
Improving Enterprise IT Governance and Management by Applying
Competitive Intelligence and External Context Discovery on
COBIT 5.0
Eduardo Costa Ramos, Flavia Maria Santoro and Fernanda Baião
NP2Tec – Research and Practice Group in Information Technology, Department of Applied Informatics,
Federal University of the State of Rio de Janeiro (UNIRIO), Rio de Janeiro, Brazil
Keywords: COBIT 5.0, External Context, Knowledge Management, Competitive Intelligence, KDD, Business Process,
Data Mining.
Abstract: COBIT 5 is a framework for governing and managing enterprise Information Technology (IT) that supports
enterprise executives and management staff in defining and achieving business goals and related IT goals
(ISACA, 2012a). Specifically, Chapter 3 of COBIT 5 specification presents some examples of events in the
enterprise’s internal and external environment that can typically signal or trigger a focus on the processes
related to IT governance and management. However, despite the fact that COBIT 5 highlights such
processes that consider the external environment, it misses to integrate them; moreover, it lacks a
knowledge perspective. Therefore, we propose an adaptation to the COBIT framework to apply competitive
intelligence on its processes. This would allow the organization to be proactive (rather than reactive) against
external changes. In this scenario, we specifically propose to apply the BPECREL (Business Process
External Context Relevance) method to identify and prioritize external variables that impact on the
execution of a process and of its specific activities. We evaluated this proposal in an example, which
showed that some discovered external variables influenced the process execution and its specific activities.
1 INTRODUCTION
The governance and management of enterprises do
not occur disorderly. Every enterprise needs to
design its own implementation plan, depending on
issues arising from the internal and external
environment, such as (ISACA 2012a): ethics and
culture; applicable laws; regulations and policies;
mission; vision and values; governance policies and
practices; business plan and strategic intentions;
operating model and level of maturity; management
style; risk appetite; capabilities and available
resources; and industry practices. Especially in the
Information Technology (IT) area, it is important to
control and work up existing enterprise governance
enablers.
COBIT 5 is a framework for governing and
managing enterprise Information Technology (IT)
that supports enterprise executives and management
staff in defining and achieving business goals and
related IT goals (ISACA, 2012a). Nevertheless, an
adequate approach for effectively adopting and
adapting COBIT 5 for each enterprise should
consider the context needs. Besides, COBIT is often
sustained by other frameworks, good practices and
standards, and these also need to be adapted to suit
specific requirements (ISACA 2012a).
A number of factors may indicate a need for
improvement in IT governance and management
within an enterprise. Chapter 3 of the COBIT 5
(2012a) specification presents some examples of
events in the enterprise’s internal and external
environment that can typically signal or trigger a
focus on the processes related to IT governance and
management:
Merge, acquisition or divestiture;
A shift in the market, economy or competitive
position;
A change in the business operating model or
sourcing arrangements;
New regulatory or compliance requirements;
A significant technology change or paradigm
shift;
An enterprise-wide governance focus or project;
89
Costa Ramos E., Santoro F. and Baião F..
Improving Enterprise IT Governance and Management by Applying Competitive Intelligence and External Context Discovery on COBIT 5.0.
DOI: 10.5220/0004159800890096
In Proceedings of the International Conference on Knowledge Management and Information Sharing (KMIS-2012), pages 89-96
ISBN: 978-989-8565-31-0
Copyright
c
2012 SCITEPRESS (Science and Technology Publications, Lda.)

A new CEO, CFO, CIO, etc;
External audit or consultant assessments;
A new business strategy or priority.
However, despite the fact that COBIT 5 highlights
these processes that consider the external
environment, it lacks their integration and a
knowledge perspective.
Therefore, we propose an adaptation to the
COBIT 5 framework to use competitive intelligence
on its processes. This would allow the organization
to be proactive (rather than reactive) against external
changes. In this scenario, we specifically propose to
apply the BPECREL (Business Process External
Context Relevance) method (Ramos et al., 2010);
(Ramos et al., 2011); (Ramos, 2011), which
identifies and prioritizes external variables that
impact on the execution of a process and of its
specific activities. The BPECREL method is based
on Competitive Intelligence concepts and Data
Mining techniques. We evaluated our proposal in an
example, which showed that some discovered
external variables influenced the process execution
and its specific activities.
This paper is structured as follows: Section 2
presents the COBIT 5 framework. Section 3
summarizes the BPECREL Method. Section 4 shows
an example scenario. Section 5 concludes this work
and points to promising evolutions.
2 COBIT 5 - A BUSINESS
FRAMEWORK FOR THE
GOVERNANCE AND
MANAGEMENT OF
ENTERPRISE IT
According to (ISACA, 2012a), in COBIT 5
specification the “COBIT” (formerly known as
Control Objectives for Information and related
Technology), is used only as its acronym. COBIT 5
is a complete, internationally accepted framework
for governing and managing enterprise information
technology (IT) that supports enterprise executives
and management in their definition and achievement
of business goals and related IT goals (ISACA,
2012a). COBIT describes five principles and seven
enablers that support enterprises in the development,
implementation, and continuous improvement and
monitoring of good IT-related governance and
management practices (ISACA, 2012a). COBIT 5 is
generic and useful for enterprises of all sizes,
whether commercial, not-for-profit or in the public
sector (ISACA, 2012a). It helps enterprises create
optimal value from IT by maintaining a balance
between achieving benefits and optimizing risk
levels and resource use.
COBIT 5 is based on five key principles for
governance and management of enterprise IT
(ISACA, 2012a): (1) Meeting Stakeholder Needs;
(2) Covering the End-to-end Enterprise; (3)
Applying a Single, Integrated Framework; (4)
Enabling a Holistic Approach; (5) Separating
Governance From Management.
The COBIT 5 process reference model succeeds
the COBIT 4.1 process model and aggregates the
Risk IT and Val IT process models to it (ISACA,
2012c). In this model, the IT-related practices and
activities of the enterprise are subdivided into two
main areas: governance and management.
Governance ensures that enterprise objectives are
achieved by evaluating stakeholder needs,
conditions and options; setting direction through
prioritization and decision making; and monitoring
performance, compliance and progress against
direction and objectives (EDM) (ISACA, 2012a).
Management plans, builds, runs and monitors
activities in alignment with the direction set by the
governance to achieve the enterprise objectives
(PBRM) (ISACA, 2012a).
Management is divided into domains of
processes. The four Management domains are in line
with the PBRM responsibility areas (plan, build, run
and monitor) (ISACA, 2012c). These domains are:
APO-Align, Plan and Organize; BAI-Build, Acquire
and Implement; DSS-Deliver, Service and Support;
and MEA-Monitor, Evaluate and Assess (ISACA,
2012a). Some Enterprise IT Management processes
are (ISACA, 2012c):
APO03 Manage enterprise architecture;
APO04 Manage innovation;
APO05 Manage portfolio;
APO06 Manage budget and costs;
APO08 Manage relationships;
APO13 Manage security;
BAI05 Manage organizational change
enablement;
BAI08 Manage knowledge;
BAI09 Manage assets;
DSS05 Manage security service;
DSS06 Manage business process controls.
COBIT 5 processes cover end-to-end business and
IT activities, i.e., a full enterprise-level view
(ISACA, 2012c). COBIT 5 covers all functions and
KMIS2012-InternationalConferenceonKnowledgeManagementandInformationSharing
90

processes required to govern and manage enterprise
information and related technologies wherever that
information may be processed (ISACA, 2012a).
COBIT 5 addresses all the relevant internal and
external IT services, as well as internal and external
business processes (ISACA, 2012a). The COBIT 5
Framework relates COBIT 5 processes to IT goals,
and these ones to enterprise’s goals. For example,
the COBIT 5 Enterprise Goal “8-Agile responses to
a changing business environment” primarily depends
on the achievement of the following IT-related
goals:
01-Alignment of IT and business strategy;
07- Delivery of IT services in line with business
requirements;
09- IT agility;
17- Knowledge, expertise and initiatives for
business innovation.
These IT-related goals primarily depend on the
achievement of other COBIT 5 Processes. As an
example, the IT-related goal “09- IT agility”
primarily depends on the achievement of the
following COBIT 5 processes:
EDM04-Ensure Resource Optimization;
APO01-Manage the IT Management Framework;
APO03-Manage Enterprise Architecture;
APO04-Manage Innovation;
APO10-Manage Suppliers;
BAI08- Manage Knowledge.
Some COBIT 5 processes that need to identify
external variables are (ISACA, 2012a):
EDM01- Ensure Governance Framework Setting
and Maintenance: this process has an activity to
analyze and identify the internal and external
environmental factors (legal, regulatory and
contractual obligations) and trends in the business
environment that may influence governance design.
APO04- Manage Innovation: this process
comprises two Key Management Practices (KMPs),
one to maintain an understanding of the enterprise
environment (APO04.02) and the other to monitor
and scan the technology environment (APO04.03).
MEA03- Monitor, Evaluate and Assess
Compliance with External Requirements: this
process is more detailed in section 4.
However, none of these COBIT 5 processes define
how to identify the external variables. The next
section presents a way of doing it.
3 THE BPCREL METHOD
This section presents BPCREL, a method that
identifies and prioritizes external variables that
impact the execution of specific activities and
outcomes of a process, applying Competitive
Intelligence (CI) concepts and Data Mining (DM)
techniques. BPCREL was previously proposed in
(Ramos, Santoro and Baiao, 2010)(Ramos, Santoro
and Baiao, 2011)(Ramos, 2011) and is illustrated in
Figure 1.
Steps 1 to 7 of BPCREL are responsible for
applying two CI methods – Key Intelligence Topics
(KIT) (Herring, 1999) and Critical Success Factors
(CSF) – to systematically define information at the
strategic level. Key Intelligence Topics (KITs)
support the specification, definition and
prioritization of information needs at the strategic
level of the organization. They represent items that
must be constantly monitored to guarantee business
success.
The specification of the contents of each KIT is
more detailed by several KIQs (Key Information
Questions). For example, the KIT “Strategic
Investment Decisions” may consist of the following
KIQs: "What is the involvement of other investors in
competitors?" and "What are the critical investments
from competitors?" (Vuori and Pirttimäki 2005).
According to BPCREL, KITs are identified through
interviews with managers, asking open questions.
Each KIT may fall into one category, and grouped
into surveillance areas. The three KIT categories are:
(i) strategic decisions and actions; (ii) topics for
early warning, considering threats and issues that
decision makers want to know previously, and (iii)
major players in the market, such as customers,
competitors, suppliers and partners (Herring 1999).
Finally, Step 8 of BPCREL follows a KDD
process to predict the process goal (defined in step
1) and to determine the relevance of the external
context variables (identified by the KIT/KIQ
approach) to the process outcomes and to the
process activities outcomes.
The 8 BPCREL steps are detailed as follows.
Step 1 – Identify Process Goal(s). Identify all the
goals related to a given process and their appropriate
measures (Rosemann et al. 2008).
Step 2 – Select KIT Category. Herring (1999) has
divided KITs into three categories: 1) Strategic
Decisions and Issues, 2) Early-warning KITs,
considering threats and issues on which decision
makers do not want to be surprised and 3) Key
player KITs (such as customers, competitors,
suppliers and partners). Each of the three categories
ImprovingEnterpriseITGovernanceandManagementbyApplyingCompetitiveIntelligenceandExternalContext
Discovery on COBIT 5.0
91

Figure 1: Method for external context variables identification.
is selected iteratively, to conduct the subsequent
steps.
Step 3 – Select Surveillance Area. Steps 3 to 6 are
part of a top-down approach, in which top level
areas must be considered to give support to the next
step. General surveillance areas are: social,
technology, economic, ecology, political, legal and
competitors, due to all industries are influenced by
them. However, they can be selected from any
framework, such as Five Forces model (Porter,
1979), SLEPT or STEEP Analysis (The Times,
2010), or from a combination of them. BPCREL
focuses on events that occur externally to the
process (or ultimately to the organization where it
runs) and somehow interfere within this process.
Rosemann et al. (2008) propose that the external
layer of their model is composed of the following
types of context: suppliers, capital providers,
workforce, partners, customers, lobbies, states,
competitors. This step is repeated for each of the
three KIT categories.
Step 4 – Identify KIT. Key Intelligence Topics
(KITs) are identified by interviewing the main
decision-makers and asking them open-ended, non-
directive questions (Herring and Francis 1999). An
interview protocol is very useful to ensure the
consistency of results (Herring 1999). Repeat this
step for each of the surveillance area selected.
Step 5 – Identify KIQ. Key Intelligence Questions
(KIQs) should be identified for each KIT. KIQs
represent the information needs listed in the KIT, i.e.
what the manager needs to know to be able to make
the decisions. It is possible to have the same KIQ for
more than one KIT. Repeat this step for each KIT
selected.
Step 6 – Identify External Context Variables.
Each KIQ may reference one or more external
variables. These are the external context variables
and are identified in this step. It is possible to have
the same variable for more than one KIQ. Repeat
this step for each KIQ identified in the previous step.
For each process goal, the result of all the executions
of steps 2 to 6 will be the final Intelligence Tree with
the following columns: Process Goal, KIT category,
Surveillance Area, KIT, KIQ and External Context
Variable.
Step 7 – Collect Past Information of the External
Context. In this step, historical data of each
identified external context variable is collected and
stored in the organizational memory. This data
should refer to the same period of which data about
the process (and its activities) outcome is also
available.
Step 8 – Determine Relevance of the External
Context to the Process Outcomes and to the
Process Activities Outcomes. This step applies data
mining techniques to prioritize which context
variable to capture and store in the Organizational
Memory, according to its relevance. A KDD process
(Fayyad et al., 1996) is followed that automatically
finds the most relevant subset of external context
variables that best predict the process (and its
activities) outcome. Before applying any KDD
process, it is necessary to understand the application
domain and identify what is expected to be
discovered from the customer’s viewpoint (Fayyad
et al., 1996). Each KDD step is detailed as follows:
Step 8.1 (Selection) – this step consists on creating
a target data set (or focusing on a subset of variables
or data samples), on which discovery is to be
performed. In this step, the historical data of the
external context is associated to the process
activities outcomes and to the process execution
results, for the same period.
Step 8.2 (Pre-processing) – this step consists on
cleaning and pre-processing the target data set in
order to obtain consistent data;
Step 8.3 (Transformation) – this step consists in
finding useful features to represent data so that the
target data set is reduced. By applying
KMIS2012-InternationalConferenceonKnowledgeManagementandInformationSharing
92

dimensionality reduction or transformation methods,
the effective number of variables under
consideration can be reduced, or invariant
representations for the data can be found (Fayyad et
al., 1996).
Step 8.4 (Data Mining - DM) – generically, data
mining consists of searching for patterns of interest
in a particular representational form. Many models
can be created to allow comparing which one has the
best accuracy for predicting a target attribute.
BPCREL applies feature selection and decision tree
data mining techniques to discover which subset of
external context variables more precisely lead to a
specific process outcome.
Step 8.5 (Interpretation/Evaluation) – this step
consists on the interpretation and evaluation of the
mined patterns. The decision tree constructed in the
previous step provides an adequate representation
for knowledge managers to understand and interpret
the circumstances in which a change in an external
variable impacted the results of process instances in
the past and, further, which activities of the
processes were impacted. We argue that this
interpretation will enable the decision maker to
prepare process adaptations required to handle future
modifications in the external variables, or at least to
quickly react to those changes in the environment,
when they occur.
4 AN EXAMPLE SCENARIO OF
APPLYING BPECREL
METHOD TO SUPPORT A
COBIT 5 PROCESS
This section illustrates an example of how we
propose to apply competitive intelligence and data
mining for supporting COBIT 5 processes that need
to monitor external variables. With this objective in
mind, we propose to apply the BPECREL method
(described in Section 3) to every main business
process of the organization. This will allow the
organization to know the relevance of each
identified external variable to each business process
(and to their specific activities).
This Section describes an example scenario in
which we have applied the BPECREL method on a
fictitious organization with 3 main business
processes. Our focus is to support the COBIT 5
process “Monitor, Evaluate and Assess Compliance
with External Requirements process (MEA03)”.
4.1 The COBIT 5 MEA03 Process
The COBIT 5 MEA03 process (“Monitor, Evaluate
and Assess Compliance with External
Requirements”) – which will be referred to as the
MEA03 process from now on – evaluates that “IT
processes and IT-supported business processes are
compliant with laws, regulations and contractual
requirements”. MEA03 also obtains “assurance that
the requirements have been identified and complied
with, and integrates IT compliance with overall
enterprise compliance”. It belongs to the
Management Area and to the Monitor, Evaluate and
Assess Domain.
According to the COBIT 5 specification (ISACA
2012a), the MEA03 process is primary related to
two COBIT 5 IT goals: “02-IT compliance and
support for business compliance with external laws
and regulations”; and “04-Managed IT-related
business risk”. These two COBIT 5 IT goals are
primary related to the following COBIT 5 Enterprise
goals: “04- Compliance with external laws and
regulations”; “15- Compliance with internal
policies”; “03- Managed business risk (safeguarding
of assets)”; “07- Business service continuity and
availability”; and “10- Optimization of service
delivery costs”.
The MEA03 process is formed by four Key
Management Practices (KMPs):
1. Identify external compliance requirements;
2. Optimize response to external requirements;
3. Confirm External Compliance;
4. Obtain assurance of external compliance.
The first KMP (MEA03.01) identifies and monitors
changes in local and international laws, regulations
and other external requirements that must be
complied with from an IT perspective, on a
continuous basis. This KMP has six activities and
the first one is to assign responsibility for identifying
and monitoring any changes of legal, regulatory and
other external contractual requirements relevant to
the use of IT resources and to the processing of
information within the enterprise business and IT
operations.
Since COBIT 5 does not specify how to identify
external requirements, we propose applying the
BPECREL method for this purpose on every main
business process.
4.2 Business Processes
Our example scenario assumes an Organization with
3 main business processes (BP): BP1, BP2 and BP3.
ImprovingEnterpriseITGovernanceandManagementbyApplyingCompetitiveIntelligenceandExternalContext
Discovery on COBIT 5.0
93
Each BP has its goals. For every BP, the
organization is interested achieving its BP goals. A
BP could be a software development process in a
software house organization, for example, and in this
case the organization must make decisions such as
whether or not to authorize the beginning of a
software development project; what to do to
maximize the chances of an ongoing project to be
concluded; and whether to deactivate a project or to
continue with it (Ramos et al., 2011); (Ramos,
2011).
4.3 Application of the Method
In this example scenario, we executed the 8 steps of
the BPECREL method to define relevant external
variables that influenced the main business
processes (BP) of our hypothetic organization, as
shown in section 4.2. The result after applying steps
1 to 7 of BPECREL is a list of possible relevant
external variables, illustrated in Table 1. Step 8
outputs a list of the relevant external variables and a
decision tree showing the relation among them and
with the BP activities and goals (Figure 2).
Step 1 to 7. For the defined process goal of every
BP (BP1, BP2 and BP3), the result of all the
executions of steps 1 to 7 was a list of possible
relevant external variables that can impact the goals
of BP1, BP2 and BP3, illustrated in Table 1. The
first column discriminates the 3 BPs. The last
column lists the goals for each BP. Intermediate
columns show fictitious candidate external variables
identified through the CI questionnaires. A cell with
“yes” states that this external variable was identified
for this BP. The list of candidate relevant external
variables per BP is composed by all the variables
referring to columns with a “yes” cell in the BP table
line. For example, the list of candidate relevant
external variables identified for BP1 and its Goal1 is
{X, Z, W, T}. According to BPCREL specification,
the historical data of each identified external context
variable is collected and stored in the organizational
memory.
Step 8. In this step we followed the KDD process
for BP1, BP2 and BP3. We applied the Feature
Selection technique to filter variables according to
their relevance. The C&RT (Standard Classification
Trees with Deployment) technique is used to build a
decision tree that explicitly shows the relation
among the relevant external variables, the process
outcomes and the process activities outcomes for
predicting the BP goal.
Table 2 shows the list of relevant external variables
per business processes identified by BPECREL. Line
2 of Table 2 shows 2 variables (Z and T) with p-value
lower than 0.05 for BP1, among the 4 possible
external variables shown in Table 1. These 2
variables stand as the most important predictors to
determine the BP1 goal. The p-value of a variable is
inversely proportional to its relevance, that is, the
lower a p-value of a variable is for a specific process
BPi, the more relevant is this variable for this
process. For example, in Table 2, the most relevant
external variable for BP1 is T, the 2
nd
most relevant is
Z; in the case of BP2, the most relevant external
variable is W, followed by N, M and Z. For BP3, the
most relevant variable is Z, followed by Y, M and
finally N.
Step 8.4 (Data Mining) – Decision trees are
powerful tools for classification and prediction that
can be generated by data mining techniques. In this
step, we show an example of a decision tree C&RT
(Figure 2).
Step 8.5 (Interpretation/Evaluation) – The
decision tree C&RT of Figure 2 shows the relation
between the relevant external context variables, the
relevant process activities outcomes and the relevant
process outcomes of BP1 and its Goal 1. The Goal 1
of BP1 is represented by a binary outcome
(dependent) variable “Goal 1” that can have 1 of 2
values: “bad” or “good”.
Table 1: Identified candidate external variables per main business process.
Business
Processes
External
Var X
External
Var Y
External
Var Z
External
Var W
External
Var M
External
Var N
External
Var T
BP Goal
BP1 Yes - Yes Yes - - Yes Goal 1
BP2 Yes - Yes Yes Yes Yes Yes Goal 2
BP3 Yes Yes Yes - Yes Yes - Goal 3
Table 2: p-Value of relevant external variables per business process.
Business
Processes
External
Var X
External
Var Y
External
Var Z
External
Var W
External
Var M
External
Var N
External
Var T
BP Goal
BP1 - - 0,0002 - - - 0,0001 Goal 1
BP2 - - 0,04 0,001 0,0003 0,0002
-
Goal 2
BP3 - 0,0002 0,0001 - 0,03 0,04 - Goal 3
KMIS2012-InternationalConferenceonKnowledgeManagementandInformationSharing
94
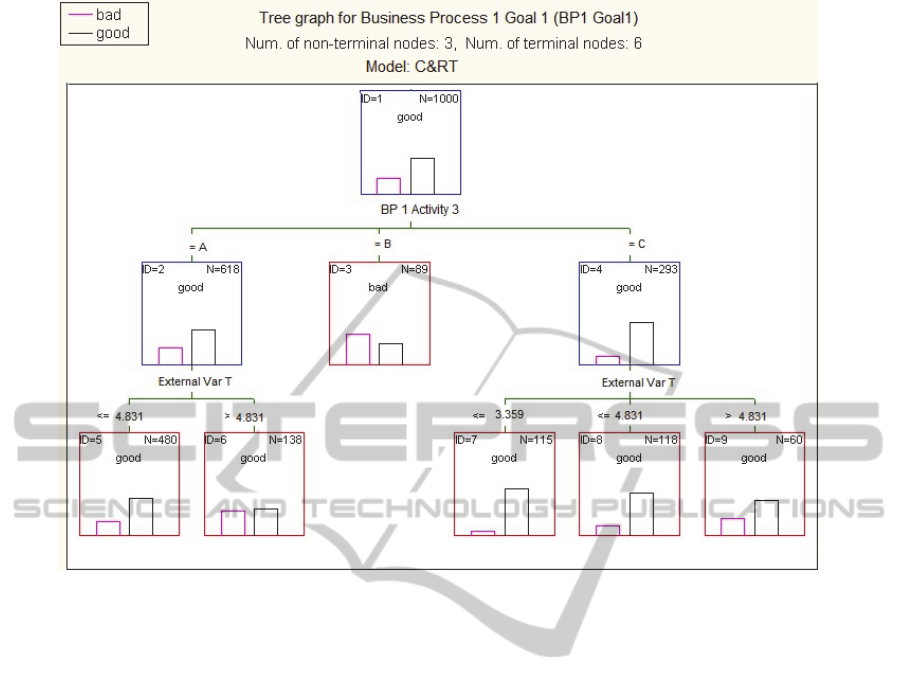
Figure 2: Part of the decision tree C&RT for the Business Process 1 considering the best predictor variables to the
dependent variable Goal 1 of BP1.
Each box in the tree of Figure 2 shows the number
of instances classified at that node and the
distribution of the dependent variable values
(Goal1). The root node (ID=1) contains 1,000
instances (i.e. all the instances in the dataset), and
splits data to 3 descendants based on the outcome of
“BP 1 Activity 3” (A, B or C). The central root
descendant (ID=3) contains 89 instances, where
most of them lead to Goal 1 as “bad”. This node is
not split further because most instances have the
same value of Goal 1 (“bad”). The other 2 root
descendants split further based on the “External Var
T” predictor variable. These split resulted in 5 leaf
nodes. The second leaf node (ID=6) clearly shows
the relevance of the external variable to the process
activity 3, by evidencing that when the “External
Var T” raises above 4.831 then both Goal 1
outcomes from BP1 occur with almost the same
probability. This may fire a change during the
process execution, with the process manager taking
actions for maximizing the chances of the goal of
BP1 being “good” (or, otherwise, minimizing the
chances of being “bad”).
5 CONCLUSIONS
5.1 Analysis and Discussion
The COBIT Framework relates COBIT 5 processes
to IT goals, and these to enterprise goals. The use of
BPECREL method in COBIT allowed not only to
discover which external variables should be
monitored, but also to know which business
processes where impacted by these variables. The
BPECREL method can go deeply until discovering
the activities of business processes that were
impacted by these external variables.
The models generated by the BPECREL method
allow the decision makers to take agile and proactive
actions, such as quickly updating a business activity
or a whole business process when there is a specific
change in an external variable, since the models
show the effects this change has produced in the
past.
It is important to note that a possible external
variable identified on BPECREL may not have its
relevance identified by the method. This may
happen when the variable was not enough relevant
to the BP or when the dataset did not have enough
ImprovingEnterpriseITGovernanceandManagementbyApplyingCompetitiveIntelligenceandExternalContext
Discovery on COBIT 5.0
95

information characterizing its relevance. The
decision makers may decide to monitor or not the
external variables that were not relevant after
applying BPECREL. In cases that a variable is
related to many BPs (as with External VarX in
table1 and table 2), it may be worthy monitoring it
even if its relevance was not detected. Moreover, the
number of impacted BP by an external variable may
increase its relevance. For example, even though
VarZ is not considered the most relevant, it impacts
the greatest number of BPs.
We can also observe that BPECREL is
associated with some other activities of MEA03. It is
possible to assess the impacts of variations on
external variables such as legal aspects that biased
the process even positively or negatively and thus
helping to make previsions while tendencies to new
deviations occur.
However, the discovered knowledge depends on
the amount of detailed information available in the
processes logs. Thus, it is essential to collect the
appropriate information about the execution of
activities within the enterprise.
5.2 Final Considerations and Future
Work
The application of BPECREL processes, such as
illustrated in this paper, highlights opportunities for
integration with other COBIT 5 processes. For
example, knowledge management initiatives may
store all knowledge gained in applying BPECREL to
facilitate their subsequent reuse in decision making;
moreover, innovation management initiatives may
adopt BPECREL to come up with opportunities for
process improvements.
Supporting the identification and prioritization of
variables to be considered in the context of the
external environment allows that changes in those
variables might trigger decision making, by adapting
the process (new requirements) or implementing
new business rules. Those are typical issues that IT
processes should also understand and provide fast
answers. Therefore, the knowledge gained on
business are reflected and aligned with actions in IT
processes.
As future work we suggest conducting case
studies to validate the proposal of improving COBIT
by applying the BPECREL method in the MEA03
process and in other COBIT 5 processes, such as
innovation management and risk management;
improving COBIT by creating a new COBIT 5
process or adapting a exiting one to centralize all
competitive intelligence activities used by COBIT 5,
such as defining external variables in the innovation
management and in MEA03 process. This could be
done by adapting the knowledge management
process. We also suggest applying the BPECREL
method in other COBIT 5 processes using all
surveillance areas proposed in the BPECREL
method and not the surveillance areas indicated in
some COBIT processes.
REFERENCES
Fayyad, U. M., Piatetsky-Shapiro, G., Smith, P. e
Uthurusamy, R. 1996. Advances in Knowledge
Discovery and Data Mining. AAAI/MIT Press.
Herring, J. P. 1999. Key Intelligence Topics: A Process to
Identify and Define Intelligence Needs. Competitive
Intelligence Review, Vol. 10, No. 2.
Herring, J. P., Francis, D. B. 1999. “Key Intelligence
Topics: A Window on the Corporate Competitive
Psyche”, Competitive Intelligence Review 10(4).
ISACA, 2012a. COBIT5: A Business Framework for the
Governance and Management of Enterprise IT. ISBN
978-1-60420-237-3. United States of America.
http://www.isaca.org/COBIT. April/2012.
ISACA, 2012b. COBIT5: Enabling Processes. ISBN 978-
1-60420-241-0. United States of America.
http://www.isaca.org/COBIT. April/2012.
ISACA, 2012c. Comparing COBIT 4.1 and COBIT 5.
https://www.isaca.org/COBIT/Documents/COBIT5-
Compare-With-4.1.ppt. April/2012.
ISACA, 2012d. Governance, risk management and
compliance (GRC). http://www.isaca.org/COBIT/
Documents/COBIT5-and-GRC.ppt. April/2012.
Porter, Michael E., 1979. How competitive forces shape
strategy, Harvard business Review, March/April 1979.
Ramos, E. C., 2011. BPECREL: A Method for
Discovering Relevant External Context Variables
Associated with Business Processes. MSc thesis.
NP2Tec, Department of Applied Informatics, Federal
University of the State of Rio de Janeiro (UNIRIO),
Rio de Janeiro, Brazil. (In Portuguese).
Ramos, E. C., Santoro, F. M., Baiao, F., 2010. Process
improvement based on External Knowledge Context.
ACIS 2010. Brisbane, Australia.
Ramos, E. C., Santoro, F. M., Baiao, F., 2011. A Method
for Discovering the Relevance of External Context
Variables to Business Processes. KMIS 2011. Paris,
France.
Rosemann, M., Recker, J., Flender, C., 2008.
"Contextualization of Business Processes,"
International Journal of Business Process Integration
and Management, vol. 3, pp. 47-60.
The Times, SLEPT analysis. 100 Edition. 2010.
www.thetimes100.co.uk. Last accessed Apr/2010.
Vuori, V., Pirttimäki, V., 2005. Identifying of Information
Needs in Seasonal Management, Frontiers of e-
Business Research, pp. 588-602.
KMIS2012-InternationalConferenceonKnowledgeManagementandInformationSharing
96
