
Tag Loss Probability Evaluation for a Continuous Flow
of Tags in the EPC-Global Standard
Javier Vales-Alonso, M. Victoria Bueno-Delgado
Esteban Egea-López and Joan García-Haro
Information Technologies and Communications Department
Polytechnic University of Cartagena, Plaza del Hopsital nº1
Cuartel de Antiguones, Cartagena, 30202, Spain
Abstract. This paper addresses the evaluation of a passive RFID system under
a continuous flow of tag arrivals and departures, for instance, in a conveyor belt
installation. In such configuration, the main operational variable is the Tag Loss
Probability (TLP). Since tags stay in the coverage area of the reader for a finite
amount of time, it is possible that some tags leave the area unidentified if many
tags compete for being simultaneously identified. A suitable configuration of
the system (flow speed, tags per block, time between blocks, etc.) must be se-
lected to assure that TLP remains under a given operative threshold. In this pa-
per we focus on the EPCglobal Class-1 Gen-2 standard, which specifies an anti-
collision protocol based on Framed Slotted Aloha. Our work is aimed at evalu-
ating the TLP for the different configurations of such protocol, and selecting
the right scenario configuration to guarantee a TLP below a given limit. This
issue has not been studied yet, despite of its relevance in real-world scenarios
based on assembly lines or other dynamic environments. Simulation results
show that both anti-collision protocol operation mode and flow configuration
heavily impacts in the performance. Additionally, real test have been conducted
which confirm simulation results.
1 Introduction
Radio Frequency IDentification (RFID) technologies are designed as an affordable
solution to remotely identify items by means of wireless communications. A RFID
system consists of one or more readers or interrogators placed in strategic zones and a
potentially large population of cheap and small devices called tags or transponders.
Tags automate the identification of the items to which they are attached. A tag con-
tains an antenna, a simple electronic circuitry and a minimum amount of memory
where it stores some information about the object (e.g. standard codes, history of
transactions, temperatures monitored by a sensor, etc.). When the tags are in the cov-
erage range of the reader system, executes an identification protocol to send their
stored information to it. This paper focuses on RFID systems based on passive tags.
Passive tags have no battery. They are simple and low-cost devices. The energy to
operate is obtained from the RF electromagnetic excitation induced when they are
Vales-Alonso J., Victoria Bueno-Delgado M., Egea-López E. and García-Haro J. (2008).
Tag Loss Probability Evaluation for a Continuous Flow of Tags in the EPC-Global Standard.
In Proceedings of the 2nd International Workshop on RFID Technology - Concepts, Applications, Challenges, pages 115-126
DOI: 10.5220/0001742901150126
Copyright
c
SciTePress

under coverage of the reader system. The identification range varies from some cen-
timeters to a couple of meters. Passive tag technology is inevitably chosen in systems
with a large number of identification objects, where the cost of the tag is a dominant
factor in the system. In passive RFID systems, the communication between the reader
and the tags share the RF spectrum. When several tags are simultaneously in the cov-
erage area, a Medium Access Control (MAC) protocol is needed to handle/avoid
collisions caused by simultaneous transmissions. The extreme simplicity of the tag is
a hard constraint for the design of suitable anti-collision protocols. Complex or so-
phisticated behavior can only exist in the reader system [1-3].
Fig. 1. Industrial environment with a passive RFID system (dynamic scenario).
The number of anti-collision algorithms for passive tags has increased considerably.
They can be classified into two types: deterministic and probabilistic protocols. The
former protocols assume a priori knowledge of the tags which must be identified, for
instance an access control door where the reader check each new identification tag
(tag card) with its list of permitted tags [1-10]. Nevertheless, in many practical sce-
narios the reader system does not have such knowledge, e. g. the unload area of a
warehouse. Therefore, protocols based on probabilistic algorithms are needed, in
which the tags should contend for the shared medium. Pure-Aloha is the most simple,
[11] anti-collision scheme has been implemented in passive tags with read-only-
memory. Slotted-Aloha outperforms Pure-Aloha [12], at a cost of requiring a reading
system that manages a slotted time synchronization. Frame-Slotted-Aloha (FSA) [5]
is a variation of Slotted-Aloha. In FSA, the reader maintains a frame structure com-
posed of a fixed or variable (Dynamic FSA) number of slots. One tag must choose a
slot within the frame, where to send its information to the reader. When a frame fin-
ishes, an identification cycle concludes. Then, the reader, following some rules,
makes a decision about to increase/decrease/maintain the number of time-slots in the
next identification cycle [13,14]. FSA has been implemented in many commercial
products: I-Code [5,15], Philips and selected by standard such as ISO/IEC-18000-6C
[16] and EPCglobal under the EPCglobal Class-1 Gen-2 standard [17]. EPCglobal is
an institution focused on the development of industry-driven standards for the Elec-
tronic Product Code (EPC) to support the use of Radio Frequency Identification
(RFID). This paper focuses on the EPCglobal standard for passive RFID systems
116

Class-1 Gen-2 [17], in the UHF band (860MHz-930MHz). This standard includes a
set of specifications for the hardware of the passive tag (which is assumed to be very
simple), and the hardware and software in the reader systems (which carry the true
system complexity). After its publication in year 2005, it has been widely adopted by
RFID systems manufacturers. Many commercial RFID systems like [18, 19] has been
implemented following this standard.
A relevant set of performance studies has been conducted in the last years for EPC-
Global standards and other protocols for passive RFID systems [13, 20-22]. Com-
monly, these studies consider a block of a given number of tags that enter into the
coverage area of a reader system, and never leaves it [4, 5, 13, 23]. We denote this as
static tags flow scenario. Three related performance measures are commonly consid-
ered on static scenarios: collision probability, packet loss probability and elapsed time
for identification. However, in many real RFID applications (e.g. a conveyor belt
installation), the tags enter the coverage area, stay there a given time, and then leave
the coverage area. We denote this as continuous tags flow scenario. For this type of
systems, a new performance measure should be evaluated: the probability of a tag
leaving the coverage range without a successful identification by the reader. We de-
note this as the Tag Loss Probability (TLP). Note that depending on the application,
even a TLP = 10
-3
may be disastrous and cause thousand of lost items per day. Let us
think, for instance, of tracking individual letters in a post company.
This paper is an attempt to conduct a performance study in a realistic continuous flow
RFID system, like the one shown in Fig. 1. We focus on a commercial RFID system
where the EPCglobal Class-1-Gen-2 is implemented [19]. The physical layer parame-
ters of the tag and reader have been brought from this commercial hardware. A rele-
vant objective of our study is to fairly evaluate if, for the same average rate of tags to
identify, systems that distribute the tag arrivals in more frequent smaller blocks out-
perform in terms of TLP to those systems in which tags are brought together in larger
batches. This issue is studied under the two configuration alternatives implemented in
EPCglobal Class-1 Gen-2. As far as the authors know, the TLP performance of EP-
Cglobal anti-collision protocols under continuous flow scenarios has not been studied
yet, despite of its relevance in real-world scenarios based on assembly lines or other
dynamic environments.
The rest of the paper is organized as follows: in section 2 the EPCglobal Class-1 Gen-
2 standard communication protocol is described as well as its frame adaptation algo-
rithm. In section 3 different scenarios are introduced together with the parameters
used to evaluate the protocols. Besides, the simulation and experimental results are
shown. Finally, section 4 concludes the paper and suggests future work.
2 EPCglobal Class-1 Gen-2
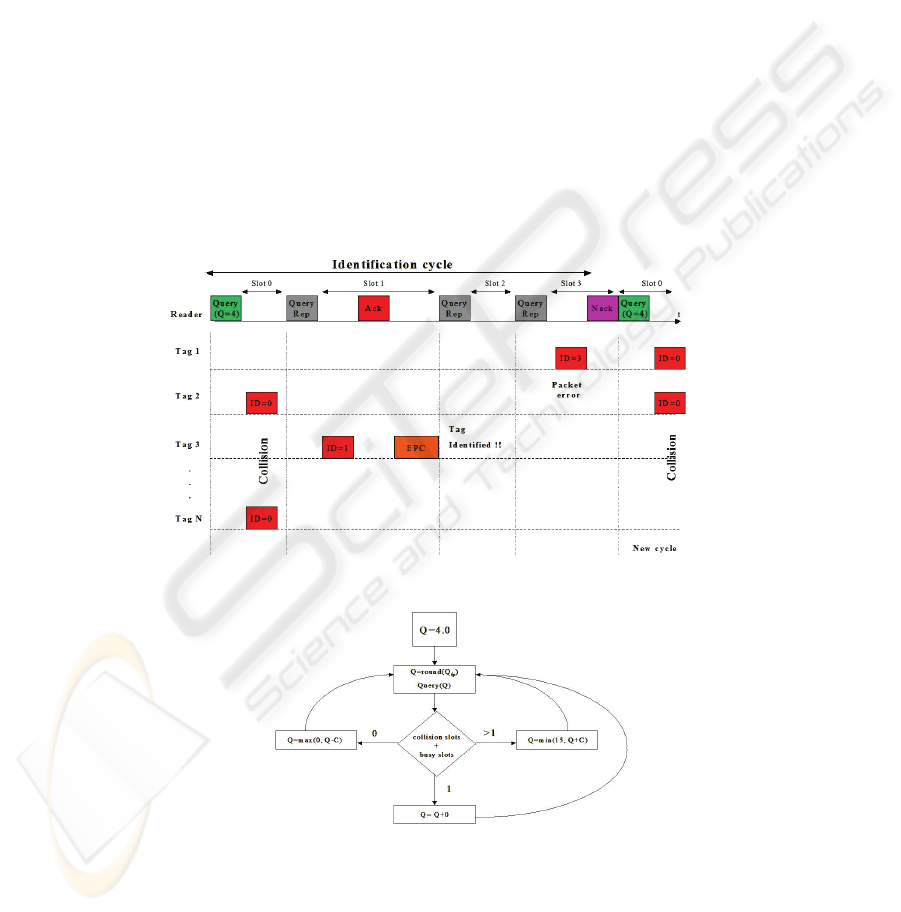
This section describes the identification procedures defined in the EPCglobal Class-1
Gen-2 standard, which are evaluated in this paper. At a first stage the reader system is
continuously monitoring the environment to detect the presence of tags by means of
Broadcast packets. Tags in the coverage area are excited by the electromagnetic
117

waves of the reader and send a reply immediately, producing a multiple collision. The
reader detects the collision and starts the identification cycle. During each identifica-
tion cycle, the time is structured as one frame, which is itself divided into slots, fol-
lowing a FSA scheme (see Fig. 2). An identification cycle starts when the reader
transmits a Query packet, including a field of four bits with the value Q ∈ 0,...,15,
stating that the length of the frame will be of 2
Q
slots. Tags in coverage receive this
packet and generate a random number r in the interval [0, 2
Q
-1]. The r value repre-
sents the slot within the frame where the tag has randomly decided to send its identi-
fication number ID=r. Inside each frame, the beginning of a slot is governed by the
reader by transmitting the QueryRep packet, excepting the slot 0, which is automati-
cally initiated by the Query packet. The tags in coverage use an internal counter to
track the number of transmitted QueryRep packets since the last Query packet, and
then recognize the slot when they should transmit. When the moment arrives, the tag
transmits its identification number ID, which corresponds to the random value r cal-
culated for contention, which is also equal to the slot number in the frame. After
transmitting its ID, three actions can follow:
(i) If more than one tag has chosen the same slot, a collision occurs which is
detected by the reader. Then, the reader reacts initiating a new slot with a
QueryRep packet (see slot 0 in Fig. 2). The tags which transmitted their ID
assume that a collision occurred, and must update their counter value to
counter=2
Q
-1. That means that they will not compete again in this identifi-
cation cycle.
(ii) If the reader receives the ID correctly, and this coincides with the slot num-
ber within the frame, then it responds with an Ack packet. All tags in cov-
erage receive the packet but only the identified tag answers with a Data
packet, e.g. an EPC code. If the reader receives the Data packet, it answers
sending a QueryRep packet, starting a new slot. The tag identified will fin-
ish its identification process (see slot 1 in Fig. 2). If the reader does not re-
ceive a correct Data packet within a given time, it considers the time-slot
has expired, and sends a Nack packet. Again, all tags in coverage receive
it, but only the tag in the identification reacts by updating its counter value
to counter=2
Q
-1. Thus, this tag will not contend again in this identification
cycle (see slot 3 in Fig. 2). After this, the reader will send a new Query or
QueryRep packet to start a new frame or slot respectively.
Finally, when a cycle finishes, a Query packet is sent again by the reader to start a
new identification cycle. Tags unidentified in the previous cycle will compete again,
choosing a new random r value.
The anti-collision mechanism described in the EPCglobal Class-1 Gen-2 standard
provides a high degree of flexibility. The reader system governs the frame structure in
two interesting ways: (i) it controls the initial number of slots of the frame through
the Q value, (ii) it can decide to reset the identification cycle at any time, by sending a
new Query packet with the same, or a new Q value. Controlling the Q value strongly
affects the identification time performance. If the Q value is high and the number of
tags in coverage is low, many empty slots appear in the frame. On the contrary, if the
Q value is low and the number of tags is high, many collisions appear. Both situations
118
should be avoided. In this paper, two configuration alternatives are tested, all of them
based on the standard:
1) Q-static configuration. All identification cycles (frames) have the value Q=4
(defining frames of 16 slots). This value is brought from the default Q value
in the standard. It is common to find commercial systems with this configu-
ration.
2) Q-dynamic configuration (denoted as frame-by-frame adaptation). The Q
value is adapted cycle-by-cycle following the algorithm depicted in Fig. 3.
The reader starts with a value Q=4. Then, in each frame it counts the number
of empty slots, and occupied slots (summing busy slots with one tag identi-
fied, and collision slots). If all slots are empty, an internal Q
fp
(Q floating
point) value is decreased by user defined variation parameter C ∈ [0.1,0.5].
If just one slot is occupied, the Q
fp
value is maintained. If more than one slot
is occupied, the Q
fp
value incremented by C. Actually, the new Q value em-
ployed in the subsequent frame is calculated from rounding Q
fp
to an integer
value, and limiting it to a minimum value of 1 and a maximum value of 15.
Note that higher values of parameter C imply faster modifications of the Q
value.
Fig. 2. EPC Class-1 Gen-2 procedure.
Fig. 3. Adaptative Q algorithm.
119
3 Tag Loss Probability Evaluation
3.1 Scenario Description
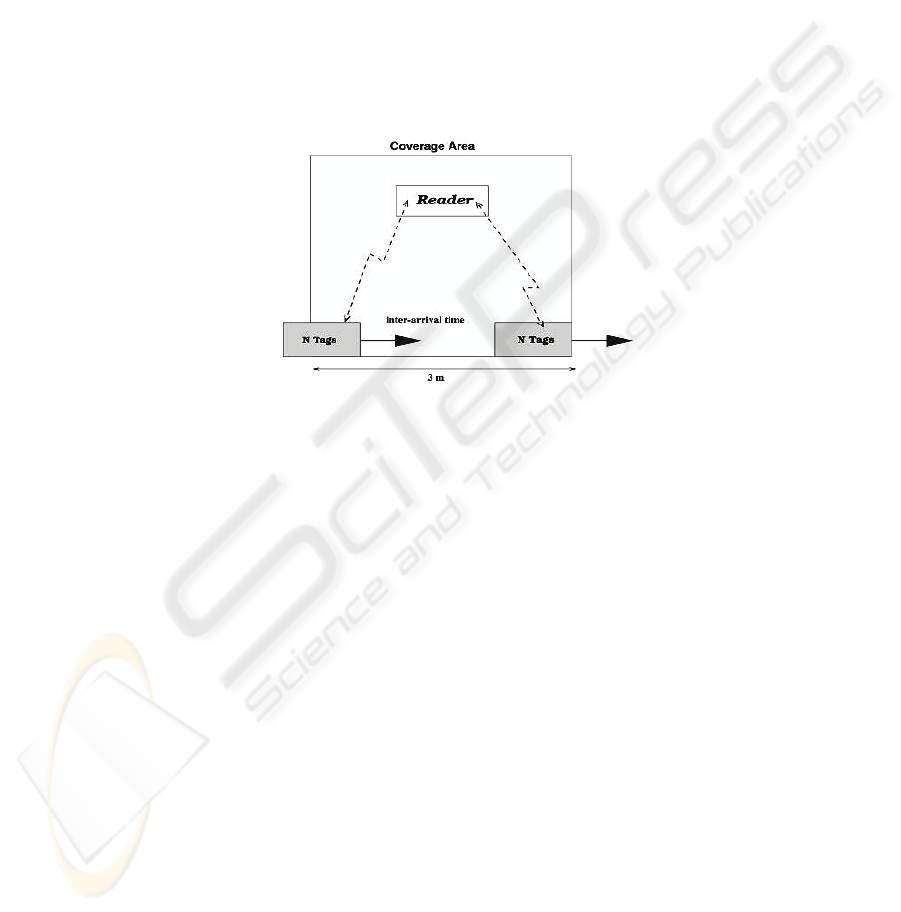
Our testing scenario corresponds with that of a warehouse in which pallets full of
items to be identified while enter the facility. Each pallet transports a deterministic
number N of tags. Pallets pass below a reader system situated at the input door of the
facility. The duration T of the coverage time (the time in which a block of tags is
under coverage of the reader system) depends on the speed of the pallet, and the cov-
erage distance. Let us suppose that in our scenario, the pallets move at a deterministic
speed of 1 m/s. The reader is located in a position so that all the tags in a pallet are in
coverage during 3 meters. That means that a pallet is in coverage for a deterministic
time of T=3 s (see Fig.4).
Fig. 4. Scenario Description.
Two parameters tune this system. First, the number of tags transported in each pallet
N. Second, the time elapsed between the arrivals of two consecutive pallets, which we
denote as inter-arrival time, T
IA
. When T
IA
<T, more than one pallet is in coverage at
the same time: some of them have just entered the coverage area, while others are
close to be out-of-range. When T
IA
≥T at most one pallet is in range at a time. This last
case corresponds to that named as static scenario. For any configuration, we denote as
λ the average rate in tags per second that enter the coverage area. Note that this equals
the average rate of tags that leaves the coverage range. Also note that the average tag
rate λ, the average number of tags in range (K), and the average time that a tag is in
range (T in our example) are related by the equation: K = λT. This can be easily ob-
tained by applying the Little’s law to the coverage area, seen as a black box where
tags enter and leave. This relation holds for any traffic pattern of tags.
Our interest lays on studying how it affects to the system performance, the burstiness
of the arrivals of tags. That is, for a given rate of tags per second that should be iden-
tified:
- what is the EPC protocol which guarantees a successful identification of a
rate of tags per second?
- is it better to distribute them in smaller blocks that arrive more frequently, so
that more than one block is in range at a time?
120
In order to obtain valuable results that may help to clarify these questions, special
care has been taken to design tests that are related to real-world scenarios. We have
employed physical layer parameters which correspond to commercial hardware.
Transmission error probability which depend on the environment where the RFID
system is installed and parameters associated with the physical configuration of the
tags and the reader: transmission/reception rate, modulation type, packet length, etc.
To take into account these parameters, the characteristics that a lot of commercial
passive tags, readers an antennas [19, 20] carry out nowadays are assumed:
Table 1. Parameters of the commercial devices assumed to get the simulation results.
Paremeters Passive tags Reader/antenna
Work frequency UHF 868MHz-928MHz UHF 868MHz-928MHz
Communication range 10cm-3m Up to 10m
Memory Available 96-256 bits --
Modulation ASK ASK/PSK
Transmission /Reception rate 40 Kbps 80Kbps
Maximum Power of the antenna -- 10 W
Maximum RF
Power of the Reader
-- 4W
3.2 Simulation Results
The evaluation results have been obtained by means of simulation. We have devel-
oped our simulation tool within the freeware network simulation environment OM-
NeT++ (Objetive Modular Network Testbed in C++) [24]. OMNeT++ is a discrete
even-driven and object oriented framework, used in many research fields like multi-
processors systems, hardware architectures validation, performance of software sys-
tems. The simulator collects statistic results for some performance measures of inter-
est like tag loss probability, identification delay, average number of identification
cycles. The two different anticollision protocols explained in section 3 have been
implemented. The Fig. 5 shows the simulation results in terms of TLP to the Q static
standard protocol. Although Q ∈ 0,...,15, it has been established to Q=4, which is the
value recommended by the standard and established in a lot of commercial readers.
EPCglobal implemented in the scenario described above: a continuous tags flow
scenario with a deterministic traffic pattern and a flow of tags arrivals per second
defined in the x axes. The influence of the inter-block arrival time of λ has been stud-
ied to different inter-blocks-arrivals times, T
IA
=0.5, 1, 2, 3s. The results of the EP-
Cglobal Class-1 Gen-2 standard with static frame show worst results, obtaining a high
TLP value with a low λ. This result is because of the fact that the Q value is low(Q =
4) and doesn't change. If Q takes a high value, the results obtained will be displaced
to the right of the graphics. In fact, the results will be better than other anticollision
procedures in terms of TLP but the identification delay will be higher, even more
when the number of tags in coverage is low because of the frame length will depend
on the Q value. The results of the Fig. 5 also confirm that if T
IA
=3s, it means T
IA
=T,
the continuous flow of tags doesn’t affect to the TLP obtained. Fig 6, shows the simu-
lation results in terms of TLP but, in this case, with the Q dynamic standard protocol
121
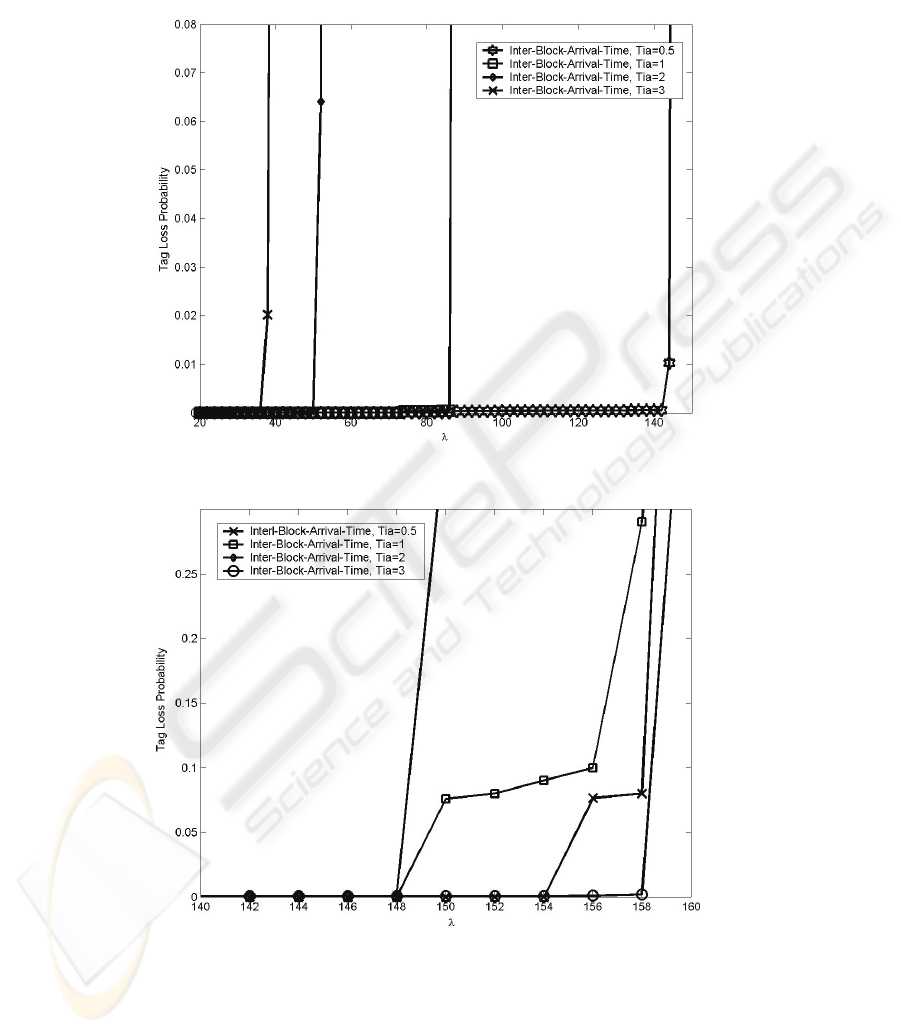
EPCglobal. The results show that this alternative configuration has a better response
in terms of TLP to a higher λ than Q static protocol. For all T
IA,
results are better using
the Q-dynamic protocol.
Fig. 5. Tag Loss Probability with Q-static protocol.
Fig. 6. Tag Loss Probability with Q-dynamic protocol.
122
TLP is clearly degraded for both protocols if λ > 160. Thus, it is necessary to reduce
the tag flow to get a given TLP limit. This threshold will depend on the requirements
of each installation.
To get an accurate vision about how to apply the results to the design of a RFID sys-
tem some criteria has to be selected. First, two different thresholds have been as-
sumed: TLP=10
-3
, 10
-6
. Then, taking into account all parameters explained in the
previous section (velocity of the pallet, read range of the reader, anticollision proto-
col, etc.) both alternatives of EPCglobal Class-1 Gen-2 standard has been evaluated.
Results are shown as the maximum number of tags per pallet for different traffic
loads and for the deterministic traffic pattern.
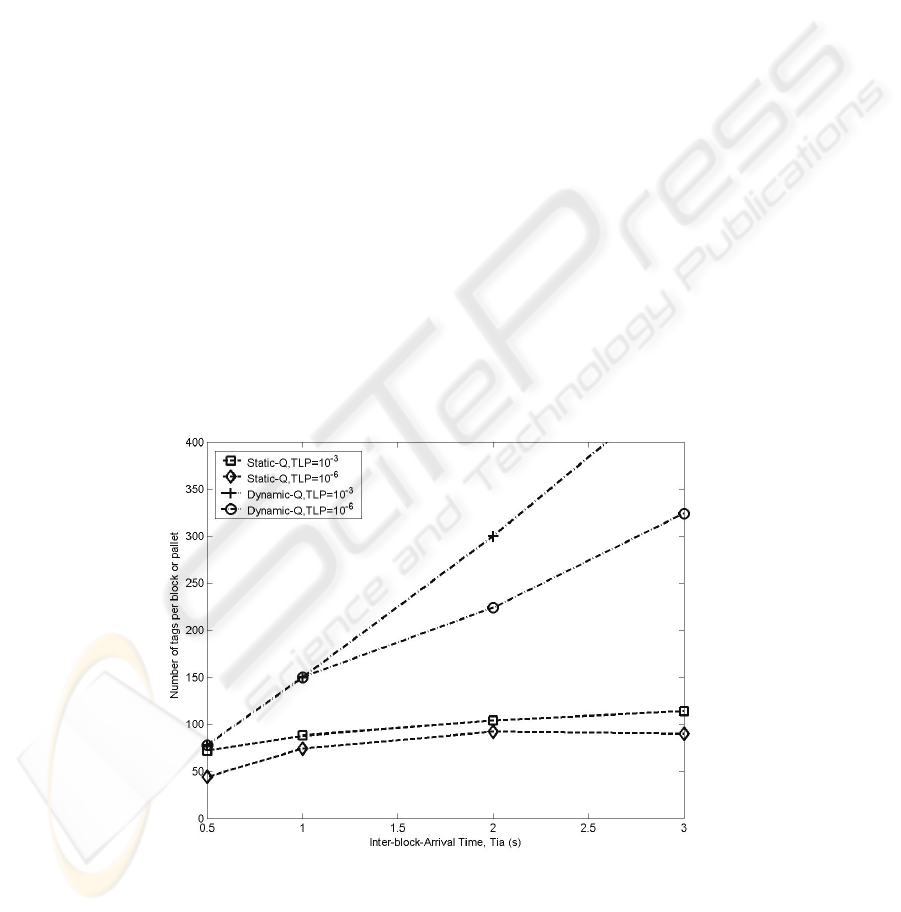
The results of the two configuration proposed in this paper are shown in the figure 7.
The X axe represents the inter-arrival time of two consecutive pallets. The Y axe
represent the number of tags in each block. Simulations show that the Q-adaptative
algorithm exhibits the best results in terms of TLP. The results of Fig.7 helps us to
answer the questions introduced in section 3.1. On the one hand, the Q-dynamic pro-
tocol is better than Q-static protocol in terms of get the maximum λ value with the
lowest TLP value. On the other hand it tags arrivals are distributed in more frequent
smaller blocks outperform in terms of TLP to those systems in which tags are brought
together in larger batches. Indeed Fig 7 help us to get select a suitable configuration
to our real RFID system. If we have a RFID system installed in a coveyor belt, we
can fix an objective TLP (e. g. TLP = 10
-6
), it means, the percentage of items that we
can permit to not identify. With the TLP fixed and taking to account the results of
Fig.7, we can design our RFID system: the reader’s anticollision protocol, the inter-
block arrival time (the velocity of the coveyor belt) the number of tags in each block
(the number of items per pallet), etc…
Fig. 7. Number of Tags per pallet with a TLP threshold.
123

3.3 Experimental Results
Finally, an experimental set-up has been studied to compute the TLP under continu-
ous flows. In this set-up we used an “Alien 8800” reader, working in the UHF band
of 868 MHz, with two circular polarized antennas (gain 6dBi), one acting as transmit-
ter and the other as receiver, installed one in front each other (2 meters away). The
tags used are compatible with EPC Class 1 Gen 2. The anti-collision protocol used by
the reader is the Q-static procedure, with Q=4. In our test we aim at simulating a
traffic flow and measuring the actual TLP associated. Two configurations where
tested:
• Coverage time of blocks, 3 s. TLP objective 10
-3
. Thus, according to Fig. 7,
the number of tags per block is slightly over 100. We use 100 tags for this
configuration.
• Coverage time of blocks, 0.5 s. TLP objective 0.1. For this configuration our
simulations suggests a maximum number of 70 tags in each block.
To simulate the actual traffic of tags we put a static block with the selected number of
tags in the coverage area. Then, we issue a reader order to the Alien reader. This
reader returns a list of each tag present, and indicates the time (with millisecond accu-
racy) at which tag is detected. Thus we compute the TLP counting the number of tags
detected after the selected coverage time. This experiment was repeated 100 times
and the average values obtained are a TLP of 0.003954 and 0.196 for the first and
second configuration, respectively. As a conclusion, the actual TLP is in both cases
slightly worst (but in the same order) than the TLP expected for such configurations.
Although tag loss in real installations (like in our test) suffers from additional issues,
such as signal propagation, which can affect the performance, our study provides a
good starting point to select a suitable system configuration.
4 Conclusions and Future Works
Most of works related to identification and anticollision procedure in the RFID sys-
tems have been studied to minimize the identification delay assuming static scenarios
with a fixed number of tags in the read range of a reader. However, several practical
RFID systems are installed in environments with a continuous flow of tags entering
and leaving the coverage area of the reader. In this case, the critical parameter is the
TLP. In this work this probability has been computed for different scenarios under
different traffic loads. All scenarios have been evaluated with the identifica-
tion/anticollision defined in the standard protocol EPCglobal Class-1 Gen2, config-
ured both with static frame and with dynamic frame cycle-by-cycle. Results show that
the standard protocol with the adaptative Q cycle-by-cycle mechanism exhibits the
best results in terms of TLP in all scenarios studied. Additionally, the results help us
to select a suitable system configuration (selecting a objective TLP and a coverage
time).
124

Acknowledgments
This research has been supported by project grant DEP2006-56158-C03—03/EQUI,
funded by the Spanish Ministerio de Educación y Ciencia, project TEC2007-67966-
01/TCM (CON-PARTE-1), funded by the Spanish Ministerio de Industria, Turismo y
Comercio, and it is also developed within the framework of "Programa de Ayudas a
Grupos de Excelencia de la Región de Murcia, de la Fundación Séneca, Agencia de
Ciencia y Tecnología de la RM (Plan Regional de Ciencia y Tecnología 2007/2010).
References
1. Hush, D.R, Wood, C. ``Analysis of tree algorithms for RFID arbitration'', Proc. of IEEE
International Symposium on Information Theory, pp. 107. 1998.
2. Jacomet, M., Ehrsam, A., Gehring, U. ``Contactless Identification device with anticollision
algorithm”. Proc. of IEEE Conference on Circuits, Systems, Computers and Communica-
tions, pp. 269-273. Athens, Greece, July 1999.
3. Jihoon Myung, Wonjun Lee, ``Adaptative Binary Splitting: A RFID tag Collision Arbitra-
tion Protocolo for tag Identification''. Mobile Networks and Applications Journal, vol(11),
pp 711-722. May 2006.
4. Shih, D., Sun, P., Yen, D., Huang, S., ``Taxonomy and survey of RFID anti-collision pro-
tocols'', Elsevier Computer Communications, vol. 29, pp. 2150--2166, 2006.
5. Vogt, H., ``Efficient Object Identification with Passive RFID tags'', Lecture Notes in Com-
puter Science, vol. 2414, pp. 98--113, 2002.
6. Draft protocol specification for a 900MHz Class 0 Radio Frequency Identification tag,
Auto-ID-Center,Feb. 2003.
7. Zhou, F., Chen, C., Jin, D., Huang, C., Min, H., ``Evaluating and Optimizing Power Con-
sumption for Anti-Collision Protocols for Applications in RFID Systems'', Proc. Int. Symp.
on Low Power Electronics and Design 2004, pp. 357-362, 2004.
8. Finkenzeller K. ``RFID Handbook: Radio-Frequency Identification Fundamentals and
Applications'', John Wiley,New York pp. 200-219, 2000.
9. Law, C. Lee, K., Siu, k-Y ``Efficient Memoryless protocol for tag Identification'', Proc. of
the 4th International Workshop on Discrete Algorithms and Methods for Mobile Comput-
ing and Communications., pp. 75-84. Bostn, Massachusetts, August 2000.
10. Juels, A., Rivest, R., Szydlo, M. ``The Bloker tag: Selective tag Blocking of RFID tags for
Consumer Privacy'', Proc. of the 10th ACM Conference on Computer and Communication
Security, pp. 103-111, 2003.
11. Finkenzeller K. ``RFID Handbook: Radio-Frequency Identification Fundamentals and
Applications'', John Wiley,New York pp. 200-219, 2000.
12. ``3.56MHz ISM Band Class 1 Radio Frequency Identification tag Interference Specifica-
tion: Candidate Recomendation, Version 1.0.0.0''. Technical Report MIT-AUTOID-WH-
002, MIT Auto ID Center, 2003.
13. Floerkemeier, C., Wille, M., ``Comparison of Transmission Schemes for Framed Aloha
based RFID'', Workshop on RFID Extended Network Deployment of Technologies and
Applications, Phoenix, AZ, January, 2006.
14. Lee, S., Joo. S. D., Lee, C. W. ``An enhanced dynamic framed slotted aloha algorithm for
RFID tag identification''. Proc. of Mobiquitous, pp 166-172. 2005.
15. Vogt, H. ``Multiple Object Identification with passive RFID'', Proc. of IEEE International
Conference on Systems, Man and Cybernetics, vol(3), 6 pp, October 2002..
125

16. ISO/IEC 18000-6C:2005, Information technology--Radio frequency identification for item
management--Part 6C: Parameters for air interface communications at 860MHz to
960MHz, 2005.
17. Class 1 Generation 2 UHF Air Interface Protocol Standard Version 1.0.9: ``Gen 2''. Online
in: http://www.epcglobalinc.org/standards
18. Intermec Reader:
psfiles.intermec.com/eps_files/eps_brochure/RFIDReader_brochure_web.pdf
19. Alien Reader: http://www.alientechnology.com/readers/index.php
20. Kawakita, Y., Mitsugi, J. ``Anti-collision performance of Gen 2 Air Protocol in Random
Error Communication Link'', Proc. Int. Symp. on Applications on Internet Workshops, pp.
68-71, 2006.
21. Mitsugi,J., Yumoto, Y., Hada, H., Murai, J. ``Auto-ID Labs. Activities and collaborations
in wireless technology for the harmonized deplyment of UHF RFID system'', Auto-ID Labs
Research Workshop, Zurich, 2004.
22. Kodialam,M., Nandagopal, T. ``Fast and Reliable Estimation Schemes in RFID Systems'',
Proc. of ACM Mobicom, pp. 322-333, Sept, 2006.
23. Egea-Lopez, E., Vales-Alonso, J., Martinez-Sala, A. S., Bueno-Delgado, M. V., Garcia-
Haro, J. ``Performance Evaluation of non-persistent CSMA as anti-collision procedure for
active RFID tags'', 5th International Conference on Wired/Wireless Internet Communica-
tions (WWIC2007), Coimbra, Portugal, May 2007.
24. A. Vargas, ``The OMNeT++ Discrete Event Simulation System'', European Simulation
Multiconference ESM 2001, Prague (Czech Republic), June 2001.
126
