
An Unified Behaviour Model to Predict Web 2.0
Adoption as a Tool for Software-Knowledge Sharing
Manuel Fernández-Utrilla, Pilar Fernández-Utrilla and Gonzalo Mariscal
Centre of Excellence of Research, Universidad Europea, Spain
Abstract. The most powerful tool for software developers to connect with
each others is social networking. These applications are normally free of
charge. The professional use of these applications exceeds beyond the fun. An
unified behaviour model to predict web 2.0 adoption as a tool for Software-
Knowledge sharing based on two solid and tested theories, theory of planned
behaviour and self-determination theory, will be reached by this study. A
single model, which will join these theories, will accurately predict a use of
these communication tools to set connections among professional groups:
software developers in particular. These models determine the factors that
mainly affect the intention to use described in order to improve these tools with
a high probability of success. These professionals could share knowledge, keys
and bugs in order to find the best solution. A representative number of
software developers have participated in this study in order to research what
the reason is because these professionals do not use these tools with that aim.
Keywords. Knowledge sharing, Social Applications, Theory of planned
behaviour, Self-determination theory, Prediction Model.
1 Introduction
The resolution of bugs or the clarification of specifications, should have found a
great ally in social applications when no solutions is reached. Web 2.0 technologies
(wikis, blogs, social applications, etc.) are playing an ever more important role in the
transfer of information and the reality which is the fact that sharing experiences helps
to improve results. According to the report of the “Observatorio Nacional de las
Telecomunicaciones y los Sistemas de Información [ONTSI]”, “Servicios Utilizados
por los Usuarios de Internet"[1], 52.4% of the users of the network of networks use
social networking technology as Forums, Facebook or Linked-In, a fact which warns
that a large number of professionals will make use of them. There are also reference
studies which show that social applications provide new ways for people to
collaborate, interact, communicate, co-create, and share ideas and knowledge [2].
Authors like Conole and McAndrew [3], confirmed through his published research
based computer tools 2.0 technologies that provide the perfect environment for
learning from communication and the act of sharing real cases every day. Another
important reference of how the exchange of information and experience can help to
find solutions is to Orehovacki, Bubas, and Konecki [4].
Fernández-Utrilla M., Fernández-Utrilla P. and Mariscal G..
An Unified Behaviour Model to Predict Web 2.0 Adoption as a Tool for Software-Knowledge Sharing.
DOI: 10.5220/0005165900030018
In Proceedings of the 5th International Workshop on Software Knowledge (SKY-2014), pages 3-18
ISBN: 978-989-758-051-2
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

On the other hand and regardless of the fact that the current generation of
software developers available to a high level in the use of social applications, the
professional use is the common denominator of all labor collectives. There are some,
such as university professors, who despite having knowledge are unwilling to use
technology in their classes 2.0 [5]. Through the study, it will be showed what the
intention to use is [6] of certain applications called social networks by software
developers in their daily professional activities.
The software developers’ community has its own professional development
culture [39]with its own problems of cooperation. This study will describe what
factors are necessary to work on in order to reduce the impact of those problems
through a behaviour model. The relationship among main stakeholders is essential
for a successful software development. Cooperation through any mean of
communication is the key to improve the results. It is common that these
professionals publish algorithms and piece of code to share knowledge with other
developers, but several problems such guaratees or supports go with them as well.
Hence software developers’ cooperation follows one sense in most of cases, a
developer shares his consolidate knowledge.
Thorugh this research work, factors which help to develop the cooperation on the
other sense, will be develop. The main goal will be to achieve those software
developers can use social applications to share knowledge and ask for solutions in
order to improve the efficacy of developments. Results will explain how to fight
against these barriers which appear around sharing knowledge through social
applications.
These Internet applications already have a strong position after many years of
operation. Their study began following the theory of six degrees of separation,
whereby it is possible to contact anyone on the planet through six contacts related
among them. The Hungarian writer Frigyes Karinthy proposed this theory in 1929.
The concept is based on the exponential growth of the number of known that each
individual has. Several studies and experiments have been done since this moment to
prove the so-called "six degrees of separation". The best known: Ithiel de Sola Pool
(MIT) and Manfred Kochen (IBM) in 50s and Stanley Milgram in the next decade.
After all, social contacts were uniquely defined as the largest network of existing
information.
The first social networking application set in the mid-90s with the site
www.classmates.com. Randy Conrads created it in 1995. He contacted former
classmates through this site. Subsequently and after the ".COM" crisis began to
appear other websites that they contacted people and creating communities such as
MySpace, created by Microsoft in 2003, or created by Lars Hinrichs Xing in 2003.
These applications are more closely known today as social networks, whether for
leisure or professional use. Currently these tools connect millions of people. A clear
example of these is Facebook, which has over 900 million users worldwide according
to its last report in 2012.
The technology of communication offers a multitude of possibilities through
these social networks. Its main focus is on transfer data from one subject to a
community associated with it [7]. For this is made available to the user several tools
are available for the users in order to develop utilities such as sending private or
public messages, pictures, data, etc. Through all these utilities you can share, discuss,
claim and even create streams of thought. There are different groups in this area that
4

could use information to improve their performances in relation to the resolution of
critical issues.
However the most powerful tool at present for the transfer of information
between people is not used in the professional field rather than a small percentage of
subjects according to the Observatory of Social Networks in Spain in 2012. It is
difficult to make a scientific explanation. This investigation will determine a
scientific model to predict the use of social networks as a communication tool
between software developers in order to share information and experiences,
improving their results.
2 State of the Art
Social psychology is presented as an option that offers the possibility to intervene in
the conduct of the professional group on which the research is developing: software
developers.
2.1 Theory of Planned Behaviour [TPB]
Theory of Planned Behaviour (TPB) is one of the most proven and accepted theories
in the scientific world. This theory was initially proposed by Professor Icek Ajzen in
1991 and has been subsequently modified and updated in 2006.
The main reason for the use of this theory is the rigorous analysis of all the
factors that make up the execution of the behaviour performed. Each analyzed
behaviour can be evaluated from different angles and therefore be caused by different
sources, but there is a common factor to all of them which is the frequency with
which they occur. The main target of this kind of theory is to discover what the
possibilities of increasing the frequency are by changing its historical causes.
Following the mentioned theory, it should be noted that human behaviour occurs
according to:
• Attitude: software developers can positively or negatively evaluate the use of
social media in their job. The degree in which they are involved, will determine
whether they do have attitude to do or not. They may consider such use helps them
improve their service through shared knowledge or bugs thrown the collective.
• Subjective Norm: is determined by the perceived social pressure on an
individual to perform certain behaviour. In this study, the focus is on the use of social
networking as an effective tool for software developers. The different players around
the subject can influence described pressure: superior, colleagues, family and the
media even.
• Perceived Control: this parameter is directly related to the perception that
software developers have about the possibility of using these social applications in
their daily work, which is running the conduct mentioned. Being specific, these
professionals have Internet access and a multitude of such tools through it. In
addition to their availability, they have the required knowledge to exploit them,
permits and authorizations and the most important: the desire to do it.
These three factors will influence the decision-making intention of professionals
5

when using social media to improve their daily activity. Therefore, the intention to
use is influenced by attitude, the subjective norm and the perceived control described
above it. The importance of each factor will be different for each worker, as they
present their personal characteristics and potentially different environment.
The intention to perform an activity, action or behaviour, is the precedent
immediately prior to its execution. It can be said since what it has exposed previously
that the particular behaviour can be explained as measurable response that results
from a particular situation in order to achieve a target.
It will need to take a sample large enough to accumulate sufficient number of
observations that allow us to evaluate the behaviour at different times and contexts.
This will generate a greater measurement and more accurate conclusions. In this
investigation, the software developer motivation to use collaborative tools exposed,
will only drive to use them when perceived control is strong enough. That is,
perceived control over the activity in question moderates the effect of intention to
use.
Theory of Planned Behaviour states that behaviour is a variable whose magnitude
will be determined by the combination of intentions and intuition that subjects have
about their control. Professionals who are under this study used social applications, if
and only if, their motivation is right and if they understand how to use.
2.2 Self-Determination Theory [SDT]
Self-Determination Theory is a theory of human motivation that has been widely
used in the health domain. It has been proven in various fields such as sports or
endocrinology [17].
This theory defines two types of behavioural regulation. Firstly, intrinsic
motivation refers to engaging in behaviour of interest, enjoyment or satisfaction
inherent in this behaviour. Secondly and equally important, extrinsic motivation
describes the participation in behaviour for reasons unrelated to their own behaviour
such as social approval.
Making a further development, intrinsic motivation represents the prototype of
autonomous or self-determined motivation according to studies presented by Ryan &
Deci [10]. This motivation is associated with the quality and the persistence of
behaviour. On the opposite side, extrinsic forms of regulation are associated with a
lack of sustained performance over time (and Decision Ryan, 10). In addition, Self-
Determination Theory (SDT) also identifies four types of extrinsic motivation, placed
at various intermediate points along a continuum from intrinsic to extrinsic
motivation. The constant is known as the perceived locus of causality (PLOC).
Self-Determination Theory (SDT) has a significant practical value, in fact, this
theory has been shown to increase behavioural persistence in different studies [12].
However, the SDT predicts that individuals, showing an extrinsic motivation or
controlled, are less willing to show a behavioural persistence.
Recent publications have suggested that autonomous and controlled motivations
or reasons for engaging in behaviour should be different of a person pursue goals
[14]. Other models such as the self-concordance [15] predict that individuals can
pursue goals that are self-consistent or independent, or self and non-self-discordant.
Sheldon and Elliot showed that individuals experience greater progress toward self or
6

consistent as far as behavioural goals are concerned, as it exerts more effort in your
search. Thus increasing the intention to use specific behaviour should be
accompanied by a fomentation of behavioural persistence.
3 Research Framework
3.1 Integration of Both Theories
In this study, we used behavioural regulation to support her persistence and
predicting the intention of use described in the Theory of Planned Behaviour. The
combination of both theories provides a more accurate prediction of the intention of
performing the behaviour. This improvement will show in the results section where
separating numbers of each theory support this statement.
Theory of Planned Behaviour (TPB) identifies the factors that address the
behaviour but does not explain why individuals create the attitudes, subjective norms
or intentions of use. By contrast, the Self-Determination Theory (SDT) helps explain
these general grounds and contextualizes the social cognitive constructs of the TPB
[16]. A more accurate model for the prediction of intention of execution of behaviour
with the integration of both theories is obtained. There is recent meta-analysis on
studies that integrate both theories providing complementary value between them
[18].
The research framework is defined uniquely by its components: software
developers and tools with an insufficiently exploited commercial potential: social
applications. The aim of the process is the prediction of intention to use social
applications as a software-knowledge sharing tool in a professional setting. This will
be used by software developers to share knowledge and bugs in order to improve
their professional productivity performed daily.
Fig. 1. Contribution – Developed Behaviour Model to Predict.
The developed research framework in this study, our contribution, can be seen on
Figure 1. Through this model, the objective described above can be evaluated. This
intention to use is the result of elements such as attitude, perceived behavioural
control and subjective norm as shown in Ajzen model comprising the Theory of
7

Planned Behaviour focused on the perception feeling. But this research has expanded
the research framework of the study in order to increase the accuracy of prediction
including another feeling: motivation. In particular two types of motivation,
autonomous and controlled derived from the Self-Determination Theory whose
development began with the studies of Decision in 1970. Note that all constructs
selected for study were chosen, validated and published in high impact research.
This framework works on the following assumptions:
• H1-H2: The self-managed privacy of the professional concerned is a factor that
negatively affects the intention to use since seeing their exposure on a social network
as a potential violation of privacy of the software developments. They can also see
that this potential invasion of privacy of the software developments affects their
effective use of social applications for the purpose.
• H3-H4: The development privacy, to which these professionals help, is also a
factor that negatively affects the intention to use since seeing this exhibition in a
social application as a potential violation of the privacy of the software
developments. They may also perceive that this potential intrusion into the privacy of
their organizations will affect current use of social applications for the purpose.
• H5: Ease of use of applications that allow managing social applications, positively
influence the software developers’ attitude towards the use of social networks.
• H6: Interactivity that may exist among colleagues through these systems, results in
a considerable improvement in the attitude they have software developers towards
the use of social applications.
• H7: The usefulness of these telematics programs have to improve the outcomes of
their developments. It will be positively assessed by software developers towards the
use of social applications.
• H8: The compatibility with the infrastructure that developers must use to work. It
will be positively assessed by professional software developers towards the use of
social applications.
• H9: Perceived self-efficacy, related to the choice to improve their daily work, will
be highly valued in perceived behavioural control they undergo this professional
sector. That is why a positive degree of autonomy is presented as essential to have
the expected results.
• H10-H15: It will be based on the assumption that elements such as attitude, both
autonomous and controlled motivation, normative beliefs and perceived behavioural
control will have a positive effect on the intention to use social applications from this
professional group.
3.2 Research Metodology
Data collection method used was to send questionnaires and receive the
corresponding data from their responses. The research consisted of four main phases:
research framework development, construction and validation of the questionnaire,
data collection and finally, data analysis.
3.2.1 Construction and Validation of Questionnaire
The first part of the questionnaire will obtain demographic information about gender,
8

age, social application usage, specific application used, etc... The rest of the
questions that take part in the developed tool have been selected from studies with
validated and adapted questionnaires to the context of the current study. In addition,
the questionnaire was piloted to confirm its validity and reliability. All survey
questions were scored on a scale "Likert" of 5 points ranging from the "1" that
expresses complete disagreement, to the "5" represents the entire agreement. In the
questionnaire are uniquely intermediate points in order to avoid mistakes.
Moreover, despite having built the questionnaire with questions from validated
questionnaires [19], there has been a pilot from 102 users to contrast reaching valid
correlation values necessary to be eligible for the study.
Related to selected questions, these are chosen from a study written in a different
language than the language in which this research has been developed. It has made
use of the normalized inverse translation process as it is one of the most suitable for
problems associated with poor translations or adaptations, and thus, to evaluate the
quality of translation [20, 21].
3.2.2 Data Collection
We have developed a questionnaire on a online tool in order to make easy the full
filling of questionnaires by software developers. This can be distributed easily,
quickly and economically among the largest number of software developers who
have been contacted by the software factories to which we made contact with. The
number of responses was 328 of which have had to remove 26 by various errors. The
table 1 shows the profile of the people who responded to the survey sent:
Table 1. Demographics.
18 < years <=
25
18,20%
26 < years <=
35
38,74%
36 < years <=
45
27,45%
Years > 45 15,61%
Female 15,31%
Male 84,69%
Degree 75,57%
Master 19,15%
Doctorate 5,28%
Forum 92,56%
Facebook 21,20%
Linked-In 9,21%
Age
Gender
Edu c a t i o n
Social Network Use
9

3.2.3 Data Analysis
We used structured equation modeling (SEM) to examine the relationships among
constructs selected. Several methods could be used but its flexibility and generality
are its strong points. SEM has rapid developments and expansion. It has been chosen
the least squares regression method for their ability to work with small sample sizes.
This is the reason because most of behaviour model studies in which it is difficult to
get large samples, use SEM in order to show more accurate results. SEM takes a
confirmatory (hypothesis testing) approach to the multivariate analysis of a structural
theory, one that stipulates causal relations among multiple variables [41].
SmartPLS 2.0.M3 [22] was used for measurements on research hypotheses
described above. Chin [23] shows in their studies to obtain meaningful
interpretations, the relational coefficient values must be above 0.2. This method
provides two components of a causal model: measurement and structured model.
Furthermore, it is particularly suitable for research with significant variances.
3.2.4 Reliability and Validity
Firstly, separated results of each theory related to the parameter R2 will show the
improvement that the research has undergone [38]. The same goal, the intention to
use of a particular behaviour, through two different psychological factors: perception
(TPB) and motivation (SDT). The last three columns show the results through the
research model.
The following table shows how the research model improves the results exposed
in this paper. This fact can be inferred since the coefficient of determination (R
2
) of
the different models. This statistical element is used in trend analysis. It is computed
as a value between 0 (0 percent) and 1 (100 percent). The higher the value, the better
the fit. TPB and SDT theories offer a R
2
factor below the same element in the
research model. Following the mean of this statistic parameter, the research model is
more solid than the other theories applied by separated.
In addition, load factors, the average composite reliability and the obtained mean
have been showed in order to expose the full research statistics. Load factors must be
at least 0.6 and preferably greater than 0.7 [23]. Almost all factor loadings exceeding
these thresholds. The “t” statistic, obtained by bootstrapping (200 resamples) showed
that all factor loadings are significant at the 0.001 level. Observed reliability of
constructs (compound reliability) for each construct (see Table 2) is greater than 0.8
(Fornell and Lacker 1981). All loadings were significant constructs above the
recommended value of “p“ of 0.05 (Gefen and Straub 2005) and have generally
exceeded the recommended threshold value of 0.707 (Barclay et al. 1995). The
average variance extracted (AVE or Average Variance Extracted) was above the
minimum of 50 percent of the variance for each construct and the square root of the
AVE for each construct was much higher than the correlation of the construct with
each other construct (Barclay et al 1995. Gefen and Straub 2005).
The means of the loaded items in each respective construct gives a value of at
least 0.1 greater than the load in other constructs (Barclay et al, 1995; Gefen and
Straub 2005) and all the items loaded is greater than the expected construct any other
construct. Therefore, it can be concluded that measured constructs were consistent
and showed a substantial degree of convergence and discriminating validity.
10
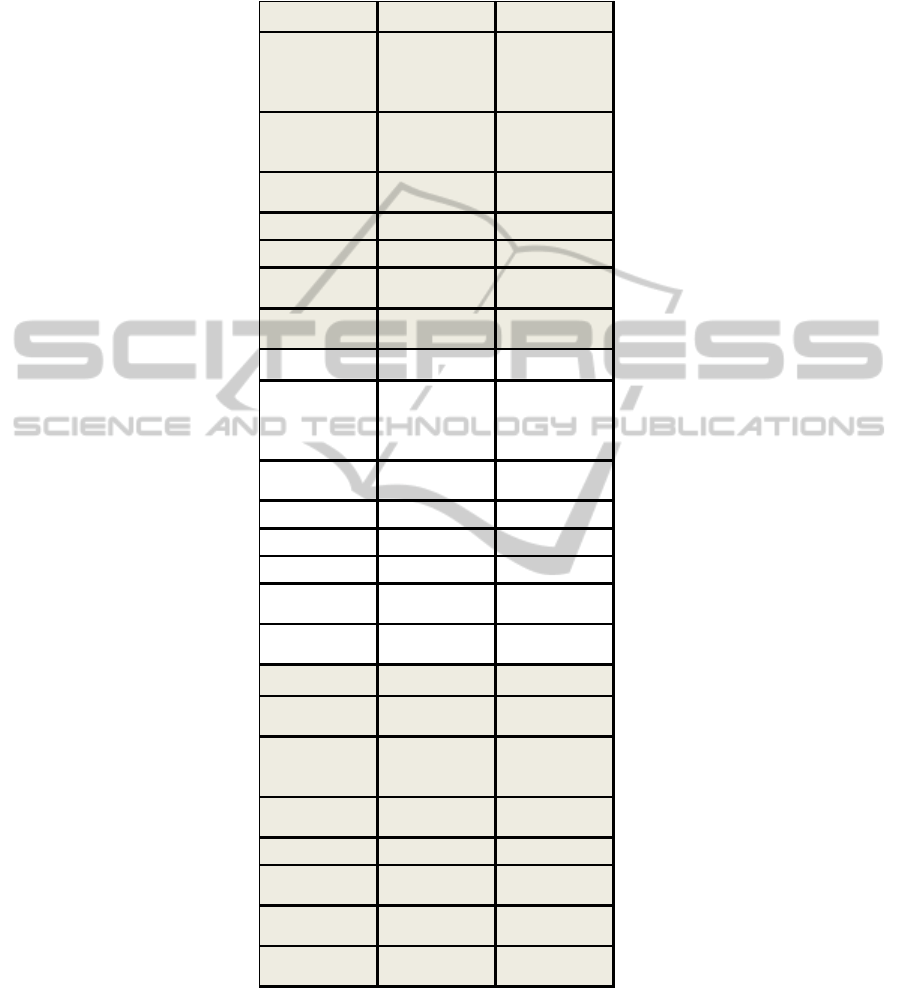
Table 2. Improvement through the research model.
Theory Construct
R
2
Theory of
Planned
Behaviour
(TPB)
Attitude 0,291
Perceived
Control
Behaviour
0,254
Normative
Belief s
0,243
Intention to
Us e
0,296
S. Netw ork
Us e
0,312
Theory Construct
R
2
Self-
Determ inatio
n Theory
(SDT)
Self-Motivation 0,218
Controlled
Mot iv at ion
0,263
Intention to
Us e
0,278
S. Netw ork
Us e
0,292
Theory Construct
R
2
Research
Model
Attitude 0,469
Perceived
Control
Behaviour
0,401
Normative
Belief s
0,381
Self-Motivation 0,343
Controlled
Mot iv at ion
0,397
Intention to
Us e
0,398
S. Netw ork
Us e
0,453
11
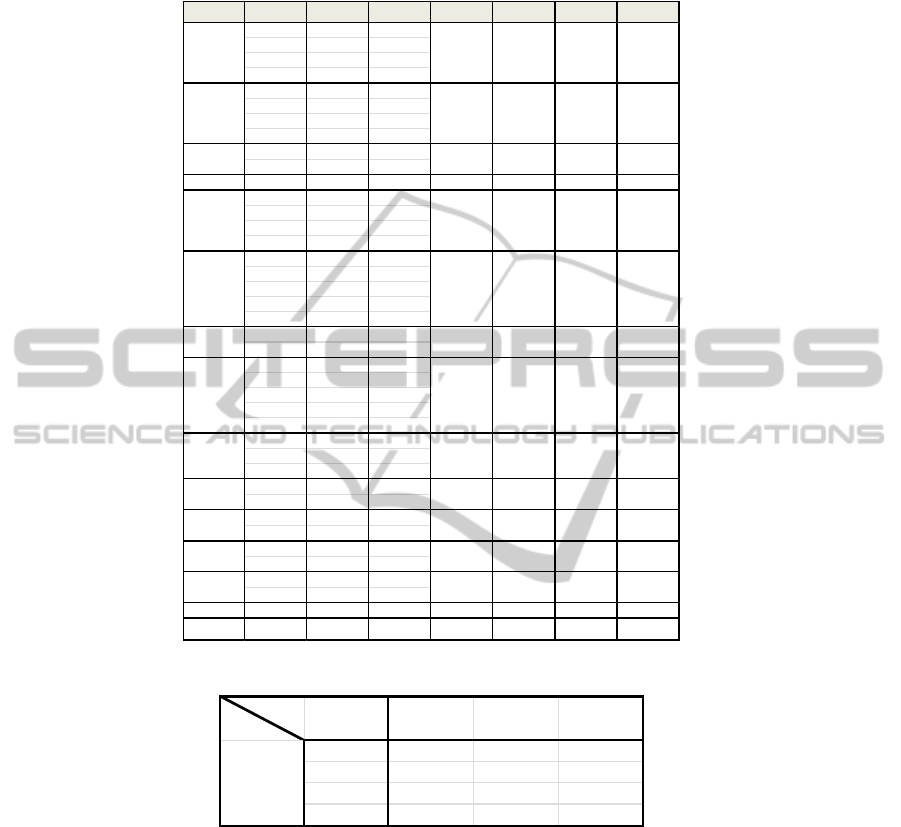
Table 3. Reliability and Validity of the Research Framework.
Table 4. Social Applications Knowledge Level.
4
Conclusions
Regarding the knowledge level about social applications, this research has been able
to get a picture of what different highlighted aspects are. In addition, it is important
to know which social application is necessary to work in the study. The obtained
results are summarized in the table below (n = 302):
A forum is the social application that achieves a higher knowledge level under
study:
Factor Ítem Load Statistical t AVE Cronbach
Composite
reliability
R
2
PRIVP1 0.764 14.287
PRIVP2 0.783 22.342
PRIVP3 0.812 13.223
PRIVPC1 0,804 19.332
PRIVU1 0.877 14.112
PRIVU2 0.721 27.332
PRIVU3 0.833 11.575
PRIVUC1 0,725 21.221
USA1 0.809 13.115
USA2 0.912 33.556
Interactivity
INTERACT1 0,908 11,998 1.000 1.000 1.000 -
UTI1 0.808 12.118
UTI2 0.811 23.429
UTI3 0.789 11.398
UTI4 0,743 22.344
COMP1 0.834 55.332
COMP2 0.853 39.223
COMP3 0.812 51.332
COMP4 0.765 50.332
COMP5 0.811 39.338
AUT1 0.811 2.221
AUT2 0.901 3.119
ACT 1 0.723 15.992
ACT 2 0.790 24.323
ACT 3 0.784 33.221
ACT 4 0.811 29.332
ACT 5 0.734 25.122
CNCS1 0.832 5.223
CNCS2 0.822 7.011
CNCS3 0.789 7.232
CNMED1 0.897 18.213
CNMED2 0.899 26.887
CCP1 0.709 9.012
CCP2 0.787 10.998
MOTA1 0.810 78.998
MOTA2 0.843 79.011
MOTC1 0.710 81.011
MOTC2 0.878 80.110
Intended use
IU1 1 6.982 0.781 0.711 0.810 0,398
Use of social
appl icati ons
USARED1 1 7.891 0.801 0.809 0.819 0,453
Self
Motivation
0.801 0.865 0.891 0,343
Controlled
motivation
0,71 0,707 0,832 0,397
Media
0,845 0,823 0,854 0,332
Perceived
control
conditions
0.801 0,775 0,732 0,413
Attitude
0.743 0,789 0,712 0,469
Social context
0,721 0,799 0,798 0,381
Compatibility
0.722 0,798 0.811 -
Self-efficacy
0.789 0,721 0.899 -
Usability
0.719 0,717 0,842 -
Utility
0.764 0.789 0,855 -
0.783 0,814 -
Th i rd P a r t
Protection
0.711 0.732 0,811 -
Self Privacy
0.732
Social
Application
Forums Facebook Linked‐In
NeverUsed 3,97% 11,26% 18,54%
Beginner 8,28% 22,52% 40,73%
Competent 67,22% 54,97% 32,12%
Expert 20,53% 11,26% 8,61%
Knowledge
Level
12
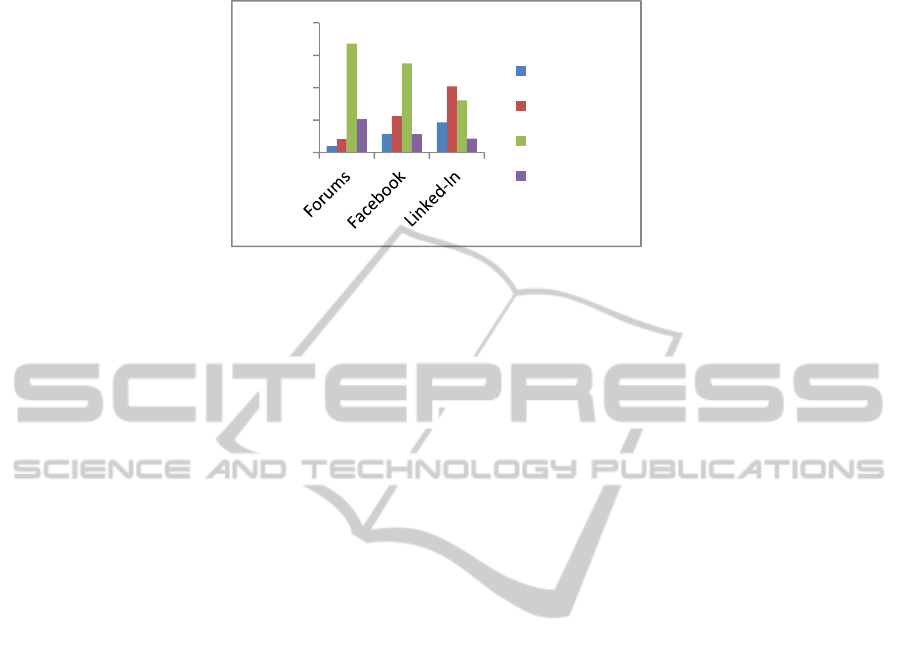
Fig. 2. Individual results about social applications knowledge level.
Main conclusions are divided between variables which have a positive impact in
the intention of use and the variables which have a negative impact. Firstly, since test
results show that all variables of Theory of Planned Behaviour and Self-
Determination Theory: attitude, subjective norm and perceived control, provide an
important and significant component of the intention to conduct and perform in
herself from certain behaviour. On the one hand the feeling of "perception" is
remarkable, being motivation as a clearly secondary sense. Safety is presented as the
main element in the aspects that have a negative contribution; in this case the zeal in
the personal data is very important balancing equal parts: fear of job loss against
potential negligence, and fear the potential violation of private data, themselves or
others, arranged in the network.
By contrast, elements such as usability, usefulness or self-efficiency, enhance
the use of social applications in order to be a tool for sharing knowledge improving
software developments. As important conclusions and issues to work are taken from
the following key points of the research on the software developers (in order of
appearance on the issues referenced in the survey):
Forum is the most used social application.
Social developers have a weak knowledge of safety policies and have been
rarely configured. Only 50% people under study report having ever done. This
is the first aspect to improve. To mitigate this aspect, it is proposed to set up
training programs in order to show possibilities which security levels in these
kinds of applications can offer. Myths and misunderstandings will be eliminate
in many cases and will definitely help them.
The self-privacy of software developers is an issue that stops the use of social
applications for any professional aspect. A large majority of workers refuses to
use them because they do not control what is done with the information that
there is in this kind of applications. This, after analyzing the full study, has a
negative effect on the attitude towards the use and perceived behavioural
control, which also directly impact on the intention to perform the behaviour.
The main highlighted factor in the interviews has been the lack of knowledge
about these technical issues: configuration and knowledge of data treatment.
Two initiatives are proposed to mitigate this issue. The first one is to share
between users and service provider. The second one is to start the training way
in order to fill knowledge gaps.
0,00%
20,00%
40,00%
60,00%
80,00%
NeverUsed
Beginner
Competent
Expert
13

In the service provider case, two main tasks are proposed: firstly clarify the
security interfaces with illustrative examples of what can be done and what not
from activation or cancellation of each of the security sections. Secondly, it is
proposed the creation of default configuration profiles for professional activities
that help their activation and use. This would provide a value that can be
quantified in confidence created in the link that connects the user to the
provider via the application.
The protection of security linked to the security of user data on which an
intervention is developed is critical. Two important aspects are concentrated
around this point. On the one hand the potential violation of user data, not
software developer personal data, without knowing the use that service provider
will be given. Furthermore, the possible negligence that could commit to make
public although the purpose of such disclosure is proactive in looking for a
solution that help user interests.
To mitigate both points raises the following proposals. Firstly, users would be
informed how to work in order to be aware of and rate the effort required and
especially the rise of human resources in the service of the resolution of their
case. Secondly, it would create a text to be signed by users seeking help through
which the practitioner is exempt from any liability acquired and got eliminating
susceptibility by professionals towards this issue.
The construct related to the "Usability" positive impacts on the attitude to use a
social application as a tool. Such systems, in particular forums, have permeated
public common knowledge so much that its use has become common
knowledge. Therefore a large majority of the population in general, and
certainly a majority representative of the group involved in the study, expressed
his comfort towards the use of these tools through Internet. The front ends,
performed considering some usability rules, have become commonplace.
Desings, that are developed based on intuition from the literature, are merely
imitations of interfaces that, due to commercial fashions, have spread among
the population. Therefore if we stick to technical definitions of usability, are
unlikely to be met strictly. Perhaps the correct term to use would be
"familiarity".
As previously mentioned, this factor positively influences the attitude,
positively influences the intention to perform the behaviour and implementation
of the same by direct action.
The "Interactivity" factor has no influence on the main elements of the used
theories from the results. Its impact on the attitude toward performing the
behaviour is minimal. The vast majority of the subjects involved in the study
did not consider the interactivity that networks provide is to be decisive in their
use.
To mitigate this effect and ensure that this factor is an incentive to increase the
intention to use, we propose show real examples to software developers the
benefit of interactivity among professionals. To show habitual patterns and
typical cases in which they see themselves in their daily activity helping to
verify that this is a valid solution to improve performance. Such interactivity as
technological element is something that is passed. The solutions allow a high
14

degree of interaction among humans in order to share any type of knowledge,
while avoiding the need to be in the same location.
All these advantages should be shown to the professionals in order to put in
relevance the access to delocalized knowledge, in this case, focusing on the
experience of other professionals who would be available to other people.
According to the initial hypothesis, the construct that should have a more
important and positive impact on the other elements of the research model, is
"Utility" without any doubt. Since results show, the utility is a concept that has
been embraced by software developers. More than 66% are aware and agree
with social applications as support for improving the results of its operations.
Therefore the attitude to use is positive and a first component of our initial
hypothesis is confirmed. Professionals see a lot of advantages.
In this research, the problem presented is how to implement this assistance
proposed to them. That is, although they see many advantages and benefits in
the use of these applications, when they are proposed to include them in their
daily routine tasks, answers are negative or neutral. Therefore, in the full model
analysis and taking into account all contributions, we must make a distinction
that justifies the neutral contribution to this construct. The sum of these two
components, theoretical and practical utility, is neutral, offsetting the resulting
weights of responses on both points of view.
Since the results of the survey, the construct "Compatibility" has not
contribution in the attitude to perform the behaviour. The group of software
developers do not consider neither positive nor negative. Most of them perceive
it from the indifference. This factor has been measured mainly about their daily
tasks. Professionals have not considered as a relevant one and that is the reason
because the indicators have pointed out that it is not a factor that significantly
influences the attitude. Therefore it has not impact in the intention to use.
As action to mitigate this perception, again training programmes are proposed.
The use of nowadays cases and simple examples help them to undertand. The
cases should show sectors or occupations where the use of such applications
could provide significant added value, and due to compatibility reasons with
their profession, their implementation is not possible.
"Auto-Efficiency" shows that software developers perceive that they have the
knowledge necessary to use and enjoy the benefits that these tools proposed in
their professional duties. His contribution to perceived behavioural control
element is positive and this can be seen in the increase of the intention to use.
Finally we present the motivation analysis in the full research model to predict the
intention to use. For this professional group, motivations have not a positive impact
to the intention to perform behaviour. This fact contradicts the research hypothesis in
which software developers are supposed to find the possibility of improving their
work as an incentive to use such online tools.
Firstly self-motivation does not exist. Hence, the lack of impact on the intention
to perform the behaviour. To mitigate this element of the model, it should work
on motivating staff through professional development in order to improve their
professional competences. The skill development is a common strategy used by
human resources departments in large companies. Among several competences,
15

the use of new technologies to improve professional performance should be the
goal to mitigate the absence of autonomous motivation in this group.
Secondly controlled motivation is presented. As previously mentioned, this
motivation is based on making demands from the top of the organization. In this
aspect, user survey shows that this professional group is against any kind of this
motivation. Therefore this factor will have a negative impact. The frequency of
performing the behaviour will not rise.
In terms of mitigation of this aspect, an imposition of a superior must be seen as
a risk or a threat of being fired. From this start point, the intention to use will be
clearly identified positively.
5 Considerations and Future Research
The main considerations to take into account in this research are: firstly, software
developers group is an important professional group that has a manifest disregard of
the safety aspects of these applications can provide them. Being a technical field far
away from his common one, being a new technology related to internet and where
they have committed many crimes on the violation of privacies, all this makes the
intention of use of social applications by software developers in order to improve
their productivity is weak.
Therefore, it is too complicated to share high-level software knowledge among
them. In these cases, it is obvious that the first step would be to provide them the
right knowledge from a professional trainer to enable them to become confident
enough to develop their work with guarantees and also improve their performance
through shared knowledge.
Next steps in this research will be to work with other professional groups who
share the characteristic of work directly related to groups of people. The teacher staff
of one university is the next start point to research and contrast this predict model. In
this case we will work on prediction models about behaviours related to the use of
social networks to share information and experiences in order to improve the
relationship with the student, their evaluations, tests, etc.
References
1. ONTSI (2012). “Servicios utilizados por los usuarios de Internet”.
2. Hartshorne, R., & Ajjan, H. (2009). Examining student decisions to adopt Web 2.0
technologies: Theory and empirical tests. [Advance online publication]. Journal of
Computing in Higher Education.
3. Conole, G. and McAndrew, P. (2010), A new approach tosupporting the design and use of
OER: Harnessing the power of web 2.0.
4. Orehovacki, T., G. Bubas & M. Konecki. (2009). Web2.0 in Education and Potential
Factors of Web 2.0 Use by Students of Information Systems. 31
st
International Conf. on
Information Technology Interfaces, 2009. ITI '09. Proceedings of the ITI 2009. pp: 443–448
5. Gill, L. & Dalgarno, B. (2008). Influences on pre-service teachers‟preparedness to use
ICTs in the classroom. Accepted paper for 'Hello! Where are you in the landscape of
16

educational technology?’ 25
th
Annual conf. of the Australasian Society for Computers in
Learning in Tertiary Education (ASCILITE), Deakin University, Melbourne, Australia
6. Ajzen, I. (2002). Perceived behavioural control, self-efficacy, locus of control, and the
theory of planned behaviour. Journal of Applied Social Psychology, 32, 665-683.
7. J. A. Barnes, (1954). “Class and committees in a Norwegian islan parish”. Department of
Sociology, London School of Economics.
8. Chatzisarantis, N. L., Hagger, M. S., Biddle, S. J. H., Smith, B., & Wang, C. K. (2003). A
meta-analysis of perceived locus on causality in expercise, sport, and physical education
contexts. Journal of Sport and Exercise Psychology, 25, 284-306.
9. Hagger, M. S., & Chatzisarantis, N. L. (2007). Intrinsic motivation and self-determination
in exercise and sport. Champaigne, IL: Human Kinetics.
10. Ryan, R. M., & Deci, E. L. (2000). Self-determination Theory and the facilitation of
intrinsic motivation, social development, and Well-being. American Psychologist, 55, 68-78.
11. Deci, E. L., & Ryan, R. M. (2000). The 'what' and 'why' of goal pursuits: Human needs and
the self-determination of behaviour. Psychological Inquiry, 11, 227-268.
12. Edmunds, J., Ntoumanis, N., & Duda, J. L. (2007). Adherence and well-being in
overweight and obese patients referred to an exercise on prescription scheme: A self-
determination theory perspective. Psychology of Sport and Exercise, 8, 722-740.
13. Edmunds, J., Ntoumanis, N., & Duda, J. L. (2007). Perceived autonomy support and
psychological need satisfaction as key psychological constructs in the exercise domain. In
M. Hagger & N. L. D. Chatzisarantis (Eds.), Self-determination in exercise and sport (pp.
35-51). Champaign, IL: Human Kinetics.
14. Vansteenkiste, M., Sierens, E., Soenens, B., & Lens, W. (2007). Willen, Moeten En
Structuur: Over Het Bevorderen Van Een Optimaal Leerproces. [To Want, To Have and
Structure: On Faciliating an Optimal Learning Process]. Begeleid Zelfstandig Leren, 37,1-27
15. Sheldon, K. M., & Elliot, A. J. (1999). Goal striving, need-satisfaction, and longitudinal
well-being: The self-concordance model. Journal of Personality and Social Psychology,
76, 482-497.
16. Hagger, M. S., Chatzisarantis, N. L., & Biddle, S. J. H. (2002). The influence of
autonomous and controlling motives on physical activity intentions within the theory of
planned behaviour. British Journal of Health Psychology, 7, 283-297.
17. Chatzisarantis, N. L., Hagger, M. S., Biddle, S. J. H., & Karageorghis, C. (2002). The
cognitive processes by which perceived locus of causality predicts participation in physical
activity. Journal of Health Psychology, 7, 685-699.
18. Hagger, M. S., & Chatzisarantis, N. L. (2009). Integrating the theory of planned behaviour
and self-determination theory in health behaviour: A meta-analysis. British Journal of
Health Psychology, 14, 275-302.
19. Sadaf, A., Newby, T. J., & Ertmer, P. A. (2012). An empirical investigation of the factors
that influence pre-service teachers’ intentions to use Web 2.0 technologies in the
classroom using decomposed theory of planned behaviour. Journal of Research on
Technology in Education, 45 (2), 171-195.
20. Hambleton, R. K. (1996). Adaptación de tests para su uso en diferentes idiomas y culturas:
fuentes de error, posibles soluciones y directrices prácticas. En J. Muñiz (coord.):
Psicometría. Madrid: Universitas.
21. Hambleton, R. K. (2005). Issues, designs and technical guidelines for adapting tests into
multiple languages and cultures. R. K. Hambleton, P. F. Merenda y S.D. Spielberger
(eds.): Adapting educational and psychological tests for cross-cultural assessment (pp. 3-
38). New Jersey: Lawrence Erlbaum Associates.
22. Ringle Christian M, Wende Sven, Will Alexander, (2005). SmartPLS 2.0. Hamburg.
23. Chin, W. W. (1998). The partial least squares approach for structural equation modeling.
In G. A. Marcoulides (Ed.), Modern methods for business research (pp. 295–236).
London: Lawrence Erlbaum Associates.
17

24. Wankel, L. M. (1993) “The importance of enjoyment to adherence and psychological
benefits from physical activity”. International Journal of Sport Psychology, 24, 151-169.
25. Ajzen, I. (2001). Nature and operation of attitudes. Annual Review of Psychology, 52(1),
27–58.
26. Ajzen, I. (1991). “The theory of planned behaviour”, Organizational Behaviour and
Human Decision Processes, 50, pp. 179-211.
27. Carsten Röcker (2010). “Why Traditional Technology Acceptance Models Won't Work for
Future Information Technologies?” World Academy of Science, Engineering and
Technology, 65.
28. Lee, J., Cerreto, F. A., & Lee, J. (2010). “Theory of Planned Behaviour and Teachers'
Decisions Regarding Use of Educational Technology”. Educational Technology &
Society, 13 (1), 152–164.
29. Millie J. Darvell, B.Behav.Sc, Shari P. Walsh, Ph.D., and Katherine M. White, Ph.D.
(2011). “Facebook Tells Me So: Applying the Theory of Planned Behaviour to Understand
Partner-Monitoring Behaviour on Facebook”. Cyberpsychology, Behaviour and Social
Networking, Volume 14, Number 12.
30. Ming-Chi Lee and Tzung-Ru Tsai (2010). “What Drives People to Continue to Play
Online Games? An Extension of Technology Model and Theory of Planned Behaviour”.
INTL. Journal of Human-Computer Interaction, 26(6), 601–620.
31. Susan Michei, Wendy Hardeman, Tom Fanshawe, A. Toby Prevost, Lyndsay Taylor &
Ann Louise Kinmonth (2008). “Investigating theoretical explanations for behaviour
change: The case study of ProActive”. Psychology and Health, 23(1): 25–39.
32. Nele Jacobs, Martin S. Hagger, Sandra Streukens, Ilse De Bourdeaudhuij and Neree Claes
(2010). “Testing an integrated model of the theory of planned behaviour and self-
determination theory for different energy balance-related behaviours and intervention
intensities”. British Journal of Health Psychology (2011), 16, 113–134.
33. Yann Truong (2009). “An Evaluation of the Theory of Planned Behaviour in Consumer
Acceptance of Online Video and Television Services”. Electronic Journal Information
Systems Evaluation Volume 12 Issue 2 (177 – 186).
34. Ayesha Sadaf, Timothy J. Newby and Peggy A. Ertmer (2012). “Exploring Factors that
Predict Preservice Teachers’ Intentions to Use Web 2.0 Technologies Using Decomposed
Theory of Planned Behaviour”. JRTE, Vol. 45, No. 2, pp. 171–195.
35. Netta Weinstein & Richard M. Ryan (2011). “A Self-determination Theory Approach to
Understanding Stress Incursion and Responses”. Stress and Health 27: 4–17.
36. Dirk Heerwegh and Geert Loosveldt (2009). “Explaining the intention to participate in a
web survey: a test of the theory of planned behaviour”. International Journal of Social
Research Methodology, Vol. 12, No. 3, 181–195.
37. Sarah McLachlan & Martin S. Hagger (2011). “The Influence of Chronically Accessible
Autonomous and Controlling Motives on Physical Activity within an Extended Theory of
Planned Behaviour”. Journal of Applied Social Psychology, 41, 2, pp. 445–470.
38. Shirley Taylor and Peter A. Todd (1995). “Understanding Information Technology Usage:
A Test of Competing Models”. Information Systems Research (6:2), pp 144-176.
39. Segal, Judith (2009). Software development cultures and cooperation problems: a field
study of the early stages of development of software for a scientific community. Computer
Supported Cooperative Work, 18(5-6), pp. 581–606.
40. Lei, Pui-Wa, & Wu, Qiong. (2007). “An NCME Instructional Module on Introduction to
Structural Equation Modeling: Issues and Practical Considerations.” http://ncme.org/
linkservid/
47EFEB5A-1320-5CAE-6EC90BFDF09AA39E/showMeta/0/, downloaded: June
14th 2014.
41. Toth, Jozsef (2013). “Trust – Networking – Innovation”. Proceedings of the 7th
International Management Conference "New Management for the New Economy",
November 7th-8th, Bucharest, Romania
18
