
Public Processes Legal Issues Verification using YAWL
Kaouther Mezaache and Latifa Mahdaoui
Department of Computing, University of Science and Technology Houari Boumediene, Algiers, Algeria
Keywords: Public Process Verification, Legal Requirements Verification, Design-Time Verification, Soundness Property,
YAWL.
Abstract: Improving public processes to build an effective e-government system has become a necessity for many
governments. For the purpose of providing quality electronic services to citizens, businesses and other public
institutions. However, this is not as easy as it seems, due to the nature of e-government system and the
requirements of its processes specially the legal ones. As a matter of fact, the law is one of the important
sources of knowledge that rigorously describes administrative procedures and their end results. Hence,
process verification will be a mandatory task to detect and to prevent process problems at the deployment
phase. Therefore, this paper aims to introduce an approach to assess public process legal issues against
soundness property using YAWL.
1 INTRODUCTION
Governments become nowadays subject of
modernization through the adoption of information
and communication technologies (ITC) (Cherouana
et al, 2017). Therefore, building an efficient e-
government system is one of the ultimate objectives
of contemporary governments. For the sake of
enhancing the access to and delivery of government
information and services to citizens, business
partners, and government entities (Layne and Lee,
2001).
It is worth mentioning that e-government cannot
be achieved by simply implementing good software
(Alpar and Olbrich, 2005), even though these later
have proven their effectiveness in the private sector.
This is due to the e-government system nature and
requirements of its processes, namely, political,
organizational, technical and especially the legal
requirements (Cherouana et al, 2017). Indeed,
according to (Hasan et al, 2015) the policies and
regulators become one of the most significant barriers
to reengineering public administration processes.
Nevertheless, (re) engineering the public
processes without respecting legal constraints is
rather dangerous (Alpar and Olbrich, 2005) and leads
to inconsistent situations which may cause an
enormous loss of trust and reputation (Hasan et al,
2015).
However, regarding their informal nature,
regulations could be source of many problems
(Aravanis et al, 2018): 1. Misinterpretation of legal
texts because of the difficulty of understanding. 2.
Lack of legislation or Legal vacuum. 3. Self-
contradictions 4. The origin of legal texts from
several sources can lead to overlapping regulations
at different levels of authority, and could sometimes
produce contradictions or conflicts between them. 5.
Frequent change and evolution of regulation over
time …Etc.
For these and other reasons, large amount of work
exists in the field of business process verification, to
maintain e-government’s proper functioning. Among
them, the approach proposed in the current paper. It
allows to perform a twofold process model
verification: formal and informal verification. Using
YAWL (see section 3), that will act as a simulator,
allowing to apprehend processes design issues that
may affect performance before proceeding to their
implementation.
The reminder of this paper is organized as
follows: some related works are presented in the
following section with a discussion about it. Section
3 introduces the proposed approach of process
verification as well as the research context. Section 4
will describe the case study used to illustrate the
approach application. Finally, we conclude the paper
with proposition of some future perspectives in
section 5.
Mezaache, K. and Mahdaoui, L.
Public Processes Legal Issues Verification using YAWL.
DOI: 10.5220/0010454702890296
In Proceedings of the 16th International Conference on Evaluation of Novel Approaches to Software Engineering (ENASE 2021), pages 289-296
ISBN: 978-989-758-508-1
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
289
2 RELATED WORK
According to (Groefsema and Bucur et al, 2013), the
formal business process verification has mainly four
goals: 1) Basic process correctness: aim to verify
process basic properties such as termination, 2)
Process compliance: aims to address and provide
solutions to the alignment between business process
and regulations (Hashmi et al, 2018), 3) Variability:
aims to support different versions of the same
process. It uses rules to specify how each version of a
process should behave, 4) Processes including
multiple parties: aim to verify the compatibility
between processes (for example).
The following table (Table 4) summarizes some
of the related work about business process
verification.
Table 1: Related work.
Article Verification Method
Verification
Purpose
(He et al,
2018)
The authors propose
a workflow nets with
incorporation of data
constraints and define
four level of
soundness and use the
reachability graph to
verify the soundness
property of the
processes.
Detecting
errors from
the data-flow
perspective
(missing data,
conflicts….).
(Aravanis et
al, 2018)
The idea here is to
reduce the workflow
while preserving its
properties using six
novel reduction rules,
then substituted the
analysis of the
soundness property of
the reduced workflow;
thus, carry out the
verification of
soundness property on
a smaller WF-Nets.
Verifying the
crucial
business
processes of a
system with
large size and
big
complexity.
(Birukou et
al, 2010)
This method
combined two
constraints solving
methods: CLP
(Constraints Logic
Programming) and
SMT (Satisfiability
Modulo Theory), they
report that SMT
approach has much
better results than the
CLP, except for a
Verifying the
modal
specifications
of the
business
processes
(that describe
the necessary
behaviours of
processes).
conflict free workflow
net. For this reason,
they combined the two
of them.
(De Moura
et al, 2010)
Business rules are
represented using the
OCL language,
considered as a pre- or
post-condition for
business processes
represented by the
UML Activity
Diagram. The model
validation is based on
the simulation of the
execution of process
instances based on
specific scenarios. If
the violation is
detected -with the help
of the USE tool- than
the execution is
stopped and the
violation is reported
and returned to the
modeler whom could
rectify the rule or the
input or outputs.
Checking the
compliance
of business
processes
with the
business rules
(represented
in OCL) at
the Run-Time
phase.
(Corradini et
al, 2010)
The authors defined a
quality framework
which classifies the
delivery processes of
an e-government
digital processes and
they implemented a
tool applying a model
checking techniques,
to verify that
developed e-
government digital
processes satisfy the
properties defined in
the quality framework
Ensuring
quality of
governmental
processes by
comparing it
to a set of
properties.
(Gilliot and
Accorsi et al,
2009)
They use the model-
checking technique
based on linear
temporal logic (LTL)
and statistical
reasoning. And the
result could be one of
the 4-valued logic:
“true,” “false,”
“presumably true,” or
“presumably false.”
Anticipating
obligation
violations at
“Run-time”.
ENASE 2021 - 16th International Conference on Evaluation of Novel Approaches to Software Engineering
290
Table 1: Related work (Cont.).
Article Verification Method
Verification
Purpose
(Jiang et al,
2015)
Authors propose A
compliance and
consistency checker
framework CCCF that
takes as input:
business process
represented with
modelling language
then formalized into
event-sequence and
regulations
represented with
Norms Nets. Then
provides three results:
whether regulations
are consistent,
whether business
process are compliant
and in case of non-
compliance which
operation to be
rectified.
Analysing
both
processes
compliance
with
regulations
and self-
consistency
of laws
(Governatori
et al, 2006)
Business
constraint in the
contract is represented
by a rule in FCL
language. While the
business processes
scenarios are
represented by BPMN
then transformed into
an event pattern (same
thing for the contract
conditions in order to
facilitate the checking
task). The comparison
results between the
events are as follows:
ideal “none violation
detected”, sub-ideal
“violation detected but
could be repaired”, a
non-ideal “a violation
detected without a
reparation” and
irrelevant situation
“there isn’t a rule to
apply in this situation.
Use of logic
in analysing
the
compliance
of business
processes
with business
contracts.
2.1 Discussion
From the works of the table above, we observe that
there are several characteristics to process
verification, that could be divided like so:
2.1.1 Concerning the Process
1. Process Perspective: the focus is on one of the
process perspectives (Van Der Aalst and Ter
Hofstede, 2005) namely: control-flow, data-flow or
resource-flow perspective.
2. Process Sector: the process could be for the
public sector or for the private sector (Corradini et al,
2010).
3. Process Complexity: i.e., a complexity factor
which specifies how far the process is complicated
(Aravanis et al, 2018).
2.1.2 Concerning the Method of Verification
1. Verification Phase: means at what phase of the
process life-cycle the verification will be performed.
According to (Hashmi et al, 2018) there are three
main strategies, namely: de-sign-time, run-time or
audit (post-execution).
2. Verification Type: stands for: 1) compliance
verification of the process with norms or 2)
consistency verification of the regulations governing
processes, or 3) both.
3. Employed Methods: refers to the methods used
to perform the verification, naming: use of logic, use
of well-known AI methods or conceptual ones…. etc.
2.1.3 Discussion
The majority of the studied papers focus on the
control flow perspective except for the (He et al,
2018) that treats the data flow perspective, without
precising the targeted sector excluding (Corradini et
al, 2010) that aims at proposing a quality framework
to ensure public processes (governmental processes)
quality. They also perform their verification at
different time of the process-life-cycle. Also, we
notice that the works mostly emphasis on the
compliance verification of processes with the
regulations -norms- and few of them have evoked the
regulation consistency verification. In the exception
of (Jiang et al, 2015) that perform the two of them at
once. We remark that various methods were used to
help in proposing verification approaches, we can
cite: logic in multiple works (Gilliot and Accorsi et
al, 2009) (Governatori et al, 2006). Finally, many
papers have used the model checking techniques to
check the applicability of the verification method.
The ultimate objective of proposing this approach
for process verification; is to detect legal problems
(legal vacuum, legal conflicts and obsolete law),
through analyzing public processes during the design-
time phase (build-time).
Public Processes Legal Issues Verification using YAWL
291
3 PUBLIC PROCESS
VERIFICATION APPROACH
3.1 Definitions
The following definitions are necessary for
understanding the rest of the paper:
Workflow-net: is a subclass of Petri nets often used
in the context of workflow management and business
process management (systems) (Process Mining
course) WF-nets specifies the dynamic behaviour of
a single case in isolation (Van Der Aalst, 2000). In
fact, one of the most important notions in the WF-nets
is that it has a well-defined input start and output end.
Yawl: stands for Yet Another Workflow Language, is
a workflow system (business process management
system) fully open-sourced. It is a language with a
strictly defined execution semantics inspired by first:
Petri Nets with graphical representation, able to
support verification (Corradini et al, 2018), also
YAWL is based on the workflow patterns
(http://www.workflowpatterns.com). Yawl is a
successor of Workflow-Nets (Adams and Hofstede,
2020).
Soundness Property: A Workflow-net is sound if and
only if the following properties hold:
Proper Completion: if the sink place is
marked, all other places are empty,
Option to Complete: it is always possible to
reach the marking that marks just the sink
place, and
Absence of Dead Parts: for any transition
there is a firing sequence enabling it.
Law: the law is any system of regulations to govern
the conduct of the people of a community, society or
nation, in response to the need for regularity,
consistency and justice based upon collective human
experience (Law dictionary).
Obsolete Law: The term is applied to statutes which
have become inoperative by lapse of time, either
because the reason for their enactment has passed
away, or their subject matter no longer exists, or they
are not applicable to changed circumstances, or are
tacitly disregarded by all men, yet without being
expressly abrogated or repealed (The law dictionary).
Legal Void (Vacuum): intuitively refers to a space in
which there is no law, is considered as a gap in the
law. In fact, it has a largely pejorative connotation for
those who feel that the law is the best means of
binding individuals and to ensure that everyone's
freedom is respected, while it will have a very
positive connotation for people who see the law as a
negative constraint and therefore, in its absence, a
space of freedom (Dinh, 2007).
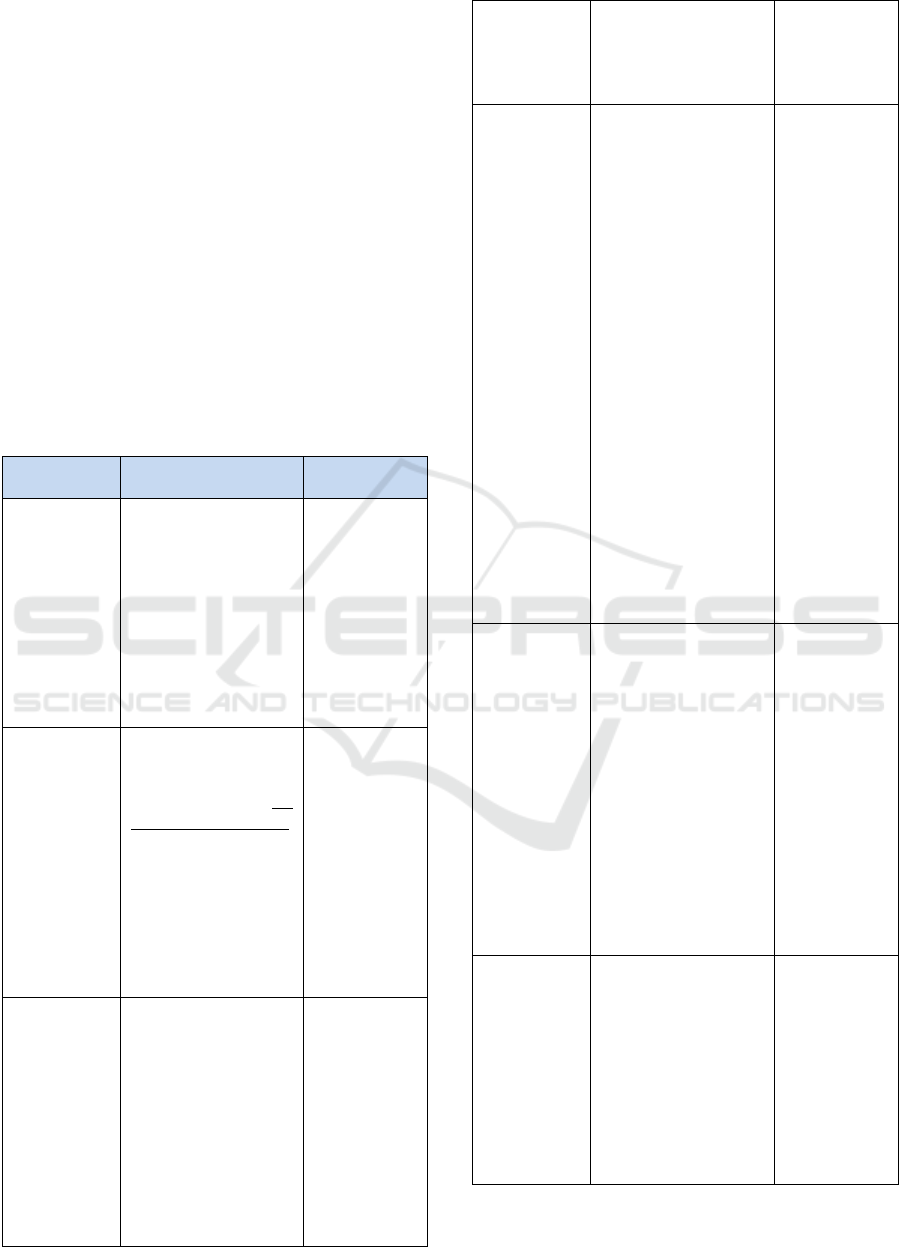
Figure 1: Framework for governmental processes design
(Cherouana et al, 2017).
3.2 Research Context
In previous works, a framework dedicated to generate
public processes from their legal texts was proposed
(Mahdaoui and Cherouana, 2012). The developed
solution was an evolutionary framework comprising
a sequence of two major phases allowing a priori
design in compliance with the law (see Fig. 1),
namely: a) legal design, b) operational design
(Cherouana et al, 2017).
The following table gives a brief description of
each phase as well as their inputs and outputs:
Table 2: Public process design phases.
N° Phase Input Description Output
1
Legal
Design
Legal
corpus
Extract from
the legal texts
the different
characteristics
constituting
the public
process and
represent it
with the
workflow-net
formalism.
Global
Model
(Abstract
Process)
2
Operational
Design
Current
models
&
Abstract
process
Add the
operational
aspect not
necessarily
defined in the
law to the
abstract
process and
specific to
each public
institution.
Public
Process
ready to
deployme
nt
Despite, the conformity of the generated process
model with the law, it cannot be definitely said that it
is valid and ready to be deployed yet. For the simple
reason that regulations and legal texts may include
ENASE 2021 - 16th International Conference on Evaluation of Novel Approaches to Software Engineering
292

some shortcomings that certainly have a negative
impact on process validity.
Accordingly, we believe that detecting gaps and
inconsistencies in the legislation is of great
importance to ensure that the designed public process
will act properly when implemented.
Hence, we aim to propose verification approaches
at different steps of the process development as
depicted in the diagram (see Fig. 2), to be specific: a)
legal corpus verification, b) abstract process
verification, and c) global model verification.
Figure 2: Steps of process development with verification
tasks.
Indeed, we have previously proposed a pre-
verification approach (Mezaache and Mahdaoui,
2020) a verification of the consistency of the legal
corpus, that will serve as a basis for extracting the
process at a very early stage (before "legal design"
phase).
Therefore, in the current paper, we are interested
in the verification of the Abstract Process (see the
coloured verification task in figure 2).
3.3 Abstract Process Verification
Approach
So that, in this sub-section, we detail the verification
of the generated model from the “Legal Design”
phase: the abstract process. Which is a twofold
procedure: Formal verification & Informal validation.
3.3.1 Formal Verification
The abstract process is the result of the legal design
phase in the development of the process. During this
phase a law study is performed to extract the
activities, roles and constraints of the to-be process,
besides the logic of the control-flow of the latter, then
represented it in workflow-net formalism. At this
stage, our concern in this paper is to check that the
generated process is not subject to problems.
According to PR Will Van Der Aalst soundness
property is at the same time basic and most important
property that each WF-net model should satisfy for
being correct and free of anomalies.
YAWL, is concerned with the design time
detection of certain undesirable characteristics in
process models. It provides two verification
approaches; the first approach is based on the
ResetNet theory which supports the use of reduction
rules while the second proposes the use of the
wofYawl analysis algorithm (based on the concept of
transition invariants “petri-net”) (Adams and
Hofstede, 2020).
Basically, the abstract process (i.e., global model)
will be verified by the Reset-Net analysis tool to
check the soundness property. Remember that the
process model is an abstraction of the law, as such
whether the result of the analysis is positive or
negative, it reflects the consistency of the law.
Here comes our proposal to interpret the results of the
soundness property legally.
Results Interpretations: To do so, we proceed by
interpreting the negative results of soundness
property analysis:
Deadlock: In fact, the existence of deadlocks means
that one of the two properties “Option to complete”
or “Proper completion” is not verified. Indicating,
that there is no appropriate path to take (set of actions)
through the model. Which implies that no
corresponding legal text(s) that explains what is the
next step or how to deal with this situation: this is
called the law void.
Dead Parts (Transitions): The existence of dead
parts means that the property “Absence of dead parts”
is not verified. This means that there are tasks that
cannot be performed in any scenario, this could
indicate that the law is obsolete and doesn't respond
to the needs anymore, or simply it is not useful.
The following table represents the resulting links
between the four soundness properties and legal
problems:
Table 3: Correspondence table between WF-nets properties
(soundness) and legal problems.
Problem Encountered in The
Process Model Analysis (Wf-
Nets Properties)
Legal Interpretation
(Legal Problems)
P1: Existence of deadlocks
(The execution is blocked
before reaching the end).
=> property 'Option to
complete /proper completion'
is not checked.
- Legal void.
- Law incompleteness
Public Processes Legal Issues Verification using YAWL
293
Table 3: Correspondence table between WF-nets properties
(soundness) and legal problems (Cont).
Problem Encountered in The
Process Model Analysis (Wf-
Nets Properties)
Legal Interpretation
(Legal Problems)
P2: Existence of transitions
that cannot be executed in any
scenario (Adams and
Hofstede, 2020).
=> property 'Absence of dead
parts' is not checked.
- Legal texts not
useful.
- Law obsolete.
- Law that does not
fulfil the needs.
P3: Multiple tokens in a place
at the same time.
=> Safeness property is not
checked.
-Conflict situation.
-Inconsistency.
It can be concluded that if there exists problems in
the analysis report of the soundness property, then the
legal texts on which the process is based are source of
these problems. Therefore, it is necessary to return to
the correspondence table to extract the appropriate
legal interpretations of the problems encountered.
3.3.2 Informal Validation
The abstract process needs to be approved by public
institution managers, owing to the fact that this model
is considered as a draft that each public institution
will enrich/complete it with its own operational
aspect (new activities, roles, constraints, gates…etc.).
That’s why, public institution has an extremely
important role in the final decision of the process
model validity.
The results of the formal verification with both
interpretations and eventual recommendations will be
sent to the public institution for study. Even though
the formal verification may contain some issues, it is
up to them to decide whether these problems are fatal
and need to be resolved, so the development process
will be suspended until solutions are put in place or
not.
This validation is informal, it comes back to the
fact that the decision is made by humans and could
not be formalized or automated.
4 CASE STUDY
We have chosen the process of managing competitive
entrance exams to the Higher School of Social
Security 'HSSS' (public institution) to obtain a
professional master's degree, for applying the
proposed validation approach. Three categories of
applicants can be distinguished: 1) External
applicants: coming from universities, preparatory
schools, etc. 2) Applicants from the social security
organisms, and 3) Foreign applicants: from foreign
countries.
The process for the first category was generated
from these legal texts 1) executive decree n°649 from
the Ministry of Higher Education and Scientific
Research 'MHESR' official site:
https://www.mesrs.dz/fr/chapitre3 , and from 2) the
school internal texts, in BPMN language. However,
the second and third categories were generated from
only internal texts because of the lack of legislation.
Process Generation in BPMN:
Case 1: First Category
Figure 3: A part of the process: ' Verification of the result
of the university course' in BPMN.
Case 2: Second Category
Figure 4: A part of the process in BPMN for competitors
from the social security organisms.
Process Transformation:
Then, the process will be transformed to the
workflow-nets formalism.
Case 1: First Category
Figure 5: The transformed process model in YAWL.
ENASE 2021 - 16th International Conference on Evaluation of Novel Approaches to Software Engineering
294
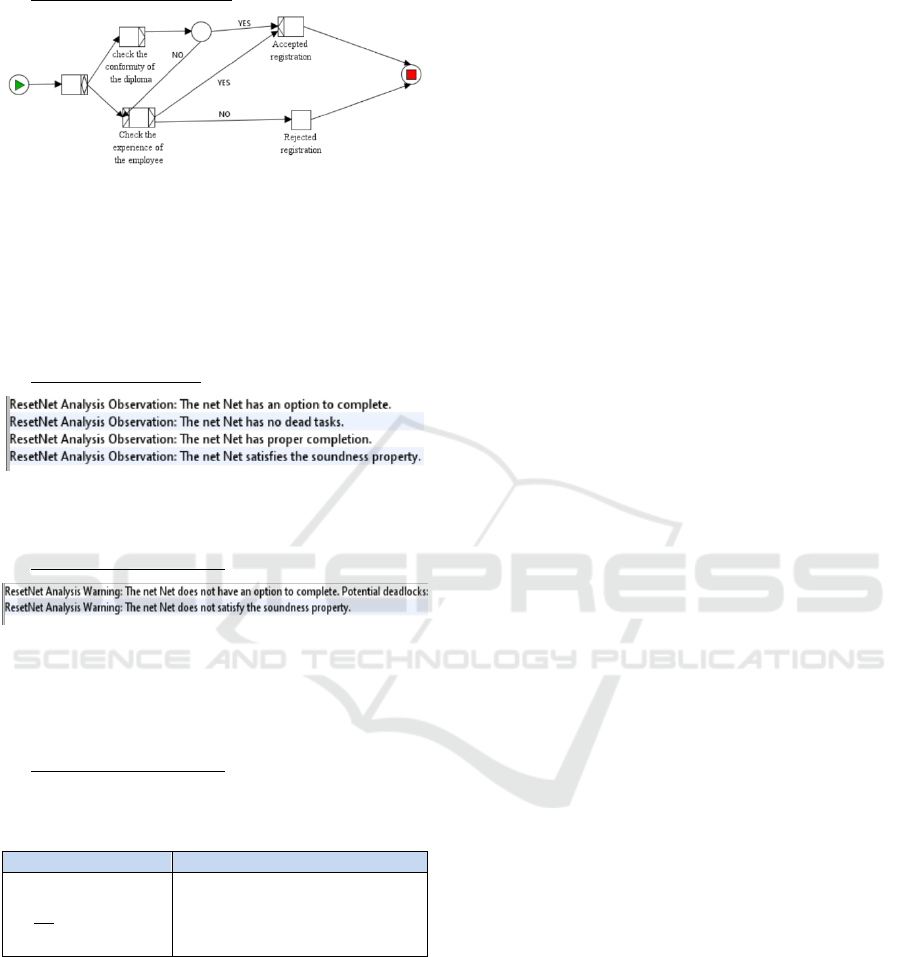
Case 2: Second Category
Figure 6: The transformed process model in YAWL.
Process Analysis (Problems Identification):
The process will be verified using the Reset-net
analysis tool of YAWL. It gives the observation about
the three properties of the soundness property:
Case 1: first category
Figure 7: The analysis results of soundness property by
ResetNet.
Case 2: second category
Figure 8: The analysis results of soundness property by
ResetNet reveals deadlocks for the second category.
Report Generation and Recommendations:
Case 2: second category
Table 4: Recommendations for the process of competitors
from the social security organisms.
Problem number Recommendations/Diagnosis
P1: is detected
- Need to Legislate Laws
concerning the competitors from
the social security organisms by
the MLSS
Discussion.
This case study was a sort of comparative application
of the presented approach on two process model
variants: the external competitors and those from the
social security organisms.
The results showed that the soundness property of
the modelled process of external competitors (first
category) are maintained, so it can surely be said that
the process is valid and could be safely deployed.
Nevertheless, the verification of the second
variant process (second category) pointed out some
problems: " deadlocks ", returning to the
correspondence table, this is due to the "legal
vacuum", i.e., the lack of legal texts clarifying how to
deal with competitors registration files. So, the
process isn’t valid and legislation activity is needed.
5 CONCLUSION
The effectiveness and efficiency of public processes
are the key for e-government system success and
improvement. Unfortunately, this cannot be achieved
without maintaining compliance with the law.
In this context, the generated processes comply
with the law because they are intended for the public
sector.
Nevertheless, the law can sometimes be source of
problems, resulting in the invalidity of the process,
which could fail once deployed.
We believe, therefore, that detection of law
deficiencies could help tremendously in improving
public processes.
Hence, we propose an approach that interpret the
results of correctness analysis of soundness property
of the process. By leveraging the analysis features
offered by workflow-net (YAWL tool).
These interpretations allow to detect legal texts
problems whom the process is based on. Then, a
report will be sent to the public administration
managers to proceed the informal validation and give
the final decision.
Since this type of analysis or verification is tidily
concerned with the model quality (Van Der Aalst in
Process Mining course). We intend to proceed the
data perspective verification to integrate more
semantics and to put interest in both content and
model in future works.
REFERENCES
Adams, M., & Ter Hofstede, A. (2020). YAWL User
Manual. User manual, The YAWL Foundation.
Alpar, P., & Olbrich, S. (2005). Legal requirements and
modelling of processes in e-government. Electronic
journal of e-government, 3(3), 107-116.
Aravanis, T., Demiris, K., & Peppas, P. (2018, November).
Legal Reasoning in Answer Set Programming. In 2018
IEEE 30th International Conference on Tools with
Artificial Intelligence (ICTAI) (pp. 302-306). IEEE.
DOI: 10.1109/ICTAI.2018.00055
Birukou, A., D’Andrea, V., Leymann, F., Serafinski,
J., Silveira, P., Strauch, S., & Tluczek, M. (2010,
Public Processes Legal Issues Verification using YAWL
295

December). An integrated solution for runtime
compliance governance in SOA. In International
Conference on Service-Oriented Computing (pp. 122-
136). Springer, Berlin, Heidelberg.
Cherouana, A., Mahdaoui, L., & Khadraoui, A. (2017).
BPM-based framework for e-government processes
improvement: legal requirements integration.
International Journal of Intelligent Information and
Database Systems, 10(1-2), 21-50.
Corradini, F., Falcioni, D., Polini, A., Polzonetti, A., & Re,
B. (2010, August). Designing quality business
processes for e-government digital services. In
International Conference on Electronic Government
(pp. 424-435). Springer, Berlin, Heidelberg. DOI
https://doi.org/10.1007/978-3-642-14799-9_36.
Corradini, F., Fornari, F., Polini, A., Re, B., & Tiezzi, F.
(2018). A formal approach to modeling and verification
of business process collaborations. Science of
Computer Programming, 166, 35-70. DOI
https://doi.org/10.1016/j.scico.2018.05.008.
De Moura Araujo, B., Schmitz, E. A., Correa, A. L., &
Alencar, A. J. (2010, March). A method for validating
the compliance of business processes to business rules.
In Proceedings of the 2010 ACM Symposium on
Applied Computing (pp. 145-149). DOI https://doi.
org/10.1145/1774088.1774117
Dinh, A. M. H. (2007). Le « vide juridique » et le « besoin
de loi ». Pour un recours à l'hypothèse du non-droit.
L'Année sociologique, 57(2), 419-453.
Gilliot, M., & Accorsi, R. (2009). Runtime predictions of
policy violations in automated buisness processes.
Extended Abstract: presented at Prime Life/IFIP
Summer School Program, 7-11.
Governatori, G., Milosevic, Z., & Sadiq, S. (2006, October).
Compliance checking between business processes and
business contracts. In 2006 10th IEEE International
Enterprise Distributed Object Computing Conference
(EDOC'06) (pp. 221-232). IEEE.
Groefsema, H., & Bucur, D. (2013). A survey of formal
business process verification. Proc. Int. Sym. Business
Modeling and Software Design, Noordwijkerhout, The
Netherlands.
Hasan, M. M., Loucopoulos, P., Anagnostopoulos, D., &
Nikolaidou, M. (2015, December). Regulatory
requirements compliance in e-Government service
development. In 2015 18th International Conference on
Computer and Information Technology (ICCIT) (pp.
254-259). IEEE.
Hashmi, M., Governatori, G., Lam, H. P., & Wynn, M. T.
(2018). Are we done with business process compliance:
state of the art and challenges ahead? Knowledge and
Information Systems, 57(1), 79-133.
He, Y., Liu, G., Xiang, D., Sun, J., Yan, C., & Jiang, C.
(2018). Verifying the correctness of workflow systems
based on workflow net with data constraints. IEEE
Access, 6, 11412-11423.
Jiang, J., Aldewereld, H., Dignum, V., Wang, S., & Baida,
Z. (2015). Regulatory compliance of business processes.
AI & society, 30(3), 393-402.
Law dictionary, https://dictionary.law.com/Default.aspx?
selected=1111, last accessed 20/02/2020
Layne, K., & Lee, J. (2001). Developing fully functional E-
government: A four stage model. Government
information quarterly, 18(2), 122-136.
Mahdaoui, L., & Cherouana, A. (2012). Towards a
methodological framework for the Government Process
Management. In International Conference on Research
Challenges in Information Science (RCIS).
Mezaache, K., & Mahdaoui, L. (2020, September). Law
analysis to support public process design. In
Proceedings of the 13th International Conference on
Theory and Practice of Electronic Governance (pp.
742-745).
Process Mining: Data Science in Action,
https://www.coursera.org/learn/process-mining/, last
accessed 20/02/2020.
The law Dictionary, https://dictionary.thelaw.com/
obsolete/, last accessed 20/02/2020
Van Der Aalst, W. M. (2000). Workflow verification:
Finding control-flow errors using petri-net-based
techniques. In Business Process Management (pp. 161-
183). Springer, Berlin, Heidelberg.
Van Der Aalst, W. M., & Ter Hofstede, A. H. (2005).
YAWL: yet another workflow language. Information
systems, 30(4), 245-275.
ENASE 2021 - 16th International Conference on Evaluation of Novel Approaches to Software Engineering
296
