
A Design Theory for Pervasive Information Systems
Panos E. Kourouthanassis and George M. Giaglis
Department of Management Science and Technology
Athens University of Economics & Business
47A Evelpidon & 33 Lefkados St., 11362, Athens, Greece
Abstract. Pervasive Information Systems (PIS) constitute an emerging class of
Information Systems where Information Technology is gradually embedded in
the physical environment, capable of accommodating user needs and wants
when desired. PIS differ from Desktop Information Systems (DIS) in that they
encompass a complex, dynamic environment composed of multiple artefacts
instead of Personal Computers only, capable of perceiving contextual
information instead of simple user input, and supporting mobility instead of
stationary services. This paper aims at proposing a design theory for PIS. In
particular, we have employed [46]’s framework of Information Systems Design
Theories (ISDT) to develop a set of prescriptions that guide the design of PIS
instances. The design theory addresses both the design product and the design
process by specifying four meta-requirements, nine meta-design considerations,
and five design method considerations. The paper emphasises mainly on the
design theory itself and does not address issues concerning its validation.
However, in the concluding remarks we briefly discuss the activities we
undertook to validate our theoretical suggestions.
1 Introduction
Information technology (IT) artefacts are already embedded in more places than just
our desktop computers, providing innovative services in ways unimaginable in the
near past. This shift in the viewpoint of information systems (IS) is commonly
referred to as ‘post-desktop’ [21] or ‘ubiquitous’ computing [48]. This trend has fired
a shift away from computers towards computerised artefacts. A new generation of
information appliances has emerged [38], differing from traditional general-purpose
computers in what they do and in the much smaller learning overhead they impose on
the user. Instead of having IT in the foreground, triggered, manipulated, and used by
humans, nowadays we witness that IT (irrespectively whether it comprises of
computers, small sensors, or other communication means) gradually resides in the
background, monitoring the activities of humans, processing and communicating this
information to other sources and intervening should it be required. This new class of
IS is often called ‘Pervasive Information Systems’ (PIS) [9] and enables new
interaction means beyond the traditional desktop paradigm.
Specifically, DIS through their form of personal computers or other stationary
access devices, were designed to fit into an office environment and the activities
E. Kourouthanassis P. and M. Giaglis G. (2006).
A Design Theory for Pervasive Information Systems.
In Proceedings of the 3rd International Workshop on Ubiquitous Computing, pages 62-70
DOI: 10.5220/0002503700620070
Copyright
c
SciTePress

taking place there. They were designed to be efficient tools in the hands of
professionals. Thus, their practice of interaction design is directed towards this
setting. Moreover, these systems are designed for use; this means that their design and
evaluation are accomplished on the basis of some definition of their functionality and
perceived usage. Thus, designers seek a solution that satisfies the basic criteria for
usability such as efficiency in use, low error rate, and support for recovery from error,
based on a general knowledge about what to do and what not to do to meet such
criteria [16, 32]. The objective is to achieve maximum usability with respect to a
general, precise notion of use, and the design is motivated by this ambition.
Consequently, the existing design approaches for DIS follow the same rationale.
Design methods such as SSADM [47], ETHICS [31], SSM [10], or Object-Oriented
Analysis [29] to name but a few popular methods, consider systems that support
predefined tasks and in many cases assume a job or office environment. Moreover,
such methods rely on the knowledge of the designer in order to recognise potential
problems and mostly offer a generic approach to design. Also, such methods tend to
focus on details of systems, something which is possible with traditional, static
systems, but which cannot always happen for the dynamic and rich environments
supported by pervasive systems. Finally, all the traditional approaches are oriented
towards the fundamental tenets of Human-Computer Interaction: design for a specific
user, performing a specific task, in a specific domain [36].
This position paper aims at proposing a methodological approach that may
facilitate designers to develop PIS instances. Specifically, we will present a design
theory for PIS. The following section presents the design challenge of PIS. Section 3
briefly introduces the methodological framework that will be used to specify the
design theory, while section 4 presents the theory itself. The final section concludes
with a critical appraisal of the proposed design theory and its practical usefulness.
2 Information Systems Design Theories
To specify our design theory we have followed the framework of Information
Systems Design Theories (ISDT) that was first articulated by [46]. An ISDT aims at
the design of classes of Information Systems, rather than the development of specific
IS instances. To this end, design theories are prescriptive, in the sense that they
provide constructs and guidelines for the achievement of stated goals, rather than
explaining phenomena (explanatory theories) or predicting outcomes (predictive
theories). Finally, design theories are theories of procedural rationality [42], as their
objective is to prescribe both the properties that an artefact should have if it is to
achieve certain goals, and the methods of artefact construction.
According to [46], design theories have two aspects; one dealing with the product
of design (the artefact that will form the outcome of applying the design theory) and
another dealing with the process of design (i.e. the method by which the design
product can be realised). We will use this distinction to describe the components that
form an ISDT. These components are summarised in the following table.
63
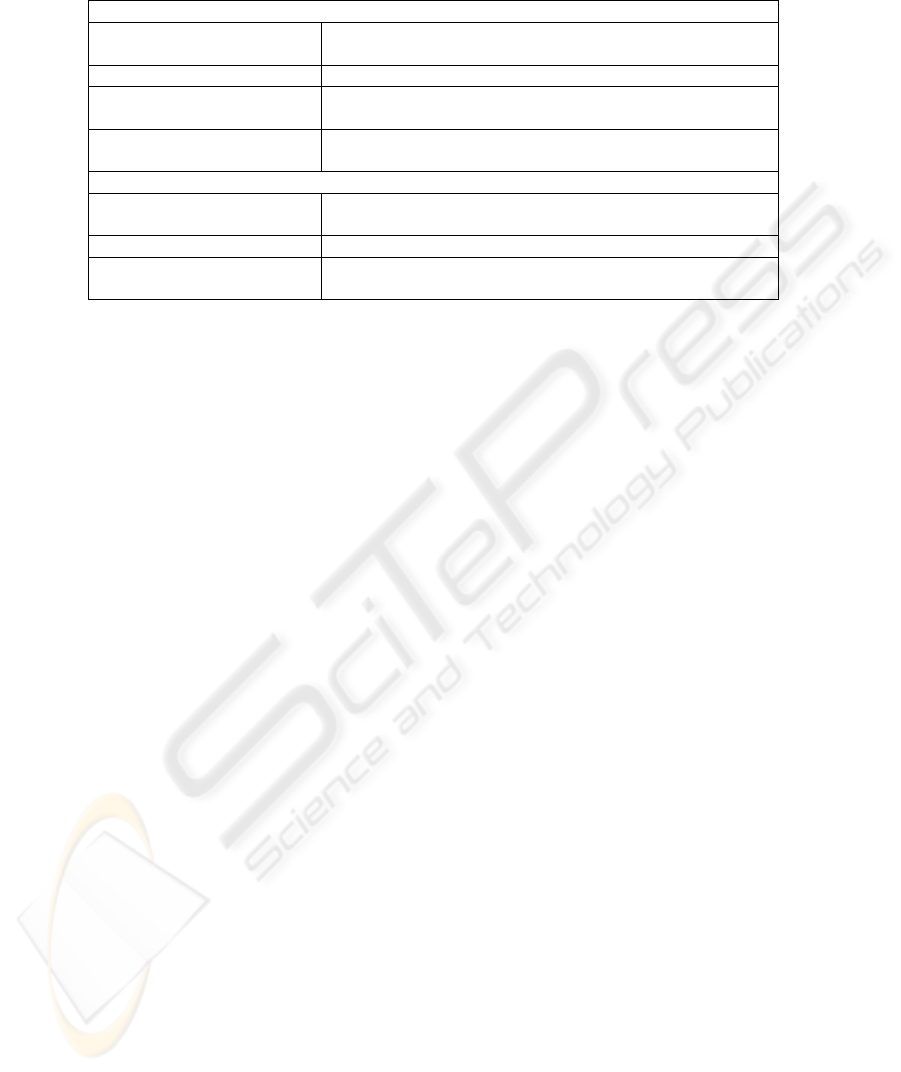
Table 1. ISDT Components.
DESIGN PRODUCT
Kernel Theories Theories from reference disciplines that govern design
requirements
Meta-Requirements The class of goals to which the theory applies
Meta-Design A class of artefacts hypothesised to meet the meta-
requirements
Design Product Hypotheses Used to test whether the meta-design satisfies the meta-
requirements
DESIGN PROCESS
Kernel Theories Theories from reference disciplines that govern the design
process
Design Method Description of procedures for artefact construction
Design Process Hypotheses Used to test whether the design method results in an artefact
consistent with the meta-design
The framework has already been used to develop design theories for, amongst
others, Executive Information Systems (EIS) [46], Decision Support Systems [22],
Group Decision Support Systems [27], Organisational Memory Information Systems
[43], Simulation Systems for IS Evaluation [15], and Emergent Knowledge Processes
[28]. The following section presents the proposed design theory for PIS.
3 A Design Theory for Pervasive Information Systems
3.1 Meta-Requirements Elicitation
The first meta-requirement refers to the profile of prospective PIS users. In the PIS
context it is highly unlike for the system designer to know in advance the types of
people who will be using the system. Take into consideration the users of the different
implementations of tour guides existing in the PIS literature [1, 5, 6, 11]; users may
range from people that are vaguely familiar with IT (mainly due to their interaction
with commonplace IT artefacts such as mobile phones) or (at extreme cases) techno-
phobic. Moreover, these types of users are opportunistic in the sense that they will use
the tour guides for a particular time frame and for a particular reason (in this example,
to augment their visiting experience). To this end, it is highly unlikely that these users
will be subject to thorough training in the system’s use as in the case of DIS users.
Conclusively, a PIS instance should support all the different user types by employing
sufficient mechanisms that enhance or facilitate user interactions with the system,
while at the same time haste users’ learning curve for using the PIS.
The second meta-requirement refers to the PIS capability to support the multitude
of different device types that may participate in the pervasive environment. [18]
distinguish among four types of devices: information access devices, intelligent
appliances, smart controls, and entertainment systems. Nevertheless, ideally a PIS
should support any device that has built-in active and passive intelligence. Therefore,
devices’ heterogeneity is the most important element that should be addressed during
the design of a PIS. Moreover, the plurality and diversity of pervasive devices
64

generate additional system requirements in terms of connectivity and integration
between them [40]. Furthermore, the design of the application and user interface
should take into account the unpredictability of end devices. In the case that an
application follows the user and moves seamlessly between devices, it is implied that
this application will have to adapt to changing hardware capabilities (different types
of pointing devices, keyboards, network types, and so on) and variability in the
available software services [3].
Designing for manipulation of contextual information, implies that a PIS should be
able to perceive relevant information of its environment (with location sensitivity and
user identity capturing being the minimum requirement as stated by [2, 12], process it,
and adapt to changes in the environment taking into account both historical and
current data. Although at present contextual information refers mainly to the users’
current location, we expect that in the near future PIS will be able to perceive
simultaneously multiple stimulants that may be contradictory one to the other. Thus,
this meta-requirement suggests that PIS should accommodate an appropriate
mechanism that will filter the different contextual information particles, process them,
and adjust their behaviour according to the information that best suits the current
occasion.
The final meta-requirement suggests that pervasive artefacts should be ‘gracefully’
embedded in the physical space. This smooth integration does not suggest that these
IT artefacts should be completely invisible to the system users, as implied by most
visionary research papers in the field [33, 41, 49, 50]. On the contrary, we follow
[37]’s considerations that pervasive technology should be governed by meaningful
presence, promoting unobtrusiveness. Thus, the challenge is to design PIS in such a
way that users perceive them as part of the environment. Universal design principles
[44] may be applied to create remembrances allowing for system usage with the
minimal distraction. Likewise, the PIS designer should also focus on the aesthetical
qualities of the pervasive artefacts [13].
3.2 Meta-Design Elicitation
The first meta-requirement clearly suggests that PIS should support opportunistic or
inexperienced users that do not have the luxury, or time, for training to the system’s
functionality. To this end, PIS designers should devise means that facilitate the
interaction of such users with the system, and minimise its learning curve. The
solution to this problem is to employ natural, easy to use and easy to learn interfaces
that facilitate a richer variety of communications capabilities between humans and
computation artefacts. At the same time, PIS designers should expect that the cases of
PIS misuse will be increased compared to DIS. This is the result of the potential PIS
users’ profile (lack of experience and/or sufficient training). Consequently, the system
design should incorporate appropriate mechanisms that minimise the degree of errors,
or guide the user in such a way that prevents errors from even occurring. Finally, PIS
should be able to perceive users’ current skill level through both the contextual
information and current system usage and adapt their functionality accordingly.
The diversity and plurality of pervasive devices poses new challenges for
information delivery applications in this environment. To meet the demands in this
heterogeneous environment, it is necessary for the information to be customized or
65

tailored according to the user's preferences, client capabilities and network
characteristics [19]. As such, PIS should incorporate a sufficient adaptation system
that can accommodate all different types of adaptations between different formats.
Already several such mechanisms have been proposed in the literature [8, 14, 17, 26,
30, 35] providing the system designer with the option to select the most appropriate
for its system requirements. Moreover, a PIS should be scalable. Scalability refers to
the ability to incrementally increase the abilities of a system, whilst maintaining, or
improving, performance [40]. As such, the issue of scalability refers mainly to
ensuring smooth and unobtrusive communication among PIS clients and backend
hardware infrastructure (such as sensors and actuators, backend systems, and so on).
Contextual management implies that sensing artefacts should be able to effectively
communicate the information they collect and process as well as trigger events that
deem necessary to support PIS users. Opposed to DIS where the user initiates the
interaction with the system, the PIS vision for invisibility and unobtrusiveness
suggests that the system is always active, continuously collecting contextual
information, and pro-acting (rather than re-acting) to the needs and demands of the
end users before they even start expressing them. Conclusively, the PIS designer
should devise an appropriate mechanism that supports proactive system operation.
Similarly, since it is extremely difficult to program each participating device and
application in the pervasive environment to receive and communicate uniformly the
information it collects, PIS designers should devise a representation format that is
efficient enough to model, process and communicate context.
The final two meta-design considerations stem from the requirement of smoothly
embedding the pervasive artefacts to the physical space. On the one hand, PIS should
be easily accessible. If designers follow the extreme suggestion to completely hide the
IT infrastructure, we might end up with a system that is completely inaccessible due
to the fact that users are unaware of how to use it or, at extreme cases, of its existence.
On the other hand, pervasive artefacts should be smoothly embedded in the physical
environment. As such, PIS designers should make sure that the systems which they
create do not conflict with or challenge the architecture of the place they will be
integrated. To reach that goal, co-operation between two previously completely
different disciplines (namely IS software engineering and civil architecture) seems to
be the logical solution. Consequently, the design of PIS should exploit the existing
material of the physical environment and gracefully embed ITin the physical world.
3.3 Design-Method Elicitation
The first design method consideration suggests that PIS designers orchestrate the
design around the informal and unstructured activities that users perform. This is also
illustrated in the functionality of various PIS implementations. For example, domestic
PIS, in their multiple instantiations, support such activities as home automation
(inventory management, light and heat adjustment, and so on), or home entertainment.
The focus on activities, as opposed to tasks, is a crucial departure from traditional
HCI design. Of course, activities and tasks are not unrelated to each other. Often an
activity will comprise several tasks, but the activity itself is more than these
component parts. The challenge in designing for activities is encompassing these
tasks in an environment that supports continuous interaction.
66

The second design method consideration suggests that prototyping through its
various forms (sketching, low-fidelity designing, and mock-ups, just to name as a
few) should be a core activity of the design process. Demonstrating prototypes to the
system users will ensure the implementation of user-friendly interfaces, as well as the
incorporation of user feedback regarding several dimensions of the system such as
usability, functionality, privacy protection, and so on. Moreover, since PIS have
significant impact to the physical environment (through the embedment of several
pervasive artefacts), prototyping may assist designers to fix functional user
requirements without implementing the PIS on a full-scale basis, thus, minimizing
implementation costs in terms of time and financial resources.
The third design method consideration suggests integrating conceptual design in
the early phases of the design process. Contextual design (CD) may be used in the
form of sketching or conceptual scenarios to demonstrate the system’s functionality to
the system’s stakeholders. Given that PIS may re-engineer the way users perform
their tasks and activities, CD may be employed as a technique that presents alternative
usage scenarios, technological solutions, or interaction techniques, so that system
users may evaluate them, and select the most user-friendly or appropriate, meeting
their goals and aspirations.
The fourth design method consideration aims at addressing issues relating to user
privacy. Indeed, context-awareness implies that the system will be able to monitor
and process personal information such as the users’ current location, activities, even
information related to the human body (e.g. users’ temperature, heartbeats, or
respiration levels). Combining these features with the capability to store this
information for future utilisation, it is not surprising that privacy protection is
considered as one of the most major properties that a PIS should take into
consideration from the very beginning of the design process with many researchers
proposing specific guidelines or models that may be applied [4, 7, 20, 25, 34].
Finally, the design of PIS should not be the concern of software engineers only.
Software engineers have the necessary skills to analyse and design a system from an
IS perspective: create entity-relationship diagrams, data-flows, large databases, select
the most appropriate technical solution to the given problem, and so on. Therefore,
they, most probably, lack the necessary skills to apply their design solution to the
physical space on an effective manner, not to mention to propose the most effective
solution based on the design problem. As such, the design team should be enriched
with additional members that may involve types of people such as architects, or
internal decorators, each providing a different perspective to the design of PIS. These
people should be involved from the early stages of the design process in order to
counsel software engineers on how to exploit environments’ smart spaces. Likewise,
they may advise them on how and where to place pervasive artefacts in an
unobtrusive, aesthetical, and possibly invisible, to the system users’, manner. Finally,
they may recommend alternative layout propositions regarding the effective
exploitation of the physical space in order to minimise hardware placement and
environment restoration costs.
67

4 Conclusions
This position paper outlined the components of a design theory for the development
of PIS. The theory consists of a set of meta-requirements, a set of meta-design
considerations, and a set of design method considerations. This research stemmed
from the lack of a consolidated framework to guide the design process of PIS. Our
intention in this paper is to present the constituting components of the proposed
design theory. As such, activities related to the validation of the design theory are
beyond the scope of this position paper, nevertheless we will briefly discuss them in
the following paragraphs.
Because ISDTs propose theoretical contributions [45, 46] we need to empirically
test their propositions. Only the accumulated weight of empirical evidence will, in
essence, establish the validity of any design theory without any doubt. In our case, the
proposed design theory has been employed for the design of a Pervasive Retail
Information System (PRIS). Specifically, we followed the theory’s prescriptions to
design and implement a PIS capable of enhancing the shopping experience in
supermarkets. The detailed design of the pervasive system has been published in [39].
To validate the propositions of the design theory we have generated a set of validation
hypotheses measuring the instance’s value and acceptance. To assess them, we
organised a field experiment in a Greek supermarket (ATLANTIK) where the PRIS
was used by supermarket shoppers to conduct part of their shopping. All research
hypotheses have been validating which indicates that the proposed design theory
results to valuable and acceptable PIS instances. The field experiment results
concerning the system’s value have been published in [23]. The field experiment
results concerning the system’s acceptance are available at [24].
The value of this research will be determined by the application of the proposed
design theory by other scholars, in their effort to design PIS instances. We believe
that this research provides an aggregated approach to describe PIS characteristics and
prescribe their development. Moreover, it represents the only consolidated approach,
to our knowledge, that investigates the problem of PIS design. In any case, the
proposed design theory aims at specifying generic design principles that should be
inherited by PIS instantiations. We decided to follow that paradigm in order to ensure
that the proposed design prescriptions are applicable to all PIS instances, irrespective
of their application domain. It is up to the PIS designers to interpret and apply these
prescriptions based on their design problem.
References
1. Abowd, G.D., Atkeson, C.G., Hong, J., Long, S., Kooper, R. and Pinkerton, M.
Cyberguide: A Mobile Context-aware Tour Guide. Wireless Networks, 3 (5) (1997) 421-
433.
2. Abowd, G.D. and Mynatt, E.D. Charting Past, Present, and Future Research in Ubiquitous
Computing. ACM Transactions on Computer-Human Interaction, 7 (1) (2000) 29-58.
3. Banavar, G. and Bernstein, A. Software Infrastructure and Design Challenges for
Ubiquitous Computing Applications. Communications of the ACM, 45 (12) (2002) 92-96.
68

4. Beckwith, R. Designing for Ubiquity: The Perception of Privacy. IEEE Pervasive
Computing, 2 (2) (2003) 40-46.
5. Bederson, B.B., Audio Augmented Reality: A Prototype Automated Tour Guide. in ACM
Conference on Human Factors in Computing (CHI '95), (New York), ACM Press (1995)
210-211.
6. Bellotti, F., Berta, R., De Gloria, A. and Margarone, M. User Testing a Hypermedia Tour
Guide. IEEE Pervasive Computing, 1 (2) (2001) 33-41.
7. Beresford, A.R. and Stajano, F. Location Privacy in Pervasive Computing. IEEE Pervasive
Computing, 2 (1) (2003) 46-55.
8. Berhe, G., Brunie, L. and Pierson, J.M., Modeling Service-Based Multimedia Content
Adaptation in Pervasive Computing. in CF'04, (Ischia, Italy) (2004).
9. Birnbaum, J. Pervasive Information Systems. Communications of the ACM, 40 (2) (1997)
40-41.
10. Checkland, P. Systems Thinking, Systems Practice. John Wiley and Sons, Chichester, UK
(1981).
11. Davies, N., Cheverst, K., Mitchell, K. and Efrat, A. Using and Determining Location in a
Context-Sensitive Tour Guide: The GUIDE Experience. IEEE Computer, 34 (8) (2001)
35-41.
12. Dey, A.K. Understanding and Using Context. Personal and Ubiquitous Computing, 5
(2001) 4-7.
13. Djajadiningrat, T., S., W., Frens, J. and Overbeeke, K. Tangible Products: Redressing the
Balance Between Appearance and Action. Personal and Ubiquitous Computing, 8 (5)
(2004) 294-309.
14. Gajos, K. and Weld, D., SUPPLE: Automatically Generating User Interfaces. in Intelligent
User Interfaces (IUI) 2004, (Funcha, Portugal) (2004).
15. Giaglis, G.M. On the Integrated Design and Evaluation of Business Processes and
Information Systems. Communications of the AIS, 2 (5) (1999).
16. Hackos, J. and Redish, J. User and Task Analysis for Interface Design. John Wiley and
Sons, New York, NY (1998).
17. Han, R., Bhagwat, P., LaMaire, R., Mummert, T., Perret, V. and Rubas, J. Dynamic
Adaptation in an Image Transcoding Proxy for Mobile WWW Browsing. IEEE Personal
Communications, 5 (6) (1998) 8-17.
18. Hansmann, U., Merk, L., Nicklous, M.S. and Stober, T. Pervasive Computing: The Mobile
World. Springer-Verlag, Berlin, Heidelberg (2003).
19. Held, A., Buchholz, S. and Schill, A., Modeling of Context Information for Pervasive
Computing Applications. in 6th World Multiconference on Systemics, Cybernetics and
Informatics (SC12002), (Orlando, FL, USA) (2002).
20. Jacobs, A.R. and Abowd, G.D. A Framework for Comparing Perspectives on Privacy and
Pervasive Technologies. IEEE Pervasive Computing, 2 (3) (2003) 78-84.
21. Jonsson, M., Context Shadow: An Infrastructure for Context Aware Computing. in
Workshop on Artificial Intelligence in Mobile Systems (AIMS) in conjunction with ECAI
2002, (Lyon, France) (2002).
22. Kasper, G.M. A theory of Decision Support System design for user calibration. Information
Systems Research, 7 (2) (1996) 215-232.
23. Kourouthanassis, P. Can technology make shopping fun? ECR Journal, 3 (2) (2004) 37-
44.
24. Kourouthanassis, P. A Design Theory for Pervasive Information Systems Department of
Management Science and Technology, Athens University of Economics and Business,
Athens, Greece (2006).
25. Langheinrich, M., Privacy by Design – Principles of Privacy-Aware Ubiquitous Systems. in
Ubicomp 2001, (Berlin, Heidelberg), Springer-Verlag (2001) 273-291.
69

26. Lei, Z. and Georganas, N.D., Context-based Media Adaptation in Pervasive Computing. in
IEEE Canadian Conference on Electrical and Computer (CCECE'01), (Toronto, Canada)
(2001).
27. Limayem, M. A design methodology for embedding decision guidance into GDSS. Group
Decision and Negotiation, 5 (2) (1996) 143-164.
28. Markus, M.L., Majchrzak, A. and Gasser, L. A Design Theory for Systems that Support
Emergent Knowledge Processes. MIS Quarterly, 26 (3) (2002) 179-212.
29. Mathiassen, L., Munk-Madsen, A., Nielsen, P.A. and Sage, J. Object Oriented Analysis and
Design. Marko Publishing, Aalborg, Denmark (2000).
30. Mohan, R., Smith, J. and Li, C.S. Adapting Multimedia Internet Content For Universal
Access. IEEE Transactions on Multimedia (1999) 104-114.
31. Mumford, E. and Weir, M. Computer Systems in Work Design - The ETHICS Method.
Associated Business Press, London (1979).
32. Nielsen, J. Usability Engineering. Academic Press (1994).
33. Norman, D.A. The Invisible Computer: Why Good Products Can Fail, the Personal
Computer Is So Complex, and Information Appliances Are the Solution. MIT Press
(1999).
34. Palen, L. and Dourish, P. Unpacking “Privacy” for a Networked World. CHI Letters, 5
(2003) 129-136.
35. Ponnekanti, S.R., Lee, B., Fox, A., Hanrahan, P. and Winograd, T., I-Crafter: A Service
Framework for Ubiquitous Computing Evironments. in UBICOMP2001, (Georgia, Atlanta)
(2001) 56-75.
36. Preece, J., Rogers, Y. and H., S. Interaction Design: Beyond Human-Computer Interaction.
Wiley and Sons, New York (2002).
37. Redstrom, J. Designing Everyday Computational Things Department of Informatics,
Goteborg University, Goteborg, Sweden (2001) 244.
38. Roussos, G. Appliance Design for Pervasive Computing. IEEE Pervasive Computing, 2 (4)
(2003) 75-77.
39. Roussos, G., Spinellis, D., Kourouthanassis, P., Gryazin, E., Pryzbliski, M., Kalpogiannis,
G. and Giaglis, G.M., Systems Architecture for Pervasive Retail. in ACM SAC Track on E-
Commerce, (2003) 350-356.
40. Saha, D. and Mukherjee, A. Pervasive Computing: A Paradigm for the 21st Century. IEEE
Computer, March (2003) 25-31.
41. Satyanarayanan, M. Pervasive Computing: Visions and Challenges. IEEE Personal
Communications, August (2001) 10-17.
42. Simon, H.A. The Sciences of the Artificial. MIT Press (1996).
43. Stein, E.W. and Zwass, V. Actualising organisational memory with Information Systems.
Information Systems Research, 6 (2) (1995) 85-117.
44. Story, M.F., Mueller, J.L. and Mace, R.L. The Universal Design File: Designing for People
of All Ages and Abilities. The Center for Universal Design, NC State University (1998).
45. Walls, J.G., Widmeyer, G.R. and El Sawy, O.A. Assessing Information System Design
Theory In Perspective: How Useful Was Our 1992 Initial Rendition? Journal of
Information Technology Theory and Application, 6 (2) (2004) 43-58.
46. Walls, J.G., Widmeyer, G.R. and El Sawy, O.A. Building an Information System design
theory for vigilant Executive Information Systems. Information Systems Research, 3 (1)
(1992) 36-59.
47. Weaver, P.L., Lambrou, N. and Walkley, N. Practical SSADM+. Pitman, London (1998).
48. Weiser, M. The Computer of the 21st Century. Scientific American, 265 (3) (1991) 66-75.
49. Weiser, M. The Computer of the 21st Century. IEEE Pervasive Computing, 1 (1) (2002)
19-25.
50. Weiser, M. Some Computer Science Issues in Ubiquitous Computing. Communications of
the ACM, 36 (7) (1993) 75-84.
70
