
DESCRIBING CRYPTOBIOSIS AS A TIME BASED
PROTECTION SYSTEM USING PETRI NETS
Bengt Carlsson
a
, K. Ingemar Jönsson
b
and Keith Clark
c
a
School of Engineering Blekinge Institute of Technology Soft Center S-37225 Ronneby
b
Department of Mathematics and Science, Kristianstad University,S-291 88 Kristianstad, Sweden
c
Department of Computing, Imperial College, London
Keywords: Cryptobiosis, Petri net, Time based security model.
Abstract: Cryptobiosis represents the state of a living organism when it sh
ows no visible signs of metabolic life, but
maintains a capacity to return to an active, metabolic state. This peculiar state, although known from a wide
variety of organisms, has received little attention from a theoretically biological perspective. A description
based on a Petri net setting and a time based security model is proposed. In order to protect against a
prolonged exposure time, the pathways for chemical reactions involved must fulfil their actions during a
limited detection and response time to fulfil the protected state of entering/leaving cryptobiosis.
1 INTRODUCTION
Within biology the term cryptobiosis, or hidden life,
represents the state of an organism when it shows no
metabolic signs of life, while still maintaining a
capacity to return to normal metabolic activity
(Keilin 1959, Clegg 2001). Organisms with a
capacity to enter cryptobiosis are found in a variety
of prokaryote, plant, and animal taxa, and has
evolved as an adaptation to survive under temporally
hostile conditions, e.g., in very dry or cold
environments (Alpert 2005). One of the most
common environmental agents inducing cryptobiosis
is desiccation, leading to a variant of cryptobiosis
called anhydrobiosis. The cryptobiotic state is
characterised by temporally arrested metabolism,
growth, reproduction and senescence (Keilin 1959,
Crowe 1971). The lack of metabolism during
cryptobiosis can be described as temporary “death”
representing a unique biological state between life
and death, a potentially reversible death (Neuman
2006).
The biochemical and physiological mechanisms
allo
wing cryptobiotic organisms to survive in an
ametabolic and (in the case of anhydrobiosis) more
or less completely dry state remain poorly
understood (Schill et al. 2004, Watanabe et. al. 2002,
Guppy 2004). Also, the problems connected with
extreme desiccation and a complete shut-down of
the metabolic machinery have rarely been analysed
theoretically. However, some criteria are necessary
to fulfil for successful cryptobiosis to take place. For
instance, the organism must either prevent cellular
damage at the entrance of cryptobiosis and during
the cryptobiotic state, or be able to repair the
damage that is potentially expressed when
reactivated. It must also be able to respond to one or
more triggering signals connected with the
cryptobiotic period. We will here describe a possible
approach to a protection system during an induction
phase, a dormancy phase and a reactivating phase of
cryptobiosis.
In order to return to an active life, an organism in
cryp
tobiosis needs to interpret signals from the
environment including reactivating itself from the
ametabolic state, i.e. recovering original biological
functions despite the lack of basic metabolic
machinery. The organism must be “raised from the
dead”, by responding to an environmental signal
announcing favourable life conditions, e.g. a drop of
water for a dehydrated organism. It has been
suggested that cryptobiosis entails reversible
computation with a bootstrapping involving a
recursive hierarchy (Neuman 2006). This is similar
to models within computer science including
creating more complex tools from simple tools
(bootstrapping), sub and superclasses within object
oriented programming (hierarchies), and logic
programming using recursive functions. We will
here use a Petri net as a tool for describing the
reversible processes of cryptobiosis, without going
into the details of the metabolic pathways involved.
Biological systems modelled by Petri nets
were i
ntroduced by Reddy et al (1993). By using
281
Carlsson B., Ingemar Jönsson K. and Clark K. (2008).
DESCRIBING CRYPTOBIOSIS AS A TIME BASED PROTECTION SYSTEM USING PETRI NETS.
In Proceedings of the First International Conference on Bio-inspired Systems and Signal Processing, pages 281-285
DOI: 10.5220/0001068002810285
Copyright
c
SciTePress
Petri net it was possible to dynamically model the
intrinsic behaviour of e.g. metabolic pathways
within a cell. In Heiner et al (2004) the metabolic
pathways conducting an apoptosis (genetically
programmed cell death) is modelled using a
qualitative Petri net.
In section 2 the different phases of
cryptobiosis are outlined followed by a description
of a time based protection system. Next, a Petri net
is introduced for modelling metabolic protection and
finally a discussion and concluding part sum up the
proposed description.
2 CRYPTOBIOSIS
Cryptobiosis may be induced by several
environmental factors e.g. low temperature
(cryobiosis), lack of oxygen (anoxybiosis) or lack of
water (anhydrobiosis). All of these factors may force
the organism to an arrested metabolism. Here, we
will use anhydrobiosis as an example to describe
cryptobiosis within a Petri net setting using a time
based security model.
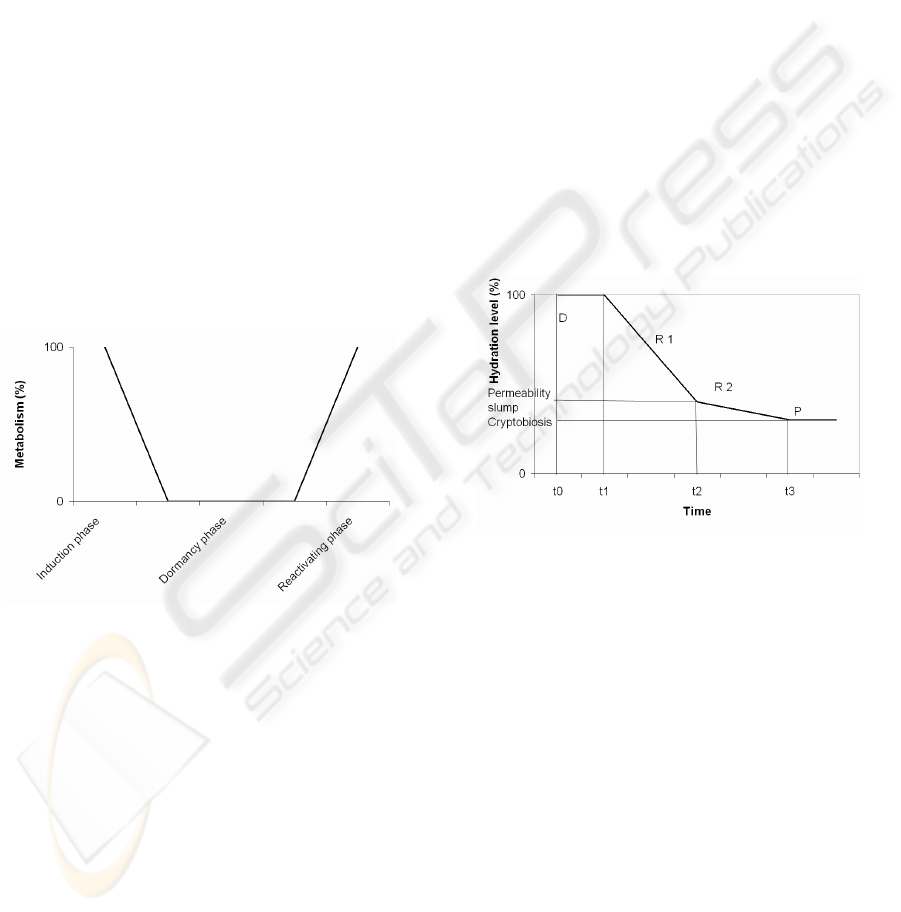
Figure 1: An idealized figure of changes in metabolism
during the induction, dormancy, and reactivating phases of
cryptobiosis. A more realistic curve would likely involve
non-linear patterns of metabolic changes during induction
and reactivation.
Figure 1 shows the three general phases
connected with cryptobiosis, where the induction
phase prepares the organism for an ametabolic state
as a result of e.g. desiccation. Note that the factor
inducing changes in metabolic rate, e.g. reduced
hydration level, is not shown in Figure 1. During the
dormancy phase the organism is inactive due to a
lack of metabolic activity, but continued desiccation
may occur because metabolism will stop well before
the animal is completely dehydrated. The
reactivating phase involves both the reverse
processes of the induction phase and a repair process
depending on damages arisen during the induction
and dormant phases.
The pattern of water loss at the induction of
cryptobiosis as a result of dehydration
(anhydrobiosis) has been well documented (Wright
1989, Wharton 1996). Initially the evaporation of
water is high, but at some point the organism has
mobilised a first protection mechanism (mainly
based on morphological changes) which
dramatically reduces the rate of further dehydration.
Wright (1989) termed this point the “permeability
slump”. After this point, the rate of dehydration is
much reduced. The remaining time, until the
organism has lost so much of its water that
metabolism is arrested, is decisive of whether the
organism will enter a cryptobiotic state or die.
During this time, the organism must mobilise the
mechanisms that should protect it as it approaches
the dry anhydrobiotic state. Figure 2 describes the
temporal change in hydration level of an
anhydrobiotic organism exposed to a desiccating
agent.
Figure 2: Patterns of water loss over time in an
anhydrobiotic organism exposed to a desiccating agent,
with phases of detection (D) and responses (R
i
), creating a
state of cryptobiotic protection (P).
In both computer science and in cryptobiotic
organisms, a detection mechanism must recognize
the attack or stress input, after which different
response mechanisms must be activated (R1 and R2
in Figure 2). In cryptobiotic organisms these
preventing mechanisms together form the protection
system which must be activated before the
metabolism disappears.
3 A TIME BASED PROTECTION
SYSTEM
To describe, in general terms, a cryptobiotic
protection system, a time based security model
(Schwartau 1999) may be used, where a protection
BIOSIGNALS 2008 - International Conference on Bio-inspired Systems and Signal Processing
282

mechanism is successful only as long as the sum of
the time needed by the detection mechanism and the
response mechanism does not exceed the time limit
of the protection.
In this model the amount of exposure time E,
which may be positive or negative, determines the
outcome of an external attack. The exposure time
defines a time period under which the organism is
exposed to the environmental stress without a
mobilized protection system. The exposure time is
determined by three factors; a protection system P, a
detection mechanism D, and a response mechanism
R, see Figure 2. The purpose of a protection system,
independent of being within computer science or life
science, is to protect involved assets. This is valid
for a certain amount of time, i.e. the involved assets
lose their values or an organism loses the
opportunity to enter a cryptobiotic state. If detection
and response time is short enough, depending on the
current attack strength, the protection system will
not be invaded or exposed. So a negative exposure
time means that the protection mechanism manages
to keep the system secured during the time when
detection and responses are established.
Let ∆P denote the duration of protection of a
system caused by an attack with strength a starting
at time t
0
and with protection strength s. Let ∆D
denote the time it takes to detect an attack with
strength a under given circumstances. Finally, let ∆R
denote the time it takes to implement sufficient
measures to eliminate the negative consequences of
the attack with strength a after the signal has been
detected. Then
),,,(),,,(),,,(),,,(
0000
ttsaPttsaRttsaDttsaE Δ−Δ+Δ=Δ
(1)
Equation (1) captures exposure time ∆E(a,s,t
0
,t)
as a relation between the three mechanisms above
and the time intervals t
0
and t where t>t
0
. The
system will be safe if and only if
, i.e., if the
system is not exposed to an attack without a
protection system.
0<ΔE
As already pointed out in Figure 2, a protection
system consisting of detection, responses and
protection are outlined for the induction phase.
During the first period of time (t
0
to t
1
) the organism
has not yet started to lose its internal water, but a
detection mechanism (D) recognizes the presence of
a stress signal. This may be, e.g., the evaporation of
surrounding water. In the next interval (t
1
to t
2
), the
organism starts to lose its body water and a first
response mechanism (R
1
) is mobilised. When the
establishment of this mechanism is completed (at t
2
),
the rate of dehydration is much reduced, but
continues until the organism has reached a level of
hydration at which metabolism stops. Since
metabolism is arrested well before the organism is
completely dry (Clegg 1986), the loss of water may
continue also after the cryptobiotic state has been
reached. In the interval between t
2
and t
3
the second
response (R
2
), representing the biochemical
preparations for the dry cryptobiotic state, takes
place. If these preparations are successful, i.e., if the
second protection system has been established
properly, the organism enters cryptobiosis. The time
available for the necessary actions (detection +
responses) will be determined by the rate of
desiccation from t
0
to t
3
, influenced in part by the
strength of the desiccation agent, and in part by the
ability of the organism to reduce the effect of this
agent. If detection or response is delayed the
protection system will not be ready, and the
organism will die or be damaged before reaching a
state of cryptobiosis. Equation (2) formalizes this
organism system:
),,,(),,,(),,,(),,,(),,,(
303222111030
ttsaPttsaRttsaRttsaDttsaE Δ−Δ+
Δ
+
Δ
=
Δ
(2)
The organism will enter a state of cryptobiosis if
∆E is negative, i.e. if the time needed to establish the
protection mechanism ∆P exceeds the sum of the
time for the detection ∆D and response mechanism
∆R
i
. The main difference in the interpretation of Eq.
(1) (representing a computer science model) and Eq.
(2) (representing a biological model) is that in the
former model the protection system is present
already at the beginning, with an expected time of
function. In the biological model, the protection
system is not described as present from the start, but
is established only after the stress agent is detected,
with an expected time of establishment (∆P).
However, from the perspective of P, the responses
R
1
leads to an intermediate protection system
(activated at the “permeability slump”) that
conceptually resembles that of computer systems,
since its location in Figure 2 defines a remaining
time within which the R
2
responses must take place.
Processes during the reactivating part must
include both activating the reversible processes of
the induction phase, and repairing of damage caused
by positive exposure time during induction and
dormancy phases.
4 USING A PETRI NET FOR
MODELLING METABOLIC
PROTECTION
A Petri net consists of nodes and arcs where nodes
are of two types; places p
i
and transitions t
i
. Tokens
DESCRIBING CRYPTOBIOSIS AS A TIME BASED PROTECTION SYSTEM USING PETRI NETS
283
represent activity of the sequence of transitions.
Places, represented by circles, are passive system
elements while transitions represented by boxes are
active system elements, e.g. in a metabolic setting
chemical compounds and chemical reactions. Arcs
connect nodes of different type. The activity of a
Petri net is a flow of tokens over the pathways of the
net
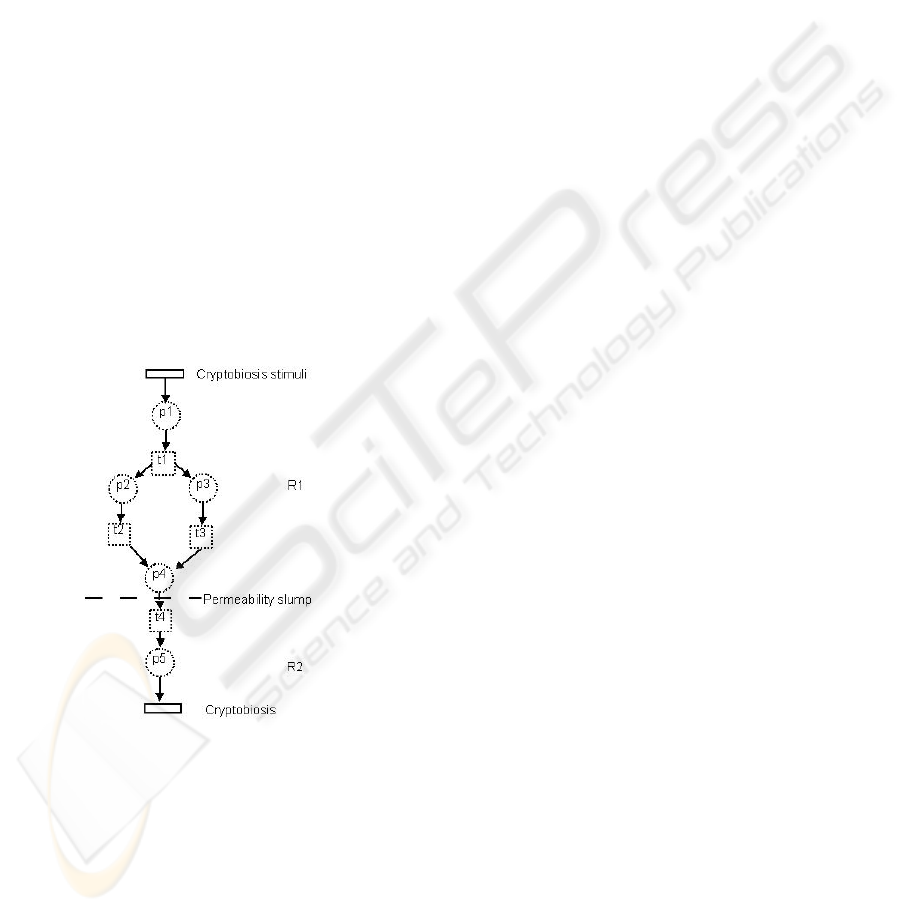
To start with, the organism must detect the state
of stress, or cryptobiosis stimuli, which in the case
of anhydrobiosis is represented by the initiation of
desiccation (loss of water), and the intensity of the
stress factor. If the humidity surrounding the
organism is very low the process towards a dry and
cryptobiotic state will be more rapid, and the
organism then has less time to prepare itself before
metabolism ceases. Preparations for the dry state
therefore often involve morphological changes that
reduce the rate of water loss (e.g., Wright 2001).
Previous research has shown that this is a critical
phase, where the cell must be able to mobilize the
necessary metabolic changes that allow it to
maintain structural integrity and enter a dry state
without lethal damage. These changes, or set of
places p
i
and transitions t
j
in a Petri net setting, are
represented as different pathways in Figure 3.
Figure 3: Induction phases of cryptobiosis. The dotted
circles and squares indicate examples of metabolic
pathways.
The dynamics of a Petri net allows transitions to
split between multiple places or places requires more
than one transition to enter a state. The number of
places and transitions are not known nor are the
structures of the pathways. When two arcs arrive at a
place it is a synchronisation step - only when the
tokens from the converging pathways have both
arrived at the place, does the transition on the
outgoing arc fire.
Examples of pathways are molecules (e.g.,
sugars, Crowe 2002) that replace structural water in
cell membranes, and molecular chaperones (stress
proteins) that prevent aggregation of proteins (Goyal
et al. 2005). All the details involved are outside the
scope of this work, but several pathways that slow
down or disappear during transforming from R1 to
R2 are involved.
Thus, the protection system allowing
cryptobiotic survival includes several protection
parameters, the induction of which relies on
metabolic activity. Note that this has to be done
before entering the cryptobiotic state, i.e. the
protection system must act proactively.
Compared to the induction phase and the
reactivating phase, which normally amounts to
minutes or hours, the dormancy phase may be much
more extended in time and may last for weeks,
months or years (Guidetti and Jönsson 2002,
Watanabe 2006).
The reactivation from the anhydrobiotic state
also provides a challenge for the organism, the
physiological details of which has yet to be
described. At some point in time the metabolism
must restart as a reaction to changed conditions, e.g.,
to rehydration. In principle this is the reverse
function of the induction phase restarting the
protection system. All the necessary biochemical
components for starting up the system are present,
and some of the protection components may be used
for energy production or for repairing DNA and
other parts of the cell.
In principle the protection system needs to be
restored to its pre-conditions with one major
addition, damaged parts or processes must be
repaired. This is part of the existing pathways
or
added as new pathways enlarging the Petri net. The
protection system will not be restored without
successful repair facilities and, in order to have a
functioning repair mechanism, some restored
protection mechanisms must be present. Meanwhile
there should be a replacement process where water
is tied to the organism again. Finally, when the
metabolism is restored to 100 percent, we are back
to a fully active organism.
5 DISCUSSION AND
CONCLUSION
As pointed out by Neuman (2004), cryptobiosis
involves reversible computation with a suggested
bootstrapping involving a recursive hierarchy. As a
model for analysing the behaviour of cryptobiotic
BIOSIGNALS 2008 - International Conference on Bio-inspired Systems and Signal Processing
284

systems, we propose using a Petri net, initiated by
one or more input signals, computing a number of
pathways for the induction and reactivating phases.
In computer science bootstrapping refers to a
process where an initial system activates a more
constant system maintaining fundamental skill. The
initial process may be simple, activating a complex
system step by step. Activating metabolism in a
cryptobiotic organism may cause a chain reaction
that step by step brings back the organism to its
initial conditions. To model cryptobiosis both a Petri
net setting and a time based security model is used,
i.e. the chemical reactions involved and time for
accomplishing the involved tasks.
The input stress to which cryptobiotic organisms
are exposed could be seen as an “attack” against a
system. The organism must first detect the attack
and then respond to it in order to protect the system.
Organisms with a fast enough detection and
response will fulfil the protection mechanism’s
conditions. In a dynamic environment, where
varying environmental conditions are presupposed,
the robustness of the protection system may be
modelled. This robustness is dependent of the
strength of stress factor, possible threshold functions
connected Petri net pathways, detection time and the
success of all responses during a limited amount of
time.
Currently the biological phenomenon of
cryptobiosis lacks comprehensive models for
describing involved processes, both at a general
level and within more specific system. Such models
may be found within computer science. Petri net
settings may describe the different biological aspects
and processes connected with cryptobiosis, and
allow simulation of them. By putting more realism
into the models, a future progress of both models
and simulation tools may result in a better
understanding of resource control within protection
systems, an important issue both within life science
as within computer science.
REFERENCES
Alpert, P., 2005, The limits and frontiers of desiccation-
tolerant life. Integr. Comp. Biol. 45: 685-695.
Clegg, J.S., 1986, The physical properties and metabolic
status of Artemia cysts at low water contents: the "
Water Replacement Hypothesis". In: LEOPOLD, A.
C. (ed.) Membranes, Metabolism, and Dry Organisms,
pp. 169-187. Comstock Publ. Ass., London.
Clegg, J.S., 2001, Cryptobiosis – a peculiar state of
biological organization, Comp. Biochem. and Physiol.
Part.B. vol 128 (4).
Crowe, J.H., 1971,
Anhydrobiosis: an unsolved problem.
Am. Nat. 105: 563-573.
Crowe L.M., 2002, Lessons from nature: the role of sugars
in anhydrobiosis. Comp. Biochem. Physiol. A 131:
505-513.
Goyal, K., Walton, L.J., Browne, J.A., Burnell, A.M., and
Tunnacliffe, A., 2005, Molecular anhydrobiology:
identifying molecules implicated in invertebrate
anhydrobiosis. Integr. Comp. Biol. 45: 702-709.
Guidetti, R. and Jönsson, K.I.,, 2002, Long-term
anhydrobiotic survival in semi-terrestrial
micrometazoans. J. Zool. 257: 181-187.
Guppy, M., 2004, The biochemistry of metabolic
depression: a history of perceptions, Comp. Biochem.
and Physiol. Part.B. vol 139 (3).
Heiner, M., Koch, I. and Will J., 2004, Model validation
of biological pathways using Petri nets – demonstrated
for apoptosis. Biosystems 75 p. 15-28.
Keilin, D., 1959, The problem of anabiosis or latent life:
history and current concept. Proc. R. Soc. Lond. B.
150: 149-191.
Neuman; Y., 2004, Meaning making in the immune
system, Perspect. Biol. Med. 47.
Neuman, Y., 2006, Cryptobiosis: A new theoretical
perspective, Progress in Biophysics and Molecular
Biology 92.
Reddy,V.N., Mavrovouniotis, M.L., Liebman, M.N., 1993,
Petri net representation in metabolic pathways.,
Proceedings of the First International Conference on
Intelligent Systems for Molecular Biology, AAAI Press
p. 328-336.
Schill, R.O. Steinbruck, G.H.B., and Köhler, H-R, Stress
2004, gene (hsp70) sequences and quantitative
expression in Milensium tardigradum (Tardigrade)
during active and cryptobiotic stages, Journal of
Experimental Biology 207.
Schartau, W., 1999, Time based security. Practical and
Provable Methods to Protect Enterprise and
Infrastructure, Network and Nation, Interpact Press.
Watanabe, M., 2006, Anhydrobiosis in invertebrates. Appl.
Entomol. Zool. 41: 15-31.
Watanabe, M., Kikawada, T., Minagawa, N., Yokuhiro,
F., and Okuda, T., 2002 Mechanism allowing an insect
to survive complete dehydration and extreme
temperatures, J. Exp. Biol. 205: 2799-2802
Wharton, D., 1996, Water loss and morphological changes
during desiccation of the anhydrobiotic nematode
Ditylenchus dipsaci. J Exp Biol. 199: 1085-93.
Wright, J.C., 1989, Desiccation tolerance and and
waterretentive mechanisms in tardigrades. J. exp. Biol.
142: 267-292.
Wright, J.C., 2001, Cryptobiosis 300 years on from van
Leuwenhoek: what have we learned about tardigrades?
Zool. Anz. 240: 563-582.
DESCRIBING CRYPTOBIOSIS AS A TIME BASED PROTECTION SYSTEM USING PETRI NETS
285
