SECURITY MODELS FOR HETEROGENEOUS NETWORKING
Glenford Mapp, Mahdi Aiash, Aboubaker Lasebae
School of Engineering and Information Sceince,Middlesex University, Hendon, London, U.K.
Raphael Phan
Electronic and Electrical Engineering, Loughborough University, Loughborough, U.K.
Keywords: Heterogeneous networks, Security models, Integrated security module, Open network, Multi-layer.
Abstract: Security for Next Generation Networks (NGN) is an attractive topic for many research groups. The Y-
Comm security group believes that a new security approach is needed to address the security challenges in
4G networks. This paper sheds light on our approach of providing security for the Y-Comm architecture as
an example of 4G communication frameworks. Our approach proposes a four-layer security integrated
module to protect data and three targeted security models to protect different network entities, thus
providing security in different situations without affecting the dynamics of the 4G networks.
1 INTRODUCTION TO Y-COMM
Future communication systems must allow
ubiquitous connectivity where users are always
connected from anywhere and at any time. The need
for continuous connection is being met by the
development and deployment of a number of
wireless technologies including 3G/HSPDA, WLAN
with 802.11n being the latest network of being
deployed, WiMax and satellite communications.
However, the widespread deployment of
wireless networks will have a significant impact on
the evolution of the Internet. These developments
mean that soon, it will not be possible to think of the
Internet as a single unified infrastructure. It would
be better to view the Internet as comprising a fast
core network with slower peripheral networks
attached around the core. The core network will
consist of a super-fast backbone using optical
switches and fast access networks which use ATM
and MPLS. Most of these peripheral networks will
make use of wireless technologies described above.
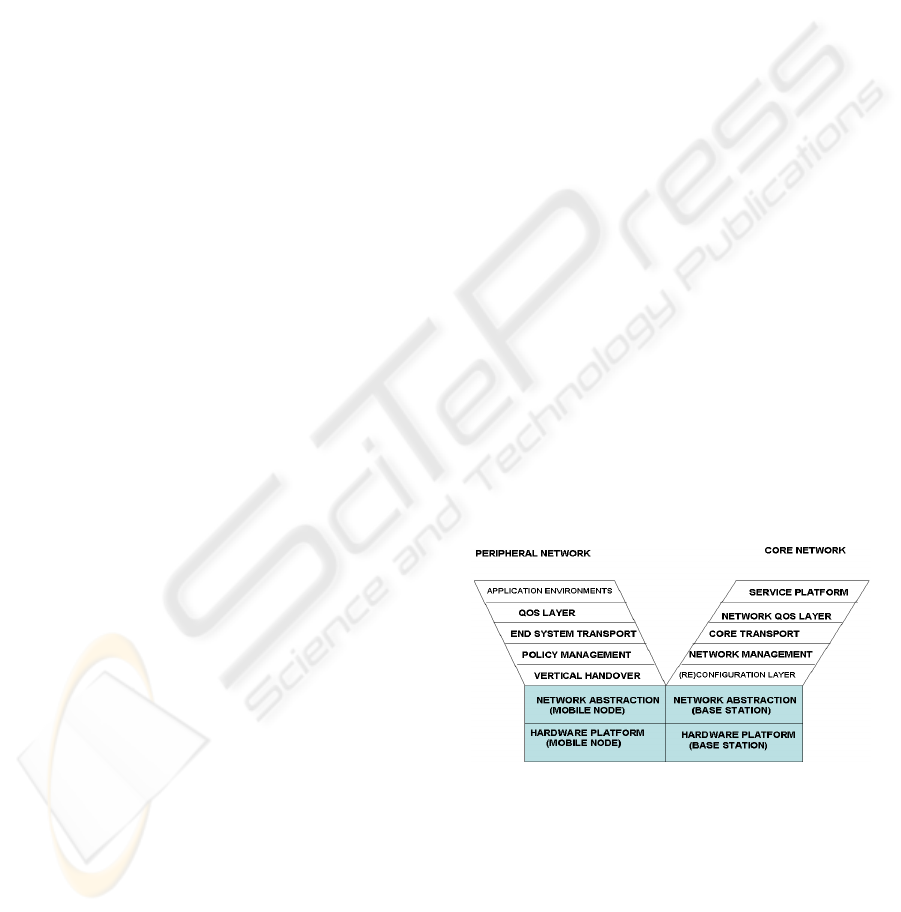
Y-Comm is architecture for heterogeneous
networking. (Mapp, et al., 2006; 2007). The
architecture consists of two frameworks. The
Peripheral framework deals with issues in peripheral
networks while the Core framework deals with
issues in the Core.
The Y-Comm architecture is shown in Figure 1.
In this architecture, the Peripheral Framework and
the Core Framework are brought together to
represent a future telecommunications environment
which supports heterogeneous devices, disparate
networking technologies, network operators and
service providers.
Figure 1: Y-Comm Architecture.
2 Y-COMM SECURITY
FRAMEWORK
Y-Comm employs a multi-layer security model
which must be applied to both the Peripheral and
Core Framework simultaneously to provide total
security. The security layers must work together
318
Mapp G., Aiash M., Lasebae A. and Phan R. (2010).
SECURITY MODELS FOR HETEROGENEOUS NETWORKING.
In Proceedings of the International Conference on Security and Cryptography, pages 318-321
DOI: 10.5220/0003032803180321
Copyright
c
SciTePress
across both frameworks in order to be fully
integrated with the new architecture. The important
point to note is that the need to support
heterogeneous networking with open architectures
means that security should not only protect data but
entities as well.
The highest layer of security is at layer seven and
is called Service and Application Security or SAS.
In the Peripheral Framework, SAS defines the
AAAC functions at the end-device and is used to
authenticate users and applications. SAS in the Core
network provides AAAC functions for services on
the Service Platform in the core network.
The next security layer is called QoS-Based
Security or QBS and is concerned with QoS issues
and the changing QoS demands of the mobile
environment as users move around. In addition, in
order to meet their service-level agreements, servers
may choose to replicate services closer to the current
position of the mobile. So it is necessary to ensure
that core endpoints and peripheral networks are not
overloaded. The QBS layer also attempts to block
QoS related attacks, such as Denial-of-Service
(DoS) attacks on networks and servers.
The next security layer is at layer five, called
Network Transport Security or NTS. In the
Peripheral network, NTS is concerned with access to
and from end-devices and the visibility of these
devices and services on the Internet. In the core
network, NTS is used to set up secure connections
through the core network. So NTS in the Core
Framework involves setting up secure tunnels
between core endpoints using mechanisms such as
IPsec to ensure that moving data across the core
network is done in a secure manner.
Finally, the fourth and last level of security is
defined at layer four but can also encompass layers
three and two. It is called Network Architecture
Security or NAS. In the Peripheral Framework, it
attempts to address security issues involved in using
particular networking technologies and the security
threats that occur from using such a technology. So
when a mobile device wishes to use any given
network, NAS is invoked to ensure that the user is
authorized to do so. NAS also ensures that the local
LAN environment is as secure as possible.
In the core network, NAS is used to secure
access to the programmable infrastructure. NAS in
this context determines which switchlets, routelets or
base-station resources may be used by the network
management system. The full Y-Comm architecture
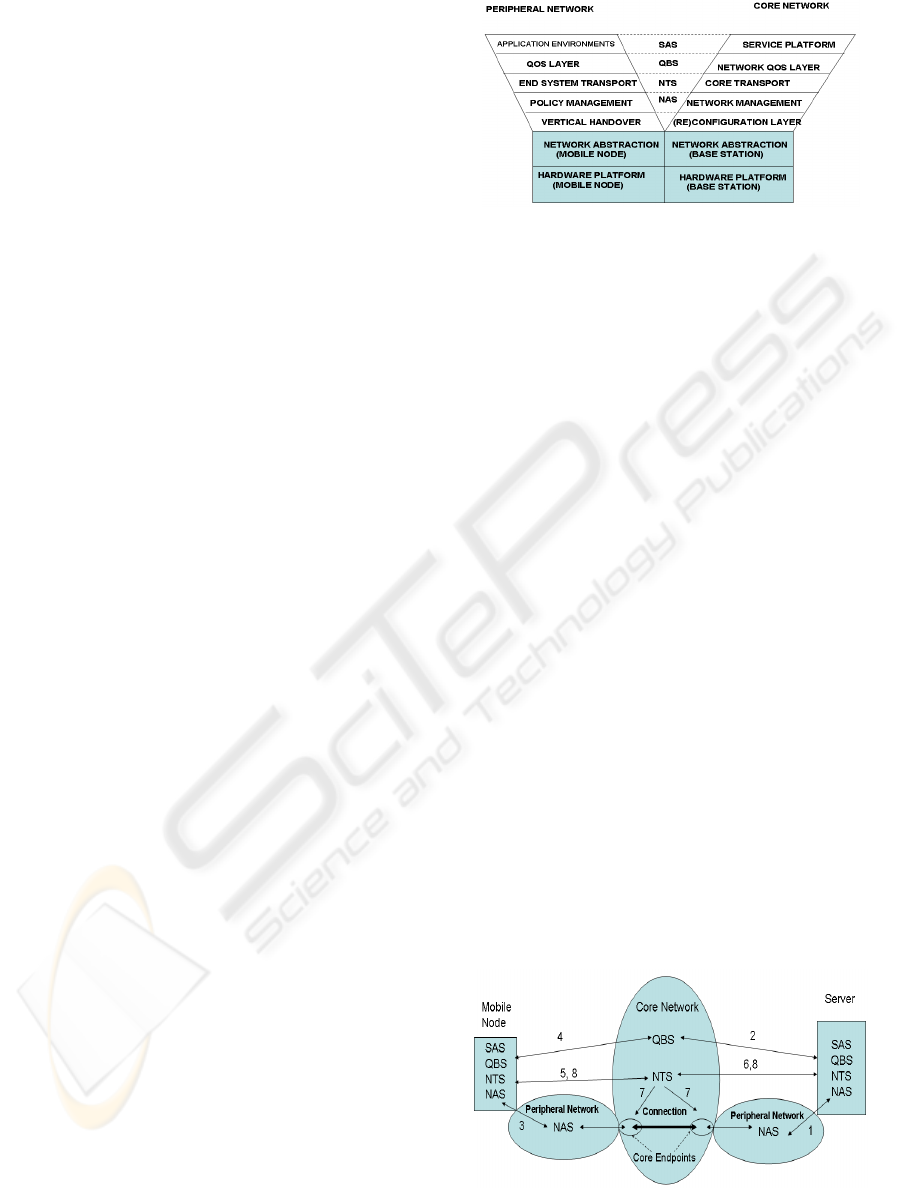
including its security layers is shown in Figure 2.
Since the security framework is integrated with the
Figure 2: Complete Y-Comm Architecture with Security
Framework.
Core and Peripheral frameworks within Y-Comm,
these security functions being part of the
communications architecture can be used to much
greater effect than previous methods.
2.1 Security Models in Y-Comm
The security layers described above are concerned
with the management of secure data transport and
the authentication of mobile devices and services.
However, because Y-Comm is an open architecture,
it is also necessary to protect entities such as users,
servers and network infrastructure. Y-Comm is
therefore able to offer three distinct network security
models (Aiash, et al., 2010). The first model is
called the Connection Security model, the second
security model is called the Ring-Based Security
model and the third security model is called the
Vertical Handover Security model.
2.1.1 Connection Security Model
In this model, the different security layers work
together to establish a connection between a mobile
node and a service being hosted at another site. See
Figure 3.
We can show how the framework is used by
looking at the interaction involved in setting up a
connection. This is shown as a series of steps.
Figure 3: Connection Security Model.
SECURITY MODELS FOR HETEROGENEOUS NETWORKING
319

Step 1: The server is started. The NAS module in
the server talks to the NAS module on the Local
LAN to get access to its wireless infrastructure.
Step 2: The QBS security module on the server
informs the QBS module in the core network about
its Service Level Agreement which contains the QoS
associated with a connection to this service.
Step 3: The mobile node is started. The NAS
module in the mobile node contacts the NAS module
in the peripheral networks to gain access to the
wireless infrastructure.
Step 4: When the mobile node wants to use the
service, the QBS Module in the mobile node
contacts the QBS module in the core network and
asks for a connection with a given quality of service
to be made to the Server. The QBS module returns
two core endpoints which must be used to set up the
connection.
Step 5: The NTS module on the mobile node
contacts the NTS module in the core network and
says that it would like a connection to the server,
using the core endpoints, the QoS and security
parameters.
Step 6: The NTS module in the core network
contacts the NTS module on the server to signal an
incoming call. At this point, the server can also
check the security of the client as well as the
security of the connection.
Step 7: If the server accepts the request, then the
NTS module in the core network joins the two core
endpoints.
Step 8: It then signals to both the client and
server that a connection has been established.
2.1.2 Ring-based Security Model
Ring-based security is an extension of “Off-by-
Default”, an idea introduced by (Ballani, et al.,
2005) See Figure 4. The Ring-Based concept does
not allow servers to be directly accessible over a
WAN such as the Internet without initially
interacting with the network infrastructure. This is
done by using the concept of scope where a server
acts only within a given scope. There are 3 scopes:
Local: Only processes on the same machine are
allowed to use a local server. This is enforced by the
SAS layer on the local machine.
LAN: Only processes on the same network are
allowed to access these servers. This is enforced by
the NAS layer of the Peripheral Network. These
servers must register with a Local DNS and are
made available to mobile devices when users are
cleared to use the peripheral network.
Global: Global Servers are accessible from any
point via the Core Network using Global Services.
This therefore involves the Core NTS and QBS
layers. In addition, servers must register with the
Global DNS.
2.1.3 Vertical Handover Security Model
As shown in Figure 5, in addition to the
Authentication, Authorization, Auditing and Cost
(AAAC) servers, new entities are involved in the
Vertical Handover Security Model (VHSM); the
QoS Brokers (QoSB) which monitor the network
performance and QoS-related issues; it accomplishes
this using admission control and auditing
mechanisms. This model is given by the steps
below:
Step 1: The QBS layer of the MN asks the QBS of
the QoSB about potential target network for
handover with required QoS and security level.
Step 2: The request is passed to the QBS layer of
the Core endpoint.
Step 3: If this information has not been already in
the Core-End point, the QoS Brokers of all the
available networks are probed by the core endpoint.
At the end of this first stage, the MN has a clear idea
of the QoS and security suits available at all
potential networks in the vicinity and could decide
on the target network for future handover.
Step 4: The NAS layer of the MN initiates a Re-
authentication process to lunch the security
mechanisms in the target network.
Step 5: Through its NAS layer, the currently
serving AAA server (CAAA) forwards the re-
authentication request along with core information
that are used to derive a fresh set of the security
parameters for the new network to the NAS layer of
a Central Authority (CA) in the Core endpoint.
Figure 4: Ring based Security Model.
Step 6: If the target network is located in the core-
endpoint, CA’s NAS layer passes the core
information to the target network to derive the
security materials and achieves the triple A tasks.
SECRYPT 2010 - International Conference on Security and Cryptography
320
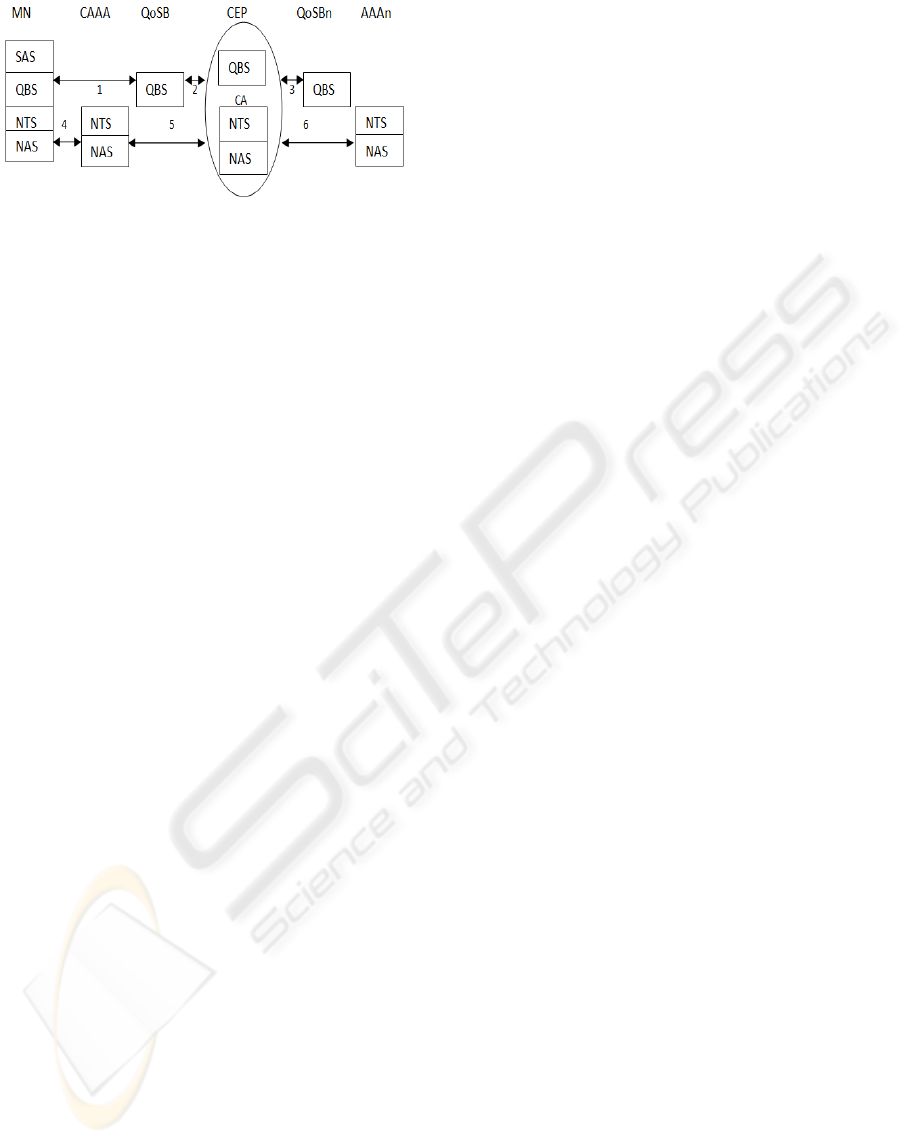
Figure 5: Vertical Handover Security Model.
The MN will check whether it has the same security
parameters the AAA of the target network has
generated using core information. In case of a match
this means that the new network is authentic.
Moreover, we presume a certain trust relations
between the AAA servers, different trust relationship
models might be implemented such as parent-child
model where the top level Authority in the Core-
endpoint issues certificates for all the AAAC servers
working in its zone. Alternatively, current
Authentication and Key Agreement protocols such
as EAP as defined in RFC 5247, might be used to set
up a lower-layer secure association among AAA
servers.
3 CONCLUDING REMARKS
We showed how the new communications
architecture for heterogeneous networking called Y-
Comm can have a multi-layer security framework.
The integration of the various layers into the security
framework as well as the fact that the model itself is
closely integrated with the overall architecture make
it possible to design new security solutions. We
believe that the security models introduced using the
Y-Comm architecture supersede a lot of security
techniques being used today, including firewalls and
Network Address Translation (NAS), leading to a
more secure but also a more efficient network
infrastructure.
REFERENCES
Saltzer, J. H. Reed, D., & Clark, D. D., 1984. End-to-end
arguments in system design. In ACM Transactions in
Computing Systems, p. 277–288.
McNair, J., Zhu, F., 2004. Vertical Handoffs in Fourth-
Generation Multinetwork Environments. In IEEE
Wireless Communications, vol. 11,.
Duda, A., Sreenan, C., 2003. Challenges for Quality of
Service in Next-Generation Mobile Networks. In
Proceedings of IT &T Annual Conference, October
2003.
Mapp, G., Cottingham, D., Shaikh , F., Vidales, P.,
Patanapongpibul, L., Baliosian ,J. & Crowcroft, J.,
2006. An Architectural Framework for Heterogeneous
Networking. In Proceedings of the International
Conference on Wireless Information Networks and
Systems (WINSYS 2006). August 2006, p.5–10.
Mapp, G., Shaikh, F., Crowcroft, J., Cottingham, D.,
Beliosian, J., 2007. Y-Comm: A Global Architecture
for Heterogeneous Networking, (Invited Paper). In the
3rd Annual International Wireless Internet Conference
(WICON 2007). Austin, Texas, USA,
October 22-24, 2007.
Irvine, C., Levin, T., 2000. Quality of Security Service. In
Proceedings of the New Security Paradigms
Workshop, September 2000.
Ballani, H., Chawathe, Y., Ratnasamy, S., Roscoe, T. &
Shenker, S., 2005. Off by Default!. In Proceedings of
the Fourth Workshop on Hot Topics in Networking
(HotNets-II), College Park, MD, USA, November
2005.
Aiash, M., Mapp, G., Lasebae, A. & Phan, R., 2010.
Providing Security in 4G Systems: Unveiling the
Challenges. In The Sixth Advanced International
Conference on Telecommunications, AICT 2010.
Barcelona, Spain, 9-15 May 2010. [Accepted paper].
SECURITY MODELS FOR HETEROGENEOUS NETWORKING
321
