
Cost-effective Private Linear Key Agreement with Adaptive CCA
Security from Prime Order Multilinear Maps and Tracing Traitors
Mriganka Mandal and Ratna Dutta
Department of Mathematics, Indian Institute of Technology Kharagpur, Kharagpur, 721302, India
Keywords:
Broadcast Encryption, Traitor Tracing, Multilinear Maps, Indistinguishability Obfuscation.
Abstract:
Private linear key agreement (PLKA) enables a group of users to agree upon a common session key in a bro-
adcast encryption (BE) scenario, while traitor tracing (TT) system allows a tracer to identify conspiracy of
a troop of colluding pirate users. This paper introduces a key encapsulation mechanism in BE that provides
the functionalities of both PLKA and TT in a unified cost-effective primitive. Our PLKA based traitor tracing
offers a solution to the problem of achieving full collusion resistance property and public traceability simul-
taneously with significant efficiency and storage compared to a sequential improvement of the PLKA based
traitor tracing systems. Our PLKA builds on a prime order multilinear group setting employing indistinguis-
hability obfuscation (iO) and pseudorandom function (PRF). The resulting scheme has a fair communication,
storage and computational efficiency compared to that of composite order groups. Our PLKA is adaptively
chosen ciphertext attack (CCA)-secure and based on the hardness of the multilinear assumption, namely, the
Decisional Hybrid Diffie-Hellman Exponent (DHDHE) assumption in standard model and so far a plausible
improvement in the literature. More precisely, our PLKA design significantly reduces the ciphertext size, pu-
blic parameter size and user secret key size. We frame a traitor tracing algorithm with shorter running time
which can be executed publicly.
1 INTRODUCTION
A private linear key agreement (PLKA) under key
encapsulation framework requires the broadcaster to
broadcast a common message, called header, for
a specific type of user sets [i] ∈ S where S =
{[1],... , [N]} ⊂ 2
[N]
and [i] = {1,...,i} is the col-
lection of users. Each user is assigned a private key
by a group manager (GM). The GM is a trusted third
party and the role of a broadcaster may be played by
the GM or by a seperate entity depending on applica-
tions. The header along with the user’s pre-assigned
private key enables users in [i] to extract a session key
common to all the users in [i]. On the other hand,
a PLKA based broadcast encryption (BE) empowers
a content broadcaster to broadcast an encrypted mes-
sage under a common session key for [i] ∈ S so that
a user u ∈[i] can decrypt the ciphertext using his pri-
vate key. The users outside [i] obtain nothing even
if they collude for both the key encapsulation model
and broadcast model of PLKA. The first construction
for PLKA was designed by (Boneh et al., 2006; Bo-
neh and Waters, 2006) followed by a number of works
(Garg et al., 2010; Boneh and Zhandry, 2014; Nishi-
maki et al., 2016).
Consider a traditional cable TV system where the
broadcaster broadcasts a classified digital content en-
crypted under a publicly known key to a set of le-
gitimate users. Each legitimate user, having a valid
private key embedded within a set-top box provided
by the GM, can successfully decrypt and recover the
classified content. Any user, who has paid to get his
private key from the GM, might make a reprint to re-
sell his private key or even publish it on the Internet.
This allows unauthorized users to decrypt the classi-
fied content without having a legal authorization, cau-
sing the broadcaster a massive financial loss. Conse-
quently, the broadcaster will attempt to identify those
rouge user.
A Traitor tracing (TT) system is devised to aid
content broadcasters to identify conspiracy of defrau-
ders who create a pirate decoder box. A coalition
of traitors might make a conspiracy to create the
pirate decoder containing an arbitrarily complex and
even obfuscated malicious program and is capable
of decrypting the encrypted digital content. The
traitors might alter their private keys in such a way
that the altered keys cannot be linked with their
356
Mandal, M. and Dutta, R.
Cost-effective Private Linear Key Agreement with Adaptive CCA Security from Prime Order Multilinear Maps and Tracing Traitors.
DOI: 10.5220/0006845503560363
In Proceedings of the 15th International Joint Conference on e-Business and Telecommunications (ICETE 2018) - Volume 2: SECRYPT, pages 356-363
ISBN: 978-989-758-319-3
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
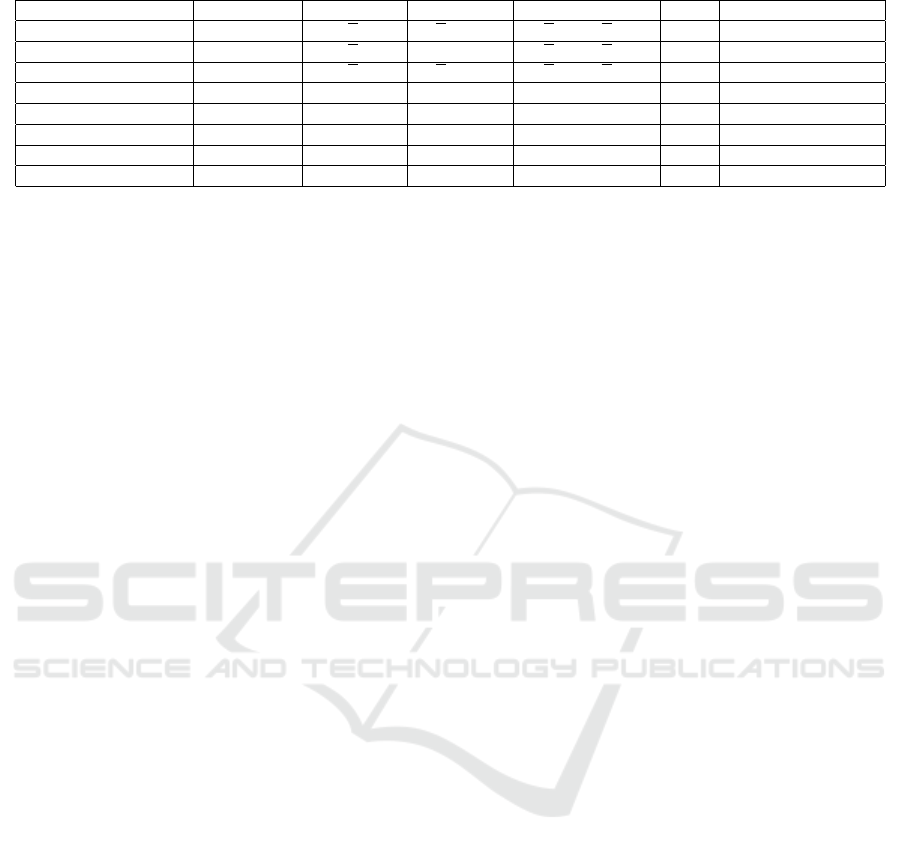
Table 1: Comparison summary of communication, storage and other functionality.
Scheme Group Type |PP| |sk
u
| |CT| TRA Complexity Assumptions
(Boneh and Waters, 2006) composite, BL 9
√
N +5 (
√
N +1) in G 6
√
N in G,
√
N in G
T
public D3DH, DHSD, BSD
(Boneh et al., 2006) composite, BL 4
√
N +3 1 in G 5
√
N in G,
√
N in G
T
secret D3DH, DHSD, BSD
(Garg et al., 2010) prime, BL 4
√
N +1 (
√
N +1) in G 6
√
N in G,
√
N in G
T
public D3DH, XDH
(Boneh and Zhandry, 2014) − poly(log N,η) η poly(logN, η) public iO & FE security
(Nishimaki et al., 2016)−I − poly(η) poly(n) poly(n,|m|) public iO & FE security
(Nishimaki et al., 2016)−II − poly(logn) poly(n) |m|+poly(log n) public iO security
(Garg et al., 2016) composite, ML poly(logN) poly(logN) poly(logN) public FE security
Ours prime, ML poly(log N, η) 1 in G
~
ρ
2 in G
~
ρ
, 3η, log(N) public DHDHE and iO security
|PP| = public parameter size, |sk
u
| = user secret key size, |CT| = ciphertext size, TRA = traceability, BL = bilinear, ML = multilinear, FE = functional encryption,
D3DH = Decision (modified) 3-party Diffie-Hellman, DHSD = Diffie-Hellman Subgroup Decision, BSD = Bilinear Subgroup Decision, XDH = External
Diffie-Hellman, DHDHE = Decisional Hybrid Diffie-Hellman Exponent assumptions, G = Bilinear source group, G
T
= Bilinear target group, G
~
ρ
= Multilinear
intermediate group, n = arbitrary bit-length of user identity, |m| = message-bit length, N = total number of users in the system and, η = security parameter.
original private keys. A traitor tracing system runs
an efficient tracing algorithm that interacts with the
pirate decoder considering it as a black-box oracle
and outputs at least one identity of the traitors in the
coalition who was involved to create the malicious
program using his own private key. Pirate cable TV,
set-top decoders, encrypted satellite radio, pirate
decryption software posted on the Internet etc. are
few examples of pirate decoder box.
A naive approach to address this problem is the fol-
lowing. For a system having N users, the broadcaster
broadcasts N ciphertext under N different public keys
whereby a legitimate user can decrypt the ciphertext
corresponding to his own secret key. Consequently,
given any pirate decoder, it is easy to pinpoint at least
one traitor whose secret key is used to fabricate the
pirate decoder. However, this solution is inefficient as
the ciphertext size is linear in N. Although a PLKA
system has the capability of fraud detection, it is not
always possible to switch a general BE scheme into
a tracing scheme. Designing a PLKA traitor tracing,
with shorter size ciphertext, public parameter and the
user secret key is a challenging task.
Related Work. Traitor tracing was formally intro-
duced by (Chor et al., 1994), followed by a several
works in different flavors (Kiayias and Yung, 2001;
Boneh and Waters, 2006; Boneh et al., 2006; Garg
et al., 2010; Boneh and Zhandry, 2014; Nishimaki
et al., 2016; Garg et al., 2016).
In 2001, (Kiayias and Yung, 2001) proposed t-
collusion resistant tracing mechanism with ciphertext
size linear in t. A collusion of at most t-users are
allowed to construct a pirate decoder in such system.
The first fully collusion resistant PLKA with traitor
tracing was proposed by (Boneh and Waters, 2006;
Boneh et al., 2006) in composite order bilinear group
with sublinear size parameters. Later, (Garg et al.,
2010) developed a similar variant on prime order bili-
nar group setting. Depending on the tracing authority,
traitor tracing systems fall into two categories − (a)
publicly traceable that does not require any secret
inputs except the public parameter in the tracing
algorithm (Boneh and Waters, 2006; Garg et al.,
2010; Boneh and Zhandry, 2014; Nishimaki et al.,
2016; Garg et al., 2016), and (b) secretly traceable
which uses a secret tracing key to identify rogue users
(Boneh et al., 2006; Kiayias and Yung, 2001). In
2014, (Boneh and Zhandry, 2014) constructed a fully
collusion resistant PLKA traitor tracing with public
traceability utilizing the constrained pseudorandom
functions (cPRFs) and indistinguishability obfusca-
tion (iO). All the aforementioned PLKA schemes use
the Hybrid Coloring tracing approach of (Kiayias and
Yung, 2001). Adopting iO, (Nishimaki et al., 2016)
exhibited that a PLKA traitor tracing is an immediate
consequence of functional encryption (FE). In (Garg
et al., 2016), a FE scheme is designed in composite
order asymmetric multilinear group setting without
iO and provides another indirect construction of
traitor tracing. None of the schemes (Nishimaki
et al., 2016; Garg et al., 2016) provide explicit
construction of PLKA traitor tracing. As pointed out
by (Garg et al., 2010), the communication, storage,
and computational efficiency of prime order groups
are much higher compared to that of composite
order group. Our main focus in this work is to build
a PLKA traitor tracing scheme over prime order
multilinear groups (Coron et al., 2015; Gentry et al.,
2015) achieving order-of-magnitude improvements
in efficiency and storage without any security breach.
Our Contribution. We design a PLKA con-
struction coupling pseudorandom function (PRF)
of (Goldreich et al., 1986) with indistinguishability
obfuscation (iO) and adopting multilinear maps over
prime order group. Note that several recent attacks
have broken many assumptions on known multilinear
maps (Coron et al., 2015; Gentry et al., 2015).
Recently, (Gu, 2015) constructed a new variant of
the multilinear maps which seemed to thwart known
attacks. We skillfully integrate the tracing mecha-
nism of (Kiayias and Yung, 2001) in our PLKA,
yielding the first fully collusion resistant and publicly
Cost-effective Private Linear Key Agreement with Adaptive CCA Security from Prime Order Multilinear Maps and Tracing Traitors
357
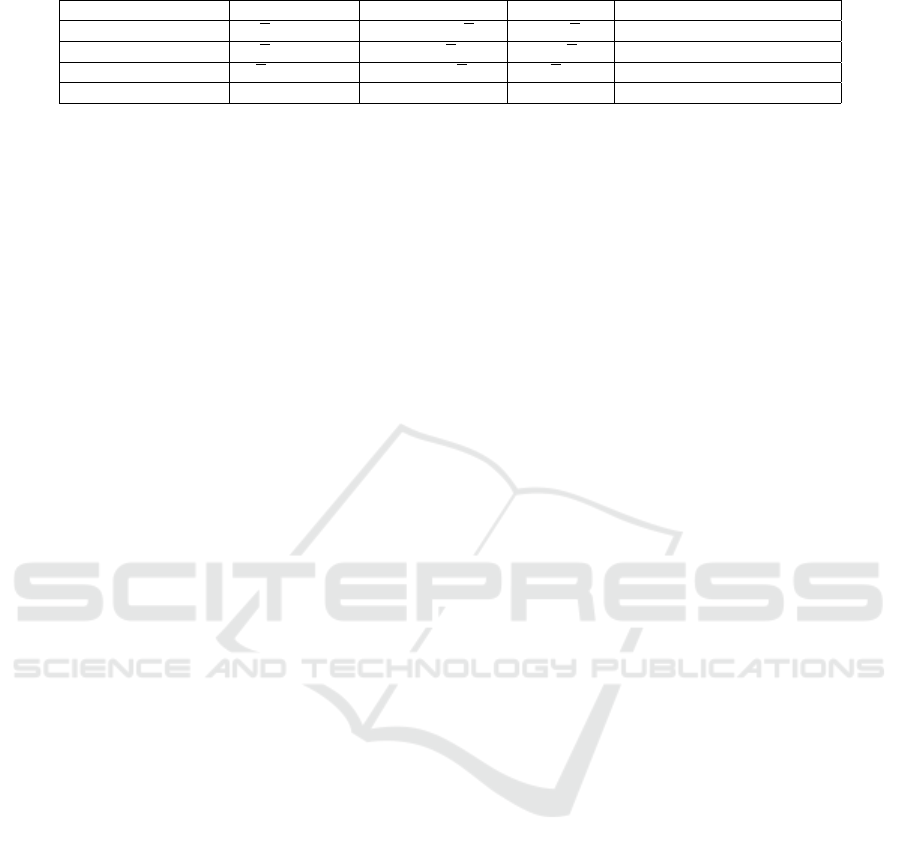
Table 2: Comparative summary of computation and tracing time.
PLKA Pairing Exponentiation Product Running Time of Tracing Algorithm
(Boneh and Waters, 2006) 3
√
N +4 (bilinear) 3N + (N +15)
√
N +4 4N + 5
√
N +4 O(N
3
)
(Boneh et al., 2006) 2
√
N +3 (bilinear) 2N +10
√
N +1 N +3
√
N +4 O(N
3
)
(Garg et al., 2010)
√
N +8 (bilinear) 3N +24
√
N 3
√
N +11 O(N
3
)
Ours 2 (multilinear) 3N +8 2N +3 poly((logN)
2
,η)
N = total number of users in the system, η = security parameter.
traceable PLKA traitor tracing in key encapsulation
framework over prime order multilinear group setting
with tracing algorithm having shorter running time.
We summarize below our main findings in this work:
• Our PLKA construction significantly reduces the
parameter sizes as exhibited by Table 1. The public
parameter size in our construction is polylogarithmic
in N while the ciphertext size is logarithmic in N.
Here, N is the total number of users in the system.
More interestingly, user secret key is a single multili-
near group element in our PLKA.
• We emphasize that our scheme is adaptively
chosen ciphertext attack (CCA)-secure under
the Decisional Hybrid Diffie-Hellman Exponent
(DHDHE)-assumption in standard security model
and relies on iO security. Note that recently iO is
aggregately constructible from the puncturable secret
key functional encryption (Kitagawa et al., 2018).
Our tracing algorithm enables to trace the conspiracy
of an arbitrary number of defrauders using the public
parameter only. On a more positive note, we have
shown that although we follow the tracing approach
of (Kiayias and Yung, 2001), the run time of our
tracing algorithm is poly((log N)
2
,η), where η is the
security parameter. However, the running time of
tracing algorithms is O(N
3
) for all the existing PLKA
traitor tracing schemes based on Hybrid Coloring
tracing mechanism of (Kiayias and Yung, 2001).
In sum, we achieve a publicly traceable and fully
collusion resistant traitor tracing scheme with shorter
running time.
• The PLKA design of (Boneh and Waters, 2006;
Boneh et al., 2006; Garg et al., 2010) uses bilinear
maps while that of (Boneh and Zhandry, 2014) is
constructed using the security of iO and cPRFs
(Boneh and Waters, 2013). The work of (Nishimaki
et al., 2016; Garg et al., 2016) are based on FE. Cou-
pling iO with the one way function, (Nishimaki et al.,
2016) constructed a FE scheme and furnished an idea
to transform it into a traitor tracing scheme. They
set up with the exponentially large identity space and
embedded user’s arbitrary information in their secret
key. As a result, the user identity bit-length become
arbitrarily large. As shown in Table 1, the size of
ciphertext and the user secret key in their works
grow with the identity bit-length which is arbitrarily
large, and also the ciphertext size depends on the
message-bit length. The size of the parameters in
our PLKA construction are independent of identity
bit-length as well as the message-bit length. Our
PLKA has similar parameter sizes as that of the
PLKA of (Boneh and Zhandry, 2014) which stance
upon four cPRFs in generic forms showing only
the input-output behavior. Additionally, the work of
(Boneh and Zhandry, 2014) utilizes the multilinear
map based cPRF of (Boneh and Waters, 2013) which
are themselves based on multilinear maps that requi-
res at least O(log N) symmetric multilinear pairing
operations which are known to be very expensive. In
contrast, we use only two PRFs of (Goldreich et al.,
1986) which are efficient due to their inherent tree
structures.
• Table 2 shows the computation comparison in terms
of number of pairings, exponentiations, multiplicati-
ons and run time of the tracing algorithm. We ex-
clude (Garg et al., 2016; Nishimaki et al., 2016; Bo-
neh and Zhandry, 2014) from Table 2 as suitable FE
schemes and multiparty key exchange protocols are
the primary requirements in these works rather than
direct constructions for traitor tracing. To trace all
the traitors, (Nishimaki et al., 2016) proposed an ora-
cle jump finding (OJF) problem and showed that any
PLKA is sufficient for traitor tracing employing OJF
problem. However, to run the tracing algorithm, the
works of (Nishimaki et al., 2016) requires the total
number q of traitors belonging to the pirate decoder
D as an extra input and run time of OJF algorithm is
poly(logN, q, η) which is faster than our PLKA con-
struction. For the bounded collusion resistant sche-
mes, q is publicly known. In many real life scenarios,
the tracing algorithm is given black-box interactions
with D and finding q at prior not always possible.
Unlike this, our tracing algorithm does not require
any prior knowledge of parameters like q and runs in
poly((logN)
2
,η) time using only the public parame-
ter as the inputs.
2 PRELIMINARY
Notation. Let, [ j] = {1, . . . , j} be the set of all po-
sitive integers from 1 to j. Given any set S, x ∈
R
S
stands for x drawn uniformly at random from S. For a
SECRYPT 2018 - International Conference on Security and Cryptography
358

randomized algorithm RandA, y ← RandA(z) repre-
sents output by RandA on input z. The equivalence
relation over a set is denoted by ≡. A probabilistic
polynomial time algorithm is denoted by PPT and η
is the security parameter.
Definition 1. (Negligible Function) A function Ψ :
N → R is said to be negligible in N, if for every po-
sitive integer c there exists an integer N
c
such that
|Ψ(N)| <
1
N
c
for all N > N
c
.
Definition 2. (Chernoff Bound) Let, X =
n
∑
i=1
X
i
,
where X
i
independent random variables for i =
1,.. . , n. Let X
i
= 1 with probability p
i
, X
i
= 0 with
probability 1 −p
i
and µ = E(X ) =
n
∑
i=1
p
i
is the expec-
tation. Then, Pr [|X −µ|≥ a] ≤ 2e
−2a
2
n
, where a = µδ
is an arbitrary constant and 0 < δ < 1.
Definition 3. (Pseudorandom Function (PRF)) A
PRF (Blum and Micali, 1984) is a function denoted
by PRF : K ×X → Y , that can be computed by a de-
terministic polynomial time algorithm which on input
a fixed but randomly chosen key k ∈ K and any point
x ∈ X , outputs PRF(k, x) ∈ Y such that PRF(k,·) is
indistinguishable from a random function.
Henceforth, PRF
k
(·) refers to PRF(k, ·) for a random
key k ∈ K .
Definition 4. (Indistinguishability Obfuscator) A
uniform probabilistic polynomial time machine iO for
a circuit class {C
η
}, with circuits of size at most η,
is called an indistinguishability obfuscator (iO) (Kit-
agawa et al., 2018) if it amuses the following proper-
ties.
• Functionality Preserving: For all security parame-
ters η ∈ N, for all circuit C ∈ {C
η
} and for all inputs
x, iO(η,C) preserves the functionality of the circuit C
under the obfuscation, i.e., Pr[∀x,C
0
(x) =C(x) : C
0
←
iO(η,C)] = 1.
• Indistinguishability: For all pairs of probabilis-
tic polynomial time adversaries A = (D
1
,D
2
),
there exists a negligible function ζ(η) such
that, if Pr[∀x,C
0
(x) = C
1
(x) : (C
0
,C
1
,σ) ←
D
1
(η)] > 1 − ζ(η) then |Pr[D
2
(σ,iO(η,C
0
)) =
1] −Pr[D
2
(σ,iO(η,C
1
)) = 1]| < ζ(η).
Note that if no confusion arises, we will omit η as an
input to iO and as a subscript for C.
2.1 Asymmetric Multilinear Map and
Complexity Assumption
A (leveled) asymmetric multilinear map aM M =
(aM M .Setup, e
~
ϑ
1
,
~
ϑ
2
) of (Coron et al., 2015; Gentry
et al., 2015) consists of the following two algorithms.
• (aPPM)← aM M .Setup(1
η
,
~
ρ): It takes as input
the security parameter 1
η
and sets up
~
ρ-leveled linear
map, where
~
ρ is some positive vector of length κ + 1.
It outputs a description of all possible groups G
~
ϑ
for
all the vectors
~
ϑ ∈ (N ∪{0})
κ+1
with the restriction
that
~
ϑ ≤
~
ρ (with component-wise comparison). For
all such vectors
~
ϑ, it outputs the canonical generators
g
~
ϑ
∈G
~
ϑ
. Let ~e
i
, i = 0,. . ., κ be the i-th standard basis
vector, with 1 at position i and 0 elsewhere. Define
G
~e
i
as the i-th source group, G
~
ρ
as the target group,
and rest of G
~
ϑ
as the intermediate groups and all the
groups have same large prime order p > 2
η
. As there
are uncountable numbers of such vectors, it is hard to
publish all. Instead, one can publish a public parame-
ter aPPM = (κ, g
~e
0
,.. . , g
~e
κ
) consisting of only source
groups’ canonical generators.
• (g
ab
~
ϑ
1
+
~
ϑ
2
)← e
~
ϑ
1
,
~
ϑ
2
(g
a
~
ϑ
1
,g
b
~
ϑ
2
): On input elements
g
a
~
ϑ
1
∈ G
~
ϑ
1
, g
b
~
ϑ
2
∈ G
~
ϑ
2
with
~
ϑ
1
+
~
ϑ
2
≤
~
ρ,
~
ϑ
1
,
~
ϑ
2
∈
R
(N ∪{0})
κ+1
, for all a, b ∈
R
Z
p
and it outputs an ele-
ment of G
~
ϑ
1
+
~
ϑ
2
such that e
~
ϑ
1
,
~
ϑ
2
(g
a
~
ϑ
1
,g
b
~
ϑ
2
) = g
ab
~
ϑ
1
+
~
ϑ
2
.
Note that we often omit the subscripts and just write
e. We can also generalize e to multiple inputs as
e(h
(1)
,h
(2)
,.. . , h
(ζ)
) = e(h
(1)
,e(h
(2)
,.. . , h
(ζ)
)). The
following assumption is from (Boneh et al., 2014).
– It runs the algorithm aM M .Setup(1
η
,2
~
ρ) to
generate aPPM = (κ,g
~e
0
,... , g
~e
κ
) and e is the
description of the multilinear map
– It picks random t and ξ from Z
p
and computes
V = g
t
~
ρ
, Γ
0
= (g
~e
0
)
ξ
, Γ
1
= (g
~e
1
)
ξ
2
, ..., Γ
κ−1
=
(g
~e
κ−1
)
ξ
2
κ−1
, Γ
κ
= (g
~e
κ
)
ξ
2
κ
+1
– It sets T
0
= (g
2
~
ρ
)
tξ
2
κ
, T
1
= R ∈
R
G
2
~
ρ
– It returns χ
µ
= (e,aPPM, Γ
0
,... , Γ
κ−1
,Γ
κ
,
V,T
µ
)
Figure 1: κ-DHDHE instance generator G
κ−DHDHE
µ
.
κ-Decisional Hybrid Diffie-Hellman Exponent As-
sumption (κ-DHDHE). The κ-DHDHE problem is to
guess µ ∈{0, 1} given χ
µ
= (e,aPPM,Γ
0
,..., Γ
κ
,V ,T
µ
)
generated by the generator G
κ−DHDHE
µ
shown in Fi-
gure 1.
Definition 5. (κ-DHDHE Assumption) The κ-
DHDHE assumption is that Adv
κ−DHDHE
B
(η) is at
most negligible for all PPT algorithms B.
2.2 Hybrid Coloring
A Hybrid Coloring of the user population, introduced
by (Kiayias and Yung, 2001), is a partition of the total
Cost-effective Private Linear Key Agreement with Adaptive CCA Security from Prime Order Multilinear Maps and Tracing Traitors
359

number of users [N] in a broadcast encryption (BE)
system. A random ciphertext C
R
induces a Hybrid
Coloring over [N] as follows.
• Let D be a pirate decoder (PD) box. We de-
fine an equivalence relation over the user secret
key space as follows: ∀ u, u
0
∈ [N], pk
u
≡ pk
u
0
iff
Pr
D(1
η
,pk
u
,C
R
) 6= D(1
η
,pk
u
0
,C
R
)
≤ε, where ε is
a negligible quantity and pk
u
and pk
u
0
are the secret
key of u and u
0
respectively.
• Assume that C
m
be a ciphertext corresponding to
a valid message m. Then, with overwhelming high
probability D(1
η
,pk
u
,C
m
) = D(1
η
,pk
u
,C
m
) for all
u,u
0
∈ [N]. In that case, we get a unique equivalence
class. Consequently, all the users will get the same
color. Let Ciphr
R
be the set of all random ciphertexts
such that for all C
0
∈Ciphr
R
, C
0
induces a unique equi-
valence class. Then, the set of all valid ciphertexts
constitute a subset of Ciphr
R
.
• A BE scheme induces a Hybrid Coloring if there
exist an algorithm that produces a ciphertext C such
that C induces a partition over the user population.
One important observation regarding the tracing
algorithm of (Kiayias and Yung, 2001) is formally sta-
ted by the following lemma.
Lemma 1. (Kiayias and Yung, 2001) The tracing
procedure using the Hybrid Coloring has time com-
plexity O(N
3
log
2
N) and identify a traitor with high
probability.
3 OUR PLKA TRACING SCHEME
Our PLKA consists of three randomized algorithms
PLKA.Setup, PLKA.Enc, PLKA.Dec and an external
tracing algorithm PLKA.Trace
D
which are described
below.
• (plparams,(plsk
1
,...,plsk
N
)) ← PLKA.Setup(η,κ):
The group manager (GM) takes as input the length
κ of the identities along with the security parame-
ter η and proceeds as follows. The identity space is
I D = {0, 1}
κ
\{0
κ
} and the total number of users the
system can allow is N = (2
κ
−1).
(i) The GM first constructs
~
ρ = (1, . . . , 1), a (κ +
1)-length vector with all 1’s, and runs the setup algo-
rithm aM M .Setup(1
η
,2
~
ρ) for the multilinear map
described in section 2.1 to generate the public para-
meter aPPM = (κ, g
~e
0
,.. . , g
~e
κ
) where g
~e
i
is the ca-
nonical generator of the i-th source group G
~e
i
for
0 ≤ i ≤ κ and G
2
~
ρ
is the target group. All the groups
have the same large prime order p > 2
η
. It genera-
tes the canonical generators g
~
ρ
and g
2
~
ρ
of the groups
G
~
ρ
and G
2
~
ρ
respectively by the repeated multilinear
pairing operations using aPPM.
(ii) Two GGM tree (Goldreich et al., 1986) based
secure pseudorandom functions PRF
rand
: {0, 1}
2η
→
{0,.. . , N} and PRF
auth
: {0, 1}
2η
×[N] →{0,1}
η
are
selected by the GM where rand, auth are keys rand-
omly chosen from the key space K = {0,1}
η
. It also
picks PRG : {0, 1}
η
→ {0, 1}
2η
, the length doubling
pseudorandom generator (Blum and Micali, 1984).
(iii) The GM chooses ξ, τ ∈
R
Z
p
, sets the pro-
grams PT
Enc
(Figure 2), PT
Dec
(Figure 3) and
obfuscate these to generate obfuscated programs
f
PT
Enc
= iO(PT
Enc
),
f
PT
Dec
= iO(PT
Dec
) respecti-
vely using a secure indistinguishability obfuscator iO.
The program PT
Enc
( j ∈ [N],t ∈ Z
p
,s ∈ {0, 1}
η
) has
(PRF
rand
,PRF
auth
,(ξ, τ), κ, g
~
ρ
,g
2
~
ρ
) hard-coded in it
and runs on input j,t, s to generate a header-session
key pair (Hdr = (r ∈{0,1}
2η
, C
1
∈[N], C
2
∈{0, 1}
η
,
C
3
∈ G
~
ρ
, C
4
∈ G
~
ρ
), K
PLKA
= (g
2
~
ρ
)
tξ
2
κ
).
Inputs: j ∈ [N], t ∈ Z
p
, s ∈{0, 1}
η
Constants: PRF
rand
, PRF
auth
, (ξ,τ), κ, g
~
ρ
, g
2
~
ρ
1. Compute:
(a) r = PRG(s)
(b) C
1
= (PRF
rand
(r) + j) mod (N + 1)
(c) C
2
= PRF
auth
(r,C
1
)
(d) C
3
= (g
~
ρ
)
t
and C
4
= (g
~
ρ
)
t
(
τ+
j
∑
i=1
ξ
2
κ
−i
)
2. Set: K
PLKA
= (g
2
~
ρ
)
tξ
2
κ
3. Output: (Hdr = (r,C
1
,C
2
,C
3
,C
4
),K
PLKA
)
Figure 2: The program PT
Enc
.
On the other hand, the program PT
Dec
(Hdr, u ∈ [N],
plsk
u
∈ G
~
ρ
) has PRF
rand
,PRF
auth
,(ξ,τ),κ, g
~
ρ
,g
2
~
ρ
hard-coded in it and runs on inputs Hdr, u, plsk
u
to
generate the correct session key K
PLKA
. The obfus-
cated programs
f
PT
Enc
and
f
PT
Dec
behave in a simi-
lar manner as PT
Enc
and PT
Dec
respectively. That
is, on the same input, PT
Enc
and
f
PT
Enc
generate the
same output. Similarly, PT
Dec
and
f
PT
Dec
provide
the same output on the same input. Note that in step
1(b) of PT
Enc
, from the GGM tree based construction
PRF
rand
(r) is an η-bit string which is converted to
an integer and added to j modulo (N + 1) to gene-
rate header component C
2
. Similarly, in step 1(a) of
PT
Dec
, to recover j from the header component C
1
we
consider the integer representation of the η-bit string
PRF
rand
(r).
(iv) The GM finally publishes the private li-
near public parameter plparams= (PRF
rand
, PRF
auth
,
SECRYPT 2018 - International Conference on Security and Cryptography
360
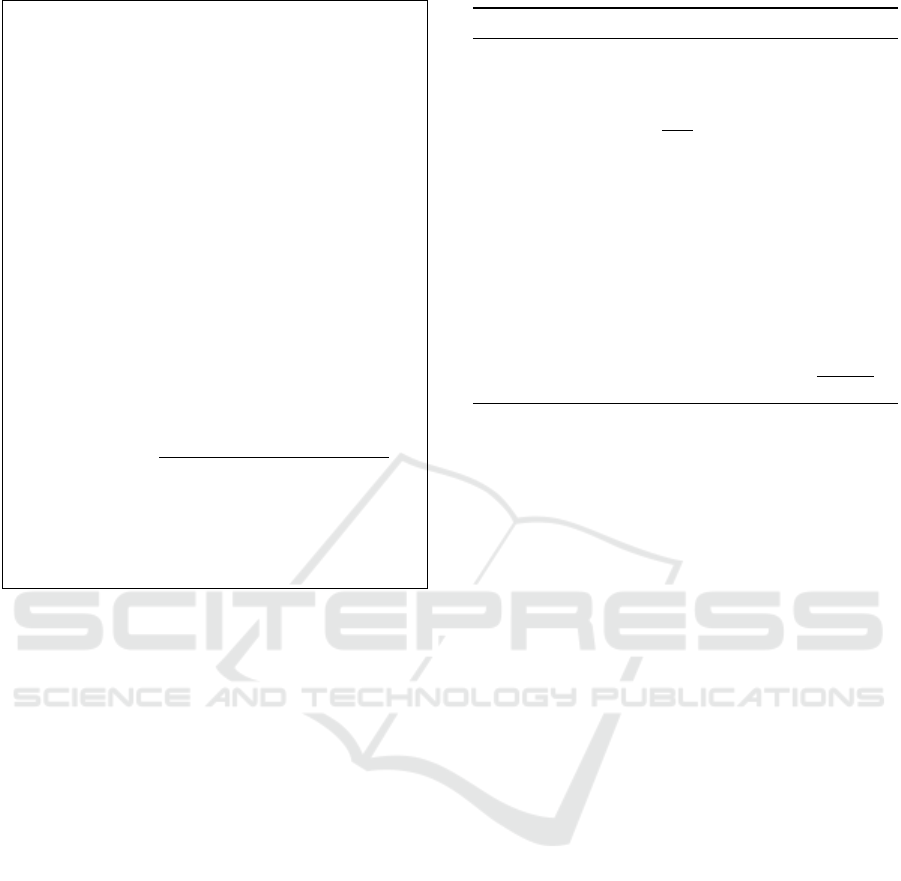
Inputs: Hdr =(r ∈ {0, 1}
2η
, C
1
∈ [N],
C
2
∈ {0,1}
η
, C
3
∈ G
~
ρ
, C
4
∈ G
~
ρ
), u ∈ [N],
plsk
u
∈ G
~
ρ
Constants: PRF
rand
, PRF
auth
, (ξ,τ), κ, g
~
ρ
, g
2
~
ρ
1. Compute:
(a) j = (C
1
−PRF
rand
(r)) mod (N + 1)
(b) x = PRG(PRF
auth
(r,C
1
))
(c) y = (g
~
ρ
)
τξ
u
2. Check that (u ≤ j) ∧ (x = PRG(C
2
)) ∧
(y = plsk
u
)
(a) If check fails, output ⊥ and stop
(b) Otherwise, compute:
i. Λ
2
κ
−i+u
= (g
~
ρ
)
ξ
2
κ
−i+u
for all i ∈ [ j], i 6= u
and Λ
u
= (g
~
ρ
)
ξ
u
ii. K
PLKA
=
e(Λ
u
,C
4
)
e
(plsk
u
·
j
∏
i=1
i6=u
Λ
2
κ
−i+u
),C
3
3. Output: K
PLKA
Figure 3: The program PT
Dec
.
PRG,
f
PT
Enc
,
f
PT
Dec
). For each user u ∈ [N], it com-
putes the user secret key plsk
u
= (g
~
ρ
)
τξ
u
and sends
plsk
u
to user u through a secure communication chan-
nel between the GM and the user u.
• (Hdr, K
PLKA
) ←PLKA.Enc(plparams, j ∈[N]): On
input an integer j ∈ [N] and the public parameter
plparams, the encryptor executes the following steps.
(i) It chooses elements t ∈
R
Z
p
and s ∈
R
{0,1}
η
.
(ii) It generates (Hdr = (r,C
1
,C
2
,C
3
,C
4
),K
PLKA
)
by running the program
f
PT
Enc
, extracted from
plparams, on input ( j ∈ [N], t ∈ Z
p
, s ∈ {0, 1}
η
),
where Hdr = (r,C
1
,C
2
,C
3
,C
4
) is the ciphertext hea-
der and K
PLKA
is the session key for all the users in
the set [ j].
(iii) Finally, it publishes Hdr as the ciphertext and
keeps K
PLKA
as secret to itself.
•(K
PLKA
∨⊥) ← PLKA.Dec(plparams,u ∈
[N], plsk
u
,Hdr = (r,C
1
,C
2
,C
3
,C
4
)): A user u ∈ [N]
uses secret key plsk
u
= (g
~
ρ
)
τξ
u
to recover the
session key K
PLKA
from the ciphertext header
Hdr = (r,C
1
,C
2
,C
3
,C
4
) as follows.
(i) It runs the program
f
PT
Dec
, extracted from
plparams, on input (Hdr = (r,C
1
,C
2
,C
3
,C
4
),u,plsk
u
).
(ii) If it passes all the checking conditions in step
2 of the program
f
PT
Dec
= iO(PT
Dec
) in Figure 3, it
Algorithm 1: Traitor tracing program Trace
D
.
1: Input: plparams, ε
2: for i = 0 to N do
3: success ← 0
4: for j = 1 to 2
logN
ε
2
do
5: (Hdr
(i)
,K
(i)
PLKA
)←PLKA.Enc(plparams, i)
6: K
(i
0
)
PLKA
← D(Hdr
(i)
)
7: if K
(i)
PLKA
= K
(i
0
)
PLKA
then
8: success ← success + 1
9: end if
10: end for
11: Y
obsrv
i
← success
12: end for
13: return T
TTS
=
n
i : Y
obsrv
i
−Y
obsrv
i−1
≥
4(logN)
2
ε
o
gets the correct key K
PLKA
as the output; otherwise
gets ⊥.
• T
TTS
←PLKA.Trace
D
(plparams,ε): The tracer ta-
kes as input the public parameter plparams, a para-
meter ε which is polynomially related to the security
parameter η. It runs the Trace
D
program of Algo-
rithm 1, on input the public parameter plparams and
the parameter ε. It outputs the set of users T
TTS
⊆
{1,.. . , N} as the traitor users.
Correctness and the proof of our tracing algorithm is
shown in the Theorem 2.
Correctness. Let, u, j ∈[N] and 1 ≤u ≤ j≤ N. Let,
(plparams,(plsk
1
,...,plsk
N
))←PLKA.Setup(η,κ),
where plparams= (PRF
rand
,PRF
auth
,PRG,
f
PT
Enc
,
f
PT
Dec
) and plsk
u
= (g
~
ρ
)
τξ
u
. Let (Hdr,K
PLKA
=
(g
2
~
ρ
)
tξ
2
κ
) ← PLKA.Enc(plparams, j ∈ [N]), where
Hdr = (r,C
1
,C
2
,C
3
,C
4
) with
C
1
= (PRF
rand
(r) + j) mod (N + 1), C
3
= (g
~
ρ
)
t
,
C
2
= PRF
auth
(r,C
1
), C
4
= (g
~
ρ
)
t
(
τ+
j
∑
i=1
ξ
2
κ
−i
)
.
A user u, with its secret key plsk
u
= (g
~
ρ
)
τξ
u
runs
PLKA.Dec(plparams,u,plsk
u
,Hdr). If u passes all
the conditions in step 2 of the program in Figure 3
in executing the program
f
PT
Dec
in plparams, then we
show below that u can recover the correct session key
K
PLKA
= (g
2
~
ρ
)
tξ
2
κ
by extracting C
3
and C
4
from Hdr
and proceeding as follows.
As, Λ
2
κ
−i+u
= (g
~
ρ
)
ξ
2
κ
−i+u
and Λ
u
= (g
~
ρ
)
ξ
u
are gi-
Cost-effective Private Linear Key Agreement with Adaptive CCA Security from Prime Order Multilinear Maps and Tracing Traitors
361
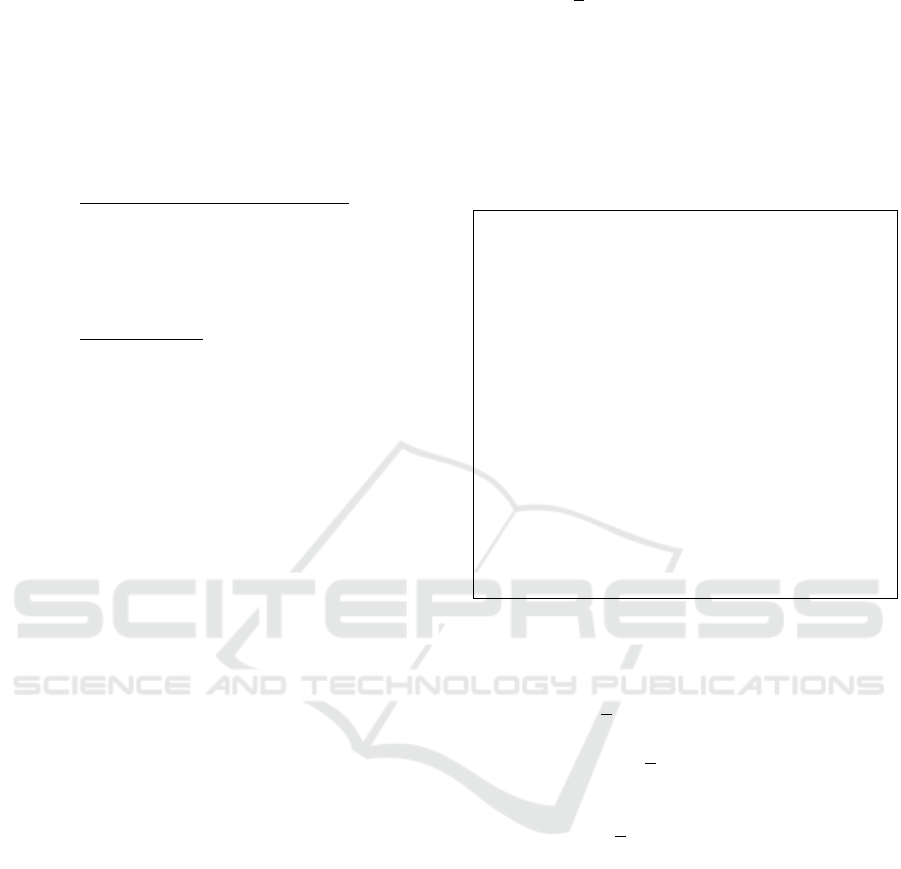
ven in PT
Dec
, we have
e(Λ
u
,C
4
)
,
e
plsk
u
·
j
∏
i=1
i6=u
Λ
2
κ
−i+u
,C
3
=
e
(g
~
ρ
)
ξ
u
,(g
~
ρ
)
t
(
τ+
j
∑
i=1
ξ
2
κ
−i
)
e
(g
~
ρ
)
τξ
u
·
j
∏
i=1
i6=u
(g
~
ρ
)
ξ
2
κ
−i+u
,(g
~
ρ
)
t
=
(g
2
~
ρ
)
ξ
u
t
j
∑
i=1
ξ
2
κ
−i
(g
2
~
ρ
)
t
j
∑
i=1
i6=u
ξ
2
κ
−i+u
= (g
2
~
ρ
)
tξ
2
κ
= K
PLKA
Remark 1. As the set system S = {[1], . . . , [N]} has
only a polynomial number of recipient sets in it, ac-
cording to (Boneh and Zhandry, 2014), the selective
and the adaptive security are equivalent.
4 SECURITY ANALYSIS
Theorem 1. (Security of Indistinguishability) As-
suming secure iO, our PLKA scheme, presented in
section 3, achieves adaptive CCA-security under the
κ-DHDHE assumption.
Proof. Due to limited space, proof is available in the
full version (Mandal and Dutta, 2018).
Theorem 2. (Security of Traceability) Suppose
that our PLKA scheme, presented in section 3, is
adaptive CCA-secure. Then, the publicly traceable
PLKA.Trace
D
algorithm outputs identity of all the
traitors.
Proof. Assume that at the beginning the adversary A
outputs a pirate decoder box D. For i = 0, . . . , N con-
struct the experiment TrExp
i
of Figure 4 using the Hy-
brid Coloring mechanism shown in section 2.2. Let
p
i
= Pr[H
i
= success] be the success probability in
the above experiment TrExp
i
for i = 0,. . . , N. Clearly,
p
0
= 0, whereas p
N
= 1 and hence |p
N
−p
0
| = 1.
Consider that user j ∈ [N] is not a traitor user.
Then, the secret key plsk
j
of user j is not embedded
into the pirate decoder box D. Note that if plsk
k
is
embedded into D for some k < j, then H
j
= H
k
=
success and consequently |p
j
− p
k
| = 0. On the ot-
her hand, if j ∈ [N] is the least positive integer such
that plsk
j
is embedded into D, then H
j
= success
but H
k
= failure for 1 ≤ k ≤ j −1. In this case,
|p
j
− p
k
| ≥
1
N
. However, the adversary A, who has
formed the pirate decoder box D, can not distinguish
the ciphertext headers Hdr
( j)
and Hdr
( j−1)
without
having the knowledge of plsk
j
, even if A has the se-
cret key plsk
k
for 1 ≤ k ≤ j −1. As a result, the
difference between the success probability in the ex-
periment TrExp
j−1
and in the experiment TrExp
j
is
negligible in the total number of user N. Therefore,
|p
j−1
−p
j
| is negligible in N.
(i) The tracer generates header-session key
pair (Hdr
(i)
,K
PLKA
(i)
)←PLKA.Enc(plparams,i),
where plparams is the public parameter genera-
ted using PLKA.Setup algorithm of our PLKA
scheme.
(ii) Then, tracer interacts with the pirate decoder
D, giving Hdr
(i)
as an input to D, and in return
tracer will get K
(i
0
)
PLKA
←D(Hdr
(i)
). Here, D acts
as a black-box oracle for this interaction.
(iii) Finally, tracer sets the success or failure H
i
as follows
H
i
=
(
success if K
PLKA
(i)
= K
(i
0
)
PLKA
failure otherwise
Figure 4: Tracing Experiment TrExp
i
for i = 0, . . ., N.
Since |p
N
− p
0
| = 1, by the triangular inequality
there must exists at least one user i
t
∈ [N] such that
|p
i
t
− p
i
t
−1
| ≥
1
N
. So that the success probability
difference between the two experiments TrExp
i
t
and
TrExp
i
t
−1
is at least
1
N
which is non-negligible. Let
the advantage of breaking the indistinguishability se-
curity of our PLKA scheme is ε = Adv
CCA−PLKA
A
(η).
If |p
i
t
− p
i
t
−1
| ≥
1
N
≥ ε, then this indicate that plsk
i
t
is embedded into D with probability at least ε and
hence the user i
t
must be a traitor. Observe that user
i
t
−1 can not be a traitor. If both i
t
and i
t
−1 are trai-
tors, then H
i
t
= success as well as H
i
t
−1
= success,
as D having plsk
i
t
−1
can return correct session keys
corresponding to both Hdr
(i
t
)
and Hdr
(i
t
−1)
. Note that
D can decrypt the ciphertext header Hdr
( j)
for any
j > i
t
−1 if plsk
i
t
−1
is embedded in D.
To ensure perfectly that the user i
t
is a traitor user,
one has to to repeat the experiment TrExp
i
t
more than
a single time. Consider that for each i = 0,. . . , N, the
tracer repeats the experiment TrExp
i
independently up
to ℜ trials. We define a random variable Y
i
as total
number of success that were returned by D during ℜ
trials of the experiment TrExp
i
. If i
t
is a traitor user,
then for one trial |p
i
t
− p
i
t
−1
| ≥ ε. Therefore, for ℜ
trials the expected difference between the random va-
SECRYPT 2018 - International Conference on Security and Cryptography
362

riable Y
i
t
and Y
i
t
−1
is at least εℜ. To perfectly ens-
ure that the user i
t
is a traitor user, we have to make
sure that the observed values of the random variables
Y
k
, denoted by Y
obsrv
k
, is sufficiently closed to their
expected values µ
k
= p
k
ℜ for k = i
t
,i
t
−1. Using
the Chernoff bound, we obtain the following relation
between Y
obsrv
k
and its expected value µ
k
= p
k
ℜ for
k = i
t
,i
t
−1, taking δ =
1
2
, and setting a =
εℜ
2
:
Pr
|Y
obsrv
k
−µ
k
| ≥
εℜ
2
≤ 2(e)
−ε
2
ℜ
2
= 2(N
1
logN
)
−ε
2
ℜ
2
≤ 2N
−log N
if ℜ ≥ 2(
logN
ε
)
2
. Observe that this probability is neg-
ligible in N using the Definition 1, as log N is an po-
sitive function.
Again from the Chernoff bound, we can write
µ
k
−
εℜ
2
≥Y
obsrv
k
≥µ
k
+
εℜ
2
. Hence, Y
obsrv
k
≥µ
k
+
εℜ
2
and −Y
obsrv
k
≥ −µ
k
+
εℜ
2
. If i
t
is a traitor, then for i
t
and i
t
−1, the difference between two observed values
Y
obsrv
i
t
and Y
obsrv
i
t
−1
(repeat each up to ℜ times) is given
by
(Y
obsrv
i
t
−Y
obsrv
i
t
−1
) ≥µ
i
t
+
εℜ
2
−µ
i
t
−1
+
εℜ
2
≥ εℜ + (µ
i
t
−µ
i
t
−1
) ≥εℜ + (p
i
t
−p
i
t
−1
)ℜ ≥2εℜ
Hence, for the traitor user i
t
, the difference bet-
ween Y
obsrv
i
t
and Y
obsrv
i
t
−1
is at least 2εℜ, where ℜ ≥
2(
logN
ε
)
2
. The complete tracing mechanism is given
in Algorithm 1.
5 CONCLUSION
In this work, we have designed an adaptively CCA-
secure PLKA traitor tracing scheme, under the prime
order multilinear group setting, which is fully col-
lusion resistance and publicly traceable. Our con-
struction is proven to be secure under the hardness
of standard DHDHE-assumption. More precisely, our
design significantly reduces the parameter sizes and
the tracing time which are so far a plausible impro-
vement in the literature.
REFERENCES
Blum, M. and Micali, S. (1984). How to generate cryp-
tographically strong sequences of pseudorandom bits.
SIAM journal on Computing, 13(4):850–864.
Boneh, D., Sahai, A., and Waters, B. (2006). Fully collusion
resistant traitor tracing with short ciphertexts and pri-
vate keys. In Advances in Cryptology-EUROCRYPT
2006, pages 573–592. Springer.
Boneh, D. and Waters, B. (2006). A fully collusion resistant
broadcast, trace, and revoke system. In Proceedings of
the 13th ACM CCS, pages 211–220. ACM.
Boneh, D. and Waters, B. (2013). Constrained pseudo-
random functions and their applications. In Interna-
tional Conference on the Theory and Application of
Cryptology and Information Security, pages 280–300.
Springer.
Boneh, D., Waters, B., and Zhandry, M. (2014). Low over-
head broadcast encryption from multilinear maps. In
Advances in Cryptology–CRYPTO 2014, pages 206–
223. Springer.
Boneh, D. and Zhandry, M. (2014). Multiparty key
exchange, efficient traitor tracing, and more from
indistinguishability obfuscation. In Advances in
Cryptology–CRYPTO 2014, pages 480–499. Springer.
Chor, B., Fiat, A., and Naor, M. (1994). Tracing traitors.
In Annual International Cryptology Conference, pa-
ges 257–270. Springer.
Coron, J.-S., Lepoint, T., and Tibouchi, M. (2015). New
multilinear maps over the integers. In Advances in
Cryptology–CRYPTO 2015, pages 267–286. Springer.
Garg, S., Gentry, C., Halevi, S., and Zhandry, M. (2016).
Functional encryption without obfuscation. In TCC,
pages 480–511. Springer.
Garg, S., Kumarasubramanian, A., Sahai, A., and Waters,
B. (2010). Building efficient fully collusion-resilient
traitor tracing and revocation schemes. In Proceedings
of the 17th ACM CCS, pages 121–130. ACM.
Gentry, C., Gorbunov, S., and Halevi, S. (2015). Graph-
induced multilinear maps from lattices. In TCC, pages
498–527. Springer.
Goldreich, O., Goldwasser, S., and Micali, S. (1986). How
to construct random functions. Journal of the ACM
(JACM), 33(4):792–807.
Gu, C. (2015). An improved multilinear map and its appli-
cations. International Journal of Information Techno-
logy and Web Engineering (IJITWE), 10(3):64–81.
Kiayias, A. and Yung, M. (2001). On crafty pirates and
foxy tracers. In Security and Privacy in Digital Rights
Management, pages 22–39. Springer.
Kitagawa, F., Nishimaki, R., and Tanaka, K. (2018).
Obfustopia built on secret-key functional encryption.
EUROCRYPT 2018.
Mandal, M. and Dutta, R. (2018). Cost-effective pri-
vate linear key agreement with adaptive CCA security
from prime order multilinear maps and tracing trai-
tors. Cryptology ePrint Archive, Report 2018/508.
https://eprint.iacr.org/2018/508.
Nishimaki, R., Wichs, D., and Zhandry, M. (2016). Anony-
mous traitor tracing: How to embed arbitrary informa-
tion in a key. In Annual International Conference on
the Theory and Applications of Cryptographic Techni-
ques, pages 388–419. Springer.
Cost-effective Private Linear Key Agreement with Adaptive CCA Security from Prime Order Multilinear Maps and Tracing Traitors
363
