
AN ADVANCED HOME ELDERCARE SERVICE
Tarik Taleb
Graduate School of Information Sciences, Tohoku University, Japan
Dario Bottazzi
Department of Electronics, Computer Science, and System Engineering, University of Bologna, Italy
Nidal Nasser
Department of Computing & Information Science, University of Guelph, Canada
Hammadi Nait-Charif
National Centre for Computer Animation, Bournemouth University, U.K.
Keywords:
Ubiquitous assistance, Pervasive computing, Healthcare network, Elderly.
Abstract:
With the increase of welfare cost all over the developed world, there is a need to resort to new technologies
that could help reduce this enormous cost and provide some quality eldercare services. This paper presents
a middleware-level solution that integrates monitoring and emergency detection solutions with networking
solutions. The proposed system enables efficient integration between a variety of sensors and actuators de-
ployed at home for emergency detection and provides a framework for creating and managing rescue teams
willing to assist elders in case of emergency situations. A prototype of the proposed system was designed and
implemented. Results were obtained from both computer simulations and a real-network testbed.
1 INTRODUCTION
World population is growing older, particularly in de-
veloped societies. As a consequence, a non-negligible
fraction of the world population is suffering from dif-
ferent impairments (e.g., vision, hearing, cognitive,
etc) that deprive people from independently perform-
ing basic activities (e.g., social interactions, house-
hold, and self-care). This growing percentage of el-
derly people in the society and the increasing number
of patients in need of home assistance put welfare sys-
tems under relevant stress.
To cope with this emerging issue, there is need
for novel forms of cost-effective welfare services and
technologies capable of accommodating the increas-
ing number of people in need of assistance. In this
vein, the US National Center on Medical Rehabilita-
tion Research (NCMRR) has defined five main direc-
tions for research related to the provision of assistance
to people in need of help. These directions pertain to
cellular (e.g., genetic abnormalities), organ (e.g., car-
diovascular pathology), action (e.g., paralysis), task-
role (e.g., Alzheimer), and social limitations (e.g., iso-
lation, depression, and memory impairment) (Mann,
2004). The two last areas form the main research fo-
cus in the NCMRR model. Indeed, there is a large
research body working on solutions at the task-role
level and addressing the social barriers. The devised
solutions aim at improving the quality of life of the el-
derly, enabling their autonomy in their daily activities,
and reducing their dependency on caregivers, fami-
lies, and friends. This is with every intention to render
their living environments more socio-emotional. Un-
like the cellular area whereby the solutions are medi-
cal curing-based, the focus of all other NCMRR areas
is on the development of technological solutions.
Indeed, a relatively new and fast growing trend in
the world of technology is the use of telecommunica-
tion technologies and pervasive computing as a tool in
the practice of medicine. The research work outlined
in this paper aims at designing a healthcare/welfare
service that enhances the daily life independence of
elderly in indoor environments. The main motiva-
30
Taleb T., Bottazzi D., Nasser N. and Nait-Charif H. (2009).
AN ADVANCED HOME ELDERCARE SERVICE.
In Proceedings of the International Conference on Health Informatics, pages 30-37
DOI: 10.5220/0001540400300037
Copyright
c
SciTePress

tion behind this research work emerges from the con-
viction that recent and ongoing advances in wireless
technologies, sensors, wearable devices, and com-
puter vision techniques, if integrated well, can offer
unique chances to improve the quality of life and pro-
vide vital assistance to elderly.
We therefore intend to design a wellness system
based on an efficient integration of pervasive comput-
ing technologies and computer vision techniques to
provide safety and quality of life to elderly and pa-
tients in need of help. In this research work, wearable
devices, sensors and computer vision techniques are
used for motion tracking, constant monitoring of the
patient’s behavior, and based on that, detection of be-
havioral abnormalities. On the other hand, telecom-
munication technologies are used to form groups of
volunteers and caregivers willing to help in case of
an emergency event, and thus provide elders with a
sense of safety. Their usage can be also extended to
forming communities of elders with common inter-
est and fostering social interactions among them. For
the sake of better customized eldercare solutions, it
would be worth focusing the work on one particular
pathology, e.g., Alzheimer, cardio-pathology. How-
ever, in this research work, we present the general
concept of our envisioned eldercare service which can
be easily tailored to any specific pathology taking into
account different factors such as clinical conditions of
the pathology and cultural profile of the patient.
Intuitively, the main advantage behind this re-
search work consists in the reduction of the social and
economic overhead of the hospitalization of elderly
and patients. Indeed, such a system will be deployed
where seniors live, will provide them with more au-
tonomy in carrying out their daily activities (e.g., re-
minding Alzheimer patients of routing activities), and
will assure them immediate assistance (from either
passing by volunteers or nursing experts) in case of
emergency events. This shall postpone or completely
avoid the transfer of elderly into nursing homes and
shall eventually allow health welfare of elderly to be
decentralized from hospital systems.
The remainder of this paper is organized as fol-
lows. Section II provides a survey on a number of
systems recently devised for ubiquitous eldercare and
discusses the advantages and pitfalls of each of them.
Section III describes the key components of the envi-
sioned home healthcare service. The major operations
of the proposed eldercare system are described in de-
tail in Section IV. The performance of the proposed
eldercare service architecture is evaluated in Section
V. The paper concludes in Section VI with a summary
recapping the main advantages and achievements of
the proposed service.
2 RELATED WORK
Ubiquitous eldercare has been gaining a great mo-
mentum in the last few years at both industry and
academia levels. Different solutions have been pro-
posed. Depending on their design goals, these so-
lutions can be categorized into two groups, namely
ubiquitous assistance and ubiquitous care networking
support (Bellavista et al., 2005).
In the first category, there has been a plethora
of research work addressing various aspects of
telemedicine. The main concerns of these solutions
consist in assisting elders in their routine life ac-
tivities, constant monitoring of their health condi-
tions, and prompt alerting in emergency events. In
(Marquis-Faulkes et al., 2003), a computer-vision
based system is proposed to support people with se-
vere vision impairments. To secure a safe navigation
of a particular environment, the system generates alert
messages, via a speech output interface, whenever a
change occurs to the layout of the environment. This
makes people, with vision deficiency and living in
that environment, aware of the occurring changes. In
(Mihailidis et al., 2004), artificial intelligence learn-
ing and planning techniques are used to define proper
steps of basic activities of daily living (e.g., hand-
washing). The resultant system provides visual or ver-
bal instructions to a person with dementia on how to
perform a particular daily living activity. The system
consists of three modules; a tracking module which
uses computer vision to monitor the actions of the
user by determining the spatial coordinates of the per-
son’s body and hands within the environment. Once
these coordinates have been determined, a planning
module determines what step the user is completing
and whether the step being completed is correct. If
the system detects that the user has made an error,
such as completing a step out of sequence or missing
a step altogether, the prompting module selects and
plays a prompt message. In (Pollack et al., 2004), a
cognitive orthotic system, called auto-minder, is pro-
posed. The system models the daily plans of an in-
dividual and decides on when and where to remind
the person of the execution of those plans. Benny et
al., in their UbiSense system, used embedded smart
vision techniques to detect changes in posture, gait
and activities. In addition to monitoring normal daily
activities and detecting potential adverse events such
as falls, the system aims to capture signs of deteri-
oration of the patients by analyzing subtle changes
in posture and gait (Lo et al., 2005). In their later
work, they used image sensing and vision-based rea-
soning to verify and further analyze events reported
by other sensors such as Accelerometer for fall detec-
AN ADVANCED HOME ELDERCARE SERVICE
31
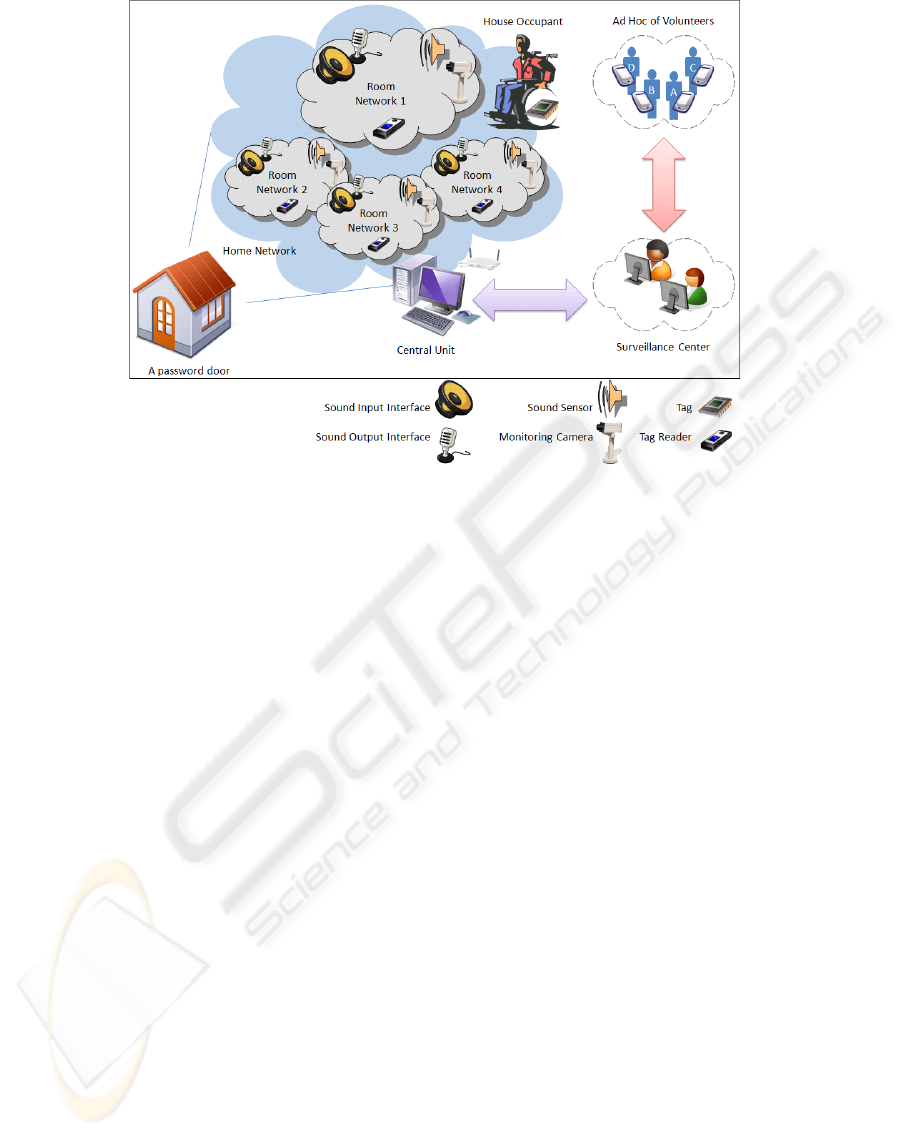
Figure 1: A smart living house with a set of intelligent devices, each with a different task.
tion (Tabar et al., 2006). The Independent Life Style
Assistant(ILSA) is another notable example of inte-
grated smart environments which aim at ubiquitous
assistance (K. Z. Haigh et al., 2004). In the ILSA sys-
tem, multiple JADE agents are deployed. The agents
support data monitoring via home-installed sensors.
The collected data are aggregated and processed to
make adequate response planning and machine learn-
ing.
The ubiquitous care networking area is still in its
infancy, with only a few solution proposals. The pri-
mary objective of ubiquitous care networking solu-
tions is to promote social interactions of elders with
their surroundings and to coordinate between the dif-
ferent actors involved in a ubiquitous eldercare event.
In (Bottazzi et al., 2006), a context-aware middleware
solution, dubbed Allocation and Group Aware Perva-
sive Environment (AGAPE), is proposed for the cre-
ation and management of ad-hoc assistance teams to
provide outdoor emergency assistance to senior citi-
zens in need of immediate help.
To conclude, different solutions have been devised
in the recent literature for both ubiquitous assistance
and ubiquitous care networking support. To the best
knowledge of the authors, no solution in the literature
has integrated the two types of ubiquitous eldercare
into one single solution. This challenging task under-
pins the focus of the research work outlined in this
paper.
3 ARCHITECTURE
DESCRIPTION
Fig. 1 depicts the envisioned architecture and its ma-
jor components. The figure portrays the case of a
smart indoor environment (e.g., living house) embed-
ding a variety of wireless devices, namely RFID (Ra-
dio Frequency Identification) readers, advanced cam-
era sensors, sound sensors, voice input/output inter-
faces, and a central unit (e.g., PC). The house is also
equipped with a smart door lock with a password-
opening function. The central unit is connected to a
surveillance center via the Internet and installs IBM
via voice in order to provide elders with a speech
based interface.
A RFID tag is adhered to the targeted senior or
a device that is frequently used by the person. Cost-
effective RFID readers are intelligently placed over
the house in a way that they provide complete cover-
age over the entire house. To avoid reader-to-tag in-
terferences, two adjacent readers are placed in a way
that the difference between their signal strengths is
less than the tag’s tolerance margin. By functioning
as the Reader Network Controller (RNC), the central
unit coordinates among the multiple readers using the
EPCglobal Low-Level Reader Protocol (LLRP).
In the considered architecture, all devices are logi-
cally located in three layers based on the order of their
inputs.RFID readers are placed in the first layer. They
are used to detect the senior when he gets nearby.
HEALTHINF 2009 - International Conference on Health Informatics
32
Their feedback is sent to the central unit. The lat-
ter uses this information to trigger camera and sound
sensors that are covering the area (i.e., room) where
the person is currently located. Other cameras and
sound sensors covering other rooms are kept off. This
is for the sake of efficient usage of energy (i.e., elec-
tricity). It also permits the central unit to analyze only
images obtained from a single camera, thus reducing
both home network overhead and computational load
that may be induced by computer vision techniques.
It should be noted that this operation can be also per-
formed using motion sensors. However, in case the
senior is sharing the house with other members of the
family, the use of motion sensors is not efficient as
they cannot distinguish the senior from the other fam-
ily members.
Advanced camera sensors are used for human mo-
tion monitoring (Nait-Charif and McKenna, 2003).
Their feedback is transmitted to the central unit. The
central unit uses this feedback to track the person and
to keep records of his motion. As will be explained
in the next section, the central unit uses also feed-
back from the camera sensors to make decision on
whether an anomaly occurred in the behavior of the
senior. For this purpose, the central unit applies a
set of algorithms to judge the conditions of the senior
(whether he is in a normal or an emergency situation)
(McKenna and Nait-Charif, 2004). Sound sensors are
used to enhance the anomaly detection (e.g., in case
the monitored senior falls down or screams for help).
For higher accuracy in capturing the elder’s behav-
ior, the central unit needs full visibility of the elder’s
context, including special layout of the objects in his
living environment. Such context awareness is pos-
sible by tagging items that are frequently used by the
senior (e.g., TV set, Sofa). Whenever a change occurs
in the layout of the living environment, updates of the
layout is possible via an efficient integration between
the inputs from the tag readers and the cameras.
Upon the detection of an anomaly, both voice in-
put and output interfaces are turned on. The central
unit first confirms with the senior if there is need for
any kind of assistance. In case this is confirmed by the
senior or there is no response from the senior within
a predefined timeout, a virtual connection is set be-
tween the central unit and the health-care service ad-
ministrator (i.e., surveillance center). The audio and
video captured from both the camera and sound sen-
sors, respectively, during the time of the emergency
event are sent to the surveillance center via the In-
ternet. As will be explained in the next section, the
surveillance center follows a number of steps to form
groups of volunteers that may provide the necessary
assistance to the senior. The service administrator
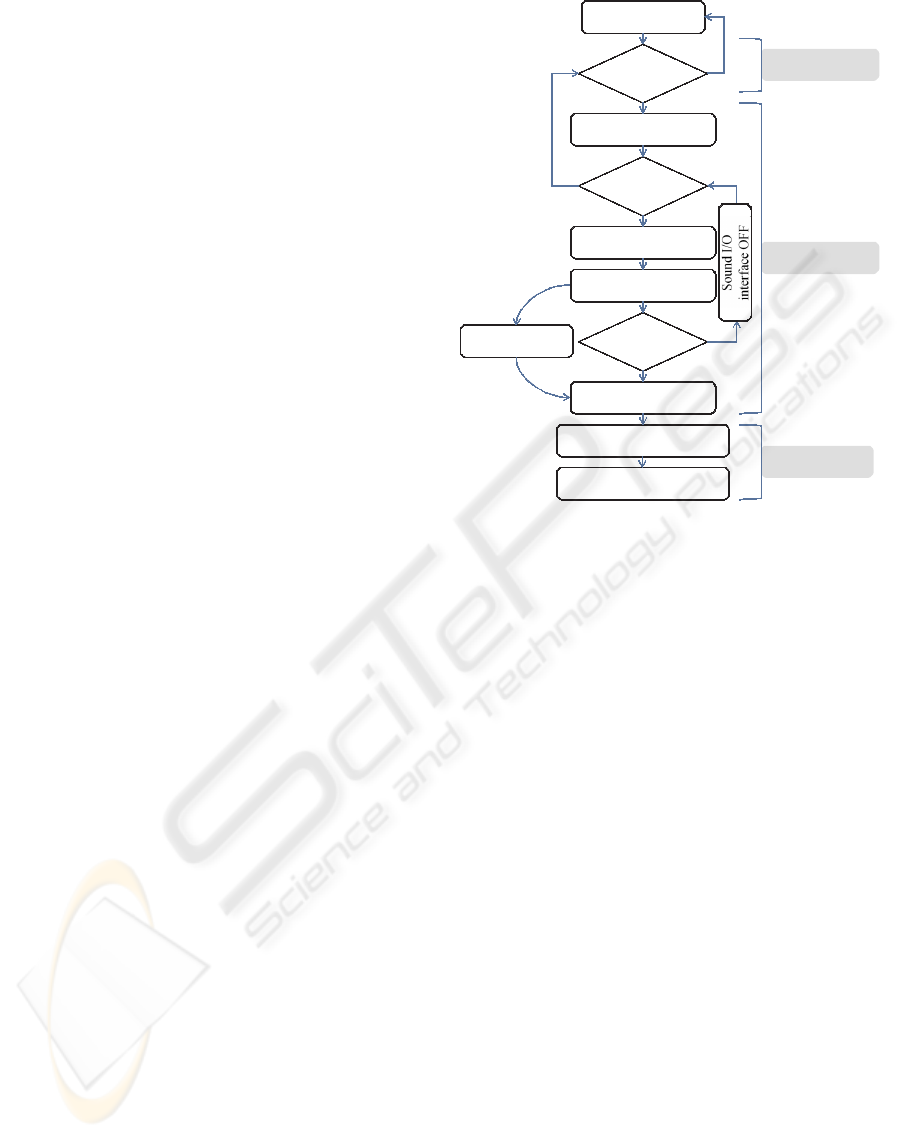
All devices OFF
Tag
detected?
Wake up camera/sound
sensor
Anomaly
detected?
Sound I/O interface ON
Is he/she
OK?
Send SOS message
along with video
Analyze video
Define emergency level
Timeout expires
Operations by SC
Contact volunteers
Form elder support group
Operation by Tag
Reader
Operations by HM
Inquiry the person if
he/she is Ok.
Yes
No
Yes
No
No
Yes
Figure 2: Major operations of the proposed eldercare sys-
tem.
will provide the selected volunteers with the password
to access the house of the senior. Major operations of
the proposed eldercare system are portrayed in Fig. 2.
4 PROPOSED ELDERCARE
SYSTEM
Anomaly Detection. At the start of the system, the
central unit develops a normal behavior model of the
elder (during the learning or profiling phase). This
model can be developed when the elder is supervised
by a nurse for a short period of time.
While receiving feedback from cameras and
sound sensors, the central unit compares the current
behavior with the normal behavior using computer vi-
sion techniques to judge the normalcy or the anomaly
of the instance. A set of predefined rules can be used
for setting up an alarm in case of anomaly.
While computer vision-based anomaly detection
is not the focus of the research work outlined in
this paper, there has been a wide library of research
work in the literature on computer vision techniques
(McKenna and Nait-Charif, 2004). These techniques
are used to track the occupant in his home environ-
ment and an AI system learns the daily life pattern in
order to detect any abnormalities such as falls or un-
usual activity/inactivity patterns that can be attributed
AN ADVANCED HOME ELDERCARE SERVICE
33

to health problem. Moreover, computer vision can be
used to collect more in-depth information in order for
the system to build more accurate models of the user
environment and help the agents at the surveillance
center to look retrospectively to events leading to any
unusual event such as a fall. In (McKenna and Nait-
Charif, 2004), a system is developed for automatically
tracking a single occupant in his home environment
(sitting room) and annotating his activities and detect-
ing any abnormal inactivity which might be a fall. In
this system, the occupant is tracked for an extended
period of time for the central unit to learn the usual en-
try/exit and inactivity zones in the sitting room. Once
the learning is done, computer vision techniques are
used to detect any unusual inactivity which can indi-
cate a matter of concern such as a fall and can be used
as part of an alarm to alert the surveillance center. In
this system, an inactivity was detected with a delay
τ
d
= 1.6 seconds.
Call for Help. Upon detection of any abnormalities
such as falls, faintness, or unusual activity/inactivity
patterns that can be attributed to health problem, the
central unit follows the steps depicted in Fig. 2. First
of all, the unit plays a prompt message via the voice
output interface inquiring the person if he is alright
or, indeed, in need of assistance. Awaiting a response
from the person, the system sets up a timeout. In
case the person confirms that he is in need of help
or the timeout expires, the system judges the event as
an emergency situation and an alert message is sent
to the surveillance center in the form of a SoS mes-
sage. Intuitively, such confirmation or timeout aims
at reducing false alerts to the surveillance center.
The alert message will be accompanied with the
capture video so the health-care service personnel
may look retrospectively at the moment just before
the event occurrence to analyze the cause of the event
and to decide whether the person is in an emergency
situation. Based on the capture video and the clinical
profile of the elder, the agent at the surveillance center
also defines the emergency level and type, its causes,
and the kid of help the person may be in need of.
To ensure a prompt assistance to the person, the
service administrator sends two types of messages:
i) a Warning Notification (WN) message to family
members, friends and relatives living in the immedi-
ate surroundings of the person, and a Call For As-
sistance (CFA) message broadcast to a database of
volunteers (e.g., passers-by, neighborhood commu-
nity representative and paid help, such as professional
caregivers, doctors, pharmacists, etc). To avoid flood-
ing the whole network with CFA messages, CFA mes-
sages are broadcast only over a particular locality
composed of a limited number of access points cov-
ering an area that forms a circle with the residence of
the senior at its center and a radius r. This locality
concept both mitigates the complexity of the group
formation problem as it limits the group management
scope and reduces responders’ intervention time.
CFA messages include information such as per-
sonal information of the senior (e.g., age, gender, etc),
the postal address of his residence, his physical and
cognitive characteristics, the kind of assistance he is
in need of, along with additional information (if avail-
able) describing the current conditions of the elder
(e.g., pulse). In response to the CFA message, volun-
teers willing to help send back an Acceptance Notifi-
cation (AN) message to the surveillance center. These
reply messages contain personal information of the
volunteers (e.g., name), their current location, and the
estimated time it may take them to get to the location
of the person in need of help.
In case of multiple replies from multiple volun-
teers, the surveillance center sorts out the most ade-
quate ones based on their geographical proximity to
the residence of the person, and some other informa-
tion already available in the database of volunteers,
such as their medical expertise, their history record
and skills in providing such assistance, and the trust
the surveillance center associates with them. The
sourcing of adequate volunteers from a group of repli-
ers prevents bystander apathy effect, which may in-
hibit responders from providing assistance to the el-
der. As will be explained later, it is based on the
multi-attribute decision making (MADM) theory.
Once the volunteers are sorted out, the surveil-
lance center notifies the selected ones of the password
to access the door of the person’s residence and the
other volunteers are simply exempted and thanked for
their eagerness to help (Fig. 3). At the same time,
the surveillance center provides the selected volun-
teers with instructions on how to assist the person.
Instructions can be either in a text or voice mode.
They consist of ”what-to-do” and ”how-to-do” lists
pertaining to tasks that need to be performed. Each
task entry in the ”what-to-do” list is associated with
an entry into the ”how-to-do” list that briefly instructs
users, untrained or unfamiliar with the system, on how
to perform the corresponding tasks. Once the volun-
teers enter the residence of the person in need of help,
the agent at the surveillance center keeps monitoring
them using the cameras available at the residence of
the person and providing them with further instruc-
tions whenever necessary.
It should be emphasized here that while it is pos-
sible to consider a self-functioning approach where
upon risk detection the central unit wirelessly broad-
casts CFP messages to an ad-hoc of passers-by, with
HEALTHINF 2009 - International Conference on Health Informatics
34
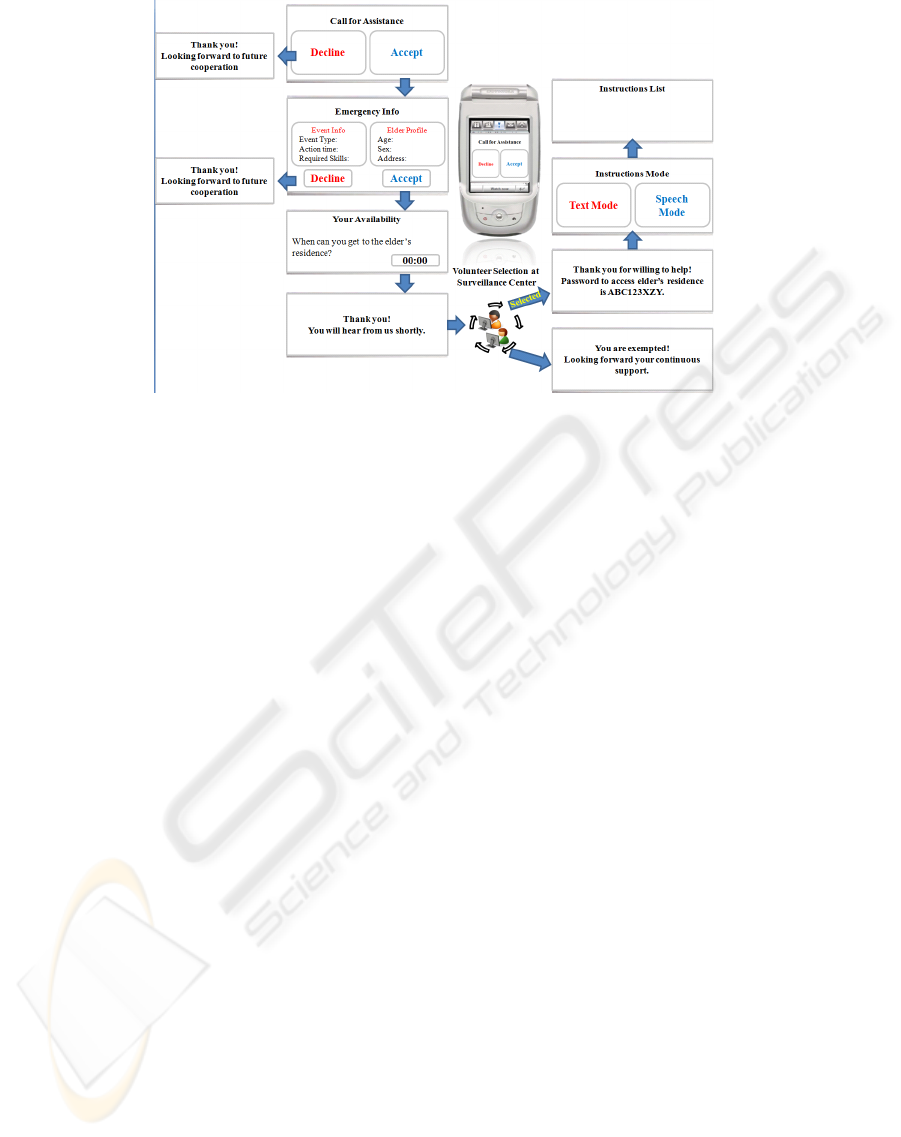
Figure 3: A prototype of application user interface.
no involvement of a central surveillance center similar
in spirit to the outdoor emergency assistance system
proposed in (Bottazzi et al., 2006), such an approach
gives rise to two major issues, mainly safety and false
alerts. The first issue is highly important as we are
aiming at indoor environments and the second is due
to the fact that computer vision still has limitations in
accurately capturing one’s activities and fully under-
standing his behavior from a video sequence, despite
of the wide library of research in this area.
Volunteers Selection Mechanism. In this section,
we describe the philosophy behind the selection of ad-
equate volunteers to cope with a particular emergency
situation. As stated earlier, the volunteer selection
mechanism is based on the multi-attribute decision
making theory. Indeed, in the proposed system, the
surveillance center maintains profiles of each volun-
teer; already subscribed to the service. For each sub-
scriber S
k
, a set of attributes {X
k, j
, j ∈ {1, 2,··· , `}
is associated. The attributes represent i) the expertise
and skills of volunteers, ii) their history record in pro-
viding assistance, and iii) the trust level the surveil-
lance center associates with them. It should be noted
that these attributes are constantly updated and main-
tained by the surveillance center.
In the proposed system, we assume that there
are M emergency levels defined a priori at the
surveillance center. For each emergency level
ℑ
i
(i ∈ {1, 2, · ·· , M}) and each attribute X
j
( j ∈
{1,2, ·· · ,`}), the surveillance center defines a weight
ω
i, j
. Additionally, with each emergency level ℑ
i
,
three parameters are associated: i) θ
α.i
defining the
minimum time within which assistance should be pro-
vided to the senior, ii) τ
i
defining the maximum time
(i.e., timeout) the surveillance center should wait for
to receive AN messages from volunteers, and iii) γ
i
defining a threshold for selecting volunteers. It should
be noted that these three parameters should be care-
fully set by the surveillance center. For example, in
case of a life-threatening event (e.g., heart attack),
both action time Θ
α.i
and waiting timeout τ
i
should
be set to small values. In case of a bone fracture due
to a fall, expertise and skills become more important
so the system can set γ to high value with focus on the
skills-related attribute. Action time θ
α
and timeout τ
can be set to relatively high values.
Upon receiving a SOS message, the agent in
charge (at the surveillance center) first defines the
corresponding emergency level based on i) the event
type determinable from the capture video (e.g., fall,
faintness, heart-attack) and ii) the profile of the se-
nior (e.g., physical and cognitive characteristics). Let
ℑ
m
denote the selected emergency level. For a time-
out τ
m
, the agent waits for responses from volunteers.
Once the system receives enough replies or the time-
out τ
m
expires, the system sorts out the replying vol-
unteers based on information available in their AN
messages, such as their physical proximity and avail-
ability, using the action time Θ
α.m
. Indeed, as ex-
plained earlier, a volunteer S
k
notifies the surveillance
center of the time he may need to reach the residence
of the senior, should he be selected for the rescue
task. Let ∆
a.k
denote the availability of volunteer S
k
in
terms of time. Using the action time Θ
α.m
of the emer-
gency level, volunteers with time availability ∆
a.k
sat-
isfying the following inequality are selected.
∆
a.k
≤ {Θ
α.m
− θ
d
− θ
SoS
− θ
H
− θ
E
− θ
select
} (1)
where θ
d
refers to the time elapsed since the actual
AN ADVANCED HOME ELDERCARE SERVICE
35

occurrence of the event till its detection by the central
unit. θ
SoS
denotes the time required to send SoS mes-
sage and the capture video to the surveillance center.
θ
H
refers to the time required by the agent to analyze
the video and to determine the emergency level. θ
E
denotes the time required to exchange signaling mes-
sages (e.g., CFA, WN, AN) between volunteers and
the surveillance center. θ
select
denotes the time re-
quired by the surveillance center to run the volunteers
selection algorithm.
At the second stage, the surveillance center sorts
(Out of the selected volunteers) those with attributes
satisfying the following condition.
`
∑
n=1
X
k,n
· ω
m,n
≥ γ
m
(2)
In case the number of volunteers selected at the sec-
ond phase are numerous, to avoid bystander apa-
thy effect only an adequate number of volunteers
are requested to assist and are provided with pass-
word to the gate of the senior’s residence along with
instructions corresponding to the determined emer-
gency level ℑ
m
.
5 PERFORMANCE EVALUATION
Our deployment settings are as shown in Fig. 1. The
used cameras are standard digital video cameras op-
erating at 30 frames per second, ceiling-mounted,
with vertically-oriented optical axes, fitted with wide-
angle lenses. For monitoring the behavior of elders
affected with severe vision impairments, the anomaly
detection algorithm proposed in (McKenna and Nait-
Charif, 2004) is used. A Pentium-based PC running
Gentoo Linux, J2SE 1.5 covering the central unit role
was also deployed in the apartment. In particular,
the system was appropriately configured and enabled
to gather sensing information from the available sen-
sors, i.e., RFID readers, sound sensors and cameras.
In our testbed, we also deployed a PC running Gen-
too Linux, J2SE 1.5 playing the surveillance center
role. In addition, by exploiting the wireless Wi-Fi in-
frastructure deployed in our campus in University of
Bologna, we also defined several localities. In our
prototype, each network cell defines a locality. In
each locality, we have also deployed a server, run-
ning Gentoo Linux, J2SE 1.5, managing among all
terminals currently located in the locality. Finally,
we also setup several wireless-enabled iPAQ PDAs,
acting as user terminals for responders. Each device
installs Personal Java, J/LMS, and client-side com-
ponents. On top of the terminals, we also imple-
mented an application prototype that provides avail-
able helpers with alert messages when an emergency
situation occurs. Indeed, the application continuously
makes the aware of the emergency notification by
emitting a sound signal with an increasing volume till
the user accepts or declines the request.
We have tested the system’s responsiveness, de-
fined as the amount of time required for forming an
elder support group, in scenarios simulated with NS-
2 and consisting of a number of devices randomly
deployed over the same locality, i.e., the same wire-
less LAN. To investigate the functionality of the sys-
tem under different network conditions, we range the
number of responders from 2 to 100. Our simula-
tion settings consider IEEE 802.11 networks with 10
Mbps transmission rate, random waypoint mobility
pattern and speeds ranging from 1 to 3m/s. For the
sake of simplicity, users are assumed to respond im-
mediately to CFA messages; time needed for a user to
detect alerting messages is set to zero. Admittedly, in
real-life scenarios, this time may dominate the overall
group formation time. The simulations demonstrate
that the system’s responsiveness is, on average, of
few seconds and tend to degrade to few tens seconds
when more than 60 LRs are available. Responsive-
ness degrades due to increase in packet losses, due
in turn to wireless network characteristics (e.g., lim-
ited bandwidth and channel error rates), in addition to
a minimal contribution from the computational load
that comes with fetching the profiles of users and with
the users selection algorithm.
Fig. 4 depicts the memory requirements as seen
from a single responder device. The figure shows
the overall memory requirements over time. In our
experiments, we tracked memory use for a respon-
der device in a locality where three other responders
were available. The experiment lasted for a duration
of 13 minutes. All data were obtained by exploiting
the JConsol profiling tool. From Fig. 4-a, the total
amount of the used heap memory varies between 0.7
MB and 1.3 MB, with an average value of about 0.9
MB. In addition, non-heap memory including data,
code and stack reaches a stable value of about 14 MB
(Fig. 4-b). From these results, it can be concluded that
the system’s group management support can be easily
installed over a PDA.
The system’s overall responsiveness, defined as
the time elapsed since the emergency occurrence till
the arrival of the first helper to the residence of the
senior in need of assistance, is an important metric
for the system performance evaluation. However, it is
highly difficult to exactly determine it. This is mainly
due to the fact that the system responsiveness depends
on unpredictable human factors, such as the behavior
of the local responders (e.g., promptness in reacting to
HEALTHINF 2009 - International Conference on Health Informatics
36
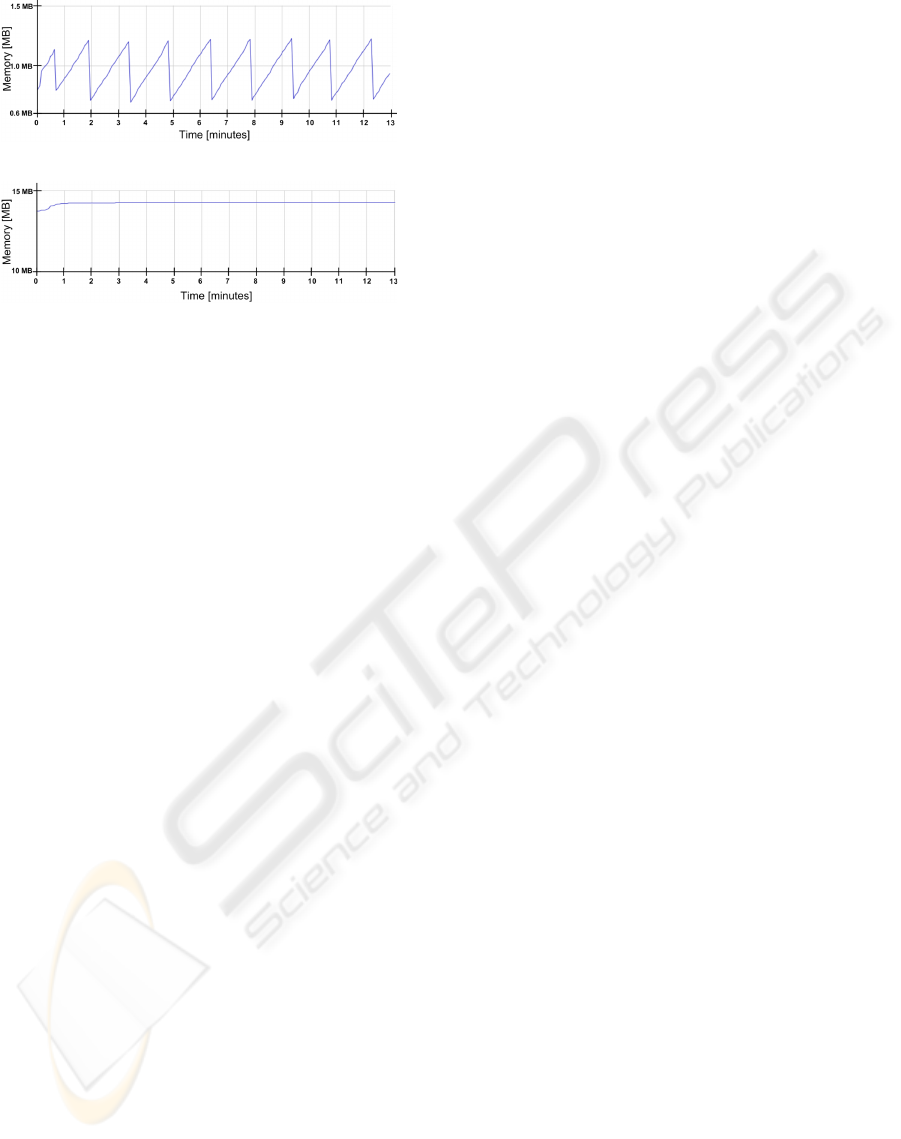
(a) Heap memory.
(b) Non-heap memory.
Figure 4: Memory use on responder devices.
CFA messages) and their availability in terms of time
which hinges, in turn, on their daily commitments.
One way to cope with this challenge is to have the
surveillance center form a statistical profile over time
on the number of volunteers that visit its area of ser-
vice and keep history track of the responsiveness of
volunteers in terms of their reaction to CFA messages.
Based on this statistical profile and history track, the
surveillance center can define a process for the arrival
of AN messages from volunteers, based on which it
can make an estimate of the system’s overall respon-
siveness to cope with a particular emergency situation
occurring at a particular time in a particular locality.
6 CONCLUDING REMARKS
A prototype system has been developed to help el-
ders at home. The proposed system is expected to
also help reduce the cost incurred by the current el-
dercare service. The system is made of sensors and
actuators that are connected to a central unit, acting as
home network manager. The system is able of gath-
ering and aggregating row information from sensing
sources and detecting possible dangerous situations
based on computer vision. A prototype user interface
was also developed for responders’ PDAs. The per-
formance of the proposed system was evaluated based
on both computer simulations and real-network ex-
periments. The results were obtained in terms of bat-
tery consumption and memory use at helpers’ termi-
nals. Once fully implemented and adopted, we expect
that the proposed system will have a great impact in
improving eldercare services all over the world.
REFERENCES
Bellavista, P., Bottazzi, D., Corradi, A., and Montanari, R.
(2005). Challenges, opportunities and solutions for
ubiquitous eldercare. Tech. report, DEIS University
of Bologna.
Bottazzi, D., Corradi, A., and Montanari, R. (2006).
Context-aware middleware solutions for anytime and
anywhere emergency assistance to elderly people.
IEEE Commun. Mag., 44(4):82–90.
K. Z. Haigh, L. M. Kiff, J. M., Guralnik, V., Geib, C. W.,
Phelps, J., and Wagner, T. (2004). The independent
lifestyle assistant (i.l.s.a.): Ai lessons learned. In Proc.
16th Innovative Applications of Artificial Intelligence
Conf. (IAAI’04), San Jose, CA.
Lo, B., Wang, J., and Yang, G. (2005). From imaging net-
works to behavior profiling: Ubiquitous sensing for
managed homecare of the. elderly. In Proc. 3rd Int’l
Conf. on Pervasive Computing, Munich, Germany.
IEEE Press.
Mann, W. C. (2004). The aging population and its needs.
IEEE Pervasive Computing Mag., 3(2):12–14.
Marquis-Faulkes, F., McKenna, S., Gregor, P., and Newell,
A. (2003). Scenario-based drama as a tool for inves-
tigating user requirements with application to home
monitoring for elderly people. In Proc. 10th Int’l
Conf. on Human-Computer Interaction (HCI’03),
Crete, Greece. IEEE Press.
McKenna, S. J. and Nait-Charif, H. (2004). Summarising
contextual activity and detecting unusual inactivity in
a supportive home environment. Pattern Analysis and
Applications, 7(4):386–401.
Mihailidis, A., Carmichael, B., and Boger, J. (2004). The
use of computer vision in an intelligent environment
to support aging-in-place, safety, and independence
in the home. IEEE Trans. Information Technology in
Biomedicine, 8(3):238–247.
Nait-Charif, H. and McKenna, S. J. (2003). Head track-
ing and action recognition in a smart meeting room.
In 4th IEEE Int’l Workshop on Performance Eval-
uation of Tracking and Surveillance, Int’l Conf. on
Computer Vision Systems (PETS-ICVS), pages 24–31,
Graz, Austria. IEEE Press.
Pollack, M., Brown, L., Colbry, D., McCarthy, C., Orosz,
C., Peintner, B., Ramakrishnane, S., and Tsamardi-
nos, I. (2004). Autominder: An intelligent cognitive
orthotic system for people with memory impairment.
Robotics and Autonomous Systems, 44(3-4):273–282.
Tabar, A., Keshavarz, A., and Aghajan, H. (2006). Smart
home care network using sensor fusion and distributed
vision-based reasoning. In Proc. 4th ACM Int’l Work-
shop on Video Surveillance and Sensor Network,,
Santa Barbara, USA. ACM Press.
AN ADVANCED HOME ELDERCARE SERVICE
37
