
Efficient Semantic Representation of Network Access Control
Configuration for Ontology-based Security Analysis
Florian Patzer
a
and J
¨
urgen Beyerer
b
Fraunhofer IOSB, Institute of Optronics, System Technologies and Image Exploitation,
Fraunhoferstr. 1, 76131 Karlsruhe, Germany
Keywords:
Network Access Control, Security Analysis, Ontology-based Security Analysis, Security Ontology.
Abstract:
Assessing countermeasures and the sufficiency of security-relevant configurations within networked system
architectures is a very complex task. Even the configuration of single network access control (NAC) instances
can be too complex to analyse manually. Therefore, model-based approaches have manifested themselves as
a solution for computer-aided configuration analysis. Unfortunately, current approaches suffer from various
issues like coping with configuration-language heterogeneity or the analysis of multiple NAC instances as one
overall system configuration, which is the case for the maturity of analysis goals. In this paper, we show how
deriving and modelling NAC configurations’ effects solves the majority of these issues by allowing generic
and simplified security analysis and model extension. The paper further presents the underlying modelling
strategy to create such configuration effect representations (hereafter referred to as effective configuration) and
explains how analyses based on previous approaches can still be performed. Moreover, the linking between
rule representations and effective configuration is demonstrated, which enables the tracing of issues, found in
the effective configuration, back to specific rules.
1 INTRODUCTION
IT and OT Systems consist of various networks and
components, often with thousands of network ac-
cess control (NAC) configurations. This makes them
too complex to manually assess their configuration,
for example to validate security policy and counter-
measure deployment. Model-based computer-aided
analysis addresses this issue by modelling security-
relevant information in a machine-interpretable man-
ner and using algorithms to find issues. The last two
decades, ontologies, which can be defined as explicit
specification of a conceptualization (Gruber, 1993),
have proven themselves to provide adequate models
for this matter (cf. Section 3). Most noticeable, the
Web Ontology Language (OWL
1
) has been success-
fully applied for various such tasks. OWL and the
Semantic Web Rule Language (SWRL
2
) have been ap-
plied widely to model security-relevant knowledge
a
https://orcid.org/0000-0001-6620-9753
b
https://orcid.org/0000-0003-3556-7181
1
https://www.w3.org/TR/owl2-overview/, last accessed:
15.12.2020
2
https://www.w3.org/Submission/SWRL/, last ac-
cessed: 15.12.2020
about a system. These models can then be ex-
tended by various existing reasoners (e.g. Pellet
3
)
or rule engines (e.g. Drools
4
), and can further be
queried by semantic query languages like SPARQL
5
or SQWRL (Semantic Query-Enhanced Web Rule
Language) (O’Connor and Das, 2009).
Ontology-based security analysis, is usually ap-
plied on manually created ontological representations
of abstract information about systems. Only view
research focusses detailed configurations in order to
identify issues with impact to the security of the re-
spective system. With the increasing availability of
machine-interpretable information about the systems
under investigation, provided by configuration man-
agement databases, software-defined networking, en-
gineering tool exports, asset management interfaces,
etc., detailed configuration gets more accessible as
time goes by. Therefore, security analysis on detailed
configuration is becoming increasingly feasible and
relevant.
3
https://github.com/stardog-union/pellet, last accessed:
15.12.2020
4
https://www.drools.org/, last accessed: 15.12.2020
5
https://www.w3.org/TR/sparql11-overview/, last ac-
cessed: 15.12.2020
550
Patzer, F. and Beyerer, J.
Efficient Semantic Representation of Network Access Control Configuration for Ontology-based Security Analysis.
DOI: 10.5220/0010285305500557
In Proceedings of the 7th International Conference on Information Systems Security and Privacy (ICISSP 2021), pages 550-557
ISBN: 978-989-758-491-6
Copyright
c
2021 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

The already mentioned network access control is
of particular importance for security analysis. This
type of countermeasure, which includes host- and
network-based firewalls and proxies, is particularly
prone to configuration errors, like missing, obsolete,
conflicting or shadowed policies. At the same time
NAC is critical for the security of a system. Thus, a
significant part of ontology-based configuration secu-
rity analysis focusses on NAC and its configuration is-
sues (Khelf and Ghoualmi-Zine, 2018). Nevertheless,
only few research has concentrated on analysing the
compliance of NAC configurations to security poli-
cies. Moreover, existing approaches addressing this
kind of challenge either suffer from crucial scalabil-
ity issues or from non-applicability for more sophisti-
cated NAC configurations (cf. Section 3).
This paper suggests to model the effects of NAC
configurations (called effective configuration), to al-
low compliance-related queries or reasoning in a
configuration-language-independent manner. The ap-
proach exploits the fact that compliance and inter-
NAC configuration analysis is focussed on the traf-
fic a NAC-instance is configured to permit or deny.
Therefore, it follows the strategy to model patterns
for the allowed or prohibited traffic, resp. the classes
of data/information flows a NAC instance allow or
block. It is important to note that effective config-
uration is not targeting analysis on rule level and
thus cannot contribute to that type of analysis. For
example, the policy ‘‘Every rule needs to define a
source and destination port range” has to be anal-
ysed at rule level and not on the modelled effec-
tive configuration. However, this paper shows that,
compared to currently available approaches, provid-
ing such a model of effective configuration signifi-
cantly improves the scalability and efficiency of se-
curity analysis and model extension (cf. Section 4).
The next sections are structured as follows: Sec-
tion 2 describes an example system architecture to
support the understanding of later sections. Subse-
quently, Section 3 describes and compares related ap-
proaches and their issues. Afterwards, the effective
configuration approach is presented in Section 4 and
used to solve an example analysis question. Finally,
the presented approach is further discussed in Section
5, before the paper is summarized in Section 6
2 WORKING EXAMPLE
This section describes a small but realistic system ar-
chitecture to support the understanding of the next
sections. Figure 1 shows the example system archi-
tecture consisting of three different internal subnets
and one subnet mimicking the internet. Following the
IEC 62443
6
security standards the networks and their
connected assets are distributed into different security
zones, namely Internet, DMZ, Office and Field.
Listing 1 shows a rule chain excerpt of the pf-
Sense
7
firewall Pfsense 1. In the pfSense configu-
ration language, inet signals the IPv4 context of a
rule. The rule processing in pfSense is rather com-
plex. However, for didactic reasons, the processing
strategy can be simplified as follows:
1. All rules without a quick instruction follow the
“last match wins” strategy.
2. Rules with a quick instruction follow the “first
match wins” strategy.
Listing 1: Reduced rules of the firewall Pfsense 1.
1 b lo c k i n i n e t a l l l a b e l
2 b l o c k o u t i n e t a l l l a b e l
3 b l o c k i n on ! em0 i n e t f ro m
1 7 2 . 1 6 . 1 1 0 . 0 / 2 4 t o any
4 b l o c k i n i n e t from 1 7 2 . 1 6 . 1 1 0 . 1 1 8
t o any
5 b l o c k i n on ! em1 i n e t f ro m
1 7 2 . 1 6 . 1 2 1 . 0 / 2 4 t o any
6 b l o c k i n i n e t from 1 7 2 . 1 6 . 1 2 1 . 1 t o
any
7 b l o c k i n on ! em2 i n e t f ro m
1 7 2 . 1 6 . 1 2 2 . 0 / 2 4 t o any
8 b l o c k i n i n e t from 1 7 2 . 1 6 . 1 2 2 . 1 t o
any
9 p a s s i n q u i c k on em0 i n e t p r o t o
t c p from 1 7 2 . 1 6 . 1 1 0 . 0 / 2 4 t o
1 7 2 . 1 6 . 1 2 2 . 0 / 2 4 p o r t = h t t p
10 p a s s i n q u i c k on em1 i n e t p r o t o
udp from 1 7 2 . 1 6 . 1 2 1 . 0 / 2 4 t o
1 7 2 . 1 6 . 1 2 2 . 1 0 3 p o r t = domain
11 p a s s i n q u i c k on em2 i n e t p r o t o
udp from 1 7 2 . 1 6 . 1 2 2 . 1 0 3 t o any
The rules state the following:
• Rules 1 and 2 are the IPv4 default blocking rules.
• Rules 3, 5 and 7 block incoming packages on each
Ethernet interface which is not internally config-
ured for the IPv4 source networks of the packages.
• Rules 4, 6 and 8 are again default blocking rules
but for the firewall interface’s IPv4 addresses.
• Rule 9 allows HTTP traffic to pass into the DMZ.
• Rule 10 allows DNS traffic from the Office zone
to the DNS server.
• Rule 11 allows any UDP traffic from the DNS
server to pass through.
6
isa99.isa.org/ISA99\%20Wiki/Home.aspx, last ac-
cessed: 15.12.2020
7
https://www.pfsense.org/, last accessed: 15.12.2020
Efficient Semantic Representation of Network Access Control Configuration for Ontology-based Security Analysis
551
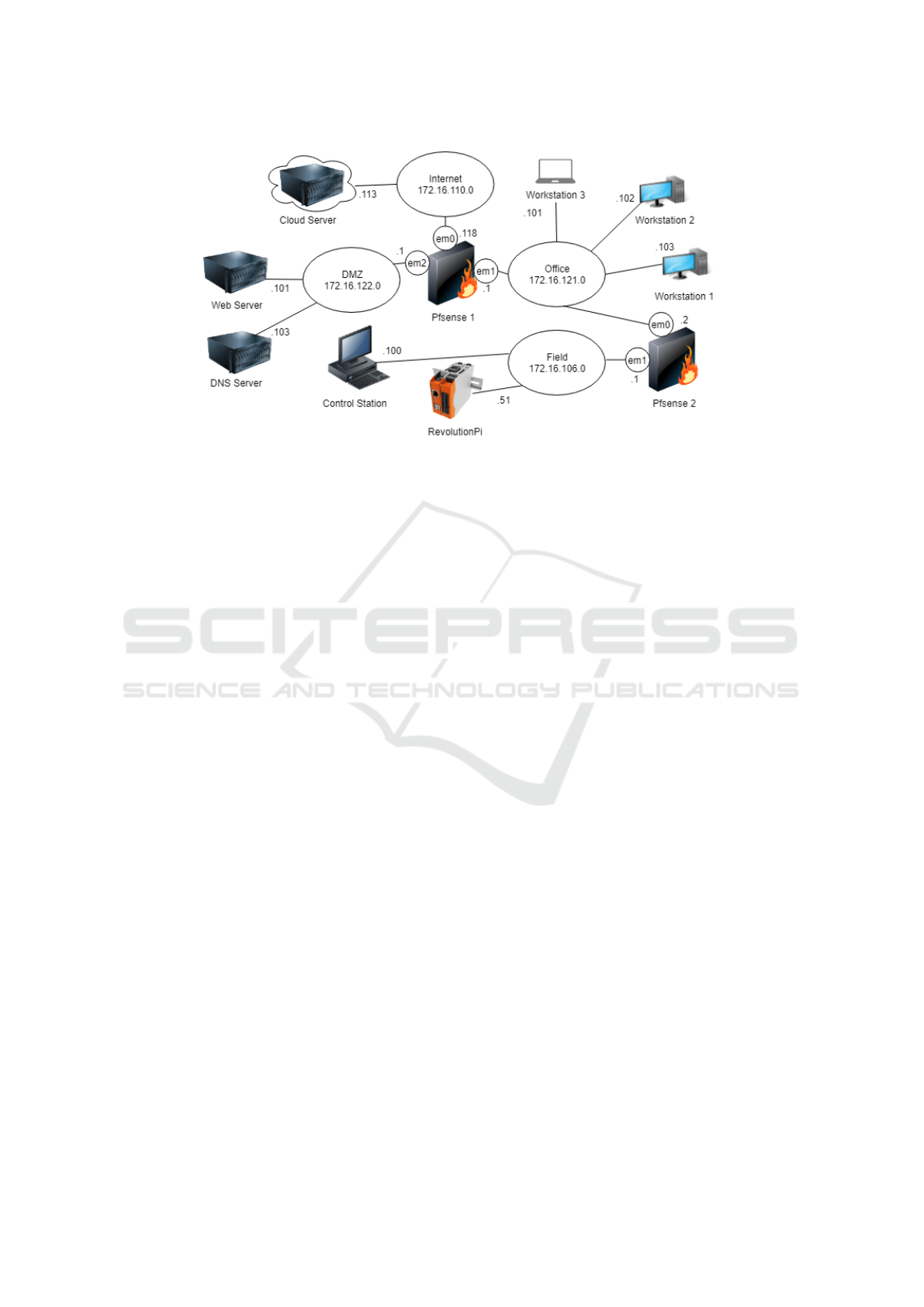
Figure 1: Example system architecture.
Due to space limitations, the remaining rules and
the configuration of the second firewall are not listed
here.
Ontological Representation. The ontological
model of the example architecture was created by
command parsing and modelling of the information
with the Web Ontology Language (OWL) Version 2
using the description logic (DL) subset (cf. (Patzer
et al., 2019)). Individual component models were
created, merged and extended by reasoning and
SWRL rules to ensure the following assumptions
about the model hold:
1. IPv4 interfaces are linked to IPv4 networks.
2. Instead of modelling every possible IPv4 address
as an individual, only the networks are modelled
as individuals. Moreover, interfaces and networks
contain data properties with numeric representa-
tions of the respective addresses.
3. The order in which the firewall rules are config-
ured is modelled via linked list (cf. Figure 2).
4. To simplify queries regarding the order of rules,
each rule has a link to all successors.
5. IPv4 subnets are inferred to be within the same
zone as their parent networks.
6. Each rule addressing an IPv4 source or destination
contains respective IPv4 interfaces.
7. Firewall types are modelled by different classes.
8. The rules are modelled as distinct individuals.
This system ontology provides a suitable model to
embed the effective configuration. However, it is not
part of the approach and therefore not the subject of
evaluation here. Rather, it serves as an “environmen-
tal example” to help the reader understand the ap-
proach.
3 RELATED APPROACHES
Previous approaches of ontology-based security anal-
ysis covering NACs can be summarized as follows:
• Approach 1 - Modelling policies in an abstract
configuration language which can be used to eval-
uate the rules and to automatically generate NAC-
specific rules (Mart
´
ınez P
´
erez et al., 2007), (Davy
et al., 2013).
• Approach 2 - Automatically translate NAC-
specific rules into an abstract configuration lan-
guage which can be used to evaluate the rules (Hu
et al., 2011), (Tong et al., 2015).
• Approach 3 - Modelling each NAC configura-
tion with language-dependent representations and
searching for issues on rule chain level (Fitzgerald
et al., 2007), (Foley and Fitzgerald, 2008), (Cor-
dova et al., 2018).
• Approach 4 - Modelling inter-policy relations
manually and searching for issues on the so cre-
ated abstract relationship (Fitzgerald et al., 2008),
(Fitzgerald et al., 2009).
In the following paragraphs, some of this research is
explained in more detail.
Research following Approach 1 concentrates on
generic policies, which are automatically trans-
formable into concrete configurations. Besides work
on general policy languages (Davy et al., 2013), the
ICISSP 2021 - 7th International Conference on Information Systems Security and Privacy
552

Table 1: Comparison of the four main classes of NAC modelling.
A 1 A 2 A 3 A 4 EC
Finding configuration issues in rule chains, like shadowed, redundant, gen-
eralized rules
1 3 4 0 (4)
Finding inter-NAC issues like inconsistencies regarding certain policies 3 2 0 1 4
Finding network-centred issues not focussing NAC-rules (cf. example ques-
tion of Section 4)
2 2 0 3 4
Providing a vendor-agnostic NAC configuration representation 4 3 0 0 2
Providing a representation covering all NAC configuration languages 2 2 0 0 3
Providing a fully automated model generation strategy 2 2 2 0 3
term most related to this approach is policy-based net-
work management (PBNM). P
´
erez et al. (Mart
´
ınez
P
´
erez et al., 2007) presented a framework and pol-
icy representation for PBNM - more precisely the dis-
tributed firewall strategy, where firewall rules are de-
fined in a centralized manner and are then enforced
at each network endpoint. Their policy representa-
tion is based on the – meanwhile outdated – OWL
mapping
8
of the common information model (CIM)
(Textor et al., 2010), which the authors extended with
concepts for the formalization of NAC policies that
are supposed to be translated to the respective NAC-
specific rules.
Approach 2 is comparable to Approach 1, but con-
centrates on the generation of the generic policies
from specific configuration. Hu et al. (Hu et al., 2011)
presented a framework to build generic policies from
arbitrary access control policies, using an ontologi-
cal approach. The authors evaluated it using a simple
firewall configuration and XACML
9
. Furthermore, as
an application of the approach, the authors showed
how redundant and conflicting configurations can be
discovered on that abstract layer. However, due to the
simplicity of the firewall configuration utilized, which
does not contain complex control, state or substitution
commands, the approach is not applicable for mod-
ern firewalls, as it is. Tong et al. (Tong et al., 2015)
presented another example of Approach 2 which also
presents a generic algorithm to create the generaliza-
tion which, according to the authors, covers all NAC
configuration languages.
Approach 1 and Approach 2 share the disad-
vantage of unpredictable expressiveness (henceforth
called Expressiveness Issue) of the generic language.
This means that it is unclear to what extend the
various configuration languages are covered by the
generic language. This is a natural issue of any lan-
guage which is supposed to formalize configurations
on a generic level. Moreover, the approaches suffer
8
https://wwwvs.cs.hs-rm.de/oss/cimowl/index.html,
last accessed: 15.12.2020
9
https://www.oasis-open.org/committees/tc home.php?
wg abbrev=xacml, last accessed: 16.12.2020
from Scalability Issues - which are discussed in more
detail later in this section - and the dependency on the
transformation algorithms. The latter dictates what
really can be analysed within the respective generic
representation of rules and is henceforth called Trans-
formation Issue.
Approach 3 enables NAC-configuration-
language-specific analysis. As an example, Foley
and Fitzgerald (Fitzgerald et al., 2007), (Foley and
Fitzgerald, 2008) proposed an OWL representation
of the Netfilter firewall and explained how this rep-
resentation is used to find configuration issues using
SWRL and reasoning. Later, the authors extended
their approach by adding risks and thresholds in order
to analyse the sufficiency of NAC policies, which
the authors suggest to use for inter-NAC analysis
(Approach 4) (Fitzgerald et al., 2008). Moreover, the
authors suggested to perform inter-NAC identifica-
tion of configuration issues, like shadowing, using
the intra-NAC approach. However, (Fitzgerald et al.,
2008) does not show how this should be scalable,
since with their method each rule would have to
be written for every possible NAC combination
separately (no generic NAC model is utilized). This
aligns to the fact that the authors later presented the
risk-based method as the inter-NAC analysis solution
of their choice in (Fitzgerald et al., 2009).
The previously mentioned Scalability Issues man-
ifest through information which needs to be evaluated
by every query or rule (Approach 1, Approach 2 and
Approach 3), vendor-specific modelling which makes
it’s application for inter-NAC analysis infeasible (Ap-
proach 3) and the necessity to manually add the rele-
vant knowledge to the model (Approach 4), instead of
generating or inferring it.
During our research, we identified six aspects
a modelling strategy of NAC configuration should
cover, in order to be adequate for security analysis.
Table 1 displays the estimated degree in which each
aspect is covered by an approach class (abbreviated
as A 1 - A 4), using a scale from 0 to 4, where 0 is no
and 4 is full coverage. Furthermore, the approach of
modelling the effective configuration (abbreviated as
Efficient Semantic Representation of Network Access Control Configuration for Ontology-based Security Analysis
553

EC) is analogously assessed and thus presents a quan-
tification of the improvement compared to related ap-
proaches.
The table shows that even approaches targeting a
certain aspect are not being estimated to cover the as-
pect to a full extend. The main reasons for this esti-
mation are their expressiveness and scalability issues
which are significantly mitigated by the approach de-
scribed in the following section. A more in depth dis-
cussion of the effective configuration approaches’ as-
sessment is provided in Section 5.
4 EFFECTIVE CONFIGURATION
This section presents the effective configuration ap-
proach which provides a solution for the Expressive-
ness Issue, Transformation Issue and Scalability Is-
sues.
Listing 2 describes the strategy of generating the
effective configuration model, which can be applied
for common NAC-configurations, as pseudo code.
This strategy is configuration language agnostic, but
contains configuration-language-specific functions an
implementation has to provide.
Listing 2: Pseudo code describing the strategy to generate
the effective configuration representation.
1 integrate additional config ( Λ )
2 transform action types( Λ )
3 f o r e a c h s ∈ Σ{
4 Λ
0
s
= transform to last match wins ( Λ
s
)
5 i n t e g r a t e Λ
0
s
i n t o Λ
6 }
7 f o r e a c h r u l e r ∈ Λ {
8 p
r
= get pattern ( r )
9 P = get overlapping patterns ( p
r
)
10 i f P 6=
/
0 {
11 P
0
= split expand reduce ( P , p
r
)
12 remove P from Π
13 add P
0
t o Π
14 } e l s e {
15 add p
r
t o Π
16 }
17 }
18 ϒ = create flow concepts ( Π )
19 f o r e a c h p ∈ Π {
20 f o r e a c h t ∈ ϒ {
21 i f p c o n t a i n s t− s p e c i f i c
i n f o r m a t i o n i
t
{
22 add to ontology ( i
t
, p )
23 }
24 }
25 }
The following list provides definitions and clarifi-
cations for Listing 2:
• Λ contains the rule chain, i.e. the main con-
figuration of the NAC instance. It is assumed
that any substitution or similar additional con-
figuration has already been resolved, or is trans-
formed into the rule chain as part of the inte-
grate additional config routine, so that Λ after
this function only consists of the rule chain and
any necessary configurations which cannot be in-
tegrated. Listing 1 contains an example for a
necessary substitution in the form of domain and
http which are placeholders for the actual ports
and need to be replaced.
• transform action types performs the transforma-
tion of the rule’s actions to “allow” and “block”.
This reduction is useful because later on the ex-
act behaviour of the NAC instance is no longer
relevant. Instead, it is only of interest whether
certain network traffic is allowed to pass the in-
stance or not. As an example, two actions that
block ICMP, where one sends a response on re-
ceiving the ICMP package and the other does not,
would both be substituted with the “block” action.
• Σ is the set of evaluation strategies of the NAC
configuration.
• Λ
s
⊂ Λ is the partial rule chain of an evaluation
strategy s ∈ Σ.
• “integrate Λ
0
s
into Λ” means that the modified
partial rule chain Λ
0
s
replaces the original partial
rule chain Λ
s
in Λ such that it integrates into the
correct overall order. This reordering is important
because the evaluation strategy of Λ
0
s
is different
to the strategy ofΛ
s
.
• Π contains both, the patterns for allowed and for
blocked traffic, in order to avoid a significant ex-
pansion of the algorithm with various redundancy
due to the additional case distinctions. Instead, all
pattern processing functions are defined as action-
type-aware.
• get overlapping patterns returns the patterns
which overlap with the passed pattern.
• split expand reduce creates as many sub-patterns
as necessary to represent the corresponding
passed patterns without containing contradictions
regarding the associated actions. This is explained
in more detail later in this section.
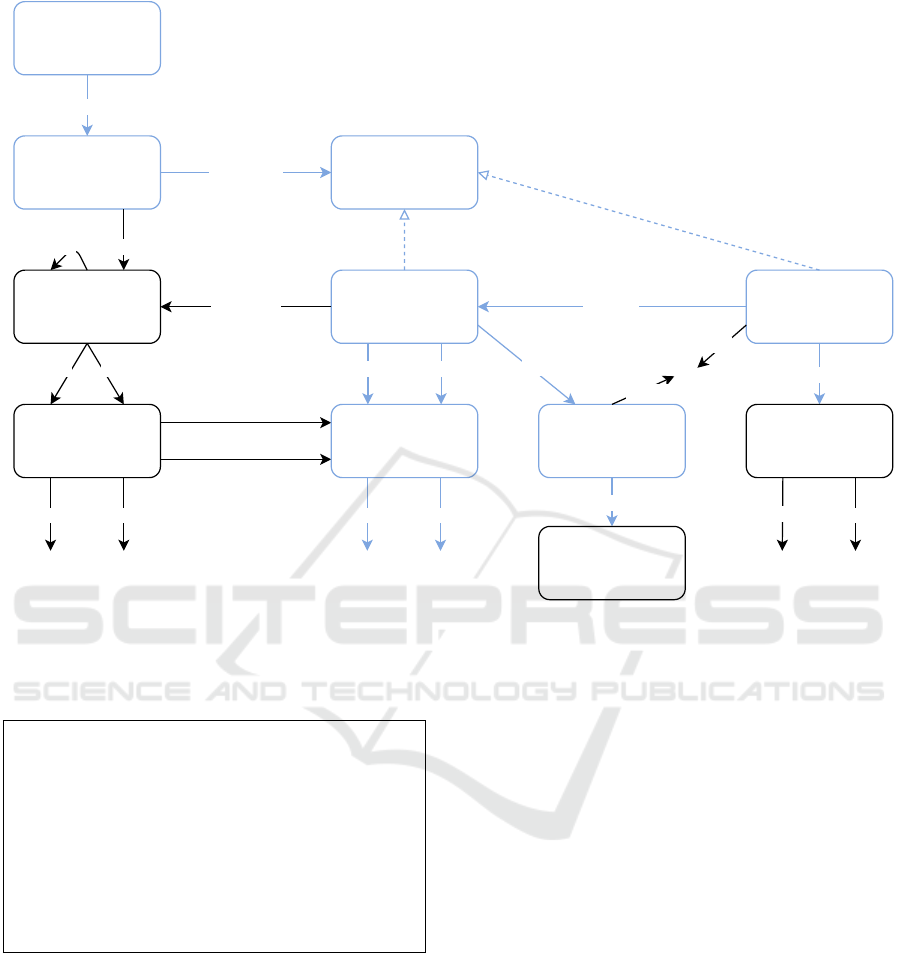
• create flow concepts creates the flow concepts
that do not yet exist in the model. These are
classes and roles that can be used per combina-
tion of action, identifier type (e.g. IPv4 address
range or ports), ISO/OSI layer and protocol to rep-
resent the respective subpattern, including its re-
lationships to other subpatterns and the respective
ICISSP 2021 - 7th International Conference on Information Systems Security and Privacy
554

rules (if also part of the model). An example of
this is shown in Figure 2.
• ϒ is the ordered list of flow concept types (cf.
AllowedIpV4Flow and AllowedTcpFlow in Fig-
ure 2). The order of the list is ascending with ref-
erence to the concerned ISO/OSI layer.
• add to ontology adds the passed information of
the pattern to the model using the flow concepts
of the corresponding flow concept type. In this
step, the already added information of the same
pattern is also linked to the newly added informa-
tion (cf. usesFlow from Figure 2). For the case of
allow actions, this reflects that each child concept
of AllowedFlow (e.g. AllowedEthernetFlow,
AllowedIpV4Flow and AllowedTcpFlow) is ei-
ther a self-contained pattern or a refinement of an-
other AllowedFlow.
The following paragraphs provide additional in-
sights to the strategy.
The first part of the strategy (lines 1-6) generalizes
the NAC configuration, by dissolving substitutions -
like names for IP networks or hosts, service names
for port numbers or NAT tags for hosts - and by trans-
forming individual processing control strategies into
a “last-match-wins” strategy. For pfSense firewalls,
the latter can be achieved by separating the normal
from the quick rules, reversing the order of the quick
rules and concatenating the list of normal rules to the
reversed list of quick rules.
Since each rule can be interpreted as a pattern and
an action, in lines 7-17 the algorithm iterates over the
patterns, derives which patterns overlap with already
processed ones and adds the others to the pattern list.
However, if a pattern p
r
overlaps with an already pro-
cessed one, the following cases can occur:
1. Patterns overlap with p
r
partially and the respec-
tive rules have a different action than r.
2. Patterns overlap with p
r
partially and the respec-
tive rules have the same action as r.
In the first case, each already processed pattern p will
be split into the parts of the pattern which are not cov-
ered by p
r
and the parts covered by p
r
. The first parts
are reintroduced to the stored pattern as substitution
for p, while the second parts get substituted by p
r
.
In the second case, the already processed patterns are
merged with p
r
. Patterns overlapping with other pat-
terns occur in every NAC configuration, since each
rule overlaps with the default rules (cf. rules 1 and 2
of Listing 1). During the processing of the algorithm,
Π remains consistent and free of contradictions.
Lines 18-25 address the actual modelling of patterns
for allowed or blocked traffic, i.e. the effective config-
uration. The already referenced Figure 2 displays an
excerpt of a model for allow patterns. As the diagram
visualizes, each allowed flow is linked to the network
knowledge of the model (cf. Section 2), which sig-
nificantly simplifies queries and processing tasks that
include, but are not limited to, the respective NAC
instance. Furthermore, the blue concepts and prop-
erties are part of the effective configuration whereas
the black concepts and properties only exist if the
NAC configuration is modelled as well. This is op-
tional, but has the advantage of supporting the intra-
NAC misconfiguration detection Approach 3 allows
(cf. Section 3). Moreover, if issues are discovered
when analysing the effective configuration, conclu-
sions on the causing rule can obviously only be drawn
if a representation of the rule is present and linked.
For this, an identifier of the rule would already be
a sufficient degree of knowledge, although existing
misconfiguration detection approaches would not be
applicable.
Example Analysis. An ontology, built using the
method described in the preceding paragraphs,
enables configuration-language-agnostic rules and
queries for connection- or traffic-based model exten-
sion and analysis (cf. Section 3). To substantiate this
claim, the following paragraphs present an exemplary
analysis based on the following question:
Is there a TCP connection possible from the Field
Zone (containing the connection initiator) to the
DMZ?
To shorten the here described example, let the
question only be answered positively if a possible
TCP/IP link can be derived, able to pass both fire-
walls, which implies that no bypasses or pivoting
opportunities are evaluated. Moreover, the example
analysis assumes that only one firewall is connected
to the Field Zone and only one path exists from the
Field Zone to the DMZ, with respect to firewalls to
pass.
In a first step, the SWRL rule in Listing 3 links
the IPv4 flows directly to the known subnets of their
source networks. An analogue rule is applied for des-
tination networks as well.
Listing 3: SWRL rule adding source networks to allowed
IPv4 flows to simplify later rules and queries.
1 Allowed Ip V4Flow ( ? a i f )
2 ˆ s r c N e t w o r k ( ? a i f , ? s r c N e t )
3 ˆ p a r e n t N e t w o r k ( ? subN et , ? s r c N e t )
4 −> s r c N e t w o r k ( ? a i f , ? s u bNet )
In consequence, the query from Listing 4 directly
results in a selection of all firewalls, supporting the
requested connection.
Efficient Semantic Representation of Network Access Control Configuration for Ontology-based Security Analysis
555
Firewall
Configuration
firewallConfig
Rule
firstRule
srcInterface
IpV4Interface
dstInterface
nextRule
ipAddress networkPrefix
assignedToNetwork
isInNetwork
AllowedIpV4Flow
allowedFlow
IpV4Network
srcNetwork dstNetwork
AllowedFlow
ipAddress networkPrefix
xsd:integer xsd:byte xsd:integer xsd:byte
AllowedTcpFlow
usesFlow
dstPortRange
PortRange
portMin
xsd:integer
AllowedInbound
EthernetFlow
usesFlow
ethernetInterface
portMax
xsd:integer
...
firewallRule
firewallRule
firewallRule
EthernetInterface
Figure 2: Excerpt of the effective configuration ontology.
Listing 4: SQWRL statement selecting all firewalls, which
have a matching allowed flow.
1 c o n t a i n s N e t w o r k ( F i e l d Z o n e , ? sn )
2 ˆ c o n t a i n s N e t w o r k (DMZ, ? dn )
3 ˆ F i r e w a l l ( ? f )
4 ˆ f i r e w a l l C o n f i g ( ? f , ? f c )
5 ˆ AllowedTcp Flow ( ? a t f )
6 ˆ a l l o w e d Fl o w ( ? fc , ? a t f )
7 ˆ u s e s F l o w ( ? a t f , ? a i f )
8 ˆ All owedIpV4F low ( ? a i f )
9 ˆ s r c N e t w o r k ( ? a i f , ? s n )
10 ˆ d s t N e t w o r k ( ? a i f , ? dn )
11 −> s q w r l : s e l e c t ( ? f )
Consequently, if the result is empty, the link is not
allowed and vice versa.
Let’s assume that the analysis should further de-
termine whether a path from the Field Zone to the
DMZ exists which only passes firewalls from the
queried set. Because each IPv4 interface (including
the ones of firewall components) is directly linked
to an IPv4 network, a transitive “connected” rela-
tion between firewalls can be inferred, if they share
a network. If Listing 4 is extended by the condition
connected(?f, ?f), the additional requirement is
fulfilled.
5 DISCUSSION AND FUTURE
WORK
As this section shows, the effective configuration ap-
proach does not suffer from Scalability Issues, since
the model is created once and generic model exten-
sion and analysis can be applied to it. Instead of
formalizing configuration on a generic or abstract
level, the effective configuration strategy models all
protocol-specific patterns that can trigger NAC ac-
tions. This is the reason for the allocation of only 2
points for aspect 4 in Table 1.
The strategy expresses all network-level effects of
the configuration by design and thus does not suffer
from the Expressiveness Issue. Furthermore, if used
accompanied by a model of the rule chain, the ap-
proach can even provide inference of a set of rules
responsible for an identified problem. Therefore, al-
though the approach does not improve rule-level anal-
ysis, to the best of our knowledge, it is the first ap-
proach to provide traceability to corresponding NAC
rules as part of an identification of a cross-NAC prob-
lem. The ability to support configuration-language-
specific rule models implies that the approach fully
ICISSP 2021 - 7th International Conference on Information Systems Security and Privacy
556

supports Approach 3 which means that it indirectly
earns the high score of aspect 1 in Table 1. In addi-
tion, the fixed strategy of deriving the disjoint patterns
accompanied by their affiliation to the block or al-
low actions mitigates the Transformation Issue. Nev-
ertheless, it should be noted that a reverse transfor-
mation has not been analysed. This and the fact that
still a configuration-language specific transformation
is needed once for every language is the reason why
the approach does not get allocated the high score re-
garding aspects 5 and 6 in Table 1.
Stateful control and filtering configurations are cur-
rently ignored by our implementations. In future work
we will analyse to what extend they should be part of
the effective configuration, resp. linked to it.
6 CONCLUSION
This paper discusses approaches for modelling net-
work access control configuration for security analy-
sis, identifies issues and proposes an alternative ap-
proach solving these issues. For this, the effective
configuration of rule chains is derived and modelled
in a configuration-language-agnostic way. The paper
shows that the approach does not suffer from scala-
bility problems, since the model is created once and
generic model extensions and analyses can be ap-
plied to it. The effective configuration represents all
protocol-specific patterns that can trigger actions in a
rule chain. Therefore, it expresses all network-level
effects of the configuration and, if used with a model
of the rule chain, can even provide inference of a set
of rules responsible for an identified problem. There-
fore, the effective configuration approach is an im-
provement over existing approaches and, moreover,
can be used in combination with them.
ACKNOWLEDGEMENTS
This work has been funded by the Federal Ministry
of Education and Research (BMBF, Germany) in the
project AICAS (project number 16KIS1063K).
REFERENCES
Cordova, R. F., Marcovich, A. L., and Santivanez, C. A.
(2018). An Efficient Method for Ontology-Based
Multi-Vendor Firewall Misconfiguration Detection: A
Real-Case Study. In Cely Callejas, J. D., editor, 2018
IEEE ANDESCON, pages 1–3, [Piscataway, New Jer-
sey]. IEEE.
Davy, S., Barron, J., Shi, L., Butler, B., Jennings, B.,
Griffin, K., and Collins, K. (2013). A language
driven approach to multi-system access control. 2013
IFIP/IEEE International Symposium on Integrated
Network Management (IM 2013), pages 1004–1008.
Fitzgerald, W. M., Foley, S. N., and Foghl
´
u, M.
´
O. (2008).
Network access control interoperation using semantic
web techniques. In WOSIS, pages 26–37.
Fitzgerald, W. M., Foley, S. N., Foghl
´
u, M.
´
O., et al.
(2009). Network access control configuration man-
agement using semantic web techniques. Journal
of Research and Practice in Information Technology,
41(2):99.
Fitzgerald, W. M., Foley, S. N., and O’Foghlu, M. (2007).
Confident firewall policy configuration management
using description logic. In 12th Nordic Workshop on
Secure IT Systems, pages 11–12.
Foley, S. N. and Fitzgerald, W. M. (2008). Semantic web
and firewall alignment. In 2008 IEEE 24th Inter-
national Conference on Data Engineering Workshop,
pages 447–453.
Gruber, T. R. (1993). A translation approach to portable
ontology specifications. Knowledge Acquisition,
5(2):199–220.
Hu, H., Ahn, G.-J., and Kulkarni, K. (15.10.2011 -
18.10.2011). Ontology-based policy anomaly man-
agement for autonomic computing. In Proceedings
of the 7th International Conference on Collaborative
Computing: Networking, Applications and Workshar-
ing. IEEE.
Khelf, R. and Ghoualmi-Zine, N. (26.11.2018 -
27.11.2018). Ipsec/firewall security policy anal-
ysis: A survey. In 2018 International Conference on
Signal, Image, Vision and their Applications (SIVA),
pages 1–7. IEEE.
Mart
´
ınez P
´
erez, G., Garc
´
ıa Clemente, F. J., and G
´
omez
Skarmeta, A. F. (2007). Managing semantic–aware
policies in a distributed firewall scenario. Internet Re-
search, 17(4):362–377.
O’Connor, M. and Das, A. (2009). SQWRL: A Query
Language for OWL. In Proceedings of the 6th In-
ternational Conference on OWL: Experiences and Di-
rections - Volume 529, OWLED’09, pages 208–215,
Aachen, DEU. CEUR-WS.org.
Patzer, F., Volz, F., Usl
¨
ander, T., Blocher, I., and Beyerer, J.
(2019). The industrie 4.0 asset administration shell as
information source for security analysis. In 2019 24th
IEEE International Conference on Emerging Tech-
nologies and Factory Automation (ETFA), pages 420–
427. IEEE.
Textor, A., Stynes, J., and Kroeger, R. (2010). Transfor-
mation of the common information model to owl. In
Current trends in web engineering, Lecture Notes in
Computer Science SL 3, Information Systems and Ap-
plication, incl. Internet/Web and HCI, pages 163–174,
Berlin. SpringerLink.
Tong, W., Liang, X., Li, X., Zhao, J., and Liang, X.
(2015). An analysis method of nac configuration con-
flict based on ontology. In Proc. of the 3rd Interna-
tional Conference on Digital Enterprise and Informa-
tion Systems (DEIS2015), page 46.
Efficient Semantic Representation of Network Access Control Configuration for Ontology-based Security Analysis
557
