
AN OFFLINE PEER-TO-PEER BROADCASTING SCHEME WITH
ANONYMITY
Shinsaku Kiyomoto, Kazuhide Fukushima
KDDI R & D Laboratories Inc., Japan
Keith M. Martin
Information Security Group, Royal Holloway University of London, U.K.
Keywords:
Peer-to-peer broadcasting, Anonymous broadcasting, Timed release encryption.
Abstract:
Content broadcasting is an effective method of delivering content to a large number of users. Although IP-
based broadcasting services are available on the Internet, their services require a broadcasting server with
huge resources, which makes them unsuitable for personal broadcast applications. An obvious alternative is
to deliver personal broadcasting services over a peer-to-peer network. Several products are now available to
support live broadcasting in such networks. However, live broadcasting in a peer-to-peer network involves a
heavy concentrated communication load and incurs network delays that result in users not necessarily viewing
a live transmission simultaneously. In this paper we consider an alternative type of peer-to-peer broadcasting
scheme, offline broadcasting, which provides a decentralized broadcasting service with anonymity. While
offline broadcasting cannot be used for live broadcast streaming, it can be used to guarantee simultaneous
viewing of predistributed content. We demonstrate that this scheme provides a practical alternative to existing
techniques for broadcasting content that can be created in advance, and present security analysis of the scheme.
1 INTRODUCTION
1.1 Background
Content broadcasting services are used for simulta-
neously distributing information to a great number of
users. A conventional broadcasting service requires
a broadcasting server with huge computational re-
sources and places a heavy burden on the network,
which makes a broadcasting service costly.
We are seeing an increase in the significance of
personal users as multimedia content providers. For
example, Consumer generated media (CGM) (Black-
shaw and Nazzaro, 2004) is a term that is increasingly
used to describe multimedia content that is created by
consumers and delivered over the Internet in relation
to their own experience of products or services. We
have also seen the rise of YouTube (YouTube, LLC,
2005) as a successful content distribution service for
the likes of CGM. Notably, YouTube provides for
anonymous content distribution, which may be one of
the reasons for its popularity since virtual identities
are a widely used in Internet communities. However,
applications such as YouTube tend to adopt a central-
ized approach to content distribution, which does not
suit all application environments.
The increasing importance of CGM raises the in-
teresting question as to whether it is possible for per-
sonal users to advance from the open publication of
multimedia content, which they can do already, to the
provision of their own broadcasting services, which
we term personal broadcasting. From experience of
existing applications such as YouTube, the capabil-
ity to support anonymous broadcasting would seem a
desirable property of any personal broadcasting appli-
cation.
1.2 Peer-to-Peer Broadcasting
Peer-to-peer networks provide efficient decentral-
ized platforms for distributing multimedia content.
Several network architectures have been proposed
for peer-to-peer technology, for example Content-
Addressable Network (CAN) (Ratnasamy et al.,
2001), Freenet (Clarke et al., 2000), Chord (Stoica
et al., 2001), and Tapestry (Zhao et al., 2004). It has
75
Kiyomoto S., Fukushima K. and M. Martin K. (2009).
AN OFFLINE PEER-TO-PEER BROADCASTING SCHEME WITH ANONYMITY.
In Proceedings of the International Conference on Security and Cr yptography, pages 75-82
DOI: 10.5220/0002182100750082
Copyright
c
SciTePress

also been shown that a peer-to-peer network can re-
duce the overall cost to content providers in compar-
ison with a content distribution scheme based on a
centralized server (Gkantsidis et al., 2006).
A number of products to support live broadcast
services in peer-to-peer networks are now available.
One example is PeerCast (PeerCast.org, 2002), which
organizes user nodes into a hierarchical structure in
order to enable efficient forwarding of streamed con-
tent. Several other peer-to-peer live broadcasting
schemes use a similar approach (Liao et al., 2006;
Luac et al., 2007). These schemes successfully use
decentralization to reduce the heavy burden of pro-
viding a broadcasting service.
However, these live broadcasting schemes suffer
from two problems. Firstly, at the time of a livebroad-
cast the network experiences a concentrated com-
munication load as the live content stream is propa-
gated throughout the community of nodes. The net-
work is further stressed if two or more nodes are si-
multaneously broadcasting. Secondly, although these
schemes aim to be efficient, it is unavoidable that
there are delays in delivery of the broadcast content,
with some nodes receiving it before others.
1.3 Offline Broadcasting
In this paper, we propose an alternative approach to
providing broadcasting services in a peer-to-peer net-
work. We refer to it as offline broadcasting since
the content is distributed ahead of its start time, but
users cannot view the content until a designated time.
While offline broadcasting cannot be used for live
streaming, it does have the following properties:
1. nodes all have the capability to simultaneously ac-
cess the content;
2. there is no communication congestion at the des-
ignated broadcast time;
3. broadcasters can create content anonymously.
Our offline broadcasting scheme does not require di-
rect communication between the broadcasting server
and users. By predistributing the content, the heavi-
est burden of the scheme is temporally and spatially
distributed amongst the users.
One way to implement an offline broadcasting
scheme would be to distribute encrypted content in
advance and then make the decryption key available at
the broadcast start time. However, if the broadcaster
forwards this decryption the key at the start time then
similar network delays to those for live broadcasting
schemes will be experienced. Alternatively, if the de-
cryption key is released by a central key server then
the complex issue of managing content-specific keys
at the server end needs to be addressed.
We propose the use of a timed-release encryption
scheme, which only requires the periodic broadcast-
ing of time information. In this way the offline broad-
casting scheme requires no interaction between the
broadcaster and users at the time of viewing. With re-
spect to anonymity, broadcasters can choose whether
or not to link their identity to the content.
1.4 Organization
The rest of the paper is organized as follows. In Sec-
tion 2, we discuss timed-release encryption. In Sec-
tion 3 we define the main components and in Section
4 we describe our offline broadcasting scheme. We
conduct a basic security and efficiency analysis of our
scheme in Section 5 and then conclude.
2 TIMED-RELEASE
ENCRYPTION
Timed-release encryption (TRE) schemes are used
to control the time at which confidential data is
disclosed. TRE schemes are useful for applica-
tions such as electronic voting, sealed-bid auction, e-
lotteries, and online games (Chalkias, 2007). There
are two approaches to realizing a TRE scheme. The
first uses time-lock puzzles (Mao, 2001) (Boneh and
Naor, 2000) (Garay and Jakobsson, 2003) to require
the receiver to perform non-parallelizable computa-
tions in order to recover confidential data. The sec-
ond approach is based on the use of a trusted time
server, which periodically publishes content indepen-
dent “time information”. Blake and Chan proposed
a scalable public key TRE (Blake and Chan, 2005)
scheme (which we will call BCTRE) that uses a time-
stamp server.
We base our offline broadcasting scheme on BC-
TRE, which we now briefly outline. Suppose that G
1
and G
2
are respectively additive and multiplicative
cyclic groups of order q (q is a prime number). Let
the bilinear pairing be a map ˆe : G
1
× G
1
→ G
2
with
the following properties:
1. Bilinearity. The following equations must be sat-
isfied:
ˆe(aP, Q) = ˆe(P, Q)
a
= ˆe(P, aQ),
ˆe(aP, bQ) = ˆe(P, Q)
ab
,
ˆe((a+ b)P, Q) = ˆe(aP, Q) ˆe(bP, Q),
ˆe(P, (a+ b)Q) = ˆe(P, aQ) ˆe(P, bQ),
for all a, b ∈ Z
∗
q
, which are taken from among n
equally spaced points on an elliptic curve.
SECRYPT 2009 - International Conference on Security and Cryptography
76

2. Non-degeneracy. ˆe(P, Q) 6= 1 is satisfied.
3. Computability. There exists an efficient algorithm
for the computation ˆe(P, Q).
We assume that the discrete logarithm (DL) problem
over G
1
, and the computational Diffie-Hellman prob-
lem are hard. From the existence of bilinear pairing in
the underlying group, the decisional Diffie-Hellman
(DDH) problem can be solved. Thus, G
1
is a Gap
Diffie-Hellman group, which is found in supersingu-
lar elliptic curves or hyperelliptic curves over a fi-
nite field. The bilinear pairing is derived from the
Weil or Tate pairing. Furthermore, the Bilinear Diffie-
Hellman (BDH) problem is assumed to be hard. For
more information, see (Boneh and Franklin, 2001).
The BCTRE scheme uses two cryptographic one-
way hash functions: H
1
: {0, 1}
∗
→ G
∗
1
, H
2
: G
2
→
{0, 1}
n
. The scheme consists of the following five
steps.
• Server’s Key Generation. A time server of a
trusted third party randomly picks G as a gener-
ator of G
1
and a private key s ∈ Z
∗
q
. The server
then computes the public key sG and the public
key and G are made publicly available.
• User’s Key Generation. Each user picks a secret
key a
i
∈ Z
∗
q
and computes the corresponding pub-
lic key (a
i
G, a
i
sG).
• Time Information Generation. At a time T ∈
{0, 1}
∗
, the time server publishes a signature
sH
1
(T) for the time T. Note that every user
can verify its validity by checking ˆe(sG, H
1
(T)) =
ˆe(G, sH
1
(T))).
• Encryption. Given a message M and a receiver’s
public key (a
i
G, a
i
sG), a sender randomly picks
r = Z
∗
q
and computes rG and ra
i
sG. The sender
then computes ρ = ˆe(ra
i
sG, H
1
(T)), where T is
the moment in time when the ciphertext should
be decrypted. Finally, the sender computes the
ciphertext CT = (rG, σ = M ⊕ H
2
(ρ)).
• Decryption. Given a ciphertext CT, a re-
ceiver’s private key a
i
and a time datum sH
1
(T)
from the server, the receiver computes ρ
′
=
ˆe(rG, sH
1
(T))
a
i
, and then the receiver recovers M
by computing σ⊕ H
2
(ρ
′
).
The BCTRE scheme is intended for content distribu-
tion to one user. In Section 3.3 we adapt it so that we
can apply it to a broadcasting scheme.
3 COMPONENTS OF PROPOSED
SCHEME
In this section, we discuss the security requirements
and components of our offline broadcasting scheme.
3.1 Entities
Four entities are involved in our offline broadcasting
scheme.
• Broadcast Stations. Broadcast stations broadcast
their content to users according to a time schedule.
The stations upload a program schedule detailing
their broadcast content to a program-listing server
to spread information about their offerings.
• Users. Users receive broadcasting services from
broadcast stations with the assistance of a time
server.
• Time Server. A time server distributes valid time
information to users. The time server is assumed
to be trusted.
• Program Listing Server. A program listing
server manages programs of broadcast content.
Users obtain information on future broadcast
content from the program-listing server. The
program-listing server is assumed to be trusted.
Note that in many of the CGM applications for this
type of scheme the set of broadcast stations and the
set of users will be the same.
3.2 Security Requirements
The main security requirements for an offline broad-
casting scheme are summarized as follows.
• Timed Release Capability. Access to broadcast
content must be infeasible until the designated
time. While users may be able to obtain encrypted
content in advance, they should not be able to
view the content until the intended time, at which
point they should be able to view the content at
the same time.
• No Content Plagiarism. Content must not be
plagiarized before its scheduled viewing time.
This is a particularly important issue for an offline
broadcasting service. The content is distributed
in advance, and an attacker can potentially re-
distribute the encrypted content as their own orig-
inal content. Thus, information about the owner-
ship of the intellectual property must be protected
until the designated time for viewing. Details of
this type of attack will be discussed in Section 5.
AN OFFLINE PEER-TO-PEER BROADCASTING SCHEME WITH ANONYMITY
77
• No Masquerading. Masquerading as a legiti-
mate broadcast station must be impossible. An
attacker may create content while pretending to
be a broadcast station. It must be impossible for
attackers to place the appearance of responsibility
for illegal content on other broadcast stations.
3.3 Timed-Release Broadcast
Encryption Scheme
We now modify the BCTRE scheme to allow it to be
used for broadcast encryption. We refer to the modifi-
cation as Broadcasting-BCTRE (B-BCTRE). The no-
tation is the same as for BCTRE (see Section 2.2).
The scheme is as follows:
• Server’s Key Generation. This step is the same
as for BCTRE.
• Broadcast Station’s Key Generation. Each
broadcast station selects a secret key b
i
∈ Z
∗
q
and
computes a public key b
i
G that is made publicly
available.
• Time Information Generation. At a time
T ∈ {0, 1}
∗
, the time server publishes a signa-
ture sH
0
(T) and sH
1
(T) for the time T. Ev-
ery user can verify its validity by checking
ˆe(sG, H
0
(T)) = ˆe(G, sH
0
(T))) and ˆe(sG, H
1
(T))
= ˆe(G, sH
1
(T))). H
0
is a cryptographic one-way
hash function: H
0
: {0, 1}
∗
→ G
∗
1
.
• Encryption. A broadcast station randomly picks
a content key seed KS = {0, 1}
k
and r = Z
∗
q
, where
k is a security parameter and satisfies k ≤ n. Then
the station computes rG. Next, the station com-
putes ρ = ˆe(rsG, H
0
(T)) ˆe(b
i
sG, H
1
(T)), where T
is the target time for decryption of the cipher-
text. Finally, the station computes the ciphertext
CT = (rG, σ = KS⊕ H
2
(ρ)).
• Decryption. Given the ciphertext CT, the broad-
cast station’s public key b
i
G, and a time datum
sH
0
(T) and sH
1
(T) from the server, the receiver
computes ρ
′
= ˆe(rG, sH
0
(T)) ˆe(b
i
G, sH
1
(T)), and
then recovers KS by computing σ⊕ H
2
(ρ
′
). Note
that only a valid public key of the broadcast sta-
tion can recover a valid KS, therefore, the decryp-
tion process implicitly checks the authenticity of
content distributors.
3.4 Content Encryption
Multimedia content typically involves huge amounts
of data and the software that displays it must de-
crypt the content in real time. Thus, the content itself
should be encrypted using relatively efficient sym-
metric techniques based on either a block cipher or
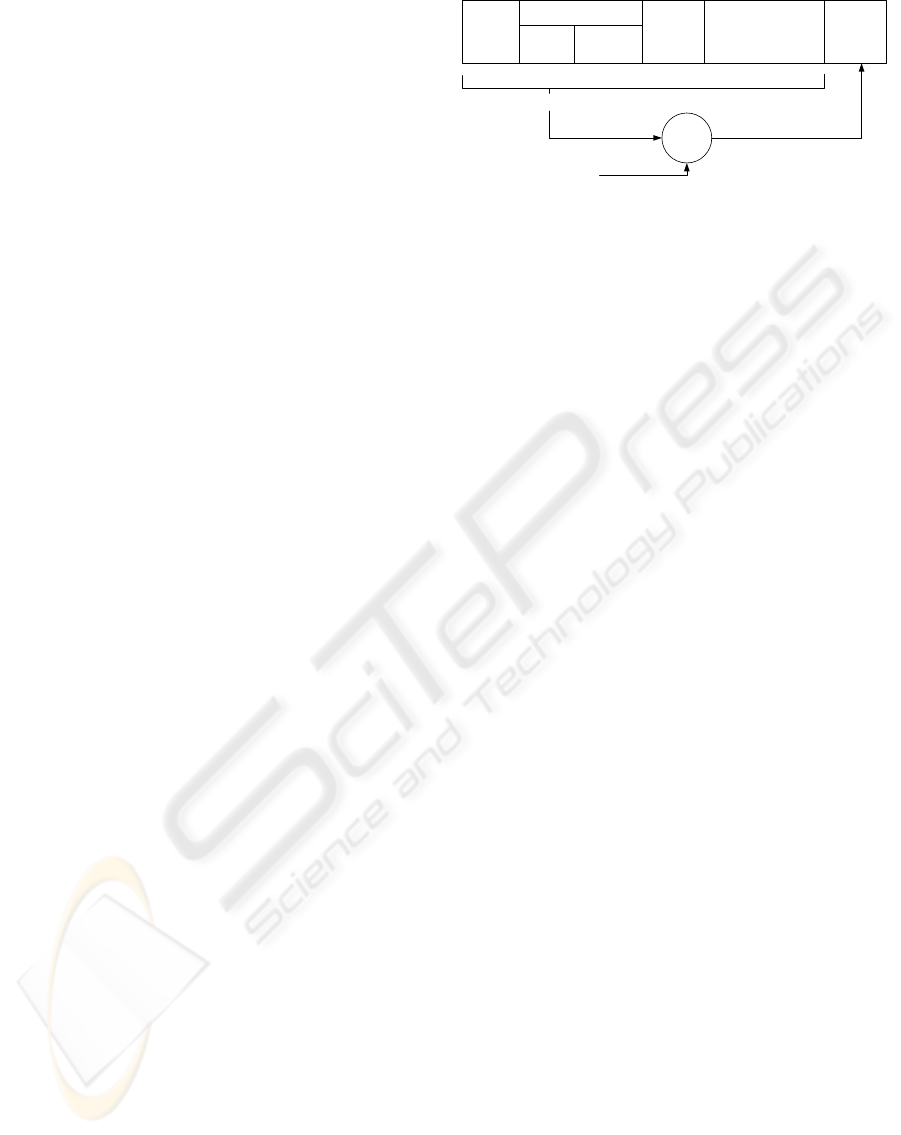
Index Key Encrypted Content Field
Content Body
Sig
Content Info.
Reference
Info.
Public Key
or Link Info.
Broadcasting
Time
Digital
Signature
Private Key of
Broadcasting Station
Figure 1: Data Format of Distributed Content.
stream cipher. The content can be played with de-
crypting the encrypted content. In general, a two-
layered structure is used by distribution services to en-
crypt multimedia content (Open Mobile Alliance Ltd,
2008). First, content is encrypted with a content key
CK using a symmetric key encryption algorithm, and
then CK is wrapped using another key that is unre-
lated to the content key.
We denote the encryption and decryption algo-
rithms for the B-BCTRE scheme by T E and T D
respectively. The B-BCTRE scheme is used for en-
crypting the content key seed KS. Symmetric key en-
cryption and decryption are denoted by S E and S D .
We also define a key derivation function K D F (KS)
that outputs the content key from the seed. The func-
tions are described as follows:
T E : CT ← T E (KS, Pu
t
, Pr
b
, T),
T D : KS ← T D (CT, Pu
b
, TI),
K D F : CK ← K D F (KS),
S E : EMC ← S E (CK, MC),
S D : MC ← S D (CK, EMC),
where MC and EMC are multimedia content and en-
crypted multimedia content respectively. The sym-
bols Pu
b
and Pr
b
denotes a public key b
i
G and pri-
vate key b
i
of the broadcast station. The public key of
the time server sG, designated time T, and time infor-
mation sH
1
(T) from the time server are denoted by
Pu
t
, T, and TI. We assume that the symmetric key
encryption scheme S E , S D , and the key distribution
function K D F are secure.
3.5 Data Format of Distributed Content
The data format of the distributed content is shown
in Figure 1. Content data consists of the body of the
content and its digital signature. The body of content
consists of four data blocks as follows:
•
Index Key:
This information is an index key for
searching for the content on a peer-to-peer system.
•
Content Info.:
The content information field in-
cludes reference information, such as index keys
for the previous and following content and the
SECRYPT 2009 - International Conference on Security and Cryptography
78

broadcasting time (start time for the content and
its expected end time). The designated time of
the content is specified in the content information
field as the start time of the content. If the content
is a part of a program that is divided into sections,
the user obtains the next section by referring to the
content information field before the start time.
•
Public Key or Link Info.:
This data is a public
key certificate of the broadcasting station or its
link information. The user obtains the public key
from the content information field or a server that
stores the public key certificate of the broadcast
station, using the link information. The user first
verifies the public key, using its certificate, and
then uses the public key for decryption at the des-
ignated time.
•
Encrypted Content Field:
This data consists of
all the encrypted data, namely the encrypted con-
tent key seed using B-BCTRE and the encrypted
content using the symmetric key encryption algo-
rithm.
In order to detect modification of any information that
must be opened before the designated time, such as
the index key and content information, the broad-
cast station may compute the digital signature S =
b
i
H
1
(CB) using the appropriate private key b
i
, where
CB is a bit string of the content body. This signature
can be verified by using the public key of the broad-
cast station b
i
G as ˆe(G, S) = ˆe(b
i
G, H
1
(CB)). The
signature must be computed using the same private
key of the broadcast station as the one used for timed-
release encryption of the content.
4 OFFLINE BROADCASTING
SCHEME
We now present our offline broadcasting scheme. We
will also explain how to realize an anonymous broad-
casting service.
4.1 System Architecture
Figure 2 provides an overview of the system architec-
ture to support our offline broadcasting scheme. We
assume that the scheme is constructed on an exist-
ing peer-to-peer network architecture such as CAN,
Chord, Freenet or Tapestry (see references). Such
peer-to-peer platforms normally provide the follow-
ing functionality:
• Discovery of Content: The peer-to-peer system
provides a search function for each node. This
function outputs addresses of nodes where content
is stored. An index key for the desired content is
used to search for the content. A scalable search
mechanism is designed into existing peer-to-peer
systems.
• Storage for Content: Each node provides storage
for content. This function also provides a regis-
tration mechanism for content items in order to
provide information to the peer-to-peer system.
Nodes register the content in their storage with the
peer-to-peer system.
• Content Distribution: This provides a protocol for
distributing content between nodes. A node sends
content that is requested by another node. Con-
tent is sometimes distributed using indirect com-
munication between nodes, in which case content
is sent to a requesting node via one or more in-
tervening nodes. Nodes along the communication
chain store the requested content automatically, if
their storage has sufficient space.
In addition to the above general functionality, in our
system each node has additional security functionality
as follows:
• Content Management: Stored content can be ver-
ified, ensuring that the signature is valid. This
functionality also checks content information and
will remove any content whose designated time
has expired.
• Decryption: This function receives time informa-
tion and decrypts content on its scheduled time for
viewing. This function is assumed to decrypt the
content to protected memory in order to avoid the
potential for making an illegal copy of the content.
Broadcast stations join the peer-to-peer system as
nodes and can both create and encrypt content. The
encryption function uses the B-BCTRE scheme de-
scribed in Section 3.3. Furthermore, for the offline
broadcasting service, we add two servers to the peer-
to-peer system as follows. These servers are common
services for all broadcast stations and users.
• Time Server: The time server generates time in-
formation periodically, and sends time data to
other nodes by broadcasting/multicasting.
• Program Listing Server: The program listing
server publishes a program list of broadcast ser-
vices. Broadcast stations register information
about their content, such as a summary, index key,
and the designated viewing time of their content
items.
AN OFFLINE PEER-TO-PEER BROADCASTING SCHEME WITH ANONYMITY
79
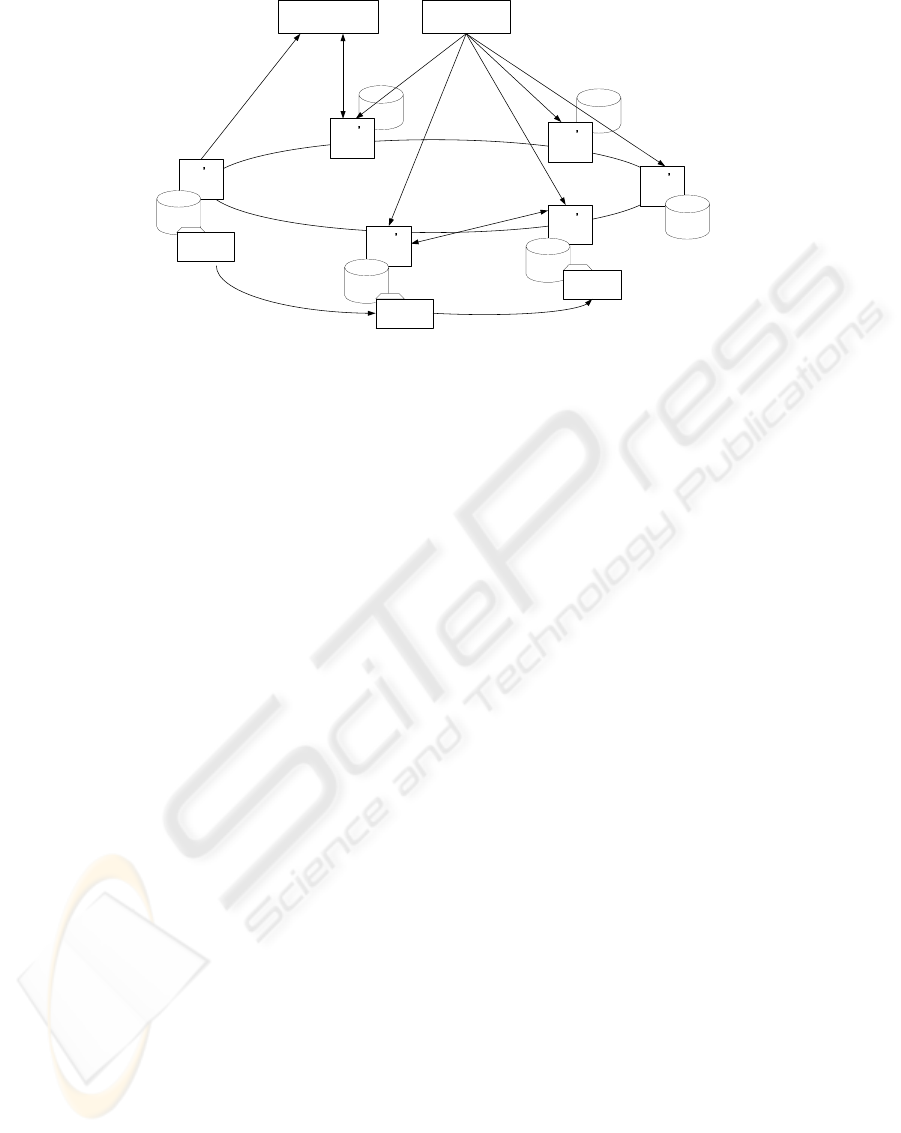
User s
Node
BS s
Node
Storage
Storage
User s
Node
Storage
Storage
User s
Node
Storage
User s
Node
User s
Node
Storage
Time
Server
Peer-to-Peer Network
Broadcast Time Info.
BS: Broadcast Station
Program Listing
Server
Content
(encrypted)
Upload Info. of
Contents
Refer Info.
of Contents
Search Contents
Content
(encrypted)
Content
(encrypted)
Distribute Contents
Distribute Contents
Figure 2: System Overview.
4.2 Procedure for Content Broadcasting
The procedure for content broadcasting in our offline
broadcasting scheme is described as follows:
1. The broadcast station encrypts its content and reg-
isters it on the peer-to-peer network. The broad-
cast station uploads information about the content
to the program listing server, which could include
a summary of the content, an index key for the
content, the designated time, and a public key cer-
tificate for the broadcast station.
2. A user checks a program list on the program list-
ing server and searches for interesting content,
then downloads that content from the nearest node
that has it. The content is distributed to users by
such actions.
3. When the user receives the content, the user ver-
ifies it as follows. If the content includes a digi-
tal signature from the broadcast station, the user
obtains the public key of the station and verifies
the signature. If the signature is invalid, the user
destroys the content. Otherwise, the user stores
the content in his own storage for the peer-to-peer
system.
4. A time server periodically broadcasts content-
independent time information. When the user re-
ceives a time datum corresponding to the desig-
nated time of the content, he can decrypt and view
the content. If the content item indicates that an-
other follows, the user searches for the next con-
tent item and downloads it while watching the cur-
rent content. The user views the subsequent con-
tent item after finishing the current item, by de-
crypting the subsequent item with the next time
datum.
5. A content item whose designated time has passed
is removed from storage. In this way, content
that the user has finished viewing is automatically
deleted from storage.
4.3 Anonymous Broadcasting Service
Our scheme can be extended to an anonymous broad-
casting service by making the broadcast station’s pub-
lic key anonymous. When the broadcast station wants
an anonymous broadcasting service, the station gen-
erates a public-private key pair for each item of con-
tent and stores the public key in the content infor-
mation field. If the service requires that only autho-
rized broadcast stations can distribute their content to
users, a certificate authority may provide a certificate
of the public key that does not include the identifier of
the station, but does include membership information.
Users verify the public key using the membership cer-
tificate.
In a peer-to-peer network, it cannot be determined
whether content is created by a node or copied from
other nodes. Furthermore, users can verify the sig-
nature and decrypt the content using the public key
and time information, however a user cannot deter-
mine the owner of the public key. Thus, the scheme
can be used to provides an anonymous broadcasting
service.
Note that a broadcast station can always provethat
the station is a valid creator of the content because
the broadcast station has the private key related to the
public key. If the content from the station is plagia-
rized, the broadcast station can provide evidence con-
firming its role as creator by demonstrating the use of
the corresponding private key to a trusted third party.
Our offline broadcasting scheme thus achieves
SECRYPT 2009 - International Conference on Security and Cryptography
80

anonymity of broadcast stations, since it is not
known who broadcast a particular content. If re-
quired, a broadcaster can repeatedly associate the
same pseudonym with broadcast content in order to
build up a reputation but without revealing their iden-
tity, just as in the case of YouTube. In addition, it
is worth noting that users also receive a degree of
anonymity since a node cannot know whether another
node decrypts and views specified content, even if the
node has the content.
5 ANALYSIS
5.1 Security Analysis
We now comment on the security of the proposed of-
fline broadcasting scheme. We first examine the se-
curity of B-BCTRE, then the three main security re-
quirements of Section 3.2, and finally consider some
other security issues.
Security of B-BCTRE. Since B-BCTRE is only a
slight modification of BCTRE, the security proof of
B-BCTRE is very similar to that of BCTRE. A sketch
of the security proof is as follows. As described in
(Blake and Chan, 2005) for BCTRE, we can rewrite
any sH
0
(T
j
) = w
j
sG for some unknown w
i
. The prob-
lem of an adversary decrypting KS without sH
0
(T
j
)
becomes that of finding ˆe(G, G)
rsw
j
from sG, w
j
G,
rG, which is equivalent to the bilinear Diffie-Hellman
problem. This problem is the same as the original
BCTRE scheme. Hence, as long as the bilinear Diffie-
Hellman is difficult, the adversary cannot decrypt KS
before its designated time unless they collude with the
time server. Secondly, we consider the problem of an
adversary generating ciphertext of the broadcast sta-
tion i without the private key b
i
. This problem is also
equivalent to the bilinear Diffie-Hellman problem of
computing ˆe(G, G)
b
i
sw
l
from sG, w
l
G, and b
i
G, where
sH
1
(T
l
) = w
l
sG. Thus, the adversary cannot alter a ci-
phertext of the broadcast station under the assumption
that the bilinear Diffie-Hellman problem is difficult.
Timed Release Capability. No user can decrypt a
content item without a time datum sH
1
(T), because it
is impossible to obtain a private key s within the limits
of feasible computational complexity.
No Content Plagiarism. A potential scenario for
content plagiarism is as follows. An attacker obtains
an encrypted content item created by a valid broad-
cast station. Next, the attacker separates the own-
ership information from the encrypted content and
the B-BCTRE ciphertext, and then creates an altered
content item using the encrypted content and the B-
BCTRE ciphertext. Finally, the attacker distributes
the altered content as their created content, before the
designated time for the original content. If we used
the basic BCTRE scheme without modification, this
attack would be successful. However, our scheme re-
quires both the public keys for the content creator and
for the time datum specifying when the content is to
be decrypted. The attacker cannot decrypt anything
until the designated time for the content, and cannot
create altered content that is decryptable using the at-
tacker’s public key. Therefore, this security require-
ment is met. After the designated time, we should
protect the content not by using cryptographic tech-
niques, but by using techniques that will be discussed
later.
No Masquerading. To masquerade as a valid broad-
cast station, a private key b
i
is needed to compute a
valid B-BCTRE ciphertext and signature. From the
assumptions of the DL and DH problems, it is infea-
sible to obtain b
i
without unrealistic computational
cost. Thus, the proposed scheme is secure against a
masquerading attack.
Denial of Service. An attacker may try to obstruct the
offline broadcasting service by altering content infor-
mation such as reference information and start time,
and then distributing altered content. However, this
attack is infeasible because any modification of the in-
formation can be detected by verifying the signature
on the content body. Content with an invalidsignature
will be removed from the peer-to-peer system. An-
other possible avenue for a denial of service attempt is
for an attacker to destroy content items stored on their
own node. This attack is also not effective because
users can obtain the content items from other nodes.
Also, an attacker may try to generate a huge volume
of dummy content items and distribute them in order
to saturate the storage capacity of other nodes. This
is a general issue in peer-to-peer content distribution
systems, however each node can check and remove
non-valid content from its own storage, and it would
be infeasible to saturate the storage of all nodes.
Content Protection on a Peer. After decryption of
a content item, an attacker has full access to the con-
tent. The attacker may copy this illegally or use it
as their own content. This problem is a general is-
sue for digital rights management systems for mul-
timedia content. A cryptographic technique cannot
protect against such actions. However, commercial
DRM services solve this problem using a number of
techniques. If content decryption is executed in mem-
ory that the attacker cannot access then the content
is securely protected. Therefore, we should prevent
access to plaintext content by an attacker. Further-
more, we must ensure that content whose designated
time is past is automatically removed from the peer-
AN OFFLINE PEER-TO-PEER BROADCASTING SCHEME WITH ANONYMITY
81

to-peer system in a way that no attacker can circum-
vent. Hence, secure implementation of both the con-
tent management and decryption function is very im-
portant.
5.2 Efficiency Analysis
In existing peer-to-peer live broadcasting schemes,
nodes receive and transfer streamed content in real
time, thus experiencing time delays as the content is
relayed. However, when using the B-BCTRE scheme,
all users can simultaneously access content when the
time server releases the relevant time datum, which is
content-indpenendent. Further, all communication ef-
fort takes place before the start time. Hence, a broad-
band network is not mandatory and the communica-
tion load is spread over time. In addition, the scheme
provides secure content distribution, unlike many of
the existing peer-to-peer broadcast schemes which re-
quire content security to be bolted on at additional
cost.
In comparison to live broadcast, users do have to
store content ahead of time. At the designated start
time, the only cost is that user nodes must decrypt the
content. The decryption of the content key consists
of two pairing computations, one multiplication, one
hash operation, and one exclusive-or operation. The
pairing computation on a 1.66 GHz Core2 perform
is expected top take around 14.5 msec (Hankerson
et al., 2008) and the transaction time of other oper-
ations is negligible. The bulk content decryption uses
efficientstandard symmetric techniques, which makes
the scheme applicable for PC-based nodes.
6 CONCLUSIONS
In this paper, we have described the design of an of-
fline broadcasting scheme for peer-to-peer networks
that can provide anonymity for the broadcaster. In
this scheme, personal users can broadcast multime-
dia content by delivering it to peers ahead of its start
time. Peers can then view the content without ac-
cessing the network, thus distributing the burden of
service to peer nodes. We have demonstrated that
this scheme provides a practical alternative to exist-
ing techniques for broadcasting content that can be
created in advance.
REFERENCES
Blackshaw, P. and Nazzaro, M. (2004). Consumer-
generated media (CGM). In Intelliseek White Paper.
Blake, I. F. and Chan, A. C.-F. (2005). Scalable, server-
passive, user-anonymous timed release cryptography.
In Proc. of IEEE International conference on Dis-
tributed Computing Systems, pages 504–513. IEEE.
Boneh, D. and Franklin, M. (2001). Identity-based encryp-
tion from the weil pairing. In Proc. of CRYPTO 2001,
LNCS, volume 2139, pages 213–229. Springer.
Boneh, D. and Naor, M. (2000). Timed commitments and
applications. In Proc. of CRYPTO 2000, LNCS, vol-
ume 1880, pages 213–229. Springer.
Chalkias, K. (2007). Timed-release encryption (TRE). In
short presentation in ECRYPT PhD Summer School,
Emerging Topics in Cryptographic Design and Crypt-
analysis.
Clarke, I., Sandberg, O., Wiley, B., and Hong, T. (2000).
Freenet: A distributed anonymous information strage
and retrieval system. In Proc. of ICSI Workshop on
Design Issues in Anonymity and Unobservability.
Garay, J. and Jakobsson, M. (2003). Timed release of stan-
dard digital signatures. In Proc. of FC 2002, LNCS,
volume 2357, pages 168–182. Springer.
Gkantsidis, C., Miller, J., and Rodriguez, P. (2006).
Anatomy of a P2P content distribution system with
network coding. In Proc. of 5th International Work-
shop on Peer-to-Peer Systems (IPTPS 2006).
Hankerson, D., Menezes, A., and Scott, M. (2008).
Software implementation of pairings. In
http://www.math.uwaterloo.ca/˜ajmeneze/publications/
pairings software.pdf.
Liao, X., Jin, H., Liu, Y., Ni, L. M., and Deng, D. (2006).
Anysee: peer-to-peer live streaming. In Proc. of IN-
FOCOM 2006, pages 1–10.
Luac, M.-T., Nienac, H., Wub, J.-C., Pengac, K.-J., Huan-
gade, P., Yaoac, J. J., Laif, C.-C., and Chenacd, H. H.
(2007). A scalable peer-to-peer IPTV system. In Proc.
of CCNC 2007, pages 313–317.
Mao, W. (2001). Timed-release cryptography. In Proc.
of SAC 2001, LNCS, volume 2259, pages 342–357.
Springer.
Open Mobile Alliance Ltd (2008). Oma digital rights man-
agement v2.1.
PeerCast.org (2002). Peercast P2P broadcasting. In
http://www.peercast.org/.
Ratnasamy, S., Francis, P., Handley, M., Karp, R., and
Shenker, S. (2001). A scalable content-addressable
network. In Proc. of SIGCOMM’01, pages 161–172.
ACM.
Stoica, I., Morris, R., Karger, D., Kaashoek, M. F., and Bal-
akrishnan, H. (2001). Chord: A scalable peer-to-peer
lookup services for internet applications. In Proc. of
SIGCOMM’01, pages 149–160. ACM.
YouTube, LLC (2005). YouTube - broadcast yourself,
http://www.youtube.com/.
Zhao, B. Y., Huang, L., Stribling, J., and S. C. Rhea, A. D. J.
(2004). Tapestry: A resilient global-scale overlay for
service deployment. In IEEE Journal on Selected Ar-
eas in Communications, volume 22, No.1, pages 41–
53. IEEE.
SECRYPT 2009 - International Conference on Security and Cryptography
82
