
A Study on Negotiation for Revealed Information with Decentralized
Asymmetric Multi-objective Constraint Optimization
Toshihiro Matsui
Nagoya Institute of Technology, Gokiso-cho Showa-ku Nagoya Aichi 466-8555, Japan
Keywords:
Privacy, Decentralized, Multi-objective, Asymmetric Constraint Optimization, Multiagent, Negotiation.
Abstract:
The control of revealed information from agents is an important issue in cooperative problem solving and
negotiation in multi-agent systems. Research in automated negotiation agents and distributed constraint opti-
mization problems address the privacy of agents. While several studies employ the secure computation that
completely inhibits to access the information in solution process, a part of the information is necessary for
selfish agents to understand the situation of an agreement. In this study, we address a decentralized framework
where agents iteratively negotiate and gradually publish the information of their utilities that are employed
to determine a solution of a constraint optimization problem among the agents. A benefit of the approach
based on constraint optimization problems is its ability of formalization for general problems. We represent
both problems to determine newly published information of utility values and to determine a solution based
on published utility values as decentralized asymmetric multi-objective constraint optimization problems. As
the first study, we investigate the opportunities to design constraints that define simple strategies of agents
to control the utility values to be published. For the objectives of individual agents, we also investigate the
influence of several social welfare functions. We experimentally show the effect and influence of the heuristics
of different criteria to select the published information of agents.
1 INTRODUCTION
The control of revealed information from agents is an
important issue in cooperative problem solving and
negotiation in multi-agent systems. Research in au-
tomated negotiation agents (Kexing, 2011) and dis-
tributed constraint optimization problems (Yeoh and
Yokoo, 2012; Fioretto et al., 2018) address the pri-
vacy of agents. While several studies employ the se-
cure computation that completely inhibits to access
the information in solution process (L
´
eaut
´
e and Falt-
ings, 2013; Grinshpoun and Tassa, 2016; Tassa et al.,
2017; Tassa et al., 2019), a part of the information is
necessary for selfish agents to understand the situation
of an agreement.
A class of asymmetric constraint optimization
problems (Grinshpoun et al., 2013) has been proposed
to represent the situation where agents have different
individual utility functions (Petcu et al., 2008; Mat-
sui et al., 2018a; Matsui et al., 2018b). This prob-
lem can be extended as the basis of a negotiation
framework that publishes/reveals selected partial in-
formation of constraints and solves the problems with
the published information. A benefit of the approach
based on constraint optimization problems is its abil-
ity of formalization for general problems.
In a previous work (Matsui, 2019), a solution
framework consisting of asymmetric constraint opti-
mization problems with the publication of private util-
ity values and a centralized local search method as
a mediator has been presented. With the approach,
agents gradually reveal their information until they
agree on the first globally consistent solution. While
the agents locally select utility values to be published
by referring the information from the mediator, pub-
lished utility values of individual agents are globally
aggregated with the traditional summation operator in
the optimization process based on the published infor-
mation.
However, there are opportunities to design de-
centralized framework without the central node. In
addition, for the problems that consider the utilities
and the cost values of published information for indi-
vidual agents, criteria of multiple objectives should
be employed. For this class of negotiation, there
are opportunities to apply the decentralized constraint
optimization with multiple objectives for individual
agents (Matsui et al., 2018a).
Matsui, T.
A Study on Negotiation for Revealed Information with Decentralized Asymmetric Multi-objective Constraint Optimization.
DOI: 10.5220/0010349601490159
In Proceedings of the 13th International Conference on Agents and Artificial Intelligence (ICAART 2021) - Volume 1, pages 149-159
ISBN: 978-989-758-484-8
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
149
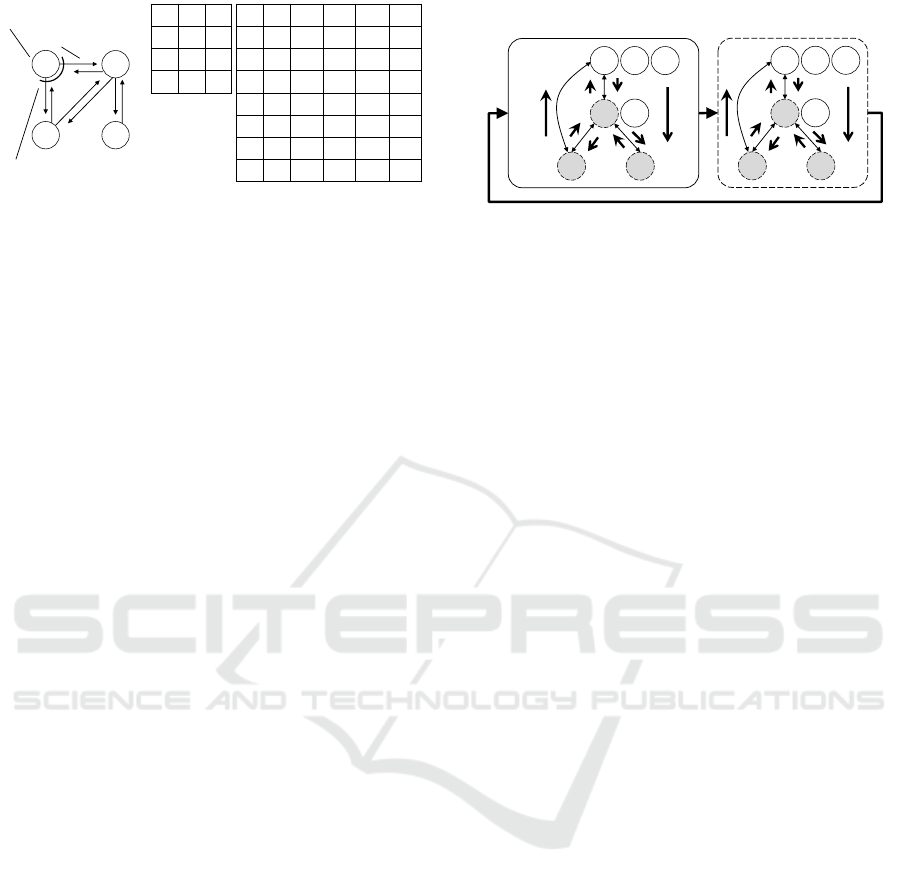
x
i
x
j
u
i,j
u
j,i
p
i,j
p
j,i
d
0
d
0
0 0 0 0
d
0
d
1
0 0 0 0
d
0
d
2
0 0 0 0
...
...
... ... ... ...
d
2
d
0
0 0 0 0
d
2
d
1
u
e
u
g
p
e
p
g
d
2
d
2
u
f
u
h
p
f
p
h
variable of agent a
0
asymmetric constraint
x
0
x
1
x
2
x
3
local valuation of a
0
x
i
u
i
p
i
d
0
0
0
d
1
u
a
p
a
d
2
u
b
p
b
Figure 1: Asymmetric multi-objective DCOP with publica-
tion cost.
For the problem settings similar to the previous study,
we address a decentralized framework where agents
iteratively negotiate and gradually publish the infor-
mation of their utilities that are employed to deter-
mine a solution of a constraint optimization problem
among the agent. In the proposed framework, util-
ity values in constraints for agents are incrementally
published to restrict revealed information, and prob-
lems with only published information are solved until
the agreement or termination condition of the negoti-
ation.
We represent both problems to determine newly
published information of utility values and to deter-
mine a solution based on published utility values as
decentralized asymmetric multi-objective constraint
optimization problems. As the first study, we inves-
tigate the opportunities to design constraints that de-
fine simple strategies of agents to control the utility
values to be published. For the objectives of individ-
ual agents, we also investigate the influence of several
social welfare functions.
Our contribution is the fundamental design of
the negotiation framework that applies a decentral-
ized constraint optimization approach with criteria for
multiple objectives among individual agents, and in-
vestigation of composite constraints of fundamental
strategies to determine newly published utility values.
Our experimental results demonstrate the influence
and effect of criteria to select published information
of constraint.
The rest of the paper is organized as follows. In
the next section, we present preliminaries of our study
including fundamental problem definitions, criteria of
optimization, and basis of solution methods by refer-
ring the previous study. Then we present a framework
with complete decentralized constraint optimization
methods that iterates rounds of negotiation process to
gradually publish utility values considering publica-
tion cost in Section 3. We experimentally investigate
the proposed approach in Section 4. We address dis-
cussions in Section 5 and conclude our study in Sec-
tion 6.
x
1
x
2
x
3
x
0
x
1
x
2
x
3
aggregation of
objectives
solution
x
1
x
2
x
3
x
0
x
1
x
2
x
3
selection of
newly published utility values
optimal solution for
published utility values
negotiation round
s
s
s
s
s
s
s
Figure 2: A negotiation framework.
2 PRELIMINARY
2.1 Asymmetric Constraint
Optimization Problem with
Publication of Private Information
In a previous study, a fundamental solution frame-
work based on an asymmetric constraint optimization
problem with publication of constraints and a cen-
tral processing that performs a local search has been
proposed (Matsui, 2019). Here, we address a similar
problem with a decentralized solution framework.
In an asymmetric constraint optimization problem
with publication of constraints, agents select the pub-
licity of each utility value in the constraints by con-
sidering their privacy cost values. This problem is
defined by hA,X,D,C,P,X
p
,D
p
i. Here, A is a set of
agents, X is a set of variables, D is a set of the do-
mains of variables, and C is a set of constraints that
define the utility values for the assignments to several
variables in X.
Agent a
i
∈ A has variable x
i
∈ X and unary con-
straint u
i
∈ C for the variable. For several pairs of
variables x
i
and x
j
, asymmetric binary constraints
u
i, j
,u
j,i
∈ C are defined. It is assumed that each agent
knows the domains of peer agents related to its asym-
metric binary constraints. Agent a
i
has u
i, j
, and a
j
has u
j,i
. Each agent aggregates its own utility value
for unary and binary constraints that are related to the
agent. The utility values are defined as u
i
: D
i
→ N
0
and u
i, j
: D
i
× D
j
→ N
0
. The functions are also de-
noted by u
i
(d) and u
i, j
(d
i
,d
j
).
P is a set of privacy cost values for utility val-
ues in constraints. p
i
∈ P corresponds to u
i
, and
p
i, j
∈ P corresponds to u
i, j
. The privacy cost values
are individually evaluated by each agent to select its
related utility value to be published. The cost val-
ues of constraints are defined as p
i
: D
i
→ N
0
and
p
i, j
: D
i
× D
j
→ N
0
. The functions are also denoted
by p
i
(d) and p
i, j
(d
i
,d
j
).
ICAART 2021 - 13th International Conference on Agents and Artificial Intelligence
150

An example of directed constraint graph and re-
lated function tables for above basic parts of a prob-
lem is shown in Figure 1.
X
p
and D
p
are a set of binary variables and a set
of the domains of the variables that represent the pub-
lication of the utility values, respectively. When a
utility value in a constraint is published, its corre-
sponding variable takes 1. Otherwise, the variable
takes 0. Variable x
p
i,(d)
∈ X
p
corresponds to utility
value u
i
(d) in unary constraint u
i
. Similarly, variable
x
p
i, j,(d,d
0
)
∈ X
p
corresponds to utility value u
i, j
(d, d
0
)
of assignments d ∈ D
i
and d
0
∈ D
j
in asymmetric bi-
nary constraint u
i, j
. If at least one of x
p
i, j,(d,d
0
)
takes 1,
x
p
i,(d)
is set to 1.
For each variable x
i
∈ X , a value d
0
∈ D
i
repre-
sents a special case where an agent does not coop-
erate with any other agents. Value d
0
is selected by
several agents when any solution cannot be globally
evaluated with utility functions whose utility values
have been partially published. For assignment d
0
to
a variable x
i
, the corresponding utility value u
i
(d
0
)
and privacy cost value p
i
(d
0
) take zero. Similarly,
u
i, j
(d
0
,d), u
i, j
(d, d
0
), and corresponding privacy cost
values take zero. Value d
0
is given as a common
value in the domains of all variables, and correspond-
ing zero utility/privacy-cost values are also defined as
common knowledge. Unpublished utility values re-
lated to assignment d
0
are defined as −∞. The evalua-
tions v
i
(d) and v
i, j
(d, d
0
) for a unary constraint and an
asymmetric binary constraint are represented by the
followings.
v
i
(d) =
u
i
(d) if x
p
i,(d)
= 1
−∞ otherwise
(1)
v
i, j
(d, d
0
) =
u
i, j
(d, d
0
) if x
p
i, j,(d,d
0
)
= 1
−∞ otherwise
(2)
With an assignment to related variables in X
p
, the lo-
cal valuation f
i
(D
i
) for agent a
i
and an assignment
D
i
to related variables in X is defined as the summa-
tion of the evaluations for its own unary constraint
and asymmetric binary constraints for neighborhood
agents in Nbr
i
that are related to i by constraints:
f
i
(D
i
) = v
i
(d
i
) +
∑
j∈Nbr
i
v
i, j
(d
i
,d
j
) , (3)
where d
i
and d
j
are the value of x
i
and x
j
in assign-
ment D
i
.
The goal the of problem is the maximization of the
globally aggregated valuations for all f
i
.
maximize ⊕
a
i
∈A
f
i
(D
i
) (4)
While a typical aggregation operator of the valuations
is the summation of the values, different operators
can be applied in the case of multi-objective problems
among individual utilities of agents as shown in Sec-
tion 2.2.
To avoid the utility value of −∞ shown in Equa-
tions (1) and (2), value d
0
can be assigned to several
agents’ variables if any other solutions cannot be eval-
uated with published part of utility functions. How-
ever, such a situation will also be avoided, since the
utility value corresponds to value d
0
is zero.
The agent can partially publish the utility values
of its own utility functions. The total published cost
of agent a
i
is defined as follows.
∑
d∈D
i
s.t. x
p
i,(d)
=1
p
i
(d) + (5)
∑
j∈Nbr
i
,d∈D
i
,d
0
∈D
j
s.t. x
p
i, j,(d,d
0
)
=1
p
i, j
(d, d
0
)
A problem is to determine the utility values to be
published within a budget. We consider a scheme of
negotiation process where agents iteratively publish
their utility values based on situations in each round
of the process.
2.2 Social Welfare Criteria
When we consider objective of individual agents, sev-
eral operators ⊕ and corresponding criteria to aggre-
gate/compare the objectives as shown in Equation (4).
For multi-objective problems, several types of social
welfare (Sen, 1997) and scalarization methods (Mar-
ler and Arora, 2004) are employed to handle the ob-
jectives. In addition to the traditional summation op-
erator and the comparison on scalar values, we em-
ploy leximin and maximin with a tie-break by a sum-
mation value, that are also employed in a solution
method (Matsui et al., 2018a). Since we employ a
solution method in the previous study to solve our
problem, we also inherit these operators and crite-
ria. While those operators and criteria are designed
for maximization problems of utilities, those can be
easily modified for minimization problems.
Summation
∑
a
i
∈A
f
i
only consider the total util-
ities. While maximin maxmin
a
i
∈A
f
i
improves the
worst case utility value, it does not consider the whole
utilities, and is not Pareto optimal. Therefore, ties
are additionally broken by comparing summation val-
ues. Leximin can be considered as an extension of
maximin where the objective values are represented
as a vector whose values are sorted in ascending or-
der, and the comparison of two vectors is based on a
dictionary order of values in the vectors. The maxi-
mization with leximin is Pareto optimal and relatively
improves fairness among objectives. See the litera-
A Study on Negotiation for Revealed Information with Decentralized Asymmetric Multi-objective Constraint Optimization
151

ture for details (Sen, 1997; Marler and Arora, 2004;
Matsui et al., 2018a).
In addition, to evaluate the fairness among agents
in a resulting solution, we also employ the Theil index
that is defined as an inverted value of entropy. T =
1
N
∑
N
i=1
x
i
x
ln
x
i
x
, where x denotes the average value
for all x
i
. T takes zero if all x
i
are equal.
2.3 Decentralized Dynamic
Programming Method for
Asymmetric Multi-objective
Constraint Optimization Problems
A class of asymmetric constraint optimization prob-
lems with individual objectives of agents and decen-
tralized complete solution methods have been pre-
sented (Matsui et al., 2018a). The goal of this study
was the application of a social welfare criteria called
leximin to pseudo-tree-based solution methods to im-
prove the fairness among individual agents. As men-
tioned above section, with the leximin, individual ob-
jectives of agents are aggregated and optimized con-
sidering the worst case and fairness among the ob-
jectives. In addition to the leximin, several social
welfare criteria including traditional summation were
compared.
The solution methods are extended versions of dy-
namic programming and tree-search based on pseudo-
trees of constraint graphs. A pseudo tree is a struc-
ture on a constraint graph that is employed to decom-
pose problems. A pseudo tree is based on a depth-
first search tree on a constraint graph, and optimiza-
tion methods are performed along the spanning tree
with back edges that are not included in the edges
of the spanning tree. For asymmetric problems, the
pseudo-tree and solution methods have been modified
so that both two agents that relate each other by a pair
of asymmetric constraints can evaluate assignments to
opposite agent’s variable. In part of Figure 2, simple
examples of the modified pseudo trees are illustrated.
See the literature for details (Matsui et al., 2018a).
In this study, we employ a variant of pseudo-tree-
based dynamic programming method DPOP (Petcu
and Faltings, 2005) that has been extended in the pre-
vious study (Matsui et al., 2018a), because it is rel-
atively simple as a basis of our extension. Note that
its scalability is limited for complex problems. When
problems are densely constrained, the tree width of
pseudo trees that corresponds to the number of com-
binations of variables in partial problems for agents
grows and cause a combinational explosion. How-
ever, for the fundamental investigation, we concen-
trate on the problems that can be addressed with this
class of complete solution methods. We develop two
variants of the solution method that are adjusted for
our problem definitions.
3 A DECENTRALIZED
SOLUTION FRAMEWORK
THAT ALTERNATES
SELECTING PUBLISHED
UTILITY VALUES AND
SOLVING PUBLISHED
PROBLEMS
3.1 Basic Framework
We propose a framework that alternates two opti-
mization methods to select utility values to be pub-
lished and to solve the current problem with published
utilities. For both optimization methods, we em-
ploy a decentralized dynamic programming method
based on pseudo trees as mentioned above. For sim-
plicity, two methods employ a common pseudo tree.
For the first investigation, we focus on the process
that incrementally publishes the utility values of con-
straints/functions. We assume that arbitrary condi-
tions and parameters to control and stop the publica-
tion process can be defined.
The framework iterates rounds of negotiation
among agents and utility values are incrementally
published. In each round, the utility values that
are published for the next problem are determined,
and the next problem with published utility values is
solved.
Similar to the previous methods, in the optimiza-
tion for the problem with published utility values, the
total utility for all agents is maximized.
3.2 Selection of Utility Values to be
Published
In the phase of selecting utility values to be published,
agents iteratively publish a part of utility values of
their own constraints in each round of negotiation. As
defined in Section 2.1, the decision variables of agent
a
i
in this problem are originally x
p
i
,x
p
i, j
∈ X
p
for Nbr
i
.
In the initial state, all the variables in X
p
are initial-
ized by 0, and they are set to 1 when their correspond-
ing utility values are published. However, the solution
space for the variables in X
p
is too huge to explore for
the complete solution method that is employed in this
study. Therefore, we define another problem for this
ICAART 2021 - 13th International Conference on Agents and Artificial Intelligence
152

negotiation to restrict solutions in the original solution
space.
The problem is defined by hA,X
s
,D,C
s
i. Here,
we introduce new decision variables X
s
. For agent
a
i
, a decision variable x
s
i
∈ X
s
is defined. Variable x
s
i
takes a value from D
i
∈ D that is the same as a part of
decision variables in the original problem. Assigning
d and d
0
to x
s
i
and x
s
j
represents that the utility values
u
i
(d) and u
i, j
(d, d
0
) are published in the next round of
negotiation. When x
s
i
takes the special variable value
d
0
, it means that no utility values relating x
i
are newly
published. In addition, if a utility value corresponding
to d and d
0
have been published, the published utility
value does not change the current situation. In the
end of each round, several original variables in X
p
are set to 1 by translating the solution for X
s
. If an
assignment to a variable x
p
i
∈ X
p
or x
p
i, j
∈ X
p
changed
from 0 to 1, its corresponding utility value is newly
published.
The structure of this problem determining the util-
ity values to be published for the next problem resem-
bles the maximization problem with published utility
values. The variables and their domains are identical
to the maximization problem for utility values. How-
ever, it is defined as a minimization problem with cost
values for published utility values. The constraints
c
i
∈ C
s
are asymmetrically defined for each agent a
i
.
Here, cost values related to a constraint can take real
number to represent ratio values. Several cost values
for the constraints can be defined based on different
publication strategies, and the cost values can be inte-
grated as vectors with a structure. We investigate fun-
damental strategies as shown in Section 3.3 and 3.4.
3.3 Criteria to Evaluate Newly
Published Utility Values
The following criteria evaluate the situation of newly
published utility values that are represented by an as-
signment to variables in X
s
. We assume that, some
information about status of published utility values is
available in the evaluation. The information can be
collected by simple additional protocols.
3.3.1 R) Degree of Privacy Cost for Published
Utility Values
Ratio of revealed privacy cost: we assume that the in-
formation of publish cost values can be employed in
the negotiation of agents by modifying them to ratio
values of locally aggregated cost values so that the
ratio values only represent a normalized degree of un-
satisfactory. For each agent, the ratio of privacy cost
values between the total values for published utilities
and total values for all constraints is defined as a cri-
terion.
c
R
i
(D
s
i
) =
(x
p+
i,(d
i
)
∗ p
i
(d
i
) +
∑
j∈Nbr
i
x
p+
i, j,(d
i
,d
j
)
∗ p
i, j
(d
i
,d
j
))/
(
∑
d∈D
i
p
i
(d) +
∑
j∈Nbr
j
,d∈D
i
,d
0
∈D
j
p
i, j
(d, d
0
)) , (6)
where, d
i
is the value of x
s
i
in assignment D
s
i
. Values
of variables x
p+
i,(d)
and x
p+
i, j,(d,d
0
)
are equal to x
p
i,(d)
and
x
p
i, j,(d,d
0
)
respectively if x
s
i
and x
s
j
does not represent
the publication of corresponding utility values. Oth-
erwise, x
p+
i,(d)
and x
p+
i, j,(d,d
0
)
are set to 1.
Since agents might relate different numbers of
constraints and utility values, the above ratio value is
also considered.
3.3.2 A) Degree of Unpublished Utility Values
Agreement opportunity: for each value d of each
agent’s variable x
s
i
, the number of unpublished utility
values that are related to the variable’s value is con-
sidered as a criterion. For x
s
i
= d
i
,
c
A
i
(d
i
) =
2|{(d
i
,d
j
)| j ∈ Nbr
i
,d
j
∈ D
j
,d
i
= d
0
∨ d
j
= d
0
}| +
|{x
p
i, j,(d
i
,d
j
)
| j ∈ Nbr
i
,d
j
∈ D
j
,d
i
6= d
0
∧ d
j
6= d
0
,
x
p
i, j,(d
i
,d
j
)
= 0}| (7)
With this criterion, we consider that when the number
of unpublished utilities that relates the assignment for
newly published utility values is relatively large, the
opportunity of agreement among agents with the as-
signment is relatively small. For the assignment of d
0
that represents no publication for a pair of variables’
values, the count of an unpublished utility for the as-
signment is doubled for emphasis.
3.3.3 U) Degree of Progress in Publication
Process
Utility publication progress: since, the cost values for
revealed information restrict the publish of utility val-
ues, a counter part of the cost values is necessary to
continue publication process. Here, we employ a ratio
of published utility values.
c
U
i
(D
s
i
) = |{x
p
i, j,(d
i
,d
j
)
| j ∈ Nbr
i
,x
p
i, j,(d
i
,d
j
)
= 1}/
∑
j∈Nbr
i
|D
i
| × |D
j
| (8)
As addressed below, this cost value is combined with
other criteria so that it has a higher priority than oth-
ers.
A Study on Negotiation for Revealed Information with Decentralized Asymmetric Multi-objective Constraint Optimization
153

3.3.4 T) A Measurement of Trade-off between
Publication Cost and Utility
Trade-off measurement: above criteria do not em-
ploy the information of utility value. To consider the
expected gain of utility by publishing utility values,
the information of utility values should be consid-
ered. However, originally the utility values should be
hidden until their publication. As abstract informa-
tion, we employ the ratio of trade-off values which
are locally aggregated as difference values between
expected utility values and cost values of published
utility values.
Since the optimal utility value is unknown, each
agent employs rough upper and lower bound values
of trade-off.
trd
i
(D
s
i
)
>
= u
i
(d
i
)+
∑
j∈Nbr
i
u
i, j
(d
i
,d
j
)−rvl
i
(D
s
i
) (9)
trd
i
(D
s
i
)
⊥
= u
i
(d
i
) − rvl
i
(D
s
i
) (10)
rvl
i
(D
s
i
) =
x
p+
i,(d
i
)
∗ p
i
(d
i
) +
∑
j∈Nbr
i
x
p+
i, j,(d
i
,d
j
)
∗ p
i, j
(d
i
,d
j
)
(11)
While arbitrary estimation values between the bounds
can be employed, we investigate simple cases for
the fundamental analysis. The estimation trade-off
value trd
i
(D
s
i
) is set to trd
i
(D
s
i
)
⊥
, (trd
i
(D
s
i
)
>
+
trd
i
(D
s
i
)
⊥
)/2 or trd
i
(D
s
i
)
>
. Then the ratio of the
trade-off value is employed as a criterion.
c
T
i
(D
s
i
) = 1−(trd
i
(D
s
i
)−trd
⊥
i
)/(trd
>
i
−trd
⊥
i
) (12)
trd
>
i
= u
i
(d
i
) +
∑
j∈Nbr
i
max
d
i
∈D
i
,d
j
∈D
j
u
i, j
(d
i
,d
j
) (13)
trd
⊥
i
= −(
∑
d∈D
i
p
i
(d) +
∑
j∈Nbr
j
,d∈D
i
,d
0
∈D
j
p
i, j
(d, d
0
))
(14)
3.3.5 S) Degree of Newly Published Utility
Values
Switch of trade-off measurement: the above cost val-
ues except U need the energy to continue publication
process. We modified the previous criteria T to con-
ditionally continue publication process. The modified
cost c
S
i
(D
s
i
) is defined as follows. First, we evaluate
the cost value for newly published utility values
rvl
new
i
(D
s
i
) = (x
p+
i,(d
i
)
− x
p
i,(d
i
)
) ∗ p
i
(d
i
) +
∑
j∈Nbr
i
(x
p+
i, j,(d
i
,d
j
)
− x
p
i, j,(d
i
,d
j
)
) ∗ p
i, j
(d
i
,d
j
)
(15)
If rvl
new
= 0, then c
S
i
(D
s
i
) = 0. Otherwise, if
trd
i
(D
s
i
) > 0,
c
S
i
(D
s
i
) = −(trd
i
(D
s
i
) − trd
⊥
i
)/(trd
>
i
−trd
⊥
i
) . (16)
In other cases, c
S
i
(D
s
i
) = c
T
i
(D
s
i
).
With this criterion, the publication is preferred by
a negative cost value when trd
i
(D
s
i
) > 0.
3.3.6 H) Hard Constraint for Termination
Hard constraint for termination: we also introduce a
cost value c
H
(D
s
i
) of hard constraint for the assign-
ments that should be avoided. The value of c
H
(D
s
i
) is
1 or 0 that represents violation or satisfaction. This
cost value should have the first priority. Here, we
employ c
H
(D
s
i
) for a termination condition based on
above trade-off value. c
H
(D
s
i
) = 1 if rvl
new
i
(D
s
i
) >
0 ∧ trd
i
(D
s
i
) < 0. Otherwise, c
H
(D
s
i
) = 0. This con-
straint inhibits the publication with negative trade-off
value where an estimation utility value is less than the
total publish cost.
3.4 Integrating Criteria for Published
Utility Values
The above criteria can be combined as hierarchically
structured cost vectors, and the optimization method
solves a minimization problem on the vectors to de-
termine the utility values to be newly published. Hard
constraint H is most prioritized. Since criteria R, A,
T with higher priorities will cause earlier convergence
without publication of sufficient utility values, cost U
should be secondary prioritized. S can be used with-
out U. T and S consider a trade-off between an esti-
mation utility and to total publish cost, while R and
A does not evaluate utility values. Considering these
properties, we investigate the following combinations
of criteria.
• S: c
H
c
S
• UAR: c
H
c
U
c
A
c
R
• URA: c
H
c
U
c
R
c
A
• UT: c
H
c
U
c
T
Here, any aggregated cost values do not exceed a cost
value with a higher priority.
For two hierarchically structured cost vectors v
v
v =
[v
1
,··· ,v
k
] and v
v
v
0
= [v
0
1
,··· ,v
0
k
], the aggregation of the
vectors is defined as v
v
v ⊕ v
v
v
0
= [v
1
⊕ v
0
1
,··· ,v
k
⊕ v
0
k
].
The comparison v
v
v < v
v
v
0
is defined as ∃t, ∀t
0
< t,v
t
0
=
v
0
t
0
∧ v
t
< v
0
t
.
We also investigate the cases where the ele-
ments of the vectors are aggregated and compared
with several criteria for multiple objectives for in-
dividual agents. Here, the lexicographic augmented
ICAART 2021 - 13th International Conference on Agents and Artificial Intelligence
154

weighted Tchebycheff function (Marler and Arora,
2004) where ties of maximum values are broken by
summation values, and leximax that is a modified lex-
imin for minimization problems are applied in addi-
tion to traditional summation.
3.5 Solution with Published Utility
Values
In each round of the negotiation to determine newly
published utility value, agents can solve a problem
with currently published utility values as shown in
Section 2.1. While this result can be employed as a
feedback to agents’ strategies, we only evaluate the
anytime property for rounds of negotiation as the first
study.
4 EVALUATION
4.1 Settings
We empirically evaluated the proposed approach.
Due to the limitation of dynamic programming
on a pseudo-tree, we solved relatively small scale
and sparse problems. A problem instance has
n variables/agents/unary-constraints and c pairs of
asymmetric binary constraints. For a pair of vari-
ables/agents, a pair of asymmetric constraints were
defined. The size of variables’ domain including d
0
was commonly set to four. Utility values of con-
straints were set to random integer values in [10,50]
based on uniform distribution. Privacy cost values
were set as follows.
• equ: A privacy cost value for a utility value u is
an integer values bmax(1,u/10)c so that there is a
positive correlation.
• inv: A privacy cost value for a utility value u is an
integer values bmax(1,(50 − u + 1)/10)c so that
there is a negative correlation.
• rnd: Random integer values in [1,5] based on uni-
form distribution.
As shown in Section 3.4, we compared the influ-
ence of several combinations of criteria for selecting
published utility values that are denoted by S, UAR,
URA and UT. In addition, as shown in Section 3.3.4,
the estimated trade-off values for the criterion T, S,
and H is set to the minimum/average/maximum val-
ues of lower and upper bounds that are denoted by
tmin/tave/tmax.
We also applied different aggregation/comparison
operators of objectives, including summation, min-
imum/minimum value with tie-break by summa-
tion, and leximin/leximax, on utility/privacy-cost val-
ues/vectors.
• sum: Summation for both minimization problems
determining published utility values and maxi-
mization problems of utilities under published
utility values.
• ms: The maximum/minimum value with a
tie-break by summation for the minimiza-
tion/maximization problems for publica-
tion/utility.
• lxm: Leximax/leximin for the minimiza-
tion/maximization problems for publica-
tion/utility.
• summs: Summation value for the minimization
problems for publication and the minimum value
for the maximization problem for utility.
• sumlxm: Summation value for the minimization
problems for publication and leximin for the max-
imization problem for utility.
Here, we assumed a simple termination condition
where an accumulated publish cost exceeds estimated
utility for next publication. In this case, each agent
does not select the corresponding assignment. When
all agents do not select new publication, the negotia-
tion process terminates.
For each setting, results are averaged over ten in-
stances.
4.2 Results
Figures 3-6 show typical anytime-curves of ‘utility’
and ‘trade-off’. Each curve corresponds to an agent.
While the utility values almost converge in earlier
rounds, trade-off values decrease until a termination.
Therefore, an issue is the selection of published util-
ity values within a budget, and we investigate the such
opportunities. In these problem settings, the trade-
off values are better in earlier steps for most agents
due to the scale of accumulated publication cost val-
ues are relatively greater than that of utility values.
This situation basically depends on publication cost
parameters of the problem settings, and by simply set-
ting smaller cost values, the peaks will move to later
rounds. Here, we do not focus on this issue because
the parameter design and more sophisticated strate-
gies of agents to handle such peaks will be included
our future work based on this investigation.
Table 1 shows the results in the final round of pub-
lication process in the case of n = 10 variables/agents,
the number of pairs of asymmetric binary constraints
c = 20, equ, and sum. Here, the following results are
A Study on Negotiation for Revealed Information with Decentralized Asymmetric Multi-objective Constraint Optimization
155
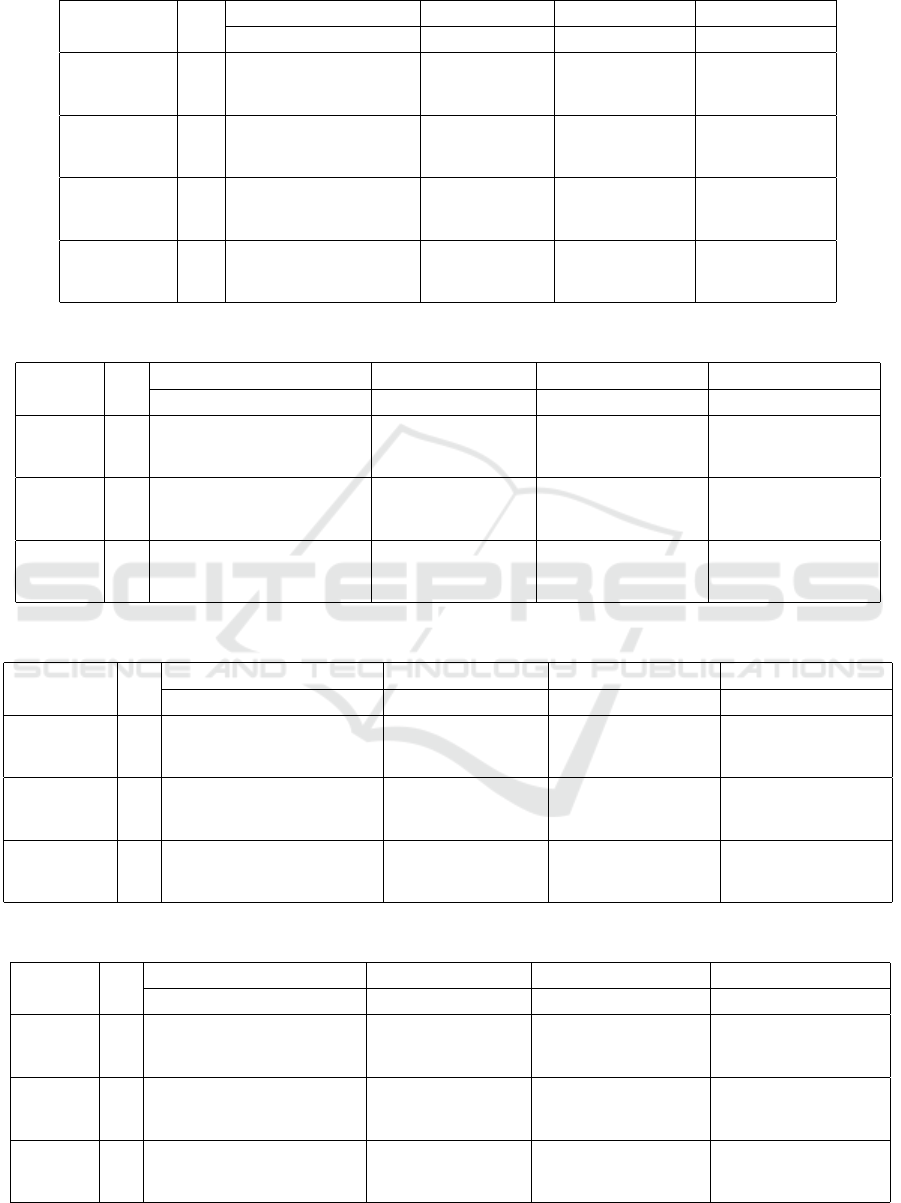
Table 1: Influence of priorities on criteria for utility values to be published (n = 10, c = 20, equ, sum).
alg. term. utiliy trade-off ratio. rvl. num. ratio. rvl. cost
round sum. min. ave. max min. ave. max. min. ave. max. min. ave. max.
sum, S, tmin 6.7 1620.9 97.4 162.1 225.0 76.9 134.1 194.2 0.181 0.291 0.429 0.178 0.292 0.435
sum, S, tave 21.2 1763.2 110.2 176.3 248.8 46.7 88.3 127.9 0.763 0.856 0.934 0.805 0.884 0.961
sum, S, tmax 21.8 1773.1 103.0 177.3 254.3 30.9 77.3 115.4 1 1 1 1 1 1
sum, UAR, tmin 6.1 1560.6 95.6 156.1 223.4 72.8 124.2 187.3 0.245 0.357 0.482 0.211 0.330 0.478
sum, UAR, tave 13.9 1770.1 106.3 177.0 251.9 39.2 84.4 123.0 0.859 0.929 0.985 0.854 0.929 0.988
sum, UAR, tmax 11.9 1773.1 103.0 177.3 254.3 30.9 77.3 115.4 1 1 1 1 1 1
sum, URA, tmin 6.0 1526.6 90.2 152.7 219.0 64.7 121.1 181.9 0.248 0.359 0.488 0.212 0.328 0.472
sum, URA, tave 14.8 1762.1 107.1 176.2 253.1 38.5 83.0 124.3 0.881 0.938 0.991 0.865 0.934 0.987
sum, URA, tmax 13.7 1773.1 103.0 177.3 254.3 30.9 77.3 115.4 1 1 1 1 1 1
sum, UT, tmin 5.5 1598.4 97.6 159.8 225.4 76.2 130.5 190.5 0.193 0.307 0.438 0.191 0.305 0.453
sum, UT, tave 16.3 1764.2 103.2 176.4 251.9 41.3 86.8 129.4 0.754 0.873 0.950 0.800 0.898 0.964
sum, UT, tmax 13.4 1773.1 103.0 177.3 254.3 30.9 77.3 115.4 1 1 1 1 1 1
Table 2: Influence of priorities on criteria for utility values to be published (n = 10, c = 20, equ, S).
alg. term. utiliy trade-off ratio. rvl. num. ratio. rvl. cost
round sum. min. ave. max theil min. ave. max. theil min. ave. max. theil min. ave. max. theil
sum, S, tmin 6.7 1620.9 97.4 162.1 225 0.032 76.9 134.1 194.2 0.039 0.181 0.291 0.429 0.032 0.178 0.292 0.435 0.035
sum, S, tave 21.2 1763.2 110.2 176.3 248.8 0.031 46.7 88.3 127.9 0.041 0.763 0.856 0.934 0.002 0.805 0.884 0.961 0.002
sum, S, tmax 21.8 1773.1 103 177.3 254.3 0.035 30.9 77.3 115.4 0.061 1 1 1 0 1 1 1 0
ms, S, tmin 6.6 1617.9 110.5 161.8 226.9 0.026 86.9 133.3 194.5 0.031 0.185 0.298 0.434 0.034 0.184 0.299 0.457 0.037
ms, S, tave 20.7 1704.4 126.5 170.4 231.3 0.019 56.9 82.2 118.3 0.025 0.755 0.853 0.940 0.002 0.807 0.885 0.955 0.001
ms, S, tmax 19.7 1710.2 126.6 171.0 232.5 0.020 44.9 71.0 102.8 0.033 1 1 1 0 1 1 1 0
lxm, S, tmin 6.5 1600.3 109.2 160.0 218.9 0.025 84.4 131.5 185.8 0.031 0.183 0.295 0.439 0.036 0.181 0.301 0.471 0.040
lxm, S, tave 20 1657.2 125.4 165.7 224 0.020 51.5 78.1 113.1 0.032 0.741 0.849 0.935 0.002 0.784 0.879 0.957 0.002
lxm, S, tmax 19.8 1653.8 126.6 165.4 219.4 0.015 38.6 65.4 90.3 0.033 1 1 1 0 1 1 1 0
Table 3: Influence of priorities on criteria for utility values to be published (n = 10, c = 20, equ, S).
alg. term. utiliy trade-off ratio. rvl. num. ratio. rvl. cost
round sum. min. ave. max theil min. ave. max. theil min. ave. max. theil min. ave. max. theil
sum, S, tmin 6.7 1620.9 97.4 162.1 225 0.032 76.9 134.1 194.2 0.039 0.181 0.291 0.429 0.032 0.178 0.292 0.435 0.035
sum, S, tave 21.2 1763.2 110.2 176.3 248.8 0.031 46.7 88.3 127.9 0.041 0.763 0.856 0.934 0.002 0.805 0.884 0.961 0.002
sum, S, tmax 21.8 1773.1 103 177.3 254.3 0.035 30.9 77.3 115.4 0.061 1 1 1 0 1 1 1 0
summs, S, tmin 6.7 1576.5 99.8 157.7 216.4 0.029 79.1 129.6 184.4 0.036 0.181 0.291 0.429 0.032 0.178 0.292 0.435 0.035
summs, S, tave 21.2 1697.5 126.6 169.8 227 0.019 54.7 81.7 114.3 0.026 0.763 0.856 0.934 0.002 0.805 0.884 0.961 0.002
summs, S, tmax 21.8 1710.2 126.6 171.0 232.5 0.020 44.9 71.0 102.8 0.033 1 1 1 0 1 1 1 0
sumlxm, S, tmin 6.7 1573.4 99.8 157.3 214.6 0.028 79.1 129.3 182.6 0.034 0.181 0.291 0.429 0.032 0.178 0.292 0.435 0.035
sumlxm, S, tave 21.2 1673.8 126.6 167.4 216.8 0.016 53.7 79.3 106.9 0.022 0.763 0.856 0.934 0.002 0.805 0.884 0.961 0.002
sumlxm, S, tmax 21.8 1653.8 126.6 165.4 219.4 0.015 38.6 65.4 90.3 0.033 1 1 1 0 1 1 1 0
Table 4: Influence of priorities on criteria for utility values to be published (n = 10, c = 20, inv, S).
alg. term. utiliy trade-off ratio. rvl. num. ratio. rvl. cost
round sum. min. ave. max theil min. ave. max. theil min. ave. max. theil min. ave. max. theil
sum, S, tmin 8.6 1703.0 107.2 170.3 235.4 0.029 87.1 145.6 205.4 0.034 0.218 0.381 0.540 0.037 0.206 0.356 0.541 0.041
sum, S, tave 22.6 1773.1 103 177.3 254.3 0.035 50.8 105.4 159.6 0.052 0.962 0.990 1 0.0001 0.940 0.986 1 0.0003
sum, S, tmax 21.8 1773.1 103 177.3 254.3 0.035 49.2 104.3 159 0.054 1 1 1 0 1 1 1 0
ms, S, tmin 8.5 1668.5 114.5 166.9 233.2 0.027 94.4 141.7 202.5 0.031 0.217 0.387 0.546 0.036 0.208 0.363 0.548 0.040
ms, S, tave 21.7 1711.7 126.6 171.2 232.5 0.020 69.2 99.2 142.1 0.024 0.963 0.991 1 0.0001 0.942 0.987 1 0.0003
ms, S, tmax 19.6 1710.2 126.6 171.0 232.5 0.020 68.1 98.0 141.3 0.025 1 1 1 0 1 1 1 0
lxm, S, tmin 8.3 1656.8 116.3 165.7 228.7 0.023 96 140.9 199.5 0.027 0.216 0.386 0.556 0.037 0.206 0.357 0.537 0.039
lxm, S, tave 21.4 1653.8 126.6 165.4 219.4 0.015 64 93.4 129.5 0.021 0.965 0.990 1 0.0001 0.945 0.987 1 0.0003
lxm, S, tmax 19.8 1653.8 126.6 165.4 219.4 0.015 63.3 92.4 128.7 0.022 1 1 1 0 1 1 1 0
ICAART 2021 - 13th International Conference on Agents and Artificial Intelligence
156
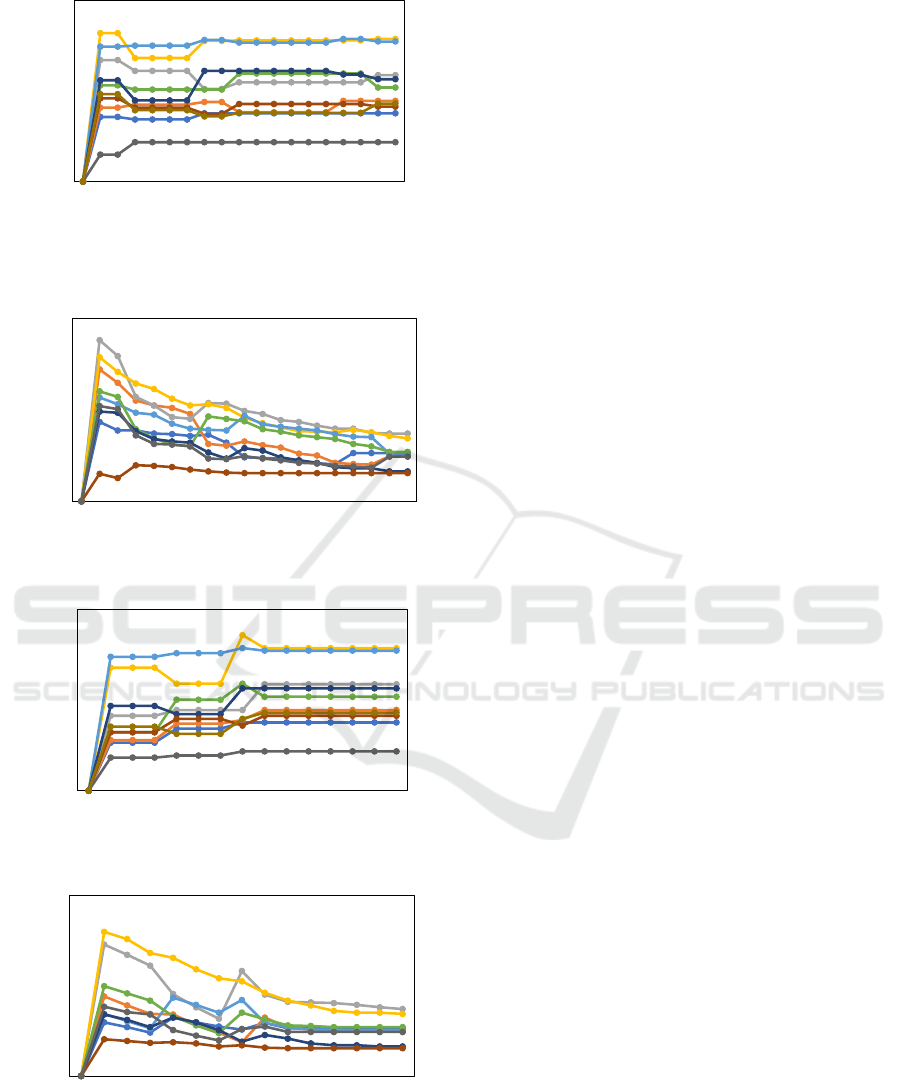
0
50
100
150
200
250
300
350
1 2 3 4 5 6 7 8 9 10111213141516171819
utility
round
(Each curve corresponds to an agent.)
Figure 3: Utility of agents (n = 10, c = 20, equ, S, lxm).
0
50
100
150
200
250
300
1 2 3 4 5 6 7 8 9 1011 1213141516171819
trade
-off (utlity
-cost)
round
Figure 4: Trade-off of agents (n = 10, c = 20, equ, S, lxm).
0
50
100
150
200
250
300
350
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
utility
round
Figure 5: Utility of agents (n = 10, c = 20, equ, URA, lxm)
0
50
100
150
200
250
300
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
trade
-off (utlity
-cost)
round
Figure 6: Trade-off of agents (n = 10, c = 20, equ, URA,
lxm).
evaluated. The minimum/average/maximum value is
evaluated for agents.
• utility: The optimal utility value of the problem
with published utility values.
• trade-off: The actual trade-off values that is the
difference between ’utility’ and the total privacy
cost value for published utility values.
• ratio. rvl. num.: The ratio of revealed number of
utility values.
• ratio. rvl. cost.: The ratio of total privacy cost
values for revealed utility values.
The result shows that the publication process contin-
ued until all the utility values are published when the
case of estimation trade-off tmax, since this estima-
tion value is too optimistic. In this problem setting,
earlier termination of publication process is relatively
better to save the privacy cost obtaining some utility.
‘Trade-off’ values of criteria S and UT that consider
trade-off between the estimation utility and the total
cost of published utility value are relatively greater
than that of other criteria in the case of tmin that ter-
minates in relatively earlier rounds. In the case of
tmin, ‘utiliy’ values of UAR is relatively better than
URA, since it considers the opportunities of aggrega-
tion. Basically, U enforces publication and dominates
other criteria. As a result, the total publication cost is
relatively greater than S.
Table 2 shows the results in the final round of pub-
lication process in the case of n = 10, c = 20, equ,
and S. Here, the Theil index that is a measurement of
in equality among agents is also evaluated. When all
agents have the same value, the Theil index value is
zero. Note that there is an inherent trade-off between
the summation/average value and fairness, while it is
often preferred for selfish agents without other mech-
anisms to trade their profits. The result shows that the
Theil index values of ‘trade-off‘ in ms and lxm are
relatively smaller than that of sum, since those crite-
ria consider the improvement of the worst case. How-
ever, lxm did not overcome ms although lxm consider
the inequality, it reveals that the difficulty to design
appropriate estimate trade-off value to be well opti-
mized. Table 3 shows the results of the same problem
settings, while the optimization criteria for publica-
tion process is sum. Since the publication process is
the same, the result shows that lxm is the fairest crite-
rion for ‘utility’ and it affects ‘trade-off’.
Table 4 shows the results in the final round of pub-
lication process in the case of n = 10, c = 20, inv, and
S. In this case, the Theil index of lxm for ‘trade-off’
was relatively better.
Table 5 shows the results in the case of n = 10, c =
20, rnd, and S. Due to the problem settings, ‘trade-off’
values were negative in a few instances in the case
of tave and tmax. For such cases, the Theil index of
A Study on Negotiation for Revealed Information with Decentralized Asymmetric Multi-objective Constraint Optimization
157
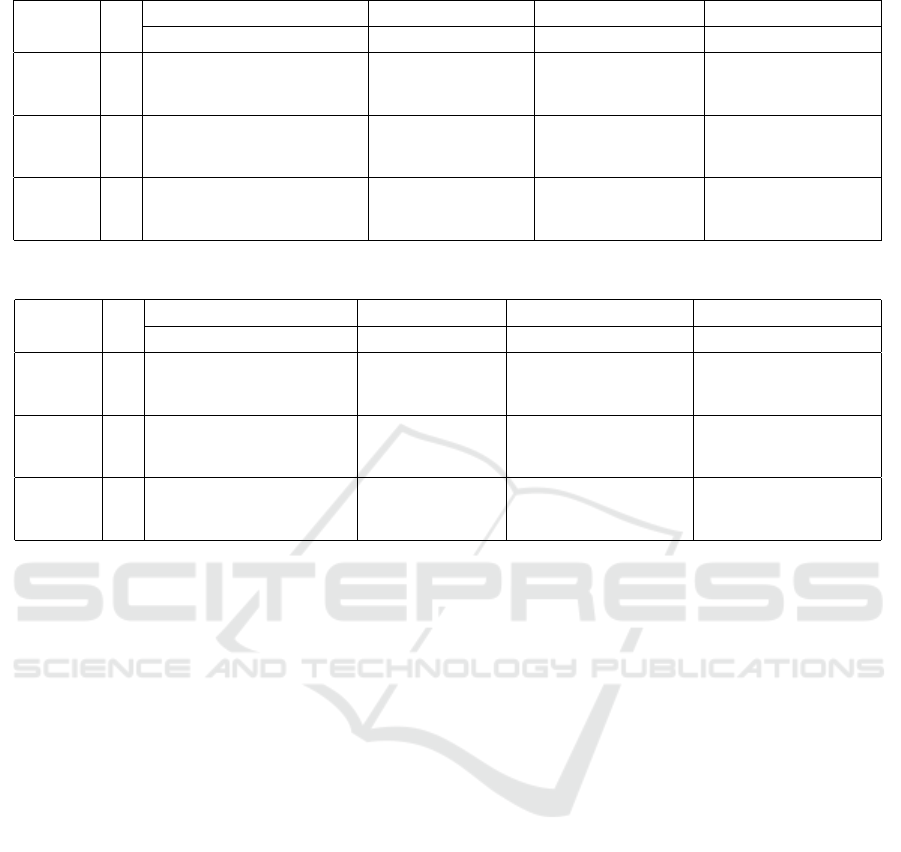
Table 5: Influence of priorities on criteria for utility values to be published (n = 10, c = 20, rnd, S).
alg. term. utiliy trade-off ratio. rvl. num. ratio. rvl. cost
round sum. min. ave. max theil min. ave. max. theil min. ave. max. theil min. ave. max. theil
sum, S, tmin 6.4 1649.5 102.8 165.0 237.5 0.03414 80.4 137.4 207.2 0.043 0.172 0.261 0.379 0.032 0.158 0.249 0.364 0.035
sum, S, tave 18.6 1760.7 105 176.1 250.6 0.03417 46.3 88.1 132 0.052 0.660 0.767 0.862 0.003 0.648 0.758 0.862 0.004
sum, S, tmax 22.1 1770.9 101.8 177.1 260.7 0.037 20.6 61.2 100.5 (0.061) 0.962 0.993 1 0.0001 0.954 0.992 1 0.00022
ms, S, tmin 6.6 1619.2 102.5 161.9 236.5 0.032 75 133.3 203.8 0.042 0.184 0.274 0.410 0.034 0.161 0.259 0.388 0.039
ms, S, tave 18.4 1675.8 117.6 167.6 236.9 0.026 46.3 79.5 119.2 0.040 0.644 0.772 0.872 0.004 0.641 0.760 0.865 0.004
ms, S, tmax 20.4 1673.8 120.5 167.4 229 0.0227 14.4 51.5 84.8 (0.048) 0.952 0.992 1 0.0002 0.944 0.991 1 0.0003
lxm, S, tmin 6.5 1624 101.6 162.4 240.6 0.033 74.3 133.4 207.6 0.045 0.183 0.278 0.419 0.037 0.162 0.262 0.404 0.041
lxm, S, tave 17.7 1644.5 117.6 164.5 232.7 0.0231 44.6 77.2 117 0.040 0.660 0.767 0.859 0.003 0.639 0.752 0.845 0.004
lxm, S, tmax 20.8 1642.1 120.5 164.2 230.8 0.020 11.8 48.2 79.9 (0.043) 0.958 0.993 1 0.0002 0.952 0.992 1 0.00025
Table 6: Influence of priorities on criteria for utility values to be published (n = 20, c = 20, equ, S).
alg. term. utiliy trade-off ratio. rvl. num. ratio. rvl. cost
round sum. min. ave. max theil min. ave. max. theil min. ave. max. theil min. ave. max. theil
sum, S, tmin 7.2 2166.6 54.4 108.3 183.5 0.057 38.3 84.7 150.3 0.066 0.254 0.463 0.683 0.031 0.262 0.472 0.707 0.032
sum, S, tave 15.1 2231.9 57.2 111.60 195.8 0.055 27.8 63.2 104.9 0.053 0.715 0.889 0.992 0.00347 0.771 0.913 0.996 0.0024
sum, S, tmax 17.1 2232.3 57 111.62 198 0.056 24.4 58.3 96.6 0.052 0.940 0.992 1 0.00024 0.965 0.995 1 0.00008
ms, S, tmin 7.2 2150.1 61.8 107.5 182.7 0.049 46 84.1 150.3 0.055 0.251 0.461 0.692 0.034 0.258 0.470 0.710 0.0331
ms, S, tave 15.1 2169.6 69.3 108.5 189.8 0.044 27.4 60.2 96.2 0.044 0.715 0.883 0.995 0.00357 0.771 0.907 0.998 0.00247
ms, S, tmax 16.4 2164.6 69.5 108.2 190.3 0.044 21 55.0 86.6 0.050 0.924 0.990 1 0.000335 0.956 0.994 1 0.000117
lxm, S, tmin 7 2108.9 61.8 105.4 171.4 0.040 46.6 82.2 139.0 0.045 0.254 0.459 0.692 0.033 0.256 0.468 0.710 0.0332
lxm, S, tave 14.2 2098.8 68.9 104.9 173.8 0.033 30.3 57.0 88.5 0.035 0.707 0.873 0.992 0.00354 0.760 0.900 0.997 0.00255
lxm, S, tmax 15.6 2102.9 69.5 105.1 171.8 0.031 24.6 51.9 79.5 0.039 0.925 0.990 1 0.000329 0.957 0.994 1 0.000116
‘trade-off’ is evaluated only for positive values and
denoted by parentheses. In this case, the benefit of
lxm seems to small. These results reveal the influence
of correlation between utility values and their publish-
cost values. Table 6 shows the results in the case of
n = 20, c = 20, equ, and S. The results resemble in
the case of n = 10 and c = 20.
The average execution time of our experimental
implementation on a computer with g++ (GCC) 4.4.7,
Linux version 2.6, Intel (R) Core (TM) i7-3770K
CPU @ 3.50GHz and 32GB memory was 973 sec-
onds in the case of n = 10, c = 20, inv, lxm, S, and
tave.
5 DISCUSSION
In the previous work (Matsui, 2019), similar prob-
lem was solved using a mediator agent that performs
a centralized local search. The goal of the study is
to find the first solution where all agents can agree
with published utility values. Therefore, the solu-
tion process only finds one of combinations of parts
of constraints that involves an assignment to all vari-
ables, and other possible complete solutions are not
explored. In addition, the criteria to aggregate and
evaluate publish cost values and utility values is the
summation.
Our study investigates the negotiation process on sim-
ilar problem with a decentralized complete solution
method employing several criteria that consider pref-
erences of individual agents. We also allow to con-
tinue the search for other solutions with better utility
values, because the complete solution method finds
the first solution after the first round. On the other
hand, due to the limitation of dynamic programming
on a pseudo-tree, we solved relatively small scale and
sparse problems in comparison to the problems in the
previous work.
We assumed that it is accepted to reveal some ab-
stract information to determine utility values to be
published, since the aim of this work is a fundamental
investigation of the proposed approach. There are op-
portunities to employ a secure computation in part of
the negotiation process of publication. In such situa-
tions, the information to be finally published so that
agents can understand the reason of an agreement on
a solution will be an issue.
We employed complete solution methods to solve
problems in each negotiation round so that local
parts of negotiation are based on optimal solutions
as a baseline. However, incomplete solution meth-
ods are necessary for practical and large-scale prob-
lems. There are opportunities to develop such solu-
tion methods for composite criteria considering social
welfare among agents. For initial investigation, we
ICAART 2021 - 13th International Conference on Agents and Artificial Intelligence
158

concentrated on fundamental benchmark problems.
Applying the proposed approach with more scalable
solution methods to practical resource allocation and
collaboration problems will be a goal of future study.
6 CONCLUSION
In this study, we addressed a negotiation framework
based on asymmetric constraint optimization prob-
lems, where agents iteratively publish utility values
of their constraints and solve the problem with pub-
lished utility values. We studied applying a decentral-
ized complete solution method to solve both phases in
each negotiation round. The proposed approach em-
ploys two solution methods based on pseudo-trees to
select utility values to be published and to solve the
problem with the published utility values. As our first
investigation, we evaluated the criterion of the dedi-
cated optimization problems and aggregation opera-
tors, and demonstrated is influence and effect.
Since we employed a complete solution method
based on pseudo-trees, the scalability for complex
problems is limited. A focus of our future work
will be decentralized solution methods for large scale
problems in practical domains. Improvement of the
proposed criterion and termination condition consid-
ering agreement among agents with dedicated pricing
of privacy and utility will also be included our future
work.
ACKNOWLEDGEMENTS
This work was supported in part by JSPS KAKENHI
Grant Number JP19K12117.
REFERENCES
Fioretto, F., Pontelli, E., and Yeoh, W. (2018). Distributed
constraint optimization problems and applications: A
survey. Journal of Artificial Intelligence Research,
61:623–698.
Grinshpoun, T., Grubshtein, A., Zivan, R., Netzer, A., and
Meisels, A. (2013). Asymmetric distributed constraint
optimization problems. Journal of Artificial Intelli-
gence Research, 47:613–647.
Grinshpoun, T. and Tassa, T. (2016). P-syncbb: A privacy
preserving branch and bound dcop algorithm. J. Artif.
Int. Res., 57(1):621–660.
Kexing, L. (2011). A survey of agent based automated ne-
gotiation. In 2011 International Conference on Net-
work Computing and Information Security, volume 2,
pages 24–27.
L
´
eaut
´
e, T. and Faltings, B. (2013). Protecting privacy
through distributed computation in multi-agent deci-
sion making. Journal of Artificial Intelligence Re-
search, 47(1):649–695.
Marler, R. T. and Arora, J. S. (2004). Survey of
multi-objective optimization methods for engineer-
ing. Structural and Multidisciplinary Optimization,
26:369–395.
Matsui, T. (2019). A study of cooperation with privacy loss
based on asymmetric constraint optimization problem
among agents. In 3rd International Conference on Ad-
vances in Artificial Intelligence, pages 127–134.
Matsui, T., Matsuo, H., Silaghi, M., Hirayama, K., and
Yokoo, M. (2018a). Leximin asymmetric multiple
objective distributed constraint optimization problem.
Computational Intelligence, 34(1):49–84.
Matsui, T., Silaghi, M., Okimoto, T., Hirayama, K., Yokoo,
M., and Matsuo, H. (2018b). Leximin multiple objec-
tive dcops on factor graphs for preferences of agents.
Fundam. Inform., 158(1-3):63–91.
Petcu, A. and Faltings, B. (2005). A scalable method
for multiagent constraint optimization. In 19th In-
ternational Joint Conference on Artificial Intelligence,
pages 266–271.
Petcu, A., Faltings, B., and Parkes, D. C. (2008). M-DPOP:
Faithful distributed implementation of efficient social
choice problems. Journal of Artificial Intelligence Re-
search, 32:705–755.
Sen, A. K. (1997). Choice, Welfare and Measurement. Har-
vard University Press.
Tassa, T., Grinshpoun, T., and Yanay, A. (2019). A Pri-
vacy Preserving Collusion Secure DCOP Algorithm.
In 28th International Joint Conference on Artificial In-
telligence, pages 4774–4780.
Tassa, T., Grinshpoun, T., and Zivan, R. (2017). Privacy
preserving implementation of the max-sum algorithm
and its variants. J. Artif. Int. Res., 59(1):311–349.
Yeoh, W. and Yokoo, M. (2012). Distributed problem solv-
ing. AI Magazine, 33(3):53–65.
A Study on Negotiation for Revealed Information with Decentralized Asymmetric Multi-objective Constraint Optimization
159
