
QoS- and Security-aware Composition of Cloud Collaborations
Olga Wenge, Ulrich Lampe and Ralf Steinmetz
Multimedia Communications Lab (KOM), TU Darmstadt, Rundeturmstr. 10, 64283 Darmstadt, Germany
Keywords:
Cloud Computing, Collaboration, Quality of Service, Security.
Abstract:
While cloud computing promises virtually unlimited resource supplies, smaller providers may not be able to
offer sufficient physical IT capacity to serve large customers. A solution is cloud collaborations, in which
multiple providers unite forces in order to conjointly offer capacities in the market. Unfortunately, both the
QoS and security properties of such collaborations will be determined by the “weakest link in the chain”,
hence resulting in a trade-off between the cumulative capacity and the non-functional characteristics of a cloud
collaboration. In this position paper, we examine how cloud collaborations can be optimally composed in a
QoS- and security-aware fashion within a market scenario involving multiple cloud providers and users. We
propose a Mixed Integer Programming-based exact optimization approach named CCCP-EXA.KOM. Based
on a quantitative evaluation, we find that the practical applicability of CCCP-EXA.KOM is limited to small-
scale problem instances and conclude that the development of tailored heuristic approaches is required.
1 INTRODUCTION
Cloud computing promises to supply virtually unlim-
ited IT capacities in a scalable, pay-as-you-go fash-
ion (Buyya et al., 2009). Yet, specifically smaller
providers may not be able to satisfy the resource de-
mands of large customers on their own due to in-
sufficient data center capacity. A solution lies in
cloud collaborations, i. e., the cooperation of multiple
providers to conjointly satisfy user demands. Unfor-
tunately, such cloud collaborations have both Quality
of Service (QoS) and security implications: since a
user may potentially be served by any provider within
a collaboration, the non-functional service attributes
– e. g., availability, latency, or data center location –
will be determined by the “weakest link in the chain”,
i. e., the provider with the lowest guarantees.
Take the example of two providers, one of which
uses encryption for data storage and one which does
not. Once these providers join forces within a collab-
oration and act as one common provider, data may be
stored at either one of them. Hence, the collabora-
tion cannot be assumed to offer data encryption, even
though the data may in fact physically reside with the
first provider, i. e., the one which applies encryption.
A similar problem occurs if two providers reside in
different jurisdictions, such as the European Union
(EU) and the United States, where data privacy laws
substantially differ (Wenge et al., 2012).
Yet, given the wide range of legal and regulatory
requirements that apply in many industries, a cloud
user faces certain requirements in choosing his/her
cloud provider, and these requirements may not be
fulfilled once two or more providers join forces within
a collaboration. Based on this scenario, we exam-
ine the Cloud Collaboration Composition Problem
(CCCP) in the work at hand. Our focus is on a bro-
ker within the cloud market, who aims to maximize
his/her profit through the composition of cloud col-
laborations from a set of providers and assignment of
users to these collaborations. In that process, QoS and
security requirements should also be satisfied.
This work introduces the CCCP as a new research
problem in the context of cloud computing. The pa-
per also presents a formal optimization model, which
permits the computation of exact, i.e., profit-optimal,
solutions for specific problem instances.
The remainder of this paper is structured as fol-
lows: In Section 2, we describe the problem in de-
tail and introduce formal notations. Based on this,
the subsequent Section 3 introduces an exact opti-
mization approach, called CCCP-EXA.KOM, which
is quantitatively evaluated in Section 4. Section 5
gives an overview of related work, and Section 6 con-
cludes the paper with a summary and outlook.
578
Wenge O., Lampe U. and Steinmetz R..
QoS- and Security-aware Composition of Cloud Collaborations.
DOI: 10.5220/0004940405780583
In Proceedings of the 4th International Conference on Cloud Computing and Services Science (CLOSER-2014), pages 578-583
ISBN: 978-989-758-019-2
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

2 FORMAL PROBLEM
STATEMENT
In our work, we take the perspective of a cloud bro-
ker, who is acting within a cloud market. This cloud
market consists of a set of cloud providers and a set
of users, formally denoted as P = {1, 2, . . . , P
#
} and
U = {1, 2, . . . , U
#
}, respectively.
Each user u ∈ U exhibits a certain resource de-
mand of RD
u
∈ R
+
units, for which he/she is will-
ing to pay a total of M
+
u
∈ R
+
monetary units. Fur-
thermore, each cloud provider p ∈ P is able to pro-
vide a resource supply of RS
p
∈ R
+
units at a to-
tal cost of M
−
p
∈ R
+
. Please note that resource de-
mands and supplies could also be expressed in a
multi-dimensional fashion, i. e., with respect to differ-
ent resource types. However, for the sake of simplic-
ity, we assume one-dimensional resource constraints
at this point, a notion that is also followed in related
publications (Hans et al., 2013).
Consumption and provision of services is sub-
ject to certain QoS and security constraints, which
we refer to by the common term of non-functional
constraints. Specifically, we assume two sets, A =
{1, 2, . . . , A
#
} and
ˆ
A = {1, 2, . . . ,
ˆ
A
#
}, of quantitative
and qualitative non-functional attributes. Quantitative
attributes represent numerical properties, e. g., avail-
ability or latency. In contrast, qualitative attributes
correspond to nominal properties, e. g., data center lo-
cation in the European Union or adherence to a certain
security policy.
The cloud providers make certain guarantees with
respect to the non-functional attributes. For each
quantitative attribute a ∈ A, the value guaranteed by
provider p ∈ P is denoted as AG
a, p
∈ R. For each
qualitative attribute ˆa ∈
ˆ
A, the corresponding infor-
mation is given by
ˆ
AG
ˆa, p
∈ {0, 1}.
Inversely, the cloud users specify certain require-
ments concerning the non-functional attributes. With
respect to each quantitative attribute a ∈ A, the value
required by user u ∈ U is denoted as AR
a,u
∈ R.
Likewise,
ˆ
AR
ˆa,u
∈ {0, 1} denotes the requirement for
each qualitativeattribute ˆa ∈
ˆ
A, i. e., indicates whether
this attribute is mandatory or not. Without loss of
generality, we assume that the users specify lower
bounds (e. g., minimum availability) on their quan-
titative non-functional requirements. Upper bounds
(e.g., maximum latency) can be easily incorporated
into the model by negation of the respective values.
As it has been briefly explained in the previous
section, the challenge for the cloud broker consists in
composing cloud collaborations, consisting of multi-
ple cloud providers, and subsequently assigning users
to them. In that process, the objective for the bro-
Figure 1: Tangible example of a CCCP instance with four
users and providers.
ker is to maximize his/her profit, i. e., the difference
between the revenue from the served cloud users and
the spending on the incorporated cloud providers. As
most important constraint, each collaboration should
obviously offer sufficient resource supplies to serve
the assigned users. The process is further subject to
the constraint that the QoS and security requirements
of each user are fulfilled by the cloud collaboration to
which he/she has been assigned.
A tangible, simplified example for a CCCP in-
stance is provided in Figure 1. The instance ex-
hibits four users and providers with different re-
source demands/supplies and non-functional require-
ments/guarantees, respectively. In the example,
providers P
2
and P
4
form a collaboration, which en-
ables them to conjointly serve users U
1
and U
2
un-
der the given constraints. Both providerssubstantially
profit from the collaboration, since their combined re-
source supply permits to serve larger customers and
allows to achieve a higher degree of resource utiliza-
tion.
3 OPTIMIZATION APPROACH
CCCP-EXA.KOM
Based on the notations that were introduced in the
previous section, the CCCP can be transformed into
an optimization model. The result is given in Model 1
and will be explained in the following.
To start with, x
u,c
and y
p,c
are the main deci-
sion variables in the model (cf. Equation 11). They
are defined as binary and indicate whether user u or
provider p, respectively, has been assigned to collab-
oration c or not. As additional axillary decision vari-
QoS-andSecurity-awareCompositionofCloudCollaborations
579

ables, we introduce y
′
p,c
, which are also binary and
serve as complement to y
p,c
, hence indicating the non-
assignment of a provider p to a collaboration c. Fur-
thermore, z
a,c
and ˆz
ˆa,c
are specified (cf. Equation 12).
They are defined as real and binary, respectively, and
represent the cumulative value of the non-functional
property a or ˆa, respectively, for collaboration c. The
variables x and y are referred to as main decision vari-
ables, since they have a direct impact on the objective
function. In contrast, y
′
, z, and ˆz only have an indirect
influence.
As outlined before, the objective consists in profit
maximization (cf. Equation 1). That is, the difference
between the revenue from the served cloud users and
the spending on the used cloud providers should be
maximized, depending on the values of the decision
variables. Please note that other objectives, such as
maximizing the number of served users or the overall
resource utilization, may easily be incorporated into
the optimization model as well. However, given the
general idea of a competitive cloud market, our initial
focus is placed on monetary objectives.
Equations 2 and 3 make sure that each user and
provider is assigned to not more than one collabo-
ration. Thus, the broker may opt to not satisfy cer-
tain users’ demands, but also to not exploit cloud
providers as part of a collaboration. Equation 4 de-
termines the inverse variable y
′
p,c
for each decision
variable y
p,c
. This definition is used in the follow-
ing two Equations 6 and 7. They determine the cu-
mulative non-functional values for quantitative and
qualitative attributes, respectively. Both equations are
formulated such that quantitative properties are given
by the “worst” value among all providers in a certain
collaboration, i. e., the “weakest link in the chain”.
Equations 8 and 9 make sure that users can only be
assigned to such collaborations that make sufficient
non-functional guarantees, given the users’ specific
non-functional requirements. Lastly, Equation 10 de-
fines a set of potential cloud collaborations. The un-
derlying notion for the given definition is that no user
or provider will be assigned to more than one collab-
oration (recall Equations 2 and 3). Hence, the maxi-
mum number of collaborations is given by the number
of users or providers, whichever is lower.
Based on the given model, it can easily be seen
that the CCCP constitutes a Mixed Integer Program
(MIP), i. e., a special form of Linear Program (LP)
that features both integer (in this case, binary) and
natural decision variables. Thus, the problem can
be solved using off-the-shelf optimization algorithms,
such as branch-and-bound (Hillier and Lieberman,
2005), in order to obtain an exact (i. e., profit maxi-
mal) solution.
While branch-and-bound is known to perform
very well on many Integer Program (IP) and MIP
problems, it is ultimately still based on the principle
of enumeration (Hillier and Lieberman, 2005). Thus,
in the worst case, the computationalcomplexity of ob-
taining an exact solution grows with the size of the
solution space. In the specific case of the CCCP, this
translates into an exponential growth with the prob-
lem size, i.e., the number of considered providers and
users.
4 EVALUATION
To assess the practical applicability of our proposed
approach CCCP-EXA.KOM, we have prototypically
implemented it in Java 7. In order to transfer Model 1
into a programmatic representation, we use the free
JavaILP framework
1
. While this potentially permits
for the application of different backend solver frame-
work, we have selected the commercial IBM ILOG
CPLEX framework
2
as default due to its favorable
performance (Meindl and Templ, 2012) and its pop-
ularity in related research, e.g., (Hans et al., 2013;
Mashayekhy and Grosu, 2012).
4.1 Evaluation Setup and Procedure
The main objective of our evaluation is to assess the
required computation time of CCCP-EXA.KOM for
different problem sizes. This allows us to judge the
applicability of the proposed approach under practi-
cal conditions, where time constraints in the decision
process play an important role. Thus, formally, we
regard computation time as the dependent variable of
our evaluation.
As independent variables, we include the number
of considered users and providers, i. e., U
#
and P
#
.
In contrast, the number of quantitative and qualita-
tive non-functional attributes were fixed (A
#
= 1 and
ˆ
A
#
= 1); hence, they constitute controlled variables.
This is justified by two aspects: First, these variables
are likely also predefined in practice. Second, they
do not have an impact on the number of decision
variables and hence, the size of the solution space.
Each specific combination of U
#
and P
#
results in a
test case. For each test case, we created 100 specific
CCCP instances with the according dimensions.
The parameter values or distributions that were
used in the problem generation process are summa-
1
http://javailp.sourceforge.net/.
2
http://www.ibm.com/software/integration/optimization/
cplex-optimizer/.
CLOSER2014-4thInternationalConferenceonCloudComputingandServicesScience
580

Model 1: Cloud Collaboration Composition Problem
Max. Pr(x, y, y
′
, z, ˆz) =
∑
u∈U,c∈C
x
u,c
× M
+
u
(1)
−
∑
p∈P,c∈C
y
p,c
× M
−
p
such that
∑
c∈C
x
u,c
≤ 1 ∀u ∈ U (2)
∑
c∈C
y
p,c
≤ 1 ∀p ∈ P (3)
y
p,c
+ y
′
p,c
= 1 ∀p ∈ P, ∀c ∈ C (4)
∑
u∈U
x
u,c
× RD
u
≤
∑
p∈P
y
p,c
× RS
p
∀c ∈ C (5)
z
a,c
≤ y
p,c
× AG
p,a
+ y
′
p,c
× max
p∈P
(AG
p,a
) (6)
∀p ∈ P, ∀c ∈ C, ∀a ∈ A
ˆz
ˆa,c
≤ y
p,c
×
ˆ
AG
p, ˆa
+ y
′
p,c
(7)
∀p ∈ P, ∀c ∈ C, ∀ ˆa ∈
ˆ
A
z
a,c
≥ x
u,c
× AR
u,a
∀u ∈ U, ∀c ∈ C, ∀a ∈ A (8)
ˆz
ˆa,c
≥ x
u,c
×
ˆ
AR
u, ˆa
∀u ∈ U, ∀c ∈ C, ∀ ˆa ∈
ˆ
A (9)
C = {1, 2, . . . , min(P
#
, U
#
)} (10)
x
u,c
∈ {0, 1} ∀u ∈ U, ∀c ∈ C (11)
y
p,c
∈ {0, 1} ∀p ∈ P, ∀c ∈ C
y
′
p,c
∈ {0, 1} ∀p ∈ P, ∀c ∈ C (12)
z
a,c
∈ R ∀a ∈ A, ∀c ∈ C
ˆz
ˆa,c
∈ {0, 1} ∀ ˆa ∈
ˆ
A, ∀c ∈ C
rized in Table 1. The specifications of the non-
functional parameters are based on the notion that
the sole quantitative and qualitative attribute repre-
sent availability (a QoS aspect) and data center lo-
cation in the European Union (a security aspect), re-
spectively. Furthermore, monetary parameters were
set such that higher availability results in quickly in-
creasing values, based on the observation that each
Table 1: Parameter values and distributions used in the
problem instance generation. Abbreviations: Uni – Uni-
form distribution; Ber – Bernoulli distribution.
Param. Value/Distribution
AR
1,u
Uni(0.99, 0.9995)
ˆ
AR
1,u
Ber(0.5)
AG
1, p
Uni(0.995, 0.9995)
ˆ
AG
1, p
Ber(0.5)
RD
u
Uni(1000, 5000)
RS
p
Uni(1000, 5000)
M
+
u
α
u
× RD
u
× log
10
(1− AR
1,u
)
2
× (1.1
ˆ
AR
1,u
)
M
−
p
β
p
× RS
p
× log
10
(1− AG
1, p
)
2
× (1.1
ˆ
AG
1, p
)
α
u
Uni(1.5, 1.75)
β
p
Uni(1.0, 1.25)
additional “nine” in the availability figure results in
doubled cost (Durkee, 2010). In contrast, a EU data
center location only leads to a moderate increase of
10%, which closely corresponds to the price differ-
ence observed for Eastern U.S. and Ireland-located
Amazon EC2 VM instances (Amazon Web Services,
Inc., 2013).
Following the generation, we computed a solu-
tion to each problem instance using our prototypi-
cal implementation of CCCP-EXA.KOM. In that pro-
cess, we imposed a timeout of 300 seconds (i.e., five
minutes) per problem instance. Based on the result-
ing sample of computation times for the successfully
solved problems, we computed the mean computa-
tion time, as well as the 95% confidence interval.
The evaluation was conducted on a desktop computer,
equipped with an Intel Core 2 Duo E7500 processor
and 4 GB of memory, operating under the 64-bit edi-
tion of Microsoft Windows 7.
4.2 Evaluation Results and Discussion
The results of our evaluation, i. e., the observed mean
computation times per test case, are graphically illus-
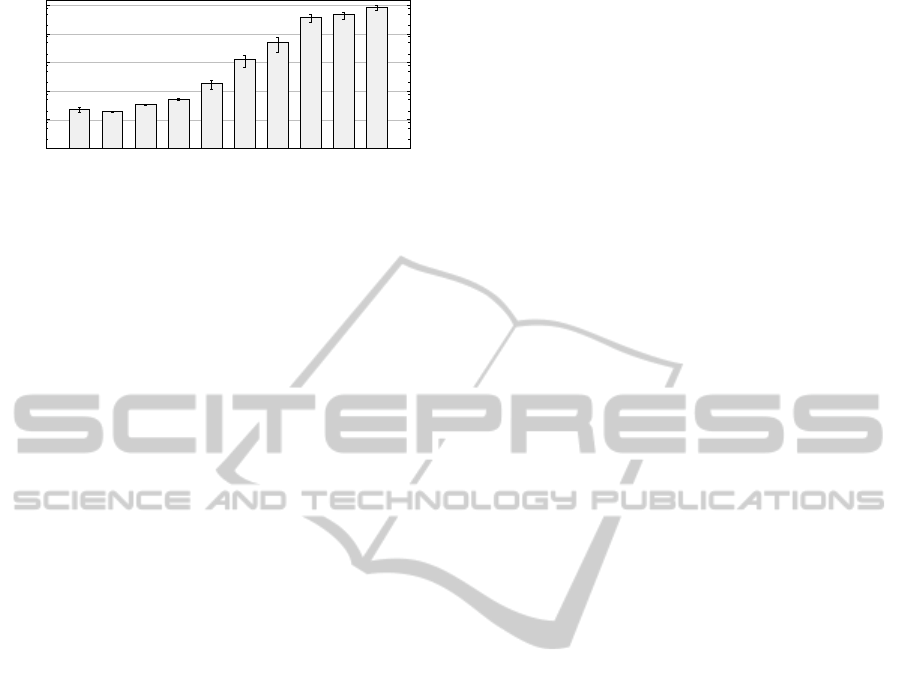
trated in Figure 2. As can be clearly seen, the compu-
tation times quickly increase with the problem size,
i. e., the considered number of users and providers.
The effect is less pronounced for the smallest two
problem classes (with U
#
≤ 6 and P
#
≤ 9); in fact,
for these two test cases, there is no statistically signif-
icant difference in mean computation time observable
at the 95% confidence level. In absolute terms, we
already find absolute computation times in the order
of magnitude of one-hundred seconds and one sec-
ond respectively for the medium-sized test cases with
U
#
≤ 8. For these test cases, increasing the number of
QoS-andSecurity-awareCompositionofCloudCollaborations
581
1
10
100
1000
10000
100000
4, 4
(100)
4, 6
(100)
6, 6
(100)
6, 9
(100)
8, 8
(100)
8, 12
(100)
10, 10
(100)
10, 15
(94)
12, 12
(90)
12, 18
(43)
Computation Time (in ms)
Problem Size U
#
, P
#
(Sample Size)
Figure 2: Evaluation results, i. e., observed mean compu-
tation times (with 95% confidence intervals) for CCCP-
EXA.KOM by test case. Please note the logarithmic scaling
of the ordinate.
providers increases the computation time by a factor
of approximately ten already.
For the four largest test cases (with U
#
≥ 10 and
P
#
≥ 10), the absolute computation times reach the
order of magnitude of seconds and ten seconds. All
observed increases are statistically significant at the
95% confidence level. In addition, the ratio of solved
problem instances sharply drops with growing prob-
lem size. This effect is most notable for the largest
problem class that involves 12 users and 18 providers,
where only 43% of the 100 problem instances could
be solved within the timeout period of five minutes.
Given that the considered problem dimensions are
still relatively small in the context of a large cloud
market, it can be concluded that the practical applica-
bility of the proposed optimization approach CCCP-
EXA.KOM is rather limited. As it has already been
explained before, a broker will likely have to de-
cide on the composition of collaborations under rigid
time constraints, since users likely require resources
at short notice.
Hence, an important future challenge consists in
the development of appropriate heuristics, which per-
mit to trade reductions in computation time against
small degradations in broker profit, and are conse-
quently applicable to practically relevant, large-scale
problem instances. In that context – apart from its
potential application to small-scale problem instances
– CCCP-EXA.KOM can serve as a valuable perfor-
mance benchmark.
5 RELATED WORK
Niyato et al. (Niyato et al., 2011) study the coopera-
tive behavior of multiple cloud providers in order to
cooperate and support the establishment of resource
pools to offer services to public cloud users. The au-
thors present a stochastic LP game model which takes
the random internal demand of cloud providers and a
transferable utility into account to define and commit
the optimal offer of cooperated cloud providers. In
contrast to our work, Niyato et al. do not consider
non-functional constraints, i.e., QoS and security re-
quirements.
In a more recent work, Niyato et al. (Niyato
et al., 2012) examine building coalitions between
cloud providers as a novel approach to optimize the
capacity expansion and maximize the mobile cloud
providers’ monetary benefits. The authors consider
cooperative game theory and the Nash equilibrium
principles in their approach and propose admission
control and revenue sharing strategies for building
cloud provider coalitions and a resource pool for mo-
bile applications. The provided results illustrate im-
provements in cloud providers’ capacity and profit
maximization by entering such cloud coalitions. Sim-
ilar to their previous work, the authors do not consider
non-functionalconstraints, which are an important as-
pect of our work.
Gohad et al. (Gohad et al., 2013) propose a dy-
namic algorithm for forming self-adaptive cloud col-
laborations based on the identifying most appropri-
ate healthy set of cloud provider resources (cloud
provider capabilities and functional abilities at the
SaaS layer), cost modeling and tenancy requirements.
The approach is highlighted with a realistic example.
In contrast to us, Gohad et al. focus on ad-hoc re-
source provisioning, rather than the long-term forma-
tion of cloud collaborations, and do not consider secu-
rity aspects. This specifically includes the cumulative
security properties of cloud collaborations that were a
focal point of our work.
Song et al. (Song et al., 2010) examine the prob-
lem of task selection and allocation to physical ma-
chines in the context of dynamic cloud collabora-
tions. Their objective consists in the balancing of re-
source demands under consideration of different re-
source types, such as CPU and memory. For that
purpose, the authors propose three heuristic optimiza-
tion approaches, and demonstrate that a cooperative
heuristic has benefits with respect to the objective of
balanced resource utilization. In contrast to us, Song
et al. focus on individual cloud providers and do not
regard security requirements.
Mashayekhy and Grosu (Mashayekhy and Grosu,
2012) model a cloud federation formation problem
based on the game theory and formulate a corre-
sponding IP-based optimization approach. In their
model, the authors consider the cooperative provi-
sioning of VM instances and storage by federated
cloud providers. Their objective consists of profit
maximization combined with the formation of stable
coalitions, i.e., coalitions in which cloud providers
do not have a monetary incentive to switch to differ-
CLOSER2014-4thInternationalConferenceonCloudComputingandServicesScience
582

ent coalitions. In contrast to our work, the authors
only consider resource constraints, but do not regard
non-functional requirements. Their work also aims at
low-level VM provisioning, rather than strategic com-
position of collaboration.
Lastly, Hans et al. (Hans et al., 2013) have ex-
amined the cost-efficient selection of cloud data cen-
ters for the delivery of multimedia services. In that
context, the authors propose an exact optimization ap-
proach based on IP. While their work is similar with
respect to the consideration of resource and QoS con-
straints, it focuses on a single cloud provider and does
neither regard the composition of collaborations nor
qualitative non-functional aspects.
In conclusion, to the best of our knowledge, we
are the first to examine the profit-maximal, strate-
gic composition of cloud collaborations under consid-
eration of cumulative non-functional properties that
result from the very formation of these collabora-
tions, i. e., are determined by the “weakest link in the
chain”. Apart from the identification of that specific
problem, our main contribution consists in the pro-
posal of an exact optimization approach, which can
serve as benchmark for future heuristic approaches.
6 SUMMARY AND OUTLOOK
While cloud computing promises access to virtually
unlimited IT resources, the physical infrastructure of
cloud providers is actually limited. Hence, smaller
providers may not be able to serve the demands of
larger customers. A possible solution is cloud collab-
orations, where multiple providers join forces to con-
jointly serve customers. Unfortunately, in such sce-
nario, non-functional QoS and security properties are
determined by the “weakest link in the chain”, render-
ing the process of composing collaborations cumber-
some.
In this work, we introduced the corresponding
Cloud Collaboration Composition Problem. We pro-
posed an initial solution approach named CCCP-
EXA.KOM based on Mixed Integer Programming,
and evaluated it with respect to its computation time
requirements. Our results indicate that exact opti-
mization approaches are only applicable to small-
scale problem instances, thus indicating the need
for the development of custom-tailored heuristic ap-
proaches.
Accordingly, the development of such heuristics
will constitute the primary focus of our future work.
In addition, we plan to extend the proposed model
to cater for more complex non-functional constraints,
such as conditional requirements (e.g., strong data
encryption is only required if data is placed outside
the European Union).
ACKNOWLEDGEMENTS
This work has partly been sponsored by the
E-Finance Lab e.V., Frankfurt a.M., Germany
(www.efinancelab.de.).
REFERENCES
Amazon Web Services, Inc. (2013). Amazon EC2 Pric-
ing, Pay as you go for Cloud Computing Service.
http://aws.amazon.com/en/ec/pricing/.
Buyya, R., Yeo, C. S., Venugopal, S., Broberg, J., and
Brandic, I. (2009). Cloud Computing and Emerging
IT Platforms: Vision, Hype, and Reality for Deliver-
ing Computing as the 5th Utility. Future Generation
Computer Systems, 25(6):599–616.
Durkee, D. (2010). Why Cloud Computing Will Never Be
Free. Queue, 8(4):20–29.
Gohad, A., Ponnalagu, K., Narendra, N. C., and Rao, P. S.
(2013). Towards Self-Adaptive Cloud Collaborations.
In 2013 Int. Conf. on Cloud Engineering.
Hans, R., Lampe, U., and Steinmetz, R. (2013). QoS-
Aware, Cost-Efficient Selection of Cloud Data Cen-
ters. In 6th Int. Conf. on Cloud Computing.
Hillier, F. and Lieberman, G. (2005). Introduction to Oper-
ations Research. McGraw-Hill, 8th edition.
Mashayekhy, L. and Grosu, D. (2012). A Coalitional Game-
Based Mechanism for Forming Cloud Federations. In
5th Int. Conf. on Utility and Cloud Computing.
Meindl, B. and Templ, M. (2012). Analysis of Commercial
and Free and Open Source Solvers for Linear Opti-
mization Problems. Technical report, Technische Uni-
versität Wien.
Niyato, D., Vasilakos, A. V., and Kun, Z. (2011). Re-
source and Revenue Sharing with Coalition Forma-
tion of Cloud Providers: Game Theoretic Approach.
In 11th Int. Symp. on Cluster, Cloud and Grid Com-
puting.
Niyato, D., Wang, P., Hossain, E., Saad, W., and Han, Z.
(2012). Game Theoretic Modeling of Cooperation
Among Service Providers in Mobile Cloud Comput-
ing Environments. In 2012 Wireless Communications
and Networking Conf.
Song, B., Hassan, M. M., and Huh, E.-N. (2010). A
Novel Heuristic-Based Task Selection and Allocation
Framework in Dynamic Collaborative Cloud Service
Platform. In 2nd Int. Conf. on Cloud Computing Tech-
nology and Science.
Wenge, O., Siebenhaar, M., Lampe, U., Schuller, D., and
Steinmetz, R. (2012). Much Ado About Security Ap-
peal: Cloud Provider Collaborations and Their Risks.
In 1st Europ. Conf. on Service-Oriented and Cloud
Computing.
QoS-andSecurity-awareCompositionofCloudCollaborations
583
