
Transitive Signatures Based on Bilinear Maps
⋆
Changshe Ma, Kefei Chen, Shengli Liu and Dong Zheng
Department of Computer Science and Engineering,
Shanghai Jiaotong University, China
Abstract. The notion of transitive signature, firstly introduced by Micali and
Rivest, is a way to digitally sign the vertices and edges of a dynamically growing,
transitively closed graph. All the previous proposed transitive signature schemes
were constructed from discrete logarithm, factoring, or RSA assumption. In this
paper, we introduce two alternative realizations of transitive signature based on
bilinear maps. The proposed transitive signature schemes possess the following
properties: (i) they are provably secure against adaptive chosen-message attacks
in the random oracle model; (ii) there are no need for node certificates in our
transitive signature schemes, so the signature algebra is compact; (iii) if using
Weil pairing, our signature schemes are more efficient than all previous proposed
schemes.
1 Introduction
1.1 Motivations
In a Public Key Infrasture (for short PKI) [8] system of depth n, there are many CAs,
and each user is given a chain of n certificates. Suppose two users A and B want to carry
out an authenticated and private communication, but they are not in the same domain
and authenticated by different CAs. So A must find a pass of certificates from him to
B. The length of the pass is linear in the number of CA nodes from A to B. Can this
pass be compressed, or in another word, can the length of the pass be shortened to the
length of one signature? As another example, in distributed networks [15], an object T
could never meet with a subject S, therefore S may not hold any prior evaluation of
trustworthiness of T . To get permit to access S, T should be somewhat trusted by S.
How can S evaluate the trustworthiness of T accurately and efficiently?
A transitive signature scheme can help us to solve these problems perfectly. The
concept of transitive signature, first introduced by Micali and Rivest in [12] and sub-
sequently formalized by Bellare and Neven in [4], is a way to build an authenticated
dynamically growing transitively closed graph G, edge by edge, such that:
– Transitivity. Given the signatures of two edges (i, j) and (j, k) of the graph G, it
is computationally feasible for anyone to derive a valid digital signature of edge
(i, k).
⋆
This work was partially supported under NFSC 60273049,60303026 and 60473020
Ma C., Chen K., Liu S. and Zheng D. (2005).
Transitive Signatures Based on Bilinear Maps.
In Proceedings of the 3rd International Workshop on Security in Information Systems, pages 48-56
DOI: 10.5220/0002542700480056
Copyright
c
SciTePress

– Unforgebility. It is computationally infeasible for any adversaries to forge a valid
digital signature of any edges that is not in the transitive closure
˜
G of the graph G,
even if the adversary can request the legitimate signer to digitally sign any number
of vertices and edges of his choice in an adaptive fashion.
1.2 Our Contributions
All the previous proposed transitive signature schemes were constructed from discrete
logarithm, factoring, or RSA assumption. It is standard practice in cryptography to seek
new and alternative realizations of primitives of potential interest, both to provide firmer
theoretical foundations for the existence of the primitive by basing it on alternative con-
jectured hard problems and to obtain performance improvements. In this paper, we pro-
vide two novel realizations of the transitive signature scheme BMTS-1 and BMTS-2
from bilinear maps to accomplish both of these objectives. These signature schemes
work in any groups where the Decision Diffie-Hellman problem (DDH) is easy, but the
Computational Diffie-Hellman problem (CDH) is hard. Such groups are referred as gap
groups [10]. Our transitive signature schemes BMTS-1 and BMTS-2 possess the fol-
lowing properties: Firstly, our transitive signature schemes are constructed without node
certificates, so the signature algebra is compact. Secondly, our schemes are provably se-
cure under adaptive chosen-message attack in the random oracle model. Furthermore,
if using Weil pairing over supersingular Elliptic curves, such as the signature in [3], our
transitive signature schemes are more efficient than all previous proposed schemes (as
showed by Figure 1 in section 5).
1.3 Related Works
The transitive signature scheme MTRS presented in [12] is provably secure under adap-
tive chosen-message attack assuming that the discrete logarithm problem is hard over
prime order group Z
∗
p
. In [4] Bellare and Neven proposed four transitive signature
schemes which are all provable security. Johnson et al introduced the notation of ho-
momorphic signature [9] and described several schemes that are homomorphic with
respect to useful binary operations. Context Extraction Signatures, introduced early by
[13], falls in the framework of [9]. A signature scheme that is homomorphic with re-
spect to the prefix operation is presented by Chari, Rabin and Rivest [7].
Recently, the bilinear maps have initiated some completely new fields in cryptogra-
phy, making it possible to realize some cryptographic primitives unknown or impracti-
cal [1–3,11]. In [2], Boneh introduced a new kind of digital signature named aggregate
signature which support aggregation.
The rest of the paper is organized as follows. In § 2, we give some notations and
definitions . In § 3, we describe the model of transitive signature schemes. In § 4, we
present two transitive signature schemes. In § 5, we provide security proofs and effi-
ciency analysis. In § 6, we draw a conclusion.
2 Notations and Definitions
In this section, we give some notations and definitions that will be used in the paper.
49

Throughout this paper, we let a ←− A denote a is selected from the set A, a
R
←− A
denote a is selected randomly and uniformly from the set A. Let a ←− b (b is an
element) denote a is assigned with the value of b. Let a ←− A(a
1
, a
2
, · · ·) denote a is
assigned with the value of the output of algorithm A on inputs a
1
, a
2
, · · ·. Let G
1
, G
2
and G
T
be three cyclic groups of prime order p, g
1
and g
2
be the generators of G
1
and
G
2
separately, ψ be a computable isomorphism from G
2
to G
1
with ψ(g
2
) = g
1
.
Definition 2.1 A bilinear map is a map e : G
1
× G
2
−→ G
T
with the following
properties:
Bilinear: for all u ∈ G
1
, v ∈ G
2
and a, b ∈ Z
p
, e(u
a
, v
b
) = e(u, v)
ab
;
Non-degenerate: e(g
1
, g
2
) 6= 1.
Computational Co-Diffie-Hellman (co-CDH). Given g
2
, g
a
2
∈ G
2
and h ∈ G
1
com-
pute h
a
∈ G
1
. An algorithm A has advantage ε in solving co-CDH problem if
Adv co-CDH
G
1
,G
2
A
= Pr[A(g
2
, g
a
2
, h) = h
a
] ≥ ε.
The probability is taken over the choice of a, h, and A’s coin tosses. An algorithm A
(t, ε)-breaks Computational co-Diffie-Hellman on G
2
and G
1
if A runs in time at most
t, and Adv co − CDH
G
1
,G
2
A
is at least ε. When G
1
= G
2
and g
1
= g
2
, these problem
reduce to the standard CDH [10].
Definition 2.2. Two groups (G
1
, G
2
) are a (t, ε)-bilinear group pair for co-Diffie-
Hellman if there exists a bilinear map e : G
1
× G
2
−→ G
T
and no algorithm (t, ε)-
breaks Computational co-Diffie-Hellman on them.
q-co-Weak Computational Diffie-Hellman Problem (q-co-WCDH).The q-co-WCDH
problem is defined as follows: given q + 2-tuple (g
1
, g
2
, g
x
2
, ..., g
x
q
2
) as input where
ψ(g
2
) = g
1
, output g
1
x
1
∈ G
1
. An algorithm A has advantage ε in solving q-co-WCDH
problem if
Adv q-co-WCDH
G
1
,G
2
A
= Pr[A(g
1
, g
2
, g
x
2
, ..., g
x
q
2
) = g
1
x
1
] ≥ ε.
The probability is taken over the choice of g
1
, g
2
and x ∈ Z
∗
p
, and A’s coin tosses.
3 Transitive Signature
All graphs in this paper are undirected. A graph G = (V, E) is said to be transitively
closed if all nodes i, j, k ∈ V such that (i, j) ∈ E and (j, k) ∈ E, it also holds that
(i, k) ∈ E: or in other words, edge (i, j) ∈ E whenever there is a path from i to j
in G. For a graph G = (V, E), its transitive closure is the graph
˜
G = (V,
˜
E), where
(i, j) ∈ E iff there is a path from i to j in G. Note that the transitive closure of any
graph G is a transitively closed graph.
Definition 3.1. A transitive signature scheme T S = (TKG, TSign, TVf, Comp) is
specified by four polynomial-time algorithms described as follows:
TKG the key generation algorithm, takes input 1
k
and returns a pair (tpk, tsk) consist-
ing of a public key and the matching private key.
TSign the signing algorithm, takes input the private key and nodes i, j ∈ V , and
returns a the original signature of edge (i, j) relative to tpk.
50

TVf the verification algorithm, given tpk, nodes i, j ∈ V , and a candidate signature σ,
verifies if σ is a valid signature of edge (i, j), returns 1 if so, otherwise returns 0.
Comp the composition algorithm, given tpk, nodes i, j, k ∈ V , where i < j < k,
the values σ
1
(the valid signature of edge (i, j)) and σ
2
(the valid signature of edge
(j, k)), then computes a value σ according the above given data. if σ is a valid
signature of edge (i, k), returns 1, otherwise returns a symbol ⊥ to indicate failure.
4 Proposed Transitive Signature Schemes
In this section we describe two bilinear transitive signature schemes via bilinear maps.
Initially, the systems need run a setup procedure to generate and publish the following
system parameters:
- a undirected graph G = (V, E),
- three cyclic groups G
1
, G
2
, G
T
of prime order p,
- generators g
1
and g
2
of G
1
and G
2
separately,
- a computable isomorphism ψ from G
2
to G
1
with ψ(g
2
) = g
1
,
- a computable bilinear map e : G
1
× G
2
−→ G
T
, and
4.1 The Scheme BMTS-1
Let H : {0, 1}
∗
−→ G
1
be a full domain hash function[6]. Then, our transitive signa-
ture scheme BMTS-1=(TKG, TSign, TVf, Comp) is defined as follows:
TKG given 1
k
, pick random x
R
←− Z
p
,and compute v ←− g
x
2
. It outputs (tpk, tsk)
←− (v, x).
TSign it maintains the state V which initially is empty. Suppose Node is the set of
integers indexing all the nodes in graph G, then V ⊂ Node represents queried
nodes. When asked to produce a signature on edge (i, j), it does as follows:
TVf on input tpk = v, and a transitive signature σ, it does as follows:
The T Sign algorithm:
If j < i Then swap i, j
If i /∈ V Then V ←− V ∪ {i}
If j /∈ V Then V ←− V ∪ {j}
δ = (H(i)H(j)
−1
)
tsk
return σ = (i, j, δ)
The T V f algorithm:
parse σ as i, j, δ
If i /∈ V ∨ j /∈ V Then return 0
Else if e(δ, g
2
) = e(H(i)H(j)
−1
, tpk)
Then return 1
Else return 0
Comp Given two valid transitive signatures σ
1
= (i, j, δ
1
) and σ
2
= (j, k, δ
2
), sup-
pose i < j < k, if not so, we can swap the sequence of i, j, k. Calculate δ = δ
1
δ
2
and output δ as the transitive composition.
4.2 The Scheme BMTS-2
The above proposed scheme needs a MapToPoint[3] hash function H : (0, 1)
∗
−→ G
1
which is probabilistic algorithm described in [3]. Now we introduce another transitive
51

signature scheme BMTS-2 which is more efficient than BMTS-1 as it uses a regular
cryptographic hash function H
1
: (0, 1)
∗
−→ (0, 1)
l
rather than a MapToPoint hash
function. This transitive signature is constructed by applying another short signature
scheme[14]. The transitive signature scheme BMTS-2 is defined as follows.
TKG given 1
k
, pick random x
R
←− Z
p
,and compute v ←− g
x
2
. It outputs (tpk, tsk) ←−
(v, x).
TSign T Sign maintains the state V which initially is empty. Suppose Node is the set
of integers indexing all the nodes in graph G, then V ⊂ Node represents queried
nodes. When asked to produce a signature on edge (i, j), it does as follows:
TVf on input tpk = v, and a transitive signature σ, it does as follows:
The T Sign algorithm:
If j < i Then swap i, j
If i /∈ V Then V ←− V ∪ {i}
If j /∈ V Then V ←− V ∪ {j}
δ = g
H
1
(i)+tsk
H
1
(j)+tsk
1
return σ = (i, j, δ).
The T V f algorithm:
parse σ as i, j, δ
If i /∈ V ∨ j /∈ V Then return 0
If e(δ, g
H
1
(j)
2
tpk) = e(g
1
, g
H
1
(i)
2
tpk)
Then return 1
Else return 0
Comp Given two valid transitive signatures σ
1
= (i, j, δ
1
) and σ
2
= (j, k, δ
2
), sup-
pose i < j < k, if not so, we can swap the sequence of i, j, k. Calculate δ = δ
1
δ
2
and output δ as the transitive composition.
5 Security and Efficiency
5.1 Security Definition of Transitive Signature Scheme
Associated to the transitive signature scheme T S = (TKG, T Sign, T V f, Comp), the
adversary F and security parameter k ∈ N is an experiment defined as follows:
Experiment :Exp
tu−cma
T S,F
(k)
H ←− Ω
(tpk, tsk) ←− T K(1
k
)
(i
′
, j
′
, σ
′
) ←− F
T Sign(tsk,·,·)
(tpk)
If T V f (i
′
, j
′
, σ
′
) = 1 ∧ i
′
, j
′
∈ V ∧ (i
′
, j
′
) /∈
˜
E Then return 1
Else return 0
This experiment begins by choosing the appropriate hash function H in the hash func-
tion family Ω and running T KG on input 1
k
to get keys (tpk, tsk). It then runs F, pro-
viding this adversary with input tpk and oracle access to the function T Sign(tsk, ·, ·).
The oracle is assumed to maintain states or toss coins as needed. Eventually, F will out-
put a triple (i
′
, j
′
, σ
′
). Let E be the set of all edges that F made oracle query i, j, and let
V be the set of all vertices i such that i is adjacent to some edge in E and
˜
G = (V,
˜
E)
be the transitive closure of G. The advantage of F in its attack on T S is defined for by
Adv
tu−cma
T S,F
= Pr(Exp
tu−cma
T S,F
(k) = 1)
Definition 5.1.Given the security parameter k ∈ N , we say that a forger F (t, q
H
, q
s
, ε,
k)-breaks the transitive signature scheme TS if the function Adv
tu−cma
T S,F
is at least ε(k)
52

for any adversary F which runs in time at most t(k); makes at most q
H
(k) queries to
the hash function and at most q
S
(k) queries to the signing oracle. A transitive signature
scheme T S is (t, q
H
, q
S
, ε, k)-transitively unforgeable under adaptive chosen-message
attack if no forger (t, q
H
, q
s
, ε, k)-breaks it.
5.2 Security Proof
We state the security of the transitive signature scheme BMTS-1 as following theorem.
Theorem 1 If (G
1
, G
2
) is a (t
′
, ε
′
)-bilinear group pair for co-Diffie-Hellman, with
each group of order p, with respective generators g
1
and g
2
, with an isomorphism ψ
computable from G
2
to G
1
. Then the transitive signature scheme BMTS-1 is (t, q
H
, q
S
, ε,
k)-transitively unforgeable under adaptive chosen-message attack for all t and ε satis-
fying
ε ≥ e
2
(q
S
(k) + 1) · ε
′
and t ≤ t
′
− C
G
1
(q
H
(k) + 3q
S
(k) + 4) − q
H
(k) − 3q
S
(k) − 5,
Where e is the base of natural logarithms, and exponentiation and inversion on G
1
take
time C
G
1
, k ∈ N is the security parameter.
proof. Assume that F is a forger algorithm that (t, q
H
, q
S
, ε, k)-breaks the signature
scheme. We will use F as a subroutine to construct an algorithm that (t
′
, ε
′
)-breaks the
co-CDH problem in (G
1
, G
2
).
Given a challenge (y, g
2
, g
a
2
), where y ∈ G
1
and g
2
∈ G
2
. Its goal is to output
y
a
∈ G
1
. Algorithm A simulates the challenger and does experiment Exp
tu−cma
T S,F
with
the forger F as follows.
Setup. A constructs tpk ←− g
a
2
, and gives the forger F the generator g
2
and tpk.
Hash Query. At any time the forger F can query the random oracle H about the node
i. To respond to these queries, A maintains a set V which contains all nodes queried
by F, and a list L of tuples < i, h
(i)
, b
(i)
, r
(i)
> as explained below. They are initially
empty. When F queries the oracle at the node i, algorithm A responds as described in
the following function H
Query(i).
Signatures Queries. A answers F’s signature queries on edge (i, j) as described in the
following function T Sign Query(i, j).
Function H
Query(i)
If i ∈ V Then return h
(i)
Else
V ←− V ∪ {i}
r
(i)
R
←− {0, 1}
b
(i)
R
←− Z
p
h
(i)
←− y
r(i)
· ψ(g
2
)
b
(i)
∈ G
1
L ←− L ∪ {(i, h
(i)
, b
(i)
, r
(i)
)}
return h
(i)
Function T Sign Query(i, j)
If i /∈ V Then H Query(i)
If j /∈ V Then H Query(j)
If r
(i)
6= r
(j)
Then abort
Else if i < j
Then return ψ(g
a
2
)
b
(i)
−b
(j)
Else return ψ(g
a
2
)
b
(j)
−b
(i)
Note: In hash query function H
Query(i), Pr[r
(i)
= 1] = 1/(q
s
(k) + 1)).
53

Output: Let F’s forgery be (i
′
, j
′
, δ
′
). Let E be the set of edges for which F queried a
signature and let
˜
G = (V,
˜
E) be the transitive closure of graph G = (V, E). A performs
the following series of checks, aborting if one of them is true.
If T V f (tpk, i
′
j
′
, δ
′
) 6= 1
|
{z }
B
2
Then abort
Elese if {i
′
, j
′
} ∈
˜
E
|
{z }
B
3
Then abort
Else if r
(i
′
)
− r
(j
′
)
= 0
|
{z }
B
4
Then abort.
If A does not abort, it calculates and outputs the required y
a
as:
y
a
←− (δ
′
)
r
(i
′
)
−r
(j
′
)
· ψ(g
a
2
)
(b
(j
′
)
−b
(i
′
)
)(r
(i
′
)
−r
(j
′
)
)
This completes the description of algorithm A. It remains to show that A solves the
instance of the co-CDH problem in (G
1
, G
2
) with advantage at least ε
′
. To do so, we
analyze the following event needed for A to succeed:
B
1
: A does not abort as a result of any of F’s signature queries.
Consequently, the advantage of A is simply the probability of A not aborting during the
experiment:
Adv co − CDH
G
1
,G
2
A
= Pr[B
1
∧
¯
B
2
∧
¯
B
3
∧
¯
B
4
]
= Pr[
¯
B
4
|B
1
∧
¯
B
2
∧
¯
B
3
] · Pr[
¯
B
2
∧
¯
B
3
|B
1
] · Pr[B
1
] (1)
In the following, we will give a lower bound for each of these terms.
(1) It is obviously that
Pr[B
1
] = Pr[A asked for signatures only on edges {i, j} with r
(i)
= r
(j)
]
≥ ((1 − 1/(q
S
(k) + 1))
2
+ 1/(q
S
(k) + 1)
2
)
m
≥ (1 − 1/(q
S
(k) + 1))
2q
S
(k)
(2)
(2) The public key given to F is from the same distribution as public keys generated by
algorithm T KG. Responses to hash queries are as in the real attack since each response
is uniformly and independently in G
1
. Since A did not abort as results of F’s signature
queries, all its responses to those queries are valid. Therefore, A will produce a valid
and nontrivial transitive signature forgery with probability at least ε. Hence
Pr[
¯
B
2
∧
¯
B
3
|B
1
] ≥ ε (3)
(3) Events B
1
and
¯
B
2
∧
¯
B
3
have occurred, and F has generated a nontrivial signature
forgery (i
′
, j
′
, δ
′
). If F asked for a signature under key tpk on some edges with one of
their nodes is i
′
, in which case the probability of r
(i
′
)
= 0 equals that of a hash query
with r
(i)
= 0, or it didn’t, then r
(i
′
)
= 0 with probability 1 − 1/(q
S
(k) + 1). So the
probability of r
(i
′
)
= 0 is at least 1 − 1/(q
S
(k) + 1). Also does node j
′
. Hence
Pr[
¯
B
4
|B
1
∧
¯
B
2
∧
¯
B
3
] ≥ 2/(q
S
(k) + 1) · (1 − 1/(q
S
(k) + 1)) (4)
54
We use the bounds from equations (2), (3) and (4) in equation (1). Algorithm A pro-
duces the correct answer with probability at least (1 −
1
q
S
(k)+1
)
2(q
S
(k)+1)−1
·
1
q
S
(k)+1
·
ε ≥
ε
e
2
·(q
S
(k)+1)
≥ ε
′
as required. Thus ε ≥ e
2
(q
S
(k) + 1) · ε
′
. Obviously, algorithm
A’s running time is at most t + C
G
1
(q
H
(k) + 3q
S
(k) + 4) + q
H
(k) + 3q
S
(k) + 5 ≤ t
′
.
This completes the proof of Theorem 1.
The security of the transitive scheme BMTS-2 is described as the following theorem.
Theorem 2 If (G
1
, G
2
) is a group pair for q-co-WCDH problem. Then the transitive
signature scheme BMTS-2 is transitively unforgeable under adaptive chosen-message
attacks in the random oracle model.
proof. The proof of this theorem is the same as that of theorem 1. So it is unnecessary
to give a full description.
5.3 Efficiency
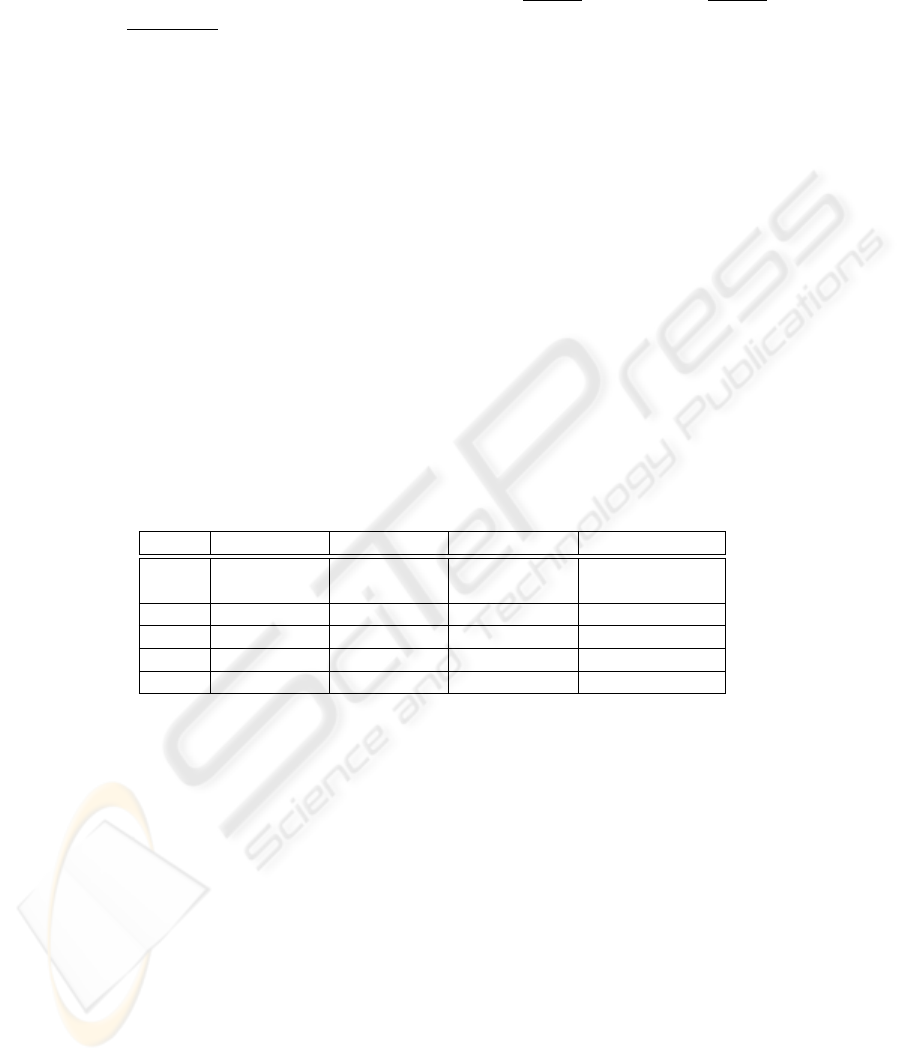
We will analyze the efficiency of BMTS-1 from the costs and signature size. Figure 1
gives us a detail comparison amongst transitive signature schemes. With regard to the
costs, we are interested in the computational cost of signing an edge; the computational
cost of verifying a candidate signature of an edge; the computational cost of composing
two edge signatures to obtain another. As showed in figure 1, whether the costs of com-
putation or the size of signature, our scheme is more efficient than all other schemes. If
using Wail pairing, the advantage of our scheme can be obviously known.
Scheme Signing Verification Composition Signature size
MRTS 2 sig. + 2 exp. 1 exp. 2 adds in Z
q
2 sig. + 2 points + 2
points
FBRS-1 2 stand.sigs O(|N|
2
) ops O(|N|
2
) ops 2 sig. + 3 points
FBRS-2 4 sqr. in Z
∗
N
O(|N|
2
) ops O(|N|
2
) ops 1point in Z
∗
N
BMTS-1 1 exp. in G
1
2 bms. O(|p|
2
) ops 1 point in G
1
BMTS-2 1 exp. in G
1
2 bms. 2 exp. O(|p|
2
) ops 1 point in G
1
Fig.1. Comparisons amongst transitive signature schemes. Abbreviations used are: “exp.” for
an exponentiation in the group; “sqr.” for a square root computation modulo N ; “ops” for the
number of elementary bit operations in big-O notation; “bm.” for bilinear map computing.
6 Conclusion
Bilinear maps have many applications in cryptographic fields. In this paper, we in-
troduced two efficient and provable secure transitive signature schemes from bilinear
maps. The proposed transitive signature schemes possess several properties such as: (i)
no need node certification, (ii) short signature, (iii) compact signature algebra. The pre-
viously presented transitive signature schemes cannot achieve all the above properties.
We also prove that our schemes are transitively unforgeable under adaptive chosen-
message attack in the random oracle model.
55

References
1. D. Boneh and M. Franklin. Identity-based encryption from the Weil pairing. SIAM, J. Com-
puting, 32(3), pp.583-615, 2003.
2. D. Boneh, C. Gentry, B. Lynn, H. Shacham, Aggregate and verifiably encrypted signatures
from bilinear maps. Advances in Cryptology–EUROCRYPT 2003, Lecture Notes in Com-
puter. Science, Vol. 2656, pp.416-432, Springer, 2003.
3. D. Boneh, B. Lymn and H. Shacham. Short signatures from the Weil pairing. Prodeedings of
Asiacrypt 2001, Vol. 2248, Lecture Notes in Computer Science, pp.514-532, Springer, 2001.
4. M. Bellare and G.. Neven. Transitive signatures based on factoring and RSA. Advances in
Cryptology - ASIACRYPT’02, Lecture Noted in Computer Science Vol.2501, pp.391-414,
Springer, 2002.
5. M. Bellare and P. Rogaway. Random oracles are practical: A paradigm for designing efficient
protocols. Proceeding s of the 1st Annual Conference on Computer and Communications
Security, ACM. pp.62-73, 1993.
6. J.-S. Coron, On the exact security of full domain hash. Advances in Cryptology–CRYPTO
2000, Lecture Notes in Computer Science, Vol.1880, pp.229-235, Springer, Berlin, 2000.
7. S. Chari, T. Rabin and R. Rivest. An efficient signature scheme for route aggregation.
http://theory.lcs.mit.edu/ rivest/publications.html, 2002.
8. R. Housley, M. Ford, W. Polk, D.solo. Internet X.509 Public Key Infrastructure: Certificate
and CRL Profile. http://www.ietf.org/rfc.html, January 1999.
9. R. Johnson, D. Molnar, D. Song and D. Wagner. Homomorphic signature schemes. Topics
in Cryptology - CT-RSA ’02, Lecture Notes in Computer Science Vol.2271, pp.244-262,
Springer, 2002.
10. A. Joux and K. Nguyen. Separating decision Diffie-Hellman form Diffie-Hellman in crypto-
graphic groups. Cryptology ePrint Archive, Report 2001/003, 2001. http://eprint.iacr.org/.
11. Changshe Ma and Kefei Chen, Publicly verifiable authenticated encryption. Electronics Let-
ters, vol 39, pp.281-282, 2003.
12. S. Micali and R. L. Rivest. Transitive signature schemes. Topics in Cryptology - CT-RSA
’02, Lecture Notes in Computer Science Vol.2271 , pp.236-243, Springer, 2002.
13. R. Steinfeld, L. Bull and Y. Zheng. Content Extraction signatures. Information security and
cryptology-ICI 2001, Lecture Notes in Computer SCience Vol.2288, pp.285-304, Spring-
Verlag, 2002.
14. Fangguo Zhang, Rei Safavi-Naini, and Willy Susilo. An Efficient Signature Scheme from
Bilinear Pairings and Its Application. Public Key Cryptography - PKC 2004, Lecture Notes
in Computer Science, volume 2947, pages 277-290. Springer, 2004.
15. H.Zhu and B. Feng, Robert H. Deng. Computing of Trust in Distributed Networks.
http://www.iacr.org, eprint.
56
