
EFFICIENT IBE-PKE PROXY RE-ENCRYPTION
Takeo Mizuno
1,2
and Hiroshi Doi
2
1
NTT Data Corporation, 3-3-3 Toyosu, Koutou-ku, Tokyo, Japan
2
Institute of Information Security, 2-14-1 Tsuruya-cho, Kanagawa-ku, Yokohama-shi, Kanagawa, Japan
Keywords:
Proxy re-encryption, public key encryption, identity-based encryption, bilinear maps.
Abstract:
In proxy re-encryption schemes, a semi-trusted entity called proxy can convert a ciphertext encrypted for
Alice into a new ciphertext for Bob without seeing the underlying plaintext. Several proxy re-encryption
schemes have been proposed, however, only one scheme which enables the conversion of IBE ciphertexts to
PKE ciphertexts has been proposed and it has some drawbacks. In that scheme, the size of the re-encrypted
ciphertext increases and Bob must be aware of existence of the proxy, which means Bob cannot decrypt a
re-encrypted ciphertext with same PKE decryption algorithm.
We propose a new, efficient scheme that enables the conversion of IBE ciphertexts to PKE ciphertexts, and
prove CPA security in the standard model. In our scheme, the size of the re-encrypted ciphertext is optimal
and Bob does not aware of existence of the proxy. As far as we knows, this is the first IBE-PKE type scheme
that holds the above properties.
1 INTRODUCTION
In proxy re-encryption schemes, a semi-trusted entity
called proxy can convert a ciphertext encrypted for
Alice into a new ciphertext, which another user Bob
can decrypt with his own secret information without
revealing the underlying plaintext. The proxy is not
fully trusted, i.e., the proxy cannot reveal Alice’s or
Bob’s secret key, and can not learn the plaintext dur-
ing the conversion.
There are many useful applications of these
schemes. For instance, Alice can securely forward
encrypted e-mails to Bob in her absence.
The proxy converts the messages which encrypted
under the email address alice@foo.com into another
ciphertexts encrypted under bob@foo.com. The
proxy does not learn the content of the messages dur-
ing conversion and Alice can forward message with-
out revealing her secret key.
Several proxy re-encryption schemes have been
proposed in the context of public key encryption
(PKE), e.g., ElGamal or RSA. Other schemes have
been proposed in the context of Identity Based En-
cryption (IBE) which the sender encrypts a plaintext
using arbitral strings that represents the recipient’s
identity as the public key. The IBE has proven useful
in solving public key-distribution issues of traditional
certificate based PKE schemes.
Matsuo proposed two proxy re-encryption
schemes. The former one enables conversion
between IBE users and the latter one enable the
conversion of PKE ciphertexts to IBE ciphertexts in
(T.Matsuo, 2007).
The latter one called hybrid scheme can be useful
in PKE and IBE mixed environments. Matsuo also
classify proxy re-encryption schemes as follows:
[PKE-PKE]-Type Scheme. Proxy converts PKE ci-
phertexts to PKE ciphertexts.(M.Mambo and
E.Okamoto, 1997), (M.Blaze et al., 1998),
(M.Jakobsson, 1999), (Y.Dodis and A.Ivan,
2003), (L.Zbou et al., 2004), (G.Ateniese et al.,
2005), and (R.Canetti and S.Hohenberger, 2007)
have been proposed as this type.
[IBE-IBE]-Type Scheme. Proxy converts IBE ci-
phertexts to IBE ciphertexts. (Y.Dodis and
A.Ivan, 2003), (T.Matsuo, 2007), and (M.Green
and G.Ateniese, 2007) have been proposed as this
type.
[PKE-IBE]-Type Scheme. Proxy converts PKE ci-
phertexts to IBE ciphertexts. (T.Matsuo, 2007)
has been proposed as this type.
[IBE-PKE]-Type Scheme. Proxy converts IBE ci-
phertexts to PKE ciphertexts. (M.Green and
285
Mizuno T. and Doi H. (2008).
EFFICIENT IBE-PKE PROXY RE-ENCRYPTION.
In Proceedings of the Inter national Conference on Security and Cryptography, pages 285-293
DOI: 10.5220/0001917802850293
Copyright
c
SciTePress
G.Ateniese, 2007) has been proposed as this type.
Green and Ateniese proposed the [IBE-PKE]-type
scheme in (M.Green and G.Ateniese, 2007); however
their scheme has following drawbacks.
1. The size of the re-encrypted ciphertext increases
as compared to that of the original ciphertext.
2. The decryption algorithm of the re-encrypted ci-
phertext is different from the original decryption
of the PKE scheme.
[IBE-IBE] type and [PKE-PKE] type of proxy
re-encryption schemes have been proposed without
such drawbacks. One of the theoretical interests is
to construct the [IBE-PKE]-type proxy re-encryption
scheme which does not have such drawbacks.
1.1 Entities of Proxy Re-Encryption
Generally, proxy re-encryption schemes have the fol-
lowing entities.
Sender. This entity encrypts plaintexts using a dele-
gator’s public key.
Delegator. This entity possesses the secret key cor-
responding to the public key used by the sender,
and delegates decryption rights.
Delegatee. The decryption rights delegates to this en-
tity from the delegator. The delegatee can decrypt
re-encrypted ciphertexts own secret key, and with-
out the delegator’s secret key.
Proxy. This semi-trusted entity re-encrypts cipher-
texts with a re-encryption keys, and outputs the
ciphertexts, which the delegatee can decrypt us-
ing his own secret key without revealing underly-
ing the plaintexts.
In [IBE-IBE], [IBE-PKE] and [PKE-IBE] type
schemes have an additional entity PKG (Private Key
Generator), which generates IBE secret keys. In our
schemes this trusted entity take a part of re-encryption
key generation.
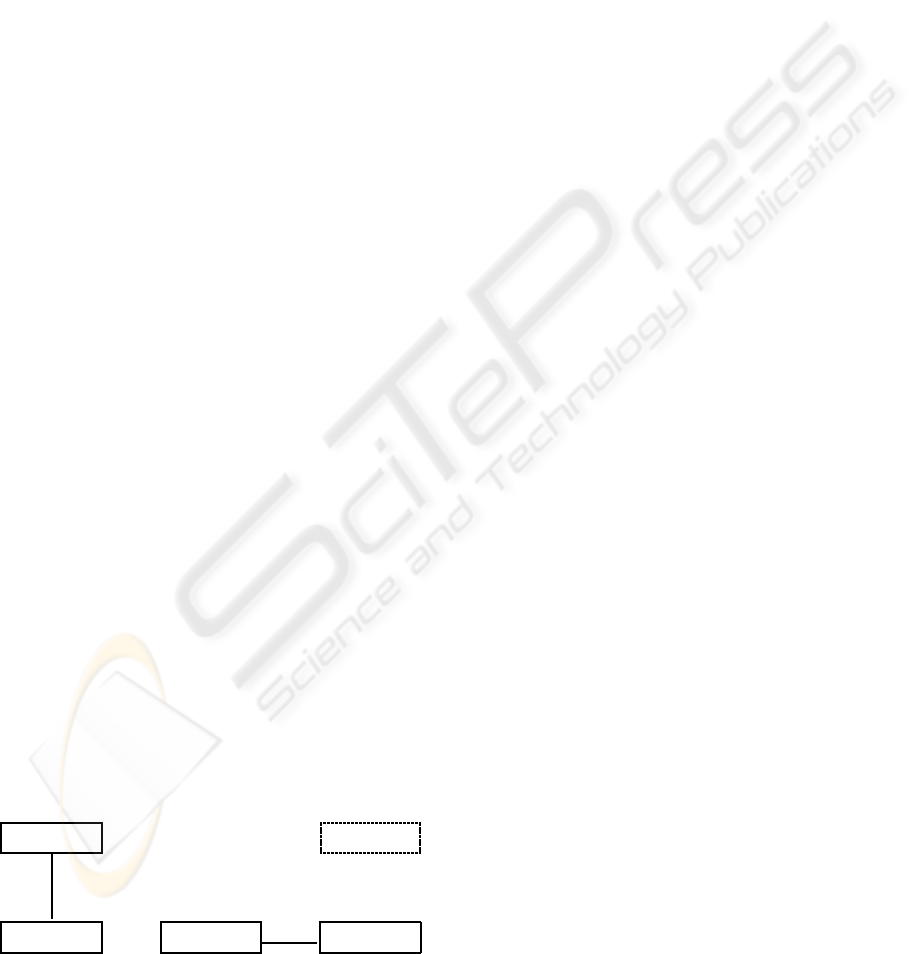
Sender
Delegator Proxy Delegatee
PKG
?
H
H
H
H
H
H
Hj
-
9
encrypts
decrypts re-encrypts decrypts
Figure 1: Entities of proxy re-encryption.
1.2 Security of Proxy Re-Encryption
With regard to the security of proxy re-encryption
schemes Green and Ateniese pointed out the previ-
ous schemes achieve a security only for chosen plain-
text attacks (CPA), and also proposed a new scheme
achieves chosen ciphertext attacks (CCA) security in
(M.Green and G.Ateniese, 2007).
Green and Ateniese described that in the previous
schemes, proxy cannot verify ciphertexts and grant
adversaries invalid re-encryption. Hence, malicious
delegatee can use a re-encryption oracle as a decryp-
tion oracle. Furthermore they proposed CCA-secure
scheme with random oracle model using Canetti,
Halevi and Kats (CHK) (R.Canetti et al., 2004) tech-
nique, which enables the proxy to validate cipher-
texts.
After Green and Ateniese pointed out the se-
curity problems with the previous schemes, Canetti
and Hohenberger proposed CCA-secure [PKE-PKE]-
type Re-Encryption scheme in the standard model
(R.Canetti and S.Hohenberger, 2007).
In this paper, we propose a new [IBE-PKE]-type
scheme, which achieves CPA-security only. How-
ever it might be possible achieve CCA-security us-
ing Green and Ateniese technique in (M.Green and
G.Ateniese, 2007).
1.3 Our Contribution
We propose the first [IBE-PKE]-type proxy re-
encryption scheme, which holds the following advan-
tages simultaneously.
• Our scheme achieves optimal ciphetext size. The
size of a re-encrypted ciphertext is same as a
PKE ciphertext, while (M.Green and G.Ateniese,
2007) [IBE-PKE]-type scheme requires addi-
tional elements of ciphertext to support re-
encryption.
• Our scheme achives proxy invisibility which
means delegatee does not require additional algo-
rithm for decryption of a re-encrypted ciphertext.
The delegatee can decrypt ciphertexts without be-
ing aware of the existence of the proxy, while it is
required in (M.Green and G.Ateniese, 2007).
• Our scheme is selective-ID secure in the standard
model, while previous [IBE-PKE]-type scheme in
(M.Green and G.Ateniese, 2007) might be full-ID
secure in the random oracle model. Furthermore
our scheme might be possible to extend full-ID
secure using IBE proposed in (B.Waters, 2005).
• In Our scheme the PKG generates re-encryption
keys, while (M.Green and G.Ateniese, 2007) del-
SECRYPT 2008 - International Conference on Security and Cryptography
286

egator generates re-encryption keys himself indi-
vidually. However this property should not af-
fect security of our scheme, because the PKG is
a trusted entity in the IBE schemes, and does not
generate re-encryption key without notifying the
delegator.
1.4 Organisation
The rest of paper consists of 4 sections. In Sec. 2
gives some definitions and preliminaries. In Sec. 3 we
define security of IBE-PKE type proxy re-encryption.
In Sec. 4 we present the IBE-PKE type proxy re-
encryption scheme, and finally conclude this study in
Sec. 5.
2 PRELIMINARIES
In this section, We describe the settings and computa-
tional assumptions used in this paper. We then define
an [IBE-PKE]-type proxy re-encryption scheme and
its security.
2.1 Bilinear Groups
Let G and G
1
be the two multiplicative cyclic groups
of prime order p, and g be a generator of G. We say
that G
1
has an admissible bilinear map ˆe : G × G →
G
1
if the following conditions hold.
1. ˆe(g
a
,g
b
) = ˆe(g,g)
ab
for all a,b
2. ˆe(g,g) 6= 1
We say that G is a bilinear group if the group ac-
tion in G can be computed efficiently and there ex-
ists a group G
1
and an efficiently computable bilinear
map ˆe as above.
2.2 Decisional Bilinear Diffie-Hellman
Assumption (dBDH)
The dBDH problem (D.Boneh and X.Boyen, 2004) in
G as follows: Let G be a bilinear group of prime order
p with an efficiently computable pairing ˆe : G × G →
G
1
, let g be a random generator of G. The dBDH
problem is to decide, given a tuple g,g
a
,g
b
,g
c
,T ∈
G
4
× G
1
as inputs, (where a,b,c∈
R
Z
∗
p
), whether T =
ˆe(g,g)
abc
or if T is a random element of G
1
.
Let k be a security parameter of suffcient size, we
define the advantage of an algorithm A as follows:
Adv
dBDH
A
= | Pr[A (g,g
a
,g
b
,g
c
, ˆe(g,g)
abc
) = 0] −
Pr[A (g,g
a
,g
b
,g
c
,T) = 0]|
where the probability is taken over the random choice
of the generator g,the random choice of a, b, c in Z
∗
p
,
the random choice of T in G
1
, and the random bits
consumed by A . We say that (k,t,ε)-dBDH assump-
tion holds in G if no t-time algorithm has advantage
Adv
dBDH
A
< ε G under security parameter k.
2.3 Identity Based Encryption Scheme
Identity Based Encryption (IBE) consists of the fol-
lowing algorithm.
SetUp
IBE
(k). Given a security parameter k as in-
put, a trusted entity Private Key Generator (PKG)
generates a master key mk and public parameters
params, and outputs mk and params.
KeyGen
IBE
(mk,params,ID). For inputs of a mas-
ter key mk, public parameters params, and an
identity ID, the PKG outputsa IBE secret key sk
ID
corresponding to the identity.
Enc
IBE
(ID,params,M). For inputs of an identity
ID, public parameters params, and a plaintext M,
computes an IBE ciphertext C
IBE
Dec
IBE
(sk
ID
,params,C
IBE
). For inputs of a IBE se-
cret key sk
ID
, public parameters params, and an
IBE ciphertextC
IBE
, decrypts and outputs a plain-
text M.
2.4 Public Key Encryption Scheme
Public Key Encryption (PKE) consists from following
algorithms.
KeyGen
PKE
(k,params). Given a security parameter
k and IBE public parameters params as input, out-
puts PKE key pair hSK,PKi where SK is a secret
key, PK is the corresponding public key PK.
Enc
PKE
(PK,M,params). For inputs of a public key
PK and plaintext M, IBE public parameters
params, outputs the PKE ciphertext C
PKE
.
Dec
PKE
(SK,C
PKE
,params). For inputs a secret key
sk, PKE ciphertext C
PKE
, and IBE public para
metes params, decrypts and outputs a plaintext M.
2.5 IBE-PKE Proxy Re-Encryption
Scheme
[IBE-PKE]-type proxy re-encryption (IBE-PKE-
PRE) consists of the following algorithm
KeyGen
PRO
(mk,ID,PK,PK
R
,params). For inputs
of a master key mk, a delegator’s identity ID, del-
egatee’s PKE public key PK and public key for
Re-Encryption PK
R
, and IBE public parameters
EFFICIENT IBE-PKE PROXY RE-ENCRYPTION
287

Table 1: comparison of [IBE-PKE] type scheme.
Property (M.Green and G.Ateniese, 2007) This work
Optimal size of re-encrypted ciphertext No Yes
Proxy Invisible No Yes
Re-encryption key generator Delegator PKG
params, a re-encrypt key rk
ID→PKE
is output to
the proxy.
ReEnc
PRO
(ID,rk
ID→PKE
,params,C
IBE
). For in-
puts of a delegator’s identity ID, a re-encrypt key
rk
ID→PKE
, IBE public parameters params, and a
IBE ciphertext C
IBE
, the proxy re-encrypts and
outputs a PKE ciphertext C
PKE
to the delegatee.
3 CHOSEN PLAINTEXT
SECURITY FOR IBE-PKE
PROXY RE-ENCRYPTION
We define chosen plaintext security for the [IBE-
PKE]-type scheme according to the following game
between an adversary A and a challenger C . We de-
fine two types of attacks, an adversary attacks against
the IBE scheme and another against the PKE scheme.
Hence, in the following game, we define an adversary
attacks against the IBE scheme as (TYPE = IBE) and
an adversary attacks against the PKE as (TYPE =
PKE).
We design the following game on the basis of
Boneh and Boyen’s selective ID secure IBE game
(D.Boneh and X.Boyen, 2004) and Green and Ate-
niese’s proxy re-encryption game (M.Green and
G.Ateniese, 2007). We show even if an adversary
obtains additional informations related to proxy re-
encryption, such as re-encryption keys, it does not
make the underlying IBE or PKE schemes weak.
In the following game, the adversary is allowed to
adaptively conduct IBE secret key queries, PKE se-
cret key queries and re-encryption key queries. These
queries imply the following situation that: The ad-
versary corrupts IBE users to obtain their IBE secret
keys, corrupts PKE users to obtain their PKE secret
keys and corrupts the proxy to obtain re-encryption
keys. We classify PKE users under two party, hon-
est party and corrupted party by adversary. The ad-
versary can obtain a PKE secret key of a corrupted
party, but restricted to get re-encryption keys which
can convert an IBE ciphertext corresponding to target
identity to a PKE ciphertext for the corrupted party,
because the adversary obviously wins the game. The
adversary also restricted to obtain a PKE secret key
of a honest party, but does not restricted to get re-
encryption keys which can convert an IBE ciphertext
to a PKE ciphertext for the honest party.
Definition 3.1. (Security of [IBE-PKE]-type proxy
re-encryption) Let S be an IBE-PKE-PRE scheme de-
fined as a tuple of algorithms (Setup
IBE
, KeyGen
IBE
,
Enc
IBE
, Dec
IBE
, KeyGen
PKE
, Enc
PKE
, Dec
PKE
,
KeyGen
PRO
, ReEnc
PRO
). The security is defined
according to the following game, where TYPE ∈
{IBE, PKE}.
Initialization. If the adversary A is (TYPE = IBE),
A outputs a target identity ID
∗
.
SetUp. The challenger C generates params,mk by
running SetUp
IBE
. C also generates PKE keys
PKE
j
,PK
j
,PK
R
j
,SK
j
where PKE
j
is a PKE
user identity ,PK
j
and SK
j
are PKE key pairs,
PK
R
j
is a public key for re-encryptioncorrespond-
ing to PKE
j
, C placed them in lists:
PPKL (PKE Public Key List) Holds PKE user identi-
ties PKE
j
, PKE public keys PK
j
and PKE pub-
lic keys for re-encryption PK
R
j
.
PSKL (PKE Secret Key List) Holds PKE user iden-
tities PKE
j
, PKE secret keys SK
j
and mark
which holds a flag that PKE user is a honest
party or corrupted party by A .
Then, C gives hparams, PPKLi to A , and keep
hmk, PSKLi secret to it self.
Phase 1. Given hparams, PPKLi, A adaptively
queries C . C responds as follows:
Extract
IBE
(ID
i
). A queries the IBE user’s secret
key sk
ID
i
with an identity ID
i
where ID
i
6= ID
∗
.
C responds sk
ID
i
corresponding to ID
i
to A .
Extract
IBE→PKE
(ID
i
,PKE
j
). A queries the re-
encryption key rk
ID
i
→PKE
j
with an identity ID
i
and a PKE user identity PKE
j
. C responds
rk
ID
i
→PKE
j
corresponding to ID
i
and PKE
j
to
A .
Extract
PKE
(PKE
j
). A queries the PKE secret
key SK
j
with a PKE user identity PKE
j
. C re-
sponds SK
j
corresponding to PKE
j
to A .
Challenge. After Phase 1 , A outputs two equal
length plaintexts M
0
,M
1
and sends them to C . C
picks b ∈
R
{0,1} and encrypts M
b
.
If (TYPE = IBE), C encrypts M under an identity
ID
∗
and responds C
∗
IBE
to A .
SECRYPT 2008 - International Conference on Security and Cryptography
288

If (TYPE = PKE), A selects a target PKE user
identity PKE
∗
from honest parties, and also sends
it to C . C encrypt M under an PKE user identity
PKE
∗
and responds C
∗
PKE
to A .
Phase 2. A continues with the queries as in Phase 1,
and C responds as before.
Solve. Finally A outputs a guess result b
′
∈ {0,1}.
The adversary A wins if b
′
= b.
Besides the abovegame, during Phase 1 and Phase
2, A restricts the following queries which A can de-
crypt a challenge ciphertext only using C ’s answers.
If (TYPE = IBE), the following queries are re-
stricted.
• Extract
IBE
(ID
∗
), where ID
∗
is the challenge
identity.
• Extract
PKE
(PKE
j
), where PKE
j
is a honest
party’s identity.
• Extract
IBE→PKE
(ID
∗
,PKE
j
), where ID
∗
is the
challenge identity and PKE
j
is a corrupted party’s
PKE user identity.
If (TYPE = PKE), the following queries are re-
stricted.
• Extract
PKE
(PKE
j
), where PKE
j
is a honest
party’s PKE user identity.
Definition 3.2. Let A be an adversary against IBE-
PKE-PRE. Define the IND-sPr-CPA advantage of A
as follows:
Adv
S
A
(k) = 2(Pr[b = b
′
] − 1/2).
We say that the IBE-PKE-PRE scheme is (k,t,q,ε)
adaptive chosen plaintext secure if for any t-time ad-
versary A that makes at most q chosen queries under
a security parameter k, we have that Adv
S
A
(k) < ε.
4 EFFICIENT IBE-PKE TYPE
PROXY RE-ENCRYPTION
We construct an [IBE-PKE]-type proxy re-encryption
scheme (IBE-PKE-PRE) which achieves CPA-secure
without Random Oracle.
IBE-PKE-PRE is enable conversion of an IBE ci-
phertext to a PKE ciphertext. Our scheme IBE-PKE-
PRE uses Boneh and Boyen’s selective ID secure IBE
scheme (D.Boneh and X.Boyen, 2004) (BB-IBE) for
IBE scheme. We construct a new (but very similar to
PKE scheme proposed in (G.Ateniese et al., 2005))
ElGamal-type PKE scheme for IBE-PKE-PRE and
propose a re-encryption scheme that converts a BB-
IBE ciphertext to this PKE scheme’s ciphertext.
4.1 BB-IBE Scheme
SetUp
IBE
(k). Given security parameter k as input,
let G,G
1
be a bilinear group of prime order p.
Let ˆe : G × G → G
1
be the bilinear map. Select
a random generator g ∈ G and random elements
h,g
2
∈ G. Pick a random element α ∈ Z
∗
p
and set
g
1
= g
α
,mk = α and set params = hg,g
1
,g
2
,hi.
Let mk be a master secret key, and params be the
public parameters.
KeyGen
IBE
(mk,params,ID). Given master secret
key mk = α, public parameters params and an
identity ID as input, the PKG picks a random ele-
ment u ∈ Z
∗
p
and outputs an IBE secret key sk
ID
.
sk
ID
= hd
1
,d
2
i = hg
α
2
g
ID
1
h
u
,g
u
i
Enc
IBE
(ID,params,M). Given an identity ID, pub-
lic parameter params and plaintext M ∈ G
1
as in-
put, select a random element r ∈ Z
∗
p
and output an
IBE ciphertext C
IBE
.
C
IBE
= hC
1
,C
2
,C
3
i =
D
g
r
,
g
ID
1
h
r
,M ˆe(g
1
,g
2
)
r
E
Dec
IBE
(sk
ID
,params,C
IBE
). Given an IBE secret
key sk
ID
, public parameters params and an IBE
ciphertext C
IBE
as input, output a plaintext M.
M =
C
3
ˆe(d
2
,C
2
)
ˆe(d
1
,C
1
)
4.2 PKE Scheme
KeyGen
PKE
(k,params). Given security parameter k
and BB-IBE public parameters params as input,
select a random element x ∈
R
Z
∗
p
and set SK = x,
PK = g
x
, output SK as a PKE secret key and PK
as a PKE public key.
If PKE user accepts delegation, PKE user also
publish public key for re-encryption PK
R
= g
1/SK
2
.
If PKE user does not wish to accept delegation,
PKE user does not publish public key for re-
encryption value.
Enc
PKE
(PK,M,params). Given a PKE public key
PK, a plaintext M ∈ G
1
and BB-IBE public pa-
rameters params as input, pick a random ele-
ment v ∈ Z
∗
p
and output a PKE ciphertextC
PKE
=
hX,Yi.
C
PKE
= hX,Yi = h ˆe(g,g)
v
,M · ˆe(g,PK)
v
i
EFFICIENT IBE-PKE PROXY RE-ENCRYPTION
289

Dec
PKE
(SK,C
PKE
,params). Given a PKE secret
key SK, a PKE ciphertextC
PKE
and BB-IBE pub-
lic parameters params as input, output a plaintext
M.
M = Y/X
SK
4.3 Proxy Re-Encryption
KeyGen
PRO
(mk,ID,PK,PK
R
,params). Given a
master secret key mk = α, a delegator’s identity
ID and a delegatee’s PKE public key PK and
public key for re-encryption PK
R
as input, PKG
outputs a re-encryption key rk
ID→PK
= hrk
1
,rk
2
i
or ⊥.
1. If ˆe(PK,PK
R
) 6= ˆe(g
2
,g), then output ⊥ and
halt.
2. Compute rk
ID→PK
and output it.
rk
ID→PK
= hrk
1
,rk
2
i =
D
PK
α
R
g
ID
1
h
t
,PK
t
E
ReEnc
PRO
(ID,rk
ID→PKE
,params,C
IBE
). Given a
delegator’s identity ID, a re-encryption key
rk
ID→PK
= hrk
1
,rk
2
i, BB-IBE public parameter
params and an IBE ciphertext C
IBE
as input, the
proxy re-encrypts and outputs a PKE ciphertext
C
PKE
or ⊥.
1. Extract C
IBE
= hC
1
,C
2
,C
3
i
2. Compute v
1
= ˆe(C
1
,g
ID
1
h),v
2
= ˆe(C
2
,g). If
v
1
6= v
2
then output ⊥ and halt. Note that, cor-
rect input values can transform as follow:
ˆe(C
1
,g
ID
1
h) = ˆe(g
r
,g
ID
1
h) = ˆe(C
2
,g)
3. Compute C
PKE
and output it.
¯
C
PKE
= h
¯
X,
¯
Yi = h ˆe(rk
1
,C
1
),C
3
· ˆe(rk
2
,C
2
)i
The delegatee can decrypt this re-encrypt
result
¯
C
PKE
using his own secret key
SK with same PKE decryption algorithm
Dec
PKE
(SK,C
PKE
,params).
4.4 Security of IBE-PKE-PRE
Theorem 4.1. Suppose that the (k,t,ε)-dBDH as-
sumption holds in (G,G
1
). Then, the IBE-PKE-
PRE is (k,t
′
,q,ε)-IND-sPr-CPA secure against a
(TYPE = IBE) adversary for any (q, k,ε) and t
′
<
t − Θ(τq), where τ denotes a maximum time for expo-
nentiation in G,G
1
.
Proof. Let A
IBE
be a t-time (TYPE = IBE) adver-
sary against the IBE-PKE-PRE. We construct an ad-
versary B
IBE
which can solve the dBDH problem
in G by using A
IBE
. The B
IBE
is given an in-
put hg,Γ
1
,Γ
2
,Γ
3
,Ti =
g,g
a
,g
b
,g
c
,T
, and distin-
guishes T is ˆe(g,g)
abc
or T ∈
R
G
1
. B
IBE
works as
follows:
Initialisation. A
IBE
outputs an identity ID
∗
and noti-
fies B
IBE
. B
IBE
generates four blank lists to write
down a query and answer pairs for every queries.
ISKL (IBE Secret Key List): Record the tuple
hID
i
,sk
ID
i
i, where ID
i
is an identity and an IBE
secret key sk
ID
i
corresponding to ID
i
.
PPKL (PKE Public Key List): Record the tuple
PKE
j
,PK
j
,PK
R
j
,
, where PKE
j
is a PKE
user identity and PK
j
and PK
R
j
are a public key
and public key for re-encryption corresponding
to PKE user identity PKE
j
.
PSKL (PKE Secret Key List): Record the tuple
PKE
j
,SK
j
,mark
, where PKE
j
is a PKE user
identity, SK
j
are PKE secret key corresponding
to PKE user identity PKE
j
and mark keeps a
flag that PKE user PKE
j
is a honest party or
corrupted party by A
IBE
.
REKL (Re-Encryption Key List): Record the tu-
ple
ID
i
,PKE
j
,rk
ID
i
→PKE
j
,t
i, j
, where ID
i
is
an identity, PKE
j
is a PKE user identity,
rk
ID
i
→PKE
j
is a re-encryption key converts IBE
ciphertext to PKE ciphertext andt
i, j
is a random
number used for generating a re-encryption
key.
Setup. The B
IBE
generates a random number z ∈
R
Z
∗
p
and sets g
1
= Γ
1
, g
2
= Γ
2
, h = g
−ID
∗
1
g
z
. B
IBE
pro-
vides public parameters params = hg,g
1
,g
2
,hi to
A
IBE
. Under these conditions, the master key
value is g
ab
which B
IBE
cannot compute.
B
IBE
generates random numbers x
j
∈
R
Z
∗
p
(0 ≤
j ≤ l) where l denotes the number of PKE users,
and sets the PKE public key and secret key as fol-
lows:
• If the PKE user PKE
j
is a corrupted party
by A
IBE
, sets the PKE public key as PK
j
=
g
x
j
, the PKE public key for re-encryption as
PK
R
j
= Γ
1/x
j
2
and the secret key as SK
j
= x
j
.
B
IBE
stores
PKE
j
,PK
j
,PK
R
j
,SK
j
to PPKL
and PSKL, and sets the mark as corrupted.
• If the PKE user PKE
j
is a honest party, sets the
PKE public key as PK
j
= Γ
x
j
2
, the PKE public
key for re-encryption as PK
R
j
= g
1/x
j
.
Under this condition, PKE secret key value is
SK
j
= bx
j
where B
IBE
cannot compute, how-
ever B
IBE
can reject the query of this value.
B
IBE
stores the secret key as SK
j
= x
j
as a sub-
stitute for computing re-encryption key values.
SECRYPT 2008 - International Conference on Security and Cryptography
290

B
IBE
stores
PKE
j
,PK
j
,PK
R
j
,SK
j
to PPKL
and PSKL and sets the mark as honest.
B
IBE
gives PPKL to A
IBE
.
Phase 1. A
IBE
adaptively queries B
IBE
, and B
IBE
re-
sponds as follows:
Extract(ID
i
). A
IBE
queries the IBE user’s secret
key sk
ID
i
with an identity ID
i
, then B
IBE
gener-
ates a random number u
i
∈
R
Z
∗
p
and computes
sk
ID
i
.
If ID
i
= ID
∗
, B
IBE
rejects the query. Otherwise,
B
IBE
computes sk
ID
i
= hd
1
,d
2
i as follows:
d
1
= g
2
−z
(ID
i
−ID
∗
)
g
(ID
i
−ID
∗
)
1
g
z
u
i
,
d
2
= g
2
−1
(ID
i
−ID
∗
)
g
u
i
.
B
IBE
writes a request and a response to ISKL
and answers sk
ID
i
to A
IBE
.
Extract
PKE
(PKE
j
). A
IBE
queries the PKE user’s
secret key SK
j
with a PKE user’s identity
PKE
j
, then B
IBE
searches the PSKL to retrieve
PKE user’s secret key SK
j
If PKE
j
marked as honest, then B
IBE
. rejects,
otherwise (PKE
j
marked as corrupted) B
IBE
answers SK
j
retrieved from PSKL.
Extract
IBE→PKE
(ID
i
,PKE
j
). A
IBE
queries the
re-encryption key rk
ID
i
→PKE
j
which can con-
verts ciphertexts from an identity ID
i
to PKE
j
,
then B
IBE
searches PSKL to retrieve PKE
j
record.
1. If ID
i
= ID
∗
and PKE
j
marked as corrupted,
then B
IBE
rejects.
2. If ID
i
= ID
∗
and PKE
j
is a honest party, then
B
IBE
generates random number t
∗, j
∈
R
Z
∗
p
and
computes rk
honest
ID
∗
→PKE
j
= hrk
∗
1
,rk
∗
2
i as follows:
rk
∗
1
= g
1
1/SK
j
(g
z
)
t
i, j
,
rk
∗
2
= g
2
t
i, j
SK
j
.
3. If ID
i
6= ID
∗
and PKE
j
marked as corrupted,
B
IBE
generates random number t
i, j
∈
R
Z
∗
p
and
computes rk
corrupted
ID
i
→PKE
j
= hrk
c
1
,rk
c
2
i as follows:
rk
c
1
= g
2
−z
SK
j
(ID
i
−ID∗)
g
(ID
i
−ID∗)
1
g
z
t
i, j
,
rk
c
2
= g
2
−1
ID
i
−ID∗
g
t
i, j
SK
j
.
4. If ID
i
6= ID
∗
and PKE
j
marked as honest, then
B
IBE
generates random number t
i, j
∈
R
Z
∗
p
and
computes rk
honest
ID
i
→PKE
j
=
rk
h
1
,rk
h
2
as follows:
rk
h
1
= g
−z
SK
j
(ID
i
−ID∗)
g
ID
i
−ID∗
1
g
z
t
i, j
,
rk
h
2
= g
2
−1
ID
i
−ID∗
g
2
t
i, j
SK
j
.
B
IBE
writes a request and a response pair to
REKL, and answers rk
ID
i
→PKE
j
to A
IBE
.
Challenge. A
IBE
outputs two equal length plaintexts
M
0
,M
1
and sends them to B
IBE
. B
IBE
selects
d(∈
R
{0,1}) and encrypts M
d
. B
IBE
computes an
IBE ciphertext C
∗
IBE
as follows:
C
∗
IBE
= hC
∗
1
,C
∗
2
,C
∗
3
i = hΓ
3
,(Γ
3
)
z
,M
d
· Ti
B
IBE
sends C
∗
IBE
to A
IBE
. Note that, if T =
ˆe(g,g)
abc
, C
∗
IBE
is a correct IBE ciphertext of M
d
under an identity ID
∗
.
Phase 2. B
IBE
answers A
IBE
’s queries in same man-
ner of Phase 1.
Solve. Finally, A
IBE
outputs a guess result d
′
∈
{0,1}. If d
′
= d, then B
IBE
judges T = ˆe(g,g)
abc
and outputs 1; otherwise, B
IBE
judges T ∈
R
G
1
and outputs 0.
We claim that in the above simulation answers of
B
IBE
are correctly distributed, and A
IBE
cannot distin-
guish our simulation from the real-world interaction.
Furthermore, Adv
dBDH
A
= Adv
S
A
IBE
, because B
IBE
does not abort during the above simulation.
In the above simulation, maximum computation
cost of the queries is at most polynomial time expo-
nentiation, hence t
′
< t − Θ(τq). Therefor, the IBE-
PKE-PRE is (k,t
′
,q,ε)-IND-sPr-CPA secure against
against an (TYPE = IBE) adversary.
Theorem 4.2. Suppose that the (k,t,ε)-dBDH as-
sumption holds in (G,G
1
). Then, the IBE-PKE-
PRE is (k,t
′
,q,ε)-IND-sPr-CPA secure against a
(TYPE = PKE) adversary for any (q, k,ε) and t
′
<
t − Θ(τq) where τ denotes a maximum time for expo-
nentiation in G,G
1
.
Proof. Let A
PKE
be a t-time (TYPE = PKE) ad-
versary against the IBE-PKE-PRE. We construct an
adversary B
PKE
which can solve dBDH problem in
G, by using A
PKE
. The B
PKE
is given an input
hg,Γ
1
,Γ
2
,Γ
3
,Ti = hg,g
a
,g
b
,g
c
,Ti, and distinguishes
T is ˆe(g,g)
abc
or T ∈
R
G
1
. B
PKE
works as follows:
Initialisation. B
PKE
generates four blank lists to
write down a query and answer pairs for every
queries, same as (TYPE = IBE) proof.
Setup. The B
PKE
generates a random number w ∈
R
Z
∗
p
and sets g
1
= g
w
, g
2
= Γ
2
, pick a random el-
ement h in G. B
PKE
provides public parameters
EFFICIENT IBE-PKE PROXY RE-ENCRYPTION
291

params = hg,g
1
,g
2
,hi to A
PKE
. Under these con-
ditions, the master key value is g
w
2
which B
PKE
can compute.
B
PKE
generates PKE user’s key pairs and stores
PPKL and PSKL same as (TYPE = IBE) proof.
B
PKE
gives PPKL to A
PKE
.
Phase 1. A
PKE
adaptively queries B
PKE
, and B
PKE
responds as follows:
Extract
IBE
(ID
i
). A
PKE
queries the IBE user’s
secret key sk
ID
i
with an identity ID
i
, then B
PKE
generates a random number u
i
∈
R
Z
∗
p
and com-
putes sk
ID
i
= hd
1
,d
2
i.
d
1
= g
w
2
g
1
ID
i
h
u
i
,
d
2
= g
u
i
.
B
PKE
writes a request and a response to ISKL
and answers sk
ID
i
to A
PKE
.
Extract
PKE
(PKE
j
). A
PKE
queries the PKE
user’s secret key SK
j
with a PKE user’s iden-
tity PKE
j
, then B
PKE
searches the PSKL to
retrieve PKE user’s secret key SK
j
If PKE
j
marked as honest, then B
PKE
rejects,
otherwise (PKE
j
marked as corrupted) B
PKE
answers SK
j
retrieved from PSKL.
Extract
IBE→PKE
(ID
i
,PKE
j
). A
PKE
queries the
re-encryption key rk
ID
i
→PKE
j
, which can con-
vert ciphertexts from an identity ID
i
to PKE
j
,
then B
PKE
searches PSKL to retrieve PKE
j
record. B
PKE
generates random number t
i, j
∈
R
Z
∗
p
and computes rk
ID
i
→PKE
j
.
1. If PKE
j
marked as honest, B
PKE
computes
rk
honest
ID
i
→PKE
j
=
rk
h
1
,rk
h
2
as follows:
rk
h
1
= g
w/SK
j
g
ID
i
1
h
t
i, j
.
rk
h
2
= g
2
t
i, j
SK
j
,
2. If PKE
j
marked as corrupted, B
PKE
computes
rk
corrupted
ID
i
→PKE
j
= hrk
c
1
,rk
c
2
i as follows:
rk
c
1
= g
2
w/SK
j
g
ID
i
1
h
t
i, j
,
rk
c
2
= g
t
i, j
SK
j
.
B
PKE
writes a request and a response to REKL,
and answers rk
ID
i
→PKE
j
to A
PKE
.
Challenge. A
PKE
outputs two equal length plaintexts
M
0
,M
1
and selects target PKE user identity PKE
∗
in honest party and sends them to B
PKE
. B
PKE
selects d(∈
R
{0,1}) and encrypts M
d
.
B
PKE
retrieve selected PKE user’s secret key
SK
∗
= x
∗
from PSKL and computes a PKE cipher-
text C
∗
PKE
as follows:
C
∗
PKE
= hX
∗
,Y
∗
i =
D
ˆe(Γ
1
,Γ
3
)
1/x
∗
,M
d
· T
E
B
PKE
sends C
∗
PKE
to A
PKE
. Note that, if T =
ˆe(g,g)
abc
, C
∗
PKE
is a correct PKE ciphertext of M
d
under a PKE user identity PKE
∗
.
Phase 2. B
PKE
answers A
PKE
’s queries in same man-
ner of Phase1.
Solve. Finally, A
PKE
outputs a guess result d
′
∈
{0,1}. If d
′
= d, then B
PKE
judges T = ˆe(g,g)
abc
and output 1; otherwise, B
PKE
judges T ∈
R
G
1
and outputs 0.
We claim that in the above simulation answers of
B
PKE
are correctly distributed, and A
PKE
cannot dis-
tinguish our simulation from the real-world interac-
tion.
Furthermore, Adv
dBDH
A
= Adv
S
A
PKE
, because B
PKE
does not abort during the above simulation.
In the above simulation, maximum computation
cost of the queries is at most polynomial time expo-
nentiation, hence t
′
< t − Θ(τq). Therefor, the IBE-
PKE-PRE is (k,t
′
,q,ε)-IND-sPr-CPA secure against
against an (TYPE = PKE) adversary.
Remark 4.1. We can simulate the game of
Theorem 4.2 without simulating IBE secret key
queries Extract
IBE
(ID
i
), re-encryption key queries
Extract
IBE→PKE
(ID
i
,PKE
j
), and public keys for re-
encryption PK
R
j
. This implies that we can proof PKE
scheme Chosen Plaintext secure under the dBDH as-
sumption.
5 CONCLUSIONS
In this paper, we propose a efficient [IBE-PKE]-type
proxy re-encryption scheme which the size of the re-
encrypted ciphertext is optimal and delegatee does not
aware of existence of the proxy. We define the secu-
rity notation and prove selective-ID secure based on
dBDH assumption in the standard model against cho-
sen plaintext attack. Furthermore our scheme might
be possible to extend full-ID secure using IBE pro-
posed in (B.Waters, 2005).
Green and Ateniese (M.Green and G.Ateniese,
2007) proposed the semantically secure Identity-
Based proxy re-encryption scheme and constructed
CCA-secure scheme applying CHK conversion tech-
nique (R.Canetti et al., 2004) to their CPA-secure
SECRYPT 2008 - International Conference on Security and Cryptography
292

scheme. It might be able to construct the CCA-secure
[IBE-PKE]-type proxy re-encryption scheme by us-
ing same technique to our CPA-secure scheme. It will
be appeared in the full version.
REFERENCES
B.Waters (2005). Efficient identity-based encryption with-
out random oracles. In In Proceedings of Eurocrypt
’05, volume 3494 of LNCS, pages 114–127. Springer-
Verlag.
D.Boneh and X.Boyen (2004). Efficient selectiveid secure
identity based encryption without random oracle. In In
Advances in Cryptology - EUROCRYPT’04, volume
3027 of LNCS, pages 223–238. Springer-Verlag.
G.Ateniese, K.Fu, M.Green, and S.Hohenberger (2005).
Improved proxy re-encryption schemes with applica-
tions to secure distributed storage. In In Proceedings
of the 12th Annual Network and Distributed System
Security Symposium - NDSS’05, pages 83–107.
L.Zbou, M.A.Marsh, F.B.Schneider, and A.Redz (2004).
Distributed blinding for elgamal reencryption. In
Technical Report 2004-1924. Cornell Computer Sci-
ence Department.
M.Blaze, G.Bleumer, and M.Strauss (1998). Divertible pro-
tocols and atomic proxy cryptography. In In Advances
in Cryptology - EUROCRYPT’98, volume 1403 of
LNCS, pages 127–144. Springer-Verlag.
M.Green and G.Ateniese (2007). Indentity-based proxy re-
encryption. In ACNS 2007, volume 4521 of LNCS,
pages 288–306. Springer-Verlag.
M.Jakobsson (1999). On quorum controlled asymmetric
proxy re-encryption. In In Proceedings of Public Key
Cryptography - PKC’99, volume 1560 of LNCS, pages
112–121. Springer-Verlag.
M.Mambo and E.Okamoto (1997). Proxy cryptosystems:
Delegation of the power to decrypt ciphertexts. In
IEICE Trans. Fund. Electronics Communications and
Computer Science E80-A/1, pages 54–63. IEICE.
R.Canetti, S.Halevi, and J.Katz (2004). Chosen-ciphertext
security from identity based encryption. In In Pro-
ceedings of Eurocrypt ’04, volume 3027 of LNCS,
pages 207–222. Springer-Verlag.
R.Canetti and S.Hohenberger (2007). Chosen-ciphertext se-
cure proxy re-encryption. In CCS ’07: Proceedings of
the 14th ACM conference on Computer and communi-
cations security, pages 185–194. ACM.
T.Matsuo (2007). Proxy re-encryption systems for identity-
based encryption. In In Proceedings of Pairing-Based
Cryptography - Pairing’07, volume 4575 of LNCS,
pages 247–267. Springer-Verlag.
Y.Dodis and A.Ivan (2003). Proxy cryptography revisited.
In In Proceedings of the 10th Annual Network and
Distributed System Security Symposium- NDSS’03.
EFFICIENT IBE-PKE PROXY RE-ENCRYPTION
293
