
Time Influence on Security Protocol
Sabina Szymoniak
a
Department of Computer Science, Czestochowa University of Technology, Poland
Keywords:
Formal Methods, Security Protocols, Timed Analysis, Verification.
Abstract:
The paper discusses the problem of influence of time parameters on protocols security. It is a significant issue
because some periods may affect us to be or not to be in the real and virtual world. Time can decide about
the security of our private data, money and many others. It is necessary to check whether used protocols
provide an appropriate security level of our data. Also, Intruder capabilities and knowledge may evolve with
time. With wrongly selected time parameters, the Intruder may perform an attack on protocol and deceive
honest users. The research has expanded the formal model and computational structure designed previously.
Based on this, we implemented a tool. This tool can calculate the correct protocol execution and carry out
simulations. Thanks to this checking the possibility of Intruder attack including various time parameters was
possible. We presented experimental results on NSPK protocol and WooLamPi protocol examples.
1 INTRODUCTION
Time is one of the most significant parameters of the
private and professional life of every person. Frac-
tions of seconds often decide about our to be or not
to be in this world. Internet communication is simi-
lar. Every day at any time Internet users sends much
information electronically. They want to participate
in secure communications. It means the information
will be delivered at the right time and will remain safe
and intact (
ˇ
Cibej Uro
ˇ
s et al., 2019).
Our communication is secured by security proto-
cols. Unfortunately, every message is exposed to a
wicked user. This user is called Intruder. The Intruder
can steal and use transmitted data. Sometimes, time
favours Intruder. The transmission time can give In-
truder many opportunities to carry out an attack. We
use timestamps to determine the date and time of the
message generation. Despite the use of them, the at-
tacker can successfully exploit message. For this rea-
son, it is significant to verify security protocols to pro-
tect against unwanted situations.
Also, respectable monitoring and solid users iden-
tification is a very important step in ensuring an ade-
quate level of resource security. Unfortunately, there
are many types of attacks. Each of them can share the
features of other attacks. One of the most significant
attacks is a Man In The Middle Attack. This attack
consists of executing a protocol not directly between
a
https://orcid.org/0000-0003-1148-5691
two honest users (A ⇔ B) but executing a protocol
with Intruder standing in the middle of the communi-
cation (A ⇔ I ⇔ B).
Modelling and verification of security protocols
(SP) is an important step in avoiding the Intruder at-
tack. For the last fifty years, a scientist from different
countries proposed many methods of SP modelling
and verification. We can indicate inductive methods
(Bella and Paulson, 1997), deductive methods (Bur-
rows et al., 1990), model checking (Kurkowski, 2013)
and others methods (Chadha et al., 2017; Basin et al.,
2018; Siedlecka-Lamch et al., 2016; Nigam et al.,
2016; Perh
´
a
ˇ
c et al., 2019) as examples. These meth-
ods started to appear and evolve with the first secu-
rity protocols such as Needham Schroeder Public Key
protocol (Needham and Schroeder, 1978). The anal-
ysis of the protocols became more exact after the in-
troduction of the Intruder model by Dolev and Yao
(Dolev and Yao, 1981).
Time modelling is an integral part of a protocol
study. The most important times, which must be con-
sidered, are delays in the network. These values have
a huge influence on the duration of the protocol ses-
sion. In the network, different situations occur. Se-
lecting the appropriate interval of delay in the network
values we can obtain a critical influence on the proto-
col correctness and also on Intruder capabilities.
Corin proposed a very interesting approach in
(Corin et al., 2007) and (Corin et al., 2004). In this
approach, Corin modelled SP using timed automata
Szymoniak, S.
Time Influence on Security Protocol.
DOI: 10.5220/0010388701810188
In Proceedings of the 16th International Conference on Evaluation of Novel Approaches to Software Engineering (ENASE 2021), pages 181-188
ISBN: 978-989-758-508-1
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
181

taken from the Alur and Dill work (Alur and Dill,
1994). Corin noticed the SP sensitivity to the pas-
sage of time. They presented the individual users’ be-
haviours by individual automata. Communication be-
tween the automata, which modelled users, was syn-
chronised accordingly. However, it was necessary to
prepare a precise and very detailed protocol specifica-
tion. Such a specification should enable disambigua-
tion of users behaviours. Also, the time values should
be set on each state.
Kurkowski formal model (Kurkowski, 2013) is
base for the presented research. This model enables
the timed and untimed SP examination. For the needs
of our analysis, we extended this model to consider
delays in the network. Only in (Jakubowska and
Penczek, 2007b; Jakubowska and Penczek, 2007a)
Jakubowska and Penczek considered delays, but they
did not continue these research. To perform our
considerations, we used Kurkowski and Jakubowska
and Penczek models. We extended combined re-
search methods (Kurkowski and also Jakubowska and
Penczek methods). We include the ability to calcu-
late the duration of individual operations performed
during the protocol execution. Delay in the network
values and encryption and decryption times could be
calculated according to the selected probability distri-
butions. Thanks to this, it is possible to simulate the
protocols executions in the network in a correct way.
The main contributions of this paper are a method and
tool which allow to examined time-sensitivity of SP.
The organisation of the rest of this paper is as
follows. In the next Section, we presented our pa-
rameters assumptions. Next, we introduced Need-
ham Schroeder Public Key protocol (NSPK) and
WooLamPi protocol (WLP) as examples. The third
Section presented research assumptions and experi-
mental results for exemplary protocols. The last Sec-
tion included our conclusions and plans for the future.
2 ASSUMPTIONS AND
PROTOCOLS
2.1 Research Methodology
This paper is an extension and continuation of previ-
ous research (Szymoniak et al., 2015) and (Szymo-
niak et al., 2017). Mentioned papers introduced the
formal model and the computational structure. The
formal model enables defining sets of time conditions,
the protocol step and a protocol.
All definitions allow the full specification of a
timed and untimed protocol. We include external and
internal actions performed during the protocol execu-
tion and time conditions. In time conditions, we took
into account delays in the network. Time conditions
are imposed on each step and also on the whole pro-
tocol execution. Thanks to this, we can consider time
influence on protocol step and the protocol.
The computational structure makes it possible to
consider the protocols executions in the physical net-
work. Thanks to this, we can consider the protocol
with Intruder. The Intruder is a user who may try to
deceive other users. Intruder’s behaviour may cause
not the fulfilment of protocol goals. We consider four
Intruder models: Dolev-Yao model, restricted Dolev-
Yao model, lazy Intruder model and restricted lazy
Intruder model (Dolev and Yao, 1981).
The main part of computational structure are def-
initions of timed protocol step, users knowledge and
the ways of its acquiring and time dependencies. In
case of time dependencies we use time of composing
the message (T
c
), step time (minimal T
min
k
, current T
k
,
maximal T
max
k
), session time (minimal T
min
s
, current
T
s
, maximal T
max
s
), lifetime (T
out
k
).
Lifetime in k-th step indicates the maximal wait-
ing for a response time. The correct formula for life-
time calculating is as follows:
T
out
k
=
n
∑
i=k
T
max
i
(1)
where:
• k - step number,
• i - step counter, for i = k...n,
• n - number of steps in the protocol,
• T
out
k
- lifetime in the k-th step,
• T
max
i
- maximal step time.
In (Szymoniak et al., 2017), we presented other
formulas.
For the research, we implemented a tool in C++.
This tool enabled testing including the assumptions
adopted at each research stage. We presented the tool
activities in detail in (Szymoniak, 2021). The tool
enables three kinds of research during which we can
examine all protocol executions:
a) Timed Analysis - which allows examining the du-
ration of the protocol steps and protocol vulnera-
bility on attacks,
b) Delay Simulations - which allows performing
simulations of delays in the network and their in-
fluence on Intruder activity,
c) E&D Simulations - which allows performing sim-
ulations of encryption and decryption times and
their influence on Intruder activity.
ENASE 2021 - 16th International Conference on Evaluation of Novel Approaches to Software Engineering
182

The most interesting aspect of the tool is the ability to
set one of four statuses for each executions:
a) correct - for executions completed in the correct
time interval with preserved time conditions,
b) !min - for executions completed with preserved
time conditions, but current session time T
s
was
lower than minimal session time T
min
s
,
c) !max - for executions completed with preserved
time conditions, but current session time T
s
was
greater than maximal session time T
max
s
,
d) error - for executions where any time condition
was not fulfilled (execution was ended with error).
By preserved time conditions we mean conditions de-
fined in every protocol step. So if the T
k
is lower than
T
out
k
for k-th step, we can mark the time conditions
preserved in the k-th step were met. Also, the protocol
must fulfil dependencies limiting its duration. When
the time conditions for every step are met and session
time is between minimal and maximal session time,
the protocol was made correctly (situation a)). Also,
we must consider some different situations. When the
Intruder tries to execute the protocol, he may not have
the right set of knowledge for ending the protocol.
Then, the Intruder must establish a parallel session
to acquire knowledge. Time of additional steps, exe-
cuted between two steps from basic execution, must
be added to basic step time and also to session time.
If Intruder actions do not consist of some operations
like encryption or decryption, the step time (and ses-
sion time) can be lower than minimal values for this
parameter calculated according to protocol structure
(situation b)). On the other hand, Intruder actions in
basic and additional steps may consist of all protocol
operation, so the step time and session time can be
greater than maximal values for this parameter calcu-
lated according to protocol structure (situation c)).
Situations b), c) and d) indicate a network failure.
The distinction between the four situations was neces-
sary to determine what the Intruder capabilities were
and also to know how the activity of an Intruder af-
fects other users and the whole network. The occur-
rence of the situation d) ends tool work with an error.
These assumptions mean that the action of a given ex-
ecution is possible as long as the session time is be-
tween T
min
s
and T
max
s
and the time conditions are met.
In (Szymoniak et al., 2017) we used the constant
delays value. Then, we decided to consider the ran-
dom values of delays in the network and carry out
simulations of the computer network including these
values. Thanks to this, it will be possible to demon-
strate the influence of this time parameter on the pro-
tocol correctness and Intruder capabilities. Also, we
decided to consider the influence of encryption and
decryption times on tested properties. We carried out
research using an abstract time unit ([tu]). It is an ar-
bitrarily selected and considered period.
2.2 Security Protocol Example
The most characteristic security protocol is the Need-
ham Schroeder Public Key protocol (NSPK), pro-
posed in (Needham and Schroeder, 1978). The pur-
pose of this protocol is mutual authentication of two
users. The scheme of timed version
1
of this protocol
in Alice-Bob notation is as follows:
α
1
A, B : {T
A
, I
A
}
K
B
α
2
B, A : {T
A
, T
B
}
K
A
α
3
A, B : {T
B
}
K
B
There are two users A and B in this protocol. In
the first step, user A generates his timestamp. Then,
he creates a ciphertext which contains timestamp T
A
and his identifier I
A
. The message is encrypted with
the public key of user B. In response, B sends to A his
timestamp and newly generated timestamp T
B
. This
message is encrypted with the key K
A
. In the last step,
A confirms his identity by sending his timestamp en-
crypted with K
B
to B.
Our tool generated eighteen executions of NSPK.
These executions differed from each other in the pa-
rameters used by the Intruder. However, only fourteen
of them are real executions, i.e. those that can exe-
cute on a computer network. Remaining executions
are impossible to perform. One of the participants in
these executions is not able to acquire relevant knowl-
edge. Designation of a real protocol executions set
was done using SAT-solver. These executions were
not included in our analysis.
The next protocol is symmetric WooLamPi proto-
col (WLP). WLP aimed in one way users authentica-
tion with public keys and the trusted server. Its timed
version scheme in Alice-Bob notation is as follows:
α
1
A, B : I
A
α
2
B, A : T
B
α
3
A, B : {T
B
}
K
AS
α
4
B, S : {I
A
, {T
B
}
K
AS
}
K
BS
α
5
S, B : {T
B
}
K
BS
There are three users in this protocol: A, B and
S (the trusted server). In the first step, user A sends
to B his identifier. Then, B generates his timestamp
and sends them to A. In third step user A creates a ci-
phertext which contains timestamp T
B
and sends them
to B. The message is encrypted by A key K
AS
which
is shared between user A and server. User B cannot
1
Timed version of the protocol was created by replacing
the random numbers (nonces) by timestamps
Time Influence on Security Protocol
183
decrypts this message, so he send it with its ID en-
crypted by key K
BS
to the server. In response, the
server sends back to B his timestamp encrypted by
key K
BS
and confirms A’s identity to B.
We assumed that Intruder impersonates only hon-
est users, not the trusted server. This restriction
caused that the implemented tool generated only four-
teen executions. Next, SAT-solver marked six of them
as impossible to execute.
The WLP executions structure is different than the
structure of NSPK protocol executions. The proto-
col initiator occurs in the first three protocol steps
only. He does not generate any confidential informa-
tion. The recipient (user with whom initiator desires
to communicate) in protocol occurs in all protocol
steps, and in fourth and fifth steps communicates with
the server. Recipient generates its timestamp. How-
ever, during the generation of executions, we adopted
assumption limiting Intruder capabilities as a recip-
ient. Intruder as a recipient can appear in two sit-
uations: as himself (with his cryptographic objects)
and impersonating an honest user and using user data
(cryptographic objects).
3 EXPERIMENTAL RESULTS
We researched three stages. In the first stage, we eval-
uated the security of the protocol for each real execu-
tion during timed analysis. Values of encryption and
decryption times were constant. They were equal to 4
[tu]. We assumed the interval of delay in the network
value (1 - 3 [tu]) and constant current delay in the net-
work (1 [tu]). The second and third stages involved
simulation tests for all real protocol executions. In the
second stage, we assumed constant values of encryp-
tion and decryption times (2 [tu]) and the interval of
delay in the network (1 -10 [tu]). We randomised cur-
rent delay values with the following probability dis-
tributions: uniform, normal, Cauchy’s, exponential.
We selected probability distributions to model dif-
ferent loads of the computer network. Normal and
uniform distributions modelled real network work.
This network sometimes has problems with the load,
but they do not affect the activity of users. Cauchy’s
distribution modelled the heavily loaded network. In
this network, there are many users, but few resources.
We try to model a fast network by an exponential dis-
tribution. In that network, there are no problems. In
the third stage of the study, we consider constant de-
lay values (2, 4, 6, 8, 10 [tu]). We randomised en-
cryption and decryption times according to a uniform
probability distribution. Also, we assumed that no
one can guess timestamp. We tested every real exe-
cution in a thousand test series during the simulation.
We will present our experimental results in more de-
tail on NSPK and WLP protocol example. Obtained
results explain the behaviour of protocol and its sen-
sitivity to time flow.
3.1 Times Analysis for NSPK Protocol
For the first stage of studies, we calculated follow-
ing lifetimes for steps: T
out
1
= 35 [tu], T
out
2
= 23 [tu],
T
out
3
= 11 [tu]. Also, we calculated minimal and max-
imal session times T
min
s
= 29 [tu], T
max
s
= 35 [tu].
Let’s analyze one of NSPK execution that maps
Lowe’s attack
2
. In this execution, Intruder uses user
A’s timestamp and his ID and public key. Unfortu-
nately, Intruder does not have the appropriate knowl-
edge to execute step α
1
. Therefore, he must establish
additional execution (β) to acquire knowledge of T
A
.
In Table 1 we show timed analysis of attacking
execution. This analysis includes times of basic (col-
umn BS ) and additional (column AS) steps and com-
ments regard to steps executions. Each step time con-
sists of four values: encryption time, time of confi-
dential information generation, delay in the network
and decryption time. In basic steps also appeared five
value (on the first position). This value is an addi-
tional step time which was executed between earlier
and current basic step.
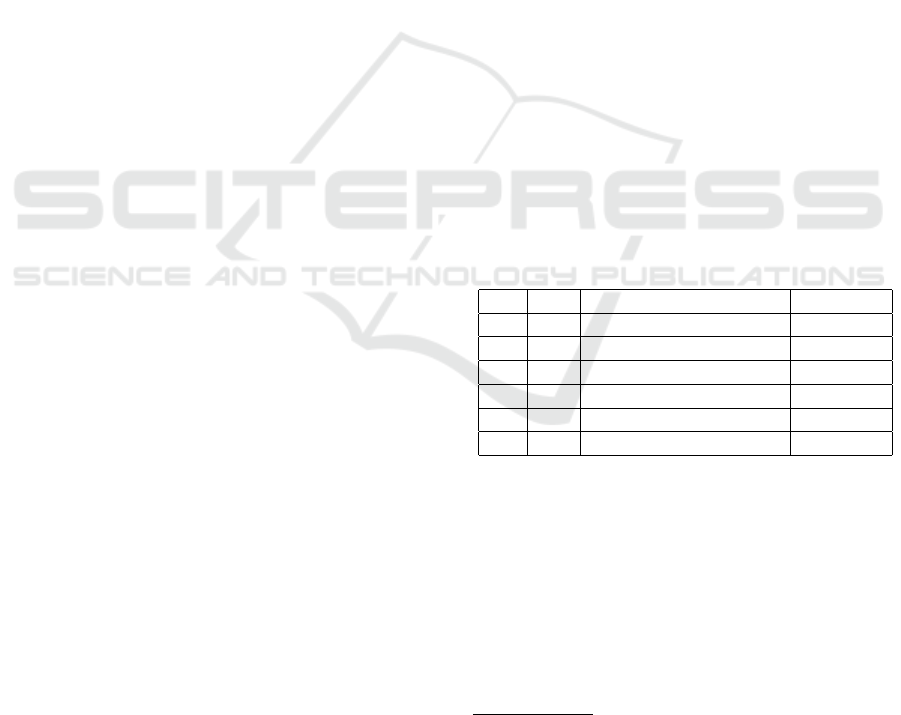
Table 1: Timed analysis of first attacking execution.
BS AS Time [tu] Comment
α
1
4 + 1 + 1 + 4 = 10 ok
β
1
4 + 0 + 1 + 4 = 9 ok
β
2
1 4 + 1 + 1 + 4 = 10 ok
α
2
19 + 4 + 0 + 1 + 4 = 28 !T
out
2
α
3
4 + 0 + 1 + 4 = 9 !T
max
s
β
3
18 + 4 + 0 + 1 + 4 = 27 !T
out
3
&&!T
max
s
Step α
1
lasted 10 [tu] (encryption time - 4 [tu],
time of confidential information generation - 1 [tu],
delay in the network - 1 [tu], and decryption time - 4
[tu]). Time conditions for the first step were met. Be-
fore step α
2
had to execute additional steps (β
1
and
β
2
). These steps lasted 19 [tu]. Additional steps time
made that the step α
2
should not be executed because
T
out
2
will not be exceeded. Step α
2
lasted for 28 [tu].
The lifetime for the second protocol step was equal to
23 [tu]. In this situation, the honest user should cancel
2
α
1
B, I : {I
B
, T
B
}
K
I
,
β
1
I, A : {I
I
, T
I
}
K
A
,
β
2
A, I : {T
I
, T
A
}
K
I
,
α
2
I, B : {T
B
, T
A
}
K
B
,
α
3
B, I : {T
A
}
K
I
,
β
3
I, A : {T
A
}
K
A
.
ENASE 2021 - 16th International Conference on Evaluation of Novel Approaches to Software Engineering
184
the communication should. If for some reason com-
munication would continue, at α
3
a similar situation
would occur. This step will last for 9 [tu] (encryption
time - 4 [tu], time of confidential information gener-
ation - 0 [tu], delay in the network - 1 [tu], and de-
cryption time - 1 [tu]). Please note that, when we add
previous steps times to session time, T
s
will be equal
to 47 [tu], while T
max
s
is equal to 35 [tu] for adopted
assumptions. Also, T
out
3
for additional step β
3
will not
be exceeded. This step must include α
2
and α
3
steps
times, so β
3
step time will be equal to 27 [tu] and will
be greater than T
out
3
. Session time for this step would
be greater than T
s
. It is impossible to conduct an at-
tack on this protocol for such time parameters.
Let’s analyse another attacking execution which
shows the Man In The Middle Attack on NSPK pro-
tocol. In this case, Intruder must establish additional
execution in order to perform an attack
3
. The attacker
uses the entire ciphertext, so it does not try to encrypt
and decrypt it. We do not add these times to the total
step time, so these steps are shorter than they should.
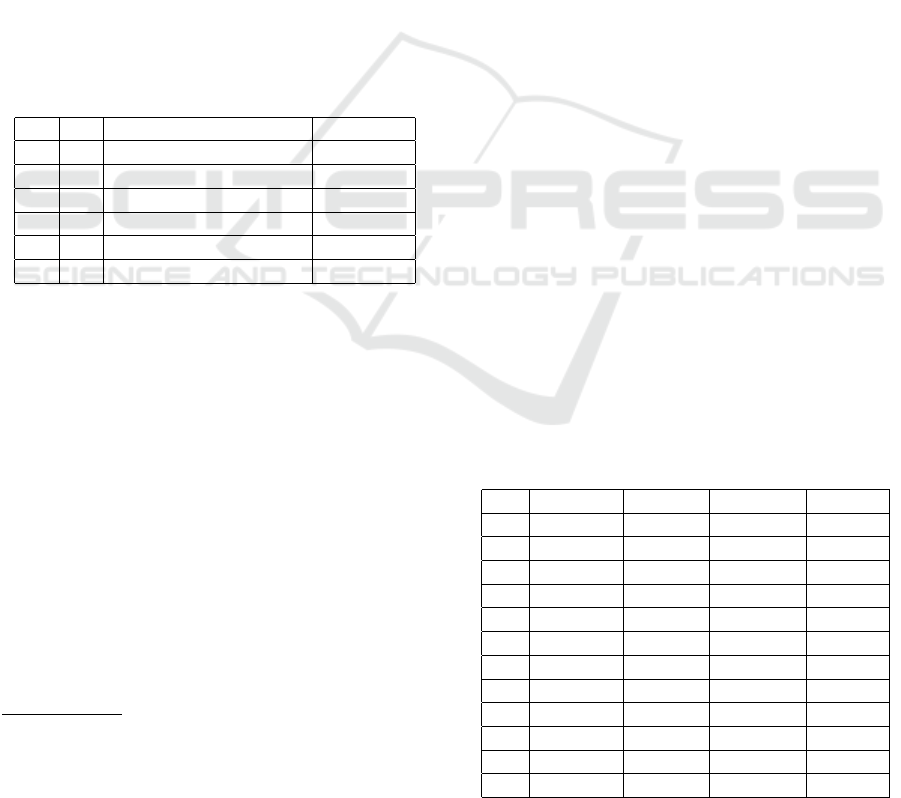
Table 2: Timed analysis of second attacking execution.
α β Time [tu] Comment
α
1
4 + 1 + 1 + 0 = 6 ok
β
1
0 + 0 + 1 + 4 = 5 ok
β
2
4 + 1 + 1 + 0 = 6 ok
α
2
11 + 0 + 0 + 1 + 4 = 16 ok
α
3
4 + 0 + 1 + 0 = 5 ok
β
3
5 + 0 + 0 + 1 + 4 = 10 ok
In Table 2 we show timed analysis of this execu-
tion. The initiator of this execution is user A, so he
generates his timestamp and encrypts the message.
We add these times values to the step time. This
step receiver is an Intruder who impersonates the user
B. In this execution Intruder uses user B’s key and
timestamp, so he cannot decrypt messages which are
addressed to user B. Decryption time would not be
added to the step time. According to above analy-
sis, step α
1
lasted 6 [tu] (encryption time - 4 [tu],
time of confidential information generation - 1 [tu],
delay in the network - 1 [tu], and decryption time - 0
[tu]). Time conditions for the first step were met. Be-
fore step α
2
had to be executed, additional steps (β
1
and β
2
) must be performed. In step α
1
an Intruder
possessed entire ciphertext which was sent in step β
1
without encryption by him. Encryption time would
3
α
1
A, I(B) : {I
A
, T
A
}
K
B
,
β
1
I(A), B : {I
A
, T
A
}
K
B
,
β
2
B, I(A) : {T
A
, T
B
}
K
A
,
α
2
I(B), A : {T
A
, T
B
}
K
A
,
α
3
A, I(B) : {T
B
}
K
B
,
β
3
I(A), B : {T
B
}
K
B
.
not be added to the step time. Please note that for such
executions when the Intruder is message sender in
the current step, encryption time would not be added
to step time, and when the Intruder is message re-
ceiver in the current step, decryption time would not
be added to step time. In step β
2
an Intruder was not
decrypted again. These steps lasted 11 [tu]. Addi-
tional steps time made that step α
2
should be done.
Step α
2
lasted for 16 [tu], while the lifetime for the
second protocol step was equal to 23 [tu]. Time con-
ditions for the second step were met. Steps α
3
and β
3
were executed without problems at 5 [tu] and 10 [tu].
All time conditions for each protocol step were met,
so a Man In The Middle Attack was possible.
3.2 Delays Simulations for NSPK
Protocol
In the second stage, we conducted simulations of the
network using randomly generated current delay in
the network values. For the previously adopted as-
sumptions, we calculated new lifetime values for each
step: T
out
1
= 44 [tu], T
out
2
= 29 [tu], T
out
3
= 14 [tu].
Also, we calculated minimal and maximal session
times: T
min
s
= 29 [tu], T
max
s
= 35 [tu]. Simulations
allowed to verify users behaviour and Intruder activ-
ity in computer networks with a different load. We
present simulations experimental results on uniform
and normal probability distributions examples.
3.2.1 Uniform Probability Distribution
We observed the following results during the simula-
tion of real NSPK executions (using the uniform prob-
ability distribution). To present the results, we num-
bered the possible executions (column No in Table 3).
Table 3: Summary of NSPK simulations with uniform dis-
tribution which ended in correct interval in [tu].
No Min(T
s
) Avg(T
s
) Max(T
s
) Avg(D)
1 17.1 30.73 43.4 5.58
2 18.1 30.69 43.3 5.57
3 α
2
29.6 41.5 5.53
4 39.2 42.4 43.9 3.27
5 17.6 29.89 41.6 5.63
6 36.3 42.56 44 3.15
7 28.5 39.57 44 4.39
8 17.3 29.57 42.6 5.52
9 26.3 41.7 44 2.92
10 17.1 29.47 42.4 5.5
11 17.7 40.75 44 2.75
12 27.7 39.75 44 4.45
Table 3 summarised the session times completed
Time Influence on Security Protocol
185

within the correct time (in [tu]). We showed the small-
est, average, and highest session times (in [tu]) and
the average value of delay in the network. During the
simulation we obtained values greater by 0.1 [tu] from
T
min
s
and equal to T
max
s
.
We observed that only one execution ended below
the correct interval. Also, we observed that for ses-
sions ended with !max status the average session time
ranged between 48.65 [tu] and 57.85 [tu]. The av-
erage delay in the network in these sessions was be-
tween 5.09 [tu] and 6.15 [tu]. The results showed how
the delay value effect on session time, the session cor-
rectness and Intruder activities. Also, they showed the
effect of additional steps executed by Intruder while
the time conditions remain maintained.
3.2.2 Normal Probability Distribution
For some situations, in our tool, we implemented spe-
cific activities. In some cases, we drew out of range
delays in the network values. It was most visible
during simulations with a normal probability distri-
bution. In this phase of simulations only honest exe-
cution have test series with correct and !max statuses.
Rest of executions ended with an error. None of the
test series ended with status !min.
Table 4: Summary of NSPK simulations with normal distri-
bution which was ended in correct interval in [tu].
No Min(T
s
) Avg(T
s
) Max(T
s
) Avg(D)
1 19.78 35.71 43.98 7.37
2 19.85 36.62 43.9 7.65
Table 4 summarised session times completed in
the correct time, including the smallest, average, and
highest session times and the average value of delay
in the network.
These results showed delays in the network val-
ues influence on the protocol step and whole proto-
col. Even using high delay value time constraints can
remain met. Wrongly chosen time parameters with
fulfilled time conditions may affect the correctness of
the honest users communication.
3.3 Encryption and Decryption
Simulations for NSPK Protocol
During the last stage of the study, we carried out the
next simulations of the protocols executions accord-
ing to assumptions mentioned earlier. We generated
encryption and decryption times according to a uni-
form probability distribution (from 1 to 10 [tu]). Ran-
dom values of encryption and decryption times have
resulted in a different correct interval for each test se-
ries. We observed that constant delays in the network
and random encryption values cause a significant re-
duction in the chance of completing a protocol session
before or after the correct protocol session time.
3.4 Timed Analysis for WLP Protocol
For WLP we assumed that Intruder impersonates only
for honest users, not for the trusted server. Please note
that in the fourth protocol step user B sends a mes-
sage to server encrypting it with his symmetric key.
In the case of impersonating Intruder, this is the user
key whose Intruder impersonates. The honest user
can encrypt the message and continue the protocol.
However, Intruder, who does not have an appropriate
cryptographic key, cannot acquire knowledge about
the cryptogram to continue the protocol.
The research involved an analysis of times influ-
ence on attack possibility. However, due to this proto-
col structure, it turned out that with the current delay
in the network value set to lower limit of delays range,
all real executions ended in correct time or before the
minimal session time. A similar situation occurred in
the case of checking encryption time influence on ex-
ecutions correctness. Regardless of encryption and
decryption times value, all executions ended in the
correct session time.
3.5 Delays Simulations for WLP
Protocol
For WLP simulation we made following assumptions
T
e
= T
d
= 2 [tu], T
g
= 2 [tu], delays range - 1 - 10 [tu].
We randomised current delays in the network values
according to earlier selected probability distributions.
Next, we calculated lifetimes values: T
out
1
=
72 [tu], T
out
2
= 62 [tu], T
out
3
= 42 [tu], T
out
4
= 28 [tu],
T
out
5
= 14 [tu].
We set a minimal session time to 27 [tu] and max-
imal session time to 72 [tu]. We did not analyse exe-
cutions marked as impossible to carry out.We present
simulations experimental results on exponential and
Cauchy’s probability distribution example.
3.5.1 Exponential Probability Distribution
During the simulation of WLP executions using the
exponential probability distribution, we observed that
the all test series ended in the correct session time.
Table 5 summarised session times completed in
the correct time (in [tu]). We showed the smallest, av-
erage, and highest session times (in [tu]) and the av-
erage value of delay in the network. At all test series,
the average value of delay in the network was equal to
ENASE 2021 - 16th International Conference on Evaluation of Novel Approaches to Software Engineering
186
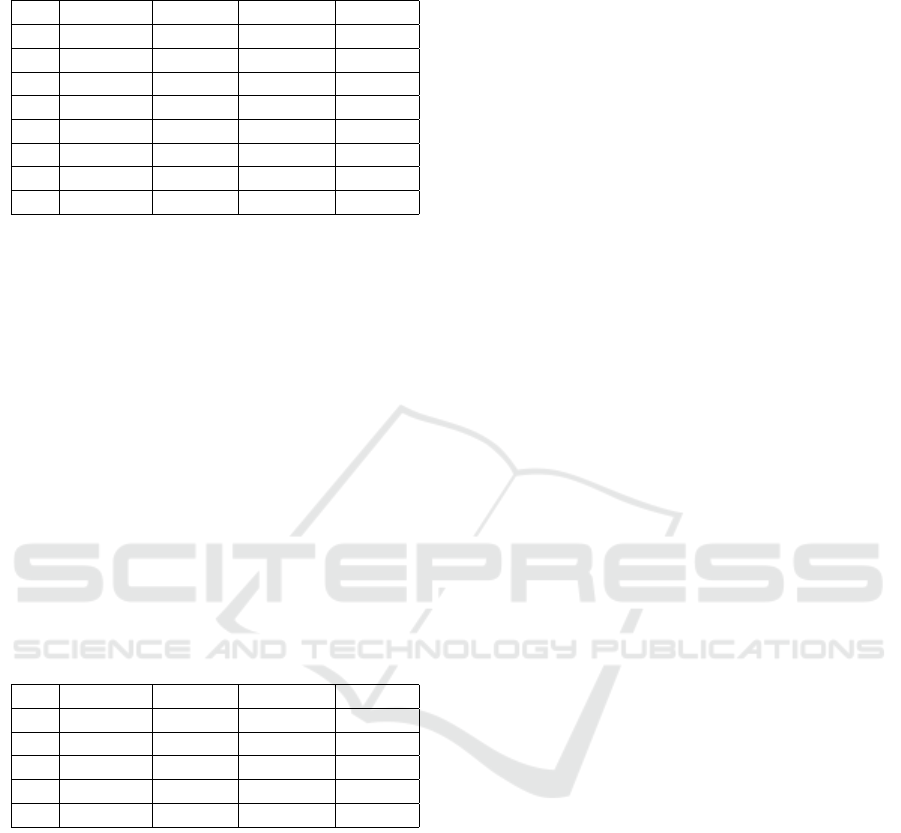
Table 5: Summary of WLP simulations with exponential
distribution which ended in correct interval in [tu].
No Min(T
s
) Avg(T
s
) Max(T
s
) Avg(D)
1 27.07 27.5 28.35 1.1
2 27.09 27.51 28.91 1.1
3 27.04 27.52 28.37 1.1
4 27.06 27.52 28.46 1.1
5 27.09 27.5 28.54 1.1
6 29.15 29.71 30.91 1.1
7 29.21 29.72 30.88 1.1
8 29.12 29.72 30.63 1.1
1.1 [tu]. None of the session times exceeded 31 [tu].
Obtained results showed that using relatively low de-
lay, the Intruder session time may end in the correct
session time. These results showed how often honest
users can be compromised by an Intruder.
3.5.2 Cauchy’s Probability Distribution
The randomisation of out-of-range values, mentioned
earlier, was particularly evident in the case of stud-
ies using Cauchy’s probability distribution. Due to
the nature of this probability distribution, a significant
number of out-of-range values have been observed.
Also, a large number of test series ended with error
have been observed. None of the test series ended
with status !min. We observed that for three execu-
tions almost all test series were ended with an error.
Table 6: Summary of WLP simulations with Cauchy’s prob-
ability distribution which ended in correct interval in [tu].
No Min(T
s
) Avg(T
s
) Max(T
s
) Avg(D)
1 50.35 63.41 71.77 8.32
2 48.87 64.49 71.74 8.56
3 45.75 63.89 71.20 8.46
4 46.59 63.45 71.93 8.34
5 48.75 64.28 71.99 8.54
Table 6 summarised session times completed in
the correct time (in [tu]). We showed the smallest,
average, and highest session times (in [tu]) and the
average value of delay in the network. These results
showed delays in the network values influence on the
protocol step and whole protocol. Even the delay
value is high, time constraints can remain met. Badly
selected time parameters can also affect the correct-
ness of honest users communication, while the time
conditions are met.
3.6 Encryption and Decryption
Simulations for WLP Protocol
During the last stage of WLP studies, simulations of
these protocols executions were carried out. Con-
stant values of delay in the network (2, 4, 6, 8 and 10
[tu]) and random values of encryption and decryption
times were taken into account. For each delay in the
network value, a thousand test series were performed.
Encryption and decryption times were generated ac-
cording to a uniform probability distribution (from 1
to 10 [tu]). Random values of encryption and decryp-
tion times have resulted in a different correct interval
for each test series.
During analysis of encryption and decryption sim-
ulations for this protocol, it can be observed that for
the stage with D = 4 [tu] all test series ended in correct
session time. Also, only four test series ended below
T
min
s
for stage with D = 2 [tu]. For the rest stages,
none of the test series ended below T
min
s
. Except for
stage with D = 10 [tu], for all stages, the number of
!max sessions was bigger than the number of wrong
sessions. This results showed how significant influ-
ence on completing a protocol session before or after
correct session time have encryption and decryption
times.
4 CONCLUSION
Time plays an important role in the private and pro-
fessional life of every person. Its special aspects were
discovered through Internet communication. Infor-
mation transmitted by electronic connections should
reach the recipient promptly. Data should also remain
safe and intact. Internet communication is secured by
special security protocols. Unfortunately, the proto-
cols are exposed to the wicked person called Intruder.
For this reason, it is important to model and verify the
security protocols to avoid unwanted situations.
The paper presented the methodology of testing
timed security protocols including delays in the net-
work. The research was based on a formal model and
computational structure. Thanks to this, it was pos-
sible to calculate the time of proper protocol execu-
tion including different time parameters. The imple-
mented tool enabled automatic verification of timed
security protocols.
The study showed the influence of time parame-
ters on the protocol. Intruder actions depended on the
values of the time parameters. The higher value of the
upper limit of delay in the network may increase In-
truder opportunities to gain knowledge and allow the
Intruder to carry out the attack. A similar situation
Time Influence on Security Protocol
187

occurred with encryption and decryption times. More
time-consuming encryption with constant delays in
the network has made Intruder chances of deceiving
honest users higher.
REFERENCES
Alur, R. and Dill, D. L. (1994). A theory of timed automata.
Theoretical Computer Science, 126:183–235.
Basin, D. A., Cremers, C., and Meadows, C. A. (2018).
Model checking security protocols. In Handbook of
Model Checking., pages 727–762. Springer.
Bella, G. and Paulson, L. C. (1997). Using isabelle to prove
properties of the kerberos authentication system. In
In DIMACS Workshop on Design and Formal Verifi-
cation of Security Protocols.
Burrows, M., Abadi, M., and Needham, R. (1990). A
logic of authentication. ACM Trans. Comput. Syst.,
8(1):18–36.
Chadha, R., Sistla, A. P., and Viswanathan, M. (2017).
Verification of randomized security protocols. In
2017 32nd Annual ACM/IEEE Symposium on Logic
in Computer Science (LICS), pages 1–12.
Corin, R., Etalle, S., Hartel, P. H., and Mader, A. (2004).
Timed model checking of security protocols. In Pro-
ceedings of the 2004 ACM Workshop on Formal Meth-
ods in Security Engineering, FMSE ’04. ACM.
Corin, R., Etalle, S., Hartel, P. H., and Mader, A. (2007).
Timed analysis of security protocols. J. Comput. Se-
cur., 15(6).
Dolev, D. and Yao, A. C. (1981). On the security of public
key protocols. Technical report, Stanford, CA, USA.
ˇ
Cibej Uro
ˇ
s, Luka, F., and Jurij, M. (2019). A symmetry-
breaking node equivalence for pruning the search
space in backtracking algorithms. Symmetry, 11(10).
Jakubowska, G. and Penczek, W. (2007a). Is your security
protocol on time? In Proceedings of the 2007 Interna-
tional Conference on Fundamentals of Software Engi-
neering, FSEN’07, pages 65–80, Berlin, Heidelberg.
Springer-Verlag.
Jakubowska, G. and Penczek, W. (2007b). Modelling and
checking timed authentication of security protocols.
Fundam. Inform., 79(3-4):363–378.
Kurkowski, M. (2013). Formalne metody weryfikacji
własno
´
sci protokoł
´
ow zabezpieczajacych w sieci-
ach komputerowych. Informatyka - Akademicka
Oficyna Wydawnicza EXIT. Akademicka Oficyna
Wydawnicza Exit.
Needham, R. M. and Schroeder, M. D. (1978). Using en-
cryption for authentication in large networks of com-
puters. Commun. ACM, 21(12):993–999.
Nigam, V., Talcott, C. L., and Urquiza, A. A. (2016). To-
wards the automated verification of cyber-physical se-
curity protocols: Bounding the number of timed in-
truders. CoRR, abs/1605.08563.
Perh
´
a
ˇ
c, J., Bilanov
´
a, Z., Steingartner, W., and Piatko, J.
(2019). Benchmark of software developed in differ-
ent component models. In 2019 IEEE 13th Interna-
tional Symposium on Applied Computational Intelli-
gence and Informatics (SACI), pages 245–250.
Siedlecka-Lamch, O., Kurkowski, M., and Piatkowski, J.
(2016). Probabilistic model checking of security pro-
tocols without perfect cryptography assumption. In
Gaj, P., Kwiecie
´
n, A., and Stera, P., editors, Com-
puter Networks, pages 107–117, Cham. Springer In-
ternational Publishing.
Szymoniak, S. (2021). Security protocols analysis in-
cluding various time parameters. Mathematical Bio-
sciences and Engineering, 18(2):1136–1153.
Szymoniak, S., Kurkowski, M., and Piatkowski, J. (2015).
Timed models of security protocols including delays
in the network. Journal of Applied Mathematics and
Computational Mechanics, 14(3):127–139.
Szymoniak, S., Siedlecka-Lamch, O., and Kurkowski, M.
(2017). Timed Analysis of Security Protocols, pages
53–63. Springer International Publishing, Cham.
ENASE 2021 - 16th International Conference on Evaluation of Novel Approaches to Software Engineering
188
