
THE ABORTION RATE OF LAZY REPLICATION PROTOCOLS
FOR DISTRIBUTED DATABASES
∗
Luis Ir
´
un-Briz, Francesc D. Mu
˜
noz-Esco
´
ı, Josep M. Bernab
´
eu-Aub
´
an
Instituto Tecnol
´
ogico de Inform
´
atica
Universidad Polit
´
ecnica de Valencia
46071 Valencia, SPAIN
Keywords:
Replication, fault tolerance, reliability, distributed systems, databases, middleware, systems integration
Abstract:
Lazy update protocols have proven to have an undesirable behavior due to their high abortion rate in scenarios
with high degree of access conflicts. In this paper, we present the problem of the abortion rate in such protocols
from an statistical point of view, in order to provide an expression that predicts the probability of an object to
be out of date during the execution of a transaction.
It is also suggested a pseudo-optimistic technique that makes use of this expression to reduce the abortion rate
caused by accesses to out of date objects.
The proposal is validated by means of simulations of the behavior of the expression. Finally, the application
of the presented results to improve lazy update protocols is discussed, providing a technique to theoretically
determine the boundaries of the improvement.
1 INTRODUCTION
Nowadays, many distributed (i.e., networked) appli-
cations have to manage large amounts of data. De-
spite the increasing ubiquitousness of information,
the access patterns to distributed data often feature a
noticeable degree of geographical locality. Moreover,
many applications require a high degree of availabil-
ity, in order to satisfy the need of offering services
at any time, to clients that are either internal or ex-
ternal to the networked application. A predominance
of locality of access patterns usually suggests a parti-
tioning of the database (Gray et al., 1996). In many
scenarios, it may be convenient or even necessary to
replicate the information in a set of servers, each one
attending its local clients. The different replicas must
then be interconnected, a WAN being usually the best-
fit architectural option.
The typical kind of applications we have in mind
are, for instance, widely distributed databases in
wide area intranets of medium and large enterprises,
for data warehousing or resource management, as
well as extranet service provisioning of such enter-
prises. Examples where such intranets of databases
∗
This work has been partially supported by the EU grant
IST-1999-20997 and the Spanish grant TIC2003-09420-
C02-01.
are deployed advantageously are enterprises with sev-
eral branch offices (e.g., banks, chains of retail-
ers, super- and hypermarkets), telecommunication
providers, travel businesses, logistics, etc. Examples
of extranet services which benefit from replication
protocols as discussed in this paper are customer re-
lationship management, e-banking, virtually all kinds
of e-business as well as most e-government applica-
tions. Common to all of these applications is that
potentially huge amounts of data are maintained and
replicated on distributed sites, while access patterns
(or at least significant contingents thereof) are highly
local. Efficiency and high availability of such services
is key to their acceptance and success.
The GlobData project (Instituto Tecnol
´
ogico de In-
form
´
atica, 2002; Rodrigues et al., 2002) strives to pro-
vide a solution for the kinds of applications just out-
lined. It does so by defining a specific architecture
for replicated databases, together with an API and a
choice of consistency modes for data access. In the
GlobData architecture, a number of consistency pro-
tocols can be implemented and plugged, each one pro-
viding particular guarantees and behaviors.
During the development of the project, we encoun-
tered that the protocols necessities of our target sce-
nario (i.e. geographical distributed applications with
a high degree of locality) could be well-fitted with a
130
Irún-Briz L., D. Muñoz-Escoí F. and M. Bernabéu-Aubán J. (2004).
THE ABORTION RATE OF LAZY REPLICATION PROTOCOLS FOR DISTRIBUTED DATABASES.
In Proceedings of the Sixth Inter national Conference on Enterprise Information Systems, pages 130-135
DOI: 10.5220/0002623301300135
Copyright
c
SciTePress

family of replication protocols classified as lazy up-
date protocols. However, we encountered that this
kind of protocols introduces a high number of abor-
tions in the system, because they propagate the up-
dates beyond the commit phase (in contrast to eager
update protocols, where the whole system is updated
inside the commit phase), making it possible for a
transaction to read out of date data, and thus, there
are consistency violations.
In (Mu
˜
noz et al., 2002; Ir
´
un-Briz, 2003), we pre-
sented two consistency protocols, using different ap-
proaches for the update propagation.
Lazy update protocols have proven to have a crit-
ical inconvenience in contrast to eager approaches:
the dramatical increase of the abortion rate in scenar-
ios with a high degree of access conflicts. This in-
convenience makes unusable the traditional lazy up-
date protocols in certain scenarios, because an unac-
ceptable number of started transactions will terminate
with an undesirable abort.
To understand the problem, this work presents a
set of expressions describing the abortion rate. In the
presentation, we model a complete system including
nodes, the sessions executed, and the objects accessed
by the sessions. Moreover, we use our LOMP algo-
rithm as an example of a lazy update protocol where
all these expressions may be directly applied. A full
description of this protocol may be found in Section
3.2 of (Ir
´
un-Briz, 2003).
Section 2 includes the description of such modeled
system, in order to formalize an analysis of the abor-
tion rate in section 3. In section 4, an empirical val-
idation of the model is presented, and section 5 will
provide a theoretical analysis of an improvement of
the lazy approach. Finally, section 6 describes some
related work, and section 7 includes some conclusions
about the applicability of the expressions.
2 THE MODELED SYSTEM
One of the problems solved by the GlobData architec-
ture(Mu
˜
noz et al., 2002) (called COPLA) is to ensure
the consistency among transactions being executed in
different database replicas. Multiple implementations
of the consistency management are possible, thus al-
lowing that a GlobData system could change its con-
sistency protocol at will. So, we use the COPLA ar-
chitecture as a platform to experiment with different
consistency algorithms working on the top of a trans-
actional system (in fact, a database) and replicated
over a distributed system.
The target system of our analysis follows a number
of considerations, designed to configure a scenario as
close as possible to a general environment that, al-
though simplified, is able to fit the requirements of
the kind of environment we are centered in. This en-
vironment was described in the introduction, and has
considerations about client applications, system load,
pattern of accesses, interconnection network, etc.
In summary, these adopted assumptions are the fol-
lowing:
• There are K COPLA managers running in the sys-
tem. Each one can be considered as a “node”
N
k=1..K
.
• Each node in the system manages a complete
replica of the database. This database contains N
objects.
• We assume that the objects stored in the database
have a identifier that is unique in the entire sys-
tem. In addition, each write operation performed
in a node includes an storage for each written ob-
ject of the local time the operation is performed, as
well as a version number of the written object.
3 PROBABILITY OF ABORTION
We can define the probability for a session S to be
aborted as: P A(S) = 1 − (P C
conc
(S) · P C
outd
(S))
where:
• P C
conc
(S) is the probability that the session con-
cludes without concurrency conflicts.
• P C
outd
(S) is the probability that the session con-
cludes without accessing to outdated objects.
The goal of this section is to determine the value
of P C
outd
(S), in order to predict the influence our
LOMP has into the abortion rate in the system. To this
end, we can calculate this probability in terms of the
probability of a session to conclude with conflicts pro-
duced by the access to outdated objects (P A
outd
(S)):
P C
outd
(S) = P C
outd
(r
i
)
nr
taking nr as the number (in mean) of objects read by
a session,
P C
outd
(S) = P C
outd
(r
i
)
P
k
nr
k
K
(1)
moreover, P C
outd
(r
i
) is the probability for an object
r
i
to have an updated version in the instant the session
accesses it. This probability can be expressed in terms
of the probability for an object to be accessed in an
outdated version (P A
outd
(r
i
)) as:
P C
outd
(r
i
) = 1 − P A
outd
(r
i
)
now, let’s see the causes of these conflicts: we took r
i
as an asynchronous object in the active node that has
not been updated since ut(r
i
); the outdated time for
r
i
satisfies δ(r
i
) = t(r
i
) − ut(r
i
); it can be seen that
P A
outd
(r
i
) depends on the number of sessions that
THE ABORTION RATE OF LAZY REPLICATION PROTOCOLS FOR DISTRIBUTED DATABASES
131

write r
i
having the chance to commit during δ(r
i
).
Let P C
T,r
i
be the probability for another concurrent
session T (that has success in its commit) to finalize
with r
i
6∈ W (T ). Then,
P A
outd
(r
i
) = 1 − (P C
T,r
i
)
C
where C depends on the number of write-sessions that
can be committed in the system during δ(r
i
) . . .
P A
outd
(r
i
) = 1 − (P C
T,r
i
)
P
k
wtps
k
×δ(r
i
)
(2)
now, we can reformulate P C
T,r
i
as P C
T,r
i
=
P [r
i
6∈ W (T )] and, considering W (T ) =
{w
1
, w
2
, . . . w
nw(T )
}, then in mean, it will be satis-
fied that:
P C
T,r
i
=
¡
P [r
i
6= w
j∈{1..nw}
]
¢
nw
taking nw as the mean of |W (T )| for every write-
session in the system.
P C
T,r
i
=
¡
P [r
i
6= w
j∈{1..nw}
]
¢
P
k
nw
k
K
(3)
The next step consists of the calculation of P [r
i
6=
w
j∈{1..nw}
]. To do this, we must observe the number
of objects in the database (N ). The probability that
an accessed object is a given one is
1
N
, thus: P [r
i
6=
w
j∈{1..nw}
] = 1 −
1
N
Finally, the complete expression can be rewritten as
follows:
P A
outd
(r
i
) = 1 −
¡
1 −
1
N
¢
P
k
nw
k
K
×
P
k
wtps
k
×δ(r
i
)
(4)
This expression provides a basic calculation of the
probability for an object access to cause the abortion
of the session by an out-of-date access.
The expression can be calculated with a few param-
eters. Only nw
k
and wtps
k
must be collected in the
nodes of the system in order to obtain the expression.
Thus, it becomes possible for a node to estimate the
convenience for an object to be locally updated be-
fore being accessed by a session. This estimation will
be performed with a certain degree of accuracy, de-
pending on the “freshness” of the values of nw
k
and
wtps
k
the node has. The way the expression can be
used, and an adequate mechanism for the propagation
of these parameters has been presented in (Ir
´
un-Briz,
2003).
4 EXPERIMENTAL VALIDATION
OF THE MODEL
We have validated the algorithm presented above by
implementing a simulation of the system. In this sim-
ulation, we have implemented nodes that concurrently
serve sessions, accessing to different objects of a dis-
tributed database. We have also modeled the concur-
rency control, and the lazy update propagation used
by LOMP.
4.1 Assumptions
The assumptions for the implementation of the sim-
ulation (Chandy and Misra, 1979; Bagrodia et al.,
1987) are compatible with the ones taken for the
model calculation, and the values have been estab-
lished to increase the number of conflicts produced
by the transactions executed in the system (i.e., this
configuration shows a “worst-case” scenario for our
system):
• There are 4 nodes in the system, each holding a
full replica of the database, that contains 20 ob-
jects. Each node executes transactions, accessing
the database.
• For every object, a local replica holds the value of
the object, and the version corresponding to the last
modification of the object. That is, the only syn-
chronous replica for each object is its owner node.
• There are three kinds of transactions, with a prob-
ability to appear of 0.2, 0.4, and 0.4 respectively:
”Type 0” (read-only): reads three objects; ”Type 1”
(read-write): reads three objects, then writes these
three objects; ”Type 2” (read&read-write): reads
six objects, then writes three of the objects read.
• The model supports the locality of the access by
means of the probability for an accessed object to
be owned by that node (i.e. the node where the
transaction is started). For read-only transactions,
this is 1/4, (this models no locality for read-only
transactions). For ”type 1” and” type 2” transac-
tions, the probability is 3/4.
• The simulation time has been set at 1,422 t.u., dis-
carding the first 2 t.u. as stabilization time for the
simulation. This allows to start up to 60,000 trans-
actions.
4.2 Accuracy of the Prediction
When the expression exceeds the established thresh-
old for an object, and an update request is sent, it is
possible for the response of this request to contain the
same version for the requested object (e.g. when the
object was, in fact, up to date). We name this situation
“Inaccurate prediction”.
The more accurate the predictions are, the less
overhead the algorithm introduces in the system. This
accuracy of the predictions will be given by the set
threshold: higher values for the threshold should pro-
vide more accurate predictions. In general, we ob-
served that higher values for the threshold increase
the accuracy of the prediction.
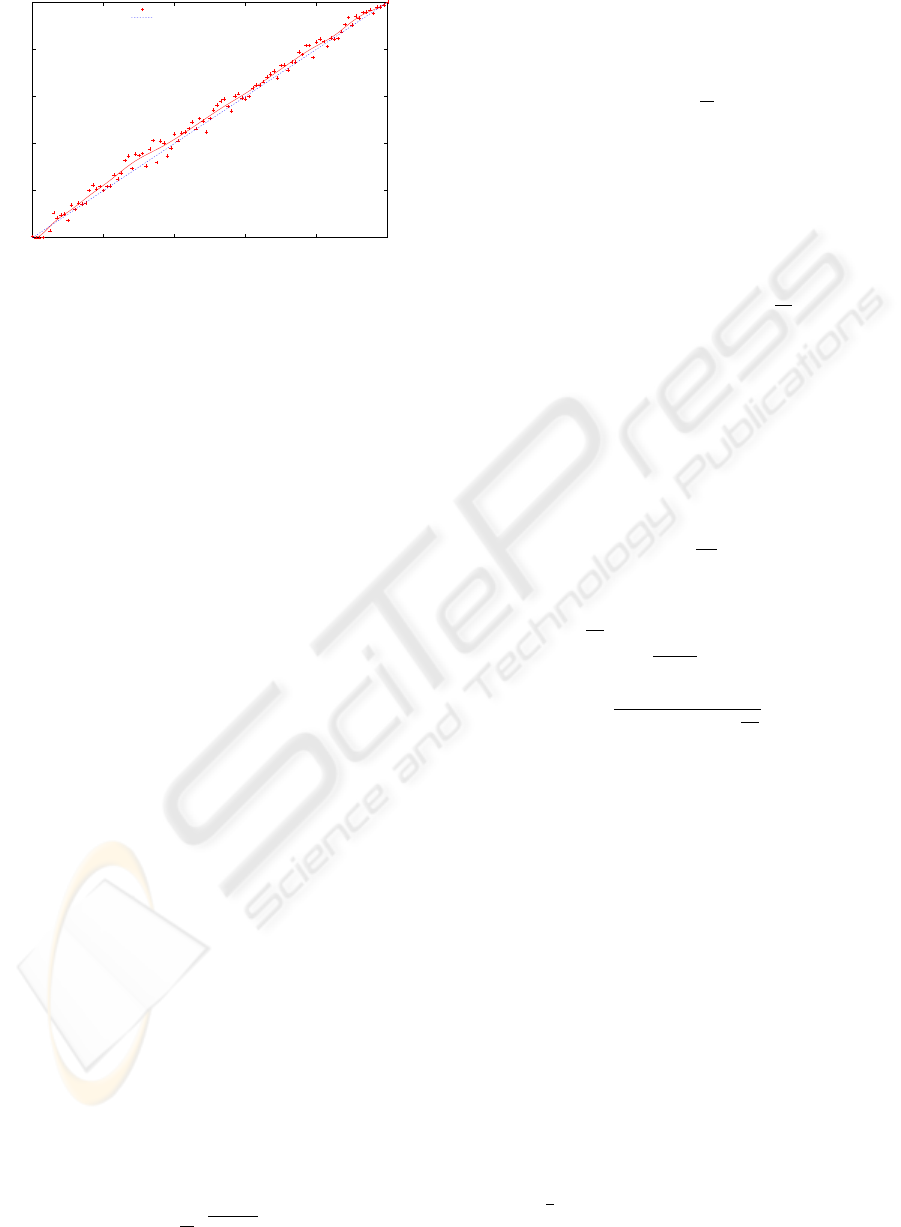
The evolution of the inaccuracy in respect to the
amount of LocalUpdate messages is shown in the fig-
ure 1. The optimum line is also shown, and corre-
sponds with the diagonal. The more accurate the pre-
diction is, the closest the curves are. The studied im-
ICEIS 2004 - DATABASES AND INFORMATION SYSTEMS INTEGRATION
132
0
20
40
60
80
100
0 0.2 0.4 0.6 0.8 1
% outdated
PA_outd
Completeness of the prediction
Predicted abortions
Actual abortions
Figure 1: Evolution of the inaccuracy for different
P[update]
plementation differs from the ideal line with a lower
bound pattern, and it is shown that is quite proximal
to the ideal.
5 THEORETICAL BOUNDARY
OF AN IMPROVEMENT
The first sections of this paper has been dedicated to
the study of an statistical expression determining the
probability for a particular object access, to obtain an
out to date value, thus causing the abortion of the re-
questing transaction.
We can make use of such expression, in order to de-
termine the achievable improvement for a transaction,
in terms of abortion rate, when the average outdate
time of the objects is decreased.
Unfortunately, this decrement in the outdate time
will cause a degradation in the service time of the ex-
ecuted transactions, and this must also be taken into
account.
In this section, we present a theoretical boundary
for the reduction of the abortion rate that an adequate
exploit of the expression can provide.
5.1 Preliminaries
The used expression for the probability of an access
to be an stale-access was presented in 4. In the ex-
pression, the elapsed time between two consecutive
updates of the object r
i
is expressed as δ(r
i
).
We can perform a serial analysis in order to de-
termine the mean value for P A
outd
(r
i
). The analy-
sis can be easily performed applying differentiate cal-
culus to the expression. The obtained expression is
showed to be:
P A
outd
= 1 −
¡
1 −
1
N
¢
P
k
nw
k
K
×
P
k
wtps
k
×δ
(5)
where δ is the mean value for the δ(r
i
) in a sys-
tem execution, and P A
outd
is the mean value for the
P A
outd
(r
i
) in the same system execution.
Now, we can obtain P C
outd
= 1 − P A
outd
, being:
P C
outd
= P C =
¡
1 −
1
N
¢
nwwt×wtps×δ
(6)
5.2 Average Outdate Time
To simplify, let’s suppose that transactions are dis-
tributed homogeneously along the system history.
Imagine the system execution history as a line,
where a number of transactions are sequentially ex-
ecuted. For a certain object o
i
, the probability for a
executed transaction to read o
i
will be
nr
N
, where nr
is the number, in mean, of objects read by any exe-
cuted transaction (either read or write transactions are
included here), and N is the number of objects in the
database.
The probability of the object o
i
to be updated by
a lazy replication protocol depends on the probability
for a transaction that read o
i
to be aborted by an stale-
access (i.e. P A
T
= P A
nr
). Thus the probability for
an object to be updated by a generic transaction will
be:
P A
nr
×
nr
N
Now, let tps be the number of transactions executed in
the system per second. Thus, there will be up(o
i
) =
tps × P A
nr
×
nr
N
updates of o
i
per second. Finally,
we can express δ(o
i
) as
1
up(o
i
)
, and, in mean:
δ =
1
tps × P A
nr
×
nr
N
(7)
If the accessed objects are updated along the transac-
tion, the value for δ will be decreased proportionally
to the amount of updates performed during the trans-
action execution.
To model this, a simple approach can be expressed
with the following expression:
δ
0
= P C × d
0
T
+ (1 − P C) × δ (8)
where d
0
T
is the duration of a transaction when the
updates are performed along its execution. For the
aborted transactions, (i.e. (1 − P C)), the mean out-
date time is unchanged (δ). In contrast, for committed
transactions, the new outdate time is decreased to d
0
T
(i.e. the duration of the transaction).
Now, the duration of a transaction when the updates
are performed will depend on the number of requested
accesses that are actually updated along the transac-
tion execution (nr × P
UP D
), and the cost of each of
these updates (K
UP D
). Note that P
UP D
is the prob-
ability for a requested object to be updated. Thus, if
P
UP D
=
1
2
, there will be forced to be updated the
half of the objects requested by a transaction.
THE ABORTION RATE OF LAZY REPLICATION PROTOCOLS FOR DISTRIBUTED DATABASES
133
In summary, the expression for d
0
T
can be com-
posed by:
d
0
T
= d
T
+ nr × P
UP D
× K
UP D
(9)
Replacing 9 in 8, the new outdate time will follow the
expression:
δ
0
= δ × (1 − P C) + P C × d
0
T
(10)
This result will be useful in section 5.3, where the
achievable abortion rate is specified in terms of δ
0
.
5.3 Abortion Rate
In mean, we can say that the achievable commit rate
will be, observing equation 6:
P C
0
=
¡
1 −
1
N
¢
nwwt×wtps×δ
0
(11)
Replacing δ
0
in the expression, we obtain:
P C
0
=
¡
1 −
1
N
¢
nwwt×wtps×δ×(1−P C)
×
¡
1 −
1
N
¢
nwwt×wtps×P C×d
0
T
(12)
That can be rewritten as:
P C
0
= P C
1+P C
µ
d
0
T
δ
−1
¶
(13)
Now, we can replace δ with the expression obtained
in (7), the resulting expression is:
P C
0
P C
= P C
P C
(
d
0
T
×(tps×(1−P C)
nr
×
nr
N
)−1
)
(14)
From the equation 14 we obtain that the improvement
of the probability for an object to be accessed in an
adequate way (i.e. not an stale access), is determined
by
P C
0
P C
, and it will be benefitted from the decrease of
the established value or any of the following expres-
sions:
• d
T
, the duration of the transactions.
• nr × P
UP D
× K
UP D
, the number of updated ob-
jects, and the computational cost of each of these
updates.
• tps, the amount of committed transactions per sec-
ond (including both read-only and read-write trans-
actions).
•
nr
N
, the relation between the amount of objects
accessed per transaction (read-only or read-write
transactions) and the total number of objects con-
tained in the database.
To simplify the expression 13, we can denote as ∆ to
the existing relation between d
0
T
and δ (i.e. ∆ =
d
0
T
δ
).
The resulting expression is:
P C
0
= P C
1+P C×(∆−1)
=⇒
P C
0
P C
= P C
P C×(∆−1)
(15)
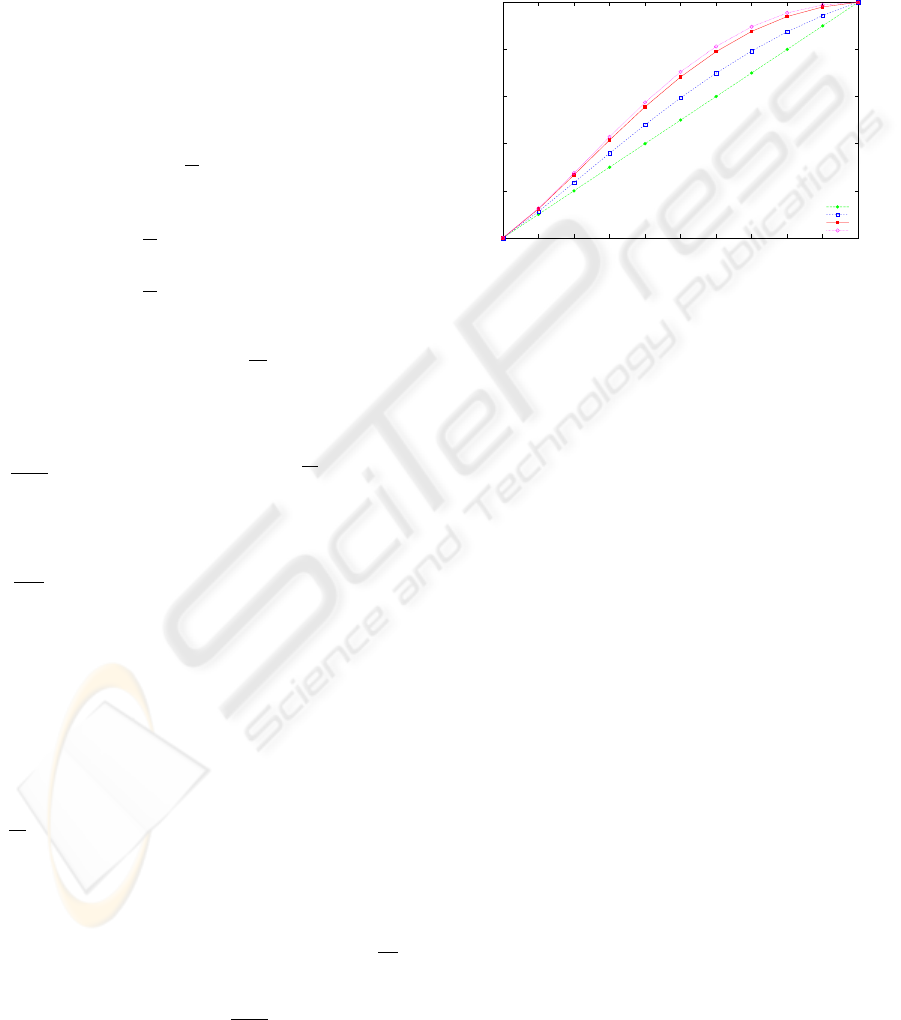
Let’s see an example for the improvement achiev-
able in an extremely simple system, where nr = 1. In
such system, we can establish as a parameter the prob-
ability for a requested object to be previously updated
(i.e. P
UP D
), and then study the achieved improve-
ment for different values of ∆ (and, consequently, dif-
ferent computational overheads).
0
0.2
0.4
0.6
0.8
1
0 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 1
Probability of Commit
PC (probability for an object to be up-to-date)
Comparison PC’ vs. PC
PC
PC’ for Delta=0.5
PC’ for Delta=0.1
PC’ for Delta=0.01
Figure 2: Evolution of the improvement varying ∆
Figure 2 shows the commit probability for a ses-
sion accessing only one object. There is shown how
the commit probability can be improved, when the
update-time is decreased to the half, up to the 120%
of the original commit time. When the update-time
is decreased ten times, the improvement reaches the
140%. Lower values of ∆ provides marginal im-
provements, at a higher computational costs.
When more than just an object is accessed in a
session, the results shows higher differences between
the commit promise, due to the factorization of such
probabilities.
These results points to the convenience, in the sce-
narios fitting the parameters described above, to apply
the techniques postulated by the presented discussion.
6 RELATED WORK
Current work in consistency protocols for replicated
databases can be found using either eager (Agrawal
et al., 1997) and lazy protocols (Breitbart and Korth,
1997; Holliday et al., 1999) using either optimistic
and pessimistic consistency control.
Each one has its pros and cons, as described in
(Gray et al., 1996). Eager protocols usually hamper
the update performance and increase transaction re-
sponse times but, on the positive side, they can yield
serializable execution of multiple transactions with-
out requiring too much effort. On the other hand,
lazy protocols may allow a transaction to read out-
dated versions of objects, hamper the abortion rate,
but they can improve transaction response times.
ICEIS 2004 - DATABASES AND INFORMATION SYSTEMS INTEGRATION
134

Pessimistic consistency control for distributed
databases (Bernstein et al., 1987) is based on the prin-
ciple of “locks” in order to avoid concurrent transac-
tions to access to the same object in an inadequate
mode. The use of “locks” minimizes the number of
aborted transactions, but degrades the performance of
the system, because the complexity introduced by the
management of the locks.
On the other hand, the traditional approach for op-
timistic consistency control was presented in (Kung
and Robinson, 1981), and its main advantage consists
on the reduction of the blocking time of the transac-
tions, using “versions” (or “timestamps”) as the basis
for its implementation. The main disadvantage of op-
timistic consistency protocols consists of the increase
in the abortion rate.
The presented approach uses a optimistic consis-
tency control, with lazy replication, and has been im-
plemented in a real environment (COPLA).
7 CONCLUSIONS
Lazy update protocols have not been widely exploited
due to its excessive abortion rate on scenarios with
high probability of access conflicts. Nevertheless,
such protocols can provide important improvements
in the performance of a distributed system, when the
abortion rate can be kept low, and the locality of the
accesses is appreciable.
We have presented an statistical study of the abor-
tion rate (as disadvantage of lazy protocols), in or-
der to provide an expression for the probability for an
accessed object to be out of date (P A
outd
(o
i
)), and
cause a further abortion of the accessing transaction.
An statistical analysis has been performed in this
paper, in order to provide an expression for the prob-
ability for a requested access to obtain a stale value of
the required object.
The application of the expression has been also dis-
cussed, in order to determine the convenience, using
a general algorithm, to update along the execution of
a transaction the objects predicted to be stale. This
discussion has provided a set of conditions, in base
to a number of parameters, where these generic algo-
rithms can improve the abortion rate of a lazy update
protocol.
Consequently, the improvement has also studied, in
base to the established decrement of the update-time
of the accessed objects, giving as conclusion that such
reductions may considerably improve the probability
for an object to be updated, thus reducing dramati-
cally the abortion rate of lazy update protocols.
Thus, this work theoretically validates the imple-
mentation of not-so-lazy update protocols based on
statistical prediction of stale accesses to reduce the
abortion rate. These protocols conform possible im-
plementations of the mentioned generic algorithm, as
a real improved update algorithm.
REFERENCES
Agrawal, D., Alonso, G., El Abbadi, A., and Stanoi,
I. (1997). Exploiting atomic broadcast in repli-
cated databases. Lecture Notes in Computer Science,
1300:496–503.
Bagrodia, R. L., Chandy, K. M., and Misra, J. (1987).
A message-based approach to discrete-event simula-
tion. IEEE Transactions on Software Engineering,
SE-13(6).
Bernstein, P. A., Hadzilacos, V., and Goodman, N. (1987).
Concurrency Control and Recovery in Database Sys-
tems. Addison Wesley, Reading, MA, EE.UU.
Breitbart, Y. and Korth, H. F. (1997). Replication and con-
sistency: being lazy helps sometimes. In Proceed-
ings of the sixteenth ACM SIGACT-SIGMOD-SIGART
symposium on Principles of Database Systems, pages
173–184. ACM Press.
Chandy, K. M. and Misra, J. (1979). Distributed simulation:
A case study in design and verification of distributed
programs. IEEE Transactions on Software Engineer-
ing, SE-5(5):440–452.
Gray, J., Helland, P., O’Neil, P., and Shasha, D. (1996).
The dangers of replication and a solution. In Proc.
of the 1996 ACM SIGMOD International Conference
on Management of Data, pages 173–182, Canada.
Holliday, J., Agrawal, D., and Abbadi, A. E. (1999).
Database replication: If you must be lazy, be consis-
tent. In Proceedings of 18
th
Symposium on Reliable
Distributed Systems SRDS’99, pages 304–305. IEEE
Computer Society Press.
Instituto Tecnol
´
ogico de Inform
´
atica (2002). GlobData Web
Site. Accessible in URL: http://globdata.iti.es.
Ir
´
un-Briz, L. (2003). Implementable Models for
Replicated and Fault-Tolerant Geographically Dis-
tributed Databases. Consistency Management for
GlobData. PhD thesis, Departamento de Sis-
temas Inform
´
aticos y Computaci
´
on, Universidad
Polit
´
ecnica de Valencia, Valencia, Spain. Available
at http://www.iti.upv.es/˜lirun.
Kung, H. T. and Robinson, J. T. (1981). On optimistic meth-
ods for concurrency control. ACM Transactions on
Database Systems, 6(2):213–226.
Mu
˜
noz, F., Ir
´
un, L., Gald
´
amez, P., Bernab
´
eu, J., Bataller, J.,
and Ba
˜
nuls, M.-C. (2002). Globdata: A platform for
supporting multiple consistency modes. Information
Systems and Databases (ISDB’02), pages 244–249.
Rodrigues, L., Miranda, H., Almeida, R., Martins, J., and
Vicente, P. (2002). The globdata fault-tolerant repli-
cated distributed object database. In Proceedings of
the First Eurasian Conference on Advances in In-
formation and Communication Technology, Teheran,
Iran.
THE ABORTION RATE OF LAZY REPLICATION PROTOCOLS FOR DISTRIBUTED DATABASES
135
