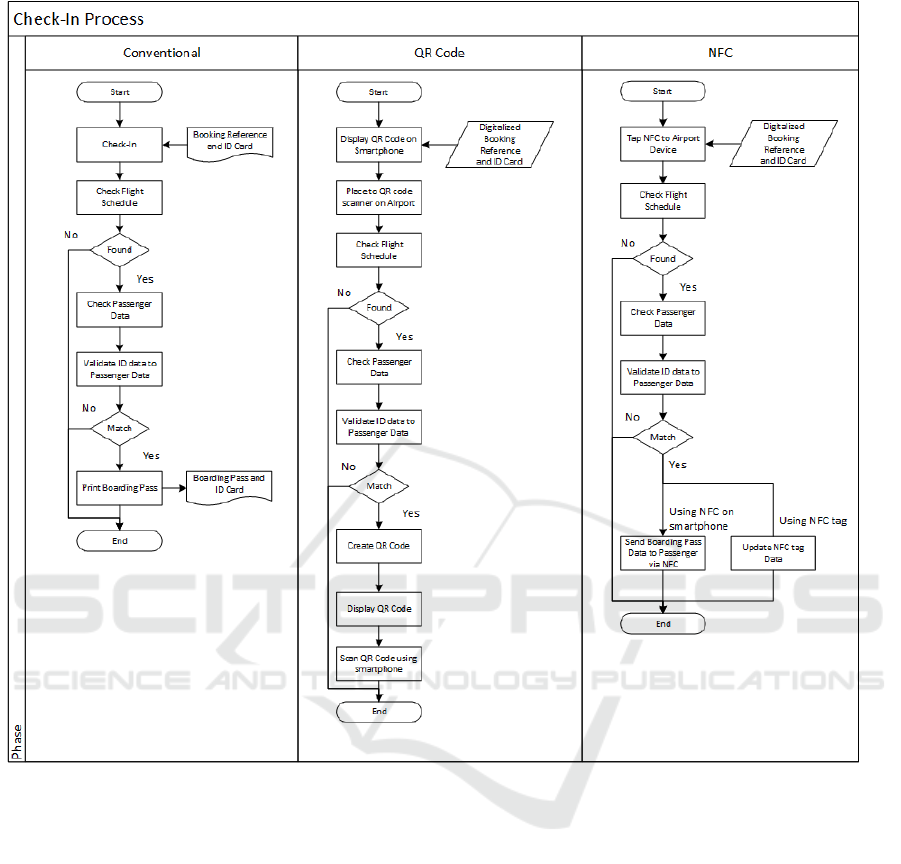
Figure 1. Flowchart proses Check-In.
plain text. The data stored or sent using QR code
(Coleman, 2011) and NFC can be in the form of
plain text , URL, telephone numbers, map
coordinates, etc (Renardi, 2017). this research
focused on how the implementation of both
technologies could overcome the security gaps in the
boarding process in airports. This study also focused
on offline transactions.
Some research has investigated the use of QR
Code in the educational sector including checking
the validity of study reports (Rochman, 2017) and
sharing links for learning materials (Durak, 2016). In
the sales sector, studies have examined the use of
QR Code as a marketing tool (Asare, 2015) and
mobile marketing (Cata, 2013). Other research has
also touched upon the payment sector (Putra, 2018)
such as, point of sales, medical records
(Basjaruddin, 2017), toll payment (Kumar, 2017),
and baggage claim in airports (Renardi, 2017). The
application of QR Code and NFC in airports can also
encourage paperless transactions and enhance data
management in smartphones (Zupanovic, 2014).
2.1 E-Ticketing
E-tickets are utilised to shorten the transaction
process and to ease the data management (Sunday,
2016). E-tickets can store information as in printed
tickets. It can also be accessed through the internet
and be stored digitally in emails or smartphones.
During the check-in, the validity of passengers’
identity is checked and their tickers are printed out.
However, by using e-tickets, passengers are not
required to print out their tickets. They only need to
EIC 2018 - The 7th Engineering International Conference (EIC), Engineering International Conference on Education, Concept and
Application on Green Technology
260
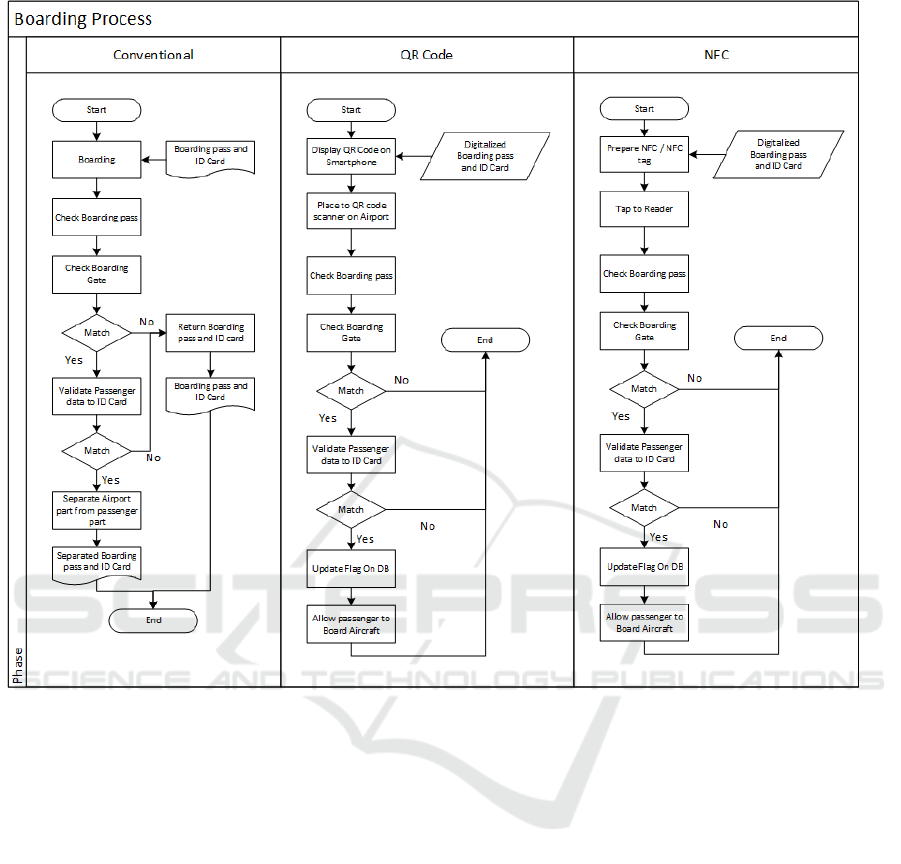
Figure 2. Flowchart proses Boarding.
show their e-tickets to the airport staff, so that the
staff can check the originality of the data. The
identity data can be stored digitally, thus, these can
be used to validate passengers’ identity (Coca,
2013).
One of the possible issues is that how to ensure
the originality of e-tickets. Automatic validation
using systems could be the solution for this problem.
QR Code (Maheswar, 2018) and NFC (Zupanofic)
are some of the transaction methods to ease the
exchange of e-tickets (Qteishat, 2014). Using these
technologies facilitates a faster input process to the
validation system and alter the interaction pattern
(between airport staff and passengers to between
systems and passengers) (Renardi, 2017).
The use of QR Code allows passengers to open
the data regarding booking reference and identity
cards. These data are shown in QR Code (Figure 1).
Passengers need to scan QR Code on the scanner.
The machine then decrypts and check the validity of
the data. The result of check-in can be given to
passengers in a form of QR Code and passengers can
scan the code to save the data. Meanwhile, the use of
NFC enables passengers to send the data using card
emulation mode or peer to peer (Figure 1). The
result of the check-in process can be given to
passengers using the peer to peer mode or
writer/reader in the NFC tag.
The boarding pass obtained during check-in is
used as a required document to enter the restricted
area of an airport and to board the airplane (Figure
2). In the conventional boarding process, the
boarding pass is printed out and given to the airport
staff, and the staff will check the accuracy of the
schedule and the departure gate. If it is correct, the
boarding pass will be torn into two parts; one part is
given to passengers and the other one is kept by the
staff. Boarding is usually done as fast as possible
although the validation process is still executed. The
use of QR Code and NFC may facilitate a faster
boarding process and a paperless transaction (Evizal,
2013).
NFC vs QR Code: A Comparison in Flight Boarding Transaction
261

2.2 Quick Response Code
QR Code is a type of matrix barcode in a two-
dimensional shape formed by an encrypted text
(Figure 3) (Asare, 2015). QR Code requires a
camera as a scanner to read, while the code can be
generated from smartphones and shown in the
screen. The making and reading process of QR Code
involved digital image processing, and it can be
stored in form of texts or pictures. QR Code can be
used in two media, that is, printed media such as,
newspapers, posters, printed tickets, and magazines
and digital media which can use websites and be
shown ion computers or smartphones (Coleman,
2011). QR Code does not require specialised media
to show the data (the QR Code) because the
important thing is that how the code can be seen and
read.
Figure 3: Example of QR Code.
QR Code is read by the party that requires that
particular information. For example, if a user wants
to make a payment using mobile phones, he/she is
required to scan QR Code owned by a point of sales.
Also, if a user wants to know some information
about certain products in a magazine, he/she needs
to scan QR Code. In airport context, it is the airport
staff who needs information, thus, they need to scan
the code.
2.2.1 Benefits of Using QR Code
The application of QR Code in the boarding process
offers some advantages. For instance, smartphones
have camera features and adequate screen quality,
thus, QR Code can be implemented more easily and
it is also cost-effective compared to NFC (Wu,
2013). Moreover, the use of QR Code does not
require any specialised media, so it can be used with
any media. QR Code is also not limited by distance.
In other words, as long as the code can be seen
clearly, it can be read. In addition, some users can
also access and use the same QR Code, but a user
can only access the code in a particular point of
time.
Another merit of using QR Code is that standard
printers and paper can be utilised to print out the
code (Sunday, 2016). However, if it is digitally used,
it does not have to be printed out. Also, the input
process does not require a keyboard. Moreover, QR
Code can store big data such as, NFC and RFID, and
it has error correction and high detection capacities.
Thus, if it is broken, it can still be read. Encryption
and digital signature can also be applied in QR
Code. Last but not least, QR Code can be used for
authentication processes such as, website login, Wi-
Fi network login, and messenger login (WhatsApp
and Line messenger).
2.2.2 QR Code Vulnerabilities
The digital application of QR Code (especially in
smartphones) has some vulnerabilities particularly in
its use in the boarding process. Some of the
vulnerabilities are caused by the use of the device
(Coleman, 2011).
1. Data Duplication
QR Code is possible to be duplicated and
shared by other parties, especially if the code is
stored in the gallery. Regarding the QR Code
which is generated once the data is made,
smartphones’ operation systems can take a
screenshot of the code, so it is saved as an
image file. Texts or pictures taken using
screenshot do not affect the object of QR Code.
This vulnerability can be overcome by limiting
access to screenshot in the application, thus,
users cannot save the image of QR Code.
Nevertheless, this method seems to be
ineffective due to a third-party application.
Also, other cameras can also be used to take a
picture of the code. It is important to note that
QR Code is transferable through emails, chat,
and pictures (using camera), thus, QR Code
might be safe to be used for important data.
2. Data Integrity
QR Code cannot be read without using
decryption, hence, it is difficult to identify the
content of the code manually. It is also difficult
to differentiate the code. This security gap may
be used to lead users to access certain sites
which can steal classified data. In its
implementation in the boarding, QR Code is
utilised in the boarding gate (final check), thus,
the consistency of QR Code with the data
EIC 2018 - The 7th Engineering International Conference (EIC), Engineering International Conference on Education, Concept and
Application on Green Technology
262
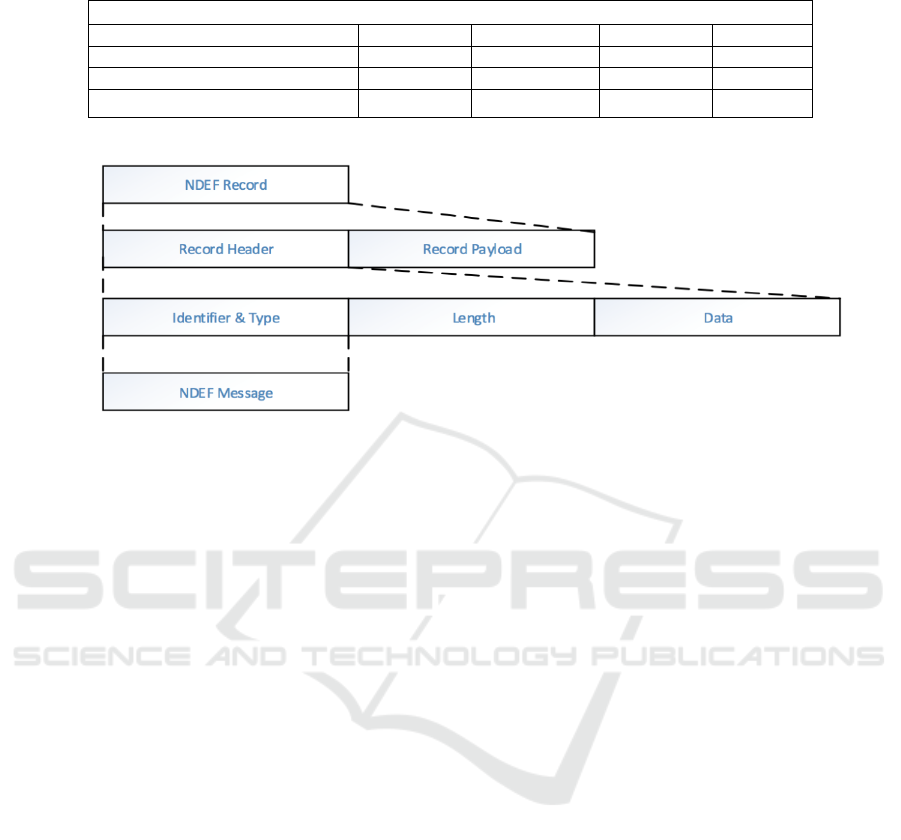
Table 1: TNF Structures.
Record Type
urn:nfc:wkt:T (text)
T
0x54
urn:nfc:wkt:U (uri)
U
0x55
urn:nfc:wkt:Sp (smart poster)
Sp
0x53
0x70
urn:nfc:wkt:Sig (signature)
Sig
0x53
0x69
0x67
Figure 4: NDEF Breakdown Structures.
should be ensured. Incorrect data may cause
administrative problems.
3. User Validation
One of the security methods used to ensure
users’ access is by using user validation in a
form of password or biometric data. However,
since the reader of the QR Code is the airport
staff, validation is done before the code is
generated. Yet, this method may cause data
duplication. Therefore, one of the possible
solutions is that using user validation in a
particular device in airports when the QR Code
is being read. Manual input may slow down the
boarding process, thus, validation using
biometric data such as, fingerprint is suggested.
2.3 Near Field Communication
NFC technology requires a particular chip in
smartphones to read data (Curran, 2012). There are
two kinds of NFC: (1) NFC installed in
smartphones, (2) NFC tag (in a form of cards, key
chains, or stickers). An NFC tag does not require
batteries because the power used to active the chip is
taken from the reader/writer device in the reading
process. Furthermore, NFC itself has three types of
operations, that is, peer to peer (P2P), card
emulation, and writer/reader (Noh, 2013). Regarding
P2P, the sender and the receiver should have an
NFC chip which is connected to smartphones or an
NFC device. The use of this mode in Android
devices can be applied using Android Beam. The
process of data exchange can be done by bring both
devices back to back. Then, the sender is required to
tap on the device’s screen. Reader/writer mode is
used in the NFC tag (passive). When writer/reader
access the NFC tag, the signal will supply power to
activate the NFC tag. Card emulation mode may
affect the NFC device in the sense that it makes the
NFC device work as if it is a smart card (Noh,
2013). This data card emulation is stored in the
secure element.
When data is being written and sent, the data are
encoded according to certain types of data. This type
of data is called Record Type Definition (RTD)
(Renardi, 2017). The function of RTD is to explain
the type of record used such as text, URL, URI, and
vCard. Type Name Format (TNF) (Table 1) is used
to explain the characteristic of RTD. The data are
then processed into NFC Data Exchange Format
(NDEF) (Figure 4).
2.3.1 Benefit of Using NFC
The implementation of NFC in the boarding
process offers some benefits. One of them is that the
distance of NFC reading which is relatively close
can enhance the security as data theft can be
minimised (easier to control) (Coca, 2013).
Moreover, the reading process inside smartphones
can only be accomplished using user (sender)
NFC vs QR Code: A Comparison in Flight Boarding Transaction
263
authorisation, except using card emulation mode or
an NFC tag. Additionally, an NFC tag can be
rewritable and less complex as it does not use
batteries. NFC is utilised for offline transactions
because data are stored in the NFC tag or secure
element (Wu, 2013). By using NFC-enabled
smartphones, users can decide when the stored data
can be read or sent and when the data that will be
stored can be received or read. The data sent using
NFC cannot be identified by third parties, except
there is the Man in The Middle attack. NFC can be
read without using certain applications as long as the
NFC mode is activated. Operation systems will then
select registered applications using NFC in their
operation. P2P mode can be securely used to send
important or sensitive data. However, to ensure the
security, encryption can be applied (Renardi, 2017).
2.3.2 NFC Vulnerabilities
NFC vulnerabilities can be found in the use of NFC-
enabled smartphones and NFC tag. In NFC-enabled
smartphones, the security gap often happens because
users do not follow prescribed procedures.
Meanwhile, regarding the NFC tag, the security gap
usually happens because there is no user validation
method (Ceipidor, 2013).
1. Unauthorized Reading (NFC Tag)
In smartphones which have an NFC sensor,
users can determine when the data will be read,
sent, received, written because the sensor is
active. The NFC tag does not have any
validation features, so it can be read anytime
and by anyone (passive). As a result, it is
possible that data can be read by third parties.
A possible solution to this is by applying
encryption to the stored data.
2. Rewriteable (NFC Tag)
Since there is no user validation mechanism in
the NFC tag, rewriting can be done by anyone.
A possible problem is that the data can be read
and changed by third parties, thus, the data
stored are not consistent. Therefore, the NFC
tag can be made read-only or a certain
key/password can be made, so that changes can
only be done by authorised users.
3. User Interaction
Sometimes, some people are not familiar with
the use of NFC, so system failures or data loss
in the NFC device or NFC tag may happen.
Moreover, P2P mode requires additional
interactions, that is, touching the smartphone’s
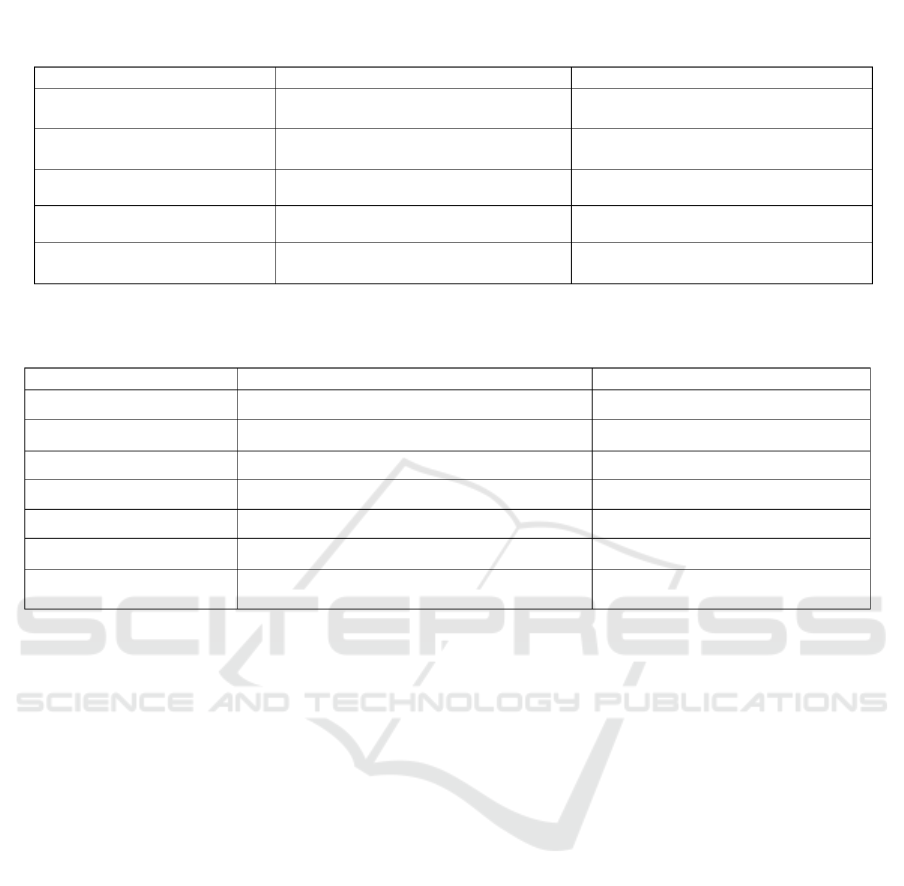
Table 2: QR Code and NFC Vulnerabilities
Aspect
QR Code
NFC
Data Modification
Yes
Yes
Data durability
Readable with 50% damage
Almost no Damage
Privacy
Low (Anyone can read QR code)
High (saved in secure element)
Unauthorized reading
Yes
Only tag or Card Emulation Mode
Security
Low (Dapat diduplikasi)
High
Table 3: QR Code and NFC Limitations
Aspect
QR Code
NFC
Read range
As long as it can be seen clearly
<10cm
Media
Display digital and printed media
NFC tag or NFC device
Identification Speed
Slow (camera focus and CPU process)
Fast (Tap and Go)
Data type coverage
Can handle common data
Can handle common data
Availability of devices
Common
Often
Best For
Online transaction
Offline transaction
Internet Usage
Mostly
Sometimes
EIC 2018 - The 7th Engineering International Conference (EIC), Engineering International Conference on Education, Concept and
Application on Green Technology
264

screen to send the data (Android Beam), hence,
more time is needed to do this transaction.
3 QR CODE VS NFC
QR Code and NFC are two technologies that are
applied in mobiles and used to facilitate contactless
transactions. Both are widely applied such as in sales
transactions, information exchange, document
validation, and check-in transactions in airplanes and
trains. The implementation of these technologies in
the boarding may triggers vulnerabilities and
limitations that can be compared in order to
determine which technology has lower risks and
wider coverage.
In the boarding, transactions are done from users
to airport systems. QR Code has a dangerous
security gap, that is, data duplication and data
breaches in the QR Code (Table 2).
As demonstrated in Table 1, although QR Code
has more vulnerabilities, it is easier to be applied
compared to NFC. In terms of security, the
implementation of QR Code can be secured by
preventing users from taking a screenshot. However,
users can still duplicate data by taking pictures of
QR Code using other devices.
The application of QR Code and NFC has some
limitations. Nevertheless, the limitations can also be
considered as the advantages in terms of security
and suitability for types of transactions. Regarding
the distance range for access, QR Code has more
advantages as it can be accessed from a distant place
as long as the image of the code can be captured by
the camera. With regard to NFC, as NFC requires a
close distance between both devices to do
transactions, it is more secured as attacks can
possible by prevented (easier to control).
Meanwhile, NFC the tag is a passive device, so
anyone may read the data.it is also as dangerous as
QR Code.
4 CONCLUSIONS
This research has shown that in terms of security,
NFC could be more secured. The application of QR
Code could be dangerous because all information
can be extracted from an image of QR Code. Thus,
this technology might not be appropriate for data
exchange which might contain important or sensitive
data that are not encrypted. QR Code could be more
suitable to be used in online transactions because the
data received from the extraction is in a form of
links. Nevertheless, QR Code could also be utilised
in offline transactions because it can send big data
like NFC. It could be argued that the boarding
process using QR Code and NFC goes through
similar stages. Further research may investigate the
implementation of biometric authentication in the
use of QR Code and NFC.
ACKNOWLEDGEMENTS
We would like to thank Ministry of Research,
Technology and Higher Education of the Republic
of Indonesia and Bandung Institute of Technology
for the research funding through Penelitian Terapan
Unggulan Perguruan Tinggi 2018.
REFERENCES
Asare, I. T. and Asare, D. 2015. The Effective Use of
Quick Response (QR) Code as a Marketing Tool.
International Journal of Education and Social
Science, Vol 2(12), pp.67-73.
Basjaruddin, N. C. et al. 2017. Developing Electronic
Medical Record Based on NFC. In: CSAI. Available
Cata, T., Patel, P. S. and Sakaguchi, T. 2013. QR Code: A
New Opportunity for Effective Mobile Marketing.
Journal of Mobile Technology, Knowledge and
Society, 2013, Vol 2013
Ceipidor, U. B. et al. 2013. Mobile Ticketing With NFC
Management for Transport Companies. Problem and
Solutions. In: 5
th
International Workshop on Near
Field Communication (NFC)Zurich: IEEE, pp.1-6.
Available
Coca, J. M. L., et al. 2013. Authentication System Using
ID Card over NFC Links: the Spanish Experience
using DNIe. In: The 4
th
International Conference on
Emerging Ubiquitous System and Pervasive Networks.
ScienceDirect, pp.91-98.
Coleman, J. 2011. QR Codes: What Are They and Why
Should You Care?. In: Kansas Library Association
Collega and University Libraries Section Proceeding,
pp.16-23
Curran, K., Millar, A. and Garvey, C. 2012. Near Field
Communication. International Journal of Electrical
and Computer Engineering (IJECE), 2(3), pp.371-382.
Durak, G., Ozkeskin,E. E. and Ataizi, M. (2016). QR
Codes In Education And Communication. Turkish
Online Journal of Distance Education-TOJDE, Vol
17(2), p.42-58.
Evizal E., et al. 2013. Development of RFID EPC Gen2
Tag for Multi Access Control System. International
Journal of Electtical and Computer Engineering
(IJECE), Vol 3(6), pp.724-731.
NFC vs QR Code: A Comparison in Flight Boarding Transaction
265

Husni, E., Kuspriyanto, K. and Basjaruddin N. 2012.
Mobile Payment Protocol for Tag-to-Tag Near Field
Communication (NFC). International Journal of
Interactive Mobile Technologies, Vol 6(4), pp.34-38.
Kiong, T. P. et al. 2014. Electronic Ticketing in Airline
Industries Among Malaysians: The Determinants.
International Journal of Business and Social Science,
Vol 5(9), p.168-174.
Kolte, S., et al. 2017. A Review on Smart Bus Ticketing
System using QR-Code. International Journal for
Scientific Research & Development, Vol 5(10),
pp.320-322.
Kumar, K. S., Choudhury R. and Basavaraju, S. 2017.
Automated toll collection system using NFC. SSRG
International Journal of Computer Science and
Engineering, Vol 4(3), pp10-13.
Lee, H. T. et al. 2014. Electronic Ticket System Based on
QR Code Identification. In: SICE Annual Conference,
p.1237-1241.
Maheshwar, V. et al. 2018 Android Application on E-
Ticketing Railway System Using QR-Code. IOSR
Journal of Engineering, Vol 13, pp.33-38.
Noh, S. K, et all. 2013. Proposal of Micropayment and
Credit Card Model using NFC Technology in Mobile
Environments. International Journal of Multimedia
and Ubiquitous Engineering, Vol 8(3), pp.295-306.
Putra, E. P., Fifilia, F. and Juwitasary, H. 2018. Trend of
NFC Technology for Payment Transaction.
TELKOMNIKA, Vol 16(2), p.795-802.
Renardi, M. B. et al. 2017., Baggage Claim in Airport
using Near Field Communication. Indonesian Journal
of Electrical Engineering and Computer Science, Vol
7(2), p.442-448.
Renardi, M. B. et al. 2017. Securing Electronic Medical
Record in Near Field Communication using Advanced
Encryption Standard (AES). Technology and Health
Care, Vol 26, pp.357-362.
Rochman, F. F., Raharjana, I. K. and Taufik, T. 2017.
Implementation of QR Code and Digital Signature to
Determine the Validity of KRS and KHS Documents.
Scientific Journal of Informatics, Vol 4(1), p.8-19.
Sunday, D. and Aliyu, W.A. 2016. Design of Mobile-
Based Travel E-Ticketing Using QR-Code. In:
Proceeding of The Second Annual Research
Conference of Federal University Lafia. Nigeria:
Indigenous Knowledge and Relevant Research,
pp.241-247.
Suparta, W. 2012. Application of Near Field
Communication Technology for Mobile Airline
Ticketing. Journal of Computer Science, Vol 8(8),
pp.1235-1243.
Wu, W. J. and Lee, W. H. 2013. An NFC E-Ticket System
with Offline Authentication. International Conference
on Information and Communications & Signal
Processing, Vol 9, pp.1-5.
Qteishat, M. K., Alshibly, H. H. and Al-maáitah, M. A.
2014. The Impact Of E-Ticketing Technique On
Customer Satisfaction: An Empirical Analysis.
Journal of Information Systems and Technology
Management, Vol 11(3), pp.519-532.
Zupanovic, D. 2014. Implementation Model for Near Field
Communication in Croation Ferry Ticketing System.
International Symposium on Intelligent Manufacturing
and Automation (DAAAM), Vol 100(2015), p.1396-
1404.
EIC 2018 - The 7th Engineering International Conference (EIC), Engineering International Conference on Education, Concept and
Application on Green Technology
266
