
Agent/Space-based Computing and RF Memory Tag
Interaction
Joni Jantunen, Ian Oliver, Sergey Boldyrev and Jukka Honkola
Nokia Research, It
¨
amerenkatu 11-13, 00180 Helsinki, Finland
Abstract. As devices become more ubiquitous and information more pervasive
technologies such as Semantic Web and Space-Based computing come to the fore
as a platform for user-interaction with their environment. Integrating technologies
such as advanced RF memory Tag with mobile devices and combining this with
computation platforms such as those supporting Semantic Web principles pro-
vides for the user innovative and novel applications.
1 Introduction
The integration of mobile devices, RF memory tags and semantic web style information
sharing and management will open new opportunities for the ad hoc gathering, sharing
of information and for more interactive applications built on top of these concepts.
RF memory tag systems will have the ability to store large quantities of informa-
tion coupled with high-bandwidth radio connections and even contain local processing
capabilities. Mobile devices, such as mobile telephones, have access to ubiquitous con-
nectivity solutions, eg: WLAN, GSM, UMTS networks, as well as sophisticated media
and processing capabilities as well as many local sensors such as GPS etc.
Semantic Web technologies provide canonical information representation formats,
in particular XML for the representation, RDF for the expression of semi-structured,
linked and linkable information and languages such as OWL for the specification of
those structures. This allows much easier integration and interoperability between ap-
plications, agents and devices through standardising many features and providing a ba-
sis for reasoning technologies leading to, at least, weak-AI capabilities.
Combining these technologies together provides a platform for highly interactive,
viral information sharing applications that can be applied in many situations: such a
platform has been implemented as in [10]. For example: mass memory tags are used as a
distribution point of information in a certain locations such as office or shopping center
information points, news stands, tourist attractions etc; even individual physical items
can be tagged - an application particular relevant in the medial sector. Applications of a
system would provide enahancements to existing service-oriented technologies.
In this paper we describe the technologies and an implementation which leads to
framework that supports such applications and interactions. Firstly we provide descrip-
tions of the technologies, then an overview of the types of applications with examples,
then a discussion on a specific interaction case which highlights particular interesting
areas of the RFID-Device-Space interaction and finally a discussion of the future direc-
tion and issues of this technology.
Jantunen J., Oliver I., Boldyrev S. and Honkola J. (2009).
Agent/Space-based Computing and RF Memory Tag Interaction.
In Proceedings of the 3rd International Workshop on RFID Technology - Concepts, Applications, Challenges , pages 27-38
DOI: 10.5220/0002172900270038
Copyright
c
SciTePress

2 Background
We focus on the integration of three major technologies: the Semantic Web, RF memory
tags and mobile devices. Within these categories we specialise on the notion of ‘Smart
Spaces’, the distribution and integration of information and a particular mass-memory,
high-bandwidth form of RF memory Tag.
2.1 Semantic Web and ‘Smart Spaces’
The Semantic Web [13] is a vision for the improvement of personal computing through
the exposition and sharing of information based upon common representation formats,
ontologies and semantics. The idea is that information would become globally ubiqui-
tous and interoperable.
However much information is not ubiquitous in the global sense; it is personalised,
hidden, private and is interpreted locally - this information tends to be the personal,
highly dynamic information that one stores about oneself: contact lists, friends, media
files, ‘my’ current context, ‘my’ family, ‘my’ home etc and the interweaving and link-
ing between these entities through ad hoc personal structures.
To address this issue we have implemented a system based around larger, more user
or personal focussed structured which we term ‘Smart Spaces’ [14]. Within a ‘Smart
Space’ (or just space) a user can encapsulate all of their information and interact with
that information according to their personal semantics and needs.
Spaces have the ability to be distributed across the user’s devices (mobile phone,
media center, personal computer etc) as well as more centralised providers. Synchroni-
sation between these distributed, individual repositories of information is asymmetric to
address device and network capabilities as well as the user’s needs in terms of security
etc.
Interaction with spaces is nominally by ‘agents’ which encapsulate fine grained
functionality which themselves may be distributed across any number of devices that
have access to the user’s space. Spaces themselves can interact through merging and
projection enabling larger spaces to be constructed either on permanent or temporary
basis.
Further interaction between users is enabled through one user granting access to
their space (or spaces) to another user’s agents or even by directly sharing the contents
of their spaces through the asymmetric distribution mechanisms.
A space can transcend over many of the user’s devices leading to the distribution of
information and queries upon that information. For any agent accessing this information
the physical location of it and the information is irrelevant: an agent sees the ‘totality’
of all information in that space. This requires sophisticated distribution algorithms that
actually preserve a degree of assymetry of information depending upon the stability,
connectivity and other properties of a particular information repository.
2.2 From Rfid to Rf Memory Tags
Radio frequency identification (RFID) technologies have been used for decades in ex-
tensive variety of applications [1]. In the simplest RFID applications the tags embedded
28

into objects only provided 1-bit presence information when exposed to the electromag-
netic field transmitted by a reader. Identification of tags with individual ID codes started
from active tags and read only memories and it has become commodity also for passive
tags. Recently, especially the mainstream development of passive RFID technologies
has been steered by applications such as logistics [2], and mobile payment [3]. In these
applications the tags may include also some amount of non-volatile memory. Thus, a
bi-directional communication link between reader and tags is required to enable also
writing of data to tags instead of read-only access. Recently, respective reader capabil-
ities have been also integrated into mobile phones [4]. That provides a possibility to
use RFID tags as part of Smart Space applications by using mobile phone readers as a
gateway.
One development branch of RFID technologies is focusing on applications where
passive RF memory tags will contain increasingly large non-volatile memory capacity
(in scale of mega- to gigabytes) [5]. Such tags would enable storage of digital content
exactly to the point where it is used e.g. into objects and physical locations. This ap-
proach is totally opposite to the network databases traditionally used in RFID systems
where tags may store only a link to the databases. The visions behind this research are
based on the foreseen development trends especially on the field of non-volatile mem-
ory technologies according to which the power consumption, physical size and price of
(non-volatile) memories are continuously decreasing. TSuch his enables development
of passive RF memory tags which can be accessed wirelessly, for example, with mobile
phones and which can be used as ubiquitous storage capacity in Smart Space applica-
tions.
In RFID systems the physical interaction is usually based on back-scattering of
narrow-band RF signals [7]. The reader device provides a continuous wave signal which
is used by the tag to extract supply voltage.
The communication from the tag to reader is possible thanks to modulation of back-
scattered signal from the tag, whereas the communication from reader to tag can be
done for example with simple amplitude or phase modulation methods respecting the
power extraction needs in the tag. Small memory capacity can be implemented with
EEPROM and the whole functionality is usually controlled by a simple finite state-
machine (FSM). However, when the storage capacity of tags increases significantly
back-scattering method based on a single frequency band may be insufficient to achieve
data-rates high enough. According to current regulations wide enough frequency bands
are not available on low frequencies and the efficiency of wireless power transfer de-
creases on high RF frequencies. Thus, either data-rate or communication range is some-
what limited. Therefore dual-band systems have been proposed for data centric Ambient
Intelligence (AmI) applications, such as, the ones used in Smart Space context [6]. An
exemplary (complete) block diagram of an RF memory tag is presented in Figure 1.
In such a system one frequency band is dedicated for wireless power transfer and one
wider band for high data-rate communication.
Section 3 categorizes groups of interactions between RF memory tags and Smart
Spaces. Depending on the category the required computational power of tag may range
from mere memory access (a simple FSM is enough) to hosting of an agent or a space
(requiring MCU or even CPU). In the two ‘classic’ ways it is sufficient that the tag
29
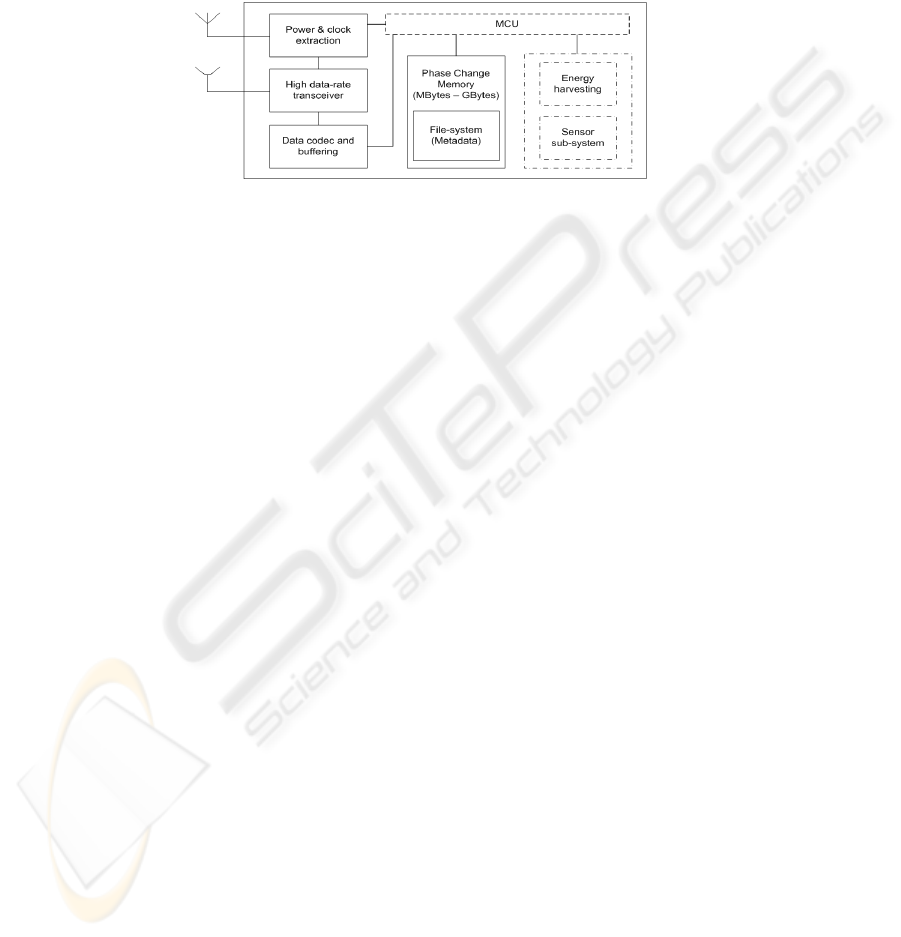
is capable of transferring the data defined by the reader with the highest possible effi-
ciency to achieve user-friendly interaction. The reader device is responsible of defining
which data is read and/or written, and basically in the tag there is no need to process
the content itself. Even the file-system can be maintained in the reader side if it is first
copied from tag to reader in the beginning of interaction and then updated version is
written to tag after the payload data in the tag has been modified.
Fig. 1. Block Diagram of RF memory Tag.
In more sophisticated cases where tags are capable of hosting an agent or running a
space it may be necessary to have sufficient processing capabilities in the tag itself. If
fully active tags are excluded from the study, to achieve easy and low cost maintenance,
the remaining alternatives are fully passive tags and semi-passive tags. In the passive
solution the data is processed fast in the tag during the reader-tag interaction. In the
semi-passive solution the data is processed over a long period of time (as a background
process) by using a dedicated power source e.g. the power harvested from the environ-
ment and only the high data-rate communication requires wireless powering provided
by the reader. In semi-passive case the tag may also function as a data-logger by slowly
collecting a huge amount of samples from a low-power sensor over a long measure-
ment period. However, these applications require extremely low power consumption
what comes to the memory accesses, data processor and sensors but also required data-
rate is extremely slow.
Altogether, the ongoing development on many technological fields will in the future
enable utilization of RF memory tag systems in Smart Spaces. Actually, Smart Space
applications may become one of the main drivers for the technological development of
aforementioned RF memory tag systems.
2.3 Distribution
The scope of distribution and corresponding infrastructures in case of RF memory tag
systems can be analysed in terms of two areas:
– physical environment, e.g. associating of the RF memory tag with direct or indirect
functionality provided by the physical environment, and
– ubiquitous device architecture, e.g. impact to the internals of a particular mobile
device
Considering further, the following can be seen:
– RF memory tag is dumb memory block and has just mechanisms for bidirectional
wireless operations (read/write)
30

– RF memory tag has enough computational power on board, but still external power
is needed, or it can be provided on a volatile basis
Therefore, the range of potential application can be variate from simple “just-in-place”
and “just-in-time” file storages coming to distributed ad hoc storage systems [9] and
going beyond asynchronous computation engines. Projecting such features to the Smart
Spaces architecture RF memory tag system enables use cases when information re-
lated to the particular physical environment can be delivered in-place on-demand or
even by estimation, in a very power and computation efficient manner. By saying “de-
livered” the whole process of extraction, recovery, storing and computing should be
understood. Since using RF memory tag system it is feasible to produce a distributed
snapshot of Smart Space which is tied with the particular physical environment by stor-
ing the run-time environment and corresponding contexts with data/information within
the RF memory tags, it also becomes possible to revoke the system once it would be
demanded by any user. In other words the distributed process of booting, suspending
and resuming of the Smart Space now becomes more flexible, reliable and less physical
context dependant.
Smart Space application infrastructure benefits from RF memory tag system as well.
Since RF memory tags infrastructure provides distributed grained approach for execu-
tion context and information handling, Smart Space application can be constructed by
traversing the RF memory tags and retrieving demanded parts of execution context and
corresponding information.
In terms of ubiquitous device architecture, as it is presented by Figure 1, RF mem-
ory tag system can enable computationally constraint device with memory extension,
distributed memory architecture, or, rich context data analysis and corresponding infor-
mation generation, which then can be uploaded to RF memory tag system.
The problem of memory management (both, execution and mass memory) in dis-
tributed environment, when substantial amount of the devices are using RF memory tag
system technology, converges to the efficient and sustained context execution which is
essential part of whole computing environment, such as Smart Space. Especially be-
cause of high dynamics and constrains the amount of memory on board the mobile
devices in Smart Space.
The approach of efficient and sustained distributed memory utilization by means
of RF memory tag illustrates the solution of such problem. Consider the computing
environment where memory is integrated with RF memory tag based architecture, and
several distributed memory modules are dispersed around the Smart Space(s). Therefore
they are considered as one stackable memory unit by means of corresponding combi-
nation of memory blocks of the environment.
Putting environment where memory is integrated with RF based memory tag ar-
chitecture and several distributed memory modules are dispersed around the Smart
Space(s). From the Smart Space perspectives and corresponding functionality is pro-
vided by distributed RF memort tag based infrastructure, at least following cases de-
scribed in section 3 can be seen.
31

3 Interaction with Tags
In this section we describe the various modes by which spaces and agents interact with
the RF Memory tags. We define four categories:
– Agents read from Tag
– Agents write to Tag
– Agents on Tag
– Space on Tag
The first two categories are the ‘classic’ ways of passively interacting with a tag and
constitute simple information retrieval and sharing. The third and fourth cases involve
much more ‘active’ interaction based requiring specific features of the agent/space ar-
chitecture. We explain these in the following sections with an addition discussion of the
actual physical interaction between devices and the RF memory tags.
3.1 User Interaction
As mentioned in the previous section, in the context of Smart Spaces many new re-
quirements for the future enhanced RFID-like technologies are set. In Smart Space
environment also the user interaction is in a critical role [6] since the fast data connec-
tion is enabled only if user voluntarily accesses RF memory tags. Therefore the system
must be fast, flexible and reliable in addition to many other requirements. The need of
bi-directional high speed data transfer is obvious to achieve convenient user experience
when the storage capacity of tags increases. Flexibility can be understood as a require-
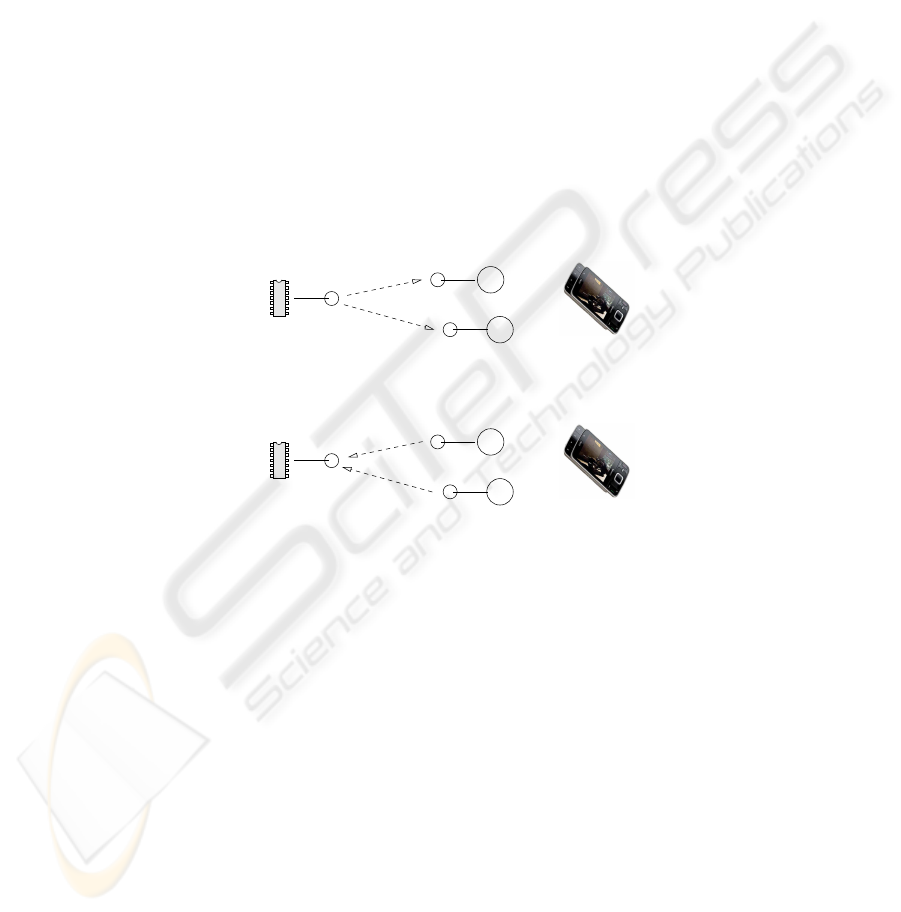
ment for practical communication range. Typical physical interaction is shown in figure
2.
Fig. 2. Physical Interaction of Device and RF memory Tag.
From user’s perspective it is needed especially to allow intuitive and convenient control
through user interface of a mobile reader. Figure 3 presents a situation where mobile
phone is used to interact with a tag which is part of a Smart Space. As can be expected,
the communication range must be long enough to avoid need for accurate pointing of
reader to tag in varying usage conditions. The communication link should also allow
movement of the reader while the user makes selections through the user interface.
32
Reliability of the user interaction can be understood as the quality of data transfers i.e.
low probability of errors on different levels but also as security and privacy aspects since
obviously users cannot tolerate such infringements if the content stored to RF memory
tags is private.
3.2 Agent Interactions
The “simple” read case is useful for applications where the tags provide relatively static
local information, for example, maps, positioning information or even marketing in-
formation such as might be found in a shopping mall style scenario. One existing ap-
plication is that found in museum environments [11, 12] and this is currently being
investigated as an initial deployment of the technology described here.
The “simple” write allows the user to write to the tag. This enables sharing of user’s
information through copying information from the user’s space to the RF memory tag.
This case would be almost invariably used in conjunction with the read case. Typical
applications here might be viral sharing of media or other information, for example,
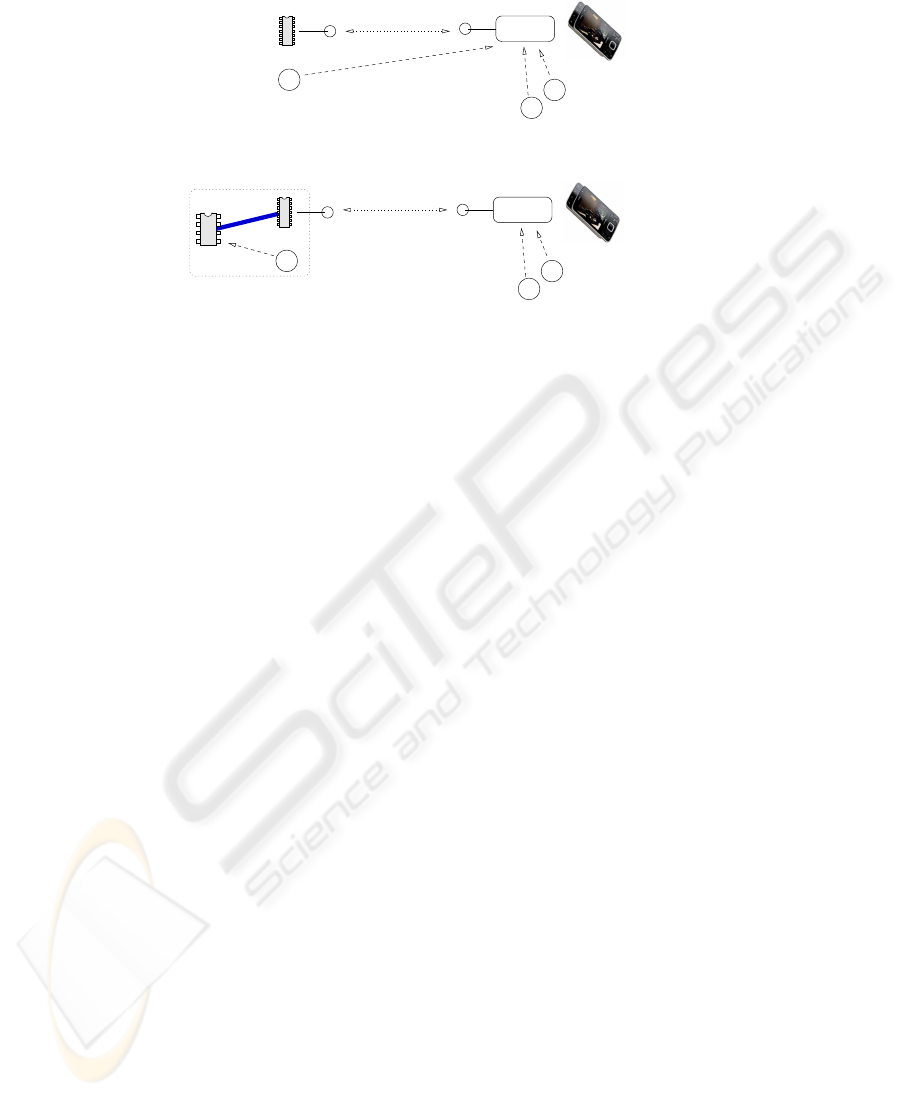
highly localized blogging and messaging. These classic cases are shown in figure 3.
A
A
RF Memory Tag
Information flow −−−>
A
A
RF Memory Tag
<−−− Information flow
Fig. 3. Classic Interaction.
The third case shown in figure 4 requires the tag to have some computational capabili-
ties. When the device with the reader is presented to the tag, it activates agents on the tag
itself which then either request to join the user’s space or are invited to the user’s space
for the duration of the time while the reader is in contact with the RF memory tag. The
agents on the tag may provide additional reasoning or other data gathering/processing
operations as well as supporting the classic read and write use cases described earlier.
The agents can access a Smart Space with five basic operations:
– Insert: Insert information into the Smart Space.
– Remove: Remove information from the Smart Space.
– Update: Update the information in the Smart Space. This is effectively an atomic
remove and insert combination.
– Query: Query for information in a Smart Space.
– Subscribe: Set up a persistent query in a smart space. A change in the query results
is communicated to the subscribing agent.
33
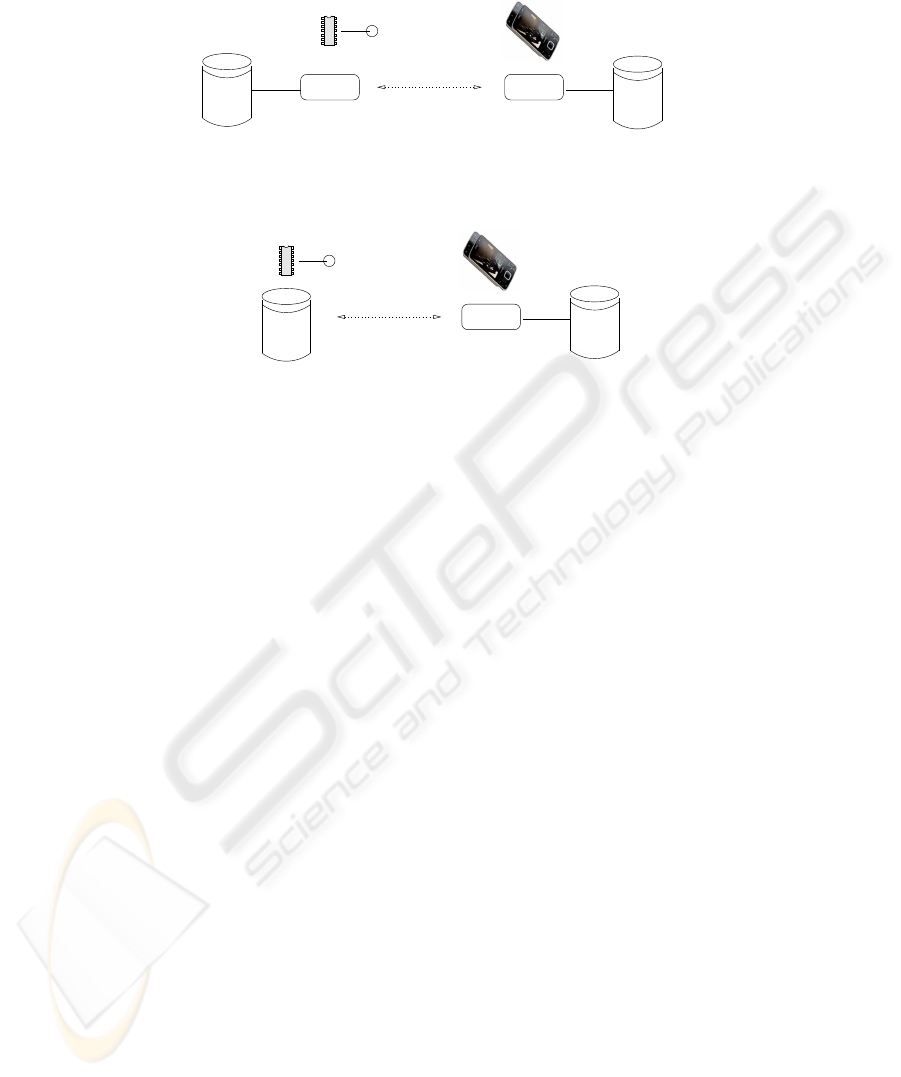
SIB
A
A
A
RF Memory Tag
Agents running "locally"
Agents copied to run "locally"
SIB
A
A
A
Agents running "locally"
Agents run at tag
<−− Information flow −−>
<−− Information flow −−>
RF Memory Tag
(AmI)
Fig. 4. Agent Interaction.
There are two individual cases to be considered here. First, where the RF memory tag
has some computation capabilities, i.e. a CPU or MCU, and second, where the compu-
tation has to be made on the reader.
The first case is conceptually more straightforward, as the agents on the RF mem-
ory tag are executed outside the mobile device and need only access to the information
stored in the space. This access may be limited by the space and thus the agents need
not to be particularly trusted.
The second case would involve running arbitrary code on the mobile device, and
presents a lot of additional problems to solve relating to security etc. Standard mech-
anisms related to e.g. downloading applications are probably not applicable, as the re-
quired interactions from the user should be kept to a minimum.
It should be noted that even as these cases differ on the implementation level and
required infrastructure, but the end result regarding the information content in the space
is the same.
This kind of “Agents on Tag” concept provides means to enhance the information
content stored on the mobile device by adding localized, positional knowledge to the
space. Furthermore, they may also utilize whatever information is available to them in
the space, perhaps creating a history of interactions for subsequent processing etc.
3.3 Space Interactions
The fourth case is particularly interesting as it provides temporary (or even permanent)
additional information for the user without resorting to agents. Any particular mobile
device is part of Smart Space environment as it is presented above, in Section 2, and
RF memory tag based infrastructure constitutes another Smart Space entity. This case
can be addressed by any two (2) Smart Spaces merge process. Similarly to the previous
agent interaction case there exist two distinct modes of operation, this time however
referring to the location of the broker that enables the space; these are visualised in
figures 5 and 6.
34
SIB SIB
RDF
Store
RDF
Store
(Mobile) Device
RF Memory Tag
distribution protocol
Fig. 5. Space Interaction (Tag hosting SIB).
SIB
RDF
Store
RDF
Store
(Mobile) Device
RF Memory Tag
distribution protocol
Fig. 6. Space Interaction (Tag not hosting SIB).
We would stick to the cases when RF memory tag based infrastructure is created by
manageable and non-manageable RF memory tags, meaning that the computational ca-
pabilities of any RF memory tag are extended, e.g. with CPU or MCU, and limited,
e.g. without CPU or MCU. To guarantee sustained data on the board of RF memory tag
there are facilities provided by memory chip and RF control. To provide mechanism for
proper allocation, management and removal of data, a recognizable list of data, ad hoc
data management system is used.
Let us concentrate more on the technical details of the process when such mobile
device would found any RF memory tag. To establish communication channel which
should be considered of ad hoc type, mobile device should scan the environment to get
the confirmation reply from any RF memory tag.
Once the physical connection is up and transport protocol is running, and RF mem-
ory tag can be mounted to be used as a storage space or it can begin to act as another
Smart Space entity. To simplify our further considerations, let us denote the mobileThis
work has been partially funded by TEKES ICT SHOK DIEM (www.diem.fi) and EU
FP6 MINAmI projects (http://www.fp6-minami.org/). device’s Smart Space as SS1, and
the RF memory tag based Smart Space as SS2.
In case if RF memory tag was mounted as a plain storage space it can be used as an
extent where, existed, SS1 keeps the data in raw (as it would be in case of any grow-
able filesystem volume). And, therefore, any POSIX like procedures could be applied
to gain the access and to store/remove the data on such volume. However, it is not really
beneficial way in case of Smart Space environment.
Since one of the main points to use the Smart Space environment is to provide in-
teroperable interaction between most of computing environment by exchanging high
abstraction level information, by means of Smart Space’s defined Insert, Remove, Sub-
scribe, Unsubscribe and Query primitives and utilizing a certain reasoning mechanism
over the different sets of that information, to extract the necessary one, the level of in-
35

teraction between mobile device and RF memory tag is pushed up to high abstraction
level of information exchange. Therefore, the rules of Smart Spaces merging process
are applied. Those can be seen within the following flow:
1. let us assume that SS1 represent an active entity from energy perspectives, therefore
it is assumed to be as a leading party (so defined master SIB or mSIB) which is
driving the merging process as such
2. even SS2 represents a passive entity from energy perspectives, it might have either
suspended SIB or RDF store facilities that can be merged with or utilized by the
corresponding SS1 facilities, thus, one of the following can take place:
(a) mounting as RDF store to SS1 facilities, providing passive information extent,
meaning that reasoning over that extent should be provided by SS1 facilities
(b) communicating as SIB-to-SIB, providing active information extent, meaning
that reasoning over that extent can be provided by resumed SS2 facilities.
3. invoke SS2 to Join the SS1 by means of Join/Leave message exchange and corre-
sponding Heartbeat message, to complete a handshake procedure
4. open communication as SIB-to-RDF (store) or SIB-to-SIB
5. prioritizing Query, Subscribe, Unsubscribe, Insert, Remove primitives to be issued
over the RF memory tag based information extent
6. prioritization is driven by reasoning over either the information extent provided by
SS1 or by SS2, thus the importance factor should be taken into account to leverage
the flow of any needed information
7. proceeding with information exchange, this can be seen as a scheduler loop over
the particular primitives queueThis work has been partially funded by TEKES
ICT SHOK DIEM (www.diem.fi) and EU FP6 MINAmI projects (http://www.fp6-
minami.org/).
8. finalizing communication as SIB-to-RDF (store) or SIB-to-SIB
9. leaving SS2 by Leave message from SS1 or invoking SS2 to send Leave message,
suspending it due to the passive mode
– any accidental power loss, which can be only due to the communication loss
(due to the nature of RF memory tag infrastructure), is accounted by transac-
tional model of any operations
Recombining cases above, to the better extent, a certain amount of agents could be
stored at RF memory tag infrastructure as well. And, once SS2 is resumed, agents are
retrieved from RF memory tag infrastructure along with information extent and the
physical context dependant application in merged SS1 and SS2 entity is assembled.
Logical flow above illustrates a strong potential of RF memory tag based infrastructure
as Smart Space environment from the hardware perspectives. Therefore the cases above
should not limit the scope of distributed RF memory tag infrastructure.
4 Issues
Any interaction in this kind of environment has security and in particular privacy issues.
Because of the shared and thus viral nature of the information, the spread of incorrect,
bad or otherwise information is made relatively trivial. There do exist methods for trust
36

and policy but these still have to gain widespread acceptance.
One particular aspect is the provision of location and temporal information - be-
cause of the physical nature of the devices we can trivially infer location and the point
in time when the interactions took place.
The trust of such a system ultimately resides with the users and the overall manage-
ment of the information being interacted with and provided. However given the rise of
social networking, microblogging and the very basic need to share information, many
of these issues are not addressed there either. Nevertheless provision of security mech-
anisms such as authentication, encryption, private space and persistence etc can help in
such matters.
Despite of these issues the benefits of such a mechanism for the user are tangible
and specifically in the areas of marketing, advertising and the provision of specific and
highly targetted temporal and location aware information.
Other concerns include the semantics and interpretation of the information con-
tained within the various spaces - a detailed discussion of these issues and some of
the solutions which are being implemented and investigated as part of the described
architecture and system can be found in [15–18]
5 Conclusions and Future Work
In this paper we have introduced and analyzed a concept where RF memory tags form
an extension to Smart Space infrastructure. Also most of the fundamental requirements
set for RF memory tag systems in such a context have been covered. In the present work
we have focused on interactions between the Smart Spaces and one individual tag.
The agent/space based system described in [10] provides a distributed infrastructure
for context gathering; while the agents themselves provide end-points for service usage.
Such services include those as provided by, for example: Nokia’s OVI
1
. Sharing through
physical access points such as RF memory tags provides additional and more novel in-
teraction with these services. This conclusively supports the trend towards context gath-
ering both in physical and virtual environments coupled with existing service-oriented
paradigms and building future information management and sharing approaches.
The future work will further extend the concept so that a population of tags forms
a platform for smart-space applications. This means that the SIB is implicitly shared
among the population by scattering copies of collaborating agents to the tags. In other
words, the tags collaborate with each other and form a SIB but due to the sporadic na-
ture of the processing capabilities and communication link enabled by the readers, the
tags have to rely on transfer of sporadic messages between each other.
Acknowledgements
This work has been partially funded by TEKES ICT SHOK DIEM (www.diem.fi) and
EU FP6 MINAmI projects (http://www.fp6-minami.org/).
1
www.ovi.com
37

References
1. J. Landt, “The history of RFID,” IEEE Potentials, vol. 24, no. 4, pp. 8-11, 2005.
2. EPCglobal, “EPC Radio-Frequency Identity Protocols Class-1 Generation-2 UHF RFID
Protocol for Communications at 860 MHz - 960 MHz Version 1.1.0”, EPCglobal Standard
Specification, 2005.
3. Pasquet, M.; Reynaud, J.; Rosenberger, C., Secure payment with NFC mobile phone in the
SmartTouch project, Collaborative Technologies and Systems, May 2008.
4. J. Savolainen, H. Hirvola, and S. Iraji, Nokia integroi lukimen E61- malliin: EPC-tunnistus
tulee pian k
¨
anykk
¨
an [Nokia Integrated a Reader into its E61 Model: EPC Identification
Comes Soon to Mobile Phones], Prosessori, pp. 42-43, August 2008.
5. J. Jantunen, A. Lappetel
¨
ainen, J. Arponen, A. P
¨
arssinen, M. Pelissier, B. Gomez, J.
Keignart, “A New Symmetric Transceiver Architecture for Pulsed Short-Range Commu-
nication,” IEEE Globecom, 2008.
6. E. Kaasinen, T. Tuomisto, P. V
¨
alkkynen, I. Jantunen, J. Sierra, ”Ubimedia based on mem-
ory tags,” Proceedings of the 12th international Conference on Entertainment and Media in
the Ubiquitous Era (Tampere, Finland, 2008). MindTrek ’08. ACM, New York, NY, 85-89.
7. K. Finkenzeller, “RFID Handbook: Radio-Frequency Identification Fundamentals and Ap-
plications”, Wiley, ISBN: 0471988510.
8. Ding L., Finin T., Peng Y., Pinheiro da Silva P., McGuinness D. L. Tracking RDF Graph
Provenance using RDF Molecules. Proceedings of the Fourth International Semantic Web
Conference, November 2005
9. S. Boldyrev, S. Balandin, Illustration of the Intelligent Workload Balancing Principle in
Distributed Data Storage Systems. Proceedings of workshop program of the 10th Interna-
tional Conference on Ubiquitous Computing, September 2008
10. Ian Oliver, Jukka Honkola, Personal Semantic Web Through A Space Based Computing
Environment, In proceedings: Middleware for the Semantic Web, Seconds IEEE Interna-
tional Conference on Semantic Computing, Santa Clara, CA, USA, August 4-7, 2008
11. Eero Hyv
¨
onen, Eetu M
¨
akel
¨
a, Tomi Kauppinen, Olli Alm, Jussi Kurki, Tuukka Ruotsalo,
Katri Sepp
¨
al
¨
a, Joeli Takala, Kimmo Puputti, Heini Kuittinen, Kim Viljanen, Jouni Tuomi-
nen, Tuomas Palonen, Matias Frosterus, Reetta Sinkkil
¨
a, Panu Paakkarinen, Joonas Laitio
and Katariina Nyberg, CultureSampo – A Collective Memory of Finnish Cultural Heritage
on the Semantic Web 2.0, November 2008
12. Tuukka Ruotsalo, Katri Sepp
¨
al
¨
a, Kim Viljanen, Eetu M
¨
akel
¨
a, Jussi Kurki, Olli Alm,
Tomi Kauppinen, Jouni Tuominen, Matias Frosterus, Reetta Sinkkil
¨
a and Eero Hyv
¨
onen,
Ontology—based Approach for Interoperability of Digital Collections, Signum, vol 5,
2008
13. Tim Berners-Lee and J Hendler and O Lassila,The Semantic Web, Scientific Ameri-
can,May 2001,vol 284:5 pp34-42
14. Ian Oliver and Jukka Honkola and Jurgen Ziegler, Dynamic, Localised Space Based Se-
mantic Webs, WWW/Internet Conference, Freiburg, Germany, October 2008
15. Ora Lassila, Some Personal Thoughts on Semantic Web and Non-symbolic AI, 4th Inter-
national Workshop on Uncertainty Reasoning for the Semantic Web October 2008
16. Hong-Gee Kim and Anseo-Dong, Pragmatics of the Semantic Web Semantic Web Work-
shop. Hawaii, USA, 2002
17. Afraz Jaffri, Hugh Glaser, Ian Millard, URI Disambiguation in the Context of Linked Data,
Linked Data on the Web (LDOW 2008), Beijing, China, April 2008
18. Kingsley Idehen and Orri Erling, Linked Data Spaces and Data Portability, Linked Data on
the Web (LDOW 2008), Beijing, China, April 2008
38
