
Optimize IoT for Operating Wastewater Treatment Plant
based on Visualizing User’s Thinking
J C Chen
*
, Y J Lin
and Z H Tsai
Department of Environmental Engineering and Science, Fooyin University, 151
Jinxue Rd., Dailiao Dist., Kaohsiung City, 83102, Taiwan (R.O.C.)
Corresponding author and e-mail: J C Chen, pl007@fy.edu.tw
Abstract. Sewer system is the major facility of avoiding improper disposal of wastewater. As
expanding wastewater treatment into rural areas, the supervision and the operation will be
more difficult. The fast innovation of IoT in sensor, wireless communication and s mart
control is gaining more and more expectation of IoT to be the next-generation option of
control system in wastewater treatment plant. At present IoT technology is moving rapidly
and its market is very competitive. There are still many uncertainties while making the
decision of upgrading control system to IoT. After all using IoT is an investment, the fault of
choosing an unpopular product and then losing support before long should be avoided. This
study shares the experiences how to identify the needs of IoT based on visualizing user's
thinking and then propose an optimal design of IoT to operating a wastewater treatment plant.
1. Introduction
Right now we face a tough situation that water pollution induced by untreated wastewater is
threatening the sustainable development in the downstream area of river. But so far the supervision
about WWTPs is weak and most of them are far behind the art of AI technology. The improper
disposal due to disorder management or chaotic operation still often happens. Although IoT is able to
extend networks connectivity and computer capability to every device in our living [1], but I do not
mean to suggest the manager of WWTPs immediately upgrading their system to IoT because of huge
diversity from their technologies and prices yet. After all using IoT is an investment, the risk due to
choosing an unpopular product and then losing support before long should be avoided.
By using IoT, Chen et al. [2] made a useful forecasting function of IoT by a neural network to
minimize losses in an emergency. In Zaragoza, Spain, a smart water management model developed
by Robles et al. [3] showed water management company a way to access a wider global market via
adopting IoT in decision support, monitoring and water governance of a pumping system. Artificial
intelligent in IoT will convert the monitoring records into valuable information, e.g. the timing and
supply of critical device [4]. At present IoT technology is moving rapidly and the market is very
competitive [5]. However people still have controversy over the anticipation that the management of
WWTPs will enter the era of IoT. Is it necessary to promote the control system of WWTP to IoT?
For seeking the truth we visited several wastewater treatment plants in the South Taiwan, interviewed
managers and operators form 8 WWTPs and visualized their decision making.
444
Chen, J., Lin, Y. and Tsai, Z.
Optimize IoT for Operating Wastewater Treatment Plant based on Visualizing User’S Thinking.
In Proceedings of the International Workshop on Environmental Management, Science and Engineering (IWEMSE 2018), pages 444-452
ISBN: 978-989-758-344-5
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
This study uses Evaluation Grid Method (EGM) to perform an in-depth interviews that is able to
clearly visualize the user’s cognition as an Evaluation Hierarchical Map [6-7]. Since Sanui modified
Kelly’s repertory grid technique to create this approach, EGM has been successfully employed in
numerous product designs and service designs [8-10].
2. Methods
A schematic overview of the methodology employed was displayed in Figure 1. On April 8, 2017,
we invited 42 experts composed of managers and operators coming from 10 WWTPs to join a
meeting of discussing what kind of smart control they need. First we made a simply explain to these
experts what this meeting is for, and then arrange all experts to take a field trip before sharing vision
each other. This meeting derived a series of analysis at upgrading each device of WWTP to smart
control and summarized their importance as Table 1.
The quality and quantity of information elicited from an interview relies on the personal ability of
an interviewer. For this concern, we created a conceptual IoT for WWTP. In Taiwan almost every
adult owns a smart phone with 4G or WiFi wireless communication. So smart phone become the first
thing existing in the list of IoT we proposed. An App coding by Ruby-on-Rails (RoR) which
connects with the monitoring database running at MySQL server, manipulates the state of visual
relay in InduSoft© and power relay in distance to remote control the device, and supports user smart
services such as device’s knowledge, operating discipline, emergence response, etc. was created to be
the interview material. We spent 3 months to cooperate with an interdisciplinary teams composed of
8 engineers with the expertise of wastewater, sensor, automatic control, and software. This App
successfully promotes the interaction between interviewer and respondent during searching the
attractiveness of IoT in the following in-depth interviews. Moreover some potential functions, e.g.
artificial intelligent to detect the emerging disorder of machine, modelling the operation of engine by
adding sensor of noise, vibration, and electric, were also included into the scope of conceptual IoT
we proposed during interview.
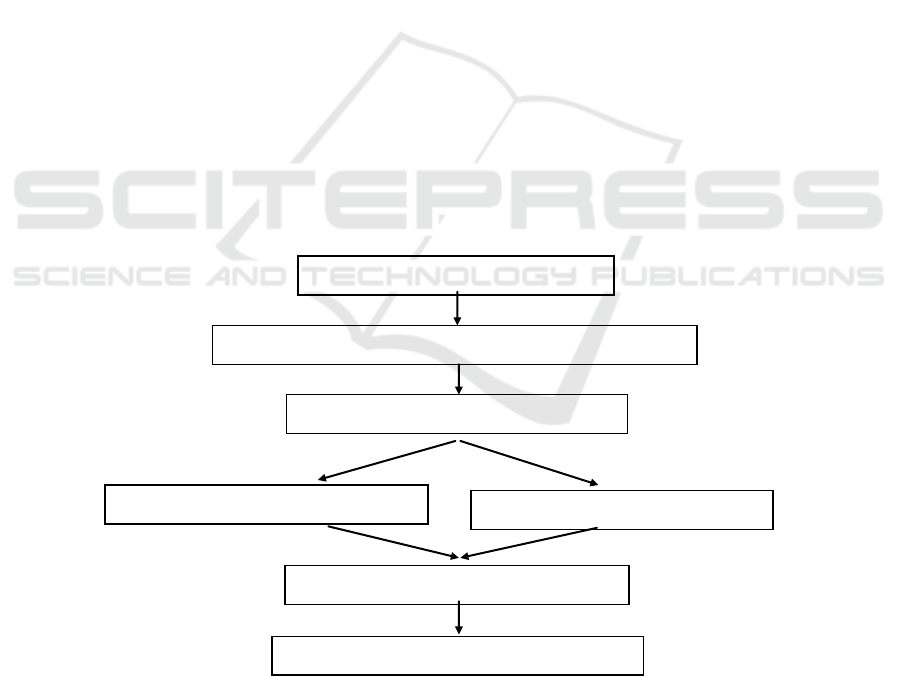
Figure 1. The schematic diagram of research methodology.
2.1. In-depth interview
Manager who has the power of dominating the budget of operating WWTP is of critical to offer
valuable experiences to this study. We visited 8 wastewater treatment plants in the South Taiwan.
Expert meeting on system analysis
Identify the demand of smart control system for WWTP
Create the conceptual IoT for WWTP
In-depth interview with managers
In-depth interview with operators
Construct evaluation hierarchical map
Optimization of IoT for operating WWTP
Optimize IoT for Operating Wastewater Treatment Plant based on Visualizing User’S Thinking
445

Each manager of these plants has been interviewed at least twice or more times. They were asked to
determine their first impression, “satisfied/dissatisfied” or “most preferred/least preferred,” over the
IoT we proposed. Then the discussion during interview will ladder up to identify the abstract reasons
(e.g. value judgment) and ladder down to form concrete features (e.g. objective and concrete
understanding). Such an in-depth interview could make the respondent much more time to confirm
each evaluation item.
Operator will be in the closest relationship with IoT in WWTP. Basically IoT is a tool designed
for assisting operator to serve their duty more efficient if the operator was willing to use it. This
study invited more than 50 new operators to participate our in-depth interview. Discussions were
focused on how they feel the help including machine knowledge, operating discipline, emergence
response through APP we provided. Each operator was interviewed at least twice. After repeated in-
depth interview, we extracted their original feelings while operating WWTP with the aid of IoT, and
then extended to infer their abstract reasons and concrete features about the service supported by IoT.
Eventually each personal evaluation hierarchical map was done as the structure of three-layer
hierarchy
Table 1. The analysis at upgrading each device of WWTP to smart control.
Device
Demand to smart control
Unit
priority
(1~5)
Water pump
Automatic control by water level
Most units
5
Grit chamber
Automatic control by sand thickness
Pumping station, primary clarifier
1
Clay washer
Operation linked with sand pump
Pumping station
3
Mechanical screen
Operation linked with flow rate
Inlet channel
2
Valve/gate
Automatic operation
Most units
3
Scraper
Automatic calibration, Automatic operation
Primary clarifier, final settling tank, sludge
thickening tank
3
Deodorizer
Automatic control by odour concentration
Primary clarifier,
aeration tank
4
Ventilating system
Staff security by operating with gas detector
Primary clarifier,
aeration tank
5
Blower
Adjust air supply by detecting DO
Aeration tank,
sand filter
5
De-foaming
system
Operation by detecting the nozzle pressure
Aeration tank
2
Recycling
Sludge system
Automatic waste sludge by F/M ratio
Aeration tank
2
Aeration system
Detect the oxygen profile
Aeration tank
5
Sludge pumping
Operating by grit/sludge thickness
final settling tank,
sludge thickening tank
5
Scum pump
Automatic control by detecting scum
Final settling tank
4
Feeding pump
Automatic adjust the feeding rate
Sedimentation, filtration, chemical treatment
4
Screw pump
Detect bearing noise
Sludge thickening tank
2
Boiler
Monitoring the digestion state
Sludge digester
5
Dewatering
machine
Detect the shift
Sludge dewatering
5
Conveyor
Detect system’s noise
Sludge dewatering
2
Polymer
preparation
Maintain the concentration of polymer
Aeration tank,
4
PS Priority at ranking 5 is the most importance
IWEMSE 2018 - International Workshop on Environmental Management, Science and Engineering
446
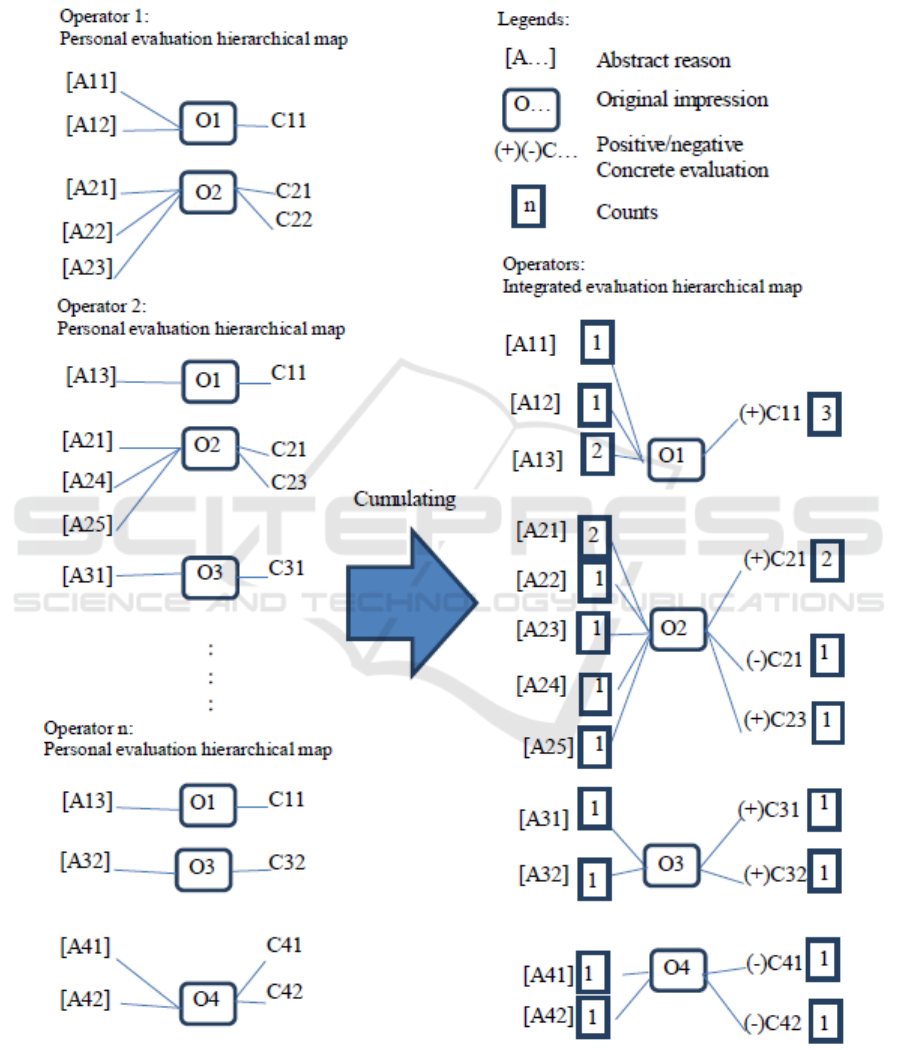
2.2. Evaluation grid method
In this study, we performed the following steps to extract the information from dialog with managers
and operators. Then we adopted EGM to establish a map with three-layer hierarchical structure that
comprises abstract reasons, original impressions, and concrete evaluations (Figure 2).
Figure 2. The process of forming evaluation hierarchical map.
Optimize IoT for Operating Wastewater Treatment Plant based on Visualizing User’S Thinking
447

2.3. Integrated evaluation hierarchical map
Overall EGM provides a method for analyzing product attractiveness factors and eliminates the
potential influence of subjectivity from few decision makers. Then we compile the personal
evaluation hierarchical maps of all the participants and calculate the number of overlapped
evaluations to plot an integrated evaluation hierarchical map. Such a visualization of user’s thinking
does effectively systemize data obtained from in-depth interview and accurately interpret the needs
during optimization of IoT designed for operating WWTP.
3. Results and discussion
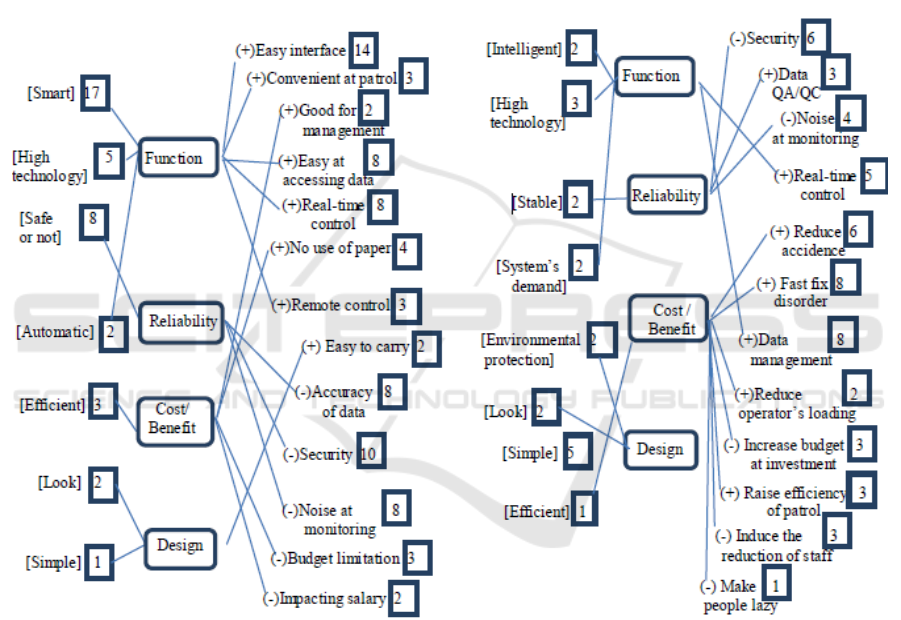
Four original impressions including “Function”, “Reliability”, “Cost/Benefit”, and “Design” are
extracted from the dialogs with operators and managers (Figure 3 and 4). We found that operators
give more concrete evaluations than managers with respect to its “Function”. It implies that operators
especially care how this future tool affects their daily works. From the view of product design, we
should focus on the need of operators. But operator is not the buyer of IoT in this case. Manager or
maybe more high rank position is the decision maker of promoting control system to IoT in practice.
The factor of “Cost/Benefit” is what manager really concern. Interestingly operators also care about
the factor of Cost/Benefit and they reflect many negative concrete evaluations, especially worrying
about their salary been changed. Even though the IoT designed for operating WWTP is powerful, an
expensive IoT would be not succeed in such a case which every manager doesn’t want to see the
resistance from operator. So the IoT suppliers have to seek a compromise between function and price.
When both managers and operators accept to use IoT they start to care its “Reliability” in
choosing which service of IoT they can trust. The accuracy and security of data are the highest
concerns during concrete evaluations of managers and operators. However hacker or terrorist might
attack the control system to make a chaos in system operation as far as IoT extending networks
connectivity to different device of WWTP. That is why I highlight IoT not a free or cheap service
because its service needs a security of high cost.
The last original impression is “Design”. The performance of manager in this item only
concentrate on the abstract reasons, that is to say manager cares about what corporate image would
be connected with using IoT. We suggest the supplier of IoT to taken into account of enterprise social
responsibility in environmental protection during designing IoT for operating WWTP.
3.1. Technical demand of IoT in WWTP
We screen some critical demands out of Table 1. What kind of technical support does the IoT
supplier have to provide for these demands? We makes an evaluation as Table 2. The architecture of
IoT was generally divided into three layers: Perception Layer, Network Layer, and Application layer.
Obviously the ability of perception is the most important service when these experts of WWTP take
into account of IoT. Perception layer is in charge of converting the information to digital signals,
which are more convenient for network transmission. This process of perception is based on several
sensing technologies. However, some objects might not be perceived directly. Right now sensors of
water level, dissolved oxygen, and sludge interface have been popularly used in WWTP. Air sensors
with respect to odor and volatile organic compound are mature in technical development but not
popular in use yet. But some sensors, like detecting the shift of dewatering machine and measuring
polymer concentration, are still in developing.
Application Layer constitutes the front end of the whole IoT architecture through which user can
obtain any kind of decision support. In this study, we provide cloud service including device’s
knowledge, operating discipline, emergence response and electric form of inspection to the operator
on patrol through an App installed in mobile phone. Moreover, this layer provides the connection
with actuating devices in distance. So expert system in cloud is able to automatically manipulate the
distant device for avoiding the situation going into chaos. Usually pumping system is only operated
IWEMSE 2018 - International Workshop on Environmental Management, Science and Engineering
448

by water level, but operation of pump in practice needs more expert’s experience. Actually the inflow
of WWTP is dynamic, the flowrate and the concentration of wastewater is variant and not the same
as the condition of original design. Even a small rainfall, a significant raise at inlet flowrate could
suddenly happen. Such a changing inflow will cause an unstable operation of WWTP, moreover
severe situation during storm will induce combined sewage overflow. Thus operating rules extracted
from historic records or expert’s experiences from long career are of critical in the automatic control
of pumping system, and are suggested to be developed as a technical service from IoT. Based on
such a smart water management model, the IoT suppliers can access a wider global market via
providing decision support, monitoring and water governance of a pumping system.
Activated sludge process is very popular used to degrade the nutrients, e.g. BOD, in wastewater.
Most of sludge in this process is alive and aerobic, so a lot of air is continuously transported into this
process via blower. A complex biodegradation is only executed by those activated sludge. So we
have to waste the old sludge out and recycle the active back. This is not an easy job to operator, as
we see, most of demands in Table 2 focuses on sludge. We suggest the supplier of IoT to make data
mining from mega data of monitoring system in activated sludge process and then to provide
operator a web-service with artificial intelligent about feeding sludge.
Next we evaluated the measurement of oxygen profile at aeration tank, the measurement of
concentration at dosage, the alarm of health risk and the alarm of machine shift as the items which
need technical support from network layer in IoT. So far the signal processing, the noise filter, the
detecting way, the communication path for the measurements in these procedures are still immature.
It is an opportunity for those IoT suppliers if they own critical patent at these new measurements.
3.2. Optimization of IoT in WWTP
After re-organizing the messages of evaluation hierarchical maps from Figure 3 and 4, we create
three procedures as below to fulfil optimization of IoT we proposed in this study.
Principle I: Minimizing the negative concern from managers is the first step, so the IoT supplier
have to meet data management in a high reliability.
Principle II: Then IoT supplier have to fast fix disorder, provide an efficient service at data
management, effectively reduce the staff’s accident to maximize the positive cognitions from
managers, but any plan for principle II must be not against the first principle.
Principle III: “simple”, “easily access data”, “real-time control” would be essential functions in
order to maximize the positive cognitions from operators. However designing these function must be
not against principle I and II.
As you see in Figure 4 negative concerns connected with reliability are primarily focused on
“security” and “noise at monitoring”. Indeed there is a growing worry that control system of WWTP
is too vulnerable to prevent cyber-attack. In addition to malicious intruder, adopting easy but
vulnerable coding method, open to connect other networks, insecure remote connection are
recognized to escalate the cyber risk of control system. In terms of security technologies and
experiences, SCADA is more mature to securing control system than IoT at present. For meeting
principle I, we suggest the decision maker of WWTP carefully extends the IoT tentacle on the basis
of SCADA to operation.
To be contrary, the IoT supplier must make much more efforts on developing web services with
predictive analysis to forecast system’s risk and cloud knowledge base with prescriptive analysis to
avoid staff stuck in the trouble of system’s disorder. Any service created for principal II must be
qualified by the standards of high information security. Here I suggest the control system and the
web service adopt different communication networks and make a gap to avoid connecting each other
networks for security. For example, the control system is connected with SCADA on the fiber
network and the predictive analysis and the prescriptive analysis from IoT are transfer to smart phone
on the wireless network.
Optimize IoT for Operating Wastewater Treatment Plant based on Visualizing User’S Thinking
449
Although manager controls the budget and owns the power of making decision to upgrade control
system to IoT, operator will be in the closest relationship with IoT of all staffs in WWTP. Nature of
IoT being a tool designed for assisting operators to serve their duty more efficient highlights an
essential precondition that operators must be willing to use it. “simple”, “easily access data”, “real-
time control” are the top 3 of features which be able to catch the eye of operators. But there is a tug
of war between “simple” and “easily access data”, also between “simple” and “real-time control”
under the above principals. We suggest the IoT suppliers to make a fast copy of system monitoring
data on different mirror server then to let operators easily access what they care about but can’t let
them touch the server of control system in practice. And we suggest a double-check procedure is
necessary before putting a command of real-time control into action, that is to say, launching real-
time control to cease system’s disorder must be reconfirmed by more than two staffs.
Figure 3. The integrated evaluation Figure 4. The integrated evaluation
hierarchical map from operators. hierarchical map from managers.
IWEMSE 2018 - International Workshop on Environmental Management, Science and Engineering
450

Table 2. Evaluate the technical support of IoT to smart control of WWTP.
The critical demand to smart control
Technical support of IoT
Perception
Network
Application
1
Automatic control of pumping system
○
○
2
Adjust air supply of blower
○
○
3
Sludge pumping
○
○
4
Detect the oxygen profile at aeration tank
○
○
5
Automatic removal of scum
○
6
Staff security
○
○
○
7
Automatic control of deodorizer
○
○
8
Preparation of chemical dosage
○
○
9
Automatic dosage feeding
○
○
10
Operate & monitor sludge digestion
○
○
11
Detect the shift of dewatering machine
○
○
PS “○” means that technical support of IoT is needed in this item.
4. Conclusions
As more and more wastewater treatment plants been built and in operation, IoT with novel sensors,
wireless communication and smart control will become the part of control system in WWTP. At
present IoT technology is moving rapidly and its market is very competitive. We suggest that
“reliability” is the first criterion in priority during adopting IoT. The decision maker of WWTP had
better add the IoT object into control system only being passed the qualification of information
security. And we also suggest adding a gap to separate control system and web service running on
different communication networks.
“simple”, “easily access data”, “real-time control” are the top 3 of IoT’s features operators care. Is
it necessary to promote the control system of WWTP to IoT? This study suggests WWTP step-by-
step expand its IoT networks and only open its connection with different network after double-check
security.
Acknowledgement
The authors express deep gratitude to the National Science Council in Taiwan for the financial
support (NSC 106-2622-E-242-001-CC2).
References
[1] Rose K, Eldridge S and Chapin L 2015 The Internet of things: an overview_ understanding the
issues and challenges of a more connected world The Internet Society (ISOC)
https://wwwinternetsocietyorg/iot
[2] Chen X, Liu X and Xu P 2015 IOT-based air pollution monitoring and forecasting system
2015 International Conference on Computer and Computational Sciences (ICCCS) 257 –
260
[3] Robles T, Diego M R A, Navarro M, Calero R, Iglesias S and Lopez M 2015 An IoT based
reference architecture for smart water management processes Journal of Wireless Mobile
Networks, Ubiquitous Computing, and Dependable Applications 6(1) 4-23
[4] Vermesan O and Friess P 2014 Internet of things-from research and innovation to market
deployment River publishers Denmark
[5] Thierer A and Castillo A 2015 Projecting the growth and economic impact of the internet of
things George Mason University, Mercatus Center, June 15, 2015
http://mercatusorg/sites/default/files/IoT-EP-v3pdf
[6] Ma M Y, Wei C C and Lin Y C 2014 An attractiveness evaluation of picture books based on
Optimize IoT for Operating Wastewater Treatment Plant based on Visualizing User’S Thinking
451

children's perspectives Proceedings of UMAP 2014 posters, demonstrations and late-
breaking results 87-92
[7] Chang H C and Chen H Y 2017 Exploration of action figure appeals using evaluation grid
method and quantification theory type I EURASIA Journal of Mathematics Science and
Technology Education 13(5) 1445-1459, DOI 1012973/eurasia201700679a
[8] Sanui J 1996 Visualization of users' requirements: introduction of the evaluation grid method
Proceedings of the 3rd Design & Decision Support Systems in Architecture & Urban
Planning Conference 1 365-374
[9] Ma M Y, Chen Y C and Li S R, 2011 How to Build Design Strategy for Attractiveness of New
Products Advances in Information Sciences & Service Sciences 3(11) 1-10
[10] Wei C C, Ma M Y and Lin Y C 2011 Applying Kansei engineering to decision making in
fragrance form design Intelligent Decision Technologies 85-94 Berlin Heidelberg: Springer
IWEMSE 2018 - International Workshop on Environmental Management, Science and Engineering
452
