
A FORWARD PRIVATE PROTOCOL BASED ON PRNG
AND LPN FOR LOW-COST RFID
Xiaolin Cao and Maire O’Neill
Centre for Secure Information Technologies (CSIT), Queen’s University Belfast, Belfast, U.K.
Keywords: RFID, Authentication, Forward privacy, PRNG, LPN.
Abstract: Low-cost Radio Frequency IDentification (RFID) tags are extremely resource-constrained devices, therefore,
difficult to defend against corruption attacks. Meanwhile, forward privacy considers how to preserve the
privacy of compromised tags. The majority of existing authentication protocols uses cryptographic hash
functions to preserve forward privacy under the random oracle model, but the expensive hardware cost of a
cryptographic hash function exceeds the budget of low-cost tags. In this paper, a novel forward private
protocol for low-cost RFID applications is proposed. It is composed of a pseudorandom number generator
(PRNG) and a learning parity with noise (LPN) problem. In comparison to previous protocols, the proposed
protocol achieves a high forward privacy level and requires a small hardware cost. The proofs of security,
correctness and forward privacy for the proposed protocol are provided under the standard model.
1 INTRODUCTION
RFID technology is increasingly being used in
access control, product tracking and logistics
management automation industries. A typical RFID
system is composed of a powerful reader ℛ
(including the backend database system) and a
number of resource constrained tags
{
}
. It is
difficult to add security features to protect them
from corruption attacks. Meanwhile, forward
privacy considers the privacy preserving problem
after a tag is compromised (Ohkubo, 2003). Thus,
developing forward private authentication protocols
for low-cost tags is a major security challenge for
the future development of RFID technology.
Much research have been carried out into
lightweight protocols based on the learning parity
with noise (LPN) problem, such as HB (Hopper and
Blum, 2001), and its variants (Juels and Weis, 2005;
Katz and Shin, 2006; Gilbert et al., 2008). These
protocols utilize the hamming weight of a Bernoulli
noise vector to achieve authentication purpose. The
operations in the LPN problem involve the
calculation of binary inner products and random
noise bit generation. Computing the binary inner
product only requires bitwise AND and XOR
operations that can be computed on the fly.
Therefore the LPN problem is a hardware-friendly
primitive, and very attractive to low-cost RFID
security. But these LPN-based protocols do not
focus on the forward privacy. Previous work by Cao
and O’Neill (2011) has employed the LPN problem
to protect the forward privacy in the F-HB protocol,
in which the LPN is used to update the key chain,
and a secure PRNG to implement a message
authentication code to defend against the GRS-MIM
attack (Gilbert et al., 2008) for the LPN problem.
However, the proposed protocol in this paper uses
the PRNG to update the key chain, uses the LPN
problem to calculate the authenticators, and does not
worry about GRS-MIM attack.
In this paper, we improve on previous work and
propose a forward private authentication protocol,
PLFP, suitable for low-cost RFID applications.
Firstly, it is composed of a secure PRNG and a LPN
problem, which can be efficiently implemented.
Secondly, it is provable secure and forward private
under the standard model rather than the random
oracle model.
The rest of the paper is organized as follows. In
section 2, the LPN problem is defined. In section 3,
the RFID security and privacy model is defined. The
proposed PLFP protocol and proof are described in
section 4. A hardware cost analysis and comparison
results are given in section 5. Section 6 concludes
this paper.
287
Cao X. and O’Neill M..
A FORWARD PRIVATE PROTOCOL BASED ON PRNG AND LPN FOR LOW-COST RFID.
DOI: 10.5220/0003520802870292
In Proceedings of the International Conference on Security and Cryptography (SECRYPT-2011), pages 287-292
ISBN: 978-989-8425-71-3
Copyright
c
2011 SCITEPRESS (Science and Technology Publications, Lda.)

2 LPN PROBLEM
Let Ber
denote the Bernoulli distribution with
parameter ∈(0,1/2), i.e. a bit ←Ber
is such
that Pr
[
=1
]
= and Pr
[
=0
]
=1−, while an
-bit vector ←Ber
,
is such that each bit of is
drawn according to Ber
. Let
denote an oracle
that returns a uniformly random -bit string. Let
Hwt() denote the hamming weight of vector . Let
be a random (×) binary matrix, let be a
random -bit vector, let ∈(0,1/2) be a noise
parameter, and let be a random -bit vector
distributed according to Ber
,
, such that Hwt()≤
. The LPN problem is such that given , , and
←(∙)⊕, find a -bit vector such that
Hwt((∙)⊕)≤.
For a fixed -bit string , let
,
denote the
oracle returning an independent (+1)-bit string
according to the distribution:
(,(⋅)⊕)|∈
{
0,1
}
,←Ber
.(1)
And for a fixed
(
×
)
matrix , let
,
be the
oracle returning an independent (+)-bit string
according to the distribution:
(,(⋅)⊕)|∈
{
0,1
}
,←Ber
,
.(2)
Lemma 1 (Katz and Shin, 2006). Assume there
exists an algorithm making oracle queries,
running in time , and
|
Pr
[
,
(
1
)
=1
]
−
Pr
[
(
1
)
=1
]
|
≥, then there is an algorithm
making (∙
log) oracle queries, running in
time (∙
log), and such that
Pr
[
,
(
1
)
=|∈
{0,1}
]
≥/4. (3)
Definition 2.1. The advantage of distinguishing
the oracle
,
and
in time , Adv
, is defined
as follows:
|
Pr
[
,
(
1
)
=1
]
−Pr
[
(
1
)
=1
]|
(4)
where the maximum value is taken over all
running in time at most with no more than oracle
queries.
In the following sections, we use LPN
(∙) to
represent the LPN problem. Every instance of
LPN
(∙) has three inputs (, , ) and one output
(), such that
=LPN
(
,,
)
=
(
⋅
)
⊕. (5)
Lemma 2. Assume there exists an algorithm
making oracle queries, within time , and such that
|
Pr
[
,
(
1
)
=1
]
−Pr
[
(
1
)
=1
]|
≥. Let
be the time taken to calculate a
,
instance.
Then there is an algorithm making () oracle
queries, running in time +
()
, and such that
|
Pr
[
,
(
1
)
=1
]
−Pr
[
(
1
)
=1
]|
≥
. (6)
Proof. We use a hybrid argument technique. Let ′
denote a (−)× binary matrix. We first define
the following hybrid distribution
with ∈[0,] as
(
,,
(
⋅
)
⊕
)
, where ∈
{
0,1
}
, ∈
{
0,1
}
,
←Ber
,
.
Upon a (+1)-bit input, draws a random
∈[0,] to construct a (+)-bit input as ’s
input. When <, it also needs to draw a random
(−)× binary matrix ′. It is straightforward
that when ’s input complies with
, the
∈[1,]; when ’s input complies with
,
, the
∈[0,−1]. The distribution of
is the same as
, and
the same as
,
. And uses ’s
outputs as its outputs. Thus
|
Pr
[
,
(
1
)
=1|
]
−Pr
[
(
1
)
=1
]|
=
1
(
(
1
)
=1)
,
− (
(
1
)
=1)
,
=
1
|
Pr
[
,
(
1
)
=1
]
−Pr
[
(
1
)
=1
]|
≥
.
Defintion 2.2. The LPN problem LPN
(∙) is
said to be (,)-secure if there is no adversary can
distinguish
,
from
with advantage
Adv
(
)
≥.
Lemma 3. Let
be the time taken to calculate a
,
instance, and LPN
(∙) be a (,
)-secure LPN
problem. Suppose there is at most one valid
,
instance such that
=LPN
(,,
), and invalid
,
instances such that {
≠LPN
(
,,
)
}
,
then based on the information above, the probability
of obtaining a valid
,
instance is upper-bounded
by
+2
within time at most +(
):
Pr
[
(
)
=LPN
(
,,
)]
≤
+2
. (7)
Proof. We claim that if there is an adversary able
to guess a valid pair utilizing the above information
with advantage at least
in time at most , then we
can use to construct an algorithm to distinguish
,
and
with advantage at least
+2
with
time at most +(
).
After the algorithm is given access to an oracle
returning a (+)-bit string , randomly draws
(+)-bit strings to form the input to . When ’s
oracle is
, these strings do not need any
modification. When ’s oracle is
,
, then needs
some time to make sure that the other random
string are not
,
instances. These operations can
SECRYPT 2011 - International Conference on Security and Cryptography
288

consume time at most (
).
When ’s oracle is
, it is clear that outputs
a valid pair with probability of 2
, because this
uniformly distributed strings provide no useful
information. When ’s oracle is
,
, outputs a
valid pair with probability of
. We let output 1
when A outputs a valid pair, else return 0. Then
|
Pr
[
,
(
1
)
=1
]
−Pr
[
(
1
)
=1
]|
≥
−
2
. From Lemma 2, we thus we get
≤2
+
,
and conclude the proof.
Lemma 4. Let LPN
(∙) be a (,
)-secure LPN
problem. Then the probability of obtaining a
collision between function LPN
(
,
,∙) and
LPN
(
,
,∙) is upper-bounded by
+2
within
time at most +(
), such that
Pr
[
LPN
(
,
,∙)=LPN
(
,
,∙)
]
≤
+2
.(8)
Proof. We claim that if there is an algorithm able
to produce a valid collision utilizing the above
information with advantage at least
in time at
most , then we can use to construct an algorithm
to distinguish
,
and
with advantage at
least
+2
with time at most +(
).
After algorithm is given access to an oracle
returning (+)-bit string , constructs a
,
instance
to form the input (,
) to . Let
()
be ’s first -bit binary digit, and
()
be ’s last l-
bit binary digit. The collision implies that
()
=
()
. When ’s oracle is
, then Pr
()
=
()
≤2
. When ’s oracle is
,
, then
Pr
()
=
()
≥
. When finds a collision,
outputs ‘1’, otherwise, ‘0’ is returned. uses ’s
output as its output.
|
Pr
[
,
(
1
)
=1
]
−
Pr
[
(
1
)
=1
]
|
≥
−2
. So we get
<
2
+
, and conclude the proof. We note that this
is a very loose upper-bound for the collision
probability.
3 RFID SECURITY DEFINITONS
In this paper, an adversary is assumed to be a
probabilistic polynomial algorithm that is allowed to
perform oracle queries during attacks. Five oracles
are defined as follows.
: It invokes the reader ℛ to start a new
authentication and returns the challenge message .
: It invokes tag to responds with the
response message to challenge message .
: It returns intercepted and modified challenge,
, and response messages, .
: It returns the final authentication result.
: It returns the current key and internal state
information of a tag , and also updates the key and
state information of tag if necessary.
Definition 3.1 (,)-adversary. An adversary
with his running time upper-bounded by and the
ability to disturb at most authentication exchanges
in this interval is called a (,)-adversary.
Definition 3.2 Security. The authentication
protocol is said to be
(
,,
)
-secure if there exists
no (,) -adversary who can impersonate an
uncorrupted with the probability more than .
Definition 3.3 Correctness. The authentication
protocol is said to be (,,)-correct if there is no
(,)-adversary who can make an uncorrupted tag
being rejected in an undisturbed authentication with
the probability more than .
The forward privacy experiment is a two phase
experiment. During the 1
st
phase, adversary
disturbs ∈
[0,] authentications with oracle
(
)
, and outputs two uncorrupted challenge
tags {
,
}. On entering the 2
nd
phase, the
experiment chooses a random bit , and is
concealed from . Then continues to disturbs with
oracle (
)
. Aftern is given access to the
oracle query to obtain the internal states of
and
, is no longer able to access any oracle related
to
and
, but can access any other oracles.
Eventually, is asked to guess the random bit by
outputting a bit ′.
Definition 3.4. The advantage of a
(
,
)
-
adversary in the above experiment is defined as:
Adv
=
|
Pr
[
outputs1
]
−1/2
|
. (9)
Definition 3.5 Forward Privacy. An authen-
tication protocol is said to be (,,)-forward-
private if there exists no
(
,
)
-adversary who can
make the Adv
more than .
4 PROPOSED PROTOCOL
The proposed PLFP protocol is depicted in Figure 1.
On each tag , there is a (,
)-secure PRNG
:{0,1}
→{0,1}
with computation time
as
defined in Berbain et al. (2009), an LPN problem
LPN
(∙), and a void function GenSec(∙), which is
used to derive a secret matrix of the LPN problem
from the secret state of the PRNG. During the
initialization stage, the tag shares its initial
internal state, a randomly -bit secret
, with the
reader. The PLFP protocol runs as follows:
1. The reader ℛ sends a challenge ∈{0,1}
to
the tag .
A FORWARD PRIVATE PROTOCOL BASED ON PRNG AND LPN FOR LOW-COST RFID
289

2. The tag first derives a matrix from its
current state using ←GenSec(), and a
noise vector ←Ber
,
, where is derived
using PRNG in the previous transactions from
. Secondly, it updates internal state ←
(
)
.
Finally, the tag answers ←LPN
(,,).
3. Upon receiving the response , the reader ℛ
verifies the response by searching tags state
chains: for each tag in the system, the reader
uses its last authenticated state
to run a
sliding window length to look for a state
satisfying ⨁(⋅)≤ . If such a
match is found, the reader accepts the tag and
updates its view of the tag’s state by the
successful match state
←
. Otherwise
the reader rejects the tag and does not update its
view.
Figure 1: The proposed PLFP protocol.
The false rejection probability,
, and false
acceptance probability,
, in every authentication
session due to the LPN problem can be defined as
=
∑
(1−)
, and
=
∑
2
.
4.1 Security
Theorem 1. Let LPN
(∙) be a (,
)-secure LPN
problem. The proposed PLFP protocol is (,
,
)-
secure with
=−
−
(
+1
)
and
=
+
(
2
+
)
+
.
Proof. The successful impersonation is the result
of (i) adversary can guess a valid instance of
oracle
,
such that
(
)
=LPN
(
,,
)
, and (ii)
adversary is falsely accepted.
We show that if there is an adversary able to
impersonate a legitimate tag with advantage at least
within time at most
, then we can use adversary
as a subroutine to construct an algorithm to
distinguish ()=
(
)
,
(
)
,…,
(
)
from a purely random sequence of -bit in time
at most
with an advantage greater than
.
One can easily check that when the input
sequence received by is
(
)
, then perfectly
simulates the interaction between the tag, the reader,
and the adversary . Thus, the probability that
outputs ‘1’ is equal to the advantage of ,
. Let us
analyze the probability that outputs ‘1’ while the
input
is a truly random string. There are at most 1
valid pair for
, and at most invalid pairs for
.
Using Lemma 3, we could bound the possibility of
guessing a valid
,
instance with the above
information is upper-bounded by (2
+
). The
second reason is the coherent property of the LPN
problem, which is upper-bounded by
. Then we
combine the two reasons to have
≥
−
(
2
+
)
−
. Using Theorem 1 in Berbain et
al. (2009), we have
≤
.
These two last inequalities show that
≤
+
(
2
+
)
+
.
4.2 Correctness
Theorem 2. Let LPN
(∙) be a (,
)-secure LPN
problem. The proposed PLFP authentication
protocol is (,
,
)-correct with
=−
−
(
+1
)
,
=
(
−1
)
(
2
+
+
)
+
+
+
.
Proof. There are two situations when a
legitimate tag is rejected by the reader: (i) an
unrecoverable desynchronization between them
happens, and (ii) a false rejection happens.
Let us analyze the first situation. The first cause
is a successful impersonation attack. In a system
composed by tags, the total possible impersonation
advantage is upper-bounded by
. The second
cause is a collision event. According to Lemma 4,
the collision probability of any two tag’s responses
is at most (2
+
) in every session. Another
reason of collision is the false acceptance, which is
upper-bounded by
. For each tag, the longest
searching chain in every authentication is . So for a
system with tags with the longest search chain
length , the collision probability of one
undisturbed authentication of a legitimate tag is
upper-bounded by
(
−1
)
(2
+
+
) in
the case that the state sequence is uniformly random
Reader ℛ Tag
∈{0,1}
Initial Shared Secret:
←Ber
,
←GenSec
(
)
←
(
)
←LPN
(
,,
)
For each tag, search a state chain starting from
:
For 0≤≤ : {
←GenSec
(
)
If ⨁(⋅)≤ : {
accept the tag,
←
, and break out }
←
(
)
}
Otherwise, reject the tag
SECRYPT 2011 - International Conference on Security and Cryptography
290

strings. The second rejection situation is upper-
bounded by
.
At the end, combining the two rejection
situations, the advantage of a correctness adversary
can be represented as
≤
(
−1
)
(
2
+
+
)
+
+
+
.
4.3 Forward Privacy
Theorem 3. Let LPN
(∙) be a (,
)-secure LPN
problem. The PLFP authentication protocol is
(,
,
) -forward-private with
=−
−
(
+1
)
and
=
(
+
)
+
(
3+2
)
.
Proof. The following proof is composed of two
steps. In the first step, we show adversary can be
used to construct a distinguisher between a pseudo
random number sequence and a real random number
sequence, and in the second step we show that the
two sequences cannot be distinguished with a non-
negligible advantage.
First, the distinguisher has an input of the as
=(
,…,
,
,…,
,…
,
,
). The can
take two different distributions, and ′ . In
distribution : the (
)
, (
)
,
and
are the pseudo random sequences constructed from
two seeds
and
through
←
(
)
and
←
(
)
. So the function of Distribution is
used to simulate the two tags
and
. In
distribution ′: the sequences are random numbers.
For the distribution , correctly simulates the
view of except for successful impersonation
attacks and false rejections. Let denote the
abnormal events in the simulation of , and
denote the complementary event. The probability of
is (−)
(
+
)
. The probability that
algorithm outputs ‘1’ with distribution is
analyzed as: Pr
[
=1|∈
]
=
∑
Pr
[
=1|∈,
]
and Pr
[
=1|∈
,
]
≥Pr
[
=1|∈,,
]
−Pr
[
|∈,
]
,
where Pr
[
=1|∈,,
]
represents the
probability that algorithm outputs ‘1’ without
abnormal events, so it equals the probability that
adversary successes, and Pr
[
|∈,
]
represents the probability of the abnormal events
happening. So we have Pr
[
=1|∈,,
]
=
+
, Pr
[
|∈,
]
=
(
−
)(
+
)
, and
Pr
[
=1|∈
]
≥
+
−
(
+
)
. In
the case of distribution ′ , is not able to
distinguish between the two purely random
sequences (
)
and (
)
and therefore
Pr
[
(
)
=1|∈
]
=1/2.
Combined with the above analysis, we obtain:
|
Pr
[
=1|∈
]
−Pr
[
=1|∈
]|
≥
−
(
+
)
. Therefore it shows that the
probability of the distributions and ′ can be
distinguished in time at most
+2
with an
advantage at least
−
(
+
)
. This can be
written as: Adv
,
+2
≥
−
(
+
)
.
According Lemma 8 in Berbain et al. (2009), we
use
+2
as input to obtain: Adv
,
+
2
)
≤
(
3+2
)
.
Combining the last two inequalities, we have
≤
(
+
)
+
(
3+2
)
.
5 ANALYSIS AND COMPARISON
Firstly, an analysis of the hardware cost of the tag is
given. The secure PRNG can be implemented very
efficiently thanks to the progress of stream ciphers
in the eSTREAM project (Cid and Robshaw, 2009).
To provide an 80-bit security level, Grain-v1 needs
only 1,294 gates. Grain-v1 uses two shift register
arrays for an initialization value (IV) and a state
value as inputs, but the PRNG only needs one shift
register array for its secret state as input. Therefore,
if Grain-v1 is used, the hardware gate number will
be less than 1,294 gates. The secret and noise
vector do not need additional storage space,
because they can be easily derived from the state and
output of the PRNG. The inner product and XOR
operation of the LPN problem can share the
hardware with the PRNG, because Grain-v1 also
uses XOR and AND operations. Then the overall
crypto hardware cost is composed of a PRNG and
some multiplexers. Therefore, the total estimated
hardware cost should be no more than 2,000 gates,
since the cost of multiplexers is no more than the
cost of registers for the IV. Additionally, the
hardware cost of the LPN problem is no more than a
CRC function, so this protocol is suitable for EPC
Class-1 Generation-2 tags (Juels, 2006), as the main
hardware cost of such tags is a PRNG and a CRC.
Secondly, the proposed protocol is compared to the
previous protocols, and the results are listed in Table
1 and 2. (i) It can be observed that this paper
provides a high forward privacy level, that is to say,
the forward privacy of all session can be protected.
Although the O-FRAP (Le et al., 2007) and PEPS
(Billet et al., 2010) protocols can provide infinite
desynchronization resistance at the protocol level,
A FORWARD PRIVATE PROTOCOL BASED ON PRNG AND LPN FOR LOW-COST RFID
291
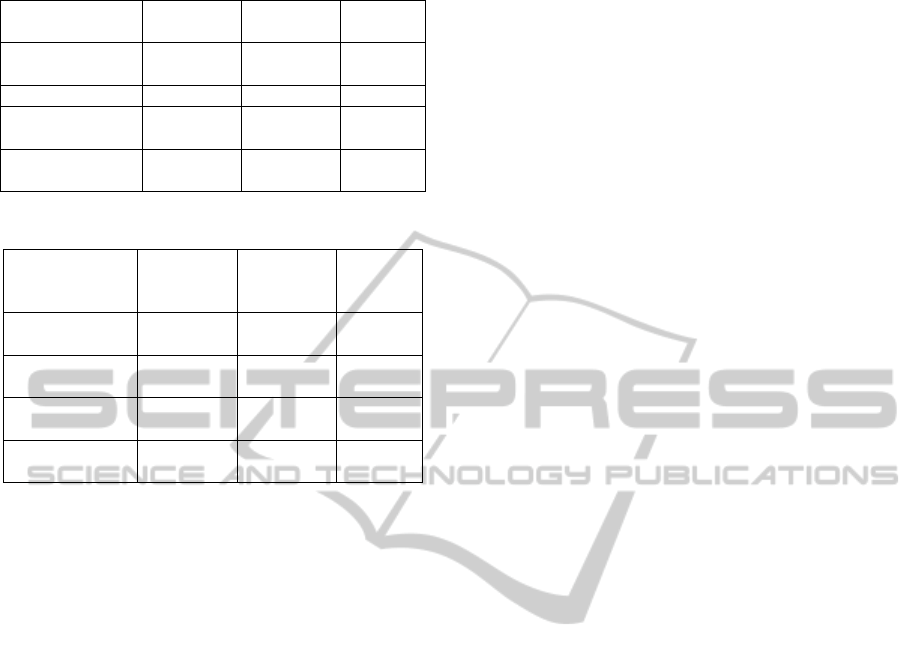
Table 1: Comparison Results 1.
Billet et
al., 2010
Cao, O’Neill,
2011
Le et al.,
2007
Forward Privacy
level
limited limited limited
Proof model standard standard UC
Desynchronizati
on Resistance
Infinite Infinite Infinite
Crypto
hardware cost
≈ 2,000
gates
≈ 3,500
gates
≈ 4,000
gates
Table 2: Comparison Results 2.
Berbain et
al., 2009
Avoine,
Oechslin,
2005
This
paper
Forward
Privacy level
high high high
Proof model standard
random
oracle
standard
Desynchroniza
tion Resistance
< < <
Crypto
hardware cost
≈ 3,500
gates
> 5,000
gates
≤ 2,000
gates
the trade-off is that they provide a limited forward
privacy (i.e., only the forward privacy of successful
sessions is assured). (ii) The hardware cost of the
proposed protocol is similar to that of the PEPS
protocol. But the proposed protocol provides a
higher forward privacy level. (iii) The F-HB (Cao
and O’Neill, 2011) uses the PRNG to implement a
message authentication code, so it consumes more
hardware than the proposed protocol.
6 CONCLUSIONS
In this paper, the PRNG and LPN problem are
proposed to construct a provable secure and forward
private authentication protocol. The PRNG and LPN
problem can be efficiently implemented on a tag
using only one low-cost stream cipher, so that this
protocol is suitable for low-cost RFID applications.
According to the hardware analysis, the proposed
protocol can meet the hardware constraints of the
EPC Class-1 Generation-2 tags, provide a high
forward privacy, and require a small hardware cost
on the tag.
RFERENCES
Avoine, G. and Oechslin, P. 2005. A Scalable and
Provably Secure Hash-Based RFID Protocol. IEEE
International Workshop on Pervasive Computing and
Communication Security.
Berbain, C., Billet, O., Etrog, J. and Gilbert, H. 2009. An
Efficient Forward Private RFID Protocol. ACM
Conference on Computer and Communications
Security (CCS).
Billet, O., Etrog, J. and Gilbert, H. 2010. Lightweight
Privacy Preserving Authentication for RFID Using a
Stream Cipher. International Workshop on Fast
Software Encryption (FSE)
Cid, C. and Robshaw, M. 2009. The eSTREAM Portfolio
2009 Annual Update. Available from:
http://www.ecrypt.eu.org/stream/.
Cao, X. and O’Neill, M. 2011. F-HB: An Efficient
Forward Private Protocol. Workshop on Lightweight
Security & Privacy: Devices, Protocols and
Applications (Lightsec2011).
Gilbert, H., Robshaw, M. J. B. and Seurin, Y. 2008. HB
#
:
Increasing the Security and Efficiency of HB+. Annual
International Conference on the Theory and
Applications of Cryptographic Techniques,
EUROCRYPT.
Hopper, N. J. and Blum, M. 2001. Secure Human
Identification Protocols. International Conference on
the Theory and Application of Cryptology and
Information Security, ASIACRYPT.
Juels, A. and Weis, S. A. 2005. Authenticating Pervasive
Devices with Human Protocols. International
Cryptology Conference, CRYPTO.
Juels, A. 2006. RFID Security and Privacy: A research
Survey. IEEE Journal on Selected Areas in
Communications.
Katz, J. and Shin, J. S. 2006. Parallel and Concurrent
Security of the HB and HB+ Protocols. Annual
International Conference on the Theory and
Applications of Cryptographic Techniques,
EUROCRYPT.
Le, T. V., Burmester, M. and de Medeiros, B. 2007.
Universally Composable and Forward-secure RFID
Authentication and Authenticated Key Exchange.
ACM Symposium on InformAtion, Computer and
Communications Security (ASIACCS).
Ohkubo, M., Suzuki, K. and Kinoshita, S. 2003.
Cryptographic Approach to Privacy-Friendly Tags.
RFID Privacy Workshop.
SECRYPT 2011 - International Conference on Security and Cryptography
292
