
An Overview of Cryptographic Accumulators
Ilker Ozcelik
1,3 a
, Sai Medury
1,2 b
, Justin Broaddus
1,2 c
and Anthony Skjellum
1,2 d
1
SimCenter, University of Tennessee at Chattanooga, Chattanooga, U.S.A.
2
Department of Computer Science and Engineering, University of Tennessee at Chattanooga,
Chattanooga, Tennessee, U.S.A.
3
Department of Computer Engineering, Recep Tayyip Erdogan University, Turkey
Keywords:
Cryptographic Accumulator, Membership Test, RSA, Merkle Tree.
Abstract:
This paper contributes a primer on cryptographic accumulators and how to apply them practically. A cryp-
tographic accumulator is a space- and time-efficient data structure used for set membership tests. Since it is
possible to represent any computational problem where the answer is yes or no as a set-membership problem,
cryptographic accumulators are invaluable data structures in computer science and engineering. But, to the
best of our knowledge, there is neither a concise survey comparing and contrasting various types of accumu-
lators nor a guide for how to apply the most appropriate one for a given application. Therefore, we address
that gap by describing cryptographic accumulators while presenting their fundamental and so-called optional
properties. We discuss the effects of each property on the given accumulator’s performance in terms of space
and time complexity, as well as communication overhead.
1 INTRODUCTION
There are many use cases where one might need to
maintain a list of elements with the purpose of deter-
mining whether an element being presented is part of
this list or not. A common example is a list of cre-
dentials that have been authorized and granted certain
privileges like an Access-Control List (ACL). During
Authentication, an account management system will
check to see whether the credentials entered are a part
of the ACL or not and grant/deny privileges accord-
ingly. If this list were small with only a few hundreds
of elements at any given time, it would not take long
to load the entire list into memory, compare each cre-
dential, and search for a match. The time complexity
of this algorithm scales linearly (O(n)) with the size
(n) of the list; therefore, it will perform poorly if the
list grows to a number in the hundreds of thousands
(and the performance is controlled by I/O speed, not
main memory speed if the list is sufficiently large).
We can reduce this complexity to sublinear (O(log n))
by doing certain pre-computations on the list, such as
by ordering it, then performing a binary search. Sub-
a
https://orcid.org/0000-0002-2032-1640
b
https://orcid.org/0000-0002-2349-8783
c
https://orcid.org/0000-0001-8540-997X
d
https://orcid.org/0000-0001-5252-6600
linear time complexity is an acceptable computational
complexity by Industry standards but there is substan-
tial overhead of sorting the elements that has the av-
erage computational complexity of O(n log n), which
increases the total computational complexity of the al-
gorithm to O(nlogn).
We can further reduce computation complexity
by trading off memory space by constructing auxil-
iary data structures like hashmaps with constant time
lookup complexity. This could be a great alternative
to pre-computation overhead and facilitates constant
time lookup, which is literally the best possible speed
up. However, this approach comes with an overhead
of having to store extra data in memory that will also
scale linearly (O(n)) with the size of the list. De-
pending on the memory size of the processing unit,
a SHA256 hashmap representing a list that contains
10 million elements may not fit in the memory of a
low-energy and resource constrained devices.
A cryptographic accumulator can be used as an al-
ternative to search-based approaches. Cryptographic
accumulators are space-efficient data structures that
rely on cryptographic primitives to achieve sublin-
ear time complexity for set membership operations.
They were first proposed to solve document time-
stamping and membership testing purposes (Benaloh
and De Mare, 1993) Later, they were employed to im-
plement authenticated data structures (Ghosh et al.,
Ozcelik, I., Medury, S., Broaddus, J. and Skjellum, A.
An Overview of Cryptographic Accumulators.
DOI: 10.5220/0010337806610669
In Proceedings of the 7th International Conference on Information Systems Security and Privacy (ICISSP 2021), pages 661-669
ISBN: 978-989-758-491-6
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
661

2014; Goodrich et al., 2002) privacy-preserving (Sla-
manig, 2012) and anonymity-conscious (Camenisch
and Lysyanskaya, 2002; Miers et al., 2013; Sudarsono
et al., 2011) applications. Also, with the advent of
blockchain technology, demand for data to be stored
in a decentralized manner is rising rapidly and crypto-
graphic accumulators are well suited to support quick
constant-time set-membership testing on such data.
Cryptographic accumulators use novel probabilis-
tic data structures for set-membership that minimize
space complexity by compressing the hashmap using
a set of cryptographic functions into a constant size
bit-based data structures like the Bloom filter (Bloom,
1970), or its more recently proposed alternative called
the cuckoo filter (Fan et al., 2014). This compression
is lossy, inevitably giving rise to false positives from
possible collisions.
Alternatively, one can use a cryptographic accu-
mulator, a hash representative generated from the el-
ements in the list, that is of constant size and pro-
vides constant time lookup complexity without po-
tential false positives (Benaloh and De Mare, 1993).
These types of cryptographic accumulators are bet-
ter suited for distributed applications where a trusted
authority is responsible for continuously maintaining
the accumulator (hash representative); the trusted au-
thority keeps the accumulator up to date with addi-
tions and deletions of elements from the list. Partici-
pants other than this authority could be clients them-
selves that are part of the list or else be verifiers that
are trying to determine whether an element being pre-
sented is part of the list. Such cryptographic accumu-
lators, also called asymmetric cryptographic accumu-
lators (Kumar et al., 2014), additionally require the
generation of witnesses (Kumar et al., 2014) for each
element.
The witness is the value corresponding to an el-
ement that is required to verify an element’s mem-
bership in the accumulator (Kumar et al., 2014); it is
unique to each element and needs to be updated each
time an element is added or deleted to the accumula-
tor. This witness can also be communicated to the
client for storage and later presentation on-demand
to a verifier. The trusted authority, often known as
the Accumulator Manager (AM) (Akkaya and Cebe,
2018), needs to perform O(n) operations to update the
witnesses of n elements for each new addition (resp,
deletion) of an element to (resp, from) the list; this
is the tradeoff for having virtually constant size com-
putation complexity and communication overhead be-
tween the verifier, client, and AM for determining set-
membership. Most studies thus far regarding crypto-
graphic accumulators have been theoretical and focus
on their underlying theories. By carefully combing
through these studies and presenting a guide with a
gentler learning curve, this paper provides an accessi-
ble discussion for those who are interested in learning,
developing, and utilizing cryptographic accumulators
in their applications.
The remainder of this paper is organized as fol-
lows: Section 2 introduces the set membership prob-
lem and cryptographic accumulators. Different archi-
tectures of cryptographic accumulators and their clas-
sification are also presented in this section. Effects
of these optional features on accumulator operations
are discussed in Section 3, in terms of memory usage,
computational- and communicational-complexity. Fi-
nally, Section 4 concludes with a discussion of current
and potential applications.
2 CRYPTO-ACCUMULATORS
In computer science and engineering, set membership
tests (yes/no) tests) are used in many applications in-
cluding database, authentication, and validation sys-
tems.
Testing set membership can be performed by run-
ning a search on the set but this method can be a
resource intensive task as the set size increases. To
address these limitations, researchers proposed cryp-
tographic accumulators (Fan et al., 2014; Baldimtsi
et al., 2017; Tremel, 2013; Reyzin and Yakoubov,
2016). The fundamental idea behind the accumula-
tor is being able to accumulate values of a set A into
a small value z in such a way that it is possible to
prove only the elements of set A have been accumu-
lated (Fazio and Nicolosi, 2002).
2.1 Classification
Cryptograph accumulators can be categorized as sym-
metric or asymmetric. Symmetric Accumulators (Ku-
mar et al., 2014) are designed using symmetric cryp-
tographic primitives and can verify membership of el-
ements without the need of a corresponding witness.
The Bloom filter (Bloom, 1970)—a type of array data
structure—is a symmetric cryptographic accumulator
that uses k-number of hash functions that set a unique
combination of indices in the array based on the in-
put element; it provides a limited representation of
set-membership with a false positive rate that grows
as the number of elements in the list approaches the
max capacity of the list (Bloom, 1970). Equation 1
provides the estimate of the false positive rate of a
simple Bloom filter construction:
FPR = (1 − [1 −
1
m
]
kn
)
k
≈ (1 − e
−kn
m
)
k
(1)
ICISSP 2021 - 7th International Conference on Information Systems Security and Privacy
662

with m being the size of the array, k being the num-
ber of hash functions, and n being the number of ac-
cumulated elements. Variations of the Bloom filter
(Fan et al., 2014) have sought to minimize this false
positive rate but are unable to eliminate it entirely.
Because Bloom filters are static accumulators, they
cannot accommodate growing list sizes, so they must
be regenerated after reaching full capacity during the
transaction discovery process
The recently proposed cuckoo filter is a dynamic
data structure that functions similarly to the simple
Bloom filter but with additional capabilities such as
the ability to delete elements. A cuckoo filter im-
plements a cuckoo hash table (Fan et al., 2014) to
save fingerprint representations of the elements in
an accumulated set. A cuckoo hash table is an ar-
ray of buckets in which each stored element is as-
sociated with two indices in the array. Two associ-
ated indices allow for the dynamic rearrangement of
the elements stored in the cuckoo hash table, provid-
ing optimized space efficiency and low false-positive
rates. For a given number of elements, a cuckoo filter
outperforms a space-optimized Bloom filter in terms
of false-positive rate and space overhead (Fan et al.,
2014).
Asymmetric Accumulators (Kumar et al., 2014)
require witness creation and update for dynamic ver-
ification of set membership (Baldimtsi et al., 2017).
They are built on asymmetric cryptographic primi-
tives (Baldimtsi et al., 2017) and require the underly-
ing hash algorithm to exhibit the quasi-commutative
property (Benaloh and De Mare, 1993). The RSA ac-
cumulator (Benaloh and De Mare, 1993) is one exam-
ple of asymmetric accumulator that uses RSA modu-
lar exponentiation to achieve the quasi-commutative
property. A simple RSA accumulator construction
consists of the following expression for addition:
acc
n
= acc
x
n−1
mod N where acc
n
is the new accu-
mulator value after addition, acc
n−1
is the old accu-
mulator value before addition, x is the element be-
ing added, and N = pq where p and q are considered
to be strong prime numbers whose Sophie Germain
prime numbers p
0
=
p−1
2
and q
0
=
q−1
2
are the accu-
mulator trapdoor. One drawback of an RSA accumu-
lator is that it is collision-free only when accumulat-
ing prime numbers. A prime representative generator
is required to accumulate composite numbers without
collision . The implementation of an RSA accumu-
lator by (Tremel, 2013) a random oracle prime repre-
sentative generator provided by (Bari
´
c and Pfitzmann,
1997) was used. Asymmetric accumulators can be
further classified based on operations supported and
the type of membership proofs provided. This classi-
fication will be further explained and analyzed in the
following sections.
A Merkle hash tree can also be implemented as an
asymmetric accumulator to prove Set Membership of
elements (Baldimtsi et al., 2017). It is classified as
an asymmetric accumulator because a member of its
set requires a witness to prove membership (or non-
membership). But, it does not use asymmetric cryp-
tographic primitives nor does it need the underlying
hash function to exhibit quasi-commutative property.
The root node of the Merkle Tree is called the Merkle
root and its value is the pairwise accumulated hash
of all of the non-root nodes in the tree. The Merkle
root value must be recalculated when there is an ad-
dition/deletion of a member in the set. Checking for
set membership can be done with a portion of the tree
(Merkle, 1989), making it unnecessary to download
the full data structure.
2.2 Architectures
There are two well known cryptographic accumula-
tor architectures: the one-way and the collision-free
accumulator.
2.2.1 One-way Accumulator
(Benaloh and De Mare, 1993) proposed the first-
ever accumulator construction, known as the One-way
Accumulator, characterized as a family of one-way
hash functions with the additional quasi-commutative
property. A one-way hash function H is a function
that can accept an arbitrarily large message M and re-
turns a constant size output that is also called a mes-
sage digest MD. For H to be a one-way hash, it must
satisfy the following properties (Weisstein, a; Weis-
stein, b):
• The description of function H should be public
and should work without needing to know secret
information.
• For a message M, it must be easy to calculate its
message digest, MD = H(M).
• Given an MD, it must be difficult to determine M
for a range where H is valid.
• For any M, the probability of finding an M
0
6= M
such that H
0
(M) = H(M) is negligible.
The quasi-commutative property is a generalization
of the commutative property. A function h defined as
h : X ?Y ⇒ X holds the quasi-commutative (Benaloh
and De Mare, 1993) if ∀x ∈ X and ∀y
1
,y
2
∈ Y ,
h(h(x,y
1
),y
2
) = h(h(x, y
2
),y
1
). (2)
Despite using a strong one-way hash function (Fazio
and Nicolosi, 2002), Benaloh and de Mare’s accumu-
lator can be compromised if an attacker can choose a
An Overview of Cryptographic Accumulators
663

subset of the values being accumulated (Fazio and Ni-
colosi, 2002). (Bari
´
c and Pfitzmann, 1997) proposed
“Collision-free accumulators” to address this issue.
2.2.2 Collision-free Accumulator
The One-Way accumulators are elementary and ideal
for Set Membership, whereas collision-free accumu-
lators are more general (Bari
´
c and Pfitzmann, 1997),
and are better suited for designing Fail-Stop signature
schemes and Group Signatures. Collision-free accu-
mulators consist of an accumulator scheme that is de-
fined together by 4 polynomial-time algorithms: Gen,
Eval, Wit and Ver.
The key generation algorithm Gen is used to gen-
erate the necessary key for a desired size accumulator,
which accepts a security parameter 1
λ
and accumula-
tor threshold value N. The threshold value defines the
maximum number of elements that can be accumu-
lated securely. Gen returns a key k from key space
K
λN
. The evaluation algorithm Eval is used to accu-
mulate elements of set A = y
1
,· ·· ,y
N
0
where N
0
≤ N.
It accepts the accumulator key k and values to be ac-
cumulated, y
1
,· ·· ,y
N
0
, as input. Eval returns the ac-
cumulated value z and an auxiliary information, aux
that will be used by other algorithms. It is important
to note that the Eval algorithm must return the same
z value for the same input, but it may generate dif-
ferent auxiliary information. The witness extraction
algorithm Wit generates the witness for a given in-
put. It accepts the accumulator key k, the input value
y
i
∈ Y
k
and the previous auxiliary and accumulator
value z generated by Eval. Wit returns a witness value
w
i
∈ W
k
to show input y
i
was accumulated. Otherwise
it returns the symbol ⊥. The verification algorithm
Ver is used to test the existence of an element in an
accumulator; it accepts the accumulator key k, accu-
mulator z, input value y
i
, and its corresponding wit-
ness w
i
. Ver returns the value TRUE or FALSE.
The accumulator scheme is paired with the prop-
erty of collision freeness. Collision freeness ensures
that an adversary bounded by polynomial-time cannot
generate a set of values Y = y
1
,y
2
,· ·· ,y
N
that pro-
duces an accumulator value z that allows for a value
y /∈ Y and a witness w that allows for y to be proven
as a member accumulated in z.
(Bari
´
c and Pfitzmann, 1997) propose two theoret-
ical constructions of collision-free accumulators for
building Fail-Stop Signature schemes. There also ex-
ists a dynamic accumulator implementation by (Ca-
menisch and Lysyanskaya, 2002) that was inspired by
the Collision-Free accumulator architecture but meant
for set-membership testing.
2.3 Properties
Cryptographic accumulator properties are discussed
next.
2.3.1 Security Properties
There are four prominent security properties of asym-
metric cryptographic accumulators: soundness, com-
pleteness, undeniability and indistinguishability.
Soundness (aka Collision-Freeness) is defined as
the probability of computing a membership witness
for an element that is not part of the accumulated
set or non-membership witness for an element part
of the accumulated set is negligible (Derler et al.,
2015). Completeness, (aka Correctness), property re-
quires that all honestly accumulated values be verified
as true with their respective witnesses with a negligi-
ble probability of error (Derler et al., 2015). An accu-
mulator is called undeniable if the probability of com-
puting a membership and non-membership witnesses
together, of the same input, is negligible. Undeni-
ability implies the collision-freenes property but not
all collision-free accumulators have the undeniability
property (Derler et al., 2015). Indistinguishability is
both a security- and privacy-related property. An ac-
cumulator is indistinguishable if no information about
the accumulated set is leaked by either the accumula-
tor or its witnesses. This can be achieved by either
accumulating a random value from the accumulation
domain or using a non-deterministic Eval Algorithm
(Derler et al., 2015).
2.3.2 Optional Crypto-Accumulator Features
Constructions can be optimized by selecting a subset
of available features. Each available feature comes
with a cost that can significantly impact the system
design and implementation. Notable features are dis-
cussed next.
The set of accumulated elements is not always
static; new elements may be added to or removed
from this set over time. This is a common case for
applications requiring to grant / revoke the privilege
of a credential If an accumulator only supports addi-
tions, it is termed additive. Similarly, an accumula-
tor that only supports deletions is termed subtractive.
Addition and subtraction can be performed by redo-
ing the accumulation process after updating the set.
But, this approach is generally not practical, since re-
calculation takes polynomial time and depends on the
size of the accumulated set (Baldimtsi et al., 2017).
Dynamic accumulators are those that can efficiently
(in sublinear or constant time complexity) update the
accumulator and the respective witness values when a
ICISSP 2021 - 7th International Conference on Information Systems Security and Privacy
664

new element is added to (resp, removed from) the ac-
cumulated set (Au et al., 2009). Accumulators that do
not support additions or deletions are termed static.
Accumulators are alo termed positive, negative, or
universal based on the type of membership proof(s)
they can support (Baldimtsi et al., 2017). Positive
accumulators only support set membership proof of
inclusion. Thus, for all elements in the accumu-
lated set, there exists an efficiently computable wit-
ness w. Negative accumulators can only support a
non-membership proof. For all elements that are con-
sidered non-members in regards to the accumulated
set, there exists an efficiently computable witness w
0
.
Lastly, a universal accumulator supports both mem-
bership and non-membership proofs (Li et al., 2007).
Zero Knowledge Proof (ZKP) is a privacy preserv-
ing membership proof used by cryptographic accu-
mulators. It was initially proposed by (Goldwasser
et al., 1989) in 1989. With ZKP, it is possible to show
the accuracy of a statement about a secret without
revealing the secret itself. This is possible because,
if one can compute the same output that the prover
provides by only accessing the input of the verifier;
it should also be possible to compute the output be-
fore such interaction occurs. Therefore, through ZKP
systems, an honest verifier need not interact with the
prover (Morais et al., 2018) to verify the accuracy of
a statement.
A single accumulator data structure alone won’t
be enough to implement ZKPs but two or more cryp-
tographic accumulator schemes can be used to imple-
ment ZKP system. Even with a combination of ac-
cumulators, the interaction mechanisms must be aug-
mented to carry out ZKPs. Additionally, these inter-
actions must be standardized to make all parties aware
of these mechanisms.
The zero knowledge property has been proven to
imply indistinguishability for cryptographic accumu-
lators (Ghosh et al., 2016). But, maintaining the in-
tegrity, zero knowledge property, and the efficiency of
the accumulator simultaneously is challenging. This
complexity can be reduced by restricting the accumu-
lator’s design to a trusted setup (Ghosh et al., 2016),
where the accumulator value is always maintained
by a trusted party. But, a trusted user is required to
generate a secret value called a trapdoor to compute
the accumulator and witness values efficiently. This
setup raises major security and centralization con-
cerns. But, there is no practical trapdoorless (strong)
accumulator that can produce constant-size proofs.
In trapdoorless accumulators, since the accumulator
manager is also considered untrusted, the witness size
grows at least like logN where N is the number of ac-
cumulated elements (Ghosh et al., 2016).
Applications can be either local, where only a sin-
gle entity / authority is responsible for proving mem-
bership, or distributed where multiple parties in a net-
work interact with each other. In the distributed case,
the communication channel between all relevant par-
ties becomes a bottleneck because membership wit-
ness additions or updates must be broadcasted each
time an element is added to or deleted from the accu-
mulator. To minimize this communication overhead,
asynchronous accumulators were proposed for dis-
tributed applications (Reyzin and Yakoubov, 2016).
The asynchronous accumulator relies on low up-
date frequency and compatibility with old accumula-
tor version (Reyzin and Yakoubov, 2016). An accu-
mulator has a low update frequency property, if the
witness of an element requires less number of updates
than the number of elements added after the element
(Reyzin and Yakoubov, 2016). Low update frequency
can be achieved only if it is additionally possible to
accurately verify membership using an outdated accu-
mulator value, in other words, the accumulator must
be backwards compatible. It is important to note that
the element tested for membership proof must be ac-
cumulated before the outdated accumulator value was
generated (Reyzin and Yakoubov, 2016).
3 COST-BENEFIT ANALYSIS
Security properties of cryptographic accumulators de-
fine the reliability of the accumulator design. It is
expected for an accumulator to satisfy these proper-
ties. However, some of the features presented in Sec-
tion 2.3.2 are design choices rather than a necessity.
We encountered four major design choices in litera-
ture and each choice affects the implementation com-
plexity and overall accumulator performance. In this
section we will present and discuss effects of these de-
sign choices in terms of space complexity, time com-
plexity, and communication overhead.
In an application, the input set that needs to be
accumulated can be static, additive, subtractive or dy-
namic. A static set is a set whose list of elements do
not change through time. In an additive and subtrac-
tive sets, elements can only be added to or deleted
from the set respectively. A dynamic set refers to the
ability to both add and delete elements from the set. In
our discussion, static accumulators will be our base-
line and the system’s initial space, time complexities
and communication overhead will not be considered.
The effects of dynamic input set over system
space, time complexity and communication overhead
is presented in Table 1. This table is compiled consid-
ering major asymmetric cryptographic accumulators
An Overview of Cryptographic Accumulators
665
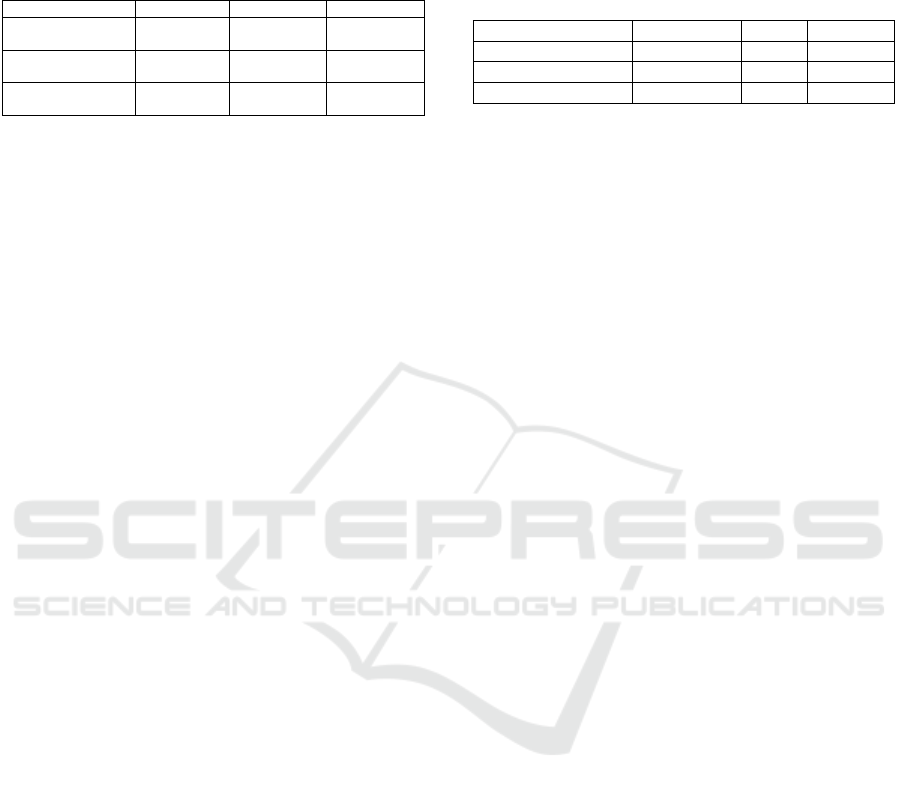
Table 1: The space-, time-complexity and communication
overhead in accumulators with input set changes. Indepen-
dent cases separated using vertical line (|) and mutually ex-
clusive cases separated using slash symbol (/).
Additive Subtractive Dynamic
Space Complexity
(Size
Acc
| Size
Wit
| Size
AM
)
O(1) | O(1) | O(1) O(1) | O(1) | O(N) O(1) | O(1) | O(N)
Time Complexity at AM
(Wit
Member
| Wit
Non−member
)
O(1) | O(N) O(N) | O(N) O(1) | O(N) | O(N)
Communication Overhead
At AM
O(1) O(N) O(1)|O(N)
with the exception of the tree based strong accumu-
lator, Merkle Tree. More information about Merkle
Tree based accumulators can be found in the discus-
sion about the accumulator manager (AM) trust.
When we evaluate space complexity based on
a dynamic input set, we will investigate accumula-
tor, witness and accumulator manager storage size
changes (see Table 1). Size of an asymmetric accumu-
lator can be specified using an accumulator threshold
value N during accumulator generation. This value
defines the upper bound on the total number of val-
ues that can be accumulated securely in the accumu-
lator (Fazio and Nicolosi, 2002). Adding and remov-
ing elements to/from these accumulators do not affect
the accumulator and witness size. On the other hand,
RSA and Bilinear Map based accumulators require a
trapdoor upon the initialization of the accumulators
themselves as well as during the deletion of a member
in the accumulated set. In otherwise trapdoorless con-
structions, accumulators’ manager storage can grow
proportional to the set size.
For every element added to the set, the accu-
mulator manager must update the accumulator value
and create a membership witness. The accumulator
manager must also update the accumulator value af-
ter each deletion of an element and provide a non-
membership witness if supported by the accumulator
construction. Accumulator update upon element ad-
dition and subtraction and generating a membership
witness for a new element are constant time processes
done by the accumulator manager. On the other hand,
generating a non-membership witness for RSA and
Bilinear Map accumulators requires more time pro-
portional to the number of elements in the set.
Asymmetric accumulators provide a constant ver-
ification and witness update time in case of an addi-
tion and subtraction of an element. However, the wit-
ness update process may cause a bottleneck in RSA
and Bilinear Map accumulators during element sub-
traction since the witnesses have to be updated by the
accumulator manager itself. However, there are pro-
posed constructions in the literature that allow for the
accumulated members to update their own witnesses
after deletion by using Bezout coefficients (Baldimtsi
et al., 2017; Li et al., 2007).
Table 2: The space-, time-complexity and communication
overhead experienced by accumulator managers (AM) with
different membership proof types. Symbols a, d, and S
(a − d) denote the number of elements added, deleted, and
present respectively. ‘∼’ represents the range.
AM Complexity/Work Positive Negative Universal
Space Complexity O(1) ∼ O(d) O(S) O(S) ∼ O(a)
Time Complexity O(1) O(1) O(1) ∼ O(S)
Communication Overhead
O(d) ∼ O(a + d) O(a + d) O(a + d)
In synchronous accumulators, the AMs must
broadcast information about new elements to witness
holders. This communication overhead is minimized
in asynchronous accumulators, since witness hold-
ers need not update accumulator/witness value as fre-
quently. But, RSA and bilinear-map accumulators
experience additional communication complexity af-
ter element subtraction because of the queries from
witness holders needed to retrieve updated witnesses
from the accumulator manager.
Cryptographic accumulators can be positive, neg-
ative, or universal based on the membership proof
they provide. Positive Accumulators provide only
membership proofs to determine whether an element
has been accumulated to the set of members. Negative
accumulators, on the other hand, provide only non-
membership proofs to determine whether an element
has been accumulated to the set of non-members.
Universal accumulators can provide both member-
ship and non-membership proofs. Table 2 describes
the time complexity, space complexity, and commu-
nication overhead of an accumulator based on the
(non-)membership proof. They show the minimum
and maximum values observed across all membership
proof types. To identify generalized operations found
across a class of accumulators with similar applica-
tions, we limited the scope by selecting dynamic ac-
cumulators that require a trusted setup with an accu-
mulator manager (AM) and synchronized communi-
cation. Also, the values for the Merkle Tree accu-
mulator were omitted from Table 2; they will be dis-
cussed in the evaluation of Table 3.
The values in Table 2 convey the range of per-
formance, including bottlenecks, one may achieve by
utilizing positive, negative, or universal accumula-
tors. The Universal Accumulator has the highest com-
plexity in all three dimensions when compared with
(Strictly) Positive or (Strictly) Negative accumulators.
However, the time complexity in Universal Accumu-
lators may be reduced by implementing a separate ac-
cumulator of positive and negative types.
The space complexity for applying positive cryp-
tographic accumulators is of the order of O(1)
for positive accumulators with the exception of
BraavosB’s (Baldimtsi et al., 2017) construction, due
ICISSP 2021 - 7th International Conference on Information Systems Security and Privacy
666
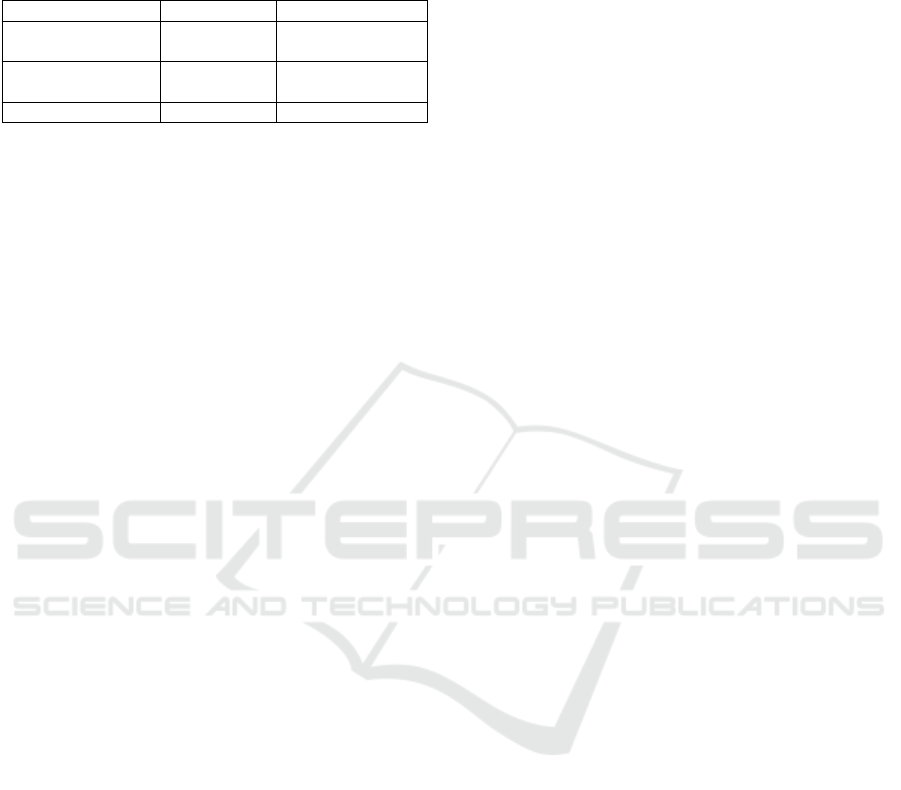
Table 3: The space-, time-complexity and communication
overhead in accumulators with Trusted AM and Untrusted
AM. Symbols a, d, and S (a − d) denote the number of
elements added, deleted, and present respectively.
Trusted AM Untrusted (Strong) AM
Space Complexity
(Size
Acc
|Size
Wit
|Size
AM
)
O(1) | O(1) | O(S) O(1) | O(loga) | O(a)
Time Complexity
(For all operations)
O(1) O(loga)
Communication Overhead O(a+d) O((a + d)loga)
to its reliance on the Range-RSA construction for ac-
cumulating deleted elements. For negative and uni-
versal accumulators, space complexity is generally
O(S), which is the number of elements that are part
of the accumulator at any given moment (not includ-
ing elements that were deleted).
The computation time complexities mentioned in
Table 2 show that all operations are typically of O(1)
except the NonMemWitCreate operation, which is the
most expensive operation if using Universal accumu-
lators built upon RSA and Bilinear Mapping crypto-
graphic algorithms.
The communication overhead is O(a + d) for dy-
namic accumulators, regardless of whether they are
positive or negative or universal, due to communica-
tion being required for Member Witness updates after
both additions and deletions of elements. For positive
accumulators like CL-RSA-B, Braavos or BraavosB
that are custom designed to minimize communica-
tion, the communication overhead is O(d) because
they don’t require communication after addition of el-
ements but only after deletion of elements.
Based on system requirements, a cryptographic
accumulator can be designed either on the foundation
of a trusted or untrusted accumulator manager. The
RSA and bilinear map implementations are restricted
to only trusted accumulator manager setups as a result
of their reliance on a secret trapdoor value for initial-
ization and constant time operations. The only known
family of accumulators that can be safely used in an
untrusted system are those based on Merkle Trees.
This is because Merkle Trees do not require trapdoor
values at any point during their operations.
Trusted accumulator manager systems use accu-
mulators that do not provide the strong accumulator
property. Accumulators based on RSA and bilinear
maps fall into these types of accumulators. As shown
in Table 3, trusted systems are relatively more scal-
able with O(1) time and space complexities. And,
similar to systems without trusted AM, the commu-
nication overhead grows linearly with the number of
member additions and deletions. However, systems
with trusted accumulator managers (AM) are central-
ized. The AM is required to maintain the integrity of
the accumulator by safeguarding the trapdoor value.
In case the trusted AM gets compromised, then the
entire system may be brought down. Acquisition of
the trapdoor value would allow an adversary to pro-
duce membership witnesses that are compatible with
the accumulator value even for non-accumulated ele-
ments, threatening the soundness of the accumulator.
This centralized infrastructure also limits the system’s
ability to distribute computational load, placing more
responsibility on the trusted accumulator manager.
Untrusted accumulator manager (AM) systems
use strong (trapdoorless) accumulators like Merkle
Trees. Their operations require O(loga) time com-
plexity; they produce witnesses of size O(log a), and
their communication overhead is of superlinear time
complexity of O((a + d) log a). Systems with un-
trusted AMs require relatively more space and can
be expensive to maintain. The size of a Merkle Tree
scales like O(a) and does not reduce in size after dele-
tions. Thus, the Merkle Tree will continue to grow
regardless of the number of deletions.
Advanced security is the main advantage of un-
trusted accumulator manager systems. The use of a
trapdoor is not required in a strong accumulator, and
the responsibility of maintaining the integrity of the
accumulated set is distributed amongst all participat-
ing untrusted accumulator managers. Further, he ab-
sence of a trapdoor allows for distribution of the com-
putational load among the untrusted managers and ac-
cumulated members.
An asynchronous accumulator must hold both the
low-update-frequency property and backwards com-
patibility property. To the best of our knowledge, the
only construction that provides a fully asynchronous
accumulator was defined by (Reyzin and Yakoubov,
2016). Another asymmetric accumulator that exhibits
the low-update-frequency property but not the old ac-
cumulator compatibility property is the CL-RSA-B
accumulator, presented by (Camenisch and Lysyan-
skaya, 2002). We refer to accumulators that only hold
the low-update-frequency property as partially asyn-
chronous. These accumulators are notably only pos-
itive accumulators. But, we are not claiming that the
construction of a negative or universal asynchronous
accumulator is infeasible; this remains an open ques-
tion.
The asynchronous accumulator defined by
(Reyzin and Yakoubov, 2016) takes the form of a
dynamic set of Merkle Trees. The number of Merkle
Trees grows by a factor of D = log
2
(n + 1). Each
subsequent Merkle Tree holds varying numbers of
members and the entire construction follows a com-
binatorial approach when additions are made (Reyzin
and Yakoubov, 2016). The benefit of using this
An Overview of Cryptographic Accumulators
667

Table 4: The space-, time-complexity and communication overhead in accumulators with varying frequency in updates.
Symbols a, d, and S (a − d) denote the number of elements added, deleted, and present respectively. ‘∼’ represents the range
Partially
Asynchronous
(Trusted)
Asynchronous
(Untrusted)
Synchronous (Trusted & Untrusted)
Space Complexity
(Size
Acc
|Size
Wit
|Size
AM
)
O(1) | O(1) | O(1) O(log a) | O(loga) | O(a) O(1) | O(1) ∼ O(loga) | O(S) ∼ O(a)
Time Complexity
(For all operations)
O(1) O(loga) O(1) ∼ log a
Communication Overhead O(d) O(loga + log d) O(a + d) ∼ O((a + d) log a)
accumulator is the reduced communication overhead
by a factor of O(loga + logb), as shown in Table 4.
The asynchronous accumulator can also be applied in
decentralized, untrusted systems because of its strong
accumulator construction. The disadvantages are the
dynamic sizes of the accumulator value and witnesses
by a factor of O(loga). The accumulator manager
(AM) also requires storage of O(a). Verification
takes O(log a) as well. To support deletion, a list of
all member values must also be stored and maintained
(Reyzin and Yakoubov, 2016).
The partially asynchronous variant in the form of
the CL-RSA-B accumulator has the advantage of con-
stant time operations and constant size accumulator
and witness values. It also only has to update wit-
nesses after a member is deleted from the set; witness
updates are not required after additions. For an ac-
cumulator scheme that is not expecting a significant
number of deletions compared to additions, this fea-
ture is ideal because the communication overhead is
only d as shown in Table 4. The main drawback of a
partially asynchronous accumulator is its inability to
exhibit the old accumulator compatibility property, so
the most up-to-date accumulator value must be held.
Another disadvantage is its restriction to trusted ac-
cumulator schemes in which the trusted accumula-
tor manager is the only entity that can generate wit-
nesses upon the addition of new members and up-
date the accumulator value when a member is deleted.
This is due to the requirement of a trapdoor to per-
form deletions in a CL-RSA-B accumulator. Once
a member is deleted, the new accumulator value as
well as the deleted member’s ID is broadcasted to the
other members to update their respective witness val-
ues (Baldimtsi et al., 2017).
In comparison with synchronous accumulators,
overall system’s communication cost is reduced in
both asynchronous and partially asynchronous accu-
mulators. Synchronous accumulators never have a
communication overhead less than O(a + b). This is
because all witnesses must be updated after an mem-
ber addition or deletion in the set and witnesses are
incompatible with old accumulator values. The deci-
sion of which asynchronous accumulator type to pick
comes down to whether the system requires a trusted
or untrusted setup. Dynamic or static sizes of witness
and accumulator values should be taken into consid-
eration too.
4 CONCLUSION
We provided a concise guide on cryptographic accu-
mulators. We presented their security and optional
properties. Also, we discussed the effects of differ-
ent optional properties on accumulator performance
in terms of space, time, and communication complex-
ity.
Cryptocurrencies were early adopters of crypto-
graphic accumulators. Bitcoin uses a Bloom Filter for
set-membership testing of transactions (Bitcoin.org,
2020a) . Bitcoin also uses Merkle Block (Bitcoin.org,
2020b) to confirm the validity of transactions without
having to download and/or maintain the entire copy
of blockchain by every participating node. In Ze-
rocoin (Miers et al., 2013), a CL-RSA-B based ac-
cumulator is implemented to represent a set of all
transactions that have been committed to blockchain
(Miers et al., 2013). The accumulator additionally
eliminates trackable linkage of addresses and facili-
tates anonymous and untraceable public transactions
(Miers et al., 2013).
Other applications of crypto accumulators in-
clude, but are not limited to, maintaining a certifi-
cate revocation list, blacklisting or whitelisting user
credentials in an authentication system and generat-
ing important client groups such as lists of high risk
and/or bankrupt clients
Cryptographic accumulators can also help main-
tain dataset privacy while sharing. They can be im-
plemented to share and maintain a list of such users
without actually revealing their identities. This prop-
erty could simplify sharing critical data sharing with
third parties. Cryptographic accumulators can also be
used in offline ID verification, credit score checking,
and medical-data verification.
ICISSP 2021 - 7th International Conference on Information Systems Security and Privacy
668

ACKNOWLEDGMENTS
This material is based upon work supported by, or
in part by,the National Science Foundation (NSF)
under grants CCF-1562659, CCF-1562306, CCF-
1617690, CCF-1822191, CCF-1821431, and The Sci-
entific and Technological Research Council of Turkey
(TUBITAK). The views and conclusions contained
herein are those of the authors and should not be in-
terpreted as representing the official policies, views,
or endorsements, either expressed or implied, of the
NSF or TUBITAK.
REFERENCES
Akkaya, K. and Cebe, M. (2018). Efficient public-key revo-
cation management for secure smart meter communi-
cations using one-way cryptographic accumulators. In
IEEE International Conference on Communications.
Florida International University.
Au, M. H., Tsang, P. P., Susilo, W., and Mu, Y. (2009). Dy-
namic universal accumulators for ddh groups and their
application to attribute-based anonymous credential
systems. In Cryptographers’ track at the RSA con-
ference, pages 295–308. Springer.
Baldimtsi, F., Camenisch, J., Dubovitskaya, M., Lysyan-
skaya, A., Reyzin, L., Samelin, K., and Yak-
oubov, S. (2017). Accumulators with applications
to anonymity-preserving revocation. In 2017 IEEE
European Symp. on Security & Privacy (EuroS&P),
pages 301–315. IEEE.
Bari
´
c, N. and Pfitzmann, B. (1997). Collision-free accumu-
lators and fail-stop signature schemes without trees.
In International Conference on the Theory and Appli-
cations of Cryptographic Techniques, pages 480–494.
Springer.
Benaloh, J. and De Mare, M. (1993). One-way accumula-
tors: A decentralized alternative to digital signatures.
In Workshop on the Theory and Application of of
Cryptographic Techniques, pages 274–285. Springer.
Bitcoin.org (2020a). Application of Bloom filters.
https://bitcoin.org/en/operating-modes-guide#
application-of-bloom-filters. [ Online; Ac-
cessed:March/2020 ].
Bitcoin.org (2020b). Merkleblock. https://bitcoin.org/
en/developer-reference#merkleblock. [ Online; Ac-
cessed:March/2020 ].
Bloom, B. H. (1970). Space/time trade-offs in hash coding
with allowable errors. Comm. of the ACM, 13(7):422–
426.
Camenisch, J. and Lysyanskaya, A. (2002). Dynamic
accumulators and application to efficient revocation
of anonymous credentials. In Annual International
Cryptology Conference, pages 61–76. Springer.
Derler, D., Hanser, C., and Slamanig, D. (2015). Revisit-
ing cryptographic accumulators, additional properties
and relations to other primitives. In Cryptographers’
track—RSA conf., pages 127–144. Springer.
Fan, B., Andersen, D. G., Kaminsky, M., and Mitzen-
macher, M. D. (2014). Cuckoo filter: Practically better
than bloom. In Proceedings of the 10th ACM Interna-
tional on Conference on emerging Networking Exper-
iments and Technologies, pages 75–88.
Fazio, N. and Nicolosi, A. (2002). Cryptographic ac-
cumulators: Definitions, constructions and applica-
tions. Paper written for course at New York Univer-
sity: www. cs. nyu. edu/nicolosi/papers/accumulators.
pdf.
Ghosh, E., Ohrimenko, O., Papadopoulos, D., Tamassia, R.,
and Triandopoulos, N. (2016). Zero-knowledge accu-
mulators and set algebra. In International Conference
on the Theory and Application of Cryptology and In-
formation Security, pages 67–100. Springer.
Ghosh, E., Ohrimenko, O., and Tamassia, R. (2014). Ver-
ifiable member and order queries on a list in zero-
knowledge. arXiv preprint arXiv:1408.3843.
Goldwasser, S., Micali, S., and Rackoff, C. (1989). The
knowledge complexity of interactive proof systems.
SIAM Journal on computing, 18(1):186–208.
Goodrich, M. T., Tamassia, R., and Hasi
´
c, J. (2002). An
efficient dynamic and distributed cryptographic accu-
mulator. In Int. Conf. on Info. Security, pages 372–
388. Springer.
Kumar, A., Lafourcade, P., and Lauradoux, C. (2014). Per-
formances of cryptographic accumulators. In 39th An-
nual IEEE Conference on Local Computer Networks,
pages 366–369. IEEE.
Li, J., Li, N., and Xue, R. (2007). Universal accumula-
tors with efficient nonmembership proofs. In Interna-
tional Conference on Applied Cryptography and Net-
work Security, pages 253–269. Springer.
Merkle, R. C. (1989). A certified digital signature. In Conf.
on the Theory and Application of Cryptology, pages
218–238. Springer.
Miers, I., Garman, C., Green, M., and Rubin, A. D. (2013).
Zerocoin: Anonymous distributed e-cash from bit-
coin. In 2013 IEEE Symposium on Security and Pri-
vacy, pages 397–411. IEEE.
Morais, E., van Wijk, C., and Koens, T. (2018). Zero knowl-
edge set membership.
Reyzin, L. and Yakoubov, S. (2016). Efficient asynchronous
accumulators for distributed pki. In International
Conference on Security and Cryptography for Net-
works, pages 292–309. Springer.
Slamanig, D. (2012). Dynamic accumulator based discre-
tionary access control for outsourced storage with un-
linkable access. In Int. Conf. on Financial Crypto. &
Data Security, pages 215–222. Springer.
Sudarsono, A., Nakanishi, T., and Funabiki, N. (2011). Effi-
cient proofs of attributes in pairing-based anonymous
credential system. In International Symposium on Pri-
vacy Enhancing Technologies Symposium, pages 246–
263. Springer.
Tremel, E. (2013). Real-world performance of crypto-
graphic accumulators. Thesis, Brown U.
Weisstein, E. W. One-way function. from Mathworld - a
Wolfram web resource. https://mathworld.wolfram.
com/One-WayFunction.html. [ Online; Accessed:
March/2020 ].
Weisstein, E. W. One-way hash function. from math-
world - a wolfram web resource. https://mathworld.
wolfram.com/One-WayHashFunction.html. [ Online;
Accessed: March/2020 ].
An Overview of Cryptographic Accumulators
669
