
FORWARD-SECURE PROXY SIGNATURE
AND REVOCATION SCHEME FOR A PROXY SIGNER WITH
MULTIPLE ORIGINAL SIGNERS
B. B. Amberker
Department of Computer Science & Engg., National Institute of Technology, Warangal, Andhra Pradesh, India
N. R. Sunitha
Department of Computer Science & Engg., Siddaganga Institute of Technology, Tumkur, Karnataka, India
Keywords:
Proxy Signature, Forward-Security, Digital Signature, Proxy Key Pair, Key Evolution, Proxy Revocation.
Abstract:
On many occasions it is required for a single person to take up the responsibilities of many persons for some
duration and work on their behalf so that the regular work goes on smoothly. For example in a bank, when
majority of the employees need to attend an important meeting during working hours, to avoid disrupting any
of the regular activities, one employee may need to play the role of many employees. An accountant may need
to play the role of a cashier, asst. manager and cheque clearing officer. In such situations the employee working
on behalf of other employees need to be delegated with signing power from the employees who perform the
activities regularly. Also, this delegation must be only for some specified time period T and after the elapse of
that time period the signing capability must be revoked. The concept of proxy signatures is used here.
A proxy signature scheme allows one user to delegate his/her signing capability to another user called a proxy
signer in such a way that the latter can sign messages on behalf of the former. After verification the verifier
is convinced of the original signer’s agreement on the signed message. Forward-Secure signatures enable the
signer to guarantee the security of messages signed in the past even if his secret key is exposed today. We have
come up with a forward secure proxy signature and revocation scheme for a proxy signer who is delegated with
signing power from multiple original signers. This scheme is based on the popular Bellare-Miner Forward-
secure scheme.
1 INTRODUCTION
A proxy signature (M. Mambo and Okamoto, 1996;
M. Mambo, 1996) allows one user Alice, called the
original signer, to delegate her signing capability to
another user Bob, called the proxy signer. After that,
the proxy signer Bob can sign messages on behalf of
the original signer Alice. Upon receiving a proxy sig-
nature on some message, a verifier can validate its
correctness by the given verification procedure. By
this the verifier is convinced of the original signer’s
agreement on the signed message. Proxy signatures
can be used in a number of applications like e-cash,
electronic commerce, mobile computing distributed
shared object systems etc.
The basic working of most proxy signature
schemes is as follows. The original signer Alice sends
a specific message with its signature to the proxy
signer Bob, who then uses this information to con-
struct a proxy private key. With the proxy private key,
Bob can generate proxy signatures by employing a
specified standard signature scheme. When a proxy
signature is given, a verifier first computes the proxy
public key and then checks its validity according to
the corresponding standard signature verification pro-
cedure.
Mambo, Usuda and Okamoto introduced the con-
cept of proxy signatures and proposed several con-
structions in (M. Mambo and Okamoto, 1996). Based
on the delegation type, they classified proxy signa-
tures as full delegation, partial delegation and delega-
tion by warrant schemes. In full delegation, Alice’s
private key is given to Bob so that Bob has the same
signing capability as Alice. But such schemes are ob-
viously impractical and insecure. In a partial dele-
gation scheme, a proxy signer has a new key called
proxy private key, which is different from Alice’s pri-
vate key. So, proxy signatures generated by using
245
B. Amberker B. and R. Sunitha N. (2008).
FORWARD-SECURE PROXY SIGNATURE AND REVOCATION SCHEME FOR A PROXY SIGNER WITH MULTIPLE ORIGINAL SIGNERS.
In Proceedings of the International Conference on Security and Cryptography, pages 245-252
DOI: 10.5220/0001919302450252
Copyright
c
SciTePress

proxy private key are different from Alice’e standard
signatures. However the proxy signer can sign any
message of his choice i.e there is no limit on the range
of messages he can sign. This limitation is eliminated
in delegation by warrant schemes by adding a warrant
that specifies what kind of messages are delegated and
may contain the identities of Alice and Bob, the dele-
gation period, etc.
Followed by the first constructions given in
(M. Mambo and Okamoto, 1996; M. Mambo, 1996),
a number of new schemes and improvements have
been proposed (S. Kim and Won., 1997; Zhang.,
1997; Zhang, 1997; N.-Y. Lee and Wang, 1998; Gho-
dosi and Pieprzyk, 1999; T. Okamoto and Okamoto,
1999; B. Lee and Kim, 2001b; B. Lee and Kim,
2001a; Park and Lee, 2001; J.-Y. Lee and Kim, 2003;
Wang and Pieprzyk., 2003; A. Boldyreva and Warin-
schi, 2003); however, most of them do not fully meet
the security requirements of a proxy signature scheme
(see Section 2) . In (S. Kim and Won., 1997), Kim,
Park and Won proposed a threshold proxy signature,
in which the original signing power is shared among
a delegated group of n proxy signers such that only
t or more of them can generate proxy signatures co-
operatively. In (B. Lee and Kim, 2001b), Lee, Kim
and Kim proposed non-designated proxy signature in
which a warrant does not designate the identity of a
proxy signer so any possible proxy signer can respond
to this delegation and become a proxy signer. Fur-
thermore, their scheme is used to design secure mo-
bile agents in electronic commerce setting (B. Lee and
Kim, 2001a). One-time proxy signatures are studied
in (Ai-Ibrahim and Cerny, 2003; Wang and Pieprzyk.,
2003). In (J.-Y. Lee and Kim, 2003), Lee, Cheon,
and Kim investigated whether a secure channel for
delivery of a signed warrant is necessary in existing
schemes. Their results show that if the secure channel
is not provided, the MUO scheme (M. Mambo and
Okamoto, 1996) and the LKK scheme (B. Lee and
Kim, 2001b; B. Lee and Kim, 2001a) are insecure. To
remove the requirement of a secure channel and over-
come some other weaknesses, they revised the MUO
and LKK schemes (M. Mambo and Okamoto, 1996;
M. Mambo, 1996; B. Lee and Kim, 2001b). In con-
trast to the above mentioned schemes, which all are
based on discrete logarithm cryptosystems, several
RSA-based proxy signature schemes are proposed in
(T. Okamoto and Okamoto, 1999; B. Lee and Kim,
2001a). In (Zhen Chuan Chai, 2004) a factorisation
based forward-secure proxy signature scheme is pro-
posed. The scheme is based on the forward-secure
scheme of Abdalla and Reyzin.
In (Guilin Wang, 2004) a proxy signature scheme
with multiple original signers suitable for wireless
electronic commerce applications is proposed. When
compared to this scheme, our scheme has the property
of forward-security (this enables the proxy signer to
guarantee the security of messages signed in the past
even if his secret key is exposed today) and the proxy
signer will be delegated with signing power only for
a time period T . After the elapse of this time period,
the proxy signer will automatically be revoked.
We consider a scenario where there is need for a
single person to take up the responsibilities of many
persons for some duration and work on their behalf so
that the regular work goes on smoothly. For example
in a bank, an accountant may need to play the role of
a cashier, asst. manager and cheque clearing officer.
In such situations the employee working on behalf of
other employees need to be delegated with signing
power from the employees who perform the activities
regularly. This can be addressed using regular proxy
signatures. In terms of proxy signatures, the prob-
lem we have considered requires a single proxy signer
to sign on behalf of multiple original signers. Regu-
lar proxy signature force the proxy signer to generate
separate proxy key pair for each original signer. In the
scheme we propose the proxy signer just computes a
single proxy key pair for n original signers. Also, as
digital signatures, proxy signatures are also vulnera-
ble to leakage of proxy secret key. If the proxy secret
key is compromised, any message can be forged. To
prevent future forgery of signatures, the concept of
forward-security (Anderson, 1997) can be used (see
section 3). We use the property of forward-security
and apply it to proxy signatures. We therefore pro-
pose a new Forward-secure proxy signature and revo-
cation scheme for a proxy signer with multiple orig-
inal signers which is based on the popular Forward-
secure Bellare-Miner scheme (Bellare, 1999). The
scheme has the following features:
• The scheme is based on Forward-secure Bellare-
Miner scheme.
• Multiple original signers can delegate signing
power to a single proxy signer.
• Proxy signer is capable of signing on behalf of
original signers only for a time period T , after
which he is revoked as a proxy signer.
• Identity of the proxy signer is available in the in-
formation sent by original signer to proxy signer.
• Secure channel is not required to send the infor-
mation to proxy signer.
• There is a facility to send warrant messages to
proxy signer and verifier.
• Original signer cannot play the role of proxy
signer.
SECRYPT 2008 - International Conference on Security and Cryptography
246

• Verifier can determine when the proxy signature
was generated.
• Both the original signer’s signature and proxy
signer’s signature are made Forward-secure.
The organisation of our paper is as follows: In
Section 2, we discuss the basic security requirement
of any proxy signature scheme. In Section 3, we de-
scribe briefly the properties of forward-secure signa-
ture schemes. In Section 4, we describe our proxy
signature scheme. In Section 5, we discuss the secu-
rity of our scheme and in Section 6, we conclude the
paper.
2 SECURITY REQUIREMENTS
OF A PROXY SIGNATURE
SCHEME
Any secure proxy signature scheme should satisfy the
following five requirements:
1. Verifiability. From the proxy signature, a verifier
is convinced of the original signer’s agreement on
the signed message.
2. Strong Uunforgeability. Only the designated
proxy signer can create a valid proxy signature on
behalf of the original signer.
3. Strong Identifiability. Anyone can determine the
identity of the corresponding proxy signer from
the proxy signature.
4. Strong Undeniability. Once a proxy signer creates
a valid proxy signature on behalf of an original
signer, he cannot repudiate the signature creation
against anyone else.
5. Proxy Signer’s Deviation. A proxy signer cannot
create a valid signature not detected as a proxy
signature.
3 FORWARD SECURE
SIGNATURE SCHEME
Digital signatures are vulnerable to leakage of secret
key. If the secret key is compromised, any message
can be forged. To prevent future forgery of signatures,
both public key and secret key must be changed. No-
tice, that this will not protect previously signed mes-
sages: such messages will have to be re-signed with
new pair of public key and secret key, but this is not
feasible. Also changing the keys frequently is not a
practical solution.
To address the above problem, the notion of for-
ward security for digital signatures was first proposed
by Anderson in (Anderson, 1997), and carefully for-
malised by Bellare and Miner in (Bellare, 1999) (see
also(Abdalla, 1997; Krawczyk, 2000; Itkis, 2001; Ko-
zlov, 2002)). The basic idea is to extend a standard
digital signature scheme with a key updation algo-
rithm so that the secret key can be changed frequently
while the public key stays the same. Unlike a standard
signature scheme, a forward secure signature scheme
has its operation divided into time periods, each of
which uses a different secret key to sign a message.
The key updation algorithm computes the secret key
for the new time period based on the previous one us-
ing a one way function. Thus, given the secret key
for any time period, it is hard to compute any of the
previously used secret keys. (It is important for the
signer to delete the old secret key as soon as the new
one is generated, since otherwise an adversary break-
ing the system could easily get hold of these undeleted
keys and forge signatures.) Therefore a receiver with
a message signed before the period in which the secret
key gets compromised, can still trust this signature,
for it is still hard to any adversary to forge previous
signatures.
To specify a forward-secure signature scheme, we
need to (i) give a rule for updating the secret key (ii)
specify the public key and (iii) specify the signing and
the verification algorithms.
4 FORWARD-SECURE PROXY
SIGNATURE AND
REVOCATION SCHEME FOR A
PROXY SIGNER WITH
MULTIPLE ORIGINAL
SIGNERS
As digital signatures, proxy signatures are also vul-
nerable to leakage of proxy secret key. If the proxy se-
cret key is compromised, any message can be forged.
To prevent future forgery of signatures, both proxy
public key and proxy secret key must be changed
which forces the original signer to change the proxy
information. But this will not protect previously
signed messages: such messages will have to be re-
signed with new pair of proxy public key and secret
key which is not feasible. To address this problem,
we use the concept of forward security for proxy sig-
natures.
The basic idea behind the construction of our
scheme is as follows: There are n persons in the
role of original signer who wants Bob to be the
FORWARD-SECURE PROXY SIGNATURE AND REVOCATION SCHEME FOR A PROXY SIGNER WITH
MULTIPLE ORIGINAL SIGNERS
247
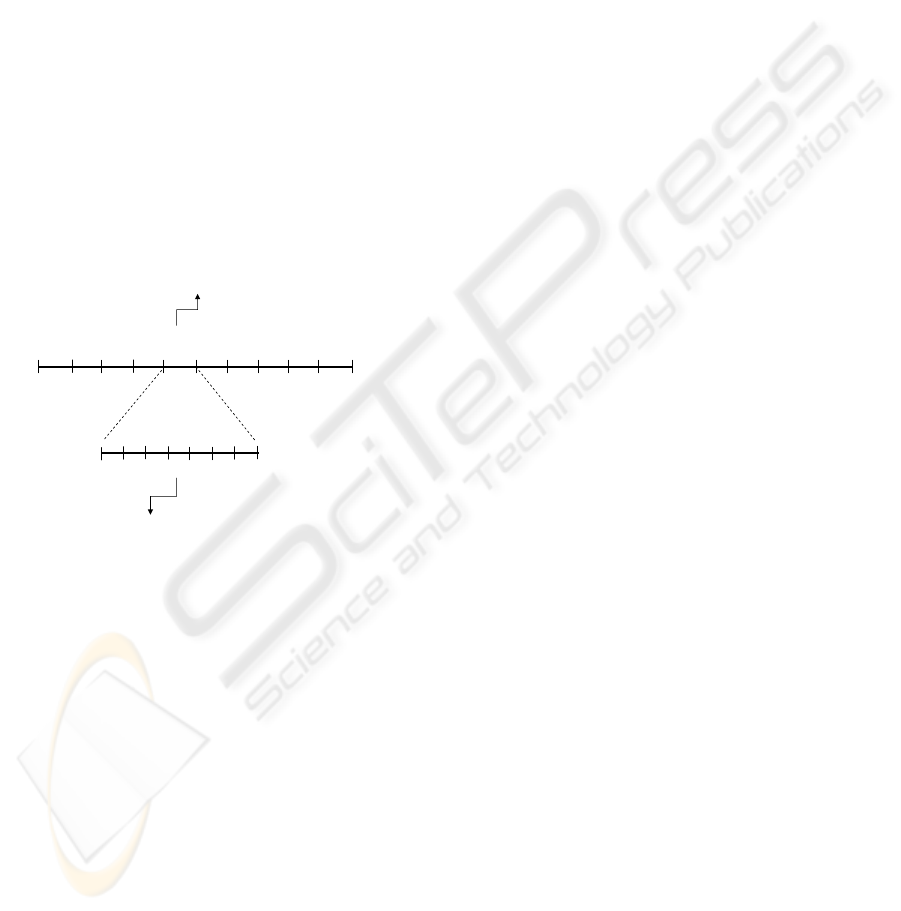
proxy signer for T time periods. Each original signer
A
x
(where x = 1, . . . , n) computes P
A
x
, j,in f o
in every
time period j (which ranges from 1 to T ) and sends it
along with other proxy information to Bob. Bob ver-
ifies that he is designated as a proxy signer by each
of the original signers. If the verification holds Bob
computes the proxy key pair (x
p,0
, y
p
). Bob divides
the time period j into T
0
time periods and signs any
messages in these j
0
time periods (which ranges from
1 to T
0
) using Forward-secure signatures (see Figure
1). Thus the proxy signatures generated by Bob are
Forward-secure proxy signatures. Bob will be able
to generate proxy signatures on behalf of the origi-
nal signers only for T time periods. After the elapse
of this time period, he is automatically revoked as a
proxy signer. On receiving the proxy signatures, the
verifier first computes the proxy public key using the
available proxy information. Using this public key
later verifies the signature using the verification equa-
tion of the forward-secure proxy signature scheme.
1
2
T
j
j’
1
2
T’
Original signer’s time periods
Proxy signer’s time periods
Proxy secret key in j’
time period
Proxy information by original signer A1
to proxy signer in j
th
time period.
P
j,A1,info
x
p, j’
Figure 1: Basic idea of the scheme.
4.1 Initial Setup
Let p, q be two large primes each congruent to
3 mod 4. Let N = p.q.
T is the time period in which the signing power is
delegated by original signers to proxy signer.
The initial secret key of original signer A
1
is SK
A
1
,0
= (SK
A
1
,(1,0)
, . . . , SK
A
1
,(l,0)
, N, 0) where
S
A
1
,(i,0)
R
← Z
∗
N
.
Secret key SK
A
1
, j
= (SK
A
1
,(1, j)
, . . . , SK
A
1
,(l, j)
) for
any time period j is obtained by updating the secret
key SK
A
1
, j−1
= (SK
A
1
,(1, j−1)
, . . . , SK
A
1
,(l, j−1)
) of the
previous time period via the update rule
SK
A
1
,(i, j)
= SK
2
A
1
,(i, j−1)
mod N, (1)
where i = 1, . . . , l.
The public key is U
A
1
= (U
A
1
,1
, . . . ,U
A
1
,l
), is cal-
culated as the value obtained on updating the base se-
cret secret key T + 1 times:
U
A
1
,i
= SK
2
T +1
A
1
,(i,0)
mod N. (2)
Let there be n number of original signers.
The initial secret key of any original signer A
x
is SK
A
x
,0
= (SK
A
x
,(1,0)
, . . . , SK
A
x
,(l,0)
, N, 0) where
S
A
x
,(i,0)
R
← Z
∗
N
and x = 1, . . . , n.
Secret key SK
A
x
, j
= (SK
A
x
,(1, j)
, . . . , SK
A
x
,(l, j)
) for
any time period j is obtained by updating the secret
key SK
A
x
, j−1
= (SK
A
x
,(1, j−1)
, . . . , SK
A
x
,(l, j−1)
) of the
previous time period via the update rule
SK
A
x
,(i, j)
= SK
2
A
x
,(i, j−1)
mod N, (3)
where i = 1, . . . , l.
The public key is U
A
x
= (U
A
x
,1
, . . . ,U
A
x
,l
), is calcu-
lated as the value obtained on updating the base secret
secret key T + 1 times:
U
A
x
,i
= SK
2
T +1
A
x
,(i,0)
mod N. (4)
Bob is a proxy signer. His initial secret
key is SK
B,0
= (SK
B,(1,0)
, . . . , SK
B,(l,0)
, N, 0) where
SK
B,(i,0)
R
← Z
∗
N
.
Secret key SK
B, j
= (SK
B,(1, j)
, . . . , SK
B,(l, j)
) for any
time period j is obtained by updating the secret key
SK
B, j−1
= (SK
B,(1, j−1)
, . . . , SK
B,(l, j−1)
) of the previ-
ous time period via the update rule
SK
B,(i, j)
= SK
2
B,(i, j−1)
mod N, (5)
where i = 1, . . . , l.
The public key U
B
= (U
B,1
, . . . ,U
B,l
), is calculated
as the value obtained on updating the base secret se-
cret key T + 1 times:
U
B,i
= SK
2
T +1
B,(i,0)
mod N (6)
4.2 Proxy Generation
Each original signer A
x
generates the proxy informa-
tion in time period j as follows:
Y
x
= R
2
T +1− j
x
mod N
where R
x
R
← Z
∗
N
and x = 1, . . . , n.
P
j,A
x
,in f o
= R
x
.
l
∏
i=1
U
B,i
l
∏
i=1
SK
c
i
A
x
,(i, j)
mod N
where c
1
, . . . , c
l
← H(M
w
,Y, j), H is a collision resis-
tant hash function and M
w
is the message for proxy
signer and the verifier (which may include warrants).
SECRYPT 2008 - International Conference on Security and Cryptography
248
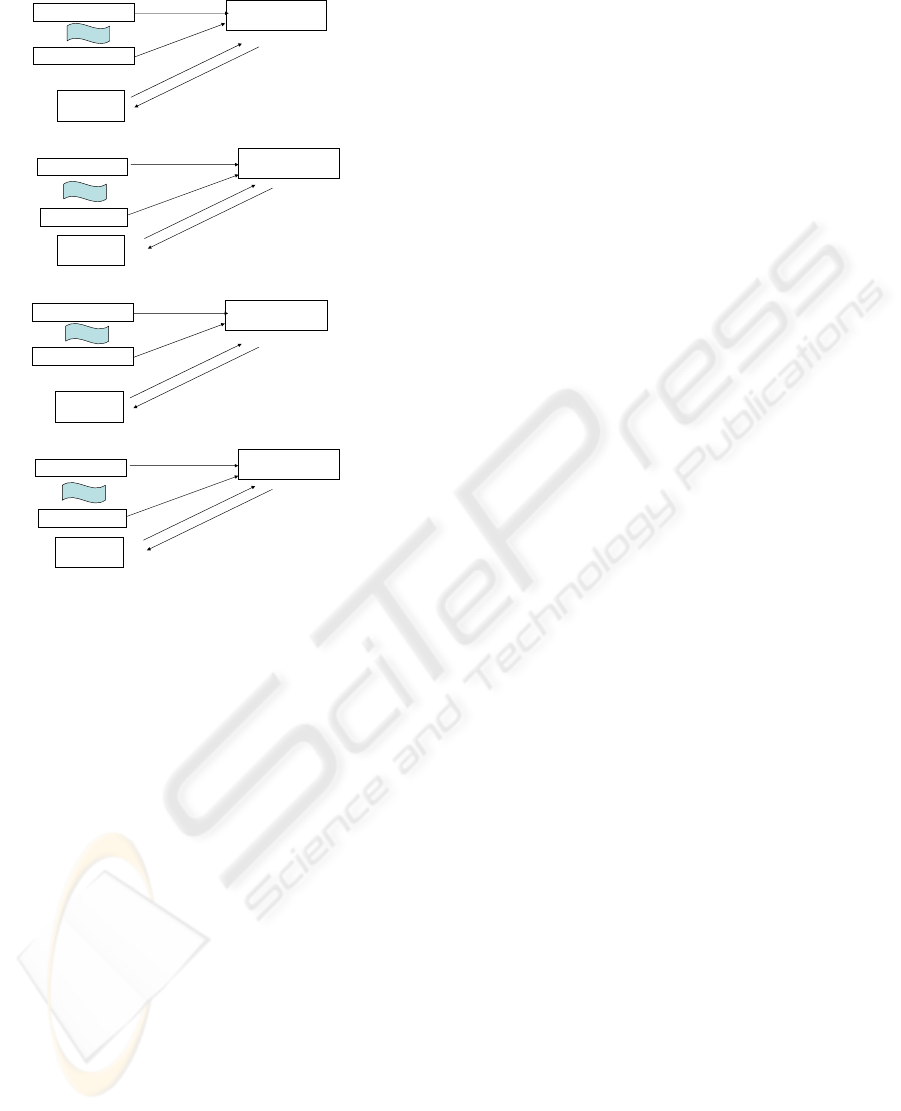
Proxy Signer
Verifier
b) j=1(< T), j’=2
<(Yp,Zp),m,j‘=2, Proxy information)>
Pr
o
x
y
Si
g
n
a
t
u
r
e
Ac
c
ept
e
d
Proxy Signer
Verifier
a) j=1(< T), j’=1
Proxy information
<(Yp,Zp),m,j‘=1,Proxy information)>
P
r
ox
y
Si
gna
t
ur
e
A
c
c
e
p
t
e
d
Original Signer n
Original Signer 1
P
ro
x
y
i
n
f
o
r
m
a
t
i
o
n
Original Signer
Original Signer 1
Proxy information
P
r
o
xy
i
n
fo
r
m
ati
o
n
Proxy Signer
Verifier
d) j=3 (> T) j’=1
<(Yp,Zp),m,j‘=1, Proxy information)>
Pr
o
x
y
Si
g
n
a
t
u
r
e
Re
j
e
ct
e
d
Proxy Signer
Verifier
c) j=2 (<T) j’=1
Proxy information
<(Yp,Zp),m,j‘=1, Proxy information)>
P
r
ox
y
Si
gna
t
ur
e
A
c
c
e
p
t
e
d
Original Signer n
Original Signer 1
P
ro
x
y
i
n
f
o
r
m
a
t
i
o
n
Original Signer
Original Signer 1
Proxy information
P
r
o
xy
i
n
fo
r
m
ati
o
n
Figure 2: Proxy Signature Model for a single proxy signer
with multiple original signers.
4.3 Proxy Delivery
Each original Signer A
x
delegates his/her signing ca-
pability to Bob by giving the following information,
(M
w
,Y
x
, P
j,A
x
,in f o
,U
A
x
,U
B
).
This information also helps to identify the orig-
inal signer and the proxy signer. Once the verifica-
tion of this signature for a given message passes with
the computation of proxy public key, the identity of
the original signer and the proxy signer is confirmed.
Thus the third requirement, Strong identifiability, of a
secure proxy signature is satisfied.
4.4 Proxy Verification
For each original signer Bob checks whether he is the
proxy signer of original signer A
x
by using the follow-
ing equation:
P
2
(T +1− j)
j,A
x
,in f o
= Y
x
.
l
∏
i=1
U
c
i
A
x
,i
.
l
∏
i=1
U
2
(T +1− j)
B,i
mod N (7)
where x = 1, . . . , n.
Notice that since
LHS = (R
x
.
l
∏
i=1
U
B,i
l
∏
i=1
SK
c
i
A
x
,(i, j)
)
2
(T +1− j)
mod N
= R
2
(T +1− j)
x
.(
l
∏
i=1
U
B,i
)
2
(T +1− j)
.(
l
∏
i=1
SK
c
i
Ax,(i, j)
)
2
(T +1− j)
mod N
= Y
x
.(
l
∏
i=1
U
B,i
)
2
(T +1− j)
.(
l
∏
i=1
SK
c
i
.2
j
A
x
,(i,0)
)
2
(T +1− j)
mod N
= Y
x
.(
l
∏
i=1
U
B,i
)
2
(T +1− j)
.(
l
∏
i=1
SK
c
i
A
x
,(i,0)
)
2
(T +1)
mod N
= Y
x
.(
l
∏
i=1
U
B,i
)
2
(T +1− j)
.(
l
∏
i=1
U
c
i
A
x
,i
) mod N
= RHS
Bob accepts the tuple (M
w
,Y
x
, P
j,A
x
,in f o
,U
A
x
,U
B
) as
valid proxy sent by an honest signer.
4.5 Proxy Key Generation
If the above verification is correct, Bob sets his ini-
tial proxy secret key x
p,0
= (x
p,(1,0)
, . . . , x
p,(l,0)
, N, 0)
in any time period j as
x
p,(i,0)
= P
j,A
1
,in fo
. .. P
j,A
n
,in fo
.(U
A
1
,i
. ..U
A
n
,i
).SK
B,(i, j)
mod N (8)
where i = 1, . . . , l.
Proxy secret key x
p, j
0
= (x
p,(1, j
0
)
, . . . , x
p,(l, j
0
)
) for
any time period j
0
is obtained by updating the proxy
secret key x
p, j
0
−1
= (x
p,(1, j
0
−1)
, . . . , x
p,(l, j
0
−1)
) of the
previous time period via the update rule
x
p,(i, j
0
)
= x
2
p,(i, j
0
−1)
mod N, (9)
where i = 1, . . . , l.
The proxy public key is y
p
= (y
p,1
, . . . , y
p,l
), is cal-
culated as the value obtained on updating the initial
proxy secret key T + 1 times:
y
p,i
= x
2
T
0
+1
p,(i,0)
mod N (10)
where T
0
is the number of sub time periods in time
period j. Note that in equation (12) the proxy private
key used to generate the proxy signature is computed
using the private key of the proxy signer and the pub-
lic key of the original signer. This ensures that the
proxy signer is creating a valid proxy signature on be-
half of the original signer. He therefore cannot repudi-
ate his signature. Thus the fourth requirement Strong
undeniability, of a secure proxy signature is satisfied.
4.6 Proxy Signature Generation
The proxy signer uses Bellare-Miner Forward-secure
signature scheme to generate proxy signature on
any message m. The signature in time period j
0
,
FORWARD-SECURE PROXY SIGNATURE AND REVOCATION SCHEME FOR A PROXY SIGNER WITH
MULTIPLE ORIGINAL SIGNERS
249

((Y
p
, Z
p
), m, j, j
0
,U
A
1
, . . . ,U
A
n
, P
j,A
1
,in f o
. . . P
j,A
n
,in f o
, M
w
)
is generated as follows:
The proxy secret key is x
p, j
0
.
Y
p
= R
2
(T +1− j
0
)
p
mod N (11)
where R
p
R
← Z
∗
N
Z
p
= R
p
.
l
∏
i=1
x
c
i
p,(i, j
0
)
mod N (12)
where c
1
, . . . , c
l
← H(m,Y, j
0
) and H is a collision re-
sistant hash function.
The proxy signer will be able to generate proxy
signatures on behalf of the original signers only for T
time periods. After the elapse of this time period, he
is automatically revoked as a proxy signer.
4.7 Proxy Signature Verification
The verifier receives the proxy signature
((Y
p
, Z
p
), m, j, j
0
,U
A
1
, . . . ,U
A
n
, P
j,A
1
,in f o
. . . P
j,A
n
,in f o
, M
w
). He computes the proxy public key
y
p
j
for the j
th
time period as y
p
j
= (y
p,1
, . . . , y
p,l
),
where
y
p,i
= (P
j,A
1
,in f o
. . . P
j,A
n
,in f o
.U
A
1
,i
. . .
U
A
n
,i
)
2
T
0
+1
.U
2
j
B,i
mod N.
LHS = x
2
T
0
+1
p,(i,0)
mod N
= (P
j,A
1
,in f o
. . . P
j,A
n
,in f o
.(U
A
1
,i
. . .U
A
n
,i
).
SK
B,(i, j)
)
2
(T
0
+1)
mod N
= (P
j,A
1
,in f o
. . . P
j,A
n
,in f o
.(U
A
1
,n
. . .
U
A
n
,i
))
2
(T
0
+1)
.(SK
B,(i, j)
)
2
(T
0
+1)
mod N
= (P
j,A
1
,in f o
. . . P
j,A
n
,in f o
.(U
A
1
,i
. . .
U
A
n
,i
))
2
(T
0
+1)
.(SK
B,(i,0)
)
2
j
.2
(T
0
+1)
mod N
= (P
j,A
1
,in f o
. . . P
j,A
n
,in f o
.(U
A
1
,i
. . .
U
A
n
,i
))
2
(T
0
+1)
.(SK
B,(i,0)
)
2
(T
0
+1)
.2
j
mod N
= (P
j,A
1
,in f o
. . . P
j,A
n
,in f o
.(U
A
1
,i
. . .
U
A
n
,i
))
2
(T
0
+1)
.U
2
j
B,i
mod N
= RHS
If the above equation holds then the received
signature is verified as follows:
Z
2
(T
0
+1− j
0
)
p
= Y
p
.
l
∏
i=1
(y
p,i
)
c
i
mod N (13)
Notice that since
LHS = (R
p
.
l
∏
i=1
x
c
i
p,(i, j
0
)
)
2
(T
0
+1− j
0
)
mod N
= R
2
(T +1− j
0
)
p
.(
l
∏
i=1
x
c
i
p,(i, j
0
)
)
2
(T
0
+1− j
0
)
mod N
= Y
p
.
l
∏
i=1
(x
c
i
p,(i,0)
)
2
j
.2
(T
0
+1− j
0
)
mod N
= Y
p
.
l
∏
i=1
(x
c
i
p,(i,0)
)
2
(T
0
+1)
mod N
= Y
p
.
l
∏
i=1
y
c
i
p,i
mod N
= RHS
the signature ((Y
p
, Z
p
), m, j, j
0
,U
A
1
, . . . ,U
A
n
,
P
j,A
1
,in f o
. . . P
j,A
n
,in f o
, M
w
) sent by an honest proxy
signer will be accepted.
If this check passes, the verifier is convinced of the
original signer’s agreement on the signed message as
the public key used to verify the signature is calcu-
lated using the public key and the proxy information
sent by the original signer. Thus the first requirement,
Verifiability, of a secure proxy signature is satisfied.
The verification passes only for the signatures
signed within the time period T . If the proxy signer
tries to sign after the time period T , the signature is
rejected as he is now a revoked signer.
Also, the signature is identified as a proxy signa-
ture and not as an ordinary signature as it is verified
only by the proxy public key (y
p
) and not by the pub-
lic key of the proxy signer (U
B
). Thus the fifth re-
quirement, that a proxy signer cannot create a valid
proxy signature not detected as a proxy signature, of
a secure proxy signature is satisfied.
In Figure 2.a., all the n original signers send the
proxy information to the proxy signer in time period
j = 1. This time period j is divided into T
0
time pe-
riods and in the first time period i.e j
0
= 1, the proxy
signer generates Forward-secure proxy signatures on
message m and sends it along with other information
to verifier. The verifier first computes the proxy pub-
lic key using the available proxy information and later
verifies the validity of the signature. The proxy sig-
nature generated by a honest proxy signer is always
accepted.
In Figure 2.b., in time period j = 1 & j
0
= 2, the
proxy signer generates Forward-secure proxy signa-
ture on message m using the same proxy information
received earlier and sends it to the verifier for accep-
tance. This procedure repeats until j
0
= T
0
after which
j gets incremented by 1.
In Figure 2.c., we observe the communication
SECRYPT 2008 - International Conference on Security and Cryptography
250

among the players of the proxy signature model in
time period j = 2 & j
0
= 1 and in Figure 2.d., we ob-
serve the working of the model in time period j = 3
& j
0
= 1, where j > T . Here the proxy signer is gen-
erating proxy signatures after the time period T . The
verification fails and thus the verifier rejects the proxy
signature.
5 SECURITY OF OUR SCHEME
1. Forgery by the Original Signer: The proxy secret
key is dependent on both the proxy information
sent by the original signer as well as the secret
key of the proxy signer. Therefore the original
signer cannot generate the proxy secret key. He
also cannot derive the proxy secret key from the
proxy public key given by equation (14) as it is
difficult to factorise the Blum William’s integer N
. Thus the original signer is unable to sign like the
proxy signer. Therefore forgery by original signer
is computationally not possible.
2. Impersonating attack: Let us assume that Bob is
not designated as a proxy signer by the original
signer A1. Though Bob can generate a proxy key
pair (x
0
p
, y
0
p
) satisfying equations (12 and 14) and
sign a message on behalf of a original signer, the
verifier on receiving the signatures, can first verify
the proxy information using the public key of A1
and later use it to compute the proxy public key. If
Bob changes the proxy information, the verifica-
tion of proxy information will fail and the verifier
rejects the proxy signature. Thus Bob cannot be-
come the proxy signer unless he is designated by
the original signer Alice.
3. Framing attack: In this attack, a third party Char-
lie forges a proxy private key and then generates
valid proxy signatures such that the verifier be-
lieves that these proxy signatures were signed by
the proxy signer Bob on behalf of the original
signer Alice. When such a proxy signature is pre-
sented, Alice cannot deny that she is the original
signer of the proxy signer Bob. The result is that
Alice and Bob will be framed.
To accomplish this attack, Charlie needs to forge
Bob’s proxy key pair (x
p
, y
p
). As forward-secure
signatures are used by proxy signer it is compu-
tationally difficult to forge the proxy secret key.
Knowing the proxy public key y
p
Charlie can-
not generate the proxy private key given by equa-
tion (14) as it is difficult to factorise the Blum
William’s integer N.
Thus our scheme withstands the above attacks. By
this we can say that only the designated proxy
signer can create a valid proxy signature on be-
half of the original signer. In other words, the
original signer and other third parties who are not
designated as proxy signer cannot create a valid
signature. Thus the second requirement, Strong
unforgeability, of a secure proxy signature is sat-
isfied.
6 CONCLUSIONS
We have considered a scenario where there is need
for a single person to take up the responsibilities of
many persons and work on their behalf. We propose
a forward-secure proxy signature scheme which helps
many original signers to delegate their signing power
to one proxy signer. These forward-Secure proxy sig-
natures guarantee the security of messages signed in
the past even if the proxy signer’s secret key is ex-
posed today. Also, the proxy signer is required to gen-
erate just a single proxy key pair to sign new messages
belonging to any of the original signers. The proxy
signer will be able to generate proxy signatures on
behalf of the original signers only for T time periods.
After the elapse of this time period, he is automati-
cally revoked as a proxy signer. The new scheme pro-
posed is based on the popular forward-secure Bellare-
Miner scheme. The scheme meets the basic require-
ments of a proxy signature scheme and certain addi-
tional properties which make the system more flexible
and secure.
REFERENCES
A. Boldyreva, A. P. and Warinschi, B. (2003). Se-
cure proxy signature schemes for delegation of sign-
ing rights. In Fourth Annual Conference on Com-
puter and Communications Security. Available at
http://eprint.iacr.org/2003/096.
Abdalla, M., R. L. (1997). A new forward-secure digital
signature scheme. In ASIACRYPT 2000. LNCS 1976,
pp. 116-129. Springer-Verlag, (2000),116-129.
Ai-Ibrahim, M. and Cerny, A. (2003). Proxy and thresh-
old one-time signatures. In 11th International Con-
ference Applied Cryptography and Network Security
(ACNS03). LNCS 2846, Springer-Verlag.
Anderson, R. (1997). Invited lecture. In Fourth Annual
Conference on Computer and Communications Secu-
rity. ACM.
B. Lee, H. K. and Kim, K. (2001a). Secure mobile agent
using strong non-designated proxy signature. In Infor-
mation Security and Privacy (ACISP01). LNCS 2119,
pp. 474-486. Springer-Verlag.
FORWARD-SECURE PROXY SIGNATURE AND REVOCATION SCHEME FOR A PROXY SIGNER WITH
MULTIPLE ORIGINAL SIGNERS
251

B. Lee, H. K. and Kim, K. (2001b). Strong proxy signa-
ture and its applications. In 2001 Symposium on Cryp-
tography and Information Security (SCIS01). Vol. 2/2,
pp. 603-608. Oiso, Japan.
Bellare, M., M. S. (1999). A forward-secure digital signa-
ture scheme. In Advances in Cryptology-Crypto 99
proceedings. Lecture notes in Computer Science, Vol.
1666. Springer-Verlag.
Ghodosi, H. and Pieprzyk, J. (1999). Repudiation of
cheating and non-repudiation of zhangs proxy sig-
nature schemes. In Information Security and Pri-
vacy (ACISP99). LNCS 1587, pp. 129-134. Springer-
Verlag.
Guilin Wang, Feng Bao, J. Z. D. R. (2004). Invited lec-
ture. In Proxy signature scheme with multiple original
signers for wireless e-commerce applications. Vehic-
ular Technology Conference, Vol. 5, pp 3249-3253,
IEEE.
Itkis, G., R. L. (2001). Invited lecture. In Forward-
secure signatures with optimal signing and verifying.
CRYPTO’01, LNCS 2139, Springer-Verlag, 332-354.
J.-Y. Lee, J. H. C. and Kim, S. (2003). An analysis of proxy
signatures: Is a secure channel necessary ? In Topics
in Cryptology - CT-RSA 2003. LNCS 2612, pp. 68-79.
Springer-Verlag.
Kozlov, A, R. L. (2002). Forward-secure signatures with
fast key update. In Security in Communication Net-
works (SCN 2002). LNCS 2576, Springer-Verlag,
(2002), (241-256).
Krawczyk, H. (2000). Simple forward-secure signatures
from any signature scheme. In Proc. of the 7th ACM
Conference on Computer and Communications Secu-
rity (CCS 2000). ACM.
M. Mambo, K. Usuda, E. O. (1996). Proxy signatures for
delegating signing operation. In 3rd ACM Conference
on Computer and Communications Security (CCS96).
pp. 48-57. ACM Press.
M. Mambo, K. U. and Okamoto, E. (1996). Invited lecture.
In Proxy signature: Delegation of the power to sign
messages. IEICE Trans. Fundamentals, Vol. E79-A,
No. 9, pp. 1338-1353.
N.-Y. Lee, T. H. and Wang, C.-H. (1998). Nonrepudia-
ble proxy signature schemes. In Information Security
and Privacy (ACISP98). LNCS 1438, pp. 415-422.
Springer-Verlag.
Park and Lee, I.-Y. (2001). A digital nominative proxy
signature scheme for mobile communications. In In-
formation and Communications Security (ICICS01).
LNCS 2229, pp. 451-455. Springer- Verlag.
S. Kim, S. P. and Won., D. (1997). Proxy signatures, re-
visited. In Information and Communications Secu-
rity (ICICS97). LNCS 1334, pp. 223-232. Springer-
Verlag.
T. Okamoto, M. T. and Okamoto, E. (1999). Extended
proxy signatures for smart cards. In Information Se-
curity Workshop (ISW99). LNCS 1729, pp. 247-258.
Springer-Verlag.
Wang, H. and Pieprzyk., J. (2003). Efficient one-time proxy
signatures. In Asiacrypt03. Springer-Verlag.
Zhang, K. (1997). Nonrepudiable proxy signature
schemes. In Manuscript, 1997. Available at
http://citeseer.nj.nec.com/360090.html.
Zhang., K. (1997). Threshold proxy signature schemes. In
Information Security Workshop (ISW97). LNCS 1396,
pp. 282-290. Springer-Verlag.
Zhen Chuan Chai, Z. C. (2004). Factoring-based proxy
signature schemes with forward-security. In First In-
ternational Symposium on Computational and Infor-
mation Science. LNCS 3314, pp 1034-1040, Springer
Verlag.
SECRYPT 2008 - International Conference on Security and Cryptography
252
