
A Declarative Model for Reasoning about Form Security
Aaron Hunter
British Columbia Institute of Technology, Burnaby, Canada
Keywords:
Reasoning about Action, Information Security, Knowledge Representation.
Abstract:
We introduce a formal methodology for analysing the security of digital forms, by representing form signing
procedures in a declarative action formalism. In practice, digital forms are represented as XML documents
and the security of information is guaranteed through the use of digital signatures. However, the security of
a form can be compromised in many different ways. For example, an honest agent might be convinced to
make a commitment that they do not wish to make or they may be fooled into believing that another agent
has committed to something when they have not. In many cases, these attacks do not require an intruder
to break any form of encryption or digital signature; instead, the intruder simply needs to manipulate the
way signatures are applied and forms are passed between agents. In this paper, we demonstrate that form
signing procedures can actually be seen as a variation of the message passing systems used in connection
with cryptographic protocols. We start with an existing declarative model for reasoning about cryptographic
protocols in the Situation Calculus, and we show how it can be extended to identify security issues related to
digital signatures, and form signing procedures. We suggest that our results could be used to help users create
secure digital forms, using tools such as IBM’s Lotus Forms software.
1 INTRODUCTION
Information is often exchanged over a network
through the use of digital forms. A form is essentially
a structured collection of data that allows an agent
to enter information, and also to commit to particu-
lar claims through the use of a signature. In the past,
the security of a signature was guaranteed through the
physical properties of paper. In the case of digital
forms, security must be demonstrated through some
form of mathematical proof. It is well known that
multi-agent systems with formal models of knowl-
edge can be used to prove the security of crypto-
graphic protocols, but such methods have not been
widely employed in the context of form validation. In
this paper, not only do we demonstrate that the same
methods can be used to prove the security of digital
forms, but we also show that it is possible to simply
modify some existing, declarative protocol verifica-
tion formalisms for use with digital forms. The result
is a declarative model of form structure that can be
used to authomatically find attacks on forms.
Our framework is based on a Situation Calcu-
lus (SitCalc) model of a message passing system, in
which honest agents pass simple messages on an in-
secure channel. In the original framework, messages
are essentially text and all attacks are based on inter-
cepting or mirroring messages. This paper makes two
contributions to existing work on logic-based mod-
els for reasoning about security. First, we provide the
foundation for an executable model of digital forms
that allows attacks on forms to be automatically dis-
covered. This is a problem of significant practical in-
terest that has not been addressed substantially in ex-
isting work. Second, our work further demonstrates
the utility of declarative models for reasoning about
security. Since the original model for protocol veri-
fication is declarative, it is actually quite straightfor-
ward to modify the solver to deal with a different se-
curity domain.
2 PRELIMINARIES
2.1 Motivation
It is well known that businesses stand to save a great
deal of money by transitioning from paper forms to
digital forms (Bertrand et al., 1995). However, while
HTML forms on the Internet are very common, they
are known to suffer from many limitations both in ex-
pressiveness and security. For example, paper forms
420
Hunter A..
A Declarative Model for Reasoning about Form Security.
DOI: 10.5220/0005213604200425
In Proceedings of the International Conference on Agents and Artificial Intelligence (ICAART-2015), pages 420-425
ISBN: 978-989-758-074-1
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)
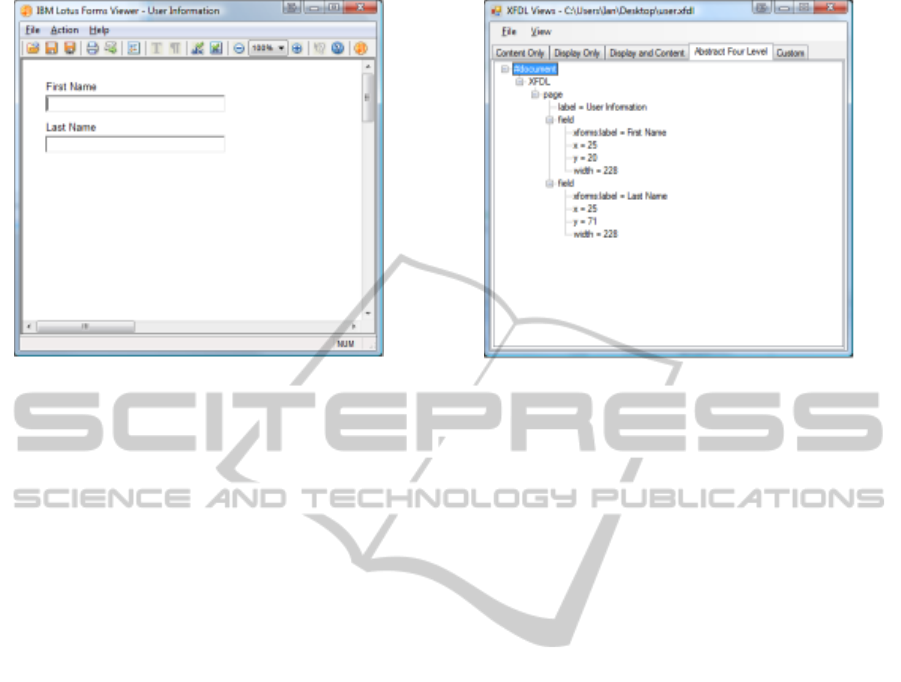
Figure 1: A Simple Form.
typically allow an agent to sign just a part of the form
in sequence with other agents. Moreover, as indicated
previously, the data on a paper form is protected by
the physical properties of paper that allow tampering
to be predicted. As a result, while businesses would
prefer to use digital forms, they would like forms that
preserve the standard conventions and capabilities of
paper forms. This has lead to the development of spe-
cialized form processing software.
The standard approach is to use XML standards
to represent the structure of a form. For example,
the XFDL standard is used by some form processing
software (Boyer, 2005). XML trees in this standard
use nodes to represent form fields, and the children
of each node represent properties of the correspond-
ing field. Field properties might include location, text,
font size, or any number of other features. As an il-
lustration, Figure 1 provides the standard view of a
simple form. Figure 2 provides a view of the XML
tree for the XFDL representation of this form.
2.2 Logical Representations of Forms
There has been some past work on formal represen-
tations of XML forms. In particular, a precise def-
inition of a document tree is introduced in (Hunter,
2012). The idea is to identify a form with a tree that
is roughly the same shape as the corresponding XFDL
representation. A vocabulary is introduced consisting
of labels and values, and then a specialized property is
introduced to indicate if a form field is visible or not.
For example, the set of labels might include the word
name and the set of values might include all names
of relevant agents. In practice, both sets would actu-
ally be generated from a finite alphabet of symbols.
Given the set of labels and values, one can define
Figure 2: The Corresponding XML Tree.
a propositional vocubulary consisting of label-value
pairs. Hence, when a form is filled out, the author
is actually asserting that certain labels have certain
values. Using this basic framework, the content of a
form is then defined to be a formula over the defined
propositional vocabulary. Modal operators for belief
can then be introduced for each agent, which are then
used to define the notion of commitment. This notion
can then be used to define attacks in terms of forcing
false commitments or other forms of deception.
The preceding formal model of digital forms helps
to make some attacks explicit, but it suffers from two
main deficiencies. First of all, the approach is not
declarative. In order to represent a form or an attack
on a form, one needs to delve into the internal repre-
sentation in terms of trees. This makes it somewhat
difficult to extend and modify the approach for differ-
ent kinds of documents. The second problem is that
this is not a model that lends itself to efficient auto-
mated reasoning. After creating the logical represen-
tation of a form, the only way to find attacks on the
form is through exploration by hand.
2.3 Cryptographic Protocol Verification
Logical approaches to the verification of crypto-
graphic protocols originated with the pioneering work
on BAN logic (Burrows et al., 1990). The basic
idea of BAN logic was to use a logic to model and
reason about the beliefs of agents participating in
the cryptographic protocol. The logic itself was not
particularly sophisticated, so it is not longer consid-
ered a viable approach to protocol verification. How-
ever, the notion of using a logical model that includes
the beliefs of agents was very influential. Many re-
lated approaches have followed, including represen-
ADeclarativeModelforReasoningaboutFormSecurity
421

tations based on epistemic logics (van der Hoek and
Wooldridge, 2002), multi-agent systems (Fagin et al.,
1995), strand spaces (Halpern and Pucella, 2003), and
logic programs (Carlucci Aiello and Massacci, 2001).
In each case, the intruder model used is called the
Dolev-Yao intruder (Dolev and Yao, 1983). In this
model, the intruder is able to intercept messages, redi-
rect messages, and spoof messages. The main limita-
tion of this intruder is that they are not able to de-
cipher encrypted messages; this is a reasonable limi-
tation if we assume strong encryption with large key
sizes.
2.4 The Situation Calculus
For the present paper, we are interested in declarative
models for reasoning about cryptographic protocols,
with particular emphasis on the SitCalc. In the inter-
est of space, we do not introduce the SitCalc here; we
refer the reader to (Levesque et al., 1998) for a basic
introduction. For now we simply introduce the basic
terminology. In the SitCalc, there are several impor-
tant categories of entities. First, there are situations
(denoted by the variable s). A situation represents a
configuration of the world, along with the history of
all actions that have been executed. There are also ac-
tions (denoted by the variable A), that represent things
that an agent can do to change the state of the world.
There is also a function symbol do, where do(s, A) is
understood to represent the situation that results when
the action A is executed in the situation s. There is a
distinguished constant s
0
representing the initial sit-
uation, so that every situation can be represented as
do(
¯
A, s
)
) for some sequence of actions
¯
A. A single
second-order induction axiom allows us to prove that
certain properties hold for all situations.
In the SitCalc, a predicate that takes a situation
as an argument is called a fluent. Informally, fluents
are used to represent properties of the world that may
change due to the effects of actions. For example,
in a message passing system, there could be a flu-
ent holds that indicates if a certain agent is holding
a particular message in a particular situation. Ac-
tion domains are fomalised in the SitCalc by explicitly
specifying the way that fluent values change when ac-
tions are executred. The effects of actions are given
by specifying precondition and effect axioms that in-
dicate which predicate values change in a situation
when an action is executed. One of the advantages
of the SitCalc for reasoning about actions is that Sit-
Calc formilizations can be translated into GoLog, an
executable logic-based language for planning.
The SitCalc formalization of message passing in
(Hunter et al., 2013) includes four different kinds of
entities: Agents, Nonces, Keys and Data. A nonce
is a random number used in a cryptographic protocol.
The main actions in the formalization are makeNonce,
encrypt, decrypt, compose, send and receive. Using
these basic entities and actions, a set of axioms is in-
troduced that specifies the effects of actions and the
capabilities of the intruder. This SitCalc formulation
is then translated into a GoLog program that can be
executed to automatically find attacks on the proto-
col in a reasonable time frame. Our approach in this
paper is to extend this model for validating security
properties on digitally signed forms.
3 FORMS AS PROTOCOLS
3.1 Intuition
In this section, we demonstrate how to develop a
declarative treatment of forms by treating forms as a
protocols. The first observation to make is that sign-
ing a form is actually a multi-step procedure that in-
volves the exchange of information. The basic steps
are as follows:
1. An agent A creates a form, requiring n of signa-
tures (possibly on different parts of the form).
2. Repeat until all unsigned parts have been signed:
(a) The agent holding the form signs any number
of empty parts.
(b) The agent passes the form to some other agent
to hold.
3. The completed form is passed to some authority.
We will refer to this process as a form signing proce-
dure.
Our basic approach is to express form signing pro-
cedures as a kind of message passing protocol. There
are several steps required:
• Replace messages with forms.
• Introduce actions for filling and signing forms.
• Specify the exact steps to a signing procedure, as
a protocol.
By formalizing all of these steps, we can automati-
cally find some forms of attack on a form signing pro-
cedure.
3.2 Formalization
Note that there are already pre-existing SitCalc for-
malizations of message passing, so we do not want to
replicate the work involved in developing such sys-
tems. Two representative SitCalc formalizations are
ICAART2015-InternationalConferenceonAgentsandArtificialIntelligence
422

•
P
P
P
P
P
P
P
P
P
•
Q
Q
Q
Q
Q
•
label
Shoes
•
value
checked
•
visible
1
•
Q
Q
Q
Q
Q
•
label
Socks
•
value
unchecked
•
visible
1
Figure 3: A Simple Form Tree.
given in (Hern
´
andez-Orallo and Pinto, 2000)) and
(Hunter et al., 2013), respectively. We use the latter as
a starting point for this work, as it includes a transla-
tion to GoLog for authomatically finding attacks. Our
approach is to extend this SitCalc theory by introduc-
ing forms that can be sent and received. Since we are
assuming an underlying SitCalc theory for message
passing, we are also assuming some of the utility ac-
tions required for constructing and sending messages.
In particular, it is useful to assume an underlying ac-
tion list that takes a sequence of n objects and pro-
duces a single object representing the list. In the re-
mainder of this section, we describe the main cate-
gories of object required for our formalization.
Items. The variable i, possibly with subscripts, will
range over form items. The intention is that an item
represents some relevant component of a form, such
as an input mechanism or a text label. For the sake of
simplicity, we think of all inputs as simple text blocks
or as text blocks with an associated checkbox for in-
put.
We introduce a functional fluent newinput(p, s)
that is used to generate a new input to place on a form,
labelled with the proposition p. The following fluents
apply to inputs:
• Label(i, p, s) – True just in case the item is la-
belled with the proposition p.
• Checked(i, s) – True just in case the associated
checkbox has been checked.
• Invisible(i, s) – True just in case the item is invis-
ible.
In practice, there are many additional options that can
be associated with a given item. For example, every
item typically has some associated coordinates indi-
cating a position on the page. The simple set provided
here is sufficient for an initial formal analysis.
Example. Suppose we would like a form to col-
lect data about the clothes people are wearing. We
might decide one item needes would be a checkbox
labelled “Shoes”. The process here would be to cre-
ate an empty form, then create an item with the label
shoes and add it to the form. We could then create
another item labelled “Socks” and add it to the form.
The XFDL tree representing this form is in Figure 3.
For now, every form that we consider has this simple
structure; but it would be straightforward to produce
more complex forms by adding new kinds of items
and new kinds of properties.
Forms. The primary activity in our framework is
the manipulation and exchange of forms. The variable
f , possibly with subscripts, will range over forms. A
form is primarily a collection of inputs that can be
signed. In addition to the unary predicate Form, we
introduce a fluent symbol Contains( f , x, s) that is true
just in case the form f contains in the input x in sit-
uation s. One important feature that must be cap-
tured is the fact that signatures do not always apply
to an entire form. For this, we need to introduce some
formal mechanism for identifying a sub-form to be
signed. In order to reduce the number of object types
required, we handle this problem by introducing the
fluent SubForm( f
1
, f
2
, s) which is true just in case ev-
ery item in f
1
is also in f
2
, in the situation s.
Sendables. The introduction of forms into the vo-
cabulary results in some potential redundancy when it
comes to sending and receiving information. In par-
ticular, both messages and forms can now be transmit-
ted between agents in (essentially) the same manner.
As such, we introduce a new type called sendable,
which is basically an abstract class that includes both
messages and forms.
3.3 Action Effect Axioms
We require actions for modifying and signing forms.
In the SitCalc, each action requires a precondition and
an effect. We remark that these conditions use a dis-
tinguished predicate called designer to indicate if a
given agent is able to design forms. The following
actions are required:
1. sign(a, f
s
, f , k) – Agent a signs the subform f
s
of
f using key k.
ADeclarativeModelforReasoningaboutFormSecurity
423

Precondition:
Poss(sign(a, f
s
, f , k), s) ≡ (Has(a, f , s) ∧
(Has(a, k, s) ∨ ∃a
0
PublicKey(a
0
, k)))
Effect:
Has(a, signed( f , k), do(sign(a, m, k), s))
2. check(a, i) – Agent a checks the item i.
Precondition:
Poss(check(a, i, s)) ≡ Has(a, i, s)∧¬checked(i, s)
Effect:
checked(i, do(check(a, i, s)))
3. uncheck(a, i) – Agent a checks the item i.
Precondition:
Poss(uncheck(a, i, s)) ≡
Has(a, i, s) ∧ checked(i, s)
Effect:
¬checked(i, do(check(a, i, s)))
4. send(a
1
, a
2
, f ) – Agent a
1
sends the form to a
2
.
An intruder can masquerade as a
2
.
Precondition:
Poss(send(a
1
, a
2
, f ), s) ≡
((Has(a
1
, f , s) ∧ a
1
6= a
2
) ∨ Has(intr, f , s))
Effect:
Sent( f , a
1
, a
2
, do(send(a
1
, a
2
, f ), s))
5. receive(a
1
, a
2
, f ) – Agent a
1
receives the form f
from a
2
. An intruder can intercept messages.
Precondition:
Poss(receive(a
1
, a
2
, f ), s) ≡ (Sent( f , a
2
, a
1
, s) ∨
(a
1
= intr ∧ ∃a
0
Sent( f , a
2
, a
0
, s)))
Effect:
Has(a, f , do(receive(a
1
, a
2
, f ), s)) ∧
¬Sent(a
2
, a
1
, f , do(receive(a
1
, a
2
, f ), s))
6. compose f orm(a, f ,
¯
i) – Agent a composes form
f consisting of items
¯
i = i
1
, . . . , i
n
. Consequently,
compose f orm is in fact a set of actions, one for
each possible number of arguments.
Precondition:
Poss(compose f orm(a, f , list(
¯
i), s) ≡
designer(a)
Effect:
Has(a, f , do(compose f orm(a, f , list(
¯
i), s))
7. sub f ormlist(a, f
s
, f ,
¯
i) – Agent a composes a sub-
form of f consisting of items
¯
i.
Precondition:
Poss(sub f ormlist(a, , f
s
, f , list(
¯
i), s) ≡
(designer(a)
V
n
j=1
contains( f , i
j
, s)
Effect:
Has(a, f
s
, do(sub f list(a, f
s
, f , list(
¯
i), s))
∧sub f orm( f
s
, f , do(sub f list(a, f
s
, f , list(
¯
i), s))
V
n
j=1
contains( f
s
, i
j
, do(sub f list(a, f
s
, f , list(
¯
i), s))
8. sub f ormsubtract(a, f
s
, f ,
¯
i) – Agent a composes
a subform of f by removing items
¯
i.
Precondition:
Poss(sub f ormlsubtract(a, , f
s
, f , list(
¯
i), s) ≡
(designer(a)
V
n
1
contains( f , i
i
, s)
Effect:
Has(a, f
s
, do(sub f ormsubtract(a, f
s
, f , list(
¯
i), s))
∧sub f orm( f
s
, f , s)
This vocabulary is sufficient for specificying a
number of attacks on form signing procedures.
3.4 Finding Attacks on Forms
We consider a simple toy example. Suppose that we
have produced a form that is intended to collect data
about the electronics someone has purchased. There
is an item representing a title “Items Purchased.”
There are then five items such as “Computer” or
“Television” with check boxes. The intention is that
the form should be filled out, signed, then returned to
the relevant authority.
Here is a high level description of an attack se-
quence on this form.
1. Form designer makes a form and sends it to A.
2. An intruder intercepts the form.
3. The intruder changes the signing area to not in-
clude the title, then forwards the form to A.
4. A checks the appropriate fields and sends the form
to the authority.
5. The intruder intercepts the form again, and
changes the title to “Items Stolen” and forwards
the signed form.
This sequence of actions can be formalized using Sit-
Calc actions from our theory as follows.
1. Use composeform and send.
2. Intercept using message passing actions.
3. Use subformsubtract to remove title. Use com-
poseform to re-add outside the signing area.
4. A fills out the form using check action.
5. Intercept again, use subformsubtract and com-
poseform again to produce final form.
In practice, a form designer might not even think
it is necessary to put the form title under the signature
of the signer. But failing to do so opens up the possi-
bility of this kind of attack, where the entire meaning
of a form is change by a malicious intruder. Worse
ICAART2015-InternationalConferenceonAgentsandArtificialIntelligence
424

yet, the meaning is changed after an honest agent has
signed the form. While this particular attack might
not be a problem, it does suggest that some form de-
signs might be vulnerable to such attacks. Unfortu-
nately, this kind of attack is very hard to find by hand;
it would be much better if it could be found automat-
ically through a translation to GoLog.
4 DISCUSSION
4.1 Future Work
There are two natural directions for future work. First,
as mentioned in the previous section, it would be valu-
able to turn our theory into an executable program
for finding attacks. The Golog implementation from
(Hunter et al., 2013) can immediately be applied to
find attacks due to form interception or mirroring. In
order to develop a more complete approach to form
validation, we would also like to have the intruder
use form modification actions. The challenge is to
avoid any infinite loops in which a sub-form is cre-
ated, then extended, then contracted forever. But this
is a standard problem already addressed in the Sit-
Calc tool for protocol verification, so it would be easy
enough to use the same methods for the form vali-
dation tool. The second obvious direction for future
research would be to allow more complex forms with
more structure and a wider range of options.
In the long run, it would be ideal to embed
our form validation tool in something like the Lotus
Forms designer tool. At present, Lotus Forms allows
a designer to create a form, but it does not look for any
particular attacks. It would be a significant improve-
ment if the designer would look for possible attacks
on a form, based on the number of signature fields
and the network over which it must be shared.
4.2 Conclusion
We have presented a SitCalc formalization of form
signing procedures. We have demonstrated that form
signing procedures can be formalized by extending
existing SitCalc tools for representing and reasoning
about cryptographic protocols. We have noted that
this is a problem of important practical significance,
which has not been extensively explored using for-
mal methods. It has however been demonstrated else-
where that key concepts such as commitment and de-
ception can be formalized in a logical framework in
which forms are represented as trees, and agents have
explicit beliefs. By using epistemic extensions of the
SitCalc, the framework presented here could there-
fore be used to formalize and reason about these more
complex notions as well. Logical methods have a
great deal to offer in the context of this problem; this
paper is just scratching the surface in terms of techni-
cal content and practical applications.
REFERENCES
Bertrand, R., Hearn, J., and Lett, B. (1995). The north amer-
ican pre- and post-processing equipment market: Cap-
turing the benefits and avoiding the pitfalls. Technical
report, Strategic Analysis Report, Gartner Group.
Boyer, J. (2005). Enterprise-level web form applications
with xfdl and xforms. In Proceedings of XML 2005
Conference and Exposition.
Burrows, M., Abadi, M., and Needham, R. (1990). A logic
of authentication. ACM Transactions on Computer
Systems, 8(1):18–36.
Carlucci Aiello, L. and Massacci, F. (2001). Verifying secu-
rity protocols as planning in logic programming. ACM
Transactions on Computational Logic, 2(4):542–580.
Dolev, D. and Yao, A. (1983). On the security of public key
protocols. IEEE Transactions on Information Theory,
2(29):198–208.
Fagin, R., Halpern, J., Moses, Y., and Vardi, M. (1995).
Reasoning About Knowledge. MIT Press.
Halpern, J. and Pucella, R. (2003). On the relation-
ship between strand spaces and multi-agent systems.
ACM Transactions on Information and System Secu-
rity (TISSEC), 6(1).
Hern
´
andez-Orallo, J. and Pinto, J. (2000). Especificaci
´
on
formal de protocolos criptogr
´
aficos en c
´
alculo de
situaciones. Novatica, 143:57–63.
Hunter, A. (2012). Structured documents: Signatures and
deception. In Proceedings of the European Intel-
ligence and Security Informatics Conference (EISIC
2012), pages 274–277.
Hunter, A., Delgrande, J., and McBride, R. (2013). Protocol
verification in a theory of action. In Proceedings of the
Canadian Conference on AI, pages 52–63.
Levesque, H., Pirri, F., and Reiter, R. (1998). Foundations
for the situation calculus. Link
¨
oping Electronic Arti-
cles in Computer and Inf. Science, 3(18):1–18.
van der Hoek, W. and Wooldridge, M. (2002). Tractable
multiagent planning for epistemic goals. In Proceed-
ings of AAMAS-02,.
ADeclarativeModelforReasoningaboutFormSecurity
425
