A NEW APPROACH FOR WORKFLOW PROCESS DELTA
ANALYSIS BASED ON SYN-NET
Xingqi Huang, Wen Zhao and Shikun Zhang
Peking University, China
Keywords: Delta analysis, workflow, process mining, Syn-net.
Abstract: Many of today's information systems are driven by explicit process models. Creating a workflow design is a
complicated process and typically there are discrepancies between the actual workflow processes and the
processes as perceived by the management. Delta analysis aims at improving this by comparing process
models obtained by process mining from event logs and predefined ones, to measure business alignment of
real behaviour of an information system with the expected behaviour. Syn-net is a new workflow model
based on Petri-net, with the conceptual foundation synchronizer and suggesting a three-layer perspective of
workflow process. In this paper, we propose a new delta analysis approach based on the reduction rules of
Syn-net, to examine the discrepancies between the discovered processes and the predefined ones.
1 INTRODUCTION
Workflow is the computerized facilitation or
automation of a process, in whole or part where
documents, information or tasks are passed between
participants according to a defined set of rules to
achieve, or contribute to, an overall business goal
(Hollingsworth, 1995).
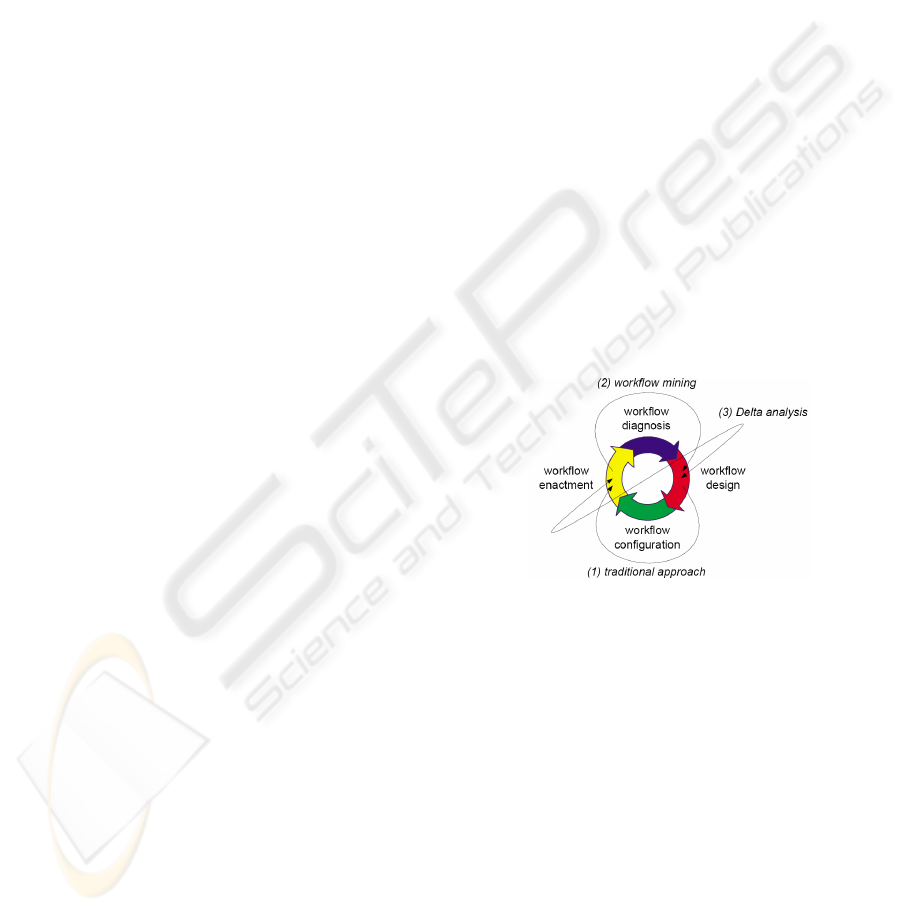
In a workflow life circle, it consists of four
phases: workflow design, workflow configuration,
workflow enactment and workflow diagnosis (Aalst
et al, 2003). In the traditional approach, well-defined
business processes should be designed before
enactment is possible and redesigned whenever
changes take place. Creating a workflow design is a
complicated time-consuming process and typically
there are discrepancies between the actual workflow
processes and the processes as perceived by the
management. In addition, nowadays workflow
technology is moving into the direction of more
operational flexibility to deal with workflow
evolution and workflow exception handling. As a
result, participants can deviate from the pre-
specified workflow design. Therefore, deviations are
natural and the current trend to develop systems
allowing for more flexibility accounts for this need.
Clearly one wants to monitor these deviations.
For example, a deviation may become common
practice rather than being a rare exception. In such a
case, the added value of a workflow system becomes
questionable and an adaptation is required.
Figure 1: Workflow life circle.
Delta analysis can be applied for analyzing
discrepancies between models defined in the design
phase and the actual executions registered in the
enactment phase. Based on the event log a process
model can be derived with process mining technique,
reflecting the observed behaviour and therefore
providing insight in what actually happened (Aalst et
al, 2003; Aalst et al, 2004; Greco et al, 2005). As
predefined model specifies how people and
organizations are assumed to work, while the
discovered one reflects how people and procedure
really work, discrepancies between both can be used
to improve the process. Also, the current trend in
workflow management is to develop systems that
allow for even more flexibility. This suggests that it
is more interesting to compare predefined process
models with “discovered” models.
480
Huang X., Zhao W. and Zhang S. (2007).
A NEW APPROACH FOR WORKFLOW PROCESS DELTA ANALYSIS BASED ON SYN-NET.
In Proceedings of the Ninth International Conference on Enterprise Information Systems - ISAS, pages 480-486
DOI: 10.5220/0002370304800486
Copyright
c
SciTePress

Workflow
log
Predefined
model
Discovered
model
Execution Process mining
Delta analysis
Figure 2: Delta analysis.
For large processes it may be difficult to
compare the predefined models and the discovered
ones. There are many ways to highlight differences
between two models in a graphical fashion.
However, most of such approaches will consider
simple “node mapping techniques” rather than
compare differences in behaviour, i.e., the focus is
on syntactical differences rather than semantic
differences (Aalst et al, 2005).
In this paper, we propose a folding approach to
highlight the discrepancies between the discovered
models and the predefine ones, using reduction rules
in Syn-net (Yuan, 2005).
The remainder of this paper is organized as
follows. Section 2 introduces the Syn-net, which is a
synchronization based workflow process model. In
section 3, we introduce process mining to discover a
process model in Syn-net from event logs, and then
present the reduction rules of Syn-net, as well as the
folding approach applying the reduction rules. In
section 4, we conclude the paper and list the future
work.
2 THE SYN-NET
Firstly, let we have a brief introduction to the Syn-
net. Here we just explain some most important
points of the model. The details of Syn-net are
explained rationally in the work of Yuan (2005).
Readers can refer to it for more information.
Syn-net is a new workflow model based on Petri-
net, with the conceptual foundation synchronizer and
suggesting a three-layer perspective of workflow
process. In Syn-net, a workflow is defined as the
formal description of a business process, including
workflow logic that describes dependences between
tasks and workflow semantics added on the logic to
describe obvious contents, as well as workflow
management to check finished tasks according to the
workflow logic and start the next task or, to select
and start the next task according to the workflow
semantics.
Figure 3: Three layer workflow model.
Workflow logic plays a decisive role in
workflow. In general, workflow logic specifies how
tasks of a business process are ordered and
disordered, i.e. how they are synchronized. The
order is derived from the causal dependences among
tasks and from organizational regulations. Besides, it
covers all possible routes for all possible cases
allowed by the business in question, i.e. it is case
irrelevant. So it is not concerned with case attributes
needed to make decisions on selective routings.
Such attributes will be introduced into the logic to
form workflow semantics. Furthermore, a task can
be executed at most once for each run of the logic.
So, iterative routing should not appear as a logic
feature. The passing of control from task to task is to
be done automatically by workflow engine since
control passing involves resource assignment to
tasks. The duty of a task is confined to the business
itself, not including business management.
The order relation among tasks is defined as
follows:
Definition 1 Order Relations among Tasks
All tasks in TASK are ordered by the nature of
the related business process. So we have a relation <,
TASKTASK
×
<
⊆
.
And we have a sub-relation <· of < : <· ⊆ < and
∈
<)',( tt
·
)'""(:" ttttTASKt <∧
<
¬
∈
∀
⇒
.
<· is the next relation among tasks. For (T
1
, T
2
)
∈
<· we say that T
2
is immediately before T
2
,
or T
2
is
immediately after T
1
. We will define workflow logic
by specifying how T
1
and T
2
, T
1
<·T
2
, are
synchronized.
The synchronizer is the central concern of
workflow logic. A place p with a local structure like
in figure
4 is called a synchronizer of pattern (a
1
, a
2
)
between T
1
and T
2
or simply a synchronizer. We
write p= (T
1
, T
2
, (a
1
, a2)). All places except start and
end places are synchronizers in Syn-net.
p
t
21
t
2m2
t
11
t
1m1
a
2
a
2
a
1
a
1
Figure 4: Synchronizer.
A NEW APPROACH FOR WORKFLOW PROCESS DELTA ANALYSIS BASED ON SYN-NET
481

In workflow logic, each transition can occur at
most once, and a synchronizer p= (T
1
, T
2
, (a
1
, a2))
can authorize the post transitions to occur only if
M(p)=a
1
× a
2
.
Definition 2 Workflow logic
A P/T system
),,,;,(
0
MWKFTP=Σ
is called
the workflow logic of (TASK, <), or WF_logic for
short, if<⋅=
}':',|)',{(
••
∈∧∈∈∃∧∈ ptptPpTtttt
,∀p
∈ P:
)1)((
0
=⇒=
•
pMp
φ
)0)((
0
=⇒≠∧
•
pMp
φ
,
and (T,<⋅) = (TASK,<⋅´).
The workflow semantics on workflow logic
denotes how to select a route for a given case based
on its attributes. Different from workflow logic,
workflow semantics is case-relevant, and it defines a
unique route for each case based on case attributes.
It specifies how conflicts in workflow logic are
resolved with case attributes, involving only those
attributes that are needed in making decision on
selective routing, while not concerned with actual
contents of tasks beyond decision-making attributes.
Returns and skips are no need to be introduced into
workflow semantics model, for the duty of workflow
semantics is only to solve the conflict in the
workflow logic and not concerned with the quality
of the task that has been done. Whether to redo or
not is the concern of workflow management, and the
actual return for redoing some tasks is judged by the
workflow engine according to the decisions of
certain participants or management rules. Such
postponed skip and returns are called implicit jumps:
jump forward and jump backward, and are dealt with
by workflow engine at runtime.
Definition 3 Workflow semantics
A C_net system
,,,,;,,( RWKFTVP=Σ
Wr, M
T
,
M
0
) is called a workflow semantics, if
(P,T;F,K,W,M
op
) is a WF_logic, where M
op
=M
0
|p,
and
:Vv ∈∀
|)(| vw
1
≤
∧|r(v)|>1 ∧ M
0
(v)=0,
:Tt ∈∀
M
T
=guard (t) + body (t).
y:=D
yΞ10
t
0
p
1
p
4
t
2
t
5
p
2
y
y<10
t
4
p
3
y:=D
t
1
y:=D
t
3
xΞΞ
x<ΞΞΞ•
x>15
x
p
0
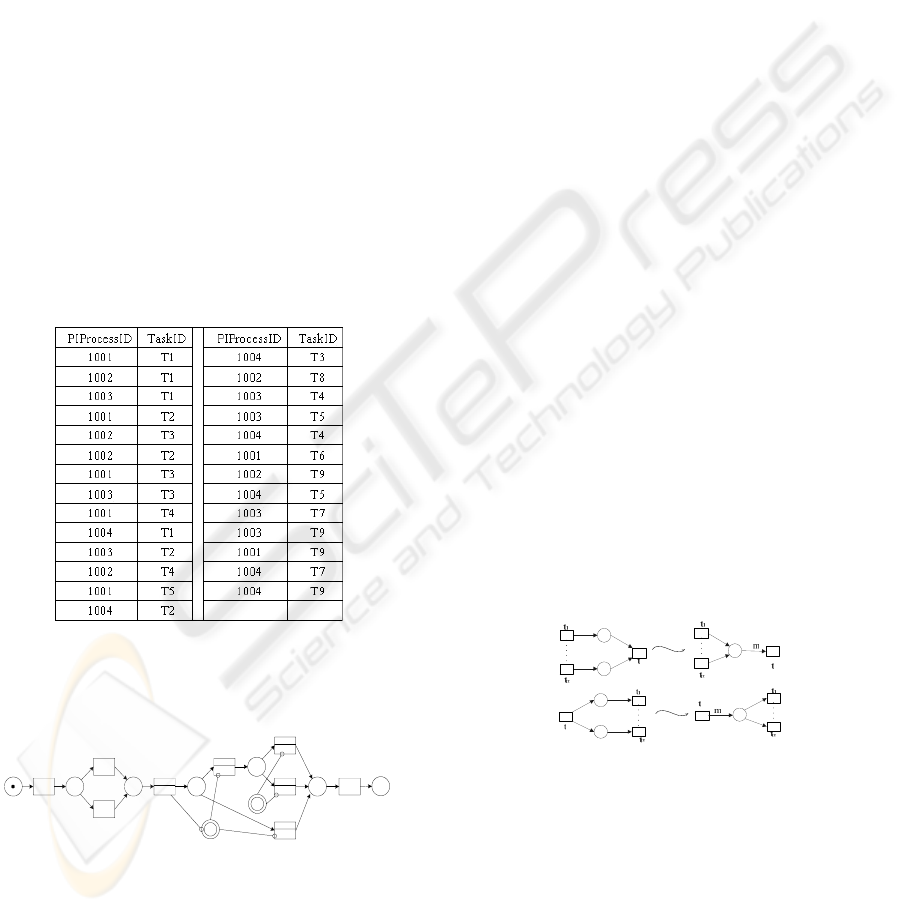
Figure 5: A process model in Syn-net.
Figure 5 is an example of the workflow logic and
semantics of a process. Here let we explain the
elements in the model. It should be noticed that
(P,T;F,K,W) has the same meaning as in P/T systems.
And (V, R, Wr, M
T
) is introduced from C_net: V is
the obvious variables of the B_form (Yuan, 2005),
and variables in V are used in guard and body of
transitions; R is the reading relation between T and
V; W
r
is the writing relation between T and V; M
T
is a
marking on transitions, consisting of a guard and a
body for
Tt
∈
; and M
0
is the initial marking of each
place in P and variable in V.
The workflow management based on workflow
semantic is a formal description of how a workflow
engine passes its control from task to task. It
resolves conflicts among routes, with given
attributes of a specific case, according to the
semantics and guards on tasks. In addition, a
management system takes care of resource
allocation for tasks, time constraint setting and other
security matters based on organization-specific
database, knowledgebase and rules for management.
In Syn-net, the management logic is given in the
dual net of workflow logic, for the place in
workflow logic is just the management task of
workflow engine.
One of the expected properties of a well-designed
Syn-net is named throughness.
Definition 4 Throughness
Let
),,,;,(
0
MWKFTP
=
Σ
be a WF_logic,
1. A marking M reachable from M
0
is a dead
marking, if
>>
¬
∈
∀
tMTt [:
. Let M
D
be the set of
all dead markings.
2. Let
}|{ ∅==
•
ppE be the set of all end places
of
Σ
. For each p in E, let M
p
be defined as
⎩
⎨
⎧
≠
=
=
ppif
ppif
pM
p
'0
'1
)'(
For all
Pp
∈
' , M
p
is called the end marking of P.
3.
Σ
is said to be through if every dead marking is
an end marking, i.e.
ED
MM ⊆
. We call this
property “Throughness”.
In Syn-net, we have proposed several reduction
rules for workflow logic analysis, to prove the
throughness of a WF_logic. If a WF_logic can be
reduced to a single place by applying the reduction
rules, then the WF_logic is dynamically through. For
delta analysis, in this paper we will show the rules
can also be applied to examine the discrepancies
between two Syn-nets.
3 DELTA ANALYSIS
For delta analysis in this paper, the predefined
process model must be a Syn-net, as well as the
ICEIS 2007 - International Conference on Enterprise Information Systems
482

process model discovered by process mining. So
firstly we present a process mining algorithm. The
algorithm receives an event log as input and returns
a Syn-net as output. It can be seen as an extension of
α-algorithm (Aalst et al, 2003; Aalst et al, 2004).
And then, we will introduce some reduction rules,
and present how to apply these rules to examine the
discrepancies between the predefined models and
discovered ones.
3.1 Using Process Mining to Obtain a
Process Model
Here we present a process mining algorithm to
discover a process model in Syn-net from event logs.
It can deal with some of the logical problems of α-
algorithm such as invisible tasks, short loops,
duplicated tasks, and so on. It is assumed that the
predefined process model is of throughness. Usually
before the workflow process is executed by
workflow engine, the model is verified according to
some rules. The constraints of Syn-net make it that
no such structure as choice and synchronization
mixed or synchronization without all its preceding
transitions fired.
The logs of workflow engine record events in
execution of processes. It is possible to assume that
each event refers to an activity, each event refers to a
case and it can have a performer, and events can
have a timestamp and are totally ordered. Also, the
logs contain data elements referring to properties of
the case and tasks. Each modification of the data
elements is also recorded.
For process mining, we need to discover a Syn-
net (P, V, T; F, K, W, R, W
r
, M
T
, M
0
)
from the logs.
In Syn-net definition, the dependence relation <• is
defined as <•={(t, t
′
)|t,t
′∈
T
∧ ∃
p
∈
P: t
∈
•
p
∧
t
′∈
p
•
}. Here the key is to find the <• relation from logs.
Let T be a set of tasks. Let σ= t
1
t
2
…t
n
∈ T* a
sequence over T of length n. ∈ , first, and last are
defined as follows: 1) t ∈ σ if and only if t ∈ {t
1
,
t
2
, … t
n
}; 2) if n ≥ 1, then first(σ) = t
1
and last(σ) =
t
n
. And next we define order relations between
transitions in the log. There are four types of order
relations: next, parallel, choice, and only possibility
of next. Let L be a log over T, and t
a
, t
b
∈T:
1. t
a
<t
b
: if there is a trace σ = t
1
t
2
t
3
…t
n
,
σ
∈
L, t
a
=t
i
and t
b
=t
i+1
2. t
a
||t
b
: if and only if t
a
<t
b
and t
a
>t
b
3. t
a
#t
b
: if neither t
a
<t
b
nor t
b
<t
a
4. t
a
<⋅t
b
: if t
a
<t
b
, and not t
b
<t
a
From workflow engine’s log, we discover relation
<⋅by identifying the next relation < in log, but not in
both direction. If t
a
<t
b
, but no t
b
<t
a
exists, it is very
likely that there is a causal dependency or
organizational regulation between t
a
and t
b
.
Let L is a workflow log, and σ is a sequence of
transitions in L. The formal description of the
algorithm is as follows:
Mining _Process (L):
1.
T
L
= {t
∈
T |
∃
σ∈
L
t
∈σ
},
2. T
first
= {t
∈
T |
∃
σ∈
L
t = first(
σ
)},
3. T
last
= {t
∈
T |
∃
σ∈
L
t = last(
σ
)},
4. X
L
= { ( A,B ) | A
⊆
T
L
∧
B
⊆
T
L
∧
∀
t
a
∈
A
∀
t
b
∈
B, t
a
<
⋅
t
b
∧
∀
t
a1
t
a2
∈
A, t
a1
# t
a2
∧
∀
t
b1
,t
b2
∈
B, t
b1
# t
b2
},
5. Y
L
= {( A,B )
∈
X
L
|
∀
( A’,B’ )
∈
X
L
, A
⊆
A’
∧
B
⊆
B’
⇒
( A,B
) = ( A’,B’ ) },
6. P
L’
= { p ( t
a
, t
b
) | t
a
∈
A, t
b
∈
B
∧
(A,B)
⊆
Y
L
}
∪
{ p( null, t
i
)
| t
i
∈
T
first
}
∪
{ p( t
o
, null) | t
o
∈
T
last
}
7. F’= { ( t, p ) | t
∈
T
L
, p
∈
P
L
’
∧
t
∈
p.pre }
∪
{ ( (p, t ) | t
∈
T
L
,p
∈
P
L
‘
∧
t
∈
p.post }
W’ = { ( f, 1 )| f
∈
F’ } K’={(p,1)| p
∈
P
L
’}
8. (P
L
,W,K)= Reduce_net(P
L
’,W’,K’);
F = { ( t, p ) | t
∈
T
L
, p
∈
P
L
∧
t
∈
p.pre }
∪
{ ( (p, t ) | t
∈
T
L
,p
∈
P
L
∧
t
∈
p.post }
9. M
T
={( t, guard, body)| t
∈
T
L
}
V={v |
∃
(t, guard, body)
∈
MT
v
∈
guard
∨
v
∈
body}
Wr = { ( t, v ) | t
∈
T
L
, v
∈
V
∧
∃
mt
∈
MT
v
∈
m
t
.body.l }
R = { ( t, v ) | t
∈
T
L
, v
∈
V
∧
∃
mt
∈
MT
v
∈
m
t
.body.r
∧
∃
mt
∈
MT
v
∈
m
t
.guard }
M
0
={(p,1 )| p
∈
{ p( null,t
i
) | t
i
∈
T
first
}
∪
{(p,0 )| p∉{ p( null ,t
i
) | t
i
∈
T
first
}
10. Syn-net (L) = (P
L
, V, T
L
, F, K, W, R, W
r
, M
T
, M
0
).
Reduce_net (P
L
’, W’, K’):
Flag=1
While Flag!=0
For each t
i
∈
T, i=1,2,..,n
P
tempi
={p|t
i
{ p| t
i
∈
p.pre
∧
p
∈
P
L
’}
P*
i
= { p| p.pre =
∪
p’.pre
∧
p.post =
∪
p’.post
∧
p’
∈
P
tempi
}
P
L1
’=P
L
’; P
Li
’=(P
Li-1
’-P
tempi
)
∪
P*
i
W
tempi
={(f,w)| f=(t,p’)
∧
t
∈∪
p’.pre
∧
p’
∈
P
tempi
}
∪
{(f,w)|f=(p’,t)
∧
t
∈∪
p’.post
∧
p’
∈
P
tempi
}
W*
i
={(f,w)| f=(t,p)
∧
p
∈
P*
i
∧
w=∑ w’
∧
(f’’,w’)
∈
W
tempi
∧
f’’
∈
(t,p’)
∧
t
∈∪
p’.pre
∧
p’
∈
P
tempi
}
W
1
’=W’; W
i
’=(W
i-1
’-W
tempi
)
∪
W*
i
K
1
’=K’; K
i
’=(K
i-1
’-{(p,k)| p
∈
P
tempi
})
∪
{(p,k)|p
∈
P*i’
∧
k=
∑ k,(p,k)
∈
K
i-1
’,p
∈
P
tempi
}
P
L
’’= P
Ln
’; W’’=W
n
’; .K’’=K
n
’
For each t
i
∈
T, i=n,n-1,…,1
P
tempi
’= { p| t
i
∈
p.post
∧
p
∈
P
L
’’}
P*
i
’ ={ p| p.pre =
∪
p’.pre
∧
p.post =
∪
p’.post
∧
p’
∈
P
tempi
’}
P
Ln
’’=P
L
’’; P
Li-1
’’=(PLi’’-P
tempi-1
’)
∪
P*
i-1
’
W
tempi
’={(f,w)| f=(t,p’)
∧
t
∈∪
p’.pre
∧
p’
∈
P
tempi
’}
∪
{(f,w)|f=(p’,t)
∧
t
∈∪
p’.post
∧
p’
∈
P
tempi
’}
W*
i
’={(f,w)| f=(t,p*i)
∧
w=∑ w’
∧
(f’’,w’)
∈
W
tempi
’
∧
f’’
∈
(t,p’)
∧
t
∈∪
p’.pre
∧
p’
∈
P
tempi
’}
W
n
’’=W’’; W
i-1
’’=(W
i
’-W
tempi-1
’)
∪
W*
i-1
’
K
n
’’=K’’; K
i-1
’’=K
i
’’-{(p,k)| p
∈
P
tempi-1
’ }
∪
{(p,k)| p
∈
P*
i-1
’’
∧
k=∑ k,(p,k)
∈
K
i
’’,p
∈
P
tempi-1
’}
A NEW APPROACH FOR WORKFLOW PROCESS DELTA ANALYSIS BASED ON SYN-NET
483
P
L
= P
L1
’’; P
L
’= P
L;
W=W
1
’’;W’=W; K=K
1
’’;K’=K
If P
tempi
=Ø
∧
P
tempi
’ =Ø then Flag=0;
Return (P
L
, W, K);
The Main idea of our algorithm is as follows.
Firstly, we define the first and last transitions.
Secondly, we construct X
L
which is the set of pairs
of transitions that have the <⋅ relation, and later
refine X
L
to Y
L
by taking only the largest elements
with respect to set inclusion. It assures that the
transitions that have choice relation share the
common place. Between every pair of transitions,
we build a place and arcs connecting the place and
transitions. Then the net needs to be reduced, for
places in Syn-net need to be synchronizers and the
model must meet constrains of Syn-net. It assures
that the discovered net has exact amount of places. K
and W can be computed with the information
recorded in the fourth step and rule of reduction.
Later V, W, Wr, R, M
T
and M
0
are added onto the
logic layer. The process model is discovered in (P,
V, T; F, K, W, R, W
r
, M
T
, M
0
).
Table 1: An example of event log.
With a log in table1, following the mining
algorithm we can obtain a process model in Syn-net
as in figure 6, which actually describes a business
process of Land and Resource Bureau.
T1
T2
T3
T4
T5
T6
T7
T8
T9
Y
22
Y>35
Y<=35
X
X
x
True
X:=D
Figure 6: Discovered process model.
It can deal with problems such as invisible tasks
and one-length loops. Firstly, because there is no
transition special for a routing purpose as in WF-net,
there will be no invisible task in our original process
model. Therefore, the problem with our process
mining work, that invisible task cannot be
discovered, may not stand. Secondly, there is no
loop or return in the process model presented by
Syn-net, for they are the duty of workflow
management, not the workflow logic and semantics.
However, when the process is at execution time,
actual loops may occur, or a task in model may
extend to multiple copies to be executed by different
participants. Hence the log may contain a sequent of
transitions like σ=t
1
t
2…
.t
k
t
k
. .t
n
,, which could be
called one-length loop. Obviously, with our model,
the one length loop makes no impact on the ability
of discovering. Both the original process model and
the mined one contain exactly one copy of t
k
which
is doubled in execution. Consequently, the drawback
of α-algorithm that it cannot be dealt with one-length
loop is solved.
3.2 Reduction Rules
Now we introduce some reduction rules in Syn-net
for delta analysis. These reduction rules can be
classified into two groups: one group with rules 1, 2
and 3 that do not impact transition set T, and the
other group with rules 4, 5 and 6 that reduce T.
Reduction Rule 1
For
},,{
1
11 a
ttT L
=
,
},,{
''
12
2
a
ttT L=
, we have
(a) the set of synchronizers
1
|)),1(,},{({ TtaTt
ii
∈
is
reducible to a single synchronizer (T
1
,T,(a
1
,a))
whose capacity is
aa
⋅
1
;
(b) the set of synchronizers
}|))1,(},{,{(
2
''
TtatT
jj
∈
is
reducible to a single synchronizer (T,T
2
,(a,a
2
))
whose capacity is
aa
⋅
2
,
where T is a set of tasks with
TT ⋅<
1
in (a) and
2
TT
⋅
<
in (b),
||1 Ta ≤≤
.
Figure 7: Reduction rule 1.
Reduction Rule 2
Let be T={t
1
,…,t
m
}, T
i
={t
ij
|1,…,a} for i=1,…,m,
and
∅
=
∩
ji
TT
for
j
i
≠
, p
i
=({t
i
},T
i
,(1,a)) for all i
are AND-split synchronizers, then if T belongs to a
single AND synchronizer
)),(,'','(
'
2
'
1
aaTT
with
''
TT ⊆
, {p
i
|i=1,…,m} can be reduced to
)),1(,,( aTTp
i
U
=
with
ampK ×=)(
.
ICEIS 2007 - International Conference on Enterprise Information Systems
484
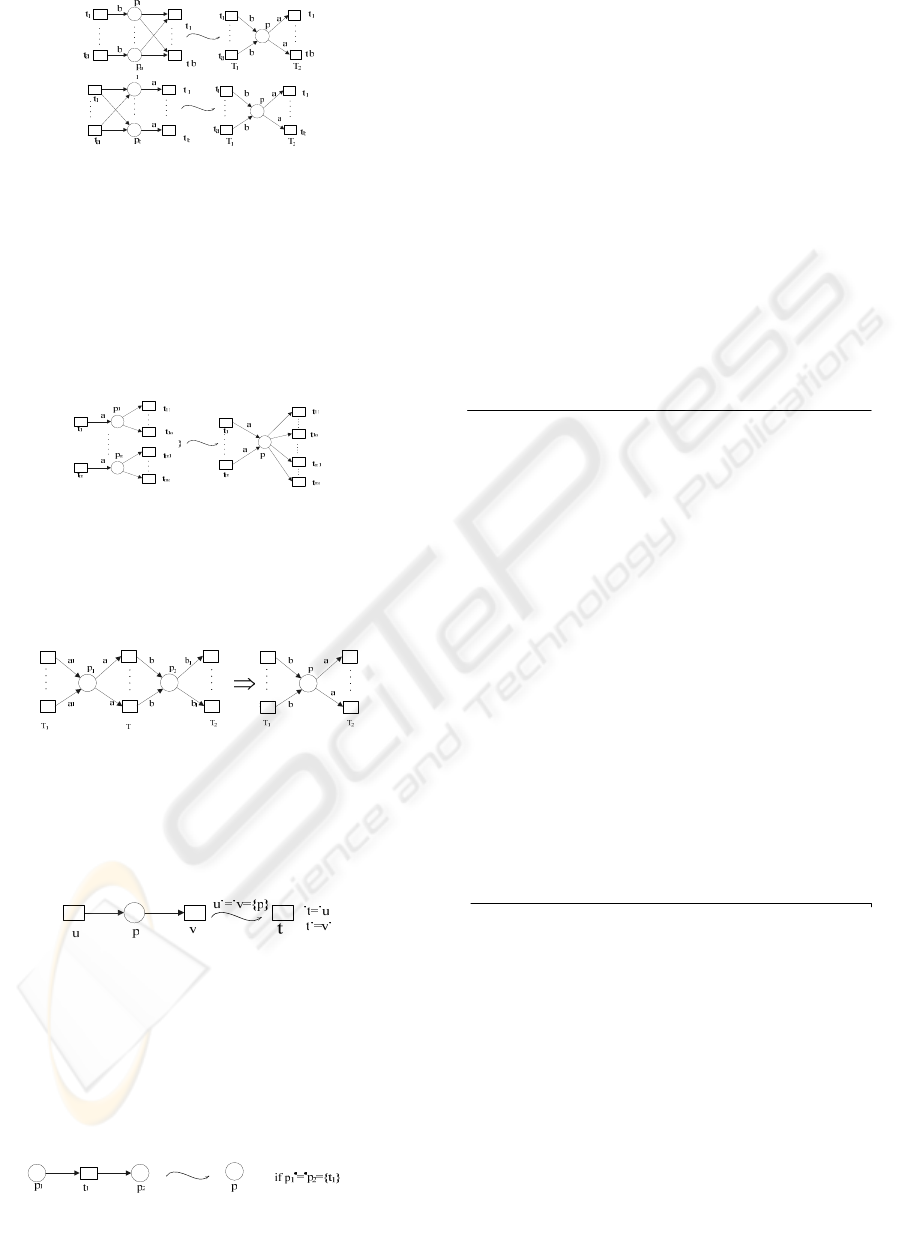
Figure 8: Reduction rule 2.
Reduction Rule 3
Let be T={t
1
,…,t
m
}, T
i
={t
ij
| j= 1,…,a} for
i=1,…,m, and
∅=∩
ji
TT for
j
i ≠ , p
i
=({t
i
},T
i
,(1,a))
for all i are AND-split synchronizers, then if T
belongs to a single AND synchronizer
)),(,'','(
'
2
'
1
aaTT
with
''TT ⊆
, {p
i
|i=1,…,m} can be
reduced to
)),1(,,( aTTp
i
∪=
with ampK
⋅
=)( .
Figure 9: Reduction rule 3.
Reduction Rule 4
Let p
1
=(T
1
,T,(a,a
1
)) and p
2
=(T,T
2
,(b
1
,b)) be
synchronizers and (p
1
,T,p
2
) is consistent, then p
1
and
p
2
can be reduced to synchronizer p=(T
1
,T
2
,(a,b)).
Figure 10: Reduction rule 4.
Reduction Rule 5
If
}{ pu =
•
and }{ pv =
•
, where p=({u},{v},(1,1)),
then ({u}, p, {v})can be reduced to a single task t
with
ut
••
= and
••
= vt .
Figure 11: Reduction rules 5.
Reduction Rule 6
If transition t and place p
1
, p
2
are satisfied with
}){(}{
1221
tppptpt =∨∅≠∧=∧∈
••••
, then p
1
and
p
2
can be reduced into one place p,
}{,
211
tppppp −∪==
•••••
. If p
1
contains tokens, p
also contains tokens.
Figure 12: Reduction rule 6.
3.3 Applying the Rules for Delta
Analysis
For large processes it may be difficult to compare
the predefined models and the discovered ones. In
this paper, we present a folding method for delta
analysis using reduction rules in Syn-net.
The central idea of delta analysis in this paper is
to fold the identical parts of the two models using
reduction rules, so as to highlight the differences
between them.
The input of the folding is the predefined process
model and discovered one, both of which are in Syn-
net. Firstly, with a dynamically through process
model A and its execution log, we apply process
mining to discover a process model named B in Syn-
net. Then, the folding works as follows:
Folding:
while(!stable1 || !stable2)
while(! stable1)
Apply rule 1- 3 to A, with transition set N;
With N of B, if
∀
t
∈
N,
∀
t
’
∈
N , t in A , t
’
in B
corresponding to t in A, has r(t)=r(t
’
) and w(t)=w(t
’
)
Apply the same rule on B with N;
if(succ)
commit reduction to A & B;
stable1count = 0; stable2 = false;
else
undo reduction to A; stable1count++;
if(stable1count==3) stable1 = true;
while(!stable2)
Apply rule 4 - 6 to A, with transition set N;
With N of B, if
∀
t
∈
N,
∀
t
’
∈
N , t in A , t
’
in B
corresponding to t in A, has r(t)=r(t
’
) and w(t)=w(t
’
)
Apply the same rule on B with N;
if(succ)
commit reduction to A & B;
stable2count = 0; stable1 = false;
else
undo reduce to A; stable2count++;
if(stable2count==3) stable2 = true;
Folding:
while(!stable1 || !stable2)
while(! stable1)
Apply rule 1 - 3 to A, with transition set N;
With N of B, if
∀
t
∈
N,
∀
t
’
∈
N , t in A , t
’
in B
corresponding to t in A, has r(t)=r(t
’
) and w(t)=w(t
’
)
Apply the same rule on B with N;
if(succ)
commit reduction to A & B;
stable1count = 0; stable2 = false;
else
undo reduction to A; stable1count++;
if(stable1count==3) stable1 = true;
while(!stable2)
Apply rule 4 - 6 to A, with transition set N;
With N of B, if
∀
t
∈
N,
∀
t
’
∈
N , t in A , t
’
in B
corresponding to t in A, has r(t)=r(t
’
) and w(t)=w(t
’
)
Apply the same rule on B with N;
if(succ)
commit reduction to A & B;
stable2count = 0; stable1 = false;
else
undo reduce to A; stable2count++;
if(stable2count==3) stable2 = true;
Figure 13: Folding Algorithm.
In the algorithm above, we alternatively apply
rules in group 1 and 2 to A and B, and with sequence
order for rules within each group, until no more
rules can be applied on both of them. Once a rule
can be applied on A, if it can also be applied on B
with the same transition set N, and for each
corresponding pair of transitions t in A and t
’
in B,
τ
∈
Ν
,
τ
’
∈
Ν
, r(t)=r(t
’
) and w(t)=w(t
’
), then commit the
reduction on both A and B, with nodes after
reduction replace the original ones, else the impact
of reduction on A must be withdrew. Then try other
rules in the group and later the other group, until
A NEW APPROACH FOR WORKFLOW PROCESS DELTA ANALYSIS BASED ON SYN-NET
485
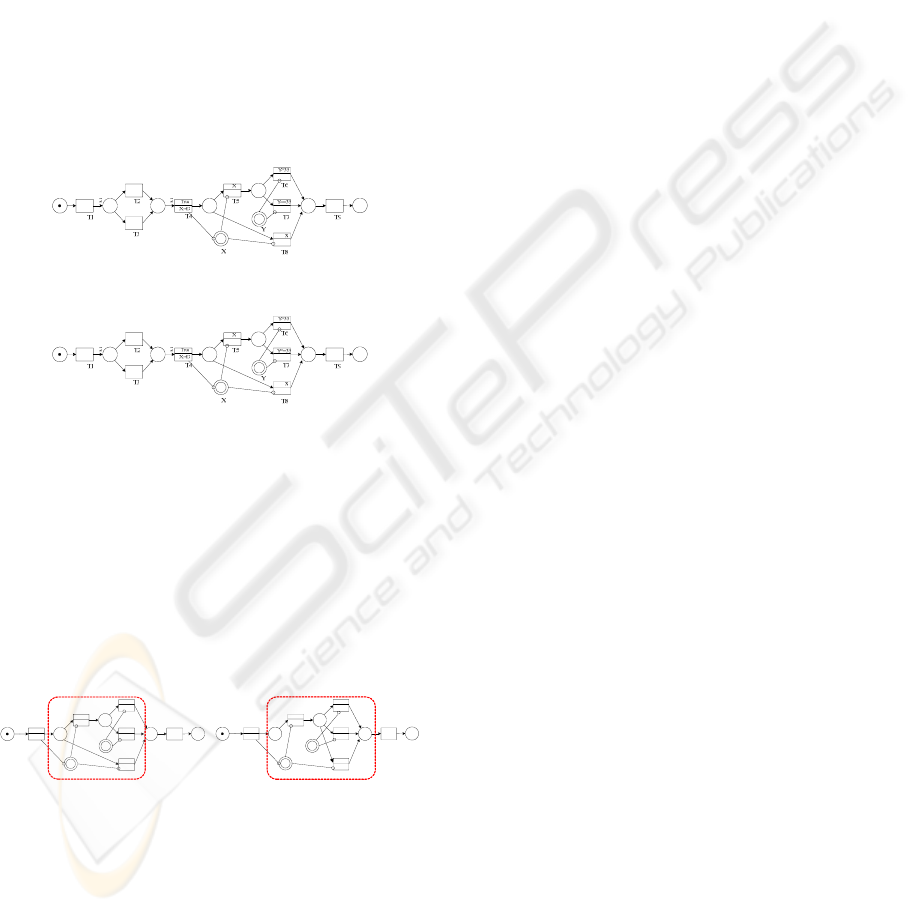
reach the fixed point, where no more rules can be
applied on both the nets. As a result, the identical
parts of both the two nets are folded, with discrepant
parts of the two nets left. If the two models are
entirely the same as each other, both of them will be
reduced to a single place, for we assume they are of
throughness.
In fact, the reduction is to ignore details
unconcerned. The same parts of the two nets are of
no importance in redesign of the business process,
because the actual behaviour is the same as
expected.
For example, figure 14 is the predefined process
model A, and figure 15 is the discovered one named
B. There is only one difference between them: in A
the transition t
8
is or-split with t
5
, and t
8
is or-split
with t
6
and t
7
in B.
Figure 14: Predefined process model.
Figure 15: Discovered process model.
Firstly the rule 4 can be applied on A, and the
rule can also be applied on B, then reduction of both
nets is committed, transitions t2, t3 and their
connected places are replaced by a single place.
Later, reduction rules can still be applied on A to
reduce it to a single place. However, because of the
discrepancy between A and B, no more rules can be
applied on both A and B for the same transition set,
leaving structures highlighting the discrepancies, as
shown in figure 16.
T4
T5
T6
T7
T8
T9
Y
Y>35
Y<=35
X
X
x
True
X:=D
T4
T5
T6
T7
T8
T9
Y
Y>35
Y<=35
X
X
¬x
True
X:=D
Figure 16: Folding.
4 CONCLUSIONS AND FUTURE
WORK
In this paper, we discussed topics of workflow
diagnosis phase in workflow life circle.
For delta analysis, firstly a process mining is
applied on the event logs to discover a process
model. Syn-net is a new workflow model with the
conceptual foundation synchronizer and suggesting a
three-layer perspective of workflow process. We
presented a process mining algorithm extending α-
algorithm, with the assumption that the predefined
model is in Syn-net and of throughness. Because of
the characteristic of Syn-net, following the algorithm
some of the drawbacks can be solved.
Since we use a folding approach for delta
analysis, we introduced some reduction rules for
folding. These rules specify how to find and fold the
identical structures of the predefined model and the
discovered one. We also presented a folding
algorithm to apply these rules, so as to highlight the
discrepancies between process models.
However, this work is far from being complete.
Since Syn-net is a new workflow model, more
researches are needed to refine the theory. For delta
analysis, reduction rules may need to be refined and
maybe some other rules will be added. Also, the
mining and folding algorithms are to be optimized to
put them into practice. Our future work will focus on
these aspects.
REFERENCES
David Hollingsworth., 1995. The Workflow Reference
Model, Document Number TC00-1003[S], Workflow
Management Coalition
W.M.P. van der Aalst, B.F. van Dongen, J. Herbst, L.
Maruster, G.Schimm, and A.J.M.M. Weijters, 2003.
Workflow Mining: A Survey of Issues and
Approaches, Data & Knowledge Engineering, Volume
47, Issue 2, 237-267. Elsevier.
W.M.P. van der Aalst, A.J.M.M. Weijters, and L.
Maruster, 2004. Workflow Mining: Discovering
Process Model from Event Logs, IEEE Transaction on
Knowledge and Data Engineering, 16(9), 1128-1142
Gianluigi Greco, Antonella Guzzo, Giuseppe Manco and
Domenico Sacca, 2005. Mining and Reasoning on
Workflows. Knowledge and Data Engineering, IEEE
Transactions, Volume17, Issue 4, 519-534
W.M.P. van der Aalst, 2005. Business alignment: using
process mining as a tool for Delta analysis and
conformance testing. Requirement Engineering 10(3),
198-211
Chongyi Yuan, 2005. Principals and Application of Petri
Nets. Publishing House of Electronics Industry. 213-
258.
ICEIS 2007 - International Conference on Enterprise Information Systems
486
