
Е-LIBRARY TECHNICAL SOLUTION:
AN EXAMPLE OF ETU ”LETI”
Yury Isaev
Center of Information Technologies, Electrotechnical University “LETI”, Saint-Petersburg, Russian Federation
Alexey Niskovsky
Networking Technologies Office, Electrotechnical University “LETI”, Saint-Petersburg, Russian Federation
Keywords: e-library network environment, application management, policy management, user access management,
network architecture.
Abstract: The practical experience of forming the e-library network environment of St. Petersburg Electrotechnical
University “LETI” library is discussed. The major related problems are considered: managing library
applications, managing user data, development and replication of software program configuration of library
staff and users workstations, managing Internet access for library staff and users. The principal technologies
used to solve these problems are described in brief.
1 INTRODUCTION
The ETU “LETI” corporate network – ETUnet – is
rather complicated computing network distributed
around the university campus. It is heterogeneous
because a lot of different hardware, software, and
protocols are used inside.
There are about 60 servers presented in the
ETUnet at the moment, about 20 of them designated
for centralized access and usage. These 20 servers
are working under the Novell NetWare platform. All
these allow the network of such level to support
high-level productivity, secure access, data safety,
scalability, etc. The number of the client’s
workstations is about 1000.
The ETUnet backbone was build on fibre optic
cable with 2300 meters length. The FDDI is used for
data transmission across the backbone.
The ETUnet is connected to the Russian
University Network (RUNNet) and Internet via fibre
optic channel with 10 Mbits per second throughput.
The university library divisions and offices are
distributed around the campus. They are placed in
different buildings and the distance between them is
wide. All these pre-define the set of technologies,
hardware, and software that was used for university
e-library network environment creation.
In the ETUnet the Novell Directory Services is
used. All network resources and services including
allowed for library are integrated into NDS. The
network management, user administration, and
service access can be done from one control point
via NDS.
2 THE GOALS OF THE
E-LIBRARY NETWORKING
ENVIRONMENT CREATION
”The networking environment” means a total
combination of software and hardware resources,
which gives a user all the complex of means for the
most effective using of the computing network
resources, and an administrator of the computing
network gets the complex of means for users
administration and control. In this case, speaking
about the networking environment of the ETU
“LETI” library, we mean resources which are given
to different users of the library for usage by the
university corporative computing network
administrator.
The goals of the e-library networking
environment creation are mostly in harmony with
285
Isaev Y. and Niskovsky A. (2004).
Ð ¸T-LIBRARY TECHNICAL SOLUTION: AN EXAMPLE OF ETU ”LETI”.
In Proceedings of the Sixth International Conference on Enterprise Information Systems, pages 285-288
Copyright
c
SciTePress

those goals that cause the wide using of the
information technologies in our life:
The integrated information environment creation
to ensure joint and effective work of the staff.
Provision of the “refusal steady” guided access
of the library staff to supplements and databases
used in the library work.
Provision of firm keeping of the library
databases (keeping from the unauthorized access,
technical breakdowns etc.).
Possibility of the access to Internet resources
keeping necessary information safety of the library
and the corporative net.
Forming and preparation of the workstations for
the library staff (PC’s software configuration, local
and network resources access definition, resource
access management by network administrator for
each librarians).
Integration of the library into the university
information and education space include:
- Making up students and teachers access to the
library electronic catalogue via web technologies
and special configured workstations.
- Administration and accounting of the library
network resources via NDS.
3 ARCHTECTURE OF THE
UNIVERSITY E-LIBRARY
Automation of the internal technological processes
in the university library accomplished by IRBIS
system. This system was built on for file-server
operations. The IRBIS system includes three
components:
Functional modules for librarians and readers;
Web-IRBIS module;
Z39.50 module.
The three servers are used in purpose of the e-
library network environment construction. The
server Bibl_3, which operates under the Novell
NetWare version 6.0 controls, gives the main
providing the library activity services. The
subsidiary services are hosted on the Bibl_1 server,
which operates under the Novell NetWare version
5.0 (Fig. 1).
The Bibl_3 server is used for the storing and
accessing the electronic catalogue, full text
documents, and IRBIS functional modules.
The Bibl_2 server provides the web access to the
electronic catalogue and full text documents (placed
on Bibl_3) by Web-IRBIS module usage. The
Z39.50 module also hosted and running on this
server for the inter-libraries information exchange.
For the Bibl_2 server transparent access to the
Bibl_3 server file system was made.
4 USED TECHNICAL SOLUTIONS
For the successful e-Library network environment
creation the following technical tasks must be
solved:
Creating of the program configurations (images)
for every kind of workstations that are used in the
university library (library staff workstations, visitor
workstations). Choosing and realizing the program
for replication of these created program
configurations.
Creating the model of personalization of the
library staff works (creating and holding personal
options, holding personal information (for
documents, e-mails, etc.), conducting the actions for
the users and workstations policies management).
Choosing and realizing the application
management system for the university library. The
application access and deliveries policies creation
for librarians and library visitors (students, lectors,
researchers, etc.).
Creating the policies for the RUNNet and
Internet access for librarians and library visitors.
Choosing and implementing the Internet access
control system.
All technical solutions and used technologies are
based on integration of ZENworks software package
(produced by Novell, Inc) with directory services
NDS of ETUnet.
4.1 The workstation software
configuration management
Among the library workstations there are two types
of them – for the librarians and for readers of the
library. In the librarians computers Microsoft
Windows 2000 Professional is used, in the readers
computers – Microsoft Windows NT 4.0
Workstation.
While creating the software images of
workstations to less the expenses for recreating the
work ability of the workstation in case of wrong
actions of the user or of some “wrong” programs,
the model of minimization of the influence of user
on work of the workstation system was chosen.
During the log in procedure of the user in corporate
university network on a local PC, from which the
registration is made, network service ZENworks
Workstation Management applies all the options
(policies stored into NDS) to the user workstation,
which are important for the effective work of the
user. After the user logging off all the options
connected with this user are removed from the
workstation. The user cannot create anything on a
hard disk of the computer (except the temporary
ICEIS 2004 - HUMAN-COMPUTER INTERACTION
286
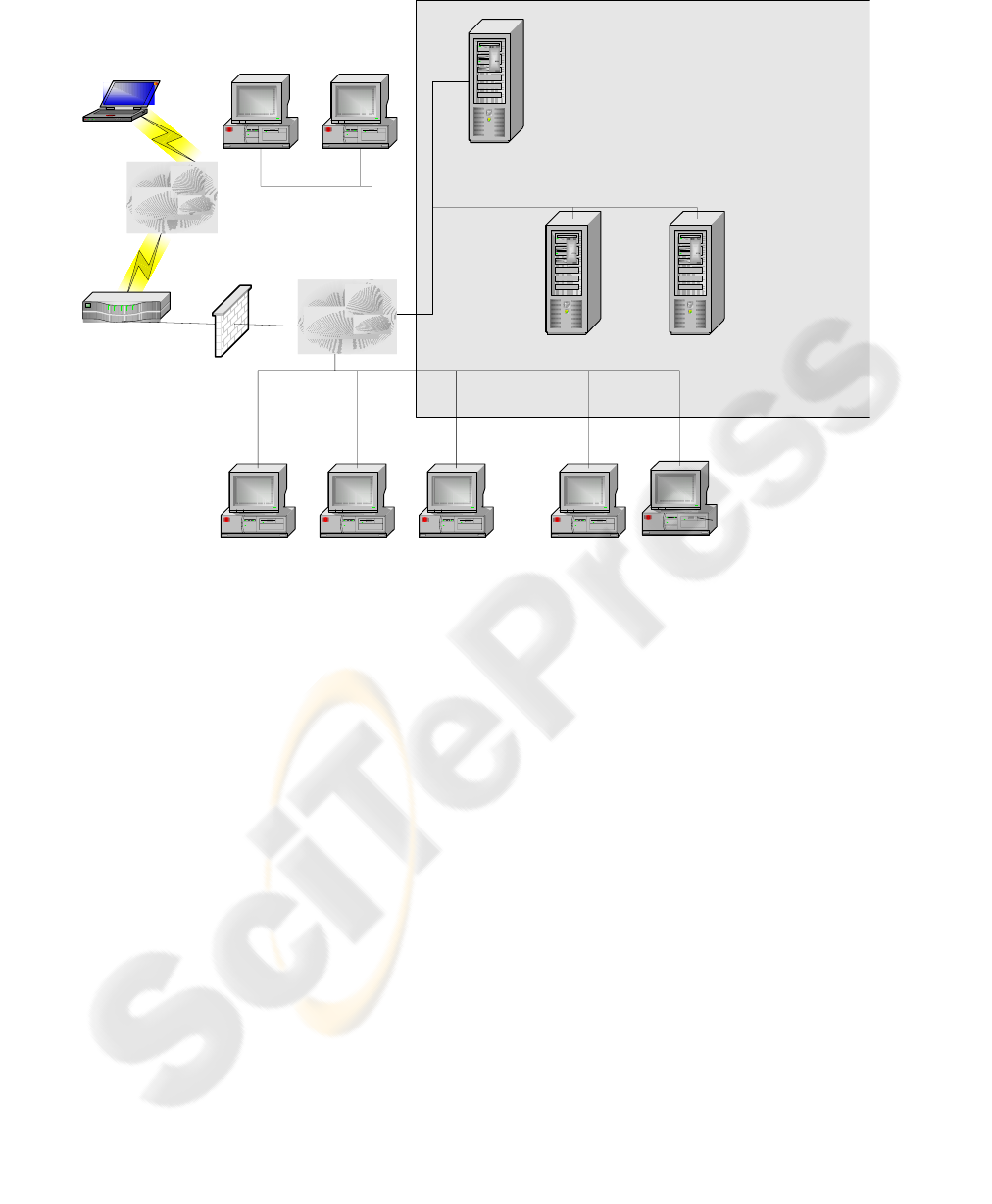
ETUNET
Internet
Bibl_1
NetWare 5.0
Bibl_2
Windows 2000 Server
Librarian Librarian Librarian
Reader
Reader
Router
Firewall
WebIRBIS
Z39.50
Acquisition
Catalogizer
Loan
Reader
Administrator
Home Directory
DNS
DHCP
Bibl_3
NetWare 6.0
Application Management
Image Server
Remote User
ETUNET Users
Full Text Documents
Figure 1: The structure of the ETU “LETI” eLibrary.
folders and files), have an access to the floppy disk
on a computer (except the cases when it is important
to work according to their work duties), and install
new programs, changing the system configuration.
All the information, that the user can operate or
change is placed on a hard disk system of the server.
An access to it is controlled by the security system
of Novell NetWare.
The using of this model of creating program
configurations of workstations helps to make the
reliability of them much more higher and as a result,
to make the “pressure” on a technical support
services less
.
The replication of the program configurations of
the workstations is realized with the help of Novell
ZENworks Imaging. It helps to create multicast of
the “images” of these stations. This replication uses
an automatic choosing of the “image” according to
the typical workstation, under the influence of its
configuration. It helps to get the “image” of the
workstation though the network. More ever, due to
the high developed functions of conducting and to
the close integration with Novell NetWare and
directory services NDS, ZENworks Imaging helps to
carry out all the important actions directly from the
workplace of an network administrator or technical
support service staff, and it doesn’t matter where the
workstation is really situated.
4.2 Application management
There are some main software applications that are
important for the work of the library staff and its
visitors. These are the groups of programs Netscape
Communicator, IRBIS modules, Microsoft Office,
Adobe Acrobat Reader, etc. During the creating of
the program’s configurations of the workstation it
became evident, that the installation of all these
software to every workstation can be unreasonable.
And the reasonable base of such a solution can be
invisible, because it could make the size of
workstation “image” very large and make the “life”
of the technical support services staff very hard.
That’s why on the base of the service Novell
ZENworks Application Management new effective
application management system was created and
integrated into ETUnet. It could solve many
problems of creating a safe access to the useful
software applications and keeping these applications
in one central point on the main library server.
Starting all these library applications is realized
form the server Bibl_3. For the most accurate work
of the programs single time copying of the important
E-LIBRARY TECHNICAL SOLUTION: AN EXAMPLE OF ETU ”LETI”
287

application files from the server to the workstation
can be demanded, as well as the changing some of
the keys in the workstation system registry.
Checking up the importance of doing such
operations and their realizing is made by the
application management services automatically after
the starting the work of this software application.
Stored on the server application files are accessible
for a user only for reading. It defends the files from
corrupting by the user’s wrong actions and protects
them from the computer viruses.
Application management helps to conduct the
user access to some software applications. On
practice it means that the program “IRBIS
Acquisitions” is able to be opened only by the
librarian from the library acquisition office. All the
rest of the users will not see the icon for “IRBIS
Acquisitions” on the workstation desktops.
Also, there is a possibility to define availability
of the software applications according to the
software and hardware configurations of the user’s
workstation. By other words, the software
application designed for Microsoft Windows 95/98
only cannot be accessible from the workstation with
Microsoft Windows 2000 Professional.
4.3 Internet access management
The library staff and visitors access to the RUNNet
and Internet is coordinated by the group of network
services DHCP and Novell BorderManager.
The DHCP service, the one of the basic network
services in the ETUnet, responses the accordance of
every workstation sending DHCP-request and send
back the IP address according to its MAC address.
Two diapasons of IP addresses are used for the
library workstations in the university library. One of
them is used for library staff workstations, the
second one – for the library users workstations. The
cause is that the library staff and the users have
different accesses to the ETUnet, RUNNet, and
Internet.
While the library staff has not limited access to
the Internet, library users have access only to the
pre-defined site addresses of other libraries in St.
Petersburg, Russia, and Europe.
The direct regulation of the Internet access is
made by Novell BorderManager software, which is
installed on the one of the main servers in the
ETUnet.
The BorderManager rules are the same as used
in the most firewall and are defined who the
concrete user or workstation with IP address inside
the ETUnet can use the Internet resources.
5 CONCLUSION
Created e-library network environment help to
organize ah efficient management and network
administration of the university library network,
informational, and digital resources. The software
applications, system policies, etc. can be effectively
managed also. All of these is the base for creating of
a modern digital library in the university in nearest
future.
REFERENCES
Puzankov D.V., Isaev Yu.N., Niskovsky A.V. The
problems of the university corporate network creation.
All-Russia scientific and methodological conference
“Telematiks’98”, Conference Proceedings. St.
Petersburg, 1998
Isaev Yu.N., Niskovsky A.V. The united space of
information and education in the St. Petersburg
Electrotechnical University “LETI”. IX International
conference and exhibition “Informational
Technologies in Education”. Conference Proceedings.
Volume III. MIPhI Press. Moscow, 1999
Niskovsky A.V., Oblomsky G.S. University Library
network environment. Tenth Avviversary International
Conference “Crimea 2003”. Libraries and
Associations in the Transient World: New
Technologies and New Forms of Cooperation.
Conference Proceedings. Volume III. Russian
National Public Library for Science and Technology.
Moscow, 2003
ICEIS 2004 - HUMAN-COMPUTER INTERACTION
288
