
An EDF-based Scheduling Algorithm for Real-time Reconfigurable
Sporadic Tasks
Hamza Gharsellaoui
1
, Mohamed Khalgui
1
and Samir Ben Ahmed
1,2
1
INSAT Institute, University of Carthage, Tunis, Tunisia
2
FST Faculty, University of Tunis El Manar, Tunis, Tunisia
Keywords:
EDF-based Scheduling Algorithm, Real-time Reconfigurable Sporadic Tasks, Intelligent Agent, Automatic
Reconfigurations.
Abstract:
This paper deals with the problem of scheduling the mixed workload of both homogeneous multiprocessor
on-line sporadic and off-line periodic tasks in a hard reconfigurable real-time environment by an optimal
EDF-based scheduling algorithm. Two forms of automatic reconfigurations which are assumed to be applied
at run-time: Addition-Removal of tasks or just modifications of their temporal parameters: WCET and/or
deadlines. Nevertheless, when such a scenario is applied to save the system at the occurrence of hardware-
software faults, or to improve its performance, some real-time properties can be violated at run-time. We
define an Intelligent Agent that automatically checks the system’s feasibility after any reconfiguration scenario
to verify if all tasks meet the required deadlines after a reconfiguration scenario ψ
h
(h ∈ 1..M, we assume
that we have M reconfiguration scenarios), was applied on a multiprocessor embedded system in the case of
shared memory. Indeed, if the system is unfeasible, then the Intelligent Agent dynamically provides precious
technical solutions for users to send sporadic tasks to idle times, by modifying the deadlines of tasks, the
worst case execution times (WCETs), the activation time, by tolerating some non critical tasks m among n
according to the (m,n) firm and a reasonable cost, by sending some tasks from their current processors to
be scheduled in other processors, or in the worst case by removing some soft tasks according to predifined
heuristic. We implement the agent to support these services in order to demonstrate the effectiveness and the
excellent performance of the new optimal algorithm in normal and overload conditions.
1 INTRODUCTION
Nowadays, due to the growing class of portable
systems, such as personal computing and commu-
nication devices, embedded and real-time systems
contain new complex software which are increasing
by the time. This complexity is growing because
many available software development models don’t
take into account the specific needs of embedded
and systems development. The software engineering
principles for embedded system should address
specific constraints such as hard timing constraints,
limited memory and power use, predefined hardware
platform technology, and hardware costs. On the
other hand, the new generations of embedded control
systems are adressing new criteria such as flexibility
and agility (H. Gharsellaoui and BenAhmed, 2012).
For these reasons, there is a need to develop tools,
methodologies in embedded software engineering
and dynamic reconfigurable embedded control sys-
tems as an independent discipline. Each system is a
subset of tasks. Each task is caracterized by its worst
case execution times (WCETs) C
p,ψ
h
i
, an offset (re-
lease time) a
p,ψ
h
i
, a period T
p,ψ
h
i
and a deadline D
p,ψ
h
i
for each reconfiguration scenario ψ
h
, (h ∈ 1..M, we
assume that we have M reconfiguration scenarios)
and on each processor p, (p ∈ 1..K, we assume that
we have K identical processors numbered from 1 to
K), and n real-time tasks numbered from 1 to n that
composed a feasible subset of tasks entitled ξ
old
and
need to be scheduled. The general goal of this paper
is to be reassured that any reconfiguration scenario
ψ
h
changing the implementation of the embedded
system does not violate real-time constraints: i.e. the
system is feasible and meets real-time constraints
even if we change its implementation and to cor-
rectly allow the minimization of the response time
of this system after any reconfiguration scenario
(H. Gharsellaoui and BenAhmed, 2012). To obtain
this optimization (minimization of response time),
377
Gharsellaoui H., Khalgui M. and Ben Ahmed S..
An EDF-based Scheduling Algorithm for Real-time Reconfigurable Sporadic Tasks.
DOI: 10.5220/0004432003770388
In Proceedings of the 8th International Joint Conference on Software Technologies (ICSOFT-EA-2013), pages 377-388
ISBN: 978-989-8565-68-6
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

we propose an intelligent agent-based architecture in
which a software agent is deployed to dynamically
adapt the system to its environment by applying
reconfiguration scenarios. A reconfiguration scenario
ψ
h
means the addition, removal or update of tasks
in order to save the whole system on the occurrence
of hardware/software faults, or also to improve its
performance when random disturbances happen at
run-time. Sporadic task is described by minimum in-
terarrival time P
p,ψ
h
i
which is assumed to be equal to
its relative deadline D
p,ψ
h
i
, and a worst-case execution
time (WCET) C
p,ψ
h
i
for each reconfiguration scenario
ψ
h
and on each processor p. A random disturbance is
defined in the current paper as any random internal
or external event allowing the addition of tasks that
we assume sporadic or removal of sporadic/periodic
tasks to adapt the system’s behavior. Indeed, a hard
real-time system typically has a mixture of off-line
and on-line workloads and assumed to be feasible
before any reconfiguration scenario ψ
h
. The off-line
requests support the normal functions of the system
while the on-line requests are sporadic tasks to
handle external events such as operator commands
and recoveryactions which are usually unpredictable.
For this reason and in this original work, we propose
a new optimal scheduling algorithm based on the
dynamic priorities scheduling Earliest Deadline First
(EDF) algorithm principles on each processor p
and for each dynamic reconfiguration scenario ψ
h
in order to obtain the feasibility of the system at
run-time, meeting real-time constraints and for the
optimization of the response time of this system.
Indeed, many real-time systems rely on the EDF
scheduling algorithm in the case of uni-processor
scheduling theory. This algorithm has been shown
to be optimal under many different conditions. For
example, for independent, preemptable tasks, on a
uni-processor, EDF is optimal in the sense that if any
algorithm can find a schedule where all tasks meet
their deadlines, then EDF can meet the deadlines
(Dertouzos, 1974).
According to (Brocal V., 2011), a hyperperiod
is defined as HP = [ζ, 2 ∗ LCM + ζ], where LCM
is the well-known Least Common Multiple of the
tasks periods and ζ is the largest task offset. This
algorithm, in our original paper assumes that spo-
radic tasks span no more than one hyperperiod of the
periodic tasks HP
(p,ψ
h
)
= [ζ
(p,ψ
h
)
,2*LCM + ζ
(p,ψ
h
)
],
where LCM
p,ψ
h
is the well-known Least Common
Multiple of tasks periods and (ζ
p,ψ
h
) is the largest
task offset of all tasks τ
p,ψ
h
k
for each reconfiguration
scenario ψ
h
on each processor p. The problem is
to find which solution proposed by the agent that
reduces the response time. To obtain these results,
the intelligent agent calculates the residual time R
p,ψ
h
i
before and after each addition scenario and calculates
the minimum of those proposed solutions in order to
obtain Resp
p,ψ
h
k
optimal noted Resp
p,ψ
h
opt
k
. Where
Resp
p,ψ
h
opt
k
is the minimum of the response time of
the current system under study given by the following
equation: Resp
p,ψ
h
opt
k
= min(Resp
p,ψ
h
k,1
, Resp
p,ψ
h
k,2
,
Resp
p,ψ
h
k,3
, Resp
p,ψ
h
k,4
, Resp
p,ψ
h
k,5
, Resp
p,ψ
h
k,6
, Resp
p,ψ
h
k,7
).
To calculate these previous values Resp
p,ψ
h
k,1
,
Resp
p,ψ
h
k,2
, Resp
p,ψ
h
k,3
, Resp
p,ψ
h
k,4
, Resp
p,ψ
h
k,5
, Resp
p,ψ
h
k,6
,
and Resp
p,ψ
h
k,7
, we proposed a new theoretical con-
cepts R
p,ψ
h
i
, S
p,ψ
h
i
, s
p,ψ
h
i
, f
p,ψ
h
i
and L
p,ψ
h
i
for the
case of real-time sporadic operating system (OS)
tasks. Where R
p,ψ
h
i
is the residual time of task σ
p,ψ
h
i
,
S
p,ψ
h
i
denotes the first release time of task σ
p,ψ
h
i
,
s
p,ψ
h
i
is the last release time of task σ
p,ψ
h
i
, f
p,ψ
h
i
denotes the estimated finishing time of task σ
p,ψ
h
i
,
and L
p,ψ
h
i
denotes the laxity of task σ
p,ψ
h
i
for each
reconfiguration scenario ψ
h
and on each processor p.
A tool RT-Reconfiguration is developed at INSAT
institute in university of Carthage, Tunisia, to support
all the services offered by the agent. The minimiza-
tion of the response time is evaluated after each
reconfiguration scenario ψ
h
and on each processor p
to be offered by the agent.
The organization of the paper is as follows.
Section 2 introduces the related work of the proposed
approach and gives the basic guarantee algorithm. In
Section 3, we present the new approach with deadline
tolerance for optimal scheduling theory. Section 4
presents the performance study, showing how this
work is a significant extension to the state of the
art of EDF scheduling and discusses experimental
results of the proposed approach research. Section
5 summarizes the main results and presents the
conclusion of the proposed approach and describes
the intended future works.
2 BACKGROUND
We present related works dealing with reconfigura-
tions and real-time scheduling of embedded systems.
Today, real-time embedded systems are found in
many diverse application areas including; automotive
electronics, avionics, telecommunications, space
systems, medical imaging, and consumer electronics.
In all of these areas, there is rapid technological
progress. Companies building embedded real-time
systems are driven by a profit motive. To succeed,
they aim to meet the needs and desires of their cus-
ICSOFT2013-8thInternationalJointConferenceonSoftwareTechnologies
378

tomers by providing systems that are more capable,
more flexible, and more effective than their competi-
tion, and by bringing these systems to market earlier.
This desire for technological progress has resulted
in a rapid increase in both software complexity and
the processing demands placed on the underlying
hardware (Brocal V., 2011). To address demands for
increasing processor performance, silicon vendors
no longer concentrate wholly on the miniaturisation
needed to increase processor clock speeds, as this
approach has led to problems with both high power
consumption and excessive heat dissipation. Instead,
there is now an increasing trend towards using
multiprocessor platforms for high-end real-time
applications (Brocal V., 2011).
For these reasons, we will use in our work the
case of real-time scheduling on homogeneous multi-
processor platforms. Before presenting our original
contribution, we will present some definitions below.
According to (H. Gharsellaoui and BenAhmed,
2012), each periodic task is described by an initial
offset a
i
(activation time), a worst-case execution
time (WCET) C
i
, a relative deadline D
i
and a period
T
i
.
According to (Buttazzo and Stankovic, 1993),
each sporadic task is described by minimum in-
terarrival time P
i
which is assumed to be equal to
its relative deadline D
i
, and a worst-case execution
time (WCET) C
i
. Hence, a sporadic task set will
be denoted as follows: Sys
2
= {σ
i
(C
i
, D
i
) }, i =
1 to m. Reconfiguration policies in the current
paper are classically distinguished into two strate-
gies: static and dynamic reconfigurations. Static
reconfigurations are applied off-line to modify
the assumed system before any system cold start,
whereas dynamic reconfigurations are dynamically
applied at run-time, which can be further divided
into two cases: manual reconfigurations applied
by users and automatic reconfigurations applied by
intelligent agents (H. Gharsellaoui and BenAhmed,
2012), (X. Wang and L, 2011). This paper focuses
on the dynamic reconfigurations of assumed mixture
of off-line and on-line workloads that should meet
deadlines defined according to user requirements.
The extension of the proposed algorithm should be
straightforward, when this assumption does not hold
and its running time is O(n + m) (T. Tia, 1994).
To illustrate the key point of the proposed dy-
namically approach, we assume that there are K
identical processors numbered from 1 to K, and n
real-time tasks numbered from 1 to n that composed
a feasible subset of tasks entitled ξ
old
and need to be
scheduled. At time t and before the application of the
reconfiguration scenario ψ
h
, each one of the tasks of
ξ
old
is feasible, e.g. the execution of each instance in
each processor is finished before the corresponding
deadline and the tasks are not assumed to be arranged
in any specific order.
Every processor p assigns a set of periodic tasks
TS
p
= {τ
p
1
, τ
p
2
,...,τ
p
n
}. This allocation is made with
an allowance algorithm at the time of the design,
for example by using one of the well known tech-
niques: first-fit (FF), next-fit (NF), best-fit (BF),
worst-fit (WF). These tasks are independent and can
be interrupted at any time. Every task τ
p
i
has an
execution time (Worst Case Execution Time) C
p
i
, one
period T
p
i
, a deadline D
p
i
which is assumed to be
less than or equal to its period, e.g. D
p
i
≤ T
p
i
. Every
task instance k has to respect its absolute deadline,
namely the k
th
authority of the task τ
p
i
, named τ
p
i,k
must be completed before time D
p
i,k
= (k-1)T
p
i
+ D
p
i
.
We express all the measures of time (e.g. periods, the
deadlines, the calculations) as being multiple of the
tick of the processor clock. Every processor p will
execute its tasks in local by using EDF, it means that
the priorities P
p
i
of periodic tasks are dynamic and the
scheduler guarantees that every instance of every task
will run before its deadline. These tasks are handled
by a global scheduler (GS), which assigns them to
processors by using the state informations of the
local schedulers. Moreover, under EDF scheduling,
a task will fit on a processor as long as the total
utilization of all tasks assigned to that processor does
not exceed unity (the total utilization factor = 1).
Finally, for reasons of simplicity, we assume that all
the overheads of context exchange, scheduling of
tasks, the preemption of the tasks and the migration
cost of the tasks are equal to zero.
We assume now the arrival at run-time of a sec-
ond subset ξ
new
which is composed of m real-time
tasks at time t
1
(t
1
= t + ∆t). We have a system
Current
Sys
(t
1
) composed of n+m tasks. In this case a
reconfiguration scenario ψ
h
is applied. The reconfig-
uration of the system Sys
ψ
h
means the modification
of its implementation that will be as follows at time t
1
:
ξ
ψ
h
= Current
ψ
h
Sys
(t
1
) = ξ
old
∪ ξ
ψ
h
new
Where ξ
old
is a subset of old tasks which are not
affected by the reconfiguration scenario ψ
h
(e.g. they
implement the system before the time t
1
), and ξ
ψ
h
new
a
subset of new tasks in the system. We assume that an
updated task is considered as a new one at time t
1
.
When the reconfiguration scenario ψ
h
is applied at
time t
1
, two cases exist:
• If tasks of ξ
ψ
h
= ξ
old
∪ ξ
ψ
h
new
are feasible, then no
AnEDF-basedSchedulingAlgorithmforReal-timeReconfigurableSporadicTasks
379
reaction should be done by the agent,
• Otherwise, the agent should provide different so-
lutions for users in order to re-obtain the system’s
feasibility.
2.1 State of the Art
Nowadays, several interesting studies have been pub-
lished to develop reconfigurable embedded control
systems. In (C. Angelov and Marian, 2005) Marian
et al. propose a static reconfiguration technique for
the reuse of tasks that implement a broad range of
systems. The work in (M. N. Rooker and Ebenhofer,
2007) proposes a methodology based on the human
intervention to dynamically reconfigure tasks of
considered systems. In (Al-Safi and Vyatkin, 2007),
an ontology-based agent is proposed by Vyatkin et al.
to perform system reconfigurations according to user
requirements and also the environment evolution.
Window-constrained scheduling is proposed in (West
and Schwan, 1999), which is based on an algorithm
named dynamic window-constrained scheduling
(DWCS). The research work in (P. Balbastre and
Crespo, 2002) provides a window-constrained-based
method to determine how much a task can increase its
computation time, without missing its deadline under
EDF scheduling. In (P. Balbastre and Crespo, 2002),
a window-constrained execution time can be assumed
for reconfigurable tasks in n among m windows of
jobs. In the current paper, a window constrained
schedule is used to separate old and new tasks that
assumed sporadic on each processor p and after each
reconfiguration scenario ψ
h
. Old and new tasks are
located in different windows to schedule the system
with a minimum response time. In (X. Wang and
L, 2011), a window constrained schedule is used to
schedule the system with a low power consumption.
In the following, we only consider periodic and spo-
radic tasks. Few results have been proposed to deal
with deadline assignment problem. Baruah, Buttazo
and Gorinsky in (H. Gharsellaoui and BenAhmed,
2012) propose to modify the deadlines of a task set
to minimize the output, seen as secondary criteria of
this work. So, we note that the optimal scheduling
algorithm based on the EDF principles and on the
dynamic reconfiguration scenario ψ
h
is that we
propose in the current original work in which we
give solutions computed and presented by the intel-
ligent agent for users to respond to their requirements.
Running Example 1:
To illustrate the key point of the proposed dynamic
reconfiguration approach, we consider ξ = Sys
1
S
Sys
2
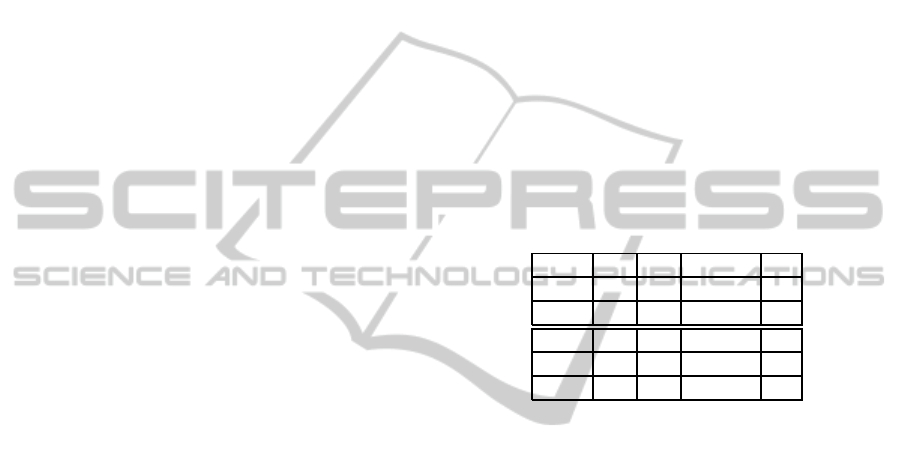
a set of 5 characterized tasks, shown in Table 1
as a motivational example. Sys
1
= τ
A
, τ
B
, and Sys
2
= σ
C
, σ
D
, and σ
E
. τ
A
and τ
B
are periodic tasks and
all the rest (σ
C
, σ
D
, and σ
E
) are sporadic tasks. Each
task can be executed immediately after its arrival and
must be finished by its deadline. First, at time t, Sys
1
is feasible because the processor utilization factor U
= 0.30 ≤ 1. We suppose after, that a reconfiguration
scenario is applied at time t1 to add 3 new sporadic
tasks σ
C
, σ
D
, and σ
E
. The new processor utilization
becomes U = 1.21 > 1 time units. Therefore the
system is unfeasible. In the following tables (table
1 and table 2), the first column represents the task
identifier, the second column represents the release
time, the third column represents the deadline of
each task which is less than or equal to its period in
these examples of real time tasks, the fourth column
represents the period and the five column represents
the worst case execution time (WCET) of each task.
∗
P
i
is the inter-arrival time.
Table 1: The characteristics of the 5 tasks.
Task a
i
D
i
T
i
= P
∗
i
C
i
A 0 10 10 2
B 0 20 20 2
C 5 15 - 5
D 5 8 - 4
E 11 12 - 1
Running Example 2:
In this section, we demonstrate the performance of
our proposed approach for both periodic synchronous
and asynchronous, and sporadic tasks. The simula-
tion runs on our tool RT-Reconfiguration and proved
by the real-time simulator Cheddar (J. Legrand,
2004) with a task set composed of old tasks (ξ
old
)
and new tasks (ξ
p,ψ
h
new
) on the processor p for each
reconfiguration scenario ψ
h
. We illustrate with a
simplified example to ease the understanding of our
approach. The task set considered for this example
is given in table 2 and is composed of 10 tasks. The
sum of utilization of all tasks is given in table 2 and
is equal to 426.1%. We have 3 identical processors
in our system to schedule these tasks. In this case,
we assume that each task’s deadline is less than
or equal to its period. The worst case execution
times, deadlines, and the time periods of all tasks are
generated randomly. In this experiment, the system
runs for time units equal to hyper-period of periodic
tasks.
In this experiment, our task set example is ini-
tially implemented by 5 characterized old tasks
(ξ
old
= {τ
1
; τ
2
; τ
3
; τ
4
; τ
5
}). These tasks are fea-
sible because the processor utilization factor U =
1.19 ≤ 3. These tasks should meet all required
ICSOFT2013-8thInternationalJointConferenceonSoftwareTechnologies
380
deadlines defined in user requirements and we have
Feasibility(Current
ξ
old
(t)) ≡ True.
Firstly, tasks are partitioned; task τ
1
is partioned on
first processor, τ
2
and τ
3
are partitioned on processor
2 while task τ
4
and τ
5
are partitioned on processor
3. We have three sets of local tasks. As there is only
one task on first processor then task τ
1
utilization
factor is the same as the first processor 1 utilization
factor ( u
1,0
= 0.285 ≤ 1) while utilization factors of
processor 2 and processor 3 are calculated as follows:
U
2,0
=
∑
(2)
2
i=1
C
2
i
T
2
i
= 0.372 < 1,
U
3,0
=
∑
(2)
3
i=1
C
3
i
T
3
i
= 0.533 < 1,
We suppose that a first reconfiguration scenario
ψ
1
(h = 1) is applied at time t
1
to add 5 new
tasks ξ
ψ
1
new
= {τ
6
; τ
7
; τ
8
; τ
9
; τ
10
}. The new pro-
cessor utilization becomes U
ψ
1
= 4.261 > 3
time units. Therefore the system is unfeasible.
Feasibility(Current
ψ
1
ξ
(t1)) ≡ False. Indeed, if the
number of tasks increases, then the overload of the
system increases too. Our optimal earliest deadline
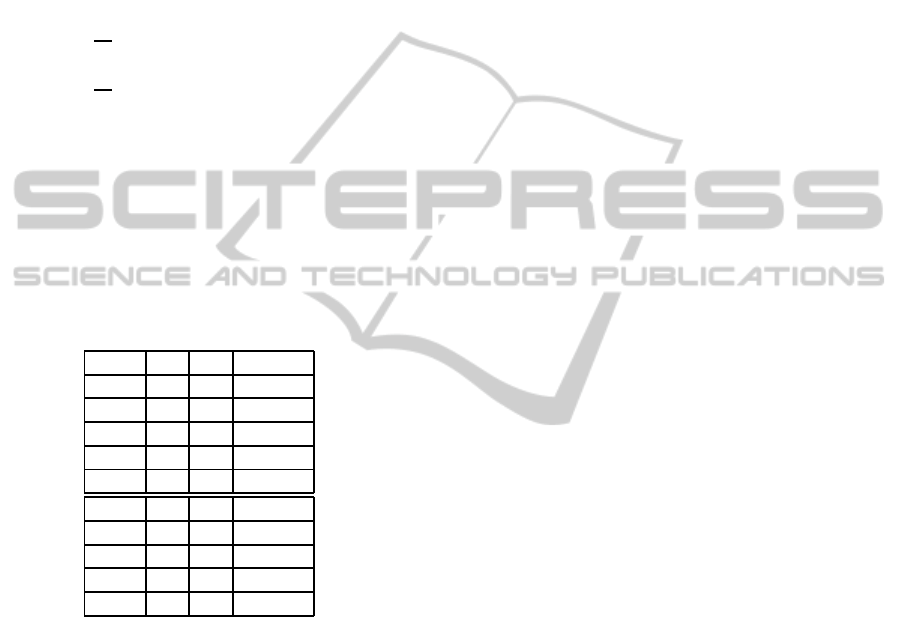
Table 2: Task Parameters.
Task C
i
D
i
T
i
= P
∗
i
τ
1
2 9 7
τ
2
3 21 20
τ
3
2 9 9
τ
4
2 13 10
τ
5
3 15 9
τ
6
14 21 19
τ
7
10 24 16
τ
8
8 18 18
τ
9
13 16 17
τ
10
5 11 12
first (OEDF) algorithm is based on the following
Guarantee Algorithm which is presented by Buttazo
and Stankovic in (Buttazzo and Stankovic, 1993).
Indeed, OEDF algorithm is an extended and ame-
liorate version of Guarantee Algorithm that usually
guarantee the system’s feasibility.
2.2 Guarantee Algorithm
The dynamic, on-line, guarantee test in terms of resid-
ual time, which is a convenient parameter to deal
with both normal and overloadconditionsis presented
here.
Algorithm GUARANTEE(ξ; σ
a
)
begin t = get current time();
R
0
= 0;
d
0
= t;
Insert σ
a
in the ordered task linked list;
ξ`= ξ
S
σ
a
;
k = position of σ
a
in the task set ξ`;
for each task σ
i
`such that i ≥ k do {
R
i
= R
i−1
+ (d
i
- d
i−1
) - c
i
;
if (R
i
< 0) then return (”Not Guaranteed”);
}
return (”Guaranteed”);
end
3 NEW APPROACH WITH
DEADLINE TOLERANCE
In this section we will present some preliminaries
concepts and we will describe our contribution after.
In (Buttazzo and Stankovic, 1993), Buttazo and
Stankovic present the Guarantie Algorithm without
the notion of deadline tolerance, and then we will ex-
tend the algorithm in our new proposed approach by
including tolerance indicator and task rejection pol-
icy. For this reason, and in order to more explain these
notions we will present some preliminaries.
3.1 Preliminaries
ξ denotes a set of active sporadic tasks σ
i
ordered by
increasing deadline in a linked list, σ
1
being the task
with the shortest absolute deadline.
a
i
denotes the arrival time of task σ
i
, i.e., the time at
which the task is activated and becomes ready to exe-
cute.
C
i
denotes the maximum computation time of task
σ
i
, i.e., the worst case execution time (WCET) needed
for the processor to execute task σ
i,k
without interrup-
tion.
c
i
denotes the dynamic computation time of task σ
i
,
i.e., the remaining worst case execution time needed
for the processor, at the current time, to complete task
σ
i,k
without interruption.
d
i
denotes the absolute deadline of task τ
i
, i.e., the
time before which the task should complete its execu-
tion, without causing any damage to the system.
D
i
denotes the relative deadline of task σ
i
, i.e., the
time interval between the arrival time and the abso-
lute deadline. S
i
denotes the first start time of task σ
i
,
i.e., the time at which task σ
i
gains the processor for
the first time. s
i
denotes the last start time of task σ
i
,
i.e., the last time, before the current time, at which
task σ
i
gained the processor.
f
i
denotes the estimated finishing time of task σ
i
, i.e.,
the time according to the current schedule at which
task σ
i
should complete its execution and leave the
AnEDF-basedSchedulingAlgorithmforReal-timeReconfigurableSporadicTasks
381

system.
L
i
denotes the laxity of task σ
i
, i.e., the maximum
time task σ
i
can be delayed before its execution be-
gins.
R
i
denotes the residual time of task σ
i
, i.e., the length
of time between the finishing time of σ
i
and its abso-
lute deadline. Baruah et al. (S. Baruah and Shasha,
1991) present a necessary and sufficient feasibility
test for synchronoussystems with pseudo-polynomial
complexity. The other known method is to use re-
sponse time analysis, which consists of computing
the worst-case response time (WCRT) of all tasks in a
system and ensuring that each task WCRT is less than
its relative deadline. To avoid these problems, and to
have a feasible system in this paper, our proposed tool
RT-Reconfiguration can be used. For this reason, we
present the following relationships among the param-
eters defined above:
d
i
= a
i
+ D
i
(1)
L
i
= d
i
- a
i
- C
i
(2)
R
i
= d
i
- f
i
(3)
f
1
= t + c
1
; f
i
= f
i−1
+ c
i
∀ i > 1 (4)
The basic properties stated by the following lemmas
and theorems are used to derive an efficient O(n+m)
algorithm for analyzing the schedulability of the spo-
radic task set whenever a new task arrives in the sys-
tems.
Lemma 1. Given a set ξ = {σ
1
, σ
2
, ...,σ
n
} of ac-
tive sporadic tasks ordered by increasing deadline in a
linked list, the residual time R
i
of each task σ
i
at time
t can be computed by the following recursiveformula:
R
1
= d
1
- t - c
1
(5)
R
i
= R
i−1
+ (d
i
− d
i−1
) - c
i
. (6) (Buttazzo and
Stankovic, 1993)
Proof. By the residual time definition (equation 3) we
have:
R
i
= d
i
- f
i
.
By the assumption on set ξ, at time t, the task σ
1
in
execution and cannot be preempted by other tasks in
the set ξ, hence its estimated finishing time is given
by the current time plus its remaining execution time:
f
1
= t + c
1
and, by equation (3), we have:
R
1
= d
1
- f
1
= d
1
- t - c
1
.
For any other task σ
i
, with i > 1, each task σ
i
will
start executing as soon as σ
i−1
completes, hence we
can write:
f
i
= f
i−1
+ c
i
(7)
and, by equation (3), we have:
R
i
= d
i
- f
i
= d
i
- f
i−1
- c
i
=
d
i
- (d
i−1
- R
i−1
) - c
i
= R
i−1
+ (d
i
- d
i−1
) - c
i
and the lemma follows.
Lemma 2. A task σ
i
is guaranteed to complete
within its deadline if and only if R
i
≥ 0 (Buttazzo and
Stankovic, 1993).
Theorem 3. A set ξ = {σ
i
, i = 1 to m} of m
active sporadic tasks ordered by increasing deadline
is feasibly schedulable if and only if R
i
≥ 0 for all σ
i
∈ ξ, (Buttazzo and Stankovic, 1993).
In our model, we assume that the minimum inter-
arrival time P
i
of each sporadic task is equal to its
relative deadline D
i
, thus a sporadic task σ
i
can be
completely characterized by specifying its worst
case execution time C
i
and its relative deadline D
i
.
Hence, a sporadic task set will be denoted as follows:
ξ = {σ
i
(C
i
, D
i
)}, i = 1 to m.
3.2 Feasibility Analysis for Tasks
By considering real-time tasks and as we mentioned
before, the schedulability analysis should be done
in the hyperperiod HP
(p,ψ
h
)
= [ζ
(p,ψ
h
)
, 2*LCM +
ζ
(p,ψ
h
)
], where LCM
p,ψ
h
is the well-known Least
Common Multiple of tasks periods and (ζ
p,ψ
h
) is the
largest task offset of all tasks τ
p,ψ
h
k
for each reconfig-
uration scenario ψ
h
on each processor p.
Let n + m be the number of tasks respectively in ξ
old
and ξ
ψ
h
new
. By assuming unfeasible system at time t
1
,
and every processor p will execute its tasks in local by
using EDF, the following formula is satisfied:
∑
n+m
i=1
C
ψ
h
i
T
ψ
h
i
> K, where K is the number of identical
processors.
Our proposed algorithm provides guarantees to both
old and new tasks in each processor p if and only if,
∑
n− j
i=1
C
p,ψ
h
i
T
p,ψ
h
i
+
∑
n+m
i=n− j+1
C
p,ψ
h
i
T
p,ψ
h
i
≤ 1
where
∑
n− j
i=1
C
p,ψ
h
i
T
p,ψ
h
i
denotes sum of utilization factor of n old
tasks in processor p for each reconfiguration scenario
ψ
h
and,
∑
n+m
i=n− j+1
C
p,ψ
h
i
T
p,ψ
h
i
denotes sum of utilization factor
of new arrival m tasks to the processor p for each
reconfiguration scenario ψ
h
.
We propose, for each reconfiguration scenario ψ
h
,
to add the tasks of ξ
old
to a linked list L
ψ
h
old
that we
sort on the increasing order of their utilization factor
values. Let j
ψ
h
be the first j tasks of L
ψ
h
old
.
Approach for each j
ψ
h
∈ [0, n]. When we add
the first j
(p,ψ
h
)
tasks of L
(p,ψ
h
)
old
to ξ
(p,ψ
h
)
new
, there are
ICSOFT2013-8thInternationalJointConferenceonSoftwareTechnologies
382

three different solutions exist for the feasibility of
the system. In such case, if j
ψ
h
= 0, then no tasks
to be added to ξ
ψ
h
new
. After each reconfiguration
scenario ψ
h
, the agent suggests the new parameters
for new tasks. After that, the agent selects tasks from
linked list which are sorted on their utilization factor
(U
p,ψ
h
i
=
C
(p,ψ
h
)
i
T
(p,ψ
h
)
i
) with respect to this order to execute
on the processor p. Tasks from linked list are moved
to be inserted and executed with new tasks. Whenever
an old task is moved from linked list to current ready
list composed of new tasks, parameters (WCET,
periods/deadlines) are recalculated and presented by
the agent to the user for each reconfiguration scenario
ψ
h
. In this case, addition of old task, neither causes
new tasks to miss their deadlines nor misses its own
deadline.
3.3 Contribution: An Algorithm for
Feasibility Testing with Respect
to Sporadic Task Systems
In the current paper, we suppose that on each
processor p, each system ξ
(p)
can be automatically
and repeatedly reconfigured at each reconfiguration
scenario ψ
h
. ξ
(p)
is initially considered as ξ
(p,0)
and
after the h
th
reconfiguration ξ
(p)
turns into ξ
(p,ψ
h
)
,
where h ∈ 1..M. We define VP
p,ψ
h
1
and VP
p,ψ
h
2
two
virtual processors to virtually execute old and new
sporadic tasks, implementing the system after the
h
th
reconfiguration scenario for each processor p. In
ξ
(p,ψ
h
)
, all old tasks from ξ
(p,ψ
h−1
)
are executed by
the newly updated VP
(p,ψ
h
)
1
and the added sporadic
tasks are executed by VP
(p,ψ
h
)
2
. The proposed
intelligent agent is trying to minimize the response
time Resp
p,ψ
h
opt
k
of ξ
(ψ
h
)
after each reconfiguration
scenario ψ
h
and for each processor p.
For example, after the first addition scenario,
ξ
(p,0)
turns into ξ
(p,1)
. ξ
(p,1)
is automatically decom-
posed into VP
(p,1)
1
and VP
(p,1)
2
for old and new tasks
with the processor utilization factors UVP
(p,1)
1
and
UVP
(p,1)
2
respectively on each processor p.
Formalization
We assume in this work a system ξ
(p)
to be composed
of a mixture of n
(p)
periodic and m
(p)
sporadic
tasks on each processor p. An assumed system
ξ
(p,ψ
h−1
)
= {τ
(p)
1
, τ
(p)
2
,...,τ
(p)
n
} turns after a reconfig-
uration scenario to ξ
(p,ψ
h
)
= {τ
(p)
1
, τ
(p)
2
,...,τ
(p)
n
σ
(p)
n+1
,
σ
(p)
n+2
,...,σ
(p)
n+m
} by considering that m
p
new sporadic
tasks are added to ξ
(p,ψ
h−1
)
. After each addition, the
tasks are logically divided into two subsets. One
contains the so called new sporadic tasks which are
added to the system, and the rest of tasks taken from
ξ
(p,ψ
h−1
)
are considered as old tasks to form the sec-
ond subset. After any addition scenario, the response
time can be increased and/or some old/new tasks miss
their deadlines. When a reconfiguration scenario
is automatically applied at run-time, the proposed
agent logically decomposes the physical processor
of ξ
(p,ψ
h
)
into two virtual processors VP
(p,ψ
h
)
1
and
VP
(p,ψ
h
)
2
with different utilization factors UVP
(p,ψ
h
)
1
and UVP
(p,ψ
h
)
2
to adapt the system to its environment
with a minimum response time. For more explaining,
after any reconfiguration scenario and in order to
keep only two virtual processors in the system ξ
(p)
,
the proposed intelligent agent automatically merges
VP
(p,ψ
h−1
)
1
and VP
(p,ψ
h−1
)
2
into VP
(p,ψ
h
)
1
and creates
also a new VP
(p)
2
named VP
(p,ψ
h
)
2
, to adapt old and
new tasks, respectively. The VP
(p,ψ
h
)
2
is assumed
to be a located logical pool in idle periods ofVP
(p,ψ
h
)
1
.
For example, we assume that k = 1 and we re-
streint in this case to a uni-processor system, and
we have 2 initial tasks τ
1
and τ
2
in an assumed
system sys
p=1
1
with ξ
(1,0)
= ξ
(0)
= { τ
1
, τ
2
}. First,
we add {σ
3
, σ
4
and σ
5
} to ξ
(0)
that automatically
turns into ξ
(ψ
1
)
= {τ
1
, τ
2
, σ
3
, σ
4
and σ
5
}. In ξ
(1)
(h
=1), subset {τ
1
, τ
2
} is considered as old tasks to be
executed by VP
(ψ
1
)
1
, whereas subset {σ
3
, σ
4
and σ
5
}
is considered as new sporadic tasks to be executed by
VP
(ψ
1
)
2
. VP
(ψ
1
)
2
is located in idle periods of VP
(ψ
1
)
1
.
We propose thereafter, the arrival of new sporadic
tasks σ
6
and σ
7
to be added to ξ
(ψ
1
)
that evolves into
ξ
(ψ
2
)
= {τ
1
, τ
2
, σ
3
, σ
4
, σ
5
, σ
6
and σ
7
}. VP
(ψ
1
)
1
and
VP
(ψ
1
)
2
are automaticlly merged into VP
(ψ
2
)
1
where
subset {τ
1
, τ
2
, σ
3
, σ
4
and σ
5
} is considered as old
tasks to be executed by this virtual processor. In this
case, subset {σ
6
, σ
7
} is executed by the second newly
created virtual processor VP
(ψ
2
)
2
which is located in
idle periods of VP
(ψ
2
)
1
.
After each addition scenario, the proposed in-
telligent agent proposes to modify the virtual
processors, to modify the deadlines of old and new
tasks, the WCETs and the activation time of some
tasks, to send some tasks from processor i to another
processor j, or to removesome soft tasks as following:
• Solution 1: Moving some arrival tasks to be
scheduled in idle times for each reconfiguration
AnEDF-basedSchedulingAlgorithmforReal-timeReconfigurableSporadicTasks
383

scenario ψ
h
and on each processor p. (idle times are
caused when some tasks complete before its worst
case execution time) (S1)
• Solution 2: maximize the d
p,ψ
h
i
for each re-
configuration scenario ψ
h
and on each processor p
(S2)
By applying equation (3) that notices:
R
i
= d
i
- f
i
, we have:
R
p,ψ
h
i
= d
p,ψ
h
i
- t - C
p,ψ
h
i
.
Or, to obtain a feasible system after a reconfiguration
scenario
ψ
h
, the following formula must be enforced:
R
p,ψ
h
i
≥ 0 on each processor p.
By this result we can write: d
p,ψ
h
inew
- t - C
p,ψ
h
i
≥
0, where d
p,ψ
h
inew
= d
p,ψ
h
i
+ θ
p,ψ
h
i
.
So, d
p,ψ
h
i
+ θ
p,ψ
h
i
- t - C
p,ψ
h
i
≥ 0 ⇒
θ
p,ψ
h
i
≥ t + C
p,ψ
h
i
- d
p,ψ
h
i
.
• Solution 3: minimize the c
i
for each recon-
figuration scenario ψ
h
and on each processor p
(S3)
By applying equation (3) that notices:
R
i
= d
i
- f
i
, we have:
R
p,ψ
h
i
= d
p,ψ
h
i
- t - C
p,ψ
h
i
.
Or, to obtain a feasible system after a reconfiguration
scenario, the following formula must be enforced:
R
p,ψ
h
i
≥ 0.
By this result we can write: d
p,ψ
h
i
- t - C
p,ψ
h
inew
≥ 0,
where C
p,ψ
h
inew
= C
p,ψ
h
i
+ β
p,ψ
h
i
.
So, d
p,ψ
h
i
- t - C
p,ψ
h
i
- β
p,ψ
h
i
≥ 0 ⇒ d
p,ψ
h
i
- t - C
p,ψ
h
i
≥
β
p,ψ
h
i
⇒ β
p,ψ
h
i
≤ d
p,ψ
h
i
- t - C
p,ψ
h
i
• Solution 4: Enforcing the release time to
come back: a
p,ψ
h
i
→ a
p,ψ
h
inew
→ (a
p,ψ
h
inew
= a
p,ψ
h
i
+ ∆
p,ψ
h
t)
for each reconfiguration scenario ψ
h
and on each
processor p (S4)
By applying equation (1) that notices:
d
i
= a
i
+ D
i
, we have:
R
p,ψ
h
i
= a
p,ψ
h
i
+ D
p,ψ
h
i
- t - C
p,ψ
h
i
.
Or, to obtain a feasible system after a reconfiguration
scenario, the following formula must be enforced:
R
p,ψ
h
i
≥ 0 ⇒ a
p,ψ
h
i
+ D
p,ψ
h
i
- t - C
p,ψ
h
i
≥ 0.
By this result we can write:
a
p,ψ
h
inew
+ D
p,ψ
h
i
- t - C
p,ψ
h
i
≥ 0, where a
p,ψ
h
inew
=
a
p,ψ
h
i
+ ∆
p,ψ
h
t.
So, we obtain: a
p,ψ
h
i
+ ∆
p,ψ
h
t + D
p,ψ
h
i
- t - C
p,ψ
h
i
≥ 0.
⇒ ∆
p,ψ
h
t ≥ t + C
p,ψ
h
i
- a
p,ψ
h
i
- D
p,ψ
h
i
.
• Solution 5: Tolerate some non critical Tasks
m
1
p
among (n + m)
p
(according to the (m,n) firm
model), on each processor p for a reasonable cost,
and for each reconfiguration scenario ψ
h
(S5)
ξ
p
= {τ
p
i
(C
p
i
, D
p
i
, m
p
i
, I
p
i
), i = 1ton
p
}.
m
p
i
= 1, it tolerates missing deadline,
m
p
i
= 0, it doesn’t tolerate missing deadline,
I
p
i
= H, Hard task,
I
p
i
= S, Soft task,
• Solution 6: Migration of some tasks from a
processor source i in order to be scheduled on another
processor destination j for each reconfiguration
scenario ψ
h
(S6)
The agent proceeds now as a sixth solution to migrate
some tasks of ξ
p,ψ
h
new
and ξ
p
old
on the processor p
for each reconfiguration scenario ψ
h
. Indeed, the
agent is responsible for allocating the tasks to the K
computing processors in an optimal way.
Run-time task migration can be defined as the
Figure 1: The Task Migration Sequence.
relocation of an executing task from its current
location, the source processor i, to a new location,
the destination processor j (i 6= j; i,j = 1..K) that must
belong to the inclusion set. We need by inclusion
set in paper, the set of processors in which tasks can
be scheduled after any reconfiguration scenario ψ
h
when a migration request has done and in this case
all the relevant state information of that migration
is transferred to the new processor. Otherwise,
it is called exclusion set. This allows the OS to
e.g., minimize energy savings and response time
of the whole system. It also enables processors
management by moving tasks away from processors
with a high amount of workload or which have their
utilization factors > 1. The architectural differences
between the source processor i and destination source
processor j are masked by capturing and transferring
the logical task state, shown by figure 1. In order to
relocate a task, the intelligent agent notifies the task
by means of a migration request signal
(1)
. Whenever
ICSOFT2013-8thInternationalJointConferenceonSoftwareTechnologies
384

that signaled task reaches a migration point (MP), it
checks if there is a pending migration request or the
destination processor j belongs to the exclusion group
of the current migrated task for each reconfiguration
scenario ψ
h
. In such case of these two reasons, all the
relevant state information of that migration point is
transferred to the intelligent agent
(2)
. Consequently,
the intelligent agent will instantiate the same task on
a different processor. The new task instantiation will
be initialized using the state information previously
captured by the intelligent agent
(3)
. Finally, the task
resumes execution at the corresponding migration
point (MP).
One of the main issues in homogeneous (we suppose
before that all the processors are identical) task
migration is the overhead incurred by checking for a
pending migration request during normal execution
(i.e. when there is no pending migration request).
Especially since a task requires frequent migration
points in order to reduce the reaction time. The
reaction time (Figure 1) is the time elapsed between
selecting a task for migration and the selected task
reaching the next migration point. In order to mini-
mize the checking overhead during normal execution,
further denoted as migration initiation, we propose a
novel technique for the new generation of embedded
systems, that uses the inclusion and exclusion group
informations of each task for each reconfiguration
scenario ψ
h
in order to reduce the area search feasi-
blity of such systems and to minimize the reaction
time and consequently the response time will be
minimized too.
• Solution 7: Removal of some non critical tasks (to
be rejected) for each reconfiguration scenario ψ
h
and
on each processor p (S7)
ξ
p
= {τ
p
i
(C
p
i
, D
p
i
, m
p
i
, I
p
i
), i = 1 to n
p
}.
m
p,ψ
h
i
= 1, it tolerates missing deadline,
m
p,ψ
h
i
= 0, it doesn’t tolerate missing deadline,
I
p,ψ
h
i
= H, Hard task,
m
p,ψ
h
i
= S, Soft task,
For every solution the corresponding response time
is:
Resp
p,ψ
h
k,1
= the response time calculated by the first
solution,
Resp
p,ψ
h
k,2
= the response time calculated by the
second solution,
Resp
p,ψ
h
k,3
= the response time calculated by the third
solution,
Resp
p,ψ
h
k,4
= the response time calculated by the fourth
solution,
Resp
p,ψ
h
k,5
= the response time calculated by the fifth
solution,
Resp
p,ψ
h
k,6
= the response time calculated by the sixth
solution,
Resp
p,ψ
h
k,7
= the response time calculated by the
seventh solution,
We define now, Resp
p,ψ
h
k
optimal noted Resp
p,ψ
h
opt
k
according to the previous seven solutions calculated
by the intelligent Agent (Solution 1, Solution 2,
Solution 3, Solution 4, Solution 5, Solution 6 and
Solution 7) by the following expression:
Resp
p,ψ
h
opt
k
= min(Resp
p,ψ
h
k,1
, Resp
p,ψ
h
k,2
, Resp
p,ψ
h
k,3
,
Resp
p,ψ
h
k,4
, Resp
p,ψ
h
k,5
, Resp
p,ψ
h
k,6
and Resp
p,ψ
h
k,7
) (the
minimum of the seven values). So, the calculation of
Resp
p,ψ
h
opt
k
allows us to obtain and to calculate the
minimizations of response times values and to get
the optimum of these values. In conclusion, we can
deduce that by arrival of ξ
ψ
h
new
tasks at run-time and
the whole system become unfeasible, the following
formula based on (A.K.MOK, 1983) is satisfied for
each reconfiguration scenario ψ
h
:
∑
(n+m)
ψ
h
i=1
C
ψ
h
i
T
ψ
h
i
> K, where K is the number of
identical processors.
Then, after the reconfiguration scenario ψ
h
was
applied at run-time to the whole system by the
inteligent agent, our proposed algorithm provides
guarantees to both old and new tasks if and only if,
we have in each processor p for each reconfiguration
scenario ψ
h
:
∑
(n+m)
(p,ψ
h
)
i=1
C
(p,ψ
h
)
i
T
(p,ψ
h
)
i
≤ 1, in each processor p for each
reconfiguration scenario ψ
h
,
Moreover, we have calculated R
(p,ψ
h
)
opt
k
=
min(R
(p,ψ
h
)
k,1
, R
(p,ψ
h
)
k,2
, R
(p,ψ
h
)
k,3
, R
(p,ψ
h
)
k,4
, R
(p,ψ
h
)
k,5
,
R
(p,ψ
h
)
k,6
and R
(p,ψ
h
)
k,7
); so we obtain also:
∑
(n+m)
(p,ψ
h
)
i=1
C
(p,ψ
h
)
i
T
(p,ψ
h
)
i
< 1, in each processor p for each
reconfiguration scenario ψ
h
with 1 ≤ p ≤ K, 1 ≤ h ≤
M.
Now by adding the following formulas, we have:
∑
(n+m)
(1,ψ
h
)
i=1
C
(1,ψ
h
)
i
T
(1,ψ
h
)
i
< 1,
∑
(n+m)
(2,ψ
h
)
i=1
C
(2,ψ
h
)
i
T
(2,ψ
h
)
i
< 1,
... < ...
... < ...
AnEDF-basedSchedulingAlgorithmforReal-timeReconfigurableSporadicTasks
385

∑
(n+m)
( j,ψ
h
)
i=1
C
( j,ψ
h
)
i
T
( j,ψ
h
)
i
< 1,
... < ...
... < ...
∑
(n+m)
(K,ψ
h
)
i=1
C
(K,ψ
h
)
i
T
(K,ψ
h
)
i
< 1,
⇒
∑
(n+m)
ψ
h
i=1
C
ψ
h
i
T
ψ
h
i
< 1 + 1+ 1+ ... + 1
|
{z }
Ktimes
.
⇒
∑
(n+m)
ψ
h
i=1
C
ψ
h
i
T
ψ
h
i
< K.
This work, concentrates on the context of sys-
tems containing a set of tasks which is not feasible.
The reconfiguration was applied in order not only
to obtain the system’s feasibility, but also to get the
performance of the system by reducing the response
time of the processes to be tolerated in interactive
environment in order to minimize the response time
of the studied reconfigurable embedded system at
run-time for each reconfiguration scenario ψ
h
and in
each processor p.
We can observe that our proposed approach provides
an optimal global scheduling algorithm which sched-
ules tasks according to EDF in each processor p for
each reconfiguration scenario ψ
h
. All tasks meet their
deadlines after a reconfiguration scenario ψ
h
was
applied at run-time. We can also observe, that our
proposed algorithm selects tasks to migrate from one
processor source i to another processor destination
j in an optimal way such that overall utilization of
task set is minimum. Parameters of tasks i.e., period,
deadline and worst case execution time, are generated
randomly. We have illustrated that our proposed al-
gorithm outperforms other scheduling multiprocessor
algorithms and a number of scheduling events are
much lower than appearing in others.
3.4 The General OEDF Scheduling
Strategy
When dealing with the deadline tolerance factor m
i
,
each task has to be computed with respect to the
deadline tolerance factor m
i
.
Algorithm GUARANTEE(ξ; σ
a
)
For each h in [1..M] Do
begin t = get current time();
R
p,ψ
h
0
= 0;
d
p,ψ
h
0
= t;
Insert σ
a
in the ordered task list;
ξ
p,ψ
h
`= ξ
p,ψ
h
S
σ
a
;
k = position of σ
a
in the task set ξ
p,ψ
h
`;
for each task σ
p,ψ
h
i
`such that i ≥ k do
{
R
p,ψ
h
i
= R
p,ψ
h
i−1
+ (d
p,ψ
h
i
- d
p,ψ
h
i−1
) - c
p,ψ
h
i
;
if (R
p,ψ
h
i
≥ 0) then
{
return (”Guaranteed”);
}
else return
(”You can try by using solution 1, or,
You can try by using solution 2, or,
You can try by using solution 3, or,
You can try by using solution 4, or,
You can try by using solution 5, or,
You can try by using solution 6, or,
You can try by using solution 7 !”);
}
• Compute(Resp
p,ψ
h
k,1
);
• Compute(Resp
p,ψ
h
k,2
);
• Compute(Resp
p,ψ
h
k,3
);
• Compute(Resp
p,ψ
h
k,4
);
• Compute(Resp
p,ψ
h
k,5
);
• Compute(Resp
p,ψ
h
k,6
);
• Compute(Resp
p,ψ
h
k,7
);
• Generate(Resp
p,ψ
h
opt
k
);
end
The extension of the proposed algorithm should
be straightforward, when this assumption does not
hold and its running time is O(n + m)
2
. So, Intu-
itively, we expect that our algorithm performs better
than the Buttazo and Stankovic one. We show the
results of our optimal proposed algorithm by means
of experimental result’s evaluation.
4 EXPERIMENTAL RESULTS
In order to evaluate our optimal OEDF algorithm, we
consider the following experiments.
4.1 Experiments
Running Example 1:
We apply our contribution to this first running exam-
ple on the particular case of uni-processor systems
(k = 1) and we could observe that the recalculation
points of the utilization factor, when parameters of
ICSOFT2013-8thInternationalJointConferenceonSoftwareTechnologies
386
new tasks are modified, decreases and becomes less
than or equal to 1 and we can deduce that the system
is now feasible.
Running Example 2:
We apply our contribution to this second running
example and we could observe that the recalculation
points of the utilization factor, when parameters of
new tasks are modified, decreases and becomes less
than or equal to k on the case of multiprocessor
systems and we can deduce that the system is now
feasible.
4.2 Simulations
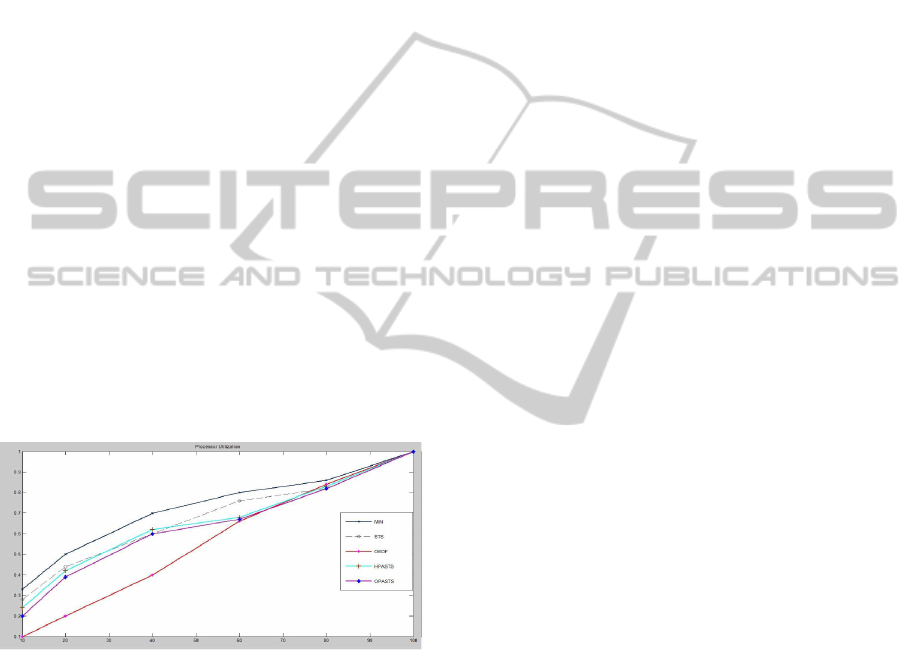
To quantify the benefits of the proposed approach
(OEDF algorithm) over the predictive system shut-
down (PSS) approach, over the MIN algorithm, the
OPASTS algorithm and over the HPASTS algorithm.
We performed a number of simulations to compare
the response time and the utilization processor under
the four strategies. The PSS technique assumes the
complete knowledge of the idle periods while the
MIN algorithm assumes the complete knowledge
of the arrivals of sporadic tasks. For more details
about both four techniques, you can see (Mani
B. Srivastava, 1998). The OEDF scheduling result is
shown in figure 2.
Figure 2: Processor Utilization.
4.3 Discussion
In experiments, if the resulting U(t) > 1, we set U(t) to
be 1. We varied the average processor utilization from
the light workload (10 tasks) to heavy workload (100
tasks) generated randomly. We observe that our ap-
proach, by the solutions of the OEDF algorithm gives
us the minimum bound for response time and utiliza-
tion factor. This observation was proven by the re-
sults given by OEDF algorithm which are lower (bet-
ter) than these of the solutions given by the predic-
tive system shutdown approach, the MIN algorithm,
the OPASTS algorithm and the HPASTS algorithm.
Also, we observe that, when we have no knowledge
of the arrival of sporadic tasks, our proposed algo-
rithm is optimal and gives better results than others
for a big number of arrival sporadic tasks and in over-
load conditions, but in a small number of tasks or light
workload, OEDF algorithm is optimal but not strictly
since it gives results close to that of the solutions of
MIN, OPASTS and HPASTS algorithms, but it is ef-
ficient and effective.
Moreover, if the number of solutions presented by the
intelligent agent to the user increases, then chances
of executing more new added tasks increase and the
performance of the real time scheduling is more effi-
cient. This is due to the fact that the reconfiguration
issues are increased, the user selects the best solution
which gives the minimum utilization factor of the sys-
tem and ameliorates the response time and hence the
chances of executing more new tasks are increased as
well.
The agent should define the different solutions for the
user. In this case, the user can choose the best solu-
tion that satisfies functional requirements. These re-
sults were suggested by the tool RT-Reconfiguration
and give a feasible system which is proven also by
Cheddar.
5 CONCLUSIONS
This paper deals with reconfigurable homogeneous
multiprocessor systems to be implemented by hybrid
systems composed of a mixture of periodic and spo-
radic tasks that should meet real-time constraints. In
this paper, we propose an optimal scheduling algo-
rithm based on the EDF principles and on the dynamic
reconfiguration for the minimization of the response
time of sporadic and periodic constrained deadline
real-time tasks on multiprocessor systems and proven
it correct. Finally, our important future work is the
generalization of our contributions for the Reconfig-
urable real-time embedded systems.
REFERENCES
A.K.MOK (1983). Fundamental Design Problems of Dis-
tributed Systems for The HardReal-Time Environment.
Technical Report No. MIT/LCS/TR-297, PhD thesis,
Laboratory for Computer Science, Massachusetts In-
stitute of Technology, Massachusetts, USA.
Al-Safi, Y. and Vyatkin, V. (2007). An ontology-based
reconfiguration agent for intelligent mechatronic sys-
tems. Int. Conf. Hol. Multi-Agent Syst. Manuf., vol.
4659, pp. 114-126, Regensburg, Germany, 4th edition.
Brocal V., BalbastreP., B. R. R. L. (2011). Task period se-
lection to minimize hyperperiod, Emerging Technolo-
AnEDF-basedSchedulingAlgorithmforReal-timeReconfigurableSporadicTasks
387

gies & Factory Automation (ETFA), IEEE conference
on, pp.1-4, 2011. doi: 10.1109/ETFA.2011.6059178,
Toulouse, France, 16th edition.
Buttazzo, G. and Stankovic, J. (1993). RED: Robust Earli-
est Deadline Scheduling. Int. Workshop On Respon-
sive Computing Systems, Austin, 3rd edition.
C. Angelov, K. S. and Marian, N. (2005). Design models
for reusable and reconfigurable state machines. L.T.
Yang et al., Eds., Proc.of Embedded Ubiquitous Com-
put.
Dertouzos, M. (1974). Control Robotics: The Procedural
Control of Physical Processes. Proceedings of the
IFIP Congress.
H. Gharsellaoui, M. K. and BenAhmed, S. (2012).
Feasible Automatic Reconfigurations of Real-Time
OS Tasks. IGI-Global Knowledge, USA, isbn13:
9781466602946 edition.
J. Legrand, L. (2004). Cheddar : a Flexible Real Time
Scheduling Framework. ACM SIGAda Ada Letters,
volume 24, number 4, pages 1-8. Edited by ACM
Press, ISSN:1094-3641.
M. N. Rooker, C. Subder, T. S. A. Z. O. H. and Ebenhofer,
G. (2007). Zero downtime reconfiguration of dis-
tributed automation systems: The CEDAC approach.
Int. Conf. Indust. Appl. Holonic Multi-Agent Syst.,
Regensburg, 3rd edition.
Mani B. Srivastava, Miodrag Potkonjak, I. H. (1998). On-
Line Scheduling of Hard Real-Time Tasks on Vari-
able Voltage Processor. International Conference on
Computer-Aided Design (ICCAD ’98), San Jose, Cal-
ifornia, USA, 8th edition.
P. Balbastre, I. R. and Crespo, A. (2002). Schedulability
analysis of window-constrained execution time tasks
for real-time control. 14th Euromicro Conf. Real-
Time Syst., 14th edition.
S. Baruah, G. Koren, B. M. A. R. L. R. and Shasha, D.
(1991). On-line Scheduling in the Presence of Over-
load. IEEE Symposium on Foundations of Computer
Science, San Juan, Puerto Rico.
T. Tia, J. W.-S. Liu, J. S. a. R. H. (1994). A linear-time
optimal acceptance test for scheduling of hard real-
time tasks. Technical report, Department of Computer
Science, University of illinois at Urbana-Champaign,
Urbana-Champaign.
West, R. and Schwan, K. (1999). Dynamic window-
constrained scheduling for multimedia applications.
IEEE 6th Int. Conf. Multi. Comput. Syst., 6th edition.
X. Wang, M. K. and L, Z. W. (2011). dynamic low power
reconfigurations of real-time embedded systems. in:
Proc. Pervas. Embedded Comput. Commu. Syst., Al-
garve, Portugal, 1st edition.
ICSOFT2013-8thInternationalJointConferenceonSoftwareTechnologies
388
