
A Newly Emerging Ethical Problem in PGIS
Ubiquitous Atoque Absconditus and Casual Offenders for Pleasure
Koshiro Susuki
Faculty of Humanities, University of Toyama, 3190 Gofuku, Toyama, Japan
Keywords: Ubiquitous Mapping, Absconditus, PGIS, Geographic Information Ethics, Cyberbullying, Casual Offenders
for Pleasure.
Abstract: Thanks to the recent technological advances of cellular phones, the practical realization of GeoAPI and SNS,
and the consolidation of wireless LAN networks, hardware has become capable of providing portable high-
speed Internet access and interactive SNS, and people can now easily communicate far more, casually and
unboundedly, via the Internet. Currently, PGIS studies mainly look at the ‘sunny side’ of GIT progress.
Although there are also relevant studies on online ethics, they rely unduly on spontaneously arising
equilibrium innervated by mutual surveillance among the people involved. However, it is an over-optimistic
and ingenuous perception regarding this exponential technological advance. In this paper, the author
illustrates the existence of ‘casual offenders for pleasure’ by referring to two recent online cyberbullying
incidents. Because the appreciation of technology-aided ubiquitous mapping can be very hard to see or to
grasp, especially for people not educated and trained to see it, the advances prompt people to nonchalantly
lower technical and ethical barriers. Further studies are essential to establish the geographic information
ethics and offer a clear-cut answer for this newly emerging problem.
1 INTRODUCTION
On 6 November 2012, a murder occurred in Zushi
City, Kanagawa Prefecture, Japan. Although the
victim had secretly relocated to an apartment at that
time to escape from the criminal’s repeated stalking,
the 40-year-old criminal somehow found the
apartment into which his ex-lover had moved,
invaded it, and stabbed her to death before hanging
himself. It is commonly called the ‘Zushi stalker
murder case’.
According to The Japanese Metropolitan Police
Department, the numbers of stalkers recognized in
2013 was the highest number, 21,089, of which 15
resulted in incidences, including the Zushi case.
Among them, there is a reason why the Zushi
incident has been given particular attention.
Immediately after the incident, there emerged the
suspicion that the criminal had prepared for the
crime using a major portal online Q & A bulletin
board for more than one year before committing the
crime. An anonymous suspect who had uploaded the
questions one after another disappeared from the
web after the incident, leaving only a series of
questions. The remaining writing still vividly
conveys how the person gradually obtained the
knowledge related to the incident while keeping the
murderer’s aim secret, such as: how to figure out an
address from a phone number, how to analyse Exif
metadata from a photo, how to uncover a locked
private account on Facebook, how to request a
professional detective search, how to purchase
weapons, and how to move to a site in Zushi.
This case symbolically presents an emerging
ethics agenda for Geographic Information Science,
or GIScience. Although it foretold of the potential
threat of the trend in Geospatial Information
Technology (GIT), for GIT-aided ubiquitous
mapping and cartography (Morita, 2003;
Reichenbacher, 2007; Gartner et al., 2007), for the
next five years on, little attention was paid to the
implication of such a technology-aided incident. In
this paper, the author critically summarizes existing
debates in relevant fields to clarify what was
overlooked and what should be considered.
2 THE RISE OF PGIS AND
INTERNET PRIVACY
Since the 1990s, the possibilities of geospatial
analysis in conjunction with GIS have dramatically
22
Susuki, K.
A Newly Emerging Ethical Problem in PGIS.
DOI: 10.5220/0006640100220027
In Proceedings of the 4th International Conference on Geographical Information Systems Theory, Applications and Management (GISTAM 2018), pages 22-27
ISBN: 978-989-758-294-3
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

increased in the context of consolidation of
geostatistical data, high precision of GPS,
improvement of PC processing capability, and
speeding up of LAN access. Geographers gradually
became aware of the magnitude of the social impacts
of GISystem. GISystem became capable of
analysing and outputting even personal level data
(Miller, 2007). GIT innovation has increased the
necessity of dealing with GIS from an
interdisciplinary science perspective, examining the
consequential social influence of the innovation as
well as the functionality of the system itself. This
has become GIScience.
Since the middle of the 2000s, this situation has
dramatically changed even further. Thanks to the
consolidation of wireless LAN networks, such as
Wi-Fi, which was initially established in 2000,
hardware became capable of providing portable
high-speed Internet access. Moreover, interactive
web services such as Mixi, Facebook, Twitter,
posting bulletin boards, Flickr, etc. were launched
one after another over the course of the decade. As a
result, communication between people far more
casually and unboundedly via the Internet, or so-
called Web 2.0, became a sudden reality. Likewise,
in the case of GIT, when map integration technology
(GeoAPI) was put into practical use on the web,
Google began to provide Street View and Google
Earth continuously in 2006-2007. From then on,
everyone could freely geo-tag and share photos and
texts on the web maps.
One of the most positive aspects stemming
from these technological innovations is the rise of
the Participatory Geographic Information Systems,
PGIS. The evolution has prompted public citizens
who were simply receivers of geographic
information to become senders, sharers, and
communicators of geographic information with use
of Social Networking Services (SNS) and online
mapping devices (Turner, 2006; Crampton, 2010).
Sometimes such grass-roots mappers voluntarily
participate in regional policy planning and local
governance, called Volunteered geographic
information (VGI) (Goodchild, 2007), or bottom-up
GIS in Talen’s (2000) nomenclature. Moreover,
such mappers can utilize GIT in the post-disaster
construction and damage repair process by simply
digitizing satellite imagery of the afflicted areas on
OpenStreetMap to help find ways around severed
roads (Norheim-Hagtun and Meier, 2010).
Cartographers generally interpret the phenomenon
positively, as a people-powered, net-rooted,
undisciplined, alternative and Dionysiac way of
mapping (Crampton, 2010; Kingsbury and Jones,
2009).
On the other hand, it became apparent that there
are potential threats stemming from this advance.
boyd and Ellison’s (2007) review of studies dealt
with online-inherent privacy issues and summarized
these as (1) damaged reputation due to rumors and
gossip; (2) unwanted contact and harassment or
stalking; (3) surveillance-like structures due to
backtracking functions; (4) use of personal data by
third-parties; and (5) hacking and identity theft
(Debatin et al. 2009). Previous studies on SNS
privacy issues mainly focused on ethical questions
involving the remote monitoring of users conducted
by the service provider. Above all, the invasion of
privacy and surveillance of geographic space as an
exercise of public power are subjects of considerable
discussion in GIScience (Armstrong, 2002).
Although the discussion about ubiquitous mapping
is still limited, some scholars coined the term
‘geosurveillance’ (Crampton, 2003) to enable
critical discussion about the potential risks of
privacy infringement through aggregation of users'
attributes and location information collected by
public authority and SNS providers. Although the
development of Information and Communications
Technology (ICT) permits people to share
geographic information in a friendlier manner, users
remain under scrutiny more tightly because of the
geosurveillance (Monmonier, 2002). Dobson and
Fisher (2003) defined the term ‘geoslavery’ as ‘a
practice in which one entity, the master, coercively
or surreptitiously monitors and exerts control over
the physical location of another individual, the slave’
(p. 48). Many scholars metaphorically refer to the
‘big brother’ motif in George Orwell’s famous novel
1984 to describe the power and position of a master
(e.g. Klinkenberg, 2007; Propen, 2005), and
Bentham’s panopticon for the systems and
techniques of monitoring (Dobson and Fisher 2007;
Koskela, 2002). Although many studies have been
extremely conscious of the potential risks of
geosurveillance by public powers, their discussions
regarding privacy infringement at individual levels
lack diversity.
There are many empirical studies on individual
offenders and victims via SNS. For instance, Gross
and Acquisti (2005), one of the classic empirical
studies on SNS profiles, found 89% of users used
their real names on their Facebook profiles, and 61%
used identifiable information in their posts. Jones
and Soltren (2005) found that 62% of student users
did not configure any privacy setting despite the fact
74% of them knew about Facebook privacy options.
A Newly Emerging Ethical Problem in PGIS
23
They also pointed out that 70% of Facebook users
posted personal information. In other words, they
could not defend their privacy effectively although
they cared about its leakage, in what Barnes (2006)
termed the ‘privacy paradox’. Some other studies
found another rationale: that the tendency to
inadequately protect one’s private information was
the consequence of exhibitionistic motives (McGrath,
2004; Ong et al., 2011). These studies demonstrate
how potential victims are vulnerable and undefended
against anonymous third party offenders on the
Internet, but they do not tell much about the
offenders. Little has been studied regarding the
offenders, except the cyberbullying and
cyberstalking studies that mostly focused on
adolescent students in a criminological context
(Smith et al., 2008; Wolak et al., 2008).
In sum, previous online privacy studies in
GIScience can be summarized as emphasizing the
risks of privacy infringement by public power or
criminological studies through SNS. However, in the
Web 2.0 era, the panoptic one-to-many relationship
becomes the many-surveilling-the-many situation of
what Shilton (2009) described as little brothers and
Rose-Redwood (2006) termed as omnopticon. In
such views, the progress of PGIS may encompass
the participatory panopticon and total loss of privacy
(Whitaker, 1999). Kawaguchi and Kawaguchi
(2012) rephrased the omnopticon as ‘paradoxical
others’ to describe the feeling of discomfort upon
being disclosed on Google Street View.
Liberally interpreted, these views suggest that
an omnoptic mutual surveillance environment
restrains and intermediates the people from deviant
behaviours as a sort of unseen hand of God. But why
do we rule out plausible alternatives?
In this paper, the author brings up two cases for
examining the possibilities not yet discussed in the
preceding contributions: the existence of casual
offenders for pleasure.
Before the Web 2.0 era, most of the people who
could create and manage maps were knowledgeable
experts who generally had educated and internalized
codes of professional ethics. However, in the
ubiquitous mapping circumstance, people can
participate in mapping behaviour far more casually
without being aware that they are in a position of
power to create geographic information, without
knowledge of cartography or ethics. Thus, the
premise that the net-rooted, undisciplined,
alternative and Dionysiac people do what experts
expect of them no longer applies.
3 CASES OF THE CASUAL
OFFENDERS FOR PLEASURE
3.1 Individual Online Peepers
On 20 February 2015, there was a case of murder in
Kanagawa prefecture, Japan. The then-13-year-old
victim had tried to withdraw from the perpetrators’
circle, and was found bound and stabbed to death by
the three juvenile criminals. The case received much
media coverage because of the atrociousness of the
crime that can hardly be attributed to their age.
However, this case became especially
memorable not only because of the savagery, but
also in the context of the present paper. The then-15-
year old podcaster, whose handle name was Noeru
(Noël), somehow located and found the chief
culprit’s family’s house and webcasted it across the
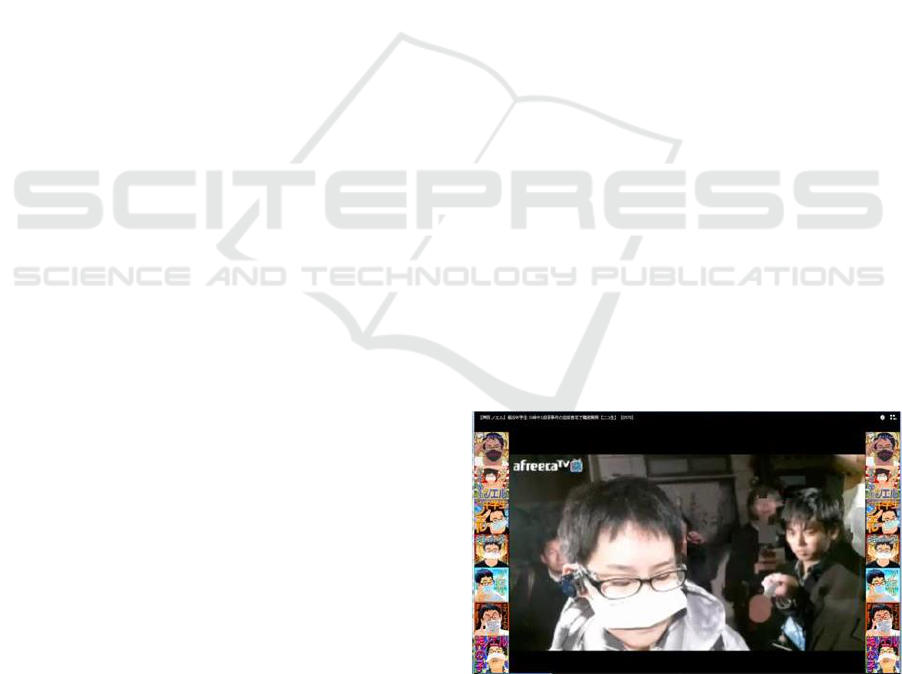
globe. Figure 1 is a screenshot of the delivered
movie (now deleted) showing a symbolic
composition of a journalist holding out a
microphone to a nameless boy as seen from his
behind. The figure demonstrates that even a boy
goes toe-to-toe with professional media in terms of
competence for information transmission. Needless
to say, Noeru (and other mappers) could determine a
location by simply specifying aggregated place
names and utilizing Google Street View to find the
same exterior appearance of the home broadcasted
by the mass media to detect the exact target location
(termed ‘dataveillance’ by Clarke, 1988). Why
would the non-involved boy do this? It is
ratiocinative to consider his aspiring to fame and
increased advertisement revenue, even if he becomes
seen as an online ‘weirdo’.
Figure 1: A screenshot of the podcasted movie
(http://www.afreecatv.jp/noeru) *now deleted.
GISTAM 2018 - 4th International Conference on Geographical Information Systems Theory, Applications and Management
24
3.2 Private Sanctions and Collective
Droves
On 15 May 2012 in Hachioji, Tokyo, an elementary
school child was on his way home from school.
Suddenly, two junior high school students
surrounded him, while making a visual recording
with a cell phone. The two adolescents found a
pretext for quarrelling with the boy, causing him to
move backward and whimper in fear. The
adolescents then uploaded the movie file on one of
the adolescent’s YouTube account for kicks
(Yomiuri Online, 21 July 2017).
Immediately after the upload, the URL was
disseminated on the Internet by SNS, and appeared
on the famous online bulletin board 2channel with
fusillade of accusations. An anonymous person
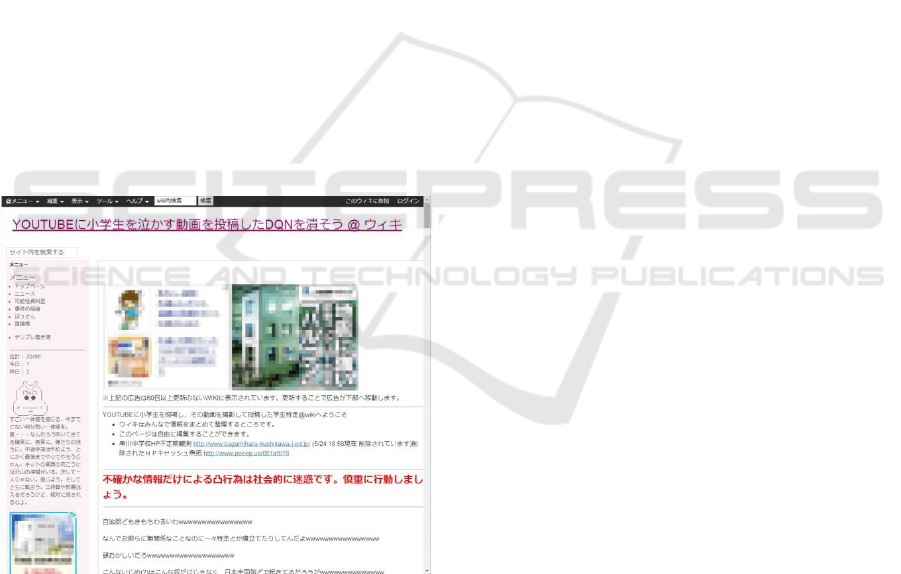
promptly created a portal site with using @wiki, a
free rental wiki maintained by a limited liability
company, Atfreaks (Figure 2). The website served as
a ‘traffic cop’, directing thousands of seekers to the
appropriate information. As the sub-domain name
/dqntokutei/ eloquently shows, the creator of the
domain cared less about right or wrong but rather to
tokutei (identify) the dqn (an argot for ‘homeboys’)
who deserved to be sanctioned.
Figure 2: The top page screenshot of the promptly created
wiki (https://www34.atwiki.jp/dqntokutei/).
Subsequently, thousands of Internet users
(mainly consisting of 2channel viewers) voluntarily
began Googling for information about the captured
location, as well as analysing the past uploaded files
on the YouTube account. The power of collective
intelligence was used to pinpoint the filmed location
before long, by scoping out distinctive landmarks
captured in the setting and comparing them with
images on Google Street View. The school uniform
of the perpetrators also revealed the school they
attended. Likewise, some of the amateur
investigators examined the contents of past uploaded
movies and found that the uploaders' faces and their
neighbourhoods were visible in some of the files.
These online droves dataveillanced all information
published online, found two nameless targets, and
privately sanctioned through complaint calls to the
schools and police stations. Five years on from this
initial burst of enthusiasm, the portal site remains on
the Internet, exposing the faces and locations of
involved individuals to the public gaze.
4 CONCLUDING REMARKS
In 1495 A.D., in medieval Germany, Ewiger
Landfriede passed by Maximilian I, German king
and emperor of the Holy Roman Empire, prohibited
Fehde (the duel) as a self-help right to take
vengeance. This was the first time in European
history when a Reichskammergericht, the Supreme
Court, was established in a related move (Jackson,
1994). As this event clearly demonstrates, the
modern concept of law and justice could not be
made possible without consignment of individual
rights of vengeance to the public power. Five
hundred and a few decades on, an overwhelming
innovation in GIT is prompting the resurgence of
this pre-modern principle in a way too modernized
figure.
The recently realized ubiquitous mapping based
on Web 2.0 circumstances is making it an open
possibility for people to create and use geographic
information anywhere and at any time, and without
advanced map-use skills (Gartner et al., 2007).
However, as the meaning of the word illustrates,
ubiquitous stands for being omnipresent, like air,
health, and water, all largely taken for granted.
In Latin, an antonym for ubiquitous is
absconditus, signifying hidden, hard to see or to
grasp (Lewis, 1890). Although air is everywhere, its
existence is largely overlooked because of its
ubiquitous nature. Likewise, in a ubiquitous
mapping situation, its presence becomes very hard to
see or to grasp, especially for people not educated
and trained to ‘see’ it. As the examples in this study
demonstrate, technological advances also enable
people to participate by nonchalantly lowering the
technical, intelligential, and ethical barriers.
For the time being, PGIS studies mainly take a
look at the sunny side of the progress in GIT.
A Newly Emerging Ethical Problem in PGIS
25

Relevant studies on online ethics place undue
reliance on spontaneously arising equilibrium
innervated by mutual surveillance among the people
involved (Rose-Redwood, 2006; Kawaguchi and
Kawaguchi, 2012). However, this view of this
exponential technological advance is over-optimistic
and ingenuous. GIS is only a device and tool. As the
Zushi murder case at the beginning of this article
shows, people can utilize the new technologies both
in good ways and bad. Further studies are clearly
essential to establish geographic information ethics
from a collaboration of relevant fields such as
information ethics, comparative jurisprudence,
geographical education as well as GIScience for
offering a clear-cut answer to this newly emerging
problem.
ACKNOWLEDGEMENTS
This work was supported by JSPS KAKENHI Grant
Number JP17H00839. Some parts of this article are
based on the following conference presentations
conducted by the author: the 63rd Annual
Conference of The Japanese Society for Ethics in
2012, the Kyoto Collegium for Bioethics in 2014,
the conferences of the Association of Japanese
Geographers in 2014 and 2015, and a keynote
speech at Hokuriku Geo-Spatial Forum 2017.
REFERENCES
Armstrong, M.P., 2002. Geographic information
technologies and their potentially erosive effects on
personal privacy. Studies in Social Sciences, 27(1), 19-
28.
Barnes, S.B., 2006. A privacy paradox: Social networking
in the United States. First Monday, 11(9) doi:
http://dx.doi.org/10.5210/fm.v11i9.1394
boyd, d.m., Ellison, N.B., 2007. Social network sites.
Journal of Computer-mediated Communication, 13,
210-230.
Calvert, C., 2004. Voyeur War-The First Amendment,
Privacy & (and) Images from the War on Terrorism.
Fordham Intellectual Property, Media and
Entertainment Law Journal, 15(1), 147-168.
Clarke, R., 1988. Information technology and
dataveillance. Communications of the ACM, 31(5),
498-512.
Crampton, J.W., 2003. Cartographic rationality and the
politics of geosurveillance and security. Cartography
and GIS, 30(2), 135-148.
Crampton, J.W., 2010. Mapping: A Critical Introduction
to Cartography and GIS, Wiley-Blackwell. Malden,
MA.
Debatin, B., Lovejoy, J. P., Horn, A. K., Hughes, B. N.
2009. Facebook and online privacy: Attitudes,
behaviors, and unintended consequences. Journal of
Computer-Mediated Communication, 15(1), 83-108.
Dobson, J.E., Fisher, P.F., 2003. Geoslavery. Technology
and Society Magazine, 22(1), 47-52.
Dobson, J. E., Fisher, P. F., 2007. The Panopticon's
changing geography. Geographical Review, 97(3),
307-323.
Gartner, G., Bennett, D. A., Morita, T., 2007. Towards
ubiquitous cartography. Cartography and Geographic
Information Science, 34(4), 247-257.
Goodchild, M.F., 2007. Citizens as sensors. GeoJournal,
69(4), 211-221.
Gross, R., Acquisti, A., 2005. Information revelation and
privacy in online social networks. Proceedings of the
2005 ACM workshop on Privacy in the Electronic
Society, 71-80.
Jackson, W.H., 1994. Chivalry in twelfth-century
Germany: the works of Hartmann von Aue (Vol. 34),
Boydell & Brewer Ltd. Cambridge.
Jones, H., Soltren, J.H., 2005. Facebook: Threats to
privacy. Project MAC: MIT Project on Mathematics
and Computing, 1, 1-76.
Kingsbury, P., Jones, J.P., 2009. Walter Benjamin’s
Dionysian adventures on Google Earth. Geoforum, 40,
502-513.
Klinkenberg, B., 2007. Geospatial technologies and the
geographies of hope and fear. Annals of the
Association of American Geographers, 97(2), 350-
360.
Kawaguchi, Y., Kawaguchi, K., 2012. What does Google
Street View bring about? -Privacy, discomfort and the
problem of paradoxical others-. Contemporary and
Applied Philosophy, 4, 19-34.
Koskela, H., 2002. ‘Cam Era’—the contemporary urban
Panopticon. Surveillance & Society, 1(3), 292-313.
Lewis, C.T., 1890. An elementary Latin dictionary.
American Book Company. New York, Cincinnati, and
Chicago.
Miller, H., 2007. Place-based versus people-based
GIScience. Geography Compass, 1(3), 503-535.
Monmonier, M., 2002. Spying with Maps: surveillance
technologies and the future of privacy, University of
Chicago Press. Chicago.
Morita, T., 2005. A Working conceptual framework for
ubiquitous mapping. Proceedings of XXII
International Cartographic Conference. A Courna,
Spain. 2005.
McGrath, J.E., 2004. Loving big brother: Performance,
privacy and surveillance space. Psychology Press.
London.
Norheim-Hagtun, I., Meier, P., 2010. Crowdsourcing for
crisis mapping in Haiti. innovations, 5(4), 81-89.
Ong, E.Y.L., Ang, R.P.. Ho, J.C.M., Lim, J.C.L., Goh,
D.H., Lee, C.S., Chua, A.Y.K., 2011. Narcissism,
extraversion and adolescents’ self-presentation on
Facebook. Personality and Individual Differences,
50(2), 180-185.
GISTAM 2018 - 4th International Conference on Geographical Information Systems Theory, Applications and Management
26

Propen, A.D., 2005. Critical GPS: Toward a new politics
of location. ACME: An International Journal for
Critical Geographies, 4(1), 131-144.
Reichenbacher, T., 2007. Adaptation in mobile and
ubiquitous cartography. In William C., Peterson, M.P.
and Gartner, G. eds. Multimedia Cartography,
Springer. Berlin Heidelberg, 383-397.
Rose-Redwood, R.S. 2006. Governmentality, geography,
and the geo-coded world. Progress in Human
Geography, 30(4), 469-486.
Shilton, K., 2009. Four billion little brothers?: Privacy,
mobile phones, and ubiquitous data collection.
Communications of the ACM, 52(11), 48-53.
Smith, P.K., Mahdavi, J., Carvalho, M., Fisher, S., Russell,
S., Tippett, N., 2008. Cyberbullying: Its nature and
impact in secondary school pupils. Journal of Child
Psychology and Psychiatry, 49(4), 376-385.
Talen, E., 2000. Bottom-up GIS. Journal of the American
Planning Association, 66, 279-294.
Turner, A., 2006. Introduction to neogeography, O'Reilly
Media, Inc.
Yomiuri Online, 21 July 2017.
http://www.yomiuri.co.jp/national/news/20120721-
OYT1T00402.htm (deleted)
Whitaker, R., 1999. The end of privacy: How total
surveillance is becoming a reality, The New Press.
New York.
Wolak, J., Finkelhor, D., Mitchell, K. J., Ybarra, M. L.,
2008. Online" predators" and their victims: myths,
realities, and implications for prevention and treatment.
American Psychologist, 63(2), 111-128.
A Newly Emerging Ethical Problem in PGIS
27
